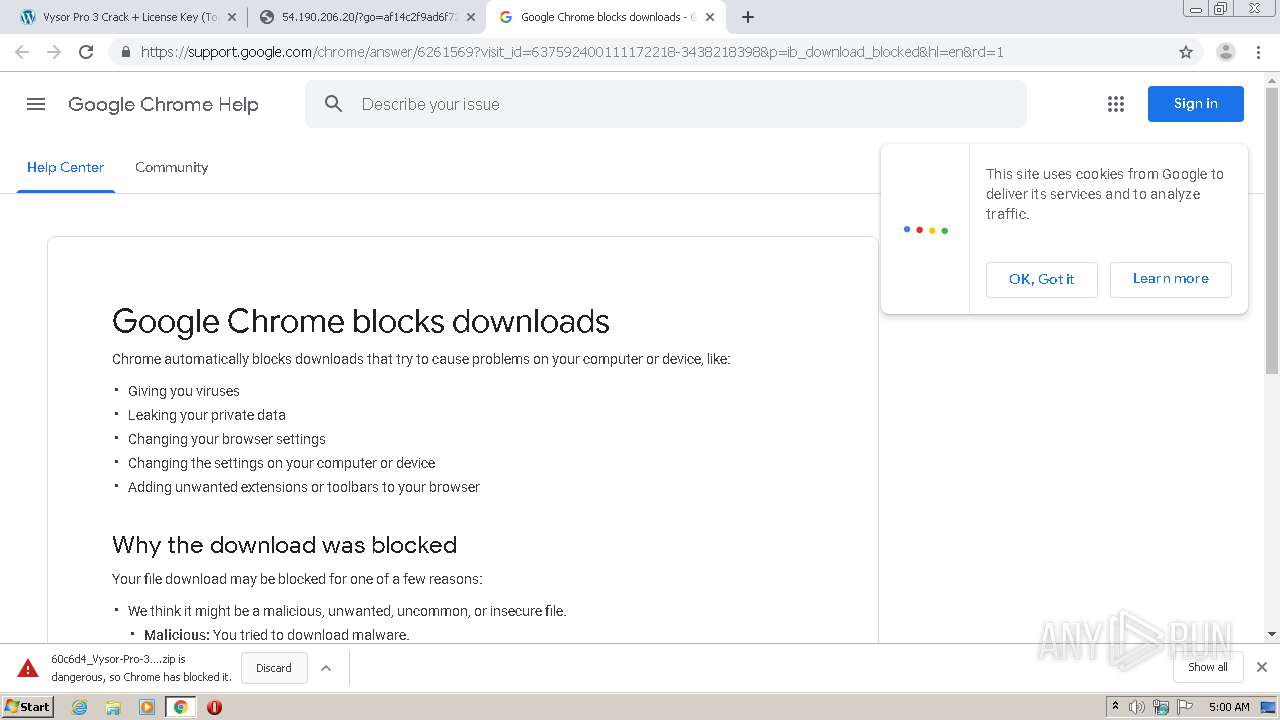
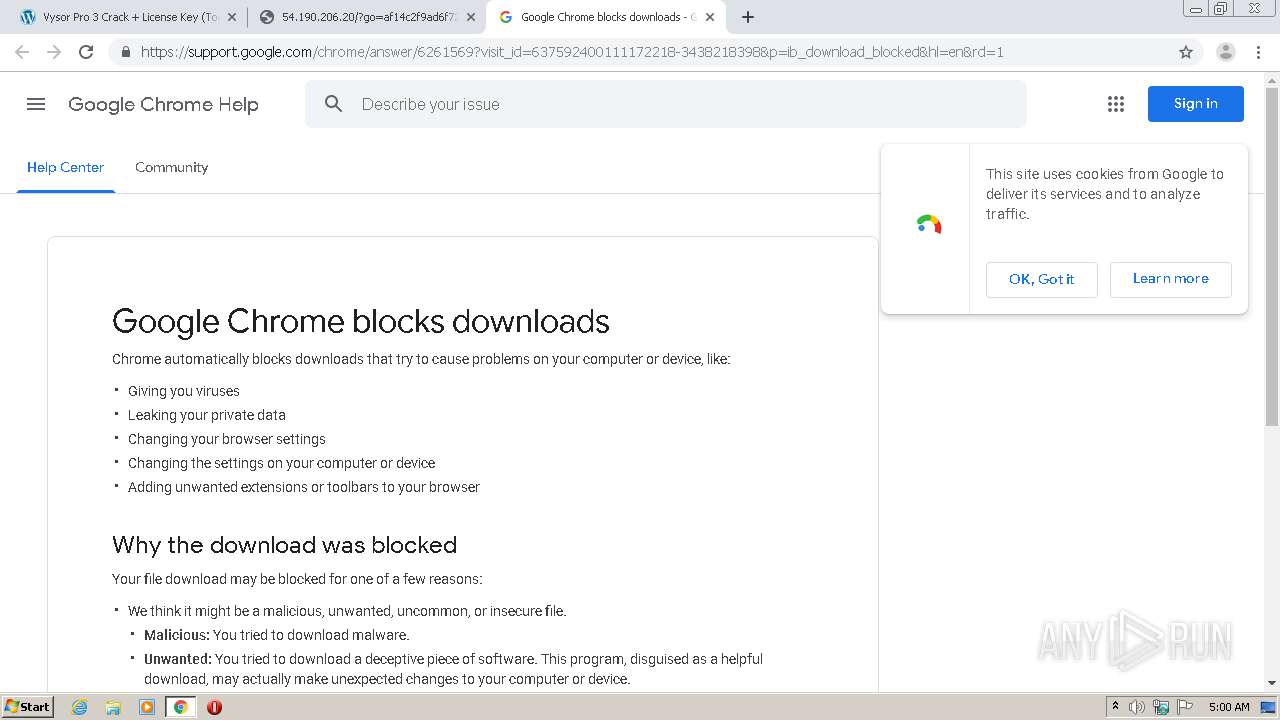
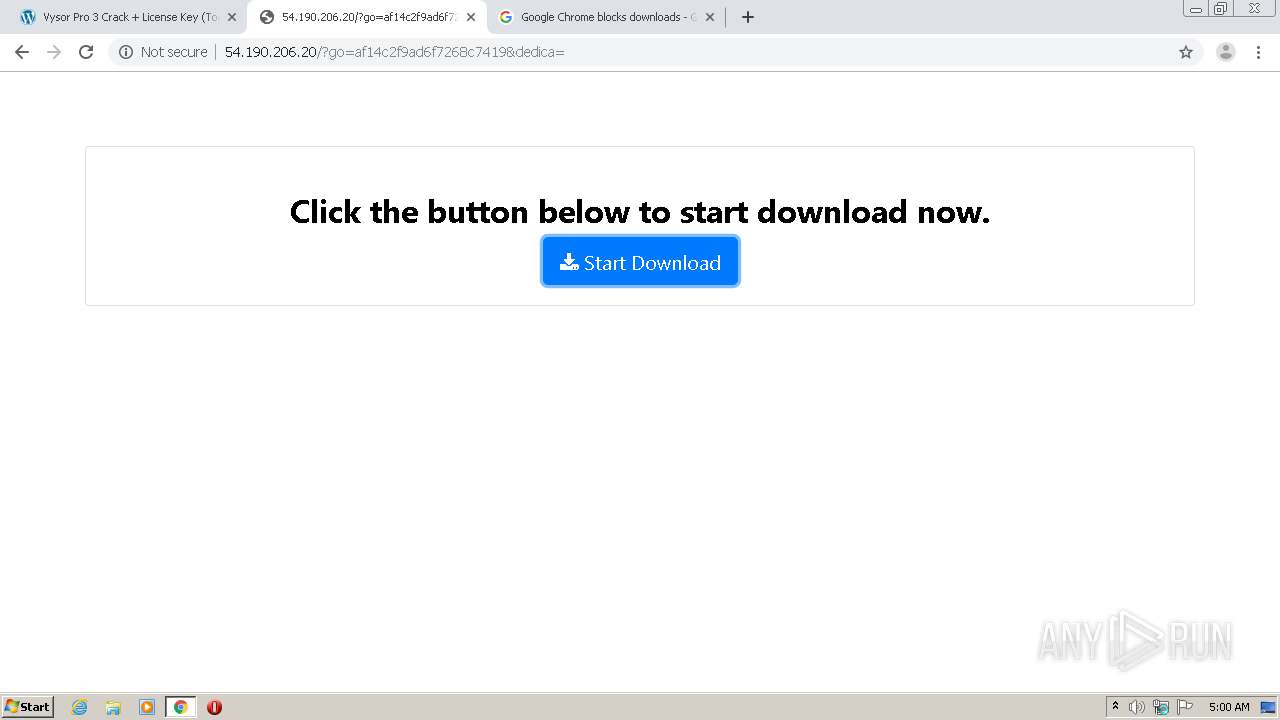
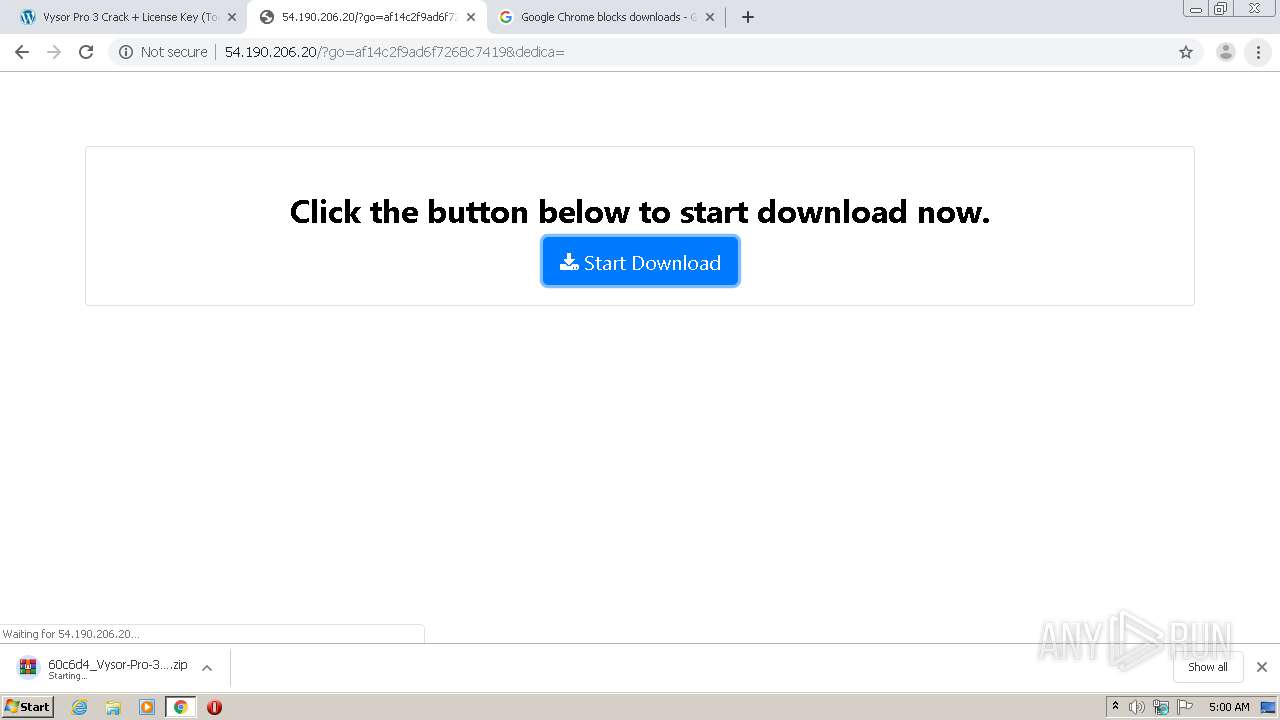
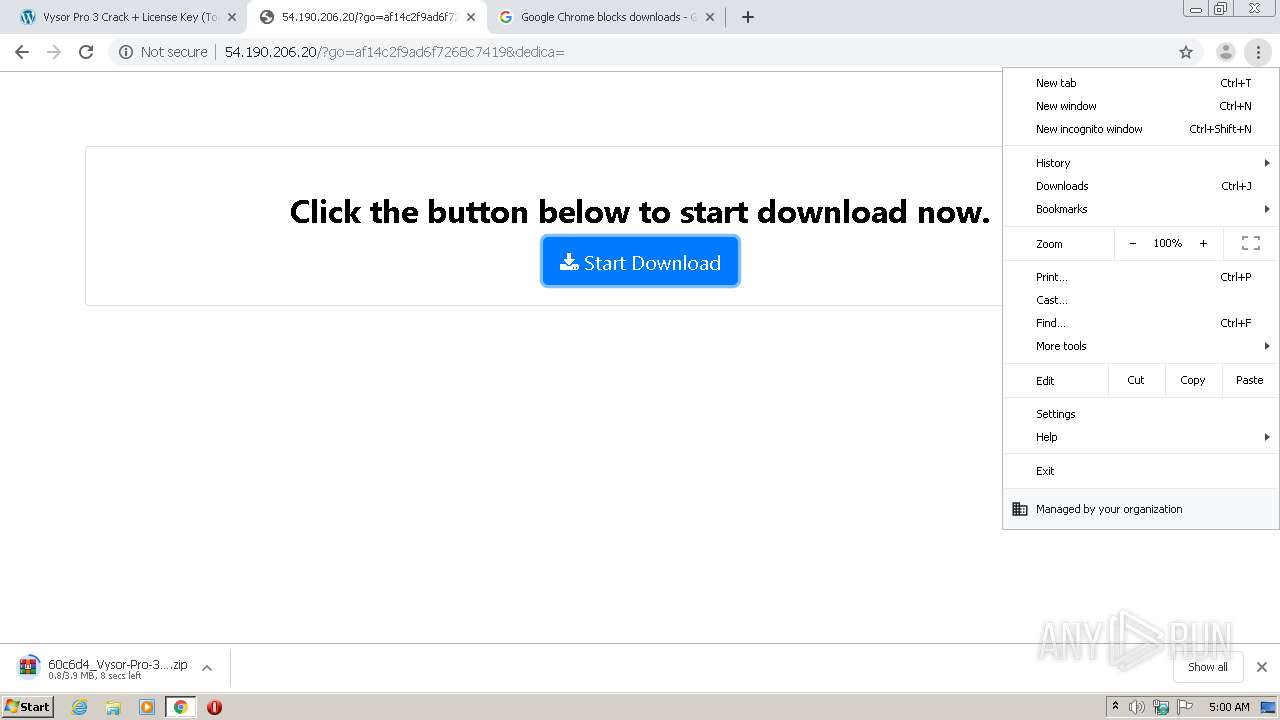
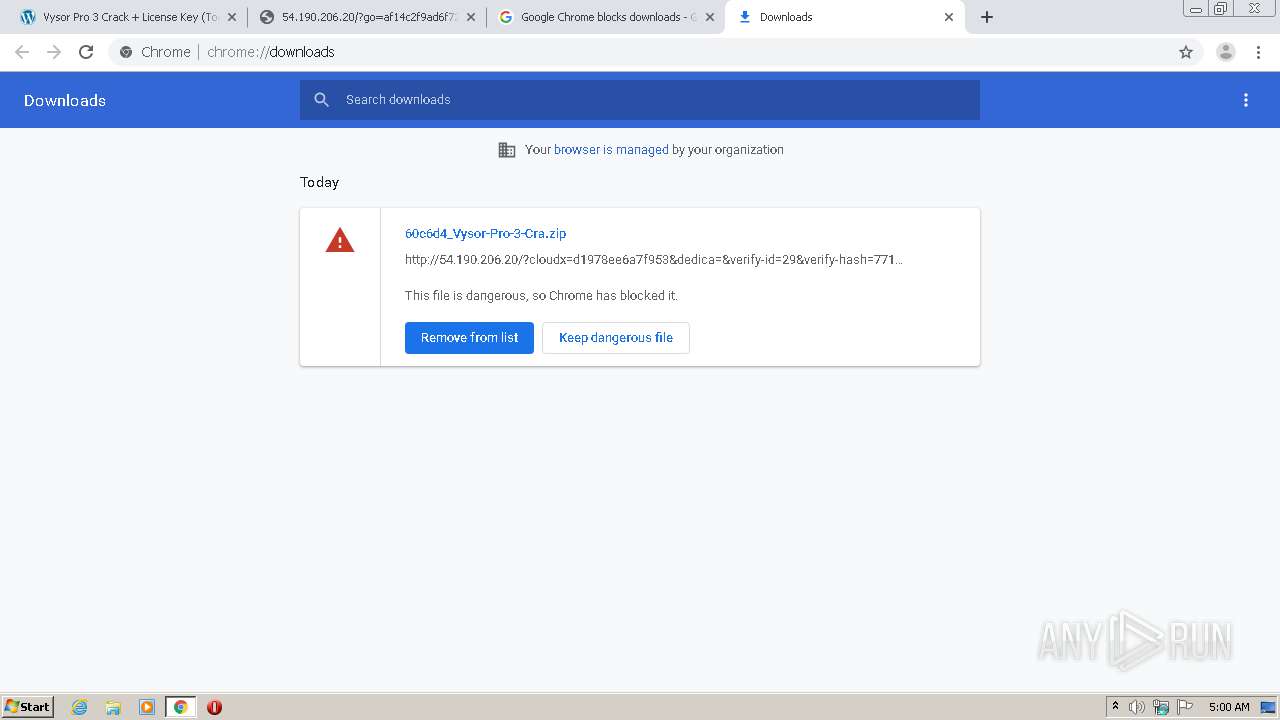
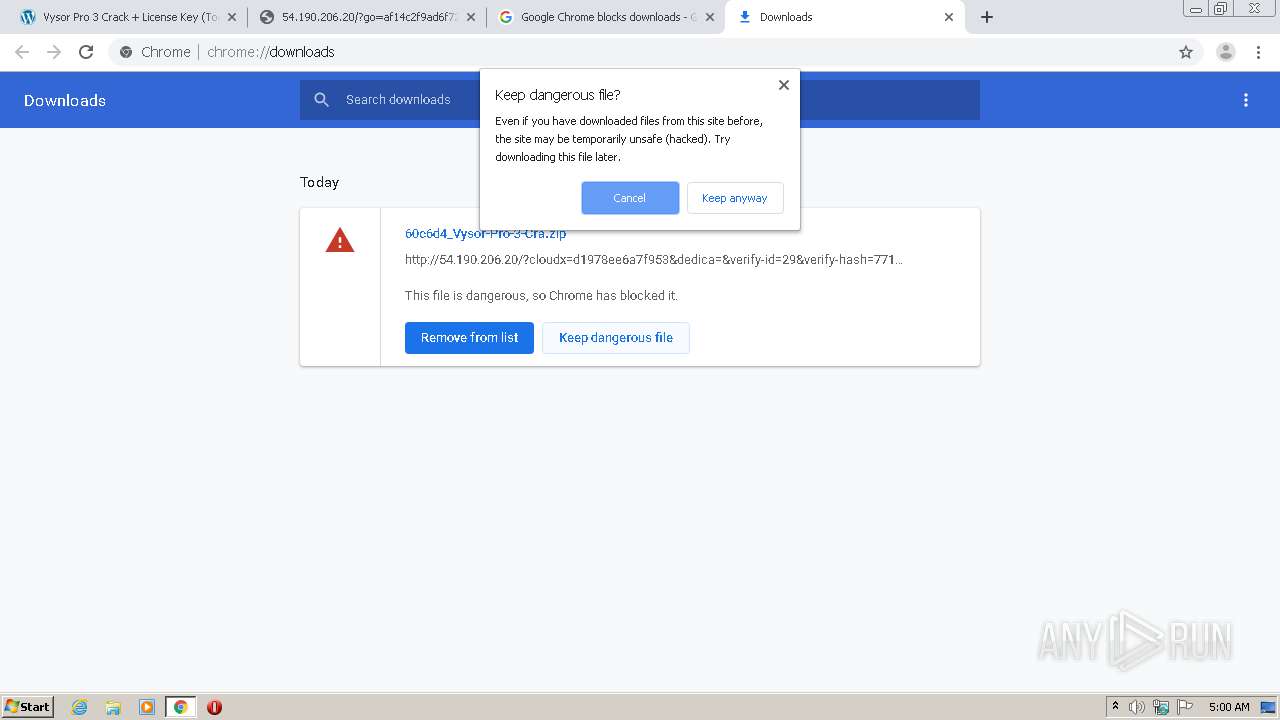
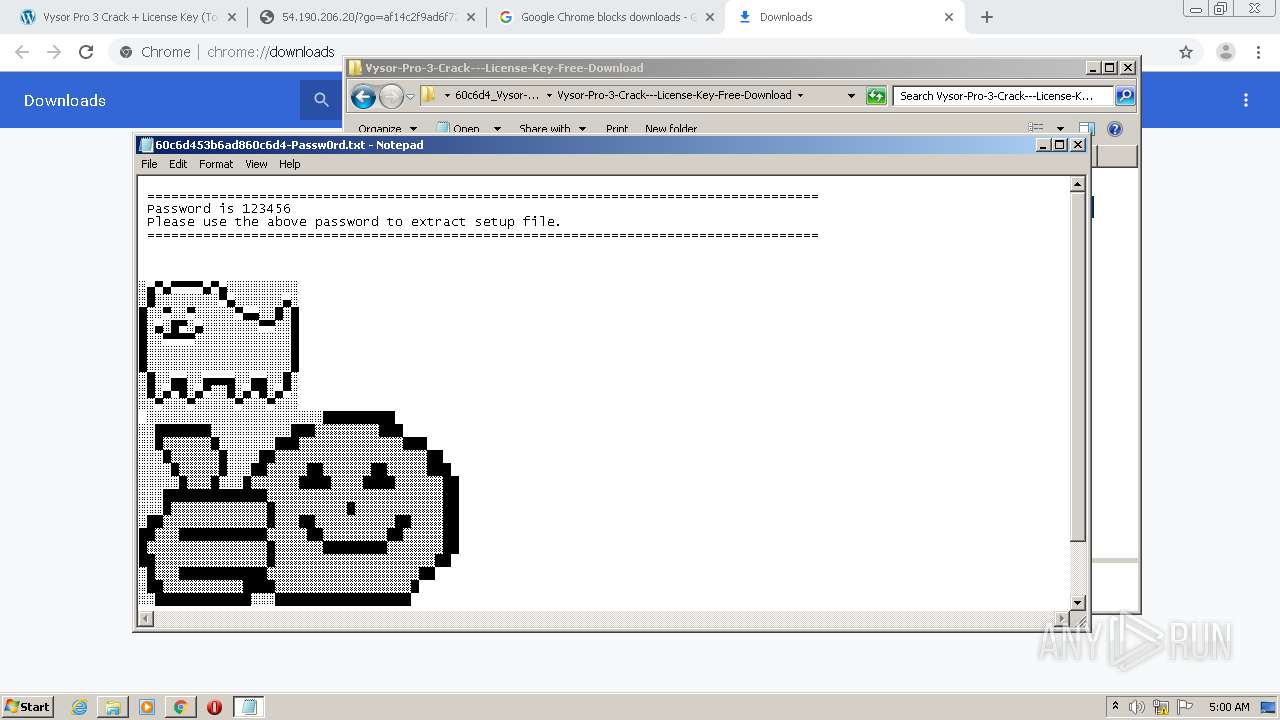
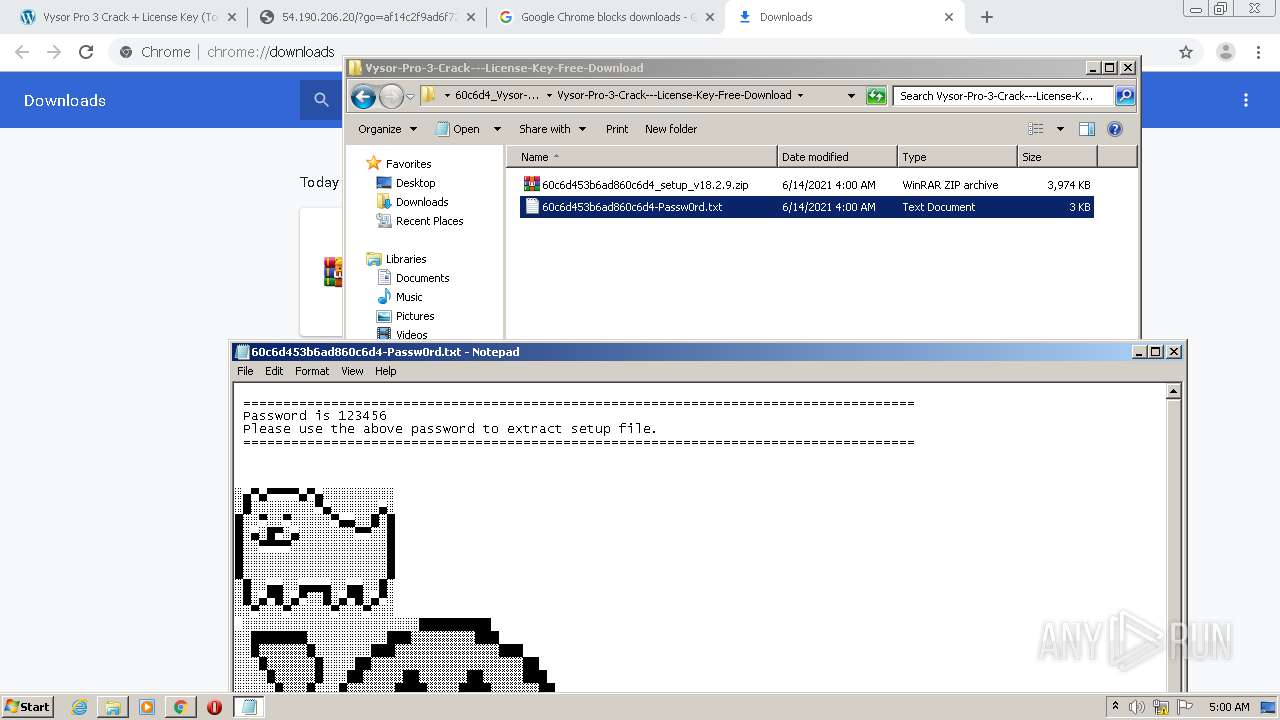
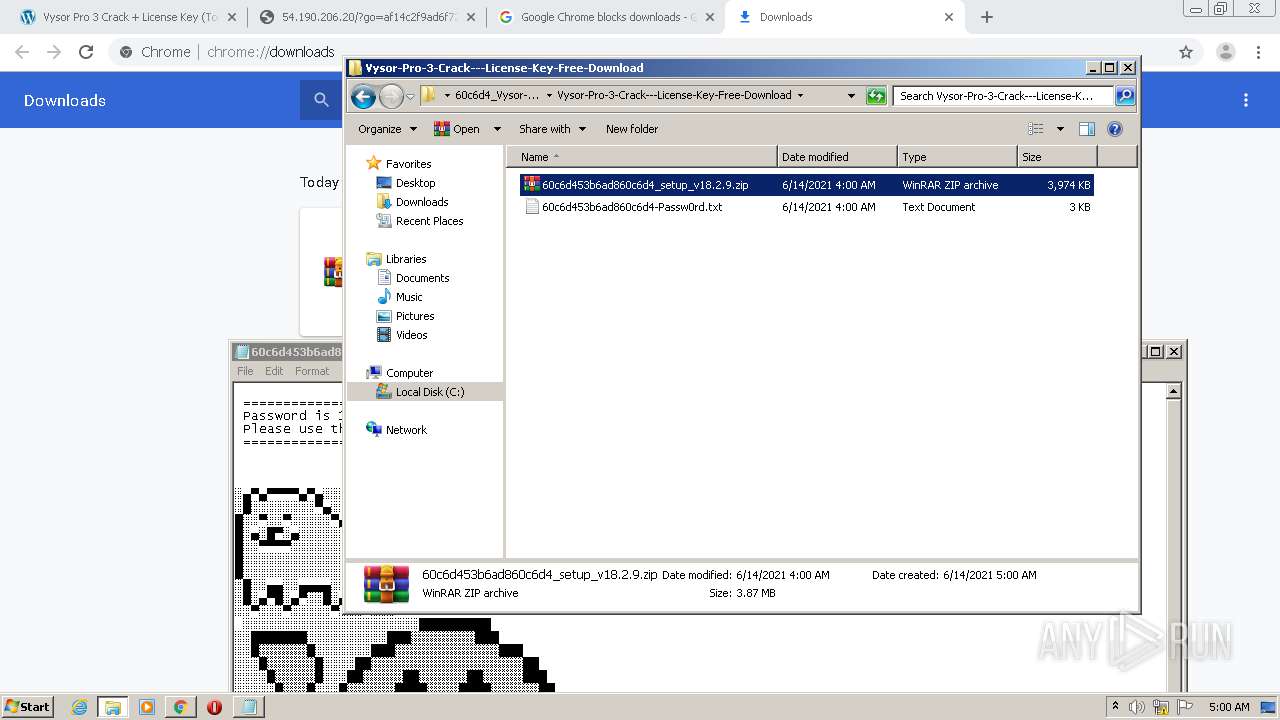
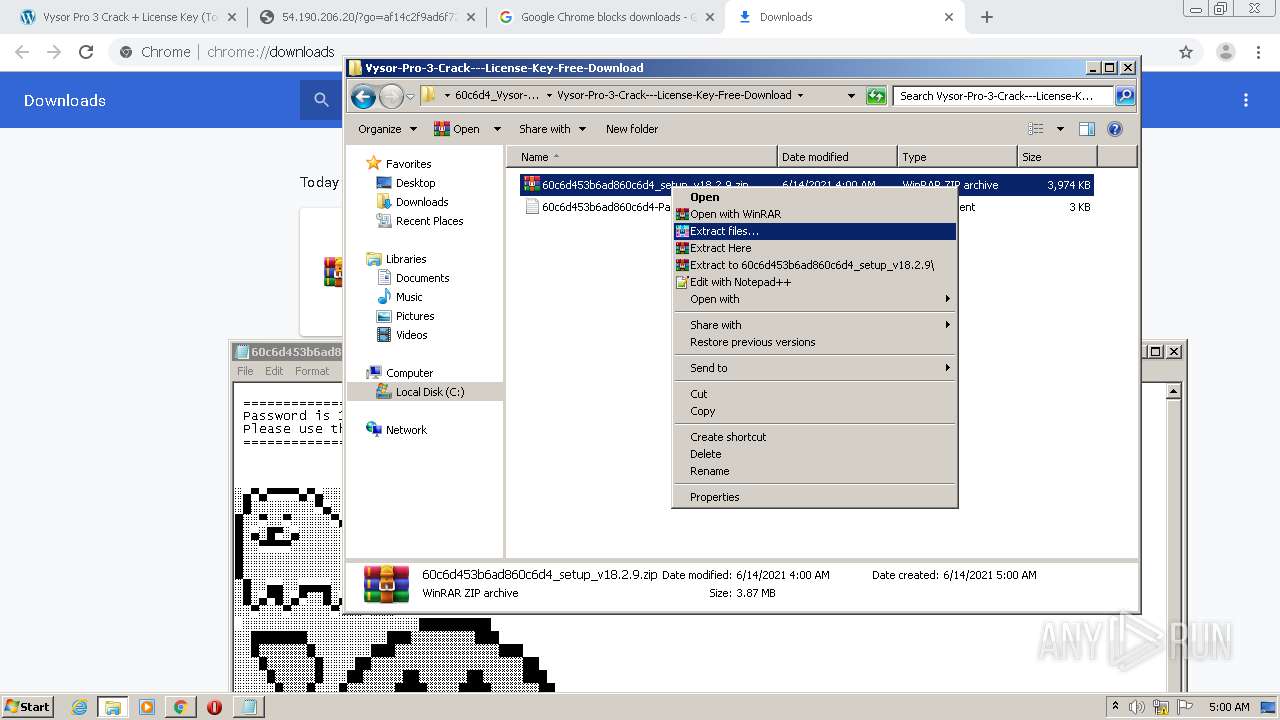
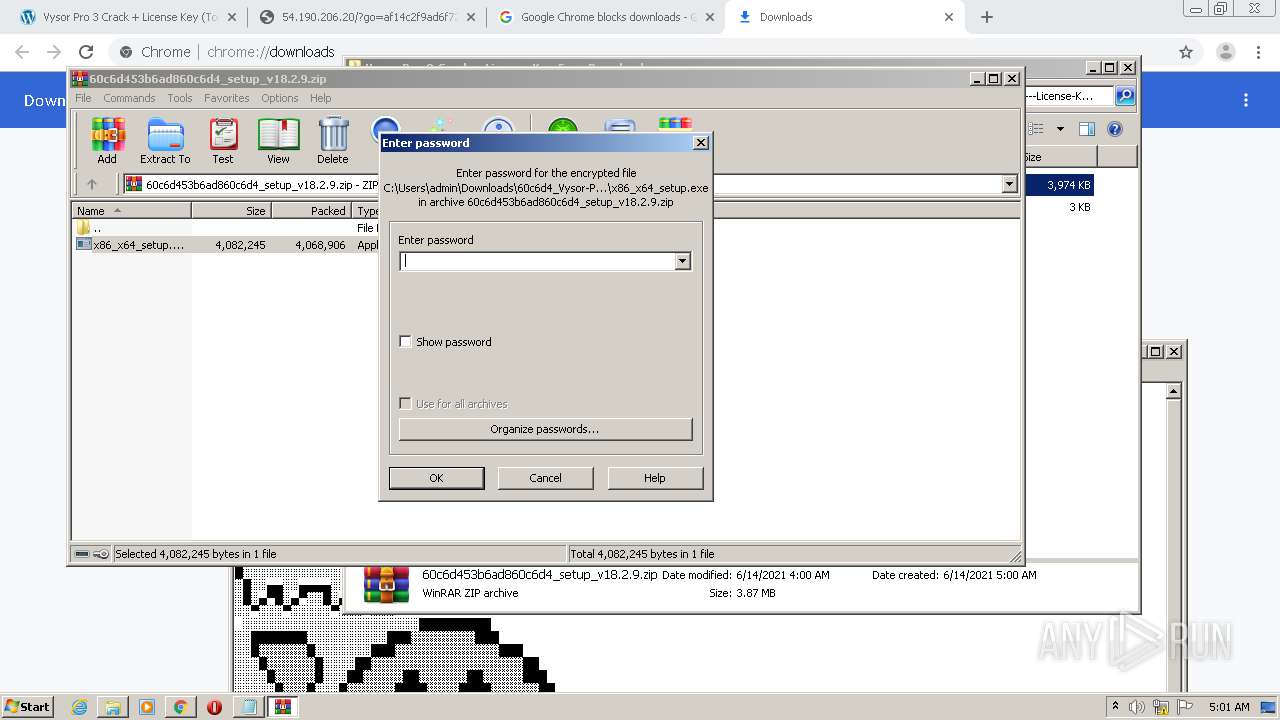
| URL: | https://crackkits.com/vysor-pro-crack/ |
| Full analysis: | https://app.any.run/tasks/bc56a0a4-c541-4e41-9083-0575fc3a77cf |
| Verdict: | Malicious activity |
| Threats: | Danabot is an advanced banking Trojan malware that was designed to steal financial information from victims. Out of the Trojans in the wild, this is one of the most advanced thanks to the modular design and a complex delivery method. |
| Analysis date: | June 14, 2021, 03:59:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FEEE475F1ED18154442D67E347103798 |
| SHA1: | 1B698F5DAB2D11AA17FA2DCF8BE9DC124CB4DDD1 |
| SHA256: | C86CE795CAAE1633E243C1B6656FE932CDE395895EB217F4BFF7D4FAAE775901 |
| SSDEEP: | 3:N8KSWLGTKTJVMl:2KSWLNy |
MALICIOUS
Application was dropped or rewritten from another process
- x86_x64_setup.exe (PID: 1840)
- x86_x64_setup.exe (PID: 2400)
- setup_installer.exe (PID: 3032)
- metina_5.exe (PID: 3664)
- metina_2.exe (PID: 1760)
- metina_3.exe (PID: 3756)
- metina_1.exe (PID: 648)
- metina_6.exe (PID: 2224)
- metina_4.exe (PID: 2664)
- setup_install.exe (PID: 2576)
- jfiag3g_gg.exe (PID: 3764)
- ovkclsFeaGxsWSFI43MgtqQE.exe (PID: 3020)
- qHdNlR18fgOe7MhumSEpTmir.exe (PID: 3380)
- NHv27pefor9cjMZxQPyaoTxI.exe (PID: 3844)
- rEyWPHzEjwsMBXGpHUKTBrhV.exe (PID: 960)
- NHv27pefor9cjMZxQPyaoTxI.exe (PID: 992)
- YrzSoesjiLwxBCoMxHQZirVc.exe (PID: 4060)
- p8g4aIxrVWYViEzCIwRjDG3Q.exe (PID: 3864)
- 4S6ougCAgc8iShZEDJo0kSnE.exe (PID: 2832)
- jfiag3g_gg.exe (PID: 1512)
- Browzar.exe (PID: 1520)
- ix78ESOrnjfX.exe (PID: 3956)
- N45w47HnqWFawEkl0bru5UlP.exe (PID: 2420)
- rMVZCe2lp19v9IjXoRM6IDf9.exe (PID: 3388)
- ovkclsFeaGxsWSFI43MgtqQE.exe (PID: 3304)
- nUcWWy3PkrkGIOnGIjiZTNEZ.exe (PID: 3584)
- xklWwL5ZQDKR8P3RorxcFDlW.exe (PID: 1556)
- LF0oWSD2TqJjfvQ1dz0Eeecm.exe (PID: 2372)
- ultramediaburner.exe (PID: 3180)
- Sq6dX94rnN0wqrGHutTck93N.exe (PID: 964)
- rMVZCe2lp19v9IjXoRM6IDf9.exe (PID: 1480)
- Wefecasofe.exe (PID: 2744)
- nUcWWy3PkrkGIOnGIjiZTNEZ.exe (PID: 3072)
- 6iawqAht8OEFOcBQIcovYGl6.exe (PID: 1376)
- ZHyvylevyhu.exe (PID: 4980)
- N45w47HnqWFawEkl0bru5UlP.exe (PID: 2752)
- kpsVuIwTxthziIAnqHxbmA3S.exe (PID: 4928)
- xklWwL5ZQDKR8P3RorxcFDlW.exe (PID: 5592)
- jooyu.exe (PID: 4320)
- file4.exe (PID: 4328)
- jfiag3g_gg.exe (PID: 5164)
- md8_8eus.exe (PID: 6128)
- jingzhang.exe (PID: 5852)
- sCUIVIyz6dLBRM80cvSf4Ms9.exe (PID: 5844)
- ix78ESOrnjfX.exe (PID: 5932)
- ix78ESOrnjfX.exe (PID: 4264)
- ix78ESOrnjfX.exe (PID: 4056)
- ix78ESOrnjfX.exe (PID: 5832)
- UltraMediaBurner.exe (PID: 4108)
- ix78ESOrnjfX.exe (PID: 4104)
- jfiag3g_gg.exe (PID: 5368)
- ix78ESOrnjfX.exe (PID: 4304)
- ix78ESOrnjfX.exe (PID: 4888)
- ix78ESOrnjfX.exe (PID: 5524)
- ix78ESOrnjfX.exe (PID: 4448)
- ix78ESOrnjfX.exe (PID: 5724)
- ix78ESOrnjfX.exe (PID: 5636)
- ix78ESOrnjfX.exe (PID: 5876)
- ix78ESOrnjfX.exe (PID: 4580)
- ix78ESOrnjfX.exe (PID: 2532)
- ix78ESOrnjfX.exe (PID: 4612)
- ix78ESOrnjfX.exe (PID: 5448)
- ix78ESOrnjfX.exe (PID: 4976)
- ix78ESOrnjfX.exe (PID: 4416)
- 75597259823.exe (PID: 5120)
- ix78ESOrnjfX.exe (PID: 4620)
- ix78ESOrnjfX.exe (PID: 5840)
- ix78ESOrnjfX.exe (PID: 5880)
- ix78ESOrnjfX.exe (PID: 3340)
- ix78ESOrnjfX.exe (PID: 4892)
- ix78ESOrnjfX.exe (PID: 4340)
- ix78ESOrnjfX.exe (PID: 5624)
- ix78ESOrnjfX.exe (PID: 3840)
- ix78ESOrnjfX.exe (PID: 4152)
- ix78ESOrnjfX.exe (PID: 3128)
- ix78ESOrnjfX.exe (PID: 4204)
- ix78ESOrnjfX.exe (PID: 1612)
- ix78ESOrnjfX.exe (PID: 5332)
- ix78ESOrnjfX.exe (PID: 5736)
- ix78ESOrnjfX.exe (PID: 2088)
- ix78ESOrnjfX.exe (PID: 3256)
- ix78ESOrnjfX.exe (PID: 5576)
- ix78ESOrnjfX.exe (PID: 5900)
- ix78ESOrnjfX.exe (PID: 1672)
- ix78ESOrnjfX.exe (PID: 5172)
- ix78ESOrnjfX.exe (PID: 4884)
- ix78ESOrnjfX.exe (PID: 6120)
- ix78ESOrnjfX.exe (PID: 1464)
- ix78ESOrnjfX.exe (PID: 1196)
- ix78ESOrnjfX.exe (PID: 6036)
- ix78ESOrnjfX.exe (PID: 5700)
- ix78ESOrnjfX.exe (PID: 4216)
- ix78ESOrnjfX.exe (PID: 5176)
- ix78ESOrnjfX.exe (PID: 5980)
- ix78ESOrnjfX.exe (PID: 1544)
- ix78ESOrnjfX.exe (PID: 5088)
- ix78ESOrnjfX.exe (PID: 5004)
- ix78ESOrnjfX.exe (PID: 3368)
- ix78ESOrnjfX.exe (PID: 5424)
- ix78ESOrnjfX.exe (PID: 5296)
- ix78ESOrnjfX.exe (PID: 6000)
- ix78ESOrnjfX.exe (PID: 5016)
- ix78ESOrnjfX.exe (PID: 4752)
- ix78ESOrnjfX.exe (PID: 5536)
- ix78ESOrnjfX.exe (PID: 4088)
- ix78ESOrnjfX.exe (PID: 3624)
- ix78ESOrnjfX.exe (PID: 2120)
- ix78ESOrnjfX.exe (PID: 5656)
- ix78ESOrnjfX.exe (PID: 5768)
- ix78ESOrnjfX.exe (PID: 5408)
- ix78ESOrnjfX.exe (PID: 4836)
- ix78ESOrnjfX.exe (PID: 5188)
- ix78ESOrnjfX.exe (PID: 308)
- ix78ESOrnjfX.exe (PID: 3884)
- ix78ESOrnjfX.exe (PID: 4356)
- ix78ESOrnjfX.exe (PID: 5460)
- ix78ESOrnjfX.exe (PID: 5604)
- ix78ESOrnjfX.exe (PID: 3852)
- ix78ESOrnjfX.exe (PID: 4528)
- ix78ESOrnjfX.exe (PID: 4924)
- ix78ESOrnjfX.exe (PID: 5240)
- ix78ESOrnjfX.exe (PID: 3652)
- ix78ESOrnjfX.exe (PID: 2988)
- ix78ESOrnjfX.exe (PID: 892)
- ix78ESOrnjfX.exe (PID: 5428)
- ix78ESOrnjfX.exe (PID: 2472)
- ix78ESOrnjfX.exe (PID: 2956)
- ix78ESOrnjfX.exe (PID: 2980)
- ix78ESOrnjfX.exe (PID: 2800)
- ix78ESOrnjfX.exe (PID: 5920)
- ix78ESOrnjfX.exe (PID: 5924)
- ix78ESOrnjfX.exe (PID: 2636)
- ix78ESOrnjfX.exe (PID: 2696)
- ix78ESOrnjfX.exe (PID: 6044)
- ix78ESOrnjfX.exe (PID: 1496)
- ix78ESOrnjfX.exe (PID: 2136)
- ix78ESOrnjfX.exe (PID: 2964)
- ix78ESOrnjfX.exe (PID: 5516)
- ix78ESOrnjfX.exe (PID: 980)
- ix78ESOrnjfX.exe (PID: 5104)
- ix78ESOrnjfX.exe (PID: 4740)
- ix78ESOrnjfX.exe (PID: 5216)
- ix78ESOrnjfX.exe (PID: 2640)
- ix78ESOrnjfX.exe (PID: 5776)
- ix78ESOrnjfX.exe (PID: 1920)
- ix78ESOrnjfX.exe (PID: 3948)
- ix78ESOrnjfX.exe (PID: 2196)
- ix78ESOrnjfX.exe (PID: 3748)
- ix78ESOrnjfX.exe (PID: 5124)
- ix78ESOrnjfX.exe (PID: 3720)
- ix78ESOrnjfX.exe (PID: 3976)
- ix78ESOrnjfX.exe (PID: 3816)
- ix78ESOrnjfX.exe (PID: 4352)
- ix78ESOrnjfX.exe (PID: 2892)
- ix78ESOrnjfX.exe (PID: 3960)
- ix78ESOrnjfX.exe (PID: 2496)
- ix78ESOrnjfX.exe (PID: 5080)
- ix78ESOrnjfX.exe (PID: 4044)
- ix78ESOrnjfX.exe (PID: 904)
- ix78ESOrnjfX.exe (PID: 2424)
- ix78ESOrnjfX.exe (PID: 3188)
- ix78ESOrnjfX.exe (PID: 2916)
- ix78ESOrnjfX.exe (PID: 5232)
- ix78ESOrnjfX.exe (PID: 5040)
- ix78ESOrnjfX.exe (PID: 2208)
- ix78ESOrnjfX.exe (PID: 2296)
- ix78ESOrnjfX.exe (PID: 2976)
- ix78ESOrnjfX.exe (PID: 2912)
- ix78ESOrnjfX.exe (PID: 584)
- ix78ESOrnjfX.exe (PID: 3392)
- ix78ESOrnjfX.exe (PID: 4420)
- ix78ESOrnjfX.exe (PID: 4156)
- ix78ESOrnjfX.exe (PID: 4028)
- ix78ESOrnjfX.exe (PID: 2864)
- ix78ESOrnjfX.exe (PID: 3888)
- ix78ESOrnjfX.exe (PID: 4732)
- 39945411238.exe (PID: 1756)
- ix78ESOrnjfX.exe (PID: 4568)
- ix78ESOrnjfX.exe (PID: 4964)
- ix78ESOrnjfX.exe (PID: 5220)
- ix78ESOrnjfX.exe (PID: 2092)
- ix78ESOrnjfX.exe (PID: 3556)
- ix78ESOrnjfX.exe (PID: 2280)
- ix78ESOrnjfX.exe (PID: 3280)
- ix78ESOrnjfX.exe (PID: 4704)
- ix78ESOrnjfX.exe (PID: 4324)
- ix78ESOrnjfX.exe (PID: 3848)
- ix78ESOrnjfX.exe (PID: 5036)
- ix78ESOrnjfX.exe (PID: 3052)
- ix78ESOrnjfX.exe (PID: 4116)
- ix78ESOrnjfX.exe (PID: 5452)
- ix78ESOrnjfX.exe (PID: 1008)
- ix78ESOrnjfX.exe (PID: 1956)
- ix78ESOrnjfX.exe (PID: 4672)
- ix78ESOrnjfX.exe (PID: 3148)
- ix78ESOrnjfX.exe (PID: 2436)
- ix78ESOrnjfX.exe (PID: 3784)
- ix78ESOrnjfX.exe (PID: 2456)
- ix78ESOrnjfX.exe (PID: 5092)
- ix78ESOrnjfX.exe (PID: 5288)
- ix78ESOrnjfX.exe (PID: 5284)
- ix78ESOrnjfX.exe (PID: 1320)
- ix78ESOrnjfX.exe (PID: 5784)
- ix78ESOrnjfX.exe (PID: 4720)
- ix78ESOrnjfX.exe (PID: 4960)
- ix78ESOrnjfX.exe (PID: 4532)
- ix78ESOrnjfX.exe (PID: 2804)
- ix78ESOrnjfX.exe (PID: 6572)
- ix78ESOrnjfX.exe (PID: 7404)
- ix78ESOrnjfX.exe (PID: 5276)
- ix78ESOrnjfX.exe (PID: 2216)
- ix78ESOrnjfX.exe (PID: 7064)
- jfiag3g_gg.exe (PID: 6856)
- ix78ESOrnjfX.exe (PID: 7044)
- ix78ESOrnjfX.exe (PID: 6380)
- ix78ESOrnjfX.exe (PID: 7888)
- ix78ESOrnjfX.exe (PID: 5336)
- ix78ESOrnjfX.exe (PID: 7316)
- ix78ESOrnjfX.exe (PID: 7616)
- ix78ESOrnjfX.exe (PID: 7192)
- jfiag3g_gg.exe (PID: 7280)
- ix78ESOrnjfX.exe (PID: 7356)
- ix78ESOrnjfX.exe (PID: 7448)
- ix78ESOrnjfX.exe (PID: 6600)
- ix78ESOrnjfX.exe (PID: 7628)
- ix78ESOrnjfX.exe (PID: 7136)
- ix78ESOrnjfX.exe (PID: 6768)
- ix78ESOrnjfX.exe (PID: 6676)
- ix78ESOrnjfX.exe (PID: 8148)
- ix78ESOrnjfX.exe (PID: 7384)
- ix78ESOrnjfX.exe (PID: 6892)
- ix78ESOrnjfX.exe (PID: 7228)
- ix78ESOrnjfX.exe (PID: 7284)
- ix78ESOrnjfX.exe (PID: 8264)
- ix78ESOrnjfX.exe (PID: 6692)
- ix78ESOrnjfX.exe (PID: 9832)
- ix78ESOrnjfX.exe (PID: 8068)
- ix78ESOrnjfX.exe (PID: 10100)
- ix78ESOrnjfX.exe (PID: 9236)
- ix78ESOrnjfX.exe (PID: 6552)
- ix78ESOrnjfX.exe (PID: 8464)
- ix78ESOrnjfX.exe (PID: 9052)
- ix78ESOrnjfX.exe (PID: 5492)
- ix78ESOrnjfX.exe (PID: 9760)
- ix78ESOrnjfX.exe (PID: 6352)
- ix78ESOrnjfX.exe (PID: 9536)
- ix78ESOrnjfX.exe (PID: 9892)
- ix78ESOrnjfX.exe (PID: 11272)
- ix78ESOrnjfX.exe (PID: 11720)
- ix78ESOrnjfX.exe (PID: 8244)
- 96356344407.exe (PID: 8488)
- ix78ESOrnjfX.exe (PID: 3488)
- ix78ESOrnjfX.exe (PID: 6376)
- ix78ESOrnjfX.exe (PID: 12104)
- ix78ESOrnjfX.exe (PID: 7808)
- ix78ESOrnjfX.exe (PID: 6664)
- ix78ESOrnjfX.exe (PID: 8956)
- ix78ESOrnjfX.exe (PID: 6936)
- ix78ESOrnjfX.exe (PID: 10268)
- ix78ESOrnjfX.exe (PID: 8900)
- ix78ESOrnjfX.exe (PID: 8444)
- ix78ESOrnjfX.exe (PID: 8552)
- ix78ESOrnjfX.exe (PID: 6660)
- ix78ESOrnjfX.exe (PID: 7088)
- ix78ESOrnjfX.exe (PID: 11744)
- ix78ESOrnjfX.exe (PID: 11316)
- ix78ESOrnjfX.exe (PID: 10428)
- ix78ESOrnjfX.exe (PID: 11236)
- ix78ESOrnjfX.exe (PID: 11428)
- ix78ESOrnjfX.exe (PID: 8124)
- ix78ESOrnjfX.exe (PID: 11200)
- ns99D6.tmp (PID: 7144)
- ix78ESOrnjfX.exe (PID: 4796)
- ix78ESOrnjfX.exe (PID: 8816)
- ix78ESOrnjfX.exe (PID: 7256)
- ix78ESOrnjfX.exe (PID: 11496)
- ix78ESOrnjfX.exe (PID: 3820)
- ix78ESOrnjfX.exe (PID: 10096)
- ix78ESOrnjfX.exe (PID: 8612)
- ix78ESOrnjfX.exe (PID: 7496)
- ix78ESOrnjfX.exe (PID: 9732)
- ix78ESOrnjfX.exe (PID: 9528)
- ix78ESOrnjfX.exe (PID: 6264)
- ix78ESOrnjfX.exe (PID: 8940)
- ix78ESOrnjfX.exe (PID: 6756)
- ix78ESOrnjfX.exe (PID: 9672)
- ix78ESOrnjfX.exe (PID: 10648)
- ix78ESOrnjfX.exe (PID: 10124)
- ix78ESOrnjfX.exe (PID: 8880)
- ix78ESOrnjfX.exe (PID: 11156)
- ix78ESOrnjfX.exe (PID: 7176)
- ix78ESOrnjfX.exe (PID: 8168)
- ix78ESOrnjfX.exe (PID: 8868)
- ix78ESOrnjfX.exe (PID: 9560)
- ix78ESOrnjfX.exe (PID: 6904)
- ix78ESOrnjfX.exe (PID: 10476)
- ix78ESOrnjfX.exe (PID: 5568)
- ix78ESOrnjfX.exe (PID: 11740)
- ix78ESOrnjfX.exe (PID: 8424)
- ix78ESOrnjfX.exe (PID: 6944)
- ix78ESOrnjfX.exe (PID: 11540)
- ix78ESOrnjfX.exe (PID: 9508)
- ix78ESOrnjfX.exe (PID: 8628)
- ix78ESOrnjfX.exe (PID: 10140)
- ix78ESOrnjfX.exe (PID: 7992)
- ix78ESOrnjfX.exe (PID: 2736)
- ix78ESOrnjfX.exe (PID: 11176)
- ix78ESOrnjfX.exe (PID: 9748)
- ix78ESOrnjfX.exe (PID: 9072)
- ix78ESOrnjfX.exe (PID: 8784)
- ix78ESOrnjfX.exe (PID: 9308)
- ix78ESOrnjfX.exe (PID: 7544)
- ix78ESOrnjfX.exe (PID: 10036)
- ix78ESOrnjfX.exe (PID: 10640)
- ix78ESOrnjfX.exe (PID: 7824)
- ix78ESOrnjfX.exe (PID: 12072)
- ix78ESOrnjfX.exe (PID: 10252)
- ix78ESOrnjfX.exe (PID: 8764)
- ix78ESOrnjfX.exe (PID: 8044)
- ix78ESOrnjfX.exe (PID: 6928)
- ix78ESOrnjfX.exe (PID: 3972)
- ix78ESOrnjfX.exe (PID: 9140)
- ix78ESOrnjfX.exe (PID: 11648)
- ix78ESOrnjfX.exe (PID: 12264)
- ix78ESOrnjfX.exe (PID: 11368)
- ix78ESOrnjfX.exe (PID: 11876)
- ix78ESOrnjfX.exe (PID: 11536)
- ix78ESOrnjfX.exe (PID: 9736)
- ix78ESOrnjfX.exe (PID: 6564)
- ix78ESOrnjfX.exe (PID: 10044)
- ix78ESOrnjfX.exe (PID: 7360)
- ix78ESOrnjfX.exe (PID: 8076)
- ix78ESOrnjfX.exe (PID: 7928)
- ix78ESOrnjfX.exe (PID: 9840)
- ix78ESOrnjfX.exe (PID: 11816)
- ix78ESOrnjfX.exe (PID: 11308)
- ix78ESOrnjfX.exe (PID: 8748)
- ix78ESOrnjfX.exe (PID: 6784)
- ix78ESOrnjfX.exe (PID: 5372)
- ix78ESOrnjfX.exe (PID: 9620)
- ix78ESOrnjfX.exe (PID: 9500)
- ix78ESOrnjfX.exe (PID: 6804)
- ix78ESOrnjfX.exe (PID: 9336)
- ix78ESOrnjfX.exe (PID: 10756)
- ix78ESOrnjfX.exe (PID: 2644)
- ix78ESOrnjfX.exe (PID: 10608)
- ix78ESOrnjfX.exe (PID: 8140)
- ix78ESOrnjfX.exe (PID: 9844)
- ix78ESOrnjfX.exe (PID: 7392)
- ix78ESOrnjfX.exe (PID: 8996)
- ix78ESOrnjfX.exe (PID: 8408)
- ix78ESOrnjfX.exe (PID: 6732)
- ix78ESOrnjfX.exe (PID: 6356)
- ix78ESOrnjfX.exe (PID: 7516)
- ix78ESOrnjfX.exe (PID: 9564)
- ix78ESOrnjfX.exe (PID: 5836)
- ix78ESOrnjfX.exe (PID: 11780)
- ix78ESOrnjfX.exe (PID: 11464)
- ix78ESOrnjfX.exe (PID: 12012)
- ix78ESOrnjfX.exe (PID: 7660)
- ix78ESOrnjfX.exe (PID: 10440)
- ix78ESOrnjfX.exe (PID: 6444)
- ix78ESOrnjfX.exe (PID: 7056)
- ix78ESOrnjfX.exe (PID: 8476)
- ix78ESOrnjfX.exe (PID: 11100)
- ix78ESOrnjfX.exe (PID: 10360)
- ix78ESOrnjfX.exe (PID: 11692)
- ix78ESOrnjfX.exe (PID: 7456)
- ix78ESOrnjfX.exe (PID: 11784)
- ix78ESOrnjfX.exe (PID: 2628)
- ix78ESOrnjfX.exe (PID: 9396)
- ix78ESOrnjfX.exe (PID: 8468)
- ix78ESOrnjfX.exe (PID: 7676)
- ix78ESOrnjfX.exe (PID: 8704)
- ix78ESOrnjfX.exe (PID: 12032)
- ix78ESOrnjfX.exe (PID: 9860)
- ix78ESOrnjfX.exe (PID: 8976)
- ix78ESOrnjfX.exe (PID: 9708)
- ix78ESOrnjfX.exe (PID: 8888)
- ix78ESOrnjfX.exe (PID: 11160)
- ix78ESOrnjfX.exe (PID: 9332)
- ix78ESOrnjfX.exe (PID: 8540)
- ix78ESOrnjfX.exe (PID: 8760)
- ix78ESOrnjfX.exe (PID: 9020)
- ix78ESOrnjfX.exe (PID: 10500)
- ix78ESOrnjfX.exe (PID: 11656)
- ix78ESOrnjfX.exe (PID: 6640)
- ix78ESOrnjfX.exe (PID: 4784)
- ix78ESOrnjfX.exe (PID: 12156)
- ix78ESOrnjfX.exe (PID: 6628)
- ix78ESOrnjfX.exe (PID: 8520)
- ix78ESOrnjfX.exe (PID: 9640)
- ix78ESOrnjfX.exe (PID: 12128)
- ix78ESOrnjfX.exe (PID: 600)
- ix78ESOrnjfX.exe (PID: 10612)
- ix78ESOrnjfX.exe (PID: 10480)
- ix78ESOrnjfX.exe (PID: 2100)
- ix78ESOrnjfX.exe (PID: 5752)
- ix78ESOrnjfX.exe (PID: 10704)
- ix78ESOrnjfX.exe (PID: 9480)
- ix78ESOrnjfX.exe (PID: 10932)
- ix78ESOrnjfX.exe (PID: 11336)
- ix78ESOrnjfX.exe (PID: 1700)
- ix78ESOrnjfX.exe (PID: 10356)
- ix78ESOrnjfX.exe (PID: 9976)
- ix78ESOrnjfX.exe (PID: 12000)
