| File name: | game.exe |
| Full analysis: | https://app.any.run/tasks/0e96b518-e446-4d40-9db7-0bf4c7d1591c |
| Verdict: | Malicious activity |
| Threats: | Chaos ransomware is a malware family known for its destructive capabilities and diverse variants. It first appeared in 2021 as a ransomware builder and later acted as a wiper. Unlike most ransomware strains that encrypt data to extort payment, early Chaos variants permanently corrupted files, while later versions adopted more conventional encryption techniques. |
| Analysis date: | June 21, 2025, 18:17:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 8536FA1FE6C23759BA25BAD70155145D |
| SHA1: | 66EE059092E55BE43DC11C67F448AE8467525A30 |
| SHA256: | C8269B6919B50F1400134E84D343E70C886C024A6E9282463832D81815195897 |
| SSDEEP: | 384:5kI0QP86k3GbneeUD5bb0reJEY8fVQ3F:5kBQP50Gqn5bmwNEVe |
MALICIOUS
Create files in the Startup directory
- svchost.exe (PID: 4888)
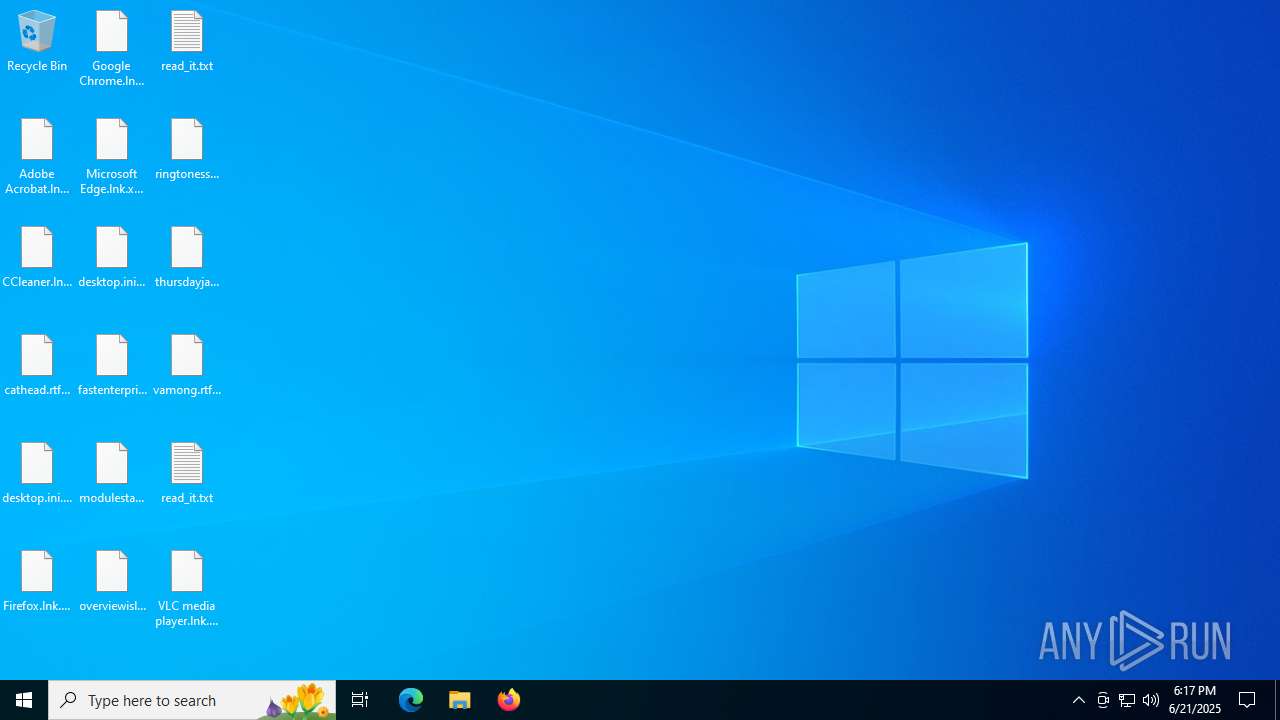
Renames files like ransomware
- svchost.exe (PID: 4888)
RANSOMWARE has been detected
- svchost.exe (PID: 4888)
CHAOS has been detected (YARA)
- svchost.exe (PID: 4888)
Deletes shadow copies
- cmd.exe (PID: 3836)
- cmd.exe (PID: 2792)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 5080)
SUSPICIOUS
The process creates files with name similar to system file names
- game.exe (PID: 1560)
Reads security settings of Internet Explorer
- game.exe (PID: 1560)
- svchost.exe (PID: 4888)
Executable content was dropped or overwritten
- game.exe (PID: 1560)
Reads the date of Windows installation
- game.exe (PID: 1560)
- svchost.exe (PID: 4888)
Starts itself from another location
- game.exe (PID: 1560)
Write to the desktop.ini file (may be used to cloak folders)
- svchost.exe (PID: 4888)
Found regular expressions for crypto-addresses (YARA)
- svchost.exe (PID: 4888)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 4888)
Executes as Windows Service
- VSSVC.exe (PID: 5928)
- wbengine.exe (PID: 6672)
- vds.exe (PID: 5904)
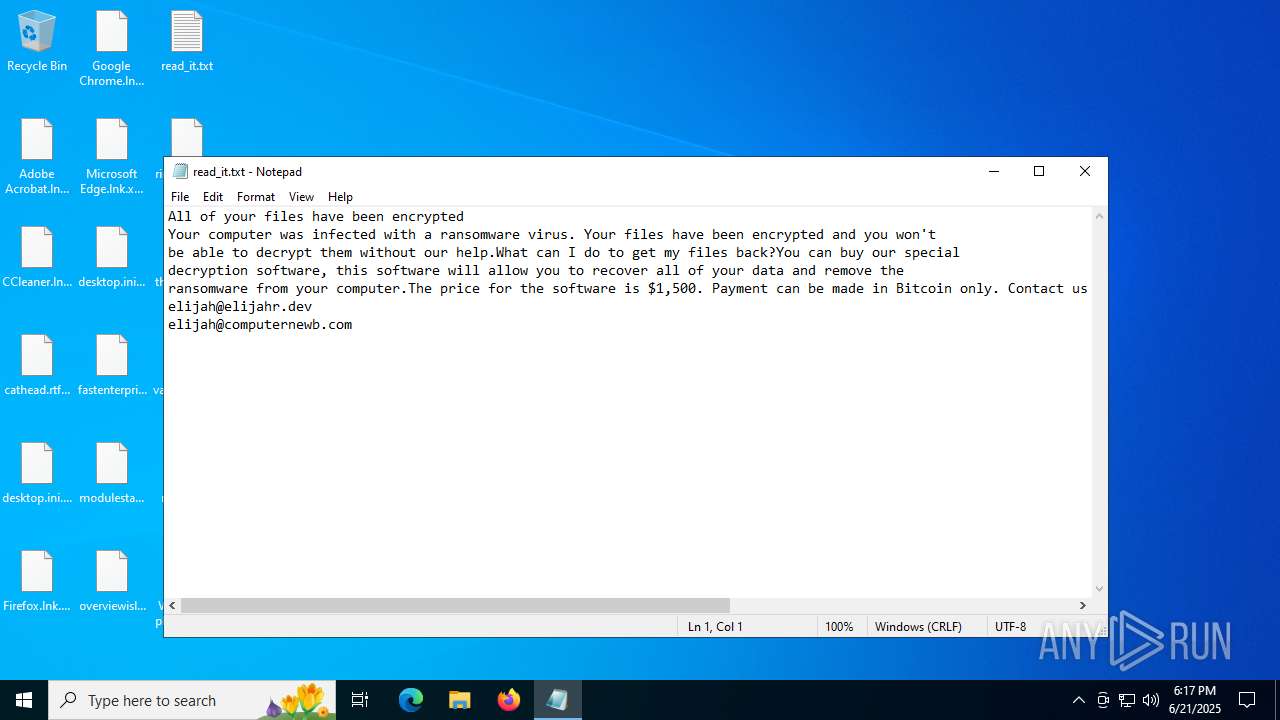
Start notepad (likely ransomware note)
- svchost.exe (PID: 4888)
INFO
Reads the computer name
- game.exe (PID: 1560)
- svchost.exe (PID: 4888)
Reads Environment values
- game.exe (PID: 1560)
- svchost.exe (PID: 4888)
Checks supported languages
- game.exe (PID: 1560)
- svchost.exe (PID: 4888)
Checks proxy server information
- game.exe (PID: 1560)
- svchost.exe (PID: 4888)
- slui.exe (PID: 5720)
Reads the machine GUID from the registry
- game.exe (PID: 1560)
- svchost.exe (PID: 4888)
Creates files or folders in the user directory
- game.exe (PID: 1560)
- svchost.exe (PID: 4888)
Disables trace logs
- game.exe (PID: 1560)
- svchost.exe (PID: 4888)
Reads the software policy settings
- game.exe (PID: 1560)
- svchost.exe (PID: 4888)
- slui.exe (PID: 5720)
Process checks computer location settings
- game.exe (PID: 1560)
- svchost.exe (PID: 4888)
Launching a file from the Startup directory
