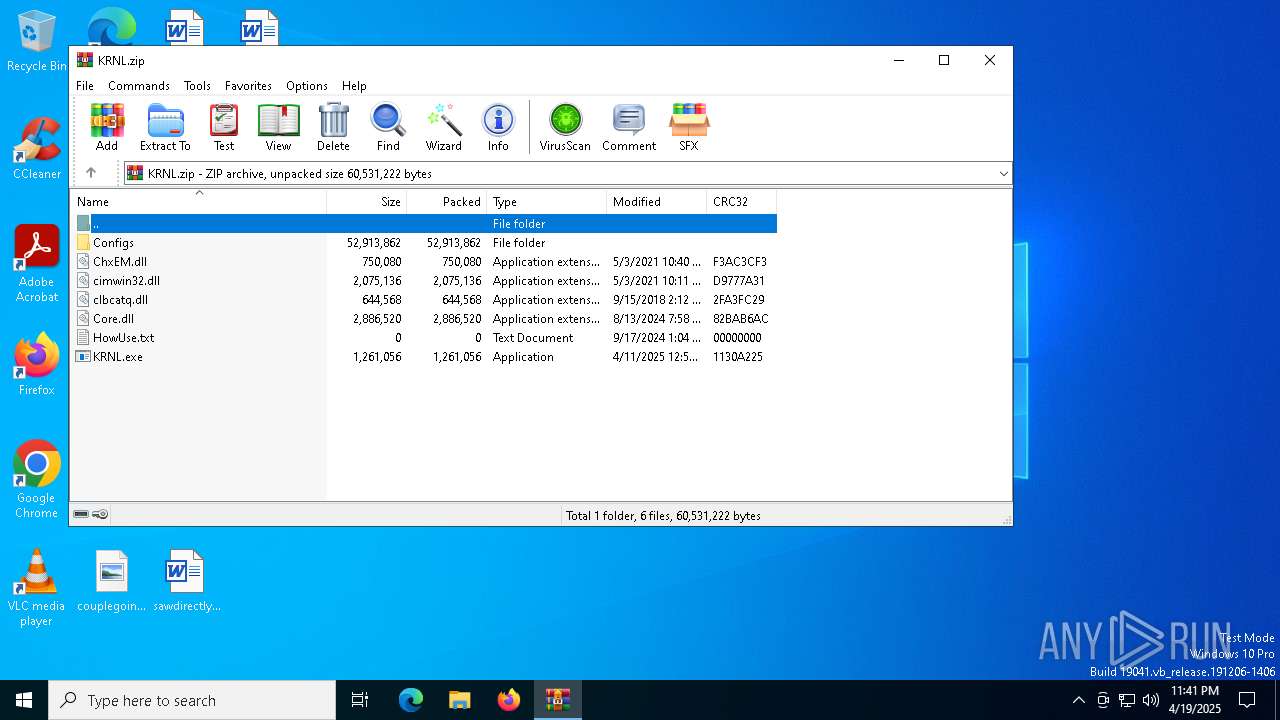
| File name: | KRNL.zip |
| Full analysis: | https://app.any.run/tasks/19ea1a36-747e-4ebc-86e9-80dbf33446c5 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 19, 2025, 23:41:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 2418997A184E92F82ED94C857F6ADE2E |
| SHA1: | AA8EDEFE6C216A1FFBD3165768E1437DDB0665EF |
| SHA256: | C867B143968CE0C887D458A945201772ADC3E538F914187B5E1BC0CD7055727C |
| SSDEEP: | 98304:egp5vXThProYZiIGr8+tcVKs9V4i2KvagCExvBxLQoJolqgl+ue04yFQDLQoJoli:5wIGr8WcSvNvCfN |
MALICIOUS
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 7604)
Connects to the CnC server
- svchost.exe (PID: 2196)
LUMMA mutex has been found
- MSBuild.exe (PID: 7604)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 7604)
LUMMA has been detected (YARA)
- MSBuild.exe (PID: 7604)
Steals credentials from Web Browsers
- MSBuild.exe (PID: 7604)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 7448)
Starts a Microsoft application from unusual location
- KRNL.exe (PID: 7584)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 7604)
Searches for installed software
- MSBuild.exe (PID: 7604)
There is functionality for taking screenshot (YARA)
- MSBuild.exe (PID: 7604)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7448)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 7448)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 7448)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 7448)
Reads the computer name
- MSBuild.exe (PID: 7604)
- MpCmdRun.exe (PID: 7984)
Checks supported languages
- MSBuild.exe (PID: 7604)
- KRNL.exe (PID: 7584)
- MpCmdRun.exe (PID: 7984)
Manual execution by a user
- KRNL.exe (PID: 7584)
Reads the software policy settings
- MSBuild.exe (PID: 7604)
- slui.exe (PID: 8056)
Reads the machine GUID from the registry
- MSBuild.exe (PID: 7604)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7448)
Create files in a temporary directory
- MpCmdRun.exe (PID: 7984)
Checks proxy server information
- slui.exe (PID: 8056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(7604) MSBuild.exe
C2 (9)changeaie.top/geps
easyupgw.live/eosz
soursopsf.run/gsoiao
xcelmodo.run/nahd
zestmodp.top/zeda
clarmodq.top/qoxo
liftally.top/xasj
salaccgfa.top/gsooz
upmodini.digital/gokk
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2021:05:03 22:40:10 |
| ZipCRC: | 0xf3ac3cf3 |
| ZipCompressedSize: | 750080 |
| ZipUncompressedSize: | 750080 |