- ix78ESOrnjfX.exe (PID: 8536)
- ix78ESOrnjfX.exe (PID: 10904)
- ix78ESOrnjfX.exe (PID: 10676)
- ix78ESOrnjfX.exe (PID: 9028)
- ix78ESOrnjfX.exe (PID: 6480)
- ix78ESOrnjfX.exe (PID: 11696)
- ix78ESOrnjfX.exe (PID: 4584)
- ix78ESOrnjfX.exe (PID: 4016)
- ix78ESOrnjfX.exe (PID: 10832)
- ix78ESOrnjfX.exe (PID: 8676)
- ix78ESOrnjfX.exe (PID: 7332)
- ix78ESOrnjfX.exe (PID: 10220)
- ix78ESOrnjfX.exe (PID: 3628)
- ix78ESOrnjfX.exe (PID: 10232)
- ix78ESOrnjfX.exe (PID: 11804)
- ix78ESOrnjfX.exe (PID: 11080)
- ix78ESOrnjfX.exe (PID: 10068)
- ix78ESOrnjfX.exe (PID: 6780)
- ix78ESOrnjfX.exe (PID: 9492)
- ix78ESOrnjfX.exe (PID: 7160)
- ix78ESOrnjfX.exe (PID: 11172)
- ix78ESOrnjfX.exe (PID: 5940)
- ix78ESOrnjfX.exe (PID: 10508)
- ix78ESOrnjfX.exe (PID: 11676)
- ix78ESOrnjfX.exe (PID: 1784)
- ix78ESOrnjfX.exe (PID: 7536)
- ix78ESOrnjfX.exe (PID: 11556)
- ix78ESOrnjfX.exe (PID: 10772)
- ix78ESOrnjfX.exe (PID: 8220)
- ix78ESOrnjfX.exe (PID: 11584)
- ix78ESOrnjfX.exe (PID: 6736)
- ix78ESOrnjfX.exe (PID: 9524)
- ix78ESOrnjfX.exe (PID: 8352)
- ix78ESOrnjfX.exe (PID: 10000)
- ix78ESOrnjfX.exe (PID: 6252)
- ix78ESOrnjfX.exe (PID: 11920)
- ix78ESOrnjfX.exe (PID: 11248)
- ix78ESOrnjfX.exe (PID: 6208)
- ix78ESOrnjfX.exe (PID: 12232)
- ix78ESOrnjfX.exe (PID: 11216)
- ix78ESOrnjfX.exe (PID: 8556)
- ix78ESOrnjfX.exe (PID: 9692)
- ix78ESOrnjfX.exe (PID: 10800)
- ix78ESOrnjfX.exe (PID: 6188)
- ix78ESOrnjfX.exe (PID: 1724)
- ix78ESOrnjfX.exe (PID: 8364)
- ix78ESOrnjfX.exe (PID: 10684)
- ix78ESOrnjfX.exe (PID: 2548)
- ix78ESOrnjfX.exe (PID: 11192)
- ix78ESOrnjfX.exe (PID: 10288)
- ix78ESOrnjfX.exe (PID: 11152)
- ix78ESOrnjfX.exe (PID: 9888)
- ix78ESOrnjfX.exe (PID: 11664)
- ix78ESOrnjfX.exe (PID: 7672)
- ix78ESOrnjfX.exe (PID: 7328)
- ix78ESOrnjfX.exe (PID: 12132)
- ix78ESOrnjfX.exe (PID: 10416)
- ix78ESOrnjfX.exe (PID: 11072)
- ix78ESOrnjfX.exe (PID: 10248)
- ix78ESOrnjfX.exe (PID: 8012)
- ix78ESOrnjfX.exe (PID: 5608)
- ix78ESOrnjfX.exe (PID: 8052)
- ix78ESOrnjfX.exe (PID: 10200)
- ix78ESOrnjfX.exe (PID: 12096)
- ix78ESOrnjfX.exe (PID: 8980)
- ix78ESOrnjfX.exe (PID: 9856)
- ix78ESOrnjfX.exe (PID: 8348)
- ix78ESOrnjfX.exe (PID: 6396)
- ix78ESOrnjfX.exe (PID: 9256)
- ix78ESOrnjfX.exe (PID: 10120)
- ix78ESOrnjfX.exe (PID: 4184)
- ix78ESOrnjfX.exe (PID: 12240)
- ix78ESOrnjfX.exe (PID: 8780)
- ix78ESOrnjfX.exe (PID: 12028)
- ix78ESOrnjfX.exe (PID: 10692)
- ix78ESOrnjfX.exe (PID: 10028)
- ix78ESOrnjfX.exe (PID: 9936)
- ix78ESOrnjfX.exe (PID: 7172)
- ix78ESOrnjfX.exe (PID: 9384)
- ix78ESOrnjfX.exe (PID: 8944)
- ix78ESOrnjfX.exe (PID: 9904)
- ix78ESOrnjfX.exe (PID: 9980)
- ix78ESOrnjfX.exe (PID: 11408)
- ix78ESOrnjfX.exe (PID: 6472)
- ix78ESOrnjfX.exe (PID: 9864)
- ix78ESOrnjfX.exe (PID: 9364)
- ix78ESOrnjfX.exe (PID: 10112)
- ix78ESOrnjfX.exe (PID: 12176)
- ix78ESOrnjfX.exe (PID: 10840)
- ix78ESOrnjfX.exe (PID: 5348)
- ix78ESOrnjfX.exe (PID: 5716)
- ix78ESOrnjfX.exe (PID: 7340)
- ix78ESOrnjfX.exe (PID: 6876)
- ix78ESOrnjfX.exe (PID: 10404)
- ix78ESOrnjfX.exe (PID: 6800)
- ix78ESOrnjfX.exe (PID: 10340)
- ix78ESOrnjfX.exe (PID: 12060)
- ix78ESOrnjfX.exe (PID: 8820)
- ix78ESOrnjfX.exe (PID: 9168)
- ix78ESOrnjfX.exe (PID: 10216)
- ix78ESOrnjfX.exe (PID: 8640)
- ix78ESOrnjfX.exe (PID: 7336)
- ix78ESOrnjfX.exe (PID: 12168)
- ix78ESOrnjfX.exe (PID: 4868)
- ix78ESOrnjfX.exe (PID: 8160)
- ix78ESOrnjfX.exe (PID: 8272)
- ix78ESOrnjfX.exe (PID: 6548)
- ix78ESOrnjfX.exe (PID: 8984)
- ix78ESOrnjfX.exe (PID: 6788)
- ix78ESOrnjfX.exe (PID: 11112)
- ix78ESOrnjfX.exe (PID: 11600)
- ix78ESOrnjfX.exe (PID: 8572)
- ix78ESOrnjfX.exe (PID: 8992)
- ix78ESOrnjfX.exe (PID: 11560)
- ix78ESOrnjfX.exe (PID: 9968)
- ix78ESOrnjfX.exe (PID: 3432)
- ix78ESOrnjfX.exe (PID: 7584)
- ix78ESOrnjfX.exe (PID: 9768)
- ix78ESOrnjfX.exe (PID: 3588)
- ix78ESOrnjfX.exe (PID: 10844)
- ix78ESOrnjfX.exe (PID: 6172)
- ix78ESOrnjfX.exe (PID: 9124)
- ix78ESOrnjfX.exe (PID: 7684)
- ix78ESOrnjfX.exe (PID: 6812)
- ix78ESOrnjfX.exe (PID: 10812)
- ix78ESOrnjfX.exe (PID: 9440)
- ix78ESOrnjfX.exe (PID: 6908)
- ix78ESOrnjfX.exe (PID: 10296)
- ix78ESOrnjfX.exe (PID: 9780)
- ix78ESOrnjfX.exe (PID: 6964)
- ix78ESOrnjfX.exe (PID: 8212)
- ix78ESOrnjfX.exe (PID: 8692)
- ix78ESOrnjfX.exe (PID: 9740)
- ix78ESOrnjfX.exe (PID: 6776)
- ix78ESOrnjfX.exe (PID: 10304)
- ix78ESOrnjfX.exe (PID: 6952)
- ix78ESOrnjfX.exe (PID: 8708)
- ix78ESOrnjfX.exe (PID: 7076)
- ix78ESOrnjfX.exe (PID: 9180)
- ix78ESOrnjfX.exe (PID: 2952)
- ix78ESOrnjfX.exe (PID: 11276)
- ix78ESOrnjfX.exe (PID: 8884)
- ix78ESOrnjfX.exe (PID: 8668)
- ix78ESOrnjfX.exe (PID: 4524)
- ix78ESOrnjfX.exe (PID: 10780)
- ix78ESOrnjfX.exe (PID: 10444)
- ix78ESOrnjfX.exe (PID: 5812)
- ix78ESOrnjfX.exe (PID: 11620)
- ix78ESOrnjfX.exe (PID: 8436)
- ix78ESOrnjfX.exe (PID: 9928)
- ix78ESOrnjfX.exe (PID: 6608)
- ix78ESOrnjfX.exe (PID: 6484)
- ix78ESOrnjfX.exe (PID: 11136)
- ix78ESOrnjfX.exe (PID: 10568)
- ix78ESOrnjfX.exe (PID: 6152)
- ix78ESOrnjfX.exe (PID: 10336)
- ix78ESOrnjfX.exe (PID: 9220)
- ix78ESOrnjfX.exe (PID: 8656)
- ix78ESOrnjfX.exe (PID: 11508)
- ix78ESOrnjfX.exe (PID: 8580)
- ix78ESOrnjfX.exe (PID: 6424)
- ix78ESOrnjfX.exe (PID: 8836)
- ix78ESOrnjfX.exe (PID: 7452)
- ix78ESOrnjfX.exe (PID: 11768)
- ix78ESOrnjfX.exe (PID: 7700)
- ix78ESOrnjfX.exe (PID: 2760)
- ix78ESOrnjfX.exe (PID: 9812)
- ix78ESOrnjfX.exe (PID: 6648)
- ix78ESOrnjfX.exe (PID: 10004)
- ix78ESOrnjfX.exe (PID: 10740)
- ix78ESOrnjfX.exe (PID: 12088)
- ix78ESOrnjfX.exe (PID: 11400)
- ix78ESOrnjfX.exe (PID: 10876)
- ix78ESOrnjfX.exe (PID: 8832)
- ix78ESOrnjfX.exe (PID: 12144)
- ix78ESOrnjfX.exe (PID: 9248)
- ix78ESOrnjfX.exe (PID: 7412)
- ix78ESOrnjfX.exe (PID: 10160)
- ix78ESOrnjfX.exe (PID: 6536)
- ix78ESOrnjfX.exe (PID: 11040)
- ix78ESOrnjfX.exe (PID: 7548)
- ix78ESOrnjfX.exe (PID: 4560)
- ix78ESOrnjfX.exe (PID: 10816)
- ix78ESOrnjfX.exe (PID: 12092)
- ix78ESOrnjfX.exe (PID: 11204)
- ebook.exe (PID: 11388)
- ix78ESOrnjfX.exe (PID: 3768)
- ix78ESOrnjfX.exe (PID: 8008)
- ix78ESOrnjfX.exe (PID: 10376)
- ix78ESOrnjfX.exe (PID: 11000)
- ix78ESOrnjfX.exe (PID: 7252)
- ix78ESOrnjfX.exe (PID: 3700)
- ix78ESOrnjfX.exe (PID: 9228)
- ix78ESOrnjfX.exe (PID: 8040)
- ix78ESOrnjfX.exe (PID: 7260)
- ix78ESOrnjfX.exe (PID: 11412)
- ix78ESOrnjfX.exe (PID: 11088)
- ix78ESOrnjfX.exe (PID: 9992)
- ix78ESOrnjfX.exe (PID: 2128)
- ix78ESOrnjfX.exe (PID: 12224)
- ix78ESOrnjfX.exe (PID: 7500)
- ix78ESOrnjfX.exe (PID: 6456)
- ix78ESOrnjfX.exe (PID: 10696)
- ix78ESOrnjfX.exe (PID: 6896)
- ix78ESOrnjfX.exe (PID: 11064)
- ix78ESOrnjfX.exe (PID: 10776)
- ix78ESOrnjfX.exe (PID: 6232)
- ix78ESOrnjfX.exe (PID: 11364)
- ix78ESOrnjfX.exe (PID: 11660)
- ix78ESOrnjfX.exe (PID: 11608)
- ix78ESOrnjfX.exe (PID: 7716)
- ix78ESOrnjfX.exe (PID: 7560)
- ix78ESOrnjfX.exe (PID: 11552)
- ix78ESOrnjfX.exe (PID: 7008)
- ix78ESOrnjfX.exe (PID: 7796)
- ix78ESOrnjfX.exe (PID: 5620)
- ix78ESOrnjfX.exe (PID: 7748)
- ix78ESOrnjfX.exe (PID: 4460)
- ix78ESOrnjfX.exe (PID: 12152)
- ix78ESOrnjfX.exe (PID: 4244)
- ix78ESOrnjfX.exe (PID: 10064)
- ix78ESOrnjfX.exe (PID: 8368)
- ix78ESOrnjfX.exe (PID: 5892)
- ix78ESOrnjfX.exe (PID: 7208)
- ix78ESOrnjfX.exe (PID: 10788)
- ix78ESOrnjfX.exe (PID: 9144)
- ix78ESOrnjfX.exe (PID: 5704)
- ix78ESOrnjfX.exe (PID: 10956)
- ix78ESOrnjfX.exe (PID: 9376)
- ix78ESOrnjfX.exe (PID: 8208)
- ix78ESOrnjfX.exe (PID: 10400)
- ix78ESOrnjfX.exe (PID: 10256)
- ix78ESOrnjfX.exe (PID: 5136)
- ix78ESOrnjfX.exe (PID: 11944)
- ix78ESOrnjfX.exe (PID: 10168)
- ix78ESOrnjfX.exe (PID: 3952)
- ix78ESOrnjfX.exe (PID: 7224)
- ix78ESOrnjfX.exe (PID: 12068)
- ix78ESOrnjfX.exe (PID: 560)
- ix78ESOrnjfX.exe (PID: 8720)
- ix78ESOrnjfX.exe (PID: 3156)
- ix78ESOrnjfX.exe (PID: 10668)
- ix78ESOrnjfX.exe (PID: 10092)
- ix78ESOrnjfX.exe (PID: 7164)
- ix78ESOrnjfX.exe (PID: 3060)
- ix78ESOrnjfX.exe (PID: 9152)
- ix78ESOrnjfX.exe (PID: 4516)
- ix78ESOrnjfX.exe (PID: 8988)
- ix78ESOrnjfX.exe (PID: 5052)
- ix78ESOrnjfX.exe (PID: 8388)
- ix78ESOrnjfX.exe (PID: 2408)
- ix78ESOrnjfX.exe (PID: 3192)
- ix78ESOrnjfX.exe (PID: 4968)
- ix78ESOrnjfX.exe (PID: 2704)
- ix78ESOrnjfX.exe (PID: 11028)
- ix78ESOrnjfX.exe (PID: 4812)
- ix78ESOrnjfX.exe (PID: 7288)
- ix78ESOrnjfX.exe (PID: 4496)
- ix78ESOrnjfX.exe (PID: 11188)
- ix78ESOrnjfX.exe (PID: 3648)
- ix78ESOrnjfX.exe (PID: 5564)
- ix78ESOrnjfX.exe (PID: 7820)
- ix78ESOrnjfX.exe (PID: 6864)
- ix78ESOrnjfX.exe (PID: 11704)
- ix78ESOrnjfX.exe (PID: 6048)
- ix78ESOrnjfX.exe (PID: 1416)
- ix78ESOrnjfX.exe (PID: 2520)
- ix78ESOrnjfX.exe (PID: 6984)
- ix78ESOrnjfX.exe (PID: 11580)
- ix78ESOrnjfX.exe (PID: 7268)
- ix78ESOrnjfX.exe (PID: 8796)
- ix78ESOrnjfX.exe (PID: 7028)
- ix78ESOrnjfX.exe (PID: 7876)
- ix78ESOrnjfX.exe (PID: 7912)
- ix78ESOrnjfX.exe (PID: 7740)
- ix78ESOrnjfX.exe (PID: 4772)
- ix78ESOrnjfX.exe (PID: 10804)
- ix78ESOrnjfX.exe (PID: 7476)
- ix78ESOrnjfX.exe (PID: 11864)
- ix78ESOrnjfX.exe (PID: 2984)
- ix78ESOrnjfX.exe (PID: 12216)
- ix78ESOrnjfX.exe (PID: 11052)
- ix78ESOrnjfX.exe (PID: 3656)
- ix78ESOrnjfX.exe (PID: 5456)
- ix78ESOrnjfX.exe (PID: 12244)
- ix78ESOrnjfX.exe (PID: 11228)
- ix78ESOrnjfX.exe (PID: 7484)
- ix78ESOrnjfX.exe (PID: 10264)
- ix78ESOrnjfX.exe (PID: 5972)
- ix78ESOrnjfX.exe (PID: 8752)
- ix78ESOrnjfX.exe (PID: 5008)
- ix78ESOrnjfX.exe (PID: 5904)
- ix78ESOrnjfX.exe (PID: 11928)
- ix78ESOrnjfX.exe (PID: 3332)
- ix78ESOrnjfX.exe (PID: 5688)
- ix78ESOrnjfX.exe (PID: 11180)
- ix78ESOrnjfX.exe (PID: 3420)
- ix78ESOrnjfX.exe (PID: 12260)
- ix78ESOrnjfX.exe (PID: 8848)
- ix78ESOrnjfX.exe (PID: 1232)
- ix78ESOrnjfX.exe (PID: 12184)
- ix78ESOrnjfX.exe (PID: 8036)
- ix78ESOrnjfX.exe (PID: 7200)
- ix78ESOrnjfX.exe (PID: 4300)
- ix78ESOrnjfX.exe (PID: 7508)
- ix78ESOrnjfX.exe (PID: 8496)
- ix78ESOrnjfX.exe (PID: 2512)
- ix78ESOrnjfX.exe (PID: 5820)
- ix78ESOrnjfX.exe (PID: 3788)
- ix78ESOrnjfX.exe (PID: 2784)
- ix78ESOrnjfX.exe (PID: 4736)
- ix78ESOrnjfX.exe (PID: 6940)
- ix78ESOrnjfX.exe (PID: 9944)
- ix78ESOrnjfX.exe (PID: 8524)
- ix78ESOrnjfX.exe (PID: 6332)
- ix78ESOrnjfX.exe (PID: 5068)
- ix78ESOrnjfX.exe (PID: 9680)
- ix78ESOrnjfX.exe (PID: 11764)
- ix78ESOrnjfX.exe (PID: 8600)
- ix78ESOrnjfX.exe (PID: 7772)
- ix78ESOrnjfX.exe (PID: 556)
- ix78ESOrnjfX.exe (PID: 10820)
- ix78ESOrnjfX.exe (PID: 3016)
- ix78ESOrnjfX.exe (PID: 7916)
- ix78ESOrnjfX.exe (PID: 8584)
- ix78ESOrnjfX.exe (PID: 10908)
- ix78ESOrnjfX.exe (PID: 7640)
- ix78ESOrnjfX.exe (PID: 1284)
- ix78ESOrnjfX.exe (PID: 11196)
- ix78ESOrnjfX.exe (PID: 11440)
- ix78ESOrnjfX.exe (PID: 6968)
- ix78ESOrnjfX.exe (PID: 6268)
- ix78ESOrnjfX.exe (PID: 8632)
- ix78ESOrnjfX.exe (PID: 2756)
- ix78ESOrnjfX.exe (PID: 5360)
- ix78ESOrnjfX.exe (PID: 10024)
- ix78ESOrnjfX.exe (PID: 4112)
- ix78ESOrnjfX.exe (PID: 12040)
- ix78ESOrnjfX.exe (PID: 5664)
- ix78ESOrnjfX.exe (PID: 8804)
- 0001.exe (PID: 9408)
- ix78ESOrnjfX.exe (PID: 10460)
- ix78ESOrnjfX.exe (PID: 11892)
- ix78ESOrnjfX.exe (PID: 10192)
- ix78ESOrnjfX.exe (PID: 10924)
- ix78ESOrnjfX.exe (PID: 2284)
- ix78ESOrnjfX.exe (PID: 12084)
- ix78ESOrnjfX.exe (PID: 3572)
- ix78ESOrnjfX.exe (PID: 9356)
- ix78ESOrnjfX.exe (PID: 6200)
- ix78ESOrnjfX.exe (PID: 5644)
- ix78ESOrnjfX.exe (PID: 11320)
- ix78ESOrnjfX.exe (PID: 5440)
- ix78ESOrnjfX.exe (PID: 8416)
- ix78ESOrnjfX.exe (PID: 10448)
- ix78ESOrnjfX.exe (PID: 9632)
- ix78ESOrnjfX.exe (PID: 11324)
- ix78ESOrnjfX.exe (PID: 8056)
- ix78ESOrnjfX.exe (PID: 9496)
- ix78ESOrnjfX.exe (PID: 9516)
- ix78ESOrnjfX.exe (PID: 4604)
- ix78ESOrnjfX.exe (PID: 6496)
- ix78ESOrnjfX.exe (PID: 11036)
- ix78ESOrnjfX.exe (PID: 9436)
- ix78ESOrnjfX.exe (PID: 5420)
- ix78ESOrnjfX.exe (PID: 11116)
- ix78ESOrnjfX.exe (PID: 6744)
- ix78ESOrnjfX.exe (PID: 7140)
- ix78ESOrnjfX.exe (PID: 7724)
- ix78ESOrnjfX.exe (PID: 11952)
- ix78ESOrnjfX.exe (PID: 1000)
- ix78ESOrnjfX.exe (PID: 7432)
- ix78ESOrnjfX.exe (PID: 2460)
- ix78ESOrnjfX.exe (PID: 8172)
- ix78ESOrnjfX.exe (PID: 8856)
- 001.exe (PID: 4484)
- ix78ESOrnjfX.exe (PID: 5856)
- ix78ESOrnjfX.exe (PID: 3440)
- ix78ESOrnjfX.exe (PID: 6436)
- ix78ESOrnjfX.exe (PID: 8440)
- ix78ESOrnjfX.exe (PID: 9476)
- ix78ESOrnjfX.exe (PID: 10852)
- ix78ESOrnjfX.exe (PID: 10872)
- ix78ESOrnjfX.exe (PID: 6320)
- ns8E69.tmp (PID: 11860)
- ix78ESOrnjfX.exe (PID: 12016)
- ix78ESOrnjfX.exe (PID: 9048)
- ix78ESOrnjfX.exe (PID: 3632)
- ix78ESOrnjfX.exe (PID: 2592)
- ix78ESOrnjfX.exe (PID: 9204)
- ix78ESOrnjfX.exe (PID: 8472)
- ix78ESOrnjfX.exe (PID: 3688)
- ix78ESOrnjfX.exe (PID: 3516)
- ix78ESOrnjfX.exe (PID: 6212)
- ix78ESOrnjfX.exe (PID: 5680)
- ix78ESOrnjfX.exe (PID: 2816)
- ix78ESOrnjfX.exe (PID: 3780)
- ix78ESOrnjfX.exe (PID: 3740)
- ix78ESOrnjfX.exe (PID: 9572)
- ix78ESOrnjfX.exe (PID: 7844)
- ix78ESOrnjfX.exe (PID: 10180)
- ix78ESOrnjfX.exe (PID: 948)
- ix78ESOrnjfX.exe (PID: 6312)
- ix78ESOrnjfX.exe (PID: 9880)
- ix78ESOrnjfX.exe (PID: 11668)
- ix78ESOrnjfX.exe (PID: 11932)
- ix78ESOrnjfX.exe (PID: 7696)
- ix78ESOrnjfX.exe (PID: 10072)
- ix78ESOrnjfX.exe (PID: 3276)
- ix78ESOrnjfX.exe (PID: 10144)
- ix78ESOrnjfX.exe (PID: 9716)
- lighteningplayer-cache-gen.exe (PID: 12188)
- ix78ESOrnjfX.exe (PID: 3396)
- ix78ESOrnjfX.exe (PID: 12192)
- ix78ESOrnjfX.exe (PID: 6184)
- ix78ESOrnjfX.exe (PID: 7576)
- ix78ESOrnjfX.exe (PID: 11652)
- ix78ESOrnjfX.exe (PID: 10408)
- ix78ESOrnjfX.exe (PID: 3184)
- ix78ESOrnjfX.exe (PID: 11700)
- ix78ESOrnjfX.exe (PID: 10672)
- ix78ESOrnjfX.exe (PID: 12268)
- ix78ESOrnjfX.exe (PID: 6292)
- ix78ESOrnjfX.exe (PID: 7180)
- ix78ESOrnjfX.exe (PID: 5396)
- ix78ESOrnjfX.exe (PID: 11856)
- ix78ESOrnjfX.exe (PID: 10244)
- ix78ESOrnjfX.exe (PID: 7400)
- ix78ESOrnjfX.exe (PID: 5168)
- ix78ESOrnjfX.exe (PID: 3224)
- ix78ESOrnjfX.exe (PID: 8728)
- ix78ESOrnjfX.exe (PID: 6748)
- ix78ESOrnjfX.exe (PID: 932)
- ix78ESOrnjfX.exe (PID: 12200)
- ix78ESOrnjfX.exe (PID: 7264)
- ix78ESOrnjfX.exe (PID: 9924)
- ix78ESOrnjfX.exe (PID: 7904)
- ix78ESOrnjfX.exe (PID: 1900)
- ix78ESOrnjfX.exe (PID: 11632)
- ix78ESOrnjfX.exe (PID: 4308)
- ix78ESOrnjfX.exe (PID: 11964)
- ix78ESOrnjfX.exe (PID: 10916)
- ix78ESOrnjfX.exe (PID: 9588)
- ix78ESOrnjfX.exe (PID: 3940)
- ix78ESOrnjfX.exe (PID: 2948)
- ix78ESOrnjfX.exe (PID: 11360)
- ix78ESOrnjfX.exe (PID: 7704)
- ix78ESOrnjfX.exe (PID: 6772)
- ix78ESOrnjfX.exe (PID: 5912)
- ix78ESOrnjfX.exe (PID: 1716)
- ix78ESOrnjfX.exe (PID: 9876)
- ix78ESOrnjfX.exe (PID: 7788)
- ix78ESOrnjfX.exe (PID: 9292)
- ix78ESOrnjfX.exe (PID: 9576)
- ix78ESOrnjfX.exe (PID: 10332)
- ix78ESOrnjfX.exe (PID: 11512)
- ix78ESOrnjfX.exe (PID: 12004)
- ix78ESOrnjfX.exe (PID: 7092)
- ix78ESOrnjfX.exe (PID: 6428)
- ix78ESOrnjfX.exe (PID: 7120)
- ix78ESOrnjfX.exe (PID: 8300)
- ix78ESOrnjfX.exe (PID: 5032)
- ix78ESOrnjfX.exe (PID: 7624)
- ix78ESOrnjfX.exe (PID: 11628)
- ix78ESOrnjfX.exe (PID: 8188)
- ix78ESOrnjfX.exe (PID: 11480)
- ix78ESOrnjfX.exe (PID: 6720)
- ix78ESOrnjfX.exe (PID: 10628)
- ix78ESOrnjfX.exe (PID: 8260)
- ix78ESOrnjfX.exe (PID: 9304)
- ix78ESOrnjfX.exe (PID: 9532)
- ix78ESOrnjfX.exe (PID: 7896)
- ix78ESOrnjfX.exe (PID: 8412)
- ix78ESOrnjfX.exe (PID: 1884)
- ix78ESOrnjfX.exe (PID: 11372)
- ix78ESOrnjfX.exe (PID: 10204)
- ix78ESOrnjfX.exe (PID: 5344)
- ix78ESOrnjfX.exe (PID: 8256)
- ix78ESOrnjfX.exe (PID: 4192)
- ix78ESOrnjfX.exe (PID: 9016)
- ix78ESOrnjfX.exe (PID: 4520)
- ix78ESOrnjfX.exe (PID: 9036)
- ix78ESOrnjfX.exe (PID: 8892)
- ix78ESOrnjfX.exe (PID: 6652)
- ix78ESOrnjfX.exe (PID: 5292)
- ix78ESOrnjfX.exe (PID: 2900)
- ix78ESOrnjfX.exe (PID: 3252)
- ix78ESOrnjfX.exe (PID: 7612)
- ix78ESOrnjfX.exe (PID: 1728)
- ix78ESOrnjfX.exe (PID: 7964)
- ix78ESOrnjfX.exe (PID: 5772)
- ix78ESOrnjfX.exe (PID: 8544)
- ix78ESOrnjfX.exe (PID: 7568)
- ix78ESOrnjfX.exe (PID: 4696)
- ix78ESOrnjfX.exe (PID: 10372)
- ix78ESOrnjfX.exe (PID: 8104)
- ix78ESOrnjfX.exe (PID: 2584)
- ix78ESOrnjfX.exe (PID: 6976)
- ix78ESOrnjfX.exe (PID: 7212)
- ix78ESOrnjfX.exe (PID: 5744)
- ix78ESOrnjfX.exe (PID: 4648)
- ix78ESOrnjfX.exe (PID: 12256)
- ix78ESOrnjfX.exe (PID: 11076)
- ix78ESOrnjfX.exe (PID: 6820)
- ix78ESOrnjfX.exe (PID: 4240)
- ix78ESOrnjfX.exe (PID: 10284)
- ix78ESOrnjfX.exe (PID: 5968)
- ix78ESOrnjfX.exe (PID: 11708)
- ix78ESOrnjfX.exe (PID: 11380)
- ix78ESOrnjfX.exe (PID: 5872)
- ix78ESOrnjfX.exe (PID: 11900)
- ix78ESOrnjfX.exe (PID: 2940)
- ix78ESOrnjfX.exe (PID: 11096)
- ix78ESOrnjfX.exe (PID: 6388)
- ix78ESOrnjfX.exe (PID: 7736)
- ix78ESOrnjfX.exe (PID: 3964)
- ix78ESOrnjfX.exe (PID: 10644)
- ix78ESOrnjfX.exe (PID: 6912)
- ix78ESOrnjfX.exe (PID: 4388)
- ix78ESOrnjfX.exe (PID: 5956)
- ix78ESOrnjfX.exe (PID: 4128)
- ix78ESOrnjfX.exe (PID: 10892)
- ix78ESOrnjfX.exe (PID: 5640)
- ix78ESOrnjfX.exe (PID: 6688)
- ix78ESOrnjfX.exe (PID: 12120)
- ix78ESOrnjfX.exe (PID: 3092)
- ix78ESOrnjfX.exe (PID: 6840)
- ix78ESOrnjfX.exe (PID: 10224)
- ix78ESOrnjfX.exe (PID: 8788)
- ix78ESOrnjfX.exe (PID: 4508)
- ix78ESOrnjfX.exe (PID: 12196)
- ix78ESOrnjfX.exe (PID: 4024)
- ix78ESOrnjfX.exe (PID: 10748)
- ix78ESOrnjfX.exe (PID: 5252)
- ix78ESOrnjfX.exe (PID: 8844)
- ix78ESOrnjfX.exe (PID: 324)
- ix78ESOrnjfX.exe (PID: 3088)
- ix78ESOrnjfX.exe (PID: 2188)
- ix78ESOrnjfX.exe (PID: 7036)
- ix78ESOrnjfX.exe (PID: 3096)
- ix78ESOrnjfX.exe (PID: 11528)
- ix78ESOrnjfX.exe (PID: 5072)
- ix78ESOrnjfX.exe (PID: 1880)
- ix78ESOrnjfX.exe (PID: 1380)
- ix78ESOrnjfX.exe (PID: 3104)
- ix78ESOrnjfX.exe (PID: 8652)
- ix78ESOrnjfX.exe (PID: 7588)
- ix78ESOrnjfX.exe (PID: 5260)
- ix78ESOrnjfX.exe (PID: 6612)
- ix78ESOrnjfX.exe (PID: 9108)
- ix78ESOrnjfX.exe (PID: 8312)
- ix78ESOrnjfX.exe (PID: 9076)
- ix78ESOrnjfX.exe (PID: 11148)
- ix78ESOrnjfX.exe (PID: 1096)
- ix78ESOrnjfX.exe (PID: 5520)
- ix78ESOrnjfX.exe (PID: 11904)
- ix78ESOrnjfX.exe (PID: 2272)
- ix78ESOrnjfX.exe (PID: 10712)
- ix78ESOrnjfX.exe (PID: 2044)
- ix78ESOrnjfX.exe (PID: 9432)
- ix78ESOrnjfX.exe (PID: 2740)
- ix78ESOrnjfX.exe (PID: 5056)
- ix78ESOrnjfX.exe (PID: 7024)
- ix78ESOrnjfX.exe (PID: 12220)
- ix78ESOrnjfX.exe (PID: 4008)
- ix78ESOrnjfX.exe (PID: 976)
- ix78ESOrnjfX.exe (PID: 10828)
- ix78ESOrnjfX.exe (PID: 3660)
- ix78ESOrnjfX.exe (PID: 5804)
- ix78ESOrnjfX.exe (PID: 8688)
- ix78ESOrnjfX.exe (PID: 9196)
- ix78ESOrnjfX.exe (PID: 9252)
- ix78ESOrnjfX.exe (PID: 7388)
- ix78ESOrnjfX.exe (PID: 11024)
- ix78ESOrnjfX.exe (PID: 7464)
- ix78ESOrnjfX.exe (PID: 11212)
- Nel.exe.com (PID: 3212)
- Nel.exe.com (PID: 6900)
- ix78ESOrnjfX.exe (PID: 12292)
- ix78ESOrnjfX.exe (PID: 7060)
- ix78ESOrnjfX.exe (PID: 4392)
- ix78ESOrnjfX.exe (PID: 5660)
- ix78ESOrnjfX.exe (PID: 11260)
- ix78ESOrnjfX.exe (PID: 12656)
- ix78ESOrnjfX.exe (PID: 13044)
- ix78ESOrnjfX.exe (PID: 12832)
- ix78ESOrnjfX.exe (PID: 13608)
- ix78ESOrnjfX.exe (PID: 14072)
- ix78ESOrnjfX.exe (PID: 12488)
- ix78ESOrnjfX.exe (PID: 2432)
- ix78ESOrnjfX.exe (PID: 13032)
- ix78ESOrnjfX.exe (PID: 13196)
- ix78ESOrnjfX.exe (PID: 13540)
- ix78ESOrnjfX.exe (PID: 14240)
- ix78ESOrnjfX.exe (PID: 12376)
- ix78ESOrnjfX.exe (PID: 12680)
- ix78ESOrnjfX.exe (PID: 14060)
- ix78ESOrnjfX.exe (PID: 14280)
- ix78ESOrnjfX.exe (PID: 12512)
- ix78ESOrnjfX.exe (PID: 13680)
- ix78ESOrnjfX.exe (PID: 13768)
- ix78ESOrnjfX.exe (PID: 13932)
- ix78ESOrnjfX.exe (PID: 13580)
- ix78ESOrnjfX.exe (PID: 13744)
- ix78ESOrnjfX.exe (PID: 13924)
- ix78ESOrnjfX.exe (PID: 14020)
- ix78ESOrnjfX.exe (PID: 12780)
- ix78ESOrnjfX.exe (PID: 12924)
- ix78ESOrnjfX.exe (PID: 13208)
- ix78ESOrnjfX.exe (PID: 12668)
- ix78ESOrnjfX.exe (PID: 12828)
- ix78ESOrnjfX.exe (PID: 12984)
- ix78ESOrnjfX.exe (PID: 14224)
- ix78ESOrnjfX.exe (PID: 12368)
- ix78ESOrnjfX.exe (PID: 12532)
- ix78ESOrnjfX.exe (PID: 13696)
- ix78ESOrnjfX.exe (PID: 13824)
- ix78ESOrnjfX.exe (PID: 12416)
- ix78ESOrnjfX.exe (PID: 13272)
- ix78ESOrnjfX.exe (PID: 13400)
- ix78ESOrnjfX.exe (PID: 13500)
- ix78ESOrnjfX.exe (PID: 12300)
- ix78ESOrnjfX.exe (PID: 12516)
- ix78ESOrnjfX.exe (PID: 12648)
- ix78ESOrnjfX.exe (PID: 13964)
- ix78ESOrnjfX.exe (PID: 14024)
- ix78ESOrnjfX.exe (PID: 14204)
- ix78ESOrnjfX.exe (PID: 12372)
- ix78ESOrnjfX.exe (PID: 13280)
- ix78ESOrnjfX.exe (PID: 13432)
- ix78ESOrnjfX.exe (PID: 13560)
- ix78ESOrnjfX.exe (PID: 13752)
- ix78ESOrnjfX.exe (PID: 5888)
- ix78ESOrnjfX.exe (PID: 12844)
- ix78ESOrnjfX.exe (PID: 12988)
- ix78ESOrnjfX.exe (PID: 13180)
- ix78ESOrnjfX.exe (PID: 12584)
- ix78ESOrnjfX.exe (PID: 12360)
- ix78ESOrnjfX.exe (PID: 12644)
- ix78ESOrnjfX.exe (PID: 12960)
- ix78ESOrnjfX.exe (PID: 13148)
- ix78ESOrnjfX.exe (PID: 14008)
- ix78ESOrnjfX.exe (PID: 14172)
- ix78ESOrnjfX.exe (PID: 14296)
- ix78ESOrnjfX.exe (PID: 13884)
- ix78ESOrnjfX.exe (PID: 14040)
- ix78ESOrnjfX.exe (PID: 12316)
- ix78ESOrnjfX.exe (PID: 12480)
- ix78ESOrnjfX.exe (PID: 13060)
- ix78ESOrnjfX.exe (PID: 3132)
- ix78ESOrnjfX.exe (PID: 13740)
- ix78ESOrnjfX.exe (PID: 14192)
- ix78ESOrnjfX.exe (PID: 13120)
- ix78ESOrnjfX.exe (PID: 13256)
- ix78ESOrnjfX.exe (PID: 12320)
- ix78ESOrnjfX.exe (PID: 13636)
- ix78ESOrnjfX.exe (PID: 14056)
- ix78ESOrnjfX.exe (PID: 14080)
- ix78ESOrnjfX.exe (PID: 12856)
- ix78ESOrnjfX.exe (PID: 13384)
- ix78ESOrnjfX.exe (PID: 12768)
- ix78ESOrnjfX.exe (PID: 12916)
- ix78ESOrnjfX.exe (PID: 13284)
- ix78ESOrnjfX.exe (PID: 13356)
- ix78ESOrnjfX.exe (PID: 14308)
- ix78ESOrnjfX.exe (PID: 12524)
- ix78ESOrnjfX.exe (PID: 13528)
- ix78ESOrnjfX.exe (PID: 13424)
- ix78ESOrnjfX.exe (PID: 13192)
- ix78ESOrnjfX.exe (PID: 12880)
- ix78ESOrnjfX.exe (PID: 13520)
- md1_1eaf.exe (PID: 13620)
- ix78ESOrnjfX.exe (PID: 13852)
- ix78ESOrnjfX.exe (PID: 13172)
- ix78ESOrnjfX.exe (PID: 13224)
- ix78ESOrnjfX.exe (PID: 13360)
- ix78ESOrnjfX.exe (PID: 13784)
- ix78ESOrnjfX.exe (PID: 12444)
- ix78ESOrnjfX.exe (PID: 14316)
- ix78ESOrnjfX.exe (PID: 12604)
- ix78ESOrnjfX.exe (PID: 13836)
- ix78ESOrnjfX.exe (PID: 14120)
- ix78ESOrnjfX.exe (PID: 13084)
- ix78ESOrnjfX.exe (PID: 13388)
- ix78ESOrnjfX.exe (PID: 12504)
- ix78ESOrnjfX.exe (PID: 14132)
- ix78ESOrnjfX.exe (PID: 12380)
- ix78ESOrnjfX.exe (PID: 12764)
- ix78ESOrnjfX.exe (PID: 13368)
- ix78ESOrnjfX.exe (PID: 13804)
- ix78ESOrnjfX.exe (PID: 12896)
- ix78ESOrnjfX.exe (PID: 13108)
- ix78ESOrnjfX.exe (PID: 12356)
- ix78ESOrnjfX.exe (PID: 13316)
- ix78ESOrnjfX.exe (PID: 8516)
- ix78ESOrnjfX.exe (PID: 13600)
- ix78ESOrnjfX.exe (PID: 12948)
- ix78ESOrnjfX.exe (PID: 10952)
- ix78ESOrnjfX.exe (PID: 12904)
- ix78ESOrnjfX.exe (PID: 13792)
- ix78ESOrnjfX.exe (PID: 13052)
- ix78ESOrnjfX.exe (PID: 5116)
- ix78ESOrnjfX.exe (PID: 12464)
- ix78ESOrnjfX.exe (PID: 12912)
- ix78ESOrnjfX.exe (PID: 2812)
- ix78ESOrnjfX.exe (PID: 12884)
- ix78ESOrnjfX.exe (PID: 13812)
- ix78ESOrnjfX.exe (PID: 13296)
- ix78ESOrnjfX.exe (PID: 13992)
- ix78ESOrnjfX.exe (PID: 12800)
- ix78ESOrnjfX.exe (PID: 12420)
- ix78ESOrnjfX.exe (PID: 6916)
- ix78ESOrnjfX.exe (PID: 12472)
- ix78ESOrnjfX.exe (PID: 10020)
- ix78ESOrnjfX.exe (PID: 12640)
- ix78ESOrnjfX.exe (PID: 12484)
- ix78ESOrnjfX.exe (PID: 13644)
- ix78ESOrnjfX.exe (PID: 12736)
- ix78ESOrnjfX.exe (PID: 14168)
- ix78ESOrnjfX.exe (PID: 13096)
- ix78ESOrnjfX.exe (PID: 13576)
- ix78ESOrnjfX.exe (PID: 12692)
- ix78ESOrnjfX.exe (PID: 12804)
- ix78ESOrnjfX.exe (PID: 12840)
- ix78ESOrnjfX.exe (PID: 12632)
- ix78ESOrnjfX.exe (PID: 7880)
- ix78ESOrnjfX.exe (PID: 12412)
- ix78ESOrnjfX.exe (PID: 13068)
- ix78ESOrnjfX.exe (PID: 12468)
- ix78ESOrnjfX.exe (PID: 13920)
- ix78ESOrnjfX.exe (PID: 13004)
- ix78ESOrnjfX.exe (PID: 12500)
- ix78ESOrnjfX.exe (PID: 13732)
- ix78ESOrnjfX.exe (PID: 2104)
- ix78ESOrnjfX.exe (PID: 13324)
- ix78ESOrnjfX.exe (PID: 7764)
- ix78ESOrnjfX.exe (PID: 12348)
- ix78ESOrnjfX.exe (PID: 13764)
- ix78ESOrnjfX.exe (PID: 14184)
- ix78ESOrnjfX.exe (PID: 12404)
- ix78ESOrnjfX.exe (PID: 1748)
- ix78ESOrnjfX.exe (PID: 8024)
- ix78ESOrnjfX.exe (PID: 13796)
- ix78ESOrnjfX.exe (PID: 760)
- ix78ESOrnjfX.exe (PID: 13080)
- ix78ESOrnjfX.exe (PID: 13008)
- ix78ESOrnjfX.exe (PID: 13236)
- ix78ESOrnjfX.exe (PID: 13176)
- ix78ESOrnjfX.exe (PID: 13720)
- ix78ESOrnjfX.exe (PID: 12552)
- ix78ESOrnjfX.exe (PID: 12968)
- ix78ESOrnjfX.exe (PID: 13020)
- ix78ESOrnjfX.exe (PID: 13632)
- ix78ESOrnjfX.exe (PID: 13912)
- ix78ESOrnjfX.exe (PID: 14104)
- ix78ESOrnjfX.exe (PID: 7020)
- ix78ESOrnjfX.exe (PID: 13028)
- ix78ESOrnjfX.exe (PID: 12788)
- ix78ESOrnjfX.exe (PID: 12432)
- ix78ESOrnjfX.exe (PID: 13800)
- ix78ESOrnjfX.exe (PID: 14096)
- ix78ESOrnjfX.exe (PID: 3144)
- ix78ESOrnjfX.exe (PID: 9872)
- ix78ESOrnjfX.exe (PID: 3044)
- ix78ESOrnjfX.exe (PID: 13788)
- ix78ESOrnjfX.exe (PID: 13024)
- ix78ESOrnjfX.exe (PID: 2364)
- ix78ESOrnjfX.exe (PID: 13292)
- ix78ESOrnjfX.exe (PID: 14124)
- ix78ESOrnjfX.exe (PID: 13972)
- ix78ESOrnjfX.exe (PID: 13728)
- ix78ESOrnjfX.exe (PID: 14152)
- ix78ESOrnjfX.exe (PID: 13996)
- ix78ESOrnjfX.exe (PID: 13592)
- ix78ESOrnjfX.exe (PID: 13904)
- ix78ESOrnjfX.exe (PID: 10464)
- ix78ESOrnjfX.exe (PID: 12560)
- ix78ESOrnjfX.exe (PID: 13876)
- ix78ESOrnjfX.exe (PID: 13440)
- ix78ESOrnjfX.exe (PID: 13940)
- ix78ESOrnjfX.exe (PID: 12868)
- ix78ESOrnjfX.exe (PID: 13808)
- ix78ESOrnjfX.exe (PID: 11436)
- ix78ESOrnjfX.exe (PID: 13496)
- ix78ESOrnjfX.exe (PID: 4440)
- ix78ESOrnjfX.exe (PID: 11044)
- ix78ESOrnjfX.exe (PID: 12448)
- ix78ESOrnjfX.exe (PID: 13304)
- ix78ESOrnjfX.exe (PID: 12436)
- ix78ESOrnjfX.exe (PID: 13000)
- ix78ESOrnjfX.exe (PID: 5540)
- ix78ESOrnjfX.exe (PID: 14176)
- ix78ESOrnjfX.exe (PID: 13464)
- ix78ESOrnjfX.exe (PID: 11836)
- ix78ESOrnjfX.exe (PID: 14264)
- ix78ESOrnjfX.exe (PID: 13088)
- ix78ESOrnjfX.exe (PID: 11636)
- ix78ESOrnjfX.exe (PID: 13300)
- ix78ESOrnjfX.exe (PID: 14164)
- ix78ESOrnjfX.exe (PID: 13944)
- ix78ESOrnjfX.exe (PID: 13164)
- ix78ESOrnjfX.exe (PID: 12636)
- ix78ESOrnjfX.exe (PID: 14284)
- ix78ESOrnjfX.exe (PID: 12600)
- ix78ESOrnjfX.exe (PID: 13160)
- ix78ESOrnjfX.exe (PID: 13936)
- ix78ESOrnjfX.exe (PID: 13336)
- ix78ESOrnjfX.exe (PID: 13624)
- ix78ESOrnjfX.exe (PID: 13504)
- ix78ESOrnjfX.exe (PID: 7240)
- ix78ESOrnjfX.exe (PID: 13116)
- ix78ESOrnjfX.exe (PID: 12568)
- ix78ESOrnjfX.exe (PID: 13476)
- ix78ESOrnjfX.exe (PID: 13816)
- ix78ESOrnjfX.exe (PID: 1904)
- ix78ESOrnjfX.exe (PID: 13712)
- ix78ESOrnjfX.exe (PID: 13404)
- ix78ESOrnjfX.exe (PID: 12992)
- ix78ESOrnjfX.exe (PID: 12664)
- ix78ESOrnjfX.exe (PID: 12872)
- ix78ESOrnjfX.exe (PID: 13480)
- ix78ESOrnjfX.exe (PID: 13900)
- ix78ESOrnjfX.exe (PID: 14100)
- ix78ESOrnjfX.exe (PID: 13348)
- ix78ESOrnjfX.exe (PID: 10552)
- ix78ESOrnjfX.exe (PID: 12624)
- ix78ESOrnjfX.exe (PID: 13844)
- ix78ESOrnjfX.exe (PID: 6056)
- ix78ESOrnjfX.exe (PID: 13868)
- ix78ESOrnjfX.exe (PID: 10680)
- ix78ESOrnjfX.exe (PID: 13616)
- ix78ESOrnjfX.exe (PID: 11736)
- ix78ESOrnjfX.exe (PID: 7864)
- ix78ESOrnjfX.exe (PID: 10316)
- ix78ESOrnjfX.exe (PID: 7444)
- ix78ESOrnjfX.exe (PID: 12576)
- ix78ESOrnjfX.exe (PID: 12700)
- ix78ESOrnjfX.exe (PID: 14004)
- ix78ESOrnjfX.exe (PID: 13872)
- ix78ESOrnjfX.exe (PID: 9472)
- ix78ESOrnjfX.exe (PID: 9724)
- ix78ESOrnjfX.exe (PID: 8096)
- ix78ESOrnjfX.exe (PID: 10632)
- ix78ESOrnjfX.exe (PID: 8280)
- ix78ESOrnjfX.exe (PID: 7832)
- ix78ESOrnjfX.exe (PID: 14532)
- ix78ESOrnjfX.exe (PID: 15124)
- ix78ESOrnjfX.exe (PID: 14860)
- ix78ESOrnjfX.exe (PID: 14968)
- ix78ESOrnjfX.exe (PID: 9160)
- ix78ESOrnjfX.exe (PID: 12652)
- ix78ESOrnjfX.exe (PID: 11432)
- ix78ESOrnjfX.exe (PID: 14724)
- ix78ESOrnjfX.exe (PID: 15600)
- ix78ESOrnjfX.exe (PID: 15720)
- ix78ESOrnjfX.exe (PID: 15944)
- ix78ESOrnjfX.exe (PID: 15840)
- ix78ESOrnjfX.exe (PID: 15208)
- ix78ESOrnjfX.exe (PID: 15348)
- ix78ESOrnjfX.exe (PID: 15452)
- ix78ESOrnjfX.exe (PID: 14768)
- ix78ESOrnjfX.exe (PID: 15132)
- ix78ESOrnjfX.exe (PID: 15432)
- ix78ESOrnjfX.exe (PID: 16044)
- ix78ESOrnjfX.exe (PID: 16240)
- ix78ESOrnjfX.exe (PID: 14340)
- ix78ESOrnjfX.exe (PID: 15292)
- ix78ESOrnjfX.exe (PID: 16156)
- ix78ESOrnjfX.exe (PID: 14516)
- ix78ESOrnjfX.exe (PID: 14672)
- ix78ESOrnjfX.exe (PID: 15664)
- ix78ESOrnjfX.exe (PID: 15824)
- ix78ESOrnjfX.exe (PID: 16012)
- ix78ESOrnjfX.exe (PID: 16356)
- ix78ESOrnjfX.exe (PID: 15368)
- ix78ESOrnjfX.exe (PID: 15460)
- ix78ESOrnjfX.exe (PID: 15580)
- ix78ESOrnjfX.exe (PID: 5788)
- ix78ESOrnjfX.exe (PID: 14876)
- ix78ESOrnjfX.exe (PID: 14912)
- ix78ESOrnjfX.exe (PID: 14656)
- ix78ESOrnjfX.exe (PID: 15244)
- ix78ESOrnjfX.exe (PID: 16180)
- ix78ESOrnjfX.exe (PID: 16380)
- ix78ESOrnjfX.exe (PID: 8508)
- ix78ESOrnjfX.exe (PID: 14616)
- ix78ESOrnjfX.exe (PID: 15796)
- ix78ESOrnjfX.exe (PID: 15912)
- ix78ESOrnjfX.exe (PID: 16056)
- ix78ESOrnjfX.exe (PID: 15264)
- ix78ESOrnjfX.exe (PID: 14448)
- ix78ESOrnjfX.exe (PID: 15536)
- ix78ESOrnjfX.exe (PID: 15148)
- ix78ESOrnjfX.exe (PID: 14744)
- ix78ESOrnjfX.exe (PID: 14920)
- ix78ESOrnjfX.exe (PID: 15056)
- ix78ESOrnjfX.exe (PID: 16212)
- ix78ESOrnjfX.exe (PID: 14480)
- ix78ESOrnjfX.exe (PID: 15392)
- ix78ESOrnjfX.exe (PID: 16008)
- ix78ESOrnjfX.exe (PID: 14956)
- ix78ESOrnjfX.exe (PID: 15736)
- ix78ESOrnjfX.exe (PID: 14836)
- ix78ESOrnjfX.exe (PID: 12388)
- ix78ESOrnjfX.exe (PID: 4644)
- ix78ESOrnjfX.exe (PID: 16360)
- ix78ESOrnjfX.exe (PID: 15024)
- ix78ESOrnjfX.exe (PID: 15708)
- gaoou.exe (PID: 16236)
- ix78ESOrnjfX.exe (PID: 14700)
- ix78ESOrnjfX.exe (PID: 15492)
- ix78ESOrnjfX.exe (PID: 15284)
- ix78ESOrnjfX.exe (PID: 15884)
- ix78ESOrnjfX.exe (PID: 16096)
- ix78ESOrnjfX.exe (PID: 4076)
- ix78ESOrnjfX.exe (PID: 14888)
- ix78ESOrnjfX.exe (PID: 15152)
- ix78ESOrnjfX.exe (PID: 15972)
- ix78ESOrnjfX.exe (PID: 14664)
- ix78ESOrnjfX.exe (PID: 14940)
- ix78ESOrnjfX.exe (PID: 15704)
- ix78ESOrnjfX.exe (PID: 14752)
- ix78ESOrnjfX.exe (PID: 3228)
- ix78ESOrnjfX.exe (PID: 15168)
- ix78ESOrnjfX.exe (PID: 15808)
- ix78ESOrnjfX.exe (PID: 2288)
- ix78ESOrnjfX.exe (PID: 16272)
- ix78ESOrnjfX.exe (PID: 15472)
- Setup3310.exe (PID: 12776)
- ix78ESOrnjfX.exe (PID: 14512)
- ix78ESOrnjfX.exe (PID: 15136)
- ix78ESOrnjfX.exe (PID: 16032)
- ix78ESOrnjfX.exe (PID: 2724)
- ix78ESOrnjfX.exe (PID: 15616)
- ix78ESOrnjfX.exe (PID: 4872)
- ix78ESOrnjfX.exe (PID: 16080)
- ix78ESOrnjfX.exe (PID: 14440)
- ix78ESOrnjfX.exe (PID: 15200)
- ix78ESOrnjfX.exe (PID: 15872)
- ix78ESOrnjfX.exe (PID: 16320)
- ix78ESOrnjfX.exe (PID: 15656)
- ix78ESOrnjfX.exe (PID: 15524)
- ix78ESOrnjfX.exe (PID: 14880)
- ix78ESOrnjfX.exe (PID: 14384)
- ix78ESOrnjfX.exe (PID: 16296)
- ix78ESOrnjfX.exe (PID: 15592)
- ix78ESOrnjfX.exe (PID: 14584)
- ix78ESOrnjfX.exe (PID: 12724)
- ix78ESOrnjfX.exe (PID: 15412)
- ix78ESOrnjfX.exe (PID: 15112)
- jfiag3g_gg.exe (PID: 14372)
- ix78ESOrnjfX.exe (PID: 15444)
- ix78ESOrnjfX.exe (PID: 13136)
- ix78ESOrnjfX.exe (PID: 16104)
- ix78ESOrnjfX.exe (PID: 14916)
- ix78ESOrnjfX.exe (PID: 15556)
- ix78ESOrnjfX.exe (PID: 15996)
- ix78ESOrnjfX.exe (PID: 15228)
- ix78ESOrnjfX.exe (PID: 14412)
- ix78ESOrnjfX.exe (PID: 16216)
- ix78ESOrnjfX.exe (PID: 14644)
- ix78ESOrnjfX.exe (PID: 14556)
- google-game.exe (PID: 15700)
- ix78ESOrnjfX.exe (PID: 14032)
- ix78ESOrnjfX.exe (PID: 3680)
- ix78ESOrnjfX.exe (PID: 8236)
- ix78ESOrnjfX.exe (PID: 15344)
- ix78ESOrnjfX.exe (PID: 14812)
- ix78ESOrnjfX.exe (PID: 14976)
- ix78ESOrnjfX.exe (PID: 16184)
- ix78ESOrnjfX.exe (PID: 15360)
- 005.exe (PID: 13152)
- ix78ESOrnjfX.exe (PID: 14408)
- ix78ESOrnjfX.exe (PID: 14548)
- ix78ESOrnjfX.exe (PID: 16228)
- ix78ESOrnjfX.exe (PID: 16120)
- ix78ESOrnjfX.exe (PID: 14992)
- ix78ESOrnjfX.exe (PID: 15976)
- ix78ESOrnjfX.exe (PID: 15288)
- ix78ESOrnjfX.exe (PID: 14736)
- ix78ESOrnjfX.exe (PID: 4468)
- ix78ESOrnjfX.exe (PID: 10880)
- ix78ESOrnjfX.exe (PID: 15924)
- ix78ESOrnjfX.exe (PID: 15008)
- ix78ESOrnjfX.exe (PID: 11004)
- ix78ESOrnjfX.exe (PID: 14420)
- ix78ESOrnjfX.exe (PID: 15908)
- ix78ESOrnjfX.exe (PID: 16300)
- ix78ESOrnjfX.exe (PID: 14784)
- ix78ESOrnjfX.exe (PID: 16348)
Drops executable file immediately after starts
- setup_installer.exe (PID: 3032)
- metina_1.exe (PID: 648)
- p8g4aIxrVWYViEzCIwRjDG3Q.exe (PID: 3864)
Changes the autorun value in the registry
- metina_4.exe (PID: 2664)
- (_____(_(_________))235 Smeargle.exe (PID: 3900)
Loads dropped or rewritten executable
- setup_install.exe (PID: 2576)
- rUNdlL32.eXe (PID: 1764)
- conhost.exe (PID: 3924)
- cmd.exe (PID: 2040)
- cmd.exe (PID: 1748)
- chrome.exe (PID: 2204)
- cmd.exe (PID: 2688)
- metina_4.exe (PID: 2664)
- chrome.exe (PID: 1680)
- chrome.exe (PID: 2292)
- chrome.exe (PID: 3548)
- DllHost.exe (PID: 2904)
- metina_1.exe (PID: 648)
- AUDIODG.EXE (PID: 376)
- chrome.exe (PID: 668)
- cmd.exe (PID: 1800)
- SearchFilterHost.exe (PID: 3168)
- chrome.exe (PID: 2060)
- WinRAR.exe (PID: 3608)
- setup_installer.exe (PID: 3032)
- DllHost.exe (PID: 1428)
- DllHost.exe (PID: 1940)
- cmd.exe (PID: 1328)
- chrome.exe (PID: 3140)
- x86_x64_setup.exe (PID: 2400)
- x86_x64_setup.exe (PID: 1840)
- cmd.exe (PID: 3152)
- DllHost.exe (PID: 1460)
- consent.exe (PID: 2644)
- metina_6.exe (PID: 2224)
- chrome.exe (PID: 2292)
- metina_3.exe (PID: 3756)
- svchost.exe (PID: 4092)
- chrome.exe (PID: 2152)
- chrome.exe (PID: 548)
- chrome.exe (PID: 1444)
- jfiag3g_gg.exe (PID: 3764)
- chrome.exe (PID: 2572)
- chrome.exe (PID: 3856)
- chrome.exe (PID: 1200)
- chrome.exe (PID: 2660)
- DllHost.exe (PID: 3636)
- chrome.exe (PID: 2828)
- metina_5.exe (PID: 3664)
- WinRAR.exe (PID: 648)
- chrome.exe (PID: 1492)
- cmd.exe (PID: 2528)
- chrome.exe (PID: 3896)
- wmiprvse.exe (PID: 2192)
- chrome.exe (PID: 2568)
- metina_2.exe (PID: 1760)
- wmiprvse.exe (PID: 2516)
- chrome.exe (PID: 2764)
- chrome.exe (PID: 3544)
- NOTEPAD.EXE (PID: 756)
- svchost.exe (PID: 2252)
- DllHost.exe (PID: 2212)
- WerFault.exe (PID: 3116)
- conhost.exe (PID: 532)
- jfiag3g_gg.exe (PID: 1512)
- YrzSoesjiLwxBCoMxHQZirVc.exe (PID: 4060)
- NHv27pefor9cjMZxQPyaoTxI.exe (PID: 3844)
- ovkclsFeaGxsWSFI43MgtqQE.exe (PID: 3020)
- rEyWPHzEjwsMBXGpHUKTBrhV.exe (PID: 960)
- qHdNlR18fgOe7MhumSEpTmir.exe (PID: 3380)
- p8g4aIxrVWYViEzCIwRjDG3Q.exe (PID: 3864)
- 4S6ougCAgc8iShZEDJo0kSnE.exe (PID: 2832)
- rMVZCe2lp19v9IjXoRM6IDf9.exe (PID: 3388)
- conhost.exe (PID: 1504)
- Browzar.exe (PID: 1520)
- conhost.exe (PID: 272)
- ovkclsFeaGxsWSFI43MgtqQE.exe (PID: 3304)
- ultramediaburner.exe (PID: 3180)
- nUcWWy3PkrkGIOnGIjiZTNEZ.exe (PID: 3584)
- ix78ESOrnjfX.exe (PID: 3956)
- N45w47HnqWFawEkl0bru5UlP.exe (PID: 2420)
- NHv27pefor9cjMZxQPyaoTxI.exe (PID: 992)
- LF0oWSD2TqJjfvQ1dz0Eeecm.exe (PID: 2372)
- conhost.exe (PID: 2960)
- conhost.exe (PID: 3456)
- conhost.exe (PID: 2908)
- xklWwL5ZQDKR8P3RorxcFDlW.exe (PID: 1556)
- 6iawqAht8OEFOcBQIcovYGl6.exe (PID: 1376)
- Wefecasofe.exe (PID: 2744)
- Sq6dX94rnN0wqrGHutTck93N.exe (PID: 964)
- kpsVuIwTxthziIAnqHxbmA3S.exe (PID: 4928)
- ZHyvylevyhu.exe (PID: 4980)
- rMVZCe2lp19v9IjXoRM6IDf9.exe (PID: 1480)
- file4.exe (PID: 4328)
- conhost.exe (PID: 5476)
- jooyu.exe (PID: 4320)
- firefox.exe (PID: 5964)
- jfiag3g_gg.exe (PID: 5164)
- jingzhang.exe (PID: 5852)
- xklWwL5ZQDKR8P3RorxcFDlW.exe (PID: 5592)
- N45w47HnqWFawEkl0bru5UlP.exe (PID: 2752)
- nUcWWy3PkrkGIOnGIjiZTNEZ.exe (PID: 3072)
- md8_8eus.exe (PID: 6128)
- wmiprvse.exe (PID: 5256)
- DllHost.exe (PID: 5148)
- sCUIVIyz6dLBRM80cvSf4Ms9.exe (PID: 5844)
- cmd.exe (PID: 6064)
- ix78ESOrnjfX.exe (PID: 4264)
- conhost.exe (PID: 4232)
- ix78ESOrnjfX.exe (PID: 5932)
- cmd.exe (PID: 4760)
- ix78ESOrnjfX.exe (PID: 4104)
- UltraMediaBurner.exe (PID: 4108)
- ix78ESOrnjfX.exe (PID: 5832)
- conhost.exe (PID: 4488)
- WerFault.exe (PID: 5028)
- ix78ESOrnjfX.exe (PID: 5636)
- ix78ESOrnjfX.exe (PID: 5724)
- ix78ESOrnjfX.exe (PID: 4304)
- ix78ESOrnjfX.exe (PID: 4888)
- ix78ESOrnjfX.exe (PID: 4056)
- jfiag3g_gg.exe (PID: 5368)
- ix78ESOrnjfX.exe (PID: 4580)
- ix78ESOrnjfX.exe (PID: 4448)
- ix78ESOrnjfX.exe (PID: 4416)
- ix78ESOrnjfX.exe (PID: 5876)
- ix78ESOrnjfX.exe (PID: 4612)
- ix78ESOrnjfX.exe (PID: 5524)
- ix78ESOrnjfX.exe (PID: 2532)
- ix78ESOrnjfX.exe (PID: 5624)
- ix78ESOrnjfX.exe (PID: 4620)
- ix78ESOrnjfX.exe (PID: 5880)
- ix78ESOrnjfX.exe (PID: 5840)
- 75597259823.exe (PID: 5120)
- ix78ESOrnjfX.exe (PID: 3340)
- ix78ESOrnjfX.exe (PID: 4892)
- ix78ESOrnjfX.exe (PID: 5448)
- ix78ESOrnjfX.exe (PID: 4976)
- ix78ESOrnjfX.exe (PID: 4340)
- ix78ESOrnjfX.exe (PID: 2088)
- ix78ESOrnjfX.exe (PID: 4152)
- ix78ESOrnjfX.exe (PID: 3128)
- ix78ESOrnjfX.exe (PID: 1612)
- taskkill.exe (PID: 5228)
- ix78ESOrnjfX.exe (PID: 3256)
- ix78ESOrnjfX.exe (PID: 5332)
- ix78ESOrnjfX.exe (PID: 4204)
- ix78ESOrnjfX.exe (PID: 3840)
- ix78ESOrnjfX.exe (PID: 5736)
- ix78ESOrnjfX.exe (PID: 1196)
- ix78ESOrnjfX.exe (PID: 5900)
- ix78ESOrnjfX.exe (PID: 1672)
- ix78ESOrnjfX.exe (PID: 5172)
- ix78ESOrnjfX.exe (PID: 6120)
- ix78ESOrnjfX.exe (PID: 1464)
- ix78ESOrnjfX.exe (PID: 4884)
- ix78ESOrnjfX.exe (PID: 5576)
- ix78ESOrnjfX.exe (PID: 6036)
- firefox.exe (PID: 6008)
- ix78ESOrnjfX.exe (PID: 5700)
- ix78ESOrnjfX.exe (PID: 5176)
- ix78ESOrnjfX.exe (PID: 3368)
- ix78ESOrnjfX.exe (PID: 4216)
- ix78ESOrnjfX.exe (PID: 5980)
- ix78ESOrnjfX.exe (PID: 1544)
- ix78ESOrnjfX.exe (PID: 5004)
- ix78ESOrnjfX.exe (PID: 5088)
- ix78ESOrnjfX.exe (PID: 5424)
- firefox.exe (PID: 2612)
- ix78ESOrnjfX.exe (PID: 5016)
- ix78ESOrnjfX.exe (PID: 5296)
- ix78ESOrnjfX.exe (PID: 4752)
- ix78ESOrnjfX.exe (PID: 6000)
- ix78ESOrnjfX.exe (PID: 5536)
- rUNdlL32.eXe (PID: 3744)
- ix78ESOrnjfX.exe (PID: 3624)
- ix78ESOrnjfX.exe (PID: 308)
- ix78ESOrnjfX.exe (PID: 5188)
- ix78ESOrnjfX.exe (PID: 5656)
- ix78ESOrnjfX.exe (PID: 2120)
- ix78ESOrnjfX.exe (PID: 3884)
- ix78ESOrnjfX.exe (PID: 5768)
- ix78ESOrnjfX.exe (PID: 5408)
- ix78ESOrnjfX.exe (PID: 4836)
- ix78ESOrnjfX.exe (PID: 4088)
- ix78ESOrnjfX.exe (PID: 3852)
- ix78ESOrnjfX.exe (PID: 5460)
- ix78ESOrnjfX.exe (PID: 4356)
- ix78ESOrnjfX.exe (PID: 4528)
- ix78ESOrnjfX.exe (PID: 5604)
- ix78ESOrnjfX.exe (PID: 4924)
- iexplore.exe (PID: 5144)
- ix78ESOrnjfX.exe (PID: 3652)
- ix78ESOrnjfX.exe (PID: 892)
- ix78ESOrnjfX.exe (PID: 5920)
- ix78ESOrnjfX.exe (PID: 5428)
- ix78ESOrnjfX.exe (PID: 5924)
- ix78ESOrnjfX.exe (PID: 2956)
- ix78ESOrnjfX.exe (PID: 2980)
- ix78ESOrnjfX.exe (PID: 2472)
- ix78ESOrnjfX.exe (PID: 5240)
- DllHost.exe (PID: 4896)
- ix78ESOrnjfX.exe (PID: 2988)
- ix78ESOrnjfX.exe (PID: 2800)
- ix78ESOrnjfX.exe (PID: 980)
- ix78ESOrnjfX.exe (PID: 1496)
- ix78ESOrnjfX.exe (PID: 2696)
- ix78ESOrnjfX.exe (PID: 6044)
- ix78ESOrnjfX.exe (PID: 2136)
- ix78ESOrnjfX.exe (PID: 2636)
- ix78ESOrnjfX.exe (PID: 2964)
- ix78ESOrnjfX.exe (PID: 3948)
- ix78ESOrnjfX.exe (PID: 5104)
- ix78ESOrnjfX.exe (PID: 5216)
- ix78ESOrnjfX.exe (PID: 2640)
- ix78ESOrnjfX.exe (PID: 5516)
- ix78ESOrnjfX.exe (PID: 1920)
- chrome.exe (PID: 2820)
- ix78ESOrnjfX.exe (PID: 4740)
- ix78ESOrnjfX.exe (PID: 5776)
- ix78ESOrnjfX.exe (PID: 3816)
- cmd.exe (PID: 840)
- ix78ESOrnjfX.exe (PID: 2196)
- ix78ESOrnjfX.exe (PID: 3748)
- conhost.exe (PID: 3736)
- cmd.exe (PID: 4988)
- ix78ESOrnjfX.exe (PID: 5124)
- ix78ESOrnjfX.exe (PID: 4352)
- conhost.exe (PID: 2276)
- ix78ESOrnjfX.exe (PID: 3720)
- ix78ESOrnjfX.exe (PID: 3976)
- chrome.exe (PID: 3344)
- ix78ESOrnjfX.exe (PID: 2892)
- ix78ESOrnjfX.exe (PID: 3960)
- ix78ESOrnjfX.exe (PID: 2496)
- ix78ESOrnjfX.exe (PID: 904)
- ix78ESOrnjfX.exe (PID: 4044)
- ix78ESOrnjfX.exe (PID: 3188)
- ix78ESOrnjfX.exe (PID: 5080)
- ix78ESOrnjfX.exe (PID: 2976)
- ix78ESOrnjfX.exe (PID: 2916)
- ix78ESOrnjfX.exe (PID: 5232)
- ix78ESOrnjfX.exe (PID: 5040)
- ix78ESOrnjfX.exe (PID: 2912)
- ix78ESOrnjfX.exe (PID: 584)
- ix78ESOrnjfX.exe (PID: 2208)
- ix78ESOrnjfX.exe (PID: 2424)
- ix78ESOrnjfX.exe (PID: 4732)
- ix78ESOrnjfX.exe (PID: 3392)
- taskkill.exe (PID: 5696)
- 39945411238.exe (PID: 1756)
- ix78ESOrnjfX.exe (PID: 4156)
- ix78ESOrnjfX.exe (PID: 4420)
- ix78ESOrnjfX.exe (PID: 2864)
- ix78ESOrnjfX.exe (PID: 2296)
- chrome.exe (PID: 620)
- ix78ESOrnjfX.exe (PID: 2280)
- ix78ESOrnjfX.exe (PID: 5220)
- ix78ESOrnjfX.exe (PID: 4568)
- ix78ESOrnjfX.exe (PID: 2092)
- ix78ESOrnjfX.exe (PID: 3556)
- ix78ESOrnjfX.exe (PID: 4964)
- ix78ESOrnjfX.exe (PID: 3888)
- ix78ESOrnjfX.exe (PID: 4028)
- ix78ESOrnjfX.exe (PID: 1956)
- ix78ESOrnjfX.exe (PID: 4704)
- ix78ESOrnjfX.exe (PID: 4116)
- ix78ESOrnjfX.exe (PID: 3052)
- ix78ESOrnjfX.exe (PID: 5452)
- ix78ESOrnjfX.exe (PID: 3280)
- ix78ESOrnjfX.exe (PID: 1008)
- ix78ESOrnjfX.exe (PID: 3848)
- ix78ESOrnjfX.exe (PID: 5036)
- ix78ESOrnjfX.exe (PID: 4672)
- ix78ESOrnjfX.exe (PID: 3148)
- ix78ESOrnjfX.exe (PID: 2436)
- ix78ESOrnjfX.exe (PID: 5092)
- firefox.exe (PID: 2788)
- ix78ESOrnjfX.exe (PID: 4324)
- ix78ESOrnjfX.exe (PID: 3784)
- ix78ESOrnjfX.exe (PID: 2456)
- ix78ESOrnjfX.exe (PID: 5288)
- ix78ESOrnjfX.exe (PID: 1320)
- iexplore.exe (PID: 628)
- ix78ESOrnjfX.exe (PID: 4960)
- ix78ESOrnjfX.exe (PID: 4532)
- ix78ESOrnjfX.exe (PID: 5284)
- ix78ESOrnjfX.exe (PID: 4720)
- chrome.exe (PID: 2000)
- ix78ESOrnjfX.exe (PID: 2804)
- ix78ESOrnjfX.exe (PID: 2216)
- ix78ESOrnjfX.exe (PID: 6572)
- ix78ESOrnjfX.exe (PID: 5784)
- chrome.exe (PID: 3508)
- ix78ESOrnjfX.exe (PID: 5276)
- ix78ESOrnjfX.exe (PID: 5336)
- ix78ESOrnjfX.exe (PID: 7316)
- ix78ESOrnjfX.exe (PID: 7064)
- ix78ESOrnjfX.exe (PID: 7044)
- timeout.exe (PID: 5152)
- jfiag3g_gg.exe (PID: 6856)
- ix78ESOrnjfX.exe (PID: 7404)
- ix78ESOrnjfX.exe (PID: 6380)
- ix78ESOrnjfX.exe (PID: 7448)
- cmd.exe (PID: 6408)
- cmd.exe (PID: 8112)
- conhost.exe (PID: 6532)
- cmd.exe (PID: 8080)
- ix78ESOrnjfX.exe (PID: 7888)
- chrome.exe (PID: 7168)
- ix78ESOrnjfX.exe (PID: 7192)
- conhost.exe (PID: 6680)
- ix78ESOrnjfX.exe (PID: 7616)
- SearchFilterHost.exe (PID: 6228)
- jfiag3g_gg.exe (PID: 7280)
- ix78ESOrnjfX.exe (PID: 7356)
- firefox.exe (PID: 7644)
- conhost.exe (PID: 8128)
- ix78ESOrnjfX.exe (PID: 6600)
- chrome.exe (PID: 7104)
- chrome.exe (PID: 5248)
- ix78ESOrnjfX.exe (PID: 6768)
- ix78ESOrnjfX.exe (PID: 7384)
- ix78ESOrnjfX.exe (PID: 7628)
- ix78ESOrnjfX.exe (PID: 7136)
- ix78ESOrnjfX.exe (PID: 8148)
- ix78ESOrnjfX.exe (PID: 7284)
- ix78ESOrnjfX.exe (PID: 6676)
- ix78ESOrnjfX.exe (PID: 6892)
- ix78ESOrnjfX.exe (PID: 7228)
- ix78ESOrnjfX.exe (PID: 10100)
- ix78ESOrnjfX.exe (PID: 6692)
- ix78ESOrnjfX.exe (PID: 9236)
- ix78ESOrnjfX.exe (PID: 8264)
- ix78ESOrnjfX.exe (PID: 9832)
- ix78ESOrnjfX.exe (PID: 6552)
- ix78ESOrnjfX.exe (PID: 9760)
- ix78ESOrnjfX.exe (PID: 6352)
- taskkill.exe (PID: 9792)
- taskkill.exe (PID: 4668)
- ix78ESOrnjfX.exe (PID: 8464)
- ix78ESOrnjfX.exe (PID: 8068)
- ix78ESOrnjfX.exe (PID: 5492)
- ix78ESOrnjfX.exe (PID: 9052)
- ix78ESOrnjfX.exe (PID: 3488)
- ix78ESOrnjfX.exe (PID: 9536)
- ix78ESOrnjfX.exe (PID: 6376)
- 96356344407.exe (PID: 8488)
- ix78ESOrnjfX.exe (PID: 9892)
- ix78ESOrnjfX.exe (PID: 11720)
- ix78ESOrnjfX.exe (PID: 11272)
- ix78ESOrnjfX.exe (PID: 12104)
- ix78ESOrnjfX.exe (PID: 6664)
- conhost.exe (PID: 11240)
- ns99D6.tmp (PID: 7144)
- ix78ESOrnjfX.exe (PID: 8244)
- ix78ESOrnjfX.exe (PID: 6936)
- ix78ESOrnjfX.exe (PID: 10268)
- ix78ESOrnjfX.exe (PID: 7808)
- ix78ESOrnjfX.exe (PID: 11744)
- ix78ESOrnjfX.exe (PID: 8900)
- ix78ESOrnjfX.exe (PID: 11316)
- ix78ESOrnjfX.exe (PID: 8552)
- ix78ESOrnjfX.exe (PID: 8444)
- ix78ESOrnjfX.exe (PID: 6660)
- ix78ESOrnjfX.exe (PID: 7088)
- ix78ESOrnjfX.exe (PID: 8956)
- ix78ESOrnjfX.exe (PID: 10428)
- ix78ESOrnjfX.exe (PID: 8816)
- chrome.exe (PID: 9240)
- ix78ESOrnjfX.exe (PID: 11236)
- ix78ESOrnjfX.exe (PID: 11428)
- ix78ESOrnjfX.exe (PID: 8124)
- ix78ESOrnjfX.exe (PID: 11200)
- ix78ESOrnjfX.exe (PID: 4796)
- ix78ESOrnjfX.exe (PID: 11496)
- firefox.exe (PID: 8576)
- ix78ESOrnjfX.exe (PID: 7256)
- ix78ESOrnjfX.exe (PID: 3820)
- ix78ESOrnjfX.exe (PID: 8612)
- ix78ESOrnjfX.exe (PID: 9732)
- ix78ESOrnjfX.exe (PID: 9528)
- ix78ESOrnjfX.exe (PID: 7496)
- ix78ESOrnjfX.exe (PID: 6264)
- ix78ESOrnjfX.exe (PID: 10096)
- ix78ESOrnjfX.exe (PID: 8940)
- ix78ESOrnjfX.exe (PID: 9672)
- ix78ESOrnjfX.exe (PID: 6756)
- ix78ESOrnjfX.exe (PID: 10124)
- ix78ESOrnjfX.exe (PID: 10648)
- powershell.exe (PID: 9024)
- ix78ESOrnjfX.exe (PID: 8880)
- ix78ESOrnjfX.exe (PID: 5568)
- ix78ESOrnjfX.exe (PID: 7176)
- firefox.exe (PID: 10012)
- ix78ESOrnjfX.exe (PID: 11156)
- ix78ESOrnjfX.exe (PID: 8168)
- ix78ESOrnjfX.exe (PID: 8868)
- ix78ESOrnjfX.exe (PID: 9560)
- ix78ESOrnjfX.exe (PID: 10476)
- ix78ESOrnjfX.exe (PID: 9508)
- ix78ESOrnjfX.exe (PID: 11740)
- ix78ESOrnjfX.exe (PID: 8424)
- ix78ESOrnjfX.exe (PID: 6944)
- ix78ESOrnjfX.exe (PID: 11540)
- ix78ESOrnjfX.exe (PID: 6904)
- ix78ESOrnjfX.exe (PID: 8784)
- ix78ESOrnjfX.exe (PID: 8628)
- ix78ESOrnjfX.exe (PID: 7992)
- ix78ESOrnjfX.exe (PID: 11176)
- ix78ESOrnjfX.exe (PID: 2736)
- ix78ESOrnjfX.exe (PID: 9748)
- ix78ESOrnjfX.exe (PID: 9072)
- ix78ESOrnjfX.exe (PID: 10140)
- ix78ESOrnjfX.exe (PID: 9308)
- ix78ESOrnjfX.exe (PID: 7544)
- ix78ESOrnjfX.exe (PID: 10640)
- ix78ESOrnjfX.exe (PID: 10036)
- ix78ESOrnjfX.exe (PID: 7824)
- ix78ESOrnjfX.exe (PID: 12072)
- ix78ESOrnjfX.exe (PID: 10252)
- ix78ESOrnjfX.exe (PID: 11876)
- ix78ESOrnjfX.exe (PID: 11368)
- ix78ESOrnjfX.exe (PID: 8044)
- ix78ESOrnjfX.exe (PID: 6928)
- ix78ESOrnjfX.exe (PID: 8764)
- ix78ESOrnjfX.exe (PID: 9140)
- ix78ESOrnjfX.exe (PID: 3972)
- ix78ESOrnjfX.exe (PID: 11648)
- ix78ESOrnjfX.exe (PID: 12264)
- rUNdlL32.eXe (PID: 10836)
- ix78ESOrnjfX.exe (PID: 11536)
- ix78ESOrnjfX.exe (PID: 10044)
- ix78ESOrnjfX.exe (PID: 6564)
- ix78ESOrnjfX.exe (PID: 7360)
- ix78ESOrnjfX.exe (PID: 9736)
- ix78ESOrnjfX.exe (PID: 7928)
- ix78ESOrnjfX.exe (PID: 9840)
- ix78ESOrnjfX.exe (PID: 11816)
- ix78ESOrnjfX.exe (PID: 8076)
- ix78ESOrnjfX.exe (PID: 10756)
- ix78ESOrnjfX.exe (PID: 11308)
- chrome.exe (PID: 11384)
- ix78ESOrnjfX.exe (PID: 8748)
- ix78ESOrnjfX.exe (PID: 6784)
- ix78ESOrnjfX.exe (PID: 5372)
- ix78ESOrnjfX.exe (PID: 9620)
- ix78ESOrnjfX.exe (PID: 9500)
- ix78ESOrnjfX.exe (PID: 6804)
- ix78ESOrnjfX.exe (PID: 6356)
- ix78ESOrnjfX.exe (PID: 10608)
- ix78ESOrnjfX.exe (PID: 8140)
- ix78ESOrnjfX.exe (PID: 9844)
- ix78ESOrnjfX.exe (PID: 8996)
- ix78ESOrnjfX.exe (PID: 8408)
- ix78ESOrnjfX.exe (PID: 7392)
- ix78ESOrnjfX.exe (PID: 6732)
- ix78ESOrnjfX.exe (PID: 9336)
- ix78ESOrnjfX.exe (PID: 2644)
- ix78ESOrnjfX.exe (PID: 5836)
- ix78ESOrnjfX.exe (PID: 7516)
- ix78ESOrnjfX.exe (PID: 9564)
- ix78ESOrnjfX.exe (PID: 11464)
- ix78ESOrnjfX.exe (PID: 11780)
- ix78ESOrnjfX.exe (PID: 7660)
- ix78ESOrnjfX.exe (PID: 12012)
- ix78ESOrnjfX.exe (PID: 7056)
- ix78ESOrnjfX.exe (PID: 10440)
- ix78ESOrnjfX.exe (PID: 6444)
- ix78ESOrnjfX.exe (PID: 8476)
- ix78ESOrnjfX.exe (PID: 11100)
- ix78ESOrnjfX.exe (PID: 10360)
- ix78ESOrnjfX.exe (PID: 7456)
- ix78ESOrnjfX.exe (PID: 11784)
- ix78ESOrnjfX.exe (PID: 11692)
- ix78ESOrnjfX.exe (PID: 9396)
- ix78ESOrnjfX.exe (PID: 8468)
- ix78ESOrnjfX.exe (PID: 2628)
- ix78ESOrnjfX.exe (PID: 7676)
- chrome.exe (PID: 6764)
- ix78ESOrnjfX.exe (PID: 8704)
- ix78ESOrnjfX.exe (PID: 12032)
- ix78ESOrnjfX.exe (PID: 8976)
- ix78ESOrnjfX.exe (PID: 9860)
- ix78ESOrnjfX.exe (PID: 9708)
- chrome.exe (PID: 9652)
- ix78ESOrnjfX.exe (PID: 8888)
- firefox.exe (PID: 9656)
- ix78ESOrnjfX.exe (PID: 9332)
- ix78ESOrnjfX.exe (PID: 9020)
- ix78ESOrnjfX.exe (PID: 6640)
- ix78ESOrnjfX.exe (PID: 8540)
- ix78ESOrnjfX.exe (PID: 8760)
- ix78ESOrnjfX.exe (PID: 10500)
- ix78ESOrnjfX.exe (PID: 11656)
- ix78ESOrnjfX.exe (PID: 11160)
- chrome.exe (PID: 9116)
- ix78ESOrnjfX.exe (PID: 4784)
- ix78ESOrnjfX.exe (PID: 6628)
- chrome.exe (PID: 9952)
- ix78ESOrnjfX.exe (PID: 2100)
- ix78ESOrnjfX.exe (PID: 12128)
- ix78ESOrnjfX.exe (PID: 8520)
- ix78ESOrnjfX.exe (PID: 12156)
- ix78ESOrnjfX.exe (PID: 600)
- ix78ESOrnjfX.exe (PID: 10612)
- ix78ESOrnjfX.exe (PID: 9640)
- ix78ESOrnjfX.exe (PID: 10480)
- ix78ESOrnjfX.exe (PID: 5752)
- ix78ESOrnjfX.exe (PID: 10704)
- ix78ESOrnjfX.exe (PID: 10356)
- ix78ESOrnjfX.exe (PID: 9480)
- ix78ESOrnjfX.exe (PID: 11336)
- ix78ESOrnjfX.exe (PID: 1700)
- ix78ESOrnjfX.exe (PID: 12000)
- ix78ESOrnjfX.exe (PID: 10932)
- ix78ESOrnjfX.exe (PID: 9976)
- ix78ESOrnjfX.exe (PID: 8676)
- ix78ESOrnjfX.exe (PID: 10904)
- ix78ESOrnjfX.exe (PID: 10676)
- ix78ESOrnjfX.exe (PID: 4016)
- ix78ESOrnjfX.exe (PID: 9028)
- ix78ESOrnjfX.exe (PID: 6480)
- ix78ESOrnjfX.exe (PID: 8536)
- ix78ESOrnjfX.exe (PID: 11696)
- ix78ESOrnjfX.exe (PID: 10832)
- ix78ESOrnjfX.exe (PID: 4584)
- ix78ESOrnjfX.exe (PID: 7332)
- ix78ESOrnjfX.exe (PID: 10220)
- ix78ESOrnjfX.exe (PID: 3628)
- ix78ESOrnjfX.exe (PID: 11080)
- ix78ESOrnjfX.exe (PID: 10232)
- ix78ESOrnjfX.exe (PID: 11804)
- ix78ESOrnjfX.exe (PID: 7160)
- ix78ESOrnjfX.exe (PID: 10068)
- ix78ESOrnjfX.exe (PID: 6780)
- ix78ESOrnjfX.exe (PID: 9492)
- ix78ESOrnjfX.exe (PID: 10508)
- ix78ESOrnjfX.exe (PID: 11172)
- ix78ESOrnjfX.exe (PID: 5940)
- ix78ESOrnjfX.exe (PID: 11676)
- ix78ESOrnjfX.exe (PID: 11556)
- ix78ESOrnjfX.exe (PID: 1784)
- ix78ESOrnjfX.exe (PID: 7536)
- ix78ESOrnjfX.exe (PID: 9524)
- ix78ESOrnjfX.exe (PID: 8220)
- ix78ESOrnjfX.exe (PID: 11584)
- ix78ESOrnjfX.exe (PID: 6736)
- ix78ESOrnjfX.exe (PID: 8352)
- ix78ESOrnjfX.exe (PID: 10000)
- ix78ESOrnjfX.exe (PID: 6252)
- ix78ESOrnjfX.exe (PID: 10772)
- ix78ESOrnjfX.exe (PID: 6208)
- ix78ESOrnjfX.exe (PID: 11248)
- ix78ESOrnjfX.exe (PID: 8556)
- ix78ESOrnjfX.exe (PID: 12232)
- ix78ESOrnjfX.exe (PID: 9692)
- ix78ESOrnjfX.exe (PID: 10800)
- ix78ESOrnjfX.exe (PID: 6188)
- ix78ESOrnjfX.exe (PID: 11920)
- ix78ESOrnjfX.exe (PID: 11216)
- ix78ESOrnjfX.exe (PID: 11664)
- ix78ESOrnjfX.exe (PID: 10684)
- ix78ESOrnjfX.exe (PID: 2548)
- ix78ESOrnjfX.exe (PID: 11192)
- chrome.exe (PID: 12108)
- ix78ESOrnjfX.exe (PID: 10288)
- ix78ESOrnjfX.exe (PID: 8364)
- ix78ESOrnjfX.exe (PID: 11152)
- ix78ESOrnjfX.exe (PID: 1724)
- ix78ESOrnjfX.exe (PID: 5608)
- ix78ESOrnjfX.exe (PID: 8012)
- ix78ESOrnjfX.exe (PID: 7672)
- ix78ESOrnjfX.exe (PID: 8052)
- ix78ESOrnjfX.exe (PID: 10416)
- ix78ESOrnjfX.exe (PID: 7328)
- ix78ESOrnjfX.exe (PID: 12132)
- ix78ESOrnjfX.exe (PID: 11072)
- ix78ESOrnjfX.exe (PID: 9888)
- ix78ESOrnjfX.exe (PID: 10200)
- ix78ESOrnjfX.exe (PID: 12096)
- ix78ESOrnjfX.exe (PID: 8980)
- ix78ESOrnjfX.exe (PID: 9856)
- ix78ESOrnjfX.exe (PID: 8348)
- ix78ESOrnjfX.exe (PID: 10248)
- ix78ESOrnjfX.exe (PID: 9936)
- ix78ESOrnjfX.exe (PID: 10120)
- ix78ESOrnjfX.exe (PID: 4184)
- ix78ESOrnjfX.exe (PID: 12240)
- ix78ESOrnjfX.exe (PID: 9256)
- ix78ESOrnjfX.exe (PID: 8780)
- ix78ESOrnjfX.exe (PID: 6396)
- ix78ESOrnjfX.exe (PID: 10028)
- ix78ESOrnjfX.exe (PID: 7172)
- ix78ESOrnjfX.exe (PID: 9384)
- ix78ESOrnjfX.exe (PID: 8944)
- ix78ESOrnjfX.exe (PID: 9904)
- ix78ESOrnjfX.exe (PID: 11408)
- ix78ESOrnjfX.exe (PID: 12028)
- ix78ESOrnjfX.exe (PID: 10692)
- ix78ESOrnjfX.exe (PID: 6472)
- ix78ESOrnjfX.exe (PID: 6876)
- ix78ESOrnjfX.exe (PID: 9864)
- ix78ESOrnjfX.exe (PID: 9364)
- ix78ESOrnjfX.exe (PID: 10112)
- ix78ESOrnjfX.exe (PID: 10840)
- ix78ESOrnjfX.exe (PID: 12176)
- ix78ESOrnjfX.exe (PID: 9980)
- ix78ESOrnjfX.exe (PID: 5716)
- ix78ESOrnjfX.exe (PID: 7340)
- ix78ESOrnjfX.exe (PID: 12060)
- ix78ESOrnjfX.exe (PID: 8820)
- ix78ESOrnjfX.exe (PID: 10404)
- ix78ESOrnjfX.exe (PID: 6800)
- ix78ESOrnjfX.exe (PID: 5348)
- ix78ESOrnjfX.exe (PID: 10340)
- ix78ESOrnjfX.exe (PID: 9168)
- ix78ESOrnjfX.exe (PID: 10216)
- ix78ESOrnjfX.exe (PID: 8640)
- ix78ESOrnjfX.exe (PID: 7336)
- ix78ESOrnjfX.exe (PID: 12168)
- ix78ESOrnjfX.exe (PID: 4868)
- ix78ESOrnjfX.exe (PID: 8160)
- ix78ESOrnjfX.exe (PID: 8272)
- ix78ESOrnjfX.exe (PID: 6548)
- ix78ESOrnjfX.exe (PID: 6788)
- ix78ESOrnjfX.exe (PID: 11112)
- ix78ESOrnjfX.exe (PID: 11600)
- ix78ESOrnjfX.exe (PID: 8572)
- ix78ESOrnjfX.exe (PID: 8992)
- ix78ESOrnjfX.exe (PID: 11560)
- ix78ESOrnjfX.exe (PID: 9968)
- ix78ESOrnjfX.exe (PID: 3432)
- ix78ESOrnjfX.exe (PID: 8984)
- ix78ESOrnjfX.exe (PID: 6172)
- ix78ESOrnjfX.exe (PID: 9768)
- ix78ESOrnjfX.exe (PID: 10844)
- ix78ESOrnjfX.exe (PID: 9124)
- ix78ESOrnjfX.exe (PID: 7684)
- ix78ESOrnjfX.exe (PID: 6812)
- ix78ESOrnjfX.exe (PID: 7584)
- ix78ESOrnjfX.exe (PID: 3588)
- ix78ESOrnjfX.exe (PID: 9440)
- ix78ESOrnjfX.exe (PID: 6908)
- ix78ESOrnjfX.exe (PID: 9740)
- ix78ESOrnjfX.exe (PID: 9780)
- ix78ESOrnjfX.exe (PID: 10296)
- ix78ESOrnjfX.exe (PID: 10812)
- ix78ESOrnjfX.exe (PID: 8212)
- ix78ESOrnjfX.exe (PID: 8692)
- ix78ESOrnjfX.exe (PID: 6776)
- ix78ESOrnjfX.exe (PID: 9180)
- ix78ESOrnjfX.exe (PID: 2952)
- ix78ESOrnjfX.exe (PID: 6952)
- ix78ESOrnjfX.exe (PID: 6964)
- ix78ESOrnjfX.exe (PID: 8708)
- ix78ESOrnjfX.exe (PID: 7076)
- ix78ESOrnjfX.exe (PID: 10304)
- ix78ESOrnjfX.exe (PID: 8668)
- ix78ESOrnjfX.exe (PID: 4524)
- ix78ESOrnjfX.exe (PID: 10444)
- ix78ESOrnjfX.exe (PID: 5812)
- ix78ESOrnjfX.exe (PID: 10780)
- ix78ESOrnjfX.exe (PID: 11620)
- ix78ESOrnjfX.exe (PID: 11276)
- ix78ESOrnjfX.exe (PID: 8436)
- ix78ESOrnjfX.exe (PID: 9928)
- ix78ESOrnjfX.exe (PID: 8884)
- ix78ESOrnjfX.exe (PID: 8580)
- ix78ESOrnjfX.exe (PID: 11136)
- ix78ESOrnjfX.exe (PID: 6484)
- ix78ESOrnjfX.exe (PID: 10568)
- ix78ESOrnjfX.exe (PID: 6152)
- ix78ESOrnjfX.exe (PID: 10336)
- ix78ESOrnjfX.exe (PID: 9220)
- ix78ESOrnjfX.exe (PID: 11508)
- ix78ESOrnjfX.exe (PID: 6608)
- ix78ESOrnjfX.exe (PID: 8836)
- ix78ESOrnjfX.exe (PID: 6424)
- ix78ESOrnjfX.exe (PID: 2760)
- ix78ESOrnjfX.exe (PID: 11768)
- ix78ESOrnjfX.exe (PID: 9812)
- cmd.exe (PID: 4576)
- ix78ESOrnjfX.exe (PID: 7452)
- conhost.exe (PID: 3728)
- ix78ESOrnjfX.exe (PID: 8656)
- ix78ESOrnjfX.exe (PID: 12144)
- ix78ESOrnjfX.exe (PID: 10740)
- ix78ESOrnjfX.exe (PID: 12088)
- ix78ESOrnjfX.exe (PID: 11400)
- ix78ESOrnjfX.exe (PID: 10876)
- ix78ESOrnjfX.exe (PID: 8832)
- ix78ESOrnjfX.exe (PID: 7700)
- ix78ESOrnjfX.exe (PID: 6648)
- ix78ESOrnjfX.exe (PID: 10004)
- ix78ESOrnjfX.exe (PID: 7412)
- ix78ESOrnjfX.exe (PID: 6536)
- ix78ESOrnjfX.exe (PID: 11040)
- ix78ESOrnjfX.exe (PID: 7548)
- ix78ESOrnjfX.exe (PID: 10160)
- ix78ESOrnjfX.exe (PID: 4560)
- ix78ESOrnjfX.exe (PID: 10816)
- ix78ESOrnjfX.exe (PID: 9248)
- ix78ESOrnjfX.exe (PID: 7252)
- ix78ESOrnjfX.exe (PID: 3700)
- ix78ESOrnjfX.exe (PID: 12092)
- ebook.exe (PID: 11388)
- ix78ESOrnjfX.exe (PID: 11204)
- ix78ESOrnjfX.exe (PID: 3768)
- ix78ESOrnjfX.exe (PID: 8008)
- ix78ESOrnjfX.exe (PID: 10376)
- ix78ESOrnjfX.exe (PID: 11000)
- ix78ESOrnjfX.exe (PID: 7500)
- ix78ESOrnjfX.exe (PID: 9228)
- ix78ESOrnjfX.exe (PID: 8040)
- ix78ESOrnjfX.exe (PID: 11412)
- ix78ESOrnjfX.exe (PID: 7260)
- ix78ESOrnjfX.exe (PID: 11088)
- ix78ESOrnjfX.exe (PID: 2128)
- ix78ESOrnjfX.exe (PID: 9992)
- ix78ESOrnjfX.exe (PID: 12224)
- ix78ESOrnjfX.exe (PID: 11608)
- ix78ESOrnjfX.exe (PID: 6896)
- ix78ESOrnjfX.exe (PID: 7716)
- ix78ESOrnjfX.exe (PID: 10696)
- ix78ESOrnjfX.exe (PID: 6456)
- ix78ESOrnjfX.exe (PID: 11064)
- ix78ESOrnjfX.exe (PID: 6232)
- ix78ESOrnjfX.exe (PID: 10776)
- ix78ESOrnjfX.exe (PID: 11660)
- ix78ESOrnjfX.exe (PID: 7796)
- ix78ESOrnjfX.exe (PID: 7560)
- ix78ESOrnjfX.exe (PID: 11552)
- ix78ESOrnjfX.exe (PID: 7008)
- ix78ESOrnjfX.exe (PID: 5620)
- ix78ESOrnjfX.exe (PID: 7748)
- ix78ESOrnjfX.exe (PID: 4460)
- ix78ESOrnjfX.exe (PID: 4244)
- ix78ESOrnjfX.exe (PID: 11364)
- ix78ESOrnjfX.exe (PID: 5892)
- ix78ESOrnjfX.exe (PID: 10064)
- ix78ESOrnjfX.exe (PID: 8368)
- ix78ESOrnjfX.exe (PID: 7208)
- ix78ESOrnjfX.exe (PID: 10788)
- ix78ESOrnjfX.exe (PID: 5704)
- ix78ESOrnjfX.exe (PID: 9144)
- ix78ESOrnjfX.exe (PID: 10956)
- ix78ESOrnjfX.exe (PID: 12152)
- ix78ESOrnjfX.exe (PID: 9376)
- ix78ESOrnjfX.exe (PID: 10400)
- ix78ESOrnjfX.exe (PID: 8208)
- ix78ESOrnjfX.exe (PID: 5136)
- ix78ESOrnjfX.exe (PID: 10256)
- ix78ESOrnjfX.exe (PID: 10168)
- ix78ESOrnjfX.exe (PID: 11944)
- ix78ESOrnjfX.exe (PID: 3952)
- ix78ESOrnjfX.exe (PID: 7224)
- ix78ESOrnjfX.exe (PID: 12068)
- ix78ESOrnjfX.exe (PID: 3060)
- ix78ESOrnjfX.exe (PID: 7164)
- ix78ESOrnjfX.exe (PID: 9152)
- ix78ESOrnjfX.exe (PID: 3156)
- ix78ESOrnjfX.exe (PID: 4516)
- ix78ESOrnjfX.exe (PID: 8720)
- ix78ESOrnjfX.exe (PID: 10668)
- ix78ESOrnjfX.exe (PID: 560)
- ix78ESOrnjfX.exe (PID: 8988)
- ix78ESOrnjfX.exe (PID: 5052)
- ix78ESOrnjfX.exe (PID: 8388)
- ix78ESOrnjfX.exe (PID: 2408)
- ix78ESOrnjfX.exe (PID: 3192)
- ix78ESOrnjfX.exe (PID: 4968)
- ix78ESOrnjfX.exe (PID: 10092)
- ix78ESOrnjfX.exe (PID: 2704)
- ix78ESOrnjfX.exe (PID: 11028)
- ix78ESOrnjfX.exe (PID: 4812)
- ix78ESOrnjfX.exe (PID: 7288)
- ix78ESOrnjfX.exe (PID: 3648)
- ix78ESOrnjfX.exe (PID: 11188)
- ix78ESOrnjfX.exe (PID: 4496)
- ix78ESOrnjfX.exe (PID: 7820)
- ix78ESOrnjfX.exe (PID: 5564)
- ix78ESOrnjfX.exe (PID: 6864)
- ix78ESOrnjfX.exe (PID: 11704)
- ix78ESOrnjfX.exe (PID: 6048)
- ix78ESOrnjfX.exe (PID: 2520)
- ix78ESOrnjfX.exe (PID: 6984)
- ix78ESOrnjfX.exe (PID: 11580)
- ix78ESOrnjfX.exe (PID: 7268)
- ix78ESOrnjfX.exe (PID: 8796)
- ix78ESOrnjfX.exe (PID: 7912)
- ix78ESOrnjfX.exe (PID: 1416)
- ix78ESOrnjfX.exe (PID: 7028)
- ix78ESOrnjfX.exe (PID: 2984)
- ix78ESOrnjfX.exe (PID: 3656)
- ix78ESOrnjfX.exe (PID: 7740)
- ix78ESOrnjfX.exe (PID: 4772)
- ix78ESOrnjfX.exe (PID: 7476)
- ix78ESOrnjfX.exe (PID: 10804)
- ix78ESOrnjfX.exe (PID: 11864)
- ix78ESOrnjfX.exe (PID: 11052)
- ix78ESOrnjfX.exe (PID: 7876)
- ix78ESOrnjfX.exe (PID: 5972)
- ix78ESOrnjfX.exe (PID: 8752)
- conhost.exe (PID: 4136)
- cmd.exe (PID: 8952)
- ix78ESOrnjfX.exe (PID: 12244)
- ix78ESOrnjfX.exe (PID: 7484)
- ix78ESOrnjfX.exe (PID: 11228)
- ix78ESOrnjfX.exe (PID: 10264)
- ix78ESOrnjfX.exe (PID: 12216)
- ix78ESOrnjfX.exe (PID: 5456)
- ix78ESOrnjfX.exe (PID: 5904)
- ix78ESOrnjfX.exe (PID: 5008)
- ix78ESOrnjfX.exe (PID: 12260)
- ix78ESOrnjfX.exe (PID: 11928)
- ix78ESOrnjfX.exe (PID: 5688)
- ix78ESOrnjfX.exe (PID: 3332)
- ix78ESOrnjfX.exe (PID: 11180)
- ix78ESOrnjfX.exe (PID: 3420)
- ix78ESOrnjfX.exe (PID: 1232)
- ix78ESOrnjfX.exe (PID: 12184)
- ix78ESOrnjfX.exe (PID: 8036)
- ix78ESOrnjfX.exe (PID: 7200)
- ix78ESOrnjfX.exe (PID: 4300)
- ix78ESOrnjfX.exe (PID: 8848)
- ix78ESOrnjfX.exe (PID: 7508)
- ix78ESOrnjfX.exe (PID: 8496)
- ix78ESOrnjfX.exe (PID: 6940)
- ix78ESOrnjfX.exe (PID: 9944)
- taskkill.exe (PID: 11924)
- ix78ESOrnjfX.exe (PID: 3788)
- ix78ESOrnjfX.exe (PID: 2784)
- ix78ESOrnjfX.exe (PID: 4736)
- ix78ESOrnjfX.exe (PID: 2512)
- ix78ESOrnjfX.exe (PID: 8600)
- ix78ESOrnjfX.exe (PID: 6332)
- ix78ESOrnjfX.exe (PID: 5068)
- chrome.exe (PID: 7688)
- ix78ESOrnjfX.exe (PID: 5820)
- ix78ESOrnjfX.exe (PID: 11764)
- ix78ESOrnjfX.exe (PID: 7772)
- ix78ESOrnjfX.exe (PID: 8524)
- ix78ESOrnjfX.exe (PID: 3016)
- cmd.exe (PID: 2444)
- ix78ESOrnjfX.exe (PID: 8584)
- conhost.exe (PID: 9148)
- ix78ESOrnjfX.exe (PID: 556)
- ix78ESOrnjfX.exe (PID: 9680)
- ix78ESOrnjfX.exe (PID: 10820)
- ix78ESOrnjfX.exe (PID: 7916)
- ix78ESOrnjfX.exe (PID: 11440)
- ix78ESOrnjfX.exe (PID: 10908)
- ix78ESOrnjfX.exe (PID: 6968)
- ix78ESOrnjfX.exe (PID: 7640)
- ix78ESOrnjfX.exe (PID: 6268)
- ix78ESOrnjfX.exe (PID: 1284)
- ix78ESOrnjfX.exe (PID: 11196)
- ix78ESOrnjfX.exe (PID: 4112)
- ix78ESOrnjfX.exe (PID: 12040)
- ix78ESOrnjfX.exe (PID: 8632)
- ix78ESOrnjfX.exe (PID: 5664)
- ix78ESOrnjfX.exe (PID: 5360)
- ix78ESOrnjfX.exe (PID: 10024)
- ix78ESOrnjfX.exe (PID: 10192)
- ix78ESOrnjfX.exe (PID: 2756)
- ix78ESOrnjfX.exe (PID: 10924)
- ix78ESOrnjfX.exe (PID: 2284)
- ix78ESOrnjfX.exe (PID: 12084)
- ix78ESOrnjfX.exe (PID: 8804)
- ix78ESOrnjfX.exe (PID: 10460)
- ix78ESOrnjfX.exe (PID: 5440)
- 0001.exe (PID: 9408)
- ix78ESOrnjfX.exe (PID: 3572)
- ix78ESOrnjfX.exe (PID: 9356)
- ix78ESOrnjfX.exe (PID: 5644)
- ix78ESOrnjfX.exe (PID: 11320)
- ix78ESOrnjfX.exe (PID: 11892)
- cmd.exe (PID: 10132)
- conhost.exe (PID: 4996)
- ix78ESOrnjfX.exe (PID: 8416)
- ix78ESOrnjfX.exe (PID: 6200)
- ix78ESOrnjfX.exe (PID: 10448)
- ix78ESOrnjfX.exe (PID: 9632)
- ix78ESOrnjfX.exe (PID: 8056)
- ix78ESOrnjfX.exe (PID: 9516)
- ix78ESOrnjfX.exe (PID: 4604)
- ix78ESOrnjfX.exe (PID: 11324)
- ix78ESOrnjfX.exe (PID: 7140)
- ix78ESOrnjfX.exe (PID: 6496)
- ix78ESOrnjfX.exe (PID: 9436)
- ix78ESOrnjfX.exe (PID: 5420)
- ix78ESOrnjfX.exe (PID: 11116)
- ix78ESOrnjfX.exe (PID: 6744)
- ix78ESOrnjfX.exe (PID: 9496)
- ix78ESOrnjfX.exe (PID: 11036)
- ix78ESOrnjfX.exe (PID: 8856)
- ix78ESOrnjfX.exe (PID: 11952)
- ix78ESOrnjfX.exe (PID: 7724)
- ix78ESOrnjfX.exe (PID: 1000)
- 001.exe (PID: 4484)
- ix78ESOrnjfX.exe (PID: 2460)
- ix78ESOrnjfX.exe (PID: 8172)
- ix78ESOrnjfX.exe (PID: 5856)
- ix78ESOrnjfX.exe (PID: 10852)
- ix78ESOrnjfX.exe (PID: 10872)
- ix78ESOrnjfX.exe (PID: 3440)
- ix78ESOrnjfX.exe (PID: 7432)
- ix78ESOrnjfX.exe (PID: 8440)
- ix78ESOrnjfX.exe (PID: 9476)
- ix78ESOrnjfX.exe (PID: 9204)
- ns8E69.tmp (PID: 11860)
- ix78ESOrnjfX.exe (PID: 6436)
- ix78ESOrnjfX.exe (PID: 9048)
- ix78ESOrnjfX.exe (PID: 3632)
- ix78ESOrnjfX.exe (PID: 2592)
- ix78ESOrnjfX.exe (PID: 12016)
- ix78ESOrnjfX.exe (PID: 3688)
- ix78ESOrnjfX.exe (PID: 3780)
- ix78ESOrnjfX.exe (PID: 8472)
- ix78ESOrnjfX.exe (PID: 3516)
- conhost.exe (PID: 4132)
- ix78ESOrnjfX.exe (PID: 6320)
- ix78ESOrnjfX.exe (PID: 5680)
- ix78ESOrnjfX.exe (PID: 2816)
- ix78ESOrnjfX.exe (PID: 3740)
- ix78ESOrnjfX.exe (PID: 9572)
- ix78ESOrnjfX.exe (PID: 7844)
- ix78ESOrnjfX.exe (PID: 10180)
- ix78ESOrnjfX.exe (PID: 6212)
- ix78ESOrnjfX.exe (PID: 948)
- ix78ESOrnjfX.exe (PID: 6312)
- ix78ESOrnjfX.exe (PID: 9880)
- ix78ESOrnjfX.exe (PID: 10144)
- ix78ESOrnjfX.exe (PID: 11932)
- ix78ESOrnjfX.exe (PID: 9716)
- ix78ESOrnjfX.exe (PID: 7696)
- ix78ESOrnjfX.exe (PID: 10072)
- ix78ESOrnjfX.exe (PID: 3276)
- ix78ESOrnjfX.exe (PID: 11668)
- ix78ESOrnjfX.exe (PID: 10408)
- ix78ESOrnjfX.exe (PID: 3184)
- ix78ESOrnjfX.exe (PID: 11700)
- ix78ESOrnjfX.exe (PID: 6184)
- ix78ESOrnjfX.exe (PID: 7576)
- ix78ESOrnjfX.exe (PID: 11652)
- ix78ESOrnjfX.exe (PID: 7180)
- ix78ESOrnjfX.exe (PID: 6292)
- ix78ESOrnjfX.exe (PID: 12268)
- ix78ESOrnjfX.exe (PID: 3396)
- ix78ESOrnjfX.exe (PID: 12192)
- ix78ESOrnjfX.exe (PID: 5396)
- ix78ESOrnjfX.exe (PID: 11856)
- lighteningplayer-cache-gen.exe (PID: 12188)
- ix78ESOrnjfX.exe (PID: 10672)
- ix78ESOrnjfX.exe (PID: 10244)
- ix78ESOrnjfX.exe (PID: 3224)
- ix78ESOrnjfX.exe (PID: 8728)
- ix78ESOrnjfX.exe (PID: 6748)
- ix78ESOrnjfX.exe (PID: 7400)
- ix78ESOrnjfX.exe (PID: 5168)
- ix78ESOrnjfX.exe (PID: 11632)
- ix78ESOrnjfX.exe (PID: 12200)
- ix78ESOrnjfX.exe (PID: 932)
- ix78ESOrnjfX.exe (PID: 7264)
- ix78ESOrnjfX.exe (PID: 9924)
- ix78ESOrnjfX.exe (PID: 7904)
- rundll32.exe (PID: 3920)
- ix78ESOrnjfX.exe (PID: 1900)
- ix78ESOrnjfX.exe (PID: 10916)
- ix78ESOrnjfX.exe (PID: 4308)
- ix78ESOrnjfX.exe (PID: 11964)
- ix78ESOrnjfX.exe (PID: 3940)
- ix78ESOrnjfX.exe (PID: 9588)
- ix78ESOrnjfX.exe (PID: 2948)
- ix78ESOrnjfX.exe (PID: 11360)
- ix78ESOrnjfX.exe (PID: 7704)
- ix78ESOrnjfX.exe (PID: 9292)
- ix78ESOrnjfX.exe (PID: 6772)
- ix78ESOrnjfX.exe (PID: 5912)
- ix78ESOrnjfX.exe (PID: 1716)
- ix78ESOrnjfX.exe (PID: 9876)
- ix78ESOrnjfX.exe (PID: 7788)
- ix78ESOrnjfX.exe (PID: 7120)
- ix78ESOrnjfX.exe (PID: 9576)
- ix78ESOrnjfX.exe (PID: 10332)
- ix78ESOrnjfX.exe (PID: 11512)
- ix78ESOrnjfX.exe (PID: 12004)
- ix78ESOrnjfX.exe (PID: 7092)
- ix78ESOrnjfX.exe (PID: 6428)
- ix78ESOrnjfX.exe (PID: 11628)
- ix78ESOrnjfX.exe (PID: 8188)
- ix78ESOrnjfX.exe (PID: 5032)
- ix78ESOrnjfX.exe (PID: 7624)
- ix78ESOrnjfX.exe (PID: 8300)
- ix78ESOrnjfX.exe (PID: 6720)
- ix78ESOrnjfX.exe (PID: 10628)
- ix78ESOrnjfX.exe (PID: 11480)
- ix78ESOrnjfX.exe (PID: 9304)
- ix78ESOrnjfX.exe (PID: 9532)
- ix78ESOrnjfX.exe (PID: 8412)
- ix78ESOrnjfX.exe (PID: 7896)
- ix78ESOrnjfX.exe (PID: 1884)
- ix78ESOrnjfX.exe (PID: 11372)
- ix78ESOrnjfX.exe (PID: 5344)
- ix78ESOrnjfX.exe (PID: 8260)
- ix78ESOrnjfX.exe (PID: 9016)
- ix78ESOrnjfX.exe (PID: 4520)
- ix78ESOrnjfX.exe (PID: 10204)
- ix78ESOrnjfX.exe (PID: 8892)
- ix78ESOrnjfX.exe (PID: 7612)
- ix78ESOrnjfX.exe (PID: 6652)
- ix78ESOrnjfX.exe (PID: 8256)
- ix78ESOrnjfX.exe (PID: 4192)
- ix78ESOrnjfX.exe (PID: 2900)
- ix78ESOrnjfX.exe (PID: 3252)
- ix78ESOrnjfX.exe (PID: 9036)
- ix78ESOrnjfX.exe (PID: 4696)
- ix78ESOrnjfX.exe (PID: 7964)
- ix78ESOrnjfX.exe (PID: 10372)
- ix78ESOrnjfX.exe (PID: 5292)
- ix78ESOrnjfX.exe (PID: 8544)
- ix78ESOrnjfX.exe (PID: 7568)
- ix78ESOrnjfX.exe (PID: 1728)
- ix78ESOrnjfX.exe (PID: 6976)
- ix78ESOrnjfX.exe (PID: 8104)
- ix78ESOrnjfX.exe (PID: 5772)
- ix78ESOrnjfX.exe (PID: 5744)
- ix78ESOrnjfX.exe (PID: 4648)
- ix78ESOrnjfX.exe (PID: 12256)
- ix78ESOrnjfX.exe (PID: 2584)
- ix78ESOrnjfX.exe (PID: 11380)
- ix78ESOrnjfX.exe (PID: 6820)
- ix78ESOrnjfX.exe (PID: 11076)
- ix78ESOrnjfX.exe (PID: 4240)
- ix78ESOrnjfX.exe (PID: 7212)
- ix78ESOrnjfX.exe (PID: 5968)
- ix78ESOrnjfX.exe (PID: 11708)
- ix78ESOrnjfX.exe (PID: 11900)
- ix78ESOrnjfX.exe (PID: 2940)
- ix78ESOrnjfX.exe (PID: 11096)
- ix78ESOrnjfX.exe (PID: 10284)
- ix78ESOrnjfX.exe (PID: 7736)
- ix78ESOrnjfX.exe (PID: 3964)
- ix78ESOrnjfX.exe (PID: 5872)
- ix78ESOrnjfX.exe (PID: 4388)
- ix78ESOrnjfX.exe (PID: 6912)
- ix78ESOrnjfX.exe (PID: 5640)
- ix78ESOrnjfX.exe (PID: 10892)
- ix78ESOrnjfX.exe (PID: 5956)
- cmd.exe (PID: 10048)
- ix78ESOrnjfX.exe (PID: 6388)
- conhost.exe (PID: 11048)
- ix78ESOrnjfX.exe (PID: 6688)
- ix78ESOrnjfX.exe (PID: 10644)
- ix78ESOrnjfX.exe (PID: 4128)
- ix78ESOrnjfX.exe (PID: 12196)
- ix78ESOrnjfX.exe (PID: 10224)
- ix78ESOrnjfX.exe (PID: 6840)
- ix78ESOrnjfX.exe (PID: 4508)
- ix78ESOrnjfX.exe (PID: 8788)
- ix78ESOrnjfX.exe (PID: 12120)
- ix78ESOrnjfX.exe (PID: 4024)
- ix78ESOrnjfX.exe (PID: 324)
- ix78ESOrnjfX.exe (PID: 3092)
- ix78ESOrnjfX.exe (PID: 8844)
- ix78ESOrnjfX.exe (PID: 10748)
- ix78ESOrnjfX.exe (PID: 2188)
- ix78ESOrnjfX.exe (PID: 1880)
- ix78ESOrnjfX.exe (PID: 7036)
- ix78ESOrnjfX.exe (PID: 3096)
- ix78ESOrnjfX.exe (PID: 11528)
- ix78ESOrnjfX.exe (PID: 5252)
- ix78ESOrnjfX.exe (PID: 3088)
- cmd.exe (PID: 6588)
- ix78ESOrnjfX.exe (PID: 5072)
- ix78ESOrnjfX.exe (PID: 3104)
- findstr.exe (PID: 7492)
- ix78ESOrnjfX.exe (PID: 1380)
- ix78ESOrnjfX.exe (PID: 8652)
- ix78ESOrnjfX.exe (PID: 7588)
- ix78ESOrnjfX.exe (PID: 5260)
- ix78ESOrnjfX.exe (PID: 6612)
- ix78ESOrnjfX.exe (PID: 9108)
- ix78ESOrnjfX.exe (PID: 9076)
- ix78ESOrnjfX.exe (PID: 11148)
- ix78ESOrnjfX.exe (PID: 1096)
- ix78ESOrnjfX.exe (PID: 5520)
- Nel.exe.com (PID: 6900)
- ix78ESOrnjfX.exe (PID: 11904)
- PING.EXE (PID: 10040)
- ix78ESOrnjfX.exe (PID: 8312)
- ix78ESOrnjfX.exe (PID: 2044)
- ix78ESOrnjfX.exe (PID: 9432)
- ix78ESOrnjfX.exe (PID: 2740)
- ix78ESOrnjfX.exe (PID: 976)
- ix78ESOrnjfX.exe (PID: 5056)
- ix78ESOrnjfX.exe (PID: 12220)
- ix78ESOrnjfX.exe (PID: 2272)
- ix78ESOrnjfX.exe (PID: 10712)
- ix78ESOrnjfX.exe (PID: 4008)
- ix78ESOrnjfX.exe (PID: 7024)
- ix78ESOrnjfX.exe (PID: 9252)
- ix78ESOrnjfX.exe (PID: 3660)
- ix78ESOrnjfX.exe (PID: 5804)
- ix78ESOrnjfX.exe (PID: 7388)
- ix78ESOrnjfX.exe (PID: 10828)
- ix78ESOrnjfX.exe (PID: 8688)
- ix78ESOrnjfX.exe (PID: 9196)
- ix78ESOrnjfX.exe (PID: 7464)
- ix78ESOrnjfX.exe (PID: 11260)
- cmd.exe (PID: 7936)
- conhost.exe (PID: 9972)
- ix78ESOrnjfX.exe (PID: 11024)
- Nel.exe.com (PID: 3212)
- ix78ESOrnjfX.exe (PID: 7060)
- ix78ESOrnjfX.exe (PID: 4392)
- ix78ESOrnjfX.exe (PID: 5660)
- ix78ESOrnjfX.exe (PID: 11212)
- ix78ESOrnjfX.exe (PID: 12656)
- ix78ESOrnjfX.exe (PID: 12488)
- ix78ESOrnjfX.exe (PID: 13608)
- ix78ESOrnjfX.exe (PID: 12832)
- ix78ESOrnjfX.exe (PID: 13044)
- ix78ESOrnjfX.exe (PID: 14072)
- ix78ESOrnjfX.exe (PID: 12292)
- ix78ESOrnjfX.exe (PID: 12680)
- ix78ESOrnjfX.exe (PID: 13032)
- ix78ESOrnjfX.exe (PID: 13196)
- ix78ESOrnjfX.exe (PID: 2432)
- ix78ESOrnjfX.exe (PID: 14240)
- RUNDLL32.EXE (PID: 12752)
- ix78ESOrnjfX.exe (PID: 12376)
- ix78ESOrnjfX.exe (PID: 14060)
- ix78ESOrnjfX.exe (PID: 14280)
- ix78ESOrnjfX.exe (PID: 12512)
- ntvdm.exe (PID: 12572)
- ix78ESOrnjfX.exe (PID: 13540)
- ix78ESOrnjfX.exe (PID: 13680)
- ix78ESOrnjfX.exe (PID: 13768)
- ix78ESOrnjfX.exe (PID: 13932)
- ix78ESOrnjfX.exe (PID: 13744)
- ix78ESOrnjfX.exe (PID: 13924)
- ix78ESOrnjfX.exe (PID: 12780)
- ix78ESOrnjfX.exe (PID: 12924)
- ix78ESOrnjfX.exe (PID: 13208)
- ix78ESOrnjfX.exe (PID: 13580)
- ix78ESOrnjfX.exe (PID: 12668)
- ix78ESOrnjfX.exe (PID: 12828)
- ix78ESOrnjfX.exe (PID: 12984)
- ix78ESOrnjfX.exe (PID: 14020)
- ix78ESOrnjfX.exe (PID: 14224)
- ix78ESOrnjfX.exe (PID: 12368)
- ix78ESOrnjfX.exe (PID: 12532)
- ix78ESOrnjfX.exe (PID: 13696)
- ix78ESOrnjfX.exe (PID: 13824)
- ix78ESOrnjfX.exe (PID: 12416)
- ix78ESOrnjfX.exe (PID: 13272)
- ix78ESOrnjfX.exe (PID: 13400)
- ix78ESOrnjfX.exe (PID: 13500)
- ix78ESOrnjfX.exe (PID: 14204)
- ix78ESOrnjfX.exe (PID: 12300)
- ix78ESOrnjfX.exe (PID: 12372)
- ix78ESOrnjfX.exe (PID: 12516)
- ix78ESOrnjfX.exe (PID: 13964)
- ix78ESOrnjfX.exe (PID: 14024)
- ix78ESOrnjfX.exe (PID: 12988)
- ix78ESOrnjfX.exe (PID: 13432)
- ix78ESOrnjfX.exe (PID: 13560)
- ix78ESOrnjfX.exe (PID: 13752)
- ix78ESOrnjfX.exe (PID: 5888)
- ix78ESOrnjfX.exe (PID: 12648)
- ix78ESOrnjfX.exe (PID: 12844)
- ix78ESOrnjfX.exe (PID: 13180)
- ix78ESOrnjfX.exe (PID: 13280)
- ix78ESOrnjfX.exe (PID: 14172)
- ix78ESOrnjfX.exe (PID: 12644)
- ix78ESOrnjfX.exe (PID: 14296)
- ix78ESOrnjfX.exe (PID: 12584)
- ix78ESOrnjfX.exe (PID: 12360)
- cmd.exe (PID: 12932)
- ix78ESOrnjfX.exe (PID: 14008)
- ix78ESOrnjfX.exe (PID: 13884)
- ix78ESOrnjfX.exe (PID: 13740)
- ix78ESOrnjfX.exe (PID: 12480)
- ix78ESOrnjfX.exe (PID: 12316)
- ix78ESOrnjfX.exe (PID: 14192)
- ix78ESOrnjfX.exe (PID: 13060)
- ix78ESOrnjfX.exe (PID: 12960)
- conhost.exe (PID: 568)
- ix78ESOrnjfX.exe (PID: 13148)
- ix78ESOrnjfX.exe (PID: 3132)
- ix78ESOrnjfX.exe (PID: 14040)
- ix78ESOrnjfX.exe (PID: 12856)
- ix78ESOrnjfX.exe (PID: 13256)
- ix78ESOrnjfX.exe (PID: 13636)
- ix78ESOrnjfX.exe (PID: 13384)
- ix78ESOrnjfX.exe (PID: 12320)
- ix78ESOrnjfX.exe (PID: 14080)
- ix78ESOrnjfX.exe (PID: 13120)
- ix78ESOrnjfX.exe (PID: 12768)
- ix78ESOrnjfX.exe (PID: 12916)
- ix78ESOrnjfX.exe (PID: 13528)
- ix78ESOrnjfX.exe (PID: 13284)
- ix78ESOrnjfX.exe (PID: 14056)
- ix78ESOrnjfX.exe (PID: 14308)
- ix78ESOrnjfX.exe (PID: 12524)
- ix78ESOrnjfX.exe (PID: 13852)
- ix78ESOrnjfX.exe (PID: 13424)
- ix78ESOrnjfX.exe (PID: 13192)
- ix78ESOrnjfX.exe (PID: 12880)
- ix78ESOrnjfX.exe (PID: 13356)
- ix78ESOrnjfX.exe (PID: 13520)
- md1_1eaf.exe (PID: 13620)
- ix78ESOrnjfX.exe (PID: 14316)
- ix78ESOrnjfX.exe (PID: 13224)
- ix78ESOrnjfX.exe (PID: 12604)
- ix78ESOrnjfX.exe (PID: 13360)
- ix78ESOrnjfX.exe (PID: 13784)
- ix78ESOrnjfX.exe (PID: 12444)
- ix78ESOrnjfX.exe (PID: 13172)
- ix78ESOrnjfX.exe (PID: 13836)
- ix78ESOrnjfX.exe (PID: 14132)
- ix78ESOrnjfX.exe (PID: 12380)
- ix78ESOrnjfX.exe (PID: 13084)
- ix78ESOrnjfX.exe (PID: 13388)
- ix78ESOrnjfX.exe (PID: 12504)
- ix78ESOrnjfX.exe (PID: 14120)
- ix78ESOrnjfX.exe (PID: 12896)
- ix78ESOrnjfX.exe (PID: 13108)
- WerFault.exe (PID: 13204)
- ix78ESOrnjfX.exe (PID: 13368)
- ix78ESOrnjfX.exe (PID: 13804)
- ix78ESOrnjfX.exe (PID: 12764)
- ix78ESOrnjfX.exe (PID: 13600)
- ix78ESOrnjfX.exe (PID: 8516)
- ix78ESOrnjfX.exe (PID: 12948)
- ix78ESOrnjfX.exe (PID: 10952)
- ix78ESOrnjfX.exe (PID: 13316)
- ntvdm.exe (PID: 14292)
- conhost.exe (PID: 12816)
- ix78ESOrnjfX.exe (PID: 12356)
- ix78ESOrnjfX.exe (PID: 13792)
- ix78ESOrnjfX.exe (PID: 13052)
- ix78ESOrnjfX.exe (PID: 12884)
- ix78ESOrnjfX.exe (PID: 5116)
- ix78ESOrnjfX.exe (PID: 12464)
- ix78ESOrnjfX.exe (PID: 12912)
- ix78ESOrnjfX.exe (PID: 2812)
- ix78ESOrnjfX.exe (PID: 12904)
- ix78ESOrnjfX.exe (PID: 6916)
- ix78ESOrnjfX.exe (PID: 12472)
- ix78ESOrnjfX.exe (PID: 13296)
- ix78ESOrnjfX.exe (PID: 13812)
- ix78ESOrnjfX.exe (PID: 13992)
- ix78ESOrnjfX.exe (PID: 12800)
- ix78ESOrnjfX.exe (PID: 12420)
- ix78ESOrnjfX.exe (PID: 13096)
- ix78ESOrnjfX.exe (PID: 10020)
- ix78ESOrnjfX.exe (PID: 12484)
- ix78ESOrnjfX.exe (PID: 13644)
- ix78ESOrnjfX.exe (PID: 12736)
- ix78ESOrnjfX.exe (PID: 14168)
- ix78ESOrnjfX.exe (PID: 12640)
- ix78ESOrnjfX.exe (PID: 12692)
- ix78ESOrnjfX.exe (PID: 13068)
- ix78ESOrnjfX.exe (PID: 12840)
- ix78ESOrnjfX.exe (PID: 12632)
- ix78ESOrnjfX.exe (PID: 7880)
- ix78ESOrnjfX.exe (PID: 12412)
- ix78ESOrnjfX.exe (PID: 13576)
- ix78ESOrnjfX.exe (PID: 12468)
- ix78ESOrnjfX.exe (PID: 13324)
- ix78ESOrnjfX.exe (PID: 13920)
- ix78ESOrnjfX.exe (PID: 13004)
- ix78ESOrnjfX.exe (PID: 12804)
- ix78ESOrnjfX.exe (PID: 13732)
- ix78ESOrnjfX.exe (PID: 2104)
- ix78ESOrnjfX.exe (PID: 8024)
- ix78ESOrnjfX.exe (PID: 13796)
- ix78ESOrnjfX.exe (PID: 12348)
- ix78ESOrnjfX.exe (PID: 13764)
- ix78ESOrnjfX.exe (PID: 7764)
- ix78ESOrnjfX.exe (PID: 12500)
- ix78ESOrnjfX.exe (PID: 12404)
- ix78ESOrnjfX.exe (PID: 1748)
- ix78ESOrnjfX.exe (PID: 13720)
- ix78ESOrnjfX.exe (PID: 12552)
- ix78ESOrnjfX.exe (PID: 760)
- ix78ESOrnjfX.exe (PID: 13080)
- ix78ESOrnjfX.exe (PID: 13008)
- ix78ESOrnjfX.exe (PID: 13236)
- ix78ESOrnjfX.exe (PID: 14184)
- ix78ESOrnjfX.exe (PID: 13176)
- ix78ESOrnjfX.exe (PID: 12788)
- ix78ESOrnjfX.exe (PID: 13632)
- ix78ESOrnjfX.exe (PID: 12968)
- ix78ESOrnjfX.exe (PID: 13020)
- ix78ESOrnjfX.exe (PID: 7020)
- ix78ESOrnjfX.exe (PID: 13028)
- ix78ESOrnjfX.exe (PID: 12432)
- ix78ESOrnjfX.exe (PID: 13024)
- ix78ESOrnjfX.exe (PID: 14096)
- ix78ESOrnjfX.exe (PID: 13800)
- ix78ESOrnjfX.exe (PID: 9872)
- ix78ESOrnjfX.exe (PID: 3044)
- ix78ESOrnjfX.exe (PID: 13912)
- ix78ESOrnjfX.exe (PID: 14104)
- ix78ESOrnjfX.exe (PID: 13788)
- ix78ESOrnjfX.exe (PID: 14152)
- ix78ESOrnjfX.exe (PID: 13996)
- ix78ESOrnjfX.exe (PID: 13292)
- ix78ESOrnjfX.exe (PID: 2364)
- ix78ESOrnjfX.exe (PID: 14124)
- ix78ESOrnjfX.exe (PID: 3144)
- ix78ESOrnjfX.exe (PID: 13972)
- ix78ESOrnjfX.exe (PID: 13728)
- ix78ESOrnjfX.exe (PID: 13440)
- ix78ESOrnjfX.exe (PID: 13592)
- ix78ESOrnjfX.exe (PID: 13940)
- ix78ESOrnjfX.exe (PID: 13904)
- ix78ESOrnjfX.exe (PID: 10464)
- ix78ESOrnjfX.exe (PID: 12560)
- ix78ESOrnjfX.exe (PID: 13876)
- ix78ESOrnjfX.exe (PID: 13496)
- ix78ESOrnjfX.exe (PID: 11436)
- ix78ESOrnjfX.exe (PID: 4440)
- ix78ESOrnjfX.exe (PID: 11044)
- ix78ESOrnjfX.exe (PID: 12448)
- ix78ESOrnjfX.exe (PID: 12868)
- ix78ESOrnjfX.exe (PID: 13808)
- ix78ESOrnjfX.exe (PID: 13304)
- ix78ESOrnjfX.exe (PID: 11836)
- ix78ESOrnjfX.exe (PID: 11636)
- ix78ESOrnjfX.exe (PID: 5540)
- ix78ESOrnjfX.exe (PID: 14176)
- ix78ESOrnjfX.exe (PID: 13464)
- ix78ESOrnjfX.exe (PID: 12436)
- ix78ESOrnjfX.exe (PID: 13944)
- ix78ESOrnjfX.exe (PID: 13000)
- ix78ESOrnjfX.exe (PID: 13300)
- ix78ESOrnjfX.exe (PID: 13088)
- ix78ESOrnjfX.exe (PID: 13936)
- ix78ESOrnjfX.exe (PID: 12636)
- ix78ESOrnjfX.exe (PID: 14284)
- ix78ESOrnjfX.exe (PID: 14264)
- ix78ESOrnjfX.exe (PID: 14164)
- ix78ESOrnjfX.exe (PID: 12600)
- ix78ESOrnjfX.exe (PID: 13160)
- ix78ESOrnjfX.exe (PID: 13336)
- ix78ESOrnjfX.exe (PID: 7240)
- ix78ESOrnjfX.exe (PID: 13476)
- ix78ESOrnjfX.exe (PID: 13816)
- ix78ESOrnjfX.exe (PID: 13164)
- ix78ESOrnjfX.exe (PID: 13116)
- ix78ESOrnjfX.exe (PID: 12568)
- ix78ESOrnjfX.exe (PID: 13624)
- ix78ESOrnjfX.exe (PID: 13504)
- ix78ESOrnjfX.exe (PID: 12872)
- ix78ESOrnjfX.exe (PID: 13404)
- ix78ESOrnjfX.exe (PID: 13900)
- ix78ESOrnjfX.exe (PID: 13712)
- ix78ESOrnjfX.exe (PID: 12992)
- ix78ESOrnjfX.exe (PID: 12664)
- ix78ESOrnjfX.exe (PID: 13480)
- ix78ESOrnjfX.exe (PID: 14100)
- ix78ESOrnjfX.exe (PID: 13872)
- ix78ESOrnjfX.exe (PID: 13348)
- ix78ESOrnjfX.exe (PID: 10552)
- ix78ESOrnjfX.exe (PID: 6056)
- ix78ESOrnjfX.exe (PID: 1904)
- ix78ESOrnjfX.exe (PID: 12624)
- ix78ESOrnjfX.exe (PID: 13844)
- ix78ESOrnjfX.exe (PID: 13616)
- ix78ESOrnjfX.exe (PID: 7864)
- ix78ESOrnjfX.exe (PID: 11736)
- ix78ESOrnjfX.exe (PID: 10316)
- ix78ESOrnjfX.exe (PID: 7444)
- ix78ESOrnjfX.exe (PID: 12576)
- ix78ESOrnjfX.exe (PID: 12700)
- ix78ESOrnjfX.exe (PID: 14004)
- ix78ESOrnjfX.exe (PID: 13868)
- ix78ESOrnjfX.exe (PID: 10680)
- ix78ESOrnjfX.exe (PID: 8096)
- ix78ESOrnjfX.exe (PID: 10632)
- ix78ESOrnjfX.exe (PID: 8280)
- ix78ESOrnjfX.exe (PID: 9724)
- ix78ESOrnjfX.exe (PID: 7832)
- ix78ESOrnjfX.exe (PID: 9472)
- ix78ESOrnjfX.exe (PID: 14532)
- ix78ESOrnjfX.exe (PID: 14724)
- ix78ESOrnjfX.exe (PID: 14860)
- ix78ESOrnjfX.exe (PID: 14968)
- ix78ESOrnjfX.exe (PID: 9160)
- ix78ESOrnjfX.exe (PID: 12652)
- ix78ESOrnjfX.exe (PID: 11432)
- ix78ESOrnjfX.exe (PID: 15452)
- ix78ESOrnjfX.exe (PID: 15840)
- ix78ESOrnjfX.exe (PID: 15124)
- ix78ESOrnjfX.exe (PID: 15208)
- ix78ESOrnjfX.exe (PID: 15348)
- ix78ESOrnjfX.exe (PID: 15600)
- ix78ESOrnjfX.exe (PID: 15720)
- ix78ESOrnjfX.exe (PID: 14768)
- ix78ESOrnjfX.exe (PID: 15132)
- ix78ESOrnjfX.exe (PID: 15292)
- ix78ESOrnjfX.exe (PID: 15432)
- ix78ESOrnjfX.exe (PID: 15944)
- ix78ESOrnjfX.exe (PID: 16044)
- ix78ESOrnjfX.exe (PID: 16240)
- ix78ESOrnjfX.exe (PID: 14340)
- ix78ESOrnjfX.exe (PID: 16012)
- ix78ESOrnjfX.exe (PID: 16156)
- ix78ESOrnjfX.exe (PID: 16356)
- ix78ESOrnjfX.exe (PID: 14516)
- ix78ESOrnjfX.exe (PID: 14672)
- ix78ESOrnjfX.exe (PID: 15664)
- ix78ESOrnjfX.exe (PID: 15824)
- ix78ESOrnjfX.exe (PID: 14656)
- ix78ESOrnjfX.exe (PID: 15244)
- ix78ESOrnjfX.exe (PID: 15460)
- ix78ESOrnjfX.exe (PID: 15368)
- ix78ESOrnjfX.exe (PID: 15580)
- ix78ESOrnjfX.exe (PID: 14876)
- ix78ESOrnjfX.exe (PID: 14912)
- ix78ESOrnjfX.exe (PID: 16056)
- ix78ESOrnjfX.exe (PID: 8508)
- ix78ESOrnjfX.exe (PID: 16380)
- ix78ESOrnjfX.exe (PID: 14616)
- ix78ESOrnjfX.exe (PID: 5788)
- ix78ESOrnjfX.exe (PID: 15796)
- ix78ESOrnjfX.exe (PID: 15912)
- ix78ESOrnjfX.exe (PID: 16180)
- conhost.exe (PID: 15476)
- ix78ESOrnjfX.exe (PID: 15536)
- ix78ESOrnjfX.exe (PID: 14744)
- ix78ESOrnjfX.exe (PID: 14920)
- ix78ESOrnjfX.exe (PID: 15056)
- ix78ESOrnjfX.exe (PID: 15264)
- cmd.exe (PID: 15220)
- ix78ESOrnjfX.exe (PID: 16212)
- ix78ESOrnjfX.exe (PID: 14480)
- ix78ESOrnjfX.exe (PID: 15392)
- cmd.exe (PID: 14764)
- ix78ESOrnjfX.exe (PID: 15148)
- ix78ESOrnjfX.exe (PID: 14448)
- ix78ESOrnjfX.exe (PID: 14956)
- ix78ESOrnjfX.exe (PID: 15736)
- ix78ESOrnjfX.exe (PID: 15024)
- ntvdm.exe (PID: 12792)
- ix78ESOrnjfX.exe (PID: 15708)
- ix78ESOrnjfX.exe (PID: 12388)
- ix78ESOrnjfX.exe (PID: 16008)
- conhost.exe (PID: 3216)
- ix78ESOrnjfX.exe (PID: 16360)
- cmd.exe (PID: 15992)
- conhost.exe (PID: 15012)
- ix78ESOrnjfX.exe (PID: 14700)
- ix78ESOrnjfX.exe (PID: 4644)
- ix78ESOrnjfX.exe (PID: 14836)
- ix78ESOrnjfX.exe (PID: 15284)
- ix78ESOrnjfX.exe (PID: 15884)
- gaoou.exe (PID: 16236)
- ix78ESOrnjfX.exe (PID: 15492)
- cmd.exe (PID: 15020)
- ix78ESOrnjfX.exe (PID: 16096)
- ix78ESOrnjfX.exe (PID: 4076)
- conhost.exe (PID: 15276)
- ix78ESOrnjfX.exe (PID: 14888)
- ix78ESOrnjfX.exe (PID: 15168)
- ix78ESOrnjfX.exe (PID: 15152)
- ix78ESOrnjfX.exe (PID: 15972)
- WerFault.exe (PID: 15740)
- ix78ESOrnjfX.exe (PID: 14664)
- ix78ESOrnjfX.exe (PID: 14752)
- ix78ESOrnjfX.exe (PID: 3228)
- ix78ESOrnjfX.exe (PID: 15808)
- ix78ESOrnjfX.exe (PID: 15136)
- ix78ESOrnjfX.exe (PID: 16272)
- ix78ESOrnjfX.exe (PID: 2288)
- ix78ESOrnjfX.exe (PID: 14940)
- ix78ESOrnjfX.exe (PID: 15704)
- ix78ESOrnjfX.exe (PID: 15472)
- ix78ESOrnjfX.exe (PID: 14440)
- ix78ESOrnjfX.exe (PID: 15200)
- ix78ESOrnjfX.exe (PID: 15872)
- ix78ESOrnjfX.exe (PID: 15616)
- ix78ESOrnjfX.exe (PID: 2724)
- ix78ESOrnjfX.exe (PID: 14512)
- ix78ESOrnjfX.exe (PID: 16032)
- Setup3310.exe (PID: 12776)
- ix78ESOrnjfX.exe (PID: 15592)
- ix78ESOrnjfX.exe (PID: 16320)
- ix78ESOrnjfX.exe (PID: 15524)
- ix78ESOrnjfX.exe (PID: 4872)
- ix78ESOrnjfX.exe (PID: 16080)
- ix78ESOrnjfX.exe (PID: 14384)
- ix78ESOrnjfX.exe (PID: 16296)
- ix78ESOrnjfX.exe (PID: 15656)
- ix78ESOrnjfX.exe (PID: 15412)
- cmd.exe (PID: 14528)
- ix78ESOrnjfX.exe (PID: 12724)
- jfiag3g_gg.exe (PID: 14372)
- ix78ESOrnjfX.exe (PID: 14880)
- ix78ESOrnjfX.exe (PID: 15112)
- ix78ESOrnjfX.exe (PID: 15444)
- ix78ESOrnjfX.exe (PID: 15556)
- ix78ESOrnjfX.exe (PID: 15996)
- ix78ESOrnjfX.exe (PID: 15228)
- ix78ESOrnjfX.exe (PID: 14412)
- ix78ESOrnjfX.exe (PID: 16104)
- conhost.exe (PID: 15180)
- ix78ESOrnjfX.exe (PID: 14584)
- ix78ESOrnjfX.exe (PID: 14556)
- cmd.exe (PID: 14356)
- ix78ESOrnjfX.exe (PID: 14032)
- ix78ESOrnjfX.exe (PID: 14644)
- ix78ESOrnjfX.exe (PID: 14916)
- ix78ESOrnjfX.exe (PID: 13136)
- conhost.exe (PID: 16136)
- ix78ESOrnjfX.exe (PID: 3680)
- ix78ESOrnjfX.exe (PID: 8236)
- google-game.exe (PID: 15700)
- ix78ESOrnjfX.exe (PID: 16216)
- ix78ESOrnjfX.exe (PID: 14976)
- ix78ESOrnjfX.exe (PID: 16184)
- cmd.exe (PID: 16304)
- ix78ESOrnjfX.exe (PID: 14812)
- conhost.exe (PID: 15544)
- ix78ESOrnjfX.exe (PID: 16120)
- ix78ESOrnjfX.exe (PID: 14992)
- ix78ESOrnjfX.exe (PID: 15360)
- ix78ESOrnjfX.exe (PID: 15344)
- ix78ESOrnjfX.exe (PID: 16228)
- ix78ESOrnjfX.exe (PID: 14548)
- cmd.exe (PID: 2936)
- ix78ESOrnjfX.exe (PID: 15924)
- ix78ESOrnjfX.exe (PID: 15008)
- ix78ESOrnjfX.exe (PID: 15976)
- ix78ESOrnjfX.exe (PID: 14408)
- 005.exe (PID: 13152)
- ix78ESOrnjfX.exe (PID: 10880)
- conhost.exe (PID: 15032)
- ix78ESOrnjfX.exe (PID: 15908)
- ix78ESOrnjfX.exe (PID: 16300)
- ix78ESOrnjfX.exe (PID: 15288)
- ix78ESOrnjfX.exe (PID: 14736)
- ix78ESOrnjfX.exe (PID: 4468)
- ix78ESOrnjfX.exe (PID: 11004)
- ix78ESOrnjfX.exe (PID: 14420)
Connects to CnC server
- setup_install.exe (PID: 2576)
- metina_4.exe (PID: 2664)
- 4S6ougCAgc8iShZEDJo0kSnE.exe (PID: 2832)
- jooyu.exe (PID: 4320)
- kpsVuIwTxthziIAnqHxbmA3S.exe (PID: 4928)
- 39945411238.exe (PID: 1756)
Runs injected code in another process
- rUNdlL32.eXe (PID: 1764)
- wmiprvse.exe (PID: 2516)
Application was injected by another process
- svchost.exe (PID: 876)
- csrss.exe (PID: 388)
- svchost.exe (PID: 672)
- svchost.exe (PID: 772)
- svchost.exe (PID: 808)
- svchost.exe (PID: 592)
- services.exe (PID: 472)
- smss.exe (PID: 264)
- svchost.exe (PID: 1052)
- csrss.exe (PID: 344)
- lsm.exe (PID: 496)
- IMEDICTUPDATE.EXE (PID: 1356)
- svchost.exe (PID: 852)
- taskeng.exe (PID: 2016)
- svchost.exe (PID: 1216)
- svchost.exe (PID: 1812)
- dwm.exe (PID: 124)
- explorer.exe (PID: 540)
- spoolsv.exe (PID: 1188)
- SearchIndexer.exe (PID: 1136)
- ctfmon.exe (PID: 1036)
- lsass.exe (PID: 488)
- winlogon.exe (PID: 428)
- wininit.exe (PID: 380)
- msiexec.exe (PID: 3264)
- svchost.exe (PID: 3348)
- host.exe (PID: 1932)
- srvpost.exe (PID: 3668)
- SearchProtocolHost.exe (PID: 3088)
Changes settings of System certificates
- metina_4.exe (PID: 2664)
- metina_3.exe (PID: 3756)
- metina_6.exe (PID: 2224)
- ZHyvylevyhu.exe (PID: 4980)
VIDAR was detected
- metina_3.exe (PID: 3756)
Actions looks like stealing of personal data
- svchost.exe (PID: 4092)
- metina_3.exe (PID: 3756)
- YrzSoesjiLwxBCoMxHQZirVc.exe (PID: 4060)
- qHdNlR18fgOe7MhumSEpTmir.exe (PID: 3380)
- N45w47HnqWFawEkl0bru5UlP.exe (PID: 2752)
- 39945411238.exe (PID: 1756)
- xklWwL5ZQDKR8P3RorxcFDlW.exe (PID: 5592)
- nUcWWy3PkrkGIOnGIjiZTNEZ.exe (PID: 3072)
- NHv27pefor9cjMZxQPyaoTxI.exe (PID: 992)
- rEyWPHzEjwsMBXGpHUKTBrhV.exe (PID: 960)
- rMVZCe2lp19v9IjXoRM6IDf9.exe (PID: 1480)
- 75597259823.exe (PID: 5120)
- RUNDLL32.EXE (PID: 12752)
Steals credentials from Web Browsers
- svchost.exe (PID: 4092)
- metina_3.exe (PID: 3756)
- qHdNlR18fgOe7MhumSEpTmir.exe (PID: 3380)
- 39945411238.exe (PID: 1756)
- xklWwL5ZQDKR8P3RorxcFDlW.exe (PID: 5592)
- N45w47HnqWFawEkl0bru5UlP.exe (PID: 2752)
- nUcWWy3PkrkGIOnGIjiZTNEZ.exe (PID: 3072)
- NHv27pefor9cjMZxQPyaoTxI.exe (PID: 992)
- rEyWPHzEjwsMBXGpHUKTBrhV.exe (PID: 960)
- rMVZCe2lp19v9IjXoRM6IDf9.exe (PID: 1480)
- 75597259823.exe (PID: 5120)
- RUNDLL32.EXE (PID: 12752)
REDLINE was detected
- rEyWPHzEjwsMBXGpHUKTBrhV.exe (PID: 960)
- qHdNlR18fgOe7MhumSEpTmir.exe (PID: 3380)
- NHv27pefor9cjMZxQPyaoTxI.exe (PID: 992)
- nUcWWy3PkrkGIOnGIjiZTNEZ.exe (PID: 3072)
- xklWwL5ZQDKR8P3RorxcFDlW.exe (PID: 5592)
- rMVZCe2lp19v9IjXoRM6IDf9.exe (PID: 1480)
- N45w47HnqWFawEkl0bru5UlP.exe (PID: 2752)
- 75597259823.exe (PID: 5120)
Stealing of credential data
- metina_3.exe (PID: 3756)
- 39945411238.exe (PID: 1756)
- N45w47HnqWFawEkl0bru5UlP.exe (PID: 2752)
- nUcWWy3PkrkGIOnGIjiZTNEZ.exe (PID: 3072)
Modifies hosts file to block updates
- YrzSoesjiLwxBCoMxHQZirVc.exe (PID: 4060)
Writes to the hosts file
- YrzSoesjiLwxBCoMxHQZirVc.exe (PID: 4060)
Runs app for hidden code execution
- cmd.exe (PID: 10048)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 6588)
Writes to a start menu file
- Nel.exe.com (PID: 3212)
DANABOT was detected
- RUNDLL32.EXE (PID: 12752)
Modifies files in Chrome extension folder
- RUNDLL32.EXE (PID: 12752)
SUSPICIOUS
Creates files in the program directory
- SearchIndexer.exe (PID: 1136)
- p8g4aIxrVWYViEzCIwRjDG3Q.exe (PID: 3864)
- metina_3.exe (PID: 3756)
- YrzSoesjiLwxBCoMxHQZirVc.exe (PID: 4060)
- 6iawqAht8OEFOcBQIcovYGl6.exe (PID: 1376)
- WerFault.exe (PID: 3116)
- sCUIVIyz6dLBRM80cvSf4Ms9.exe (PID: 5844)
- WerFault.exe (PID: 5028)
- lighteningplayer-cache-gen.exe (PID: 12188)
Creates files in the user directory
- lsass.exe (PID: 488)
- explorer.exe (PID: 540)
- metina_6.exe (PID: 2224)
- svchost.exe (PID: 4092)
- Browzar.exe (PID: 1520)
- sCUIVIyz6dLBRM80cvSf4Ms9.exe (PID: 5844)
- powershell.exe (PID: 9024)
- 96356344407.exe (PID: 8488)
- Nel.exe.com (PID: 3212)
Creates files in the Windows directory
- svchost.exe (PID: 852)
- svchost.exe (PID: 772)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3608)
- x86_x64_setup.exe (PID: 1840)
- setup_installer.exe (PID: 3032)
- metina_1.exe (PID: 648)
- metina_5.exe (PID: 3664)
- metina_5.tmp (PID: 2872)
- metina_4.exe (PID: 2664)
- metina_6.exe (PID: 2224)
- metina_2.exe (PID: 1760)
- p8g4aIxrVWYViEzCIwRjDG3Q.exe (PID: 3864)
- metina_3.exe (PID: 3756)
- (_____(_(_________))235 Smeargle.exe (PID: 3900)
- ovkclsFeaGxsWSFI43MgtqQE.exe (PID: 3304)
- ultramediaburner.exe (PID: 3180)
- LF0oWSD2TqJjfvQ1dz0Eeecm.exe (PID: 2372)
- 6iawqAht8OEFOcBQIcovYGl6.exe (PID: 1376)
- ultramediaburner.tmp (PID: 2264)
- kpsVuIwTxthziIAnqHxbmA3S.exe (PID: 4928)
- 4S6ougCAgc8iShZEDJo0kSnE.exe (PID: 2832)
- jooyu.exe (PID: 4320)
- jingzhang.exe (PID: 5852)
- sCUIVIyz6dLBRM80cvSf4Ms9.exe (PID: 5844)
- ZHyvylevyhu.exe (PID: 4980)
- ebook.exe (PID: 11388)
- cmd.exe (PID: 6588)
- Nel.exe.com (PID: 3212)
- gaoou.exe (PID: 16236)
- Setup3310.exe (PID: 12776)
- Setup3310.tmp (PID: 15516)
- google-game.exe (PID: 15700)
Drops a file with too old compile date
- setup_installer.exe (PID: 3032)
- metina_5.exe (PID: 3664)
- metina_5.tmp (PID: 2872)
- metina_6.exe (PID: 2224)
- p8g4aIxrVWYViEzCIwRjDG3Q.exe (PID: 3864)
- (_____(_(_________))235 Smeargle.exe (PID: 3900)
- ultramediaburner.exe (PID: 3180)
- 6iawqAht8OEFOcBQIcovYGl6.exe (PID: 1376)
- ultramediaburner.tmp (PID: 2264)
- sCUIVIyz6dLBRM80cvSf4Ms9.exe (PID: 5844)
- ZHyvylevyhu.exe (PID: 4980)
- Setup3310.exe (PID: 12776)
- Setup3310.tmp (PID: 15516)
Drops a file that was compiled in debug mode
- setup_installer.exe (PID: 3032)
- metina_4.exe (PID: 2664)
- metina_1.exe (PID: 648)
- metina_5.tmp (PID: 2872)
- metina_6.exe (PID: 2224)
- metina_2.exe (PID: 1760)
- metina_3.exe (PID: 3756)
- ovkclsFeaGxsWSFI43MgtqQE.exe (PID: 3304)
- LF0oWSD2TqJjfvQ1dz0Eeecm.exe (PID: 2372)
- 6iawqAht8OEFOcBQIcovYGl6.exe (PID: 1376)
- ultramediaburner.tmp (PID: 2264)
- 4S6ougCAgc8iShZEDJo0kSnE.exe (PID: 2832)
- jingzhang.exe (PID: 5852)
- sCUIVIyz6dLBRM80cvSf4Ms9.exe (PID: 5844)
- ZHyvylevyhu.exe (PID: 4980)
- Setup3310.tmp (PID: 15516)
- google-game.exe (PID: 15700)
Drops a file with a compile date too recent
- setup_installer.exe (PID: 3032)
- metina_4.exe (PID: 2664)
- metina_1.exe (PID: 648)
- p8g4aIxrVWYViEzCIwRjDG3Q.exe (PID: 3864)
- metina_6.exe (PID: 2224)
- (_____(_(_________))235 Smeargle.exe (PID: 3900)
- LF0oWSD2TqJjfvQ1dz0Eeecm.exe (PID: 2372)
- 6iawqAht8OEFOcBQIcovYGl6.exe (PID: 1376)
- ebook.exe (PID: 11388)
- ZHyvylevyhu.exe (PID: 4980)
Starts CMD.EXE for commands execution
- setup_install.exe (PID: 2576)
- 4S6ougCAgc8iShZEDJo0kSnE.exe (PID: 2832)
- metina_6.exe (PID: 2224)
- metina_3.exe (PID: 3756)
- YrzSoesjiLwxBCoMxHQZirVc.exe (PID: 4060)
- ZHyvylevyhu.exe (PID: 4980)
- 0001.exe (PID: 9408)
- cmd.exe (PID: 10048)
Searches for installed software
- svchost.exe (PID: 808)
- metina_3.exe (PID: 3756)
- qHdNlR18fgOe7MhumSEpTmir.exe (PID: 3380)
- rMVZCe2lp19v9IjXoRM6IDf9.exe (PID: 1480)
- 39945411238.exe (PID: 1756)
- N45w47HnqWFawEkl0bru5UlP.exe (PID: 2752)
- nUcWWy3PkrkGIOnGIjiZTNEZ.exe (PID: 3072)
- NHv27pefor9cjMZxQPyaoTxI.exe (PID: 992)
- xklWwL5ZQDKR8P3RorxcFDlW.exe (PID: 5592)
- rEyWPHzEjwsMBXGpHUKTBrhV.exe (PID: 960)
- rundll32.exe (PID: 3920)
- 75597259823.exe (PID: 5120)
- RUNDLL32.EXE (PID: 12752)
Reads the cookies of Google Chrome
- jfiag3g_gg.exe (PID: 3764)
- svchost.exe (PID: 4092)
- metina_3.exe (PID: 3756)
- jfiag3g_gg.exe (PID: 5164)
- jfiag3g_gg.exe (PID: 5368)
- qHdNlR18fgOe7MhumSEpTmir.exe (PID: 3380)
- 39945411238.exe (PID: 1756)
- xklWwL5ZQDKR8P3RorxcFDlW.exe (PID: 5592)
- N45w47HnqWFawEkl0bru5UlP.exe (PID: 2752)
- nUcWWy3PkrkGIOnGIjiZTNEZ.exe (PID: 3072)
- NHv27pefor9cjMZxQPyaoTxI.exe (PID: 992)
- rEyWPHzEjwsMBXGpHUKTBrhV.exe (PID: 960)
- rMVZCe2lp19v9IjXoRM6IDf9.exe (PID: 1480)
- 75597259823.exe (PID: 5120)
- jfiag3g_gg.exe (PID: 14372)
Low-level read access rights to disk partition
- svchost.exe (PID: 4092)
Uses RUNDLL32.EXE to load library
- metina_1.exe (PID: 648)
- LF0oWSD2TqJjfvQ1dz0Eeecm.exe (PID: 2372)
- jingzhang.exe (PID: 5852)
- ebook.exe (PID: 11388)
- rundll32.exe (PID: 3920)
Checks for external IP
- metina_4.exe (PID: 2664)
- svchost.exe (PID: 4092)
- kpsVuIwTxthziIAnqHxbmA3S.exe (PID: 4928)
- jooyu.exe (PID: 4320)
- gaoou.exe (PID: 16236)
Adds / modifies Windows certificates
- metina_3.exe (PID: 3756)
- metina_6.exe (PID: 2224)
- metina_4.exe (PID: 2664)
- ZHyvylevyhu.exe (PID: 4980)
Application launched itself
- NHv27pefor9cjMZxQPyaoTxI.exe (PID: 3844)
- ovkclsFeaGxsWSFI43MgtqQE.exe (PID: 3020)
- rMVZCe2lp19v9IjXoRM6IDf9.exe (PID: 3388)
- N45w47HnqWFawEkl0bru5UlP.exe (PID: 2420)
- nUcWWy3PkrkGIOnGIjiZTNEZ.exe (PID: 3584)
- xklWwL5ZQDKR8P3RorxcFDlW.exe (PID: 1556)
- ix78ESOrnjfX.exe (PID: 3956)
- cmd.exe (PID: 10048)
- Nel.exe.com (PID: 6900)
- rundll32.exe (PID: 3920)
Creates a directory in Program Files
- (_____(_(_________))235 Smeargle.exe (PID: 3900)
- p8g4aIxrVWYViEzCIwRjDG3Q.exe (PID: 3864)
- 6iawqAht8OEFOcBQIcovYGl6.exe (PID: 1376)
- ultramediaburner.tmp (PID: 2264)
- sCUIVIyz6dLBRM80cvSf4Ms9.exe (PID: 5844)
Creates a software uninstall entry
- p8g4aIxrVWYViEzCIwRjDG3Q.exe (PID: 3864)
- 6iawqAht8OEFOcBQIcovYGl6.exe (PID: 1376)
- sCUIVIyz6dLBRM80cvSf4Ms9.exe (PID: 5844)
Reads the cookies of Mozilla Firefox
- svchost.exe (PID: 4092)
- metina_3.exe (PID: 3756)
- qHdNlR18fgOe7MhumSEpTmir.exe (PID: 3380)
- 39945411238.exe (PID: 1756)
- xklWwL5ZQDKR8P3RorxcFDlW.exe (PID: 5592)
- N45w47HnqWFawEkl0bru5UlP.exe (PID: 2752)
- nUcWWy3PkrkGIOnGIjiZTNEZ.exe (PID: 3072)
- NHv27pefor9cjMZxQPyaoTxI.exe (PID: 992)
- rEyWPHzEjwsMBXGpHUKTBrhV.exe (PID: 960)
- rMVZCe2lp19v9IjXoRM6IDf9.exe (PID: 1480)
- 75597259823.exe (PID: 5120)
Reads internet explorer settings
- Browzar.exe (PID: 1520)
Loads DLL from Mozilla Firefox
- csrss.exe (PID: 388)
- csrss.exe (PID: 344)
- RUNDLL32.EXE (PID: 12752)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4760)
- cmd.exe (PID: 840)
- cmd.exe (PID: 6408)
- cmd.exe (PID: 8112)
- cmd.exe (PID: 8952)
Starts Internet Explorer
- Wefecasofe.exe (PID: 2744)
Reads Environment values
- YrzSoesjiLwxBCoMxHQZirVc.exe (PID: 4060)
- qHdNlR18fgOe7MhumSEpTmir.exe (PID: 3380)
- xklWwL5ZQDKR8P3RorxcFDlW.exe (PID: 5592)
- nUcWWy3PkrkGIOnGIjiZTNEZ.exe (PID: 3072)
- 96356344407.exe (PID: 8488)
- N45w47HnqWFawEkl0bru5UlP.exe (PID: 2752)
- rMVZCe2lp19v9IjXoRM6IDf9.exe (PID: 1480)
- NHv27pefor9cjMZxQPyaoTxI.exe (PID: 992)
- rEyWPHzEjwsMBXGpHUKTBrhV.exe (PID: 960)
- 75597259823.exe (PID: 5120)
Starts CMD.EXE for self-deleting
- metina_3.exe (PID: 3756)
Starts application with an unusual extension
- sCUIVIyz6dLBRM80cvSf4Ms9.exe (PID: 5844)
- cmd.exe (PID: 6588)
- Nel.exe.com (PID: 6900)
Executes PowerShell scripts
- ns99D6.tmp (PID: 7144)
Reads CPU info
- 96356344407.exe (PID: 8488)
Removes files from Windows directory
- svchost.exe (PID: 1216)
Drop AutoIt3 executable file
- cmd.exe (PID: 6588)
- Nel.exe.com (PID: 3212)
Executes application which crashes
- cmd.exe (PID: 7936)
- 96356344407.exe (PID: 8488)
- cmd.exe (PID: 15220)
- cmd.exe (PID: 16304)
INFO
Application launched itself
- chrome.exe (PID: 2204)
- firefox.exe (PID: 6008)
- chrome.exe (PID: 2820)
- firefox.exe (PID: 2612)
- iexplore.exe (PID: 5144)
Reads the hosts file
- chrome.exe (PID: 2204)
- chrome.exe (PID: 3140)
- svchost.exe (PID: 1052)
- chrome.exe (PID: 2820)
- chrome.exe (PID: 2000)
Manual execution by user
- WinRAR.exe (PID: 3608)
- WinRAR.exe (PID: 648)
- NOTEPAD.EXE (PID: 756)
- x86_x64_setup.exe (PID: 2400)
- x86_x64_setup.exe (PID: 1840)
Application was dropped or rewritten from another process
- metina_5.tmp (PID: 2872)
- (_____(_(_________))235 Smeargle.exe (PID: 3900)
- ultramediaburner.tmp (PID: 2264)
- Setup3310.tmp (PID: 15516)
Loads dropped or rewritten executable
- metina_5.tmp (PID: 2872)
- (_____(_(_________))235 Smeargle.exe (PID: 3900)
- ultramediaburner.tmp (PID: 2264)
- Setup3310.tmp (PID: 15516)
Reads settings of System Certificates
- metina_6.exe (PID: 2224)
- ZHyvylevyhu.exe (PID: 4980)
- chrome.exe (PID: 2000)
- jooyu.exe (PID: 4320)
- iexplore.exe (PID: 5144)
- iexplore.exe (PID: 628)
- svchost.exe (PID: 1052)
Creates files in the program directory
- (_____(_(_________))235 Smeargle.exe (PID: 3900)
- ultramediaburner.tmp (PID: 2264)
- firefox.exe (PID: 2612)
Creates a software uninstall entry
- ultramediaburner.tmp (PID: 2264)
Creates files in the user directory
- firefox.exe (PID: 2612)
- iexplore.exe (PID: 5144)
Changes internet zones settings
- iexplore.exe (PID: 5144)
Reads CPU info
- firefox.exe (PID: 2612)
Dropped object may contain Bitcoin addresses
- ZHyvylevyhu.exe (PID: 4980)
Adds / modifies Windows certificates
- chrome.exe (PID: 2000)
- iexplore.exe (PID: 5144)
Changes settings of System certificates
- chrome.exe (PID: 2000)
- iexplore.exe (PID: 5144)
Reads internet explorer settings
- iexplore.exe (PID: 628)
Reads the computer name
- RUNDLL32.EXE (PID: 12752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
1 586
Monitored processes
1 581
Malicious processes
1 117
Suspicious processes
355
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Windows\system32\Dwm.exe" | C:\Windows\System32\dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 264 | \SystemRoot\System32\smss.exe | C:\Windows\System32\smss.exe | System | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Session Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 272 | \??\C:\Windows\system32\conhost.exe "-635794380-1213949309-1305861360-9575568851573093299-1496291537-70975285795606186" | C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 308 | "C:\Program Files\Browzar\ix78ESOrnjfX.exe" | C:\Program Files\Browzar\ix78ESOrnjfX.exe | — | ix78ESOrnjfX.exe | |||||||||||
User: admin Company: HttpSessionStateContainer Integrity Level: HIGH Description: DefaultSettingValueAttribute Exit code: 0 Version: 658.594.755.513 Modules
| |||||||||||||||
| 324 | "C:\Program Files\Browzar\ix78ESOrnjfX.exe" | C:\Program Files\Browzar\ix78ESOrnjfX.exe | — | ix78ESOrnjfX.exe | |||||||||||
User: admin Company: HttpSessionStateContainer Integrity Level: HIGH Description: DefaultSettingValueAttribute Exit code: 0 Version: 658.594.755.513 Modules
| |||||||||||||||
| 344 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 376 | C:\Windows\system32\AUDIODG.EXE 0x6b8 | C:\Windows\system32\AUDIODG.EXE | — | svchost.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Audio Device Graph Isolation Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 380 | wininit.exe | C:\Windows\System32\wininit.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Start-Up Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 388 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 428 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
26 172
Read events
24 498
Write events
1 652
Delete events
22
Modification events
| (PID) Process: | (668) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2204-13268116783248125 |
Value: 259 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
246
Suspicious files
147
Text files
516
Unknown types
133
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-60C6D430-89C.pma | — | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\21863e31-485a-42b1-9824-c514c2aaa8e8.tmp | — | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF13f36c.TMP | text | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF13f3ba.TMP | text | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF13f36c.TMP | text | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF13f56f.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
59
DNS requests
39
Threats
292
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3140 | chrome.exe | GET | 301 | 104.21.29.203:80 | http://faizabeauty.xyz/?s=29&q=Vysor-Pro-3-Crack---License-Key-Free-Download&g=aca1c2f40a043a5bbed47ef06e11d76f&mode= | US | — | — | suspicious |
2872 | metina_5.tmp | HEAD | 200 | 198.54.116.159:80 | http://cor-tips.com/After_math_Eminem/AdvertiserInstaller/UltraMediaBurner/UltraMediaBurner.exe | US | — | — | suspicious |
2224 | metina_6.exe | GET | — | 136.144.41.133:80 | http://136.144.41.133/WW/file2.exe | NL | — | — | malicious |
2872 | metina_5.tmp | GET | — | 198.54.116.159:80 | http://cor-tips.com/After_math_Eminem/AdvertiserInstaller/UltraMediaBurner/UltraMediaBurner.exe | US | — | — | suspicious |
2224 | metina_6.exe | GET | — | 185.156.177.26:80 | http://privacytoolsforyou.xyz/downloads/toolspab2.exe | RU | — | — | suspicious |
2664 | metina_4.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | text | 255 b | malicious |
3140 | chrome.exe | GET | 200 | 54.190.206.20:80 | http://54.190.206.20/favicon.ico | US | text | 106 b | unknown |
3140 | chrome.exe | GET | 302 | 54.190.206.20:80 | http://54.190.206.20/?t=29&q=Vysor-Pro-3-Crack---License-Key-Free-Download&dedica=&2ea09d5ad88e3a7ab0b2ff88354f755cb900df08=59614c5088cd9973f8fccb781d21a6148c1f6923 | US | html | 19.0 Kb | unknown |
3140 | chrome.exe | POST | 200 | 54.190.206.20:80 | http://54.190.206.20/?go=af14c2f9ad6f7268c7419&dedica= | US | html | 647 b | unknown |
3140 | chrome.exe | POST | 200 | 54.190.206.20:80 | http://54.190.206.20/?cloudx=d1978ee6a7f953&dedica=&verify-id=29&verify-hash=7719a1c782a1ba91c031a682a0a2f8658209adbf&verify-msch=Vnlzb3ItUHJvLTMtQ3JhY2stLS1MaWNlbnNlLUtleS1GcmVlLURvd25sb2Fk&download=1&xtrans=MTM4 | US | compressed | 3.88 Mb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3140 | chrome.exe | 35.190.80.1:443 | a.nel.cloudflare.com | Google Inc. | US | suspicious |
3140 | chrome.exe | 104.21.29.203:80 | faizabeauty.xyz | Cloudflare Inc | US | suspicious |
3140 | chrome.exe | 142.250.185.109:443 | accounts.google.com | Google Inc. | US | suspicious |
3140 | chrome.exe | 104.21.30.103:443 | crackkits.com | Cloudflare Inc | US | unknown |
3140 | chrome.exe | 142.250.186.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 192.0.76.3:443 | stats.wp.com | Automattic, Inc | US | suspicious |
3140 | chrome.exe | 142.250.184.206:443 | clients1.google.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 142.250.185.195:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 104.16.18.94:80 | cdnjs.cloudflare.com | Cloudflare Inc | US | unknown |
3140 | chrome.exe | 54.190.206.20:80 | — | Amazon.com, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crackkits.com |
| malicious |
accounts.google.com |
| shared |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
stats.wp.com |
| whitelisted |
pixel.wp.com |
| whitelisted |
clients1.google.com |
| whitelisted |
href.li |
| shared |
frionene.xyz |
| unknown |
a.nel.cloudflare.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3140 | chrome.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
2576 | setup_install.exe | A Network Trojan was detected | AV TROJAN GCleaner Downloader CnC Activity |
2576 | setup_install.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
2664 | metina_4.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
2664 | metina_4.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
1052 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .cf Domain |
2872 | metina_5.tmp | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2224 | metina_6.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2224 | metina_6.exe | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
2224 | metina_6.exe | Misc activity | ET INFO Packed Executable Download |
81 ETPRO signatures available at the full report