- svchost.exe (PID: 4888)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1068)
- notepad.exe (PID: 5496)
Reads Microsoft Office registry keys
- svchost.exe (PID: 4888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:06:21 16:58:37+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 20992 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x706e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | game.exe |
| LegalCopyright: | |
| OriginalFileName: | game.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
176
Monitored processes
21
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 684 | C:\WINDOWS\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Loader Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | wmic shadowcopy delete | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1560 | "C:\Users\admin\AppData\Local\Temp\game.exe" | C:\Users\admin\AppData\Local\Temp\game.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 1 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2220 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2368 | wbadmin delete catalog -quiet | C:\Windows\System32\wbadmin.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® BLB Backup Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2792 | "C:\Windows\System32\cmd.exe" /C wbadmin delete catalog -quiet | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3768 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 3836 | "C:\Windows\System32\cmd.exe" /C vssadmin delete shadows /all /quiet & wmic shadowcopy delete | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4156 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4520 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 986
Read events
6 937
Write events
31
Delete events
18
Modification events
| (PID) Process: | (1560) game.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\game_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1560) game.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\game_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1560) game.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\game_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1560) game.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\game_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1560) game.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\game_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1560) game.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\game_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1560) game.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\game_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1560) game.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\game_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1560) game.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\game_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1560) game.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\game_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
1
Suspicious files
1
Text files
610
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1560 | game.exe | C:\Users\admin\AppData\Roaming\svchost.exe | executable | |
MD5:8536FA1FE6C23759BA25BAD70155145D | SHA256:C8269B6919B50F1400134E84D343E70C886C024A6E9282463832D81815195897 | |||
| 4888 | svchost.exe | C:\Users\admin\Desktop\read_it.txt | text | |
MD5:7059210FB852321B5E82F6FAD379CDCB | SHA256:A16E064B66C20714F483EE277B6EBF1EE707D09EDC920971EA39B9A1FCC41949 | |||
| 4888 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svchost.url | binary | |
MD5:83660DEB1A47E0B191FDA82BDFD61827 | SHA256:87089BD6FEDDA43B5E4D738B5BF246BA1B2E5C248B9220F0D1E742B827F30B0D | |||
| 4888 | svchost.exe | C:\Users\admin\Desktop\desktop.ini.uese | text | |
MD5:BF3AAFBBDCF3EFF9B594874AF32B74D7 | SHA256:4A3A5DD8827371EB047BACF1B63C6AF7CBD873906C318FFB2B5B2E11651DBF5D | |||
| 4888 | svchost.exe | C:\Users\admin\Desktop\cathead.rtf | text | |
MD5:8A3050A274152ADC35639B26BBCBA578 | SHA256:1F9C4A287AF8A0C86F7CE77F7EF31A46C6710B7CF61D0282FFCA5894985257E0 | |||
| 4888 | svchost.exe | C:\Users\admin\Desktop\cathead.rtf.tt4f | text | |
MD5:8A3050A274152ADC35639B26BBCBA578 | SHA256:1F9C4A287AF8A0C86F7CE77F7EF31A46C6710B7CF61D0282FFCA5894985257E0 | |||
| 4888 | svchost.exe | C:\Users\admin\Desktop\fastenterprise.rtf | text | |
MD5:4F9A3643B967B5DF840C2EBAE73A3FFB | SHA256:50C6630907803FD268DB676DBA328782CF80DCC48D20FABEE29BCFA7142716AA | |||
| 4888 | svchost.exe | C:\Users\admin\Desktop\desktop.ini | text | |
MD5:BF3AAFBBDCF3EFF9B594874AF32B74D7 | SHA256:4A3A5DD8827371EB047BACF1B63C6AF7CBD873906C318FFB2B5B2E11651DBF5D | |||
| 4888 | svchost.exe | C:\Users\admin\Desktop\overviewislands.png | text | |
MD5:C57FCEE15F9BC7AF6F560D0F87FD5365 | SHA256:EAD902C980DFFE0AFD39D3CA3F68B18BDEFBE6E5F23AB05B016F6BEB307D0F1E | |||
| 4888 | svchost.exe | C:\Users\admin\Desktop\modulestar.jpg.1l76 | text | |
MD5:DE43DD0B9FBC51BD09DE1FA3A5988174 | SHA256:903EF4E09D9CA56987F677CF30DDF743E4CF0900CAF1B5EBAF176B6F643E54DE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
48
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5628 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
2596 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1984 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1984 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6672 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1560 | game.exe | 104.26.3.158:443 | computernewb.com | CLOUDFLARENET | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4888 | svchost.exe | 104.26.3.158:443 | computernewb.com | CLOUDFLARENET | US | whitelisted |
2596 | svchost.exe | 20.190.159.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2596 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
computernewb.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
wbadmin.exe | Invalid parameter passed to C runtime function.
|