| ZipFileName: | ChxEM.dll |
Total processes
127
Monitored processes
8
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7448 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\KRNL.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7584 | "C:\Users\admin\Desktop\KRNL.exe" | C:\Users\admin\Desktop\KRNL.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7604 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | KRNL.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
Lumma(PID) Process(7604) MSBuild.exe C2 (9)changeaie.top/geps easyupgw.live/eosz soursopsf.run/gsoiao xcelmodo.run/nahd zestmodp.top/zeda clarmodq.top/qoxo liftally.top/xasj salaccgfa.top/gsooz upmodini.digital/gokk | |||||||||||||||
| 7920 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR7448.45215\Rar$Scan24937.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7928 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7984 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR7448.45215" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8056 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 436
Read events
8 426
Write events
10
Delete events
0
Modification events
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\KRNL.zip | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
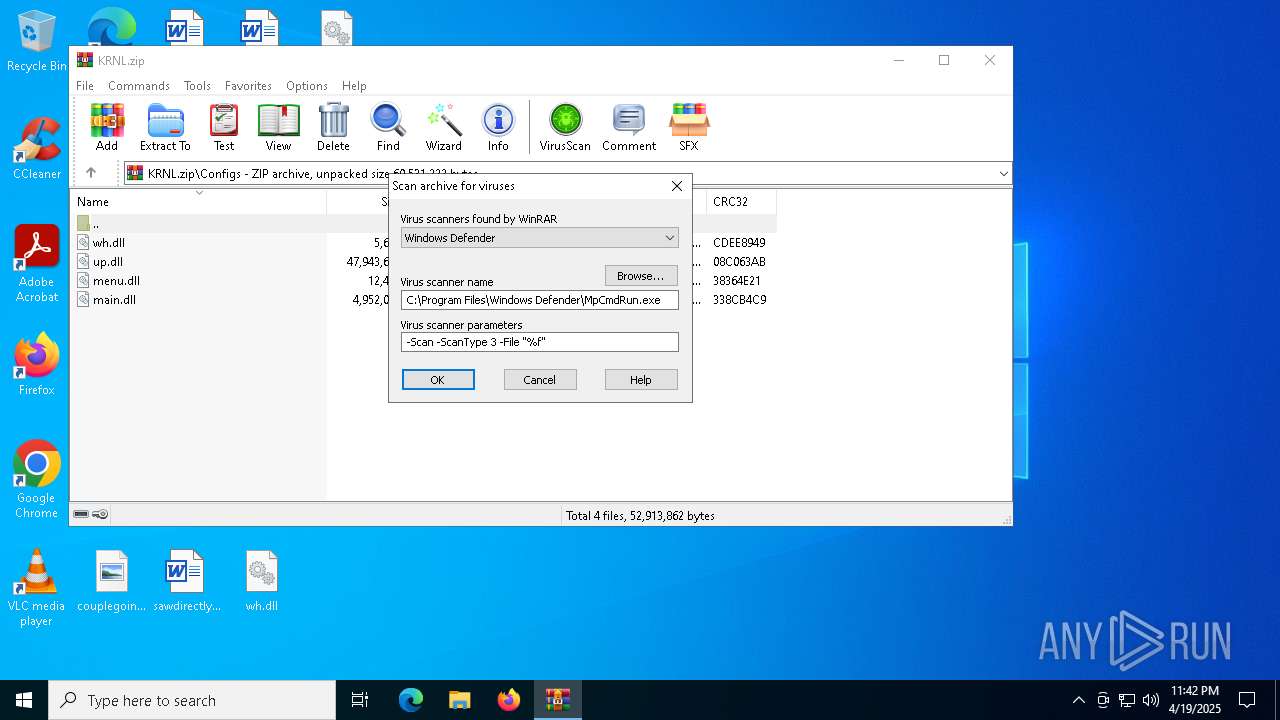
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
5
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7448.45215\KRNL.zip\Configs\up.dll | — | |
MD5:— | SHA256:— | |||
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7448.45215\KRNL.zip\Core.dll | text | |
MD5:3F79F1B8C67A57C6F87487DE138CCD3B | SHA256:53D32AA885F04F1FE0A3594298B8AE05540C826C5B4BA4720944E2B91D8B7608 | |||
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7448.45215\KRNL.zip\Configs\menu.dll | text | |
MD5:C9C78C96CD57E682CC633DF02483BDEF | SHA256:8E1254CD6D363EB52633D7591ED8FED6779067370C52784814ACF09A5A485ADE | |||
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7448.45215\KRNL.zip\cimwin32.dll | executable | |
MD5:98F5C44CCE00EF0FAD189CA8B0B512EE | SHA256:58A3059D120FCB1E304F311749234FD11533FCCE6706ECAC8F5CEBA8754B5D64 | |||
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7448.45215\KRNL.zip\ChxEM.dll | executable | |
MD5:5ECB27B7EF6A5DC2BB158AFAC448CEBA | SHA256:772EE2CD6461DA4D13AC3F3AAD595E137015447ED500B686B5604B9207A02751 | |||
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7448.45215\KRNL.zip\clbcatq.dll | executable | |
MD5:12112113BDFAF0CC03517604440217D5 | SHA256:C5D4F3DFA14DEABD6A845E6F0B04C39A9A539C1A4D6C71B25943EB9BF9C9A3F5 | |||
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7448.45215\KRNL.zip\Configs\main.dll | executable | |
MD5:96D2A1BFBE79B68678B78017BF4CA532 | SHA256:5E97D896A427313467F598567F4DD60AFC891F6B516FAF3FC8D6379A7DF40DE4 | |||
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7448.45215\KRNL.zip\KRNL.exe | executable | |
MD5:6342FC6D0CF20BCE8AA903A8CE8AF369 | SHA256:A1B3164E0327A2EE19171DEBC62D31C5665F81923589E6424CEA08A801D1DF48 | |||
| 7984 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | binary | |
MD5:82409DB98897B478D7BE10941234DC2D | SHA256:BF0948FA15FCC8793179543D891BAE6B96F4960550CDB04C22E54D7A5BEC2ABB | |||
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7448.45215\Rar$Scan24937.bat | text | |
MD5:FF7E1430C8D93ED03E646722332BF981 | SHA256:1A8B04B93A84FF9E6B9EEAF16559E0D6E617234BCF040E4EB9C458B988BF573D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
50
DNS requests
14
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
7812 | SIHClient.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7812 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
7812 | SIHClient.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 20.3.187.198:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
7812 | SIHClient.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
7812 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7812 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7812 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7604 | MSBuild.exe | 104.21.85.126:443 | clarmodq.top | CLOUDFLARENET | — | malicious |
7812 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7812 | SIHClient.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7812 | SIHClient.exe | 23.38.73.129:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
clarmodq.top |
| malicious |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected Domain Associated with Malware Distribution (clarmodq .top) |
7604 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (clarmodq .top) |
7604 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
7604 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
7604 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
7604 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
7604 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |