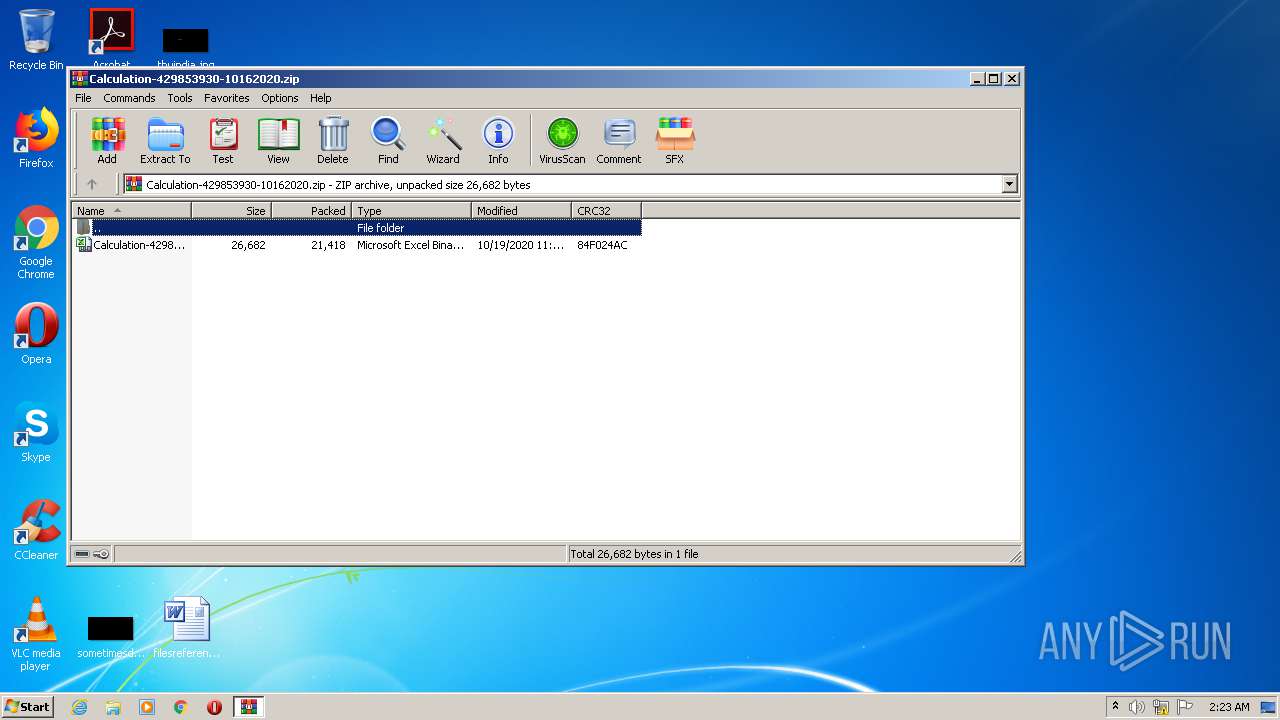
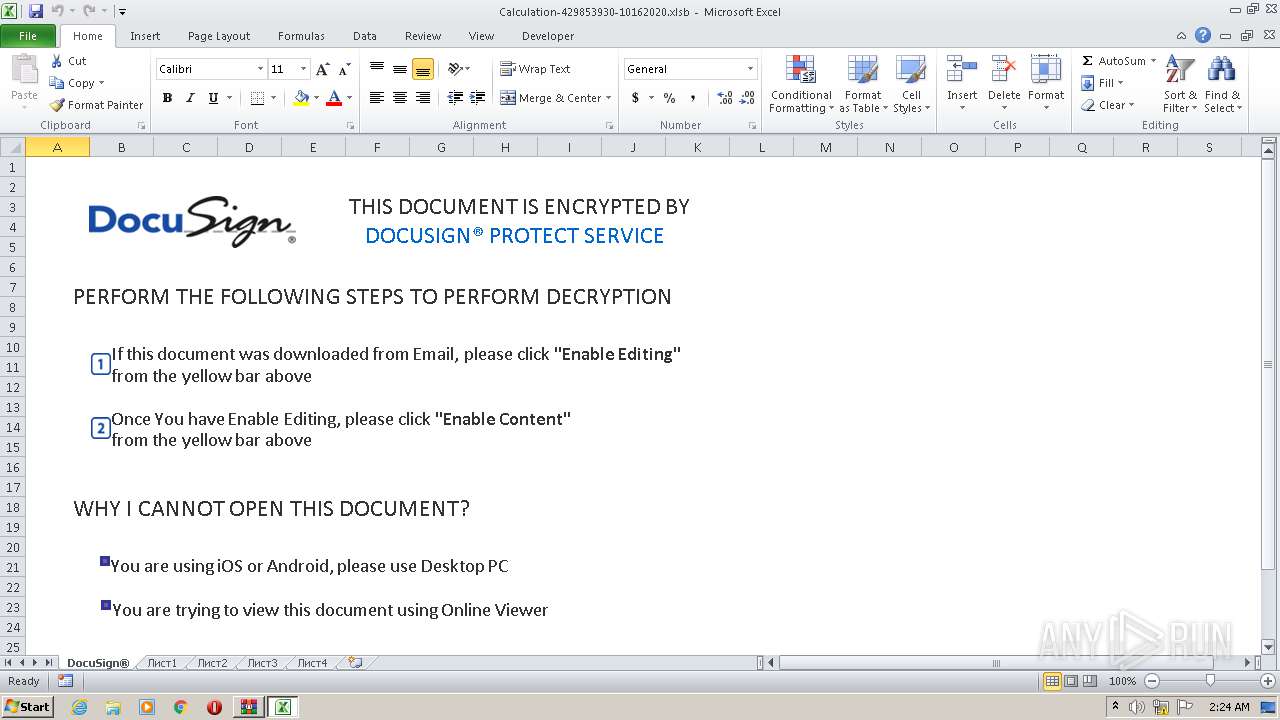
| File name: | Calculation-429853930-10162020.zip |
| Full analysis: | https://app.any.run/tasks/50abd3d4-de88-4aff-92ae-77510f6c38e0 |
| Verdict: | Malicious activity |
| Threats: | Qbot is a banking Trojan — a malware designed to collect banking information from victims. Qbot targets organizations mostly in the US. It is equipped with various sophisticated evasion and info-stealing functions and worm-like functionality, and a strong persistence mechanism. |
| Analysis date: | October 20, 2020, 01:23:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 1032B66E61B9DEC680F6BC40A82FC9C6 |
| SHA1: | DF82525963C2E087B0B33523362B5869602A6972 |
| SHA256: | C7F9E84F21F171642F89DAD8EE778E9E0094AC24253AB81BBEF2120F4AFC7FE4 |
| SSDEEP: | 384:8gGk+KFME6e7jjoZUUqxQ7p4teW38AB0rXw2bPvVK3ZHxzWt7RKI/B2rqieO:7VFMM7wZUUwqWMMyXvbQ3ZRz+0IQqXO |
MALICIOUS
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 1960)
Executable content was dropped or overwritten
- EXCEL.EXE (PID: 1960)
Application was dropped or rewritten from another process
- nosto.exe (PID: 3928)
- nosto.exe (PID: 2096)
- ytfovlym.exe (PID: 3396)
- ytfovlym.exe (PID: 1864)
QBOT was detected
- nosto.exe (PID: 3928)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 3932)
SUSPICIOUS
Starts Microsoft Office Application
- WinRAR.exe (PID: 1932)
Application launched itself
- nosto.exe (PID: 3928)
- ytfovlym.exe (PID: 3396)
Creates files in the user directory
- nosto.exe (PID: 3928)
Executable content was dropped or overwritten
- nosto.exe (PID: 3928)
- cmd.exe (PID: 3932)
Starts itself from another location
- nosto.exe (PID: 3928)
Starts CMD.EXE for commands execution
- nosto.exe (PID: 3928)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 1960)
Reads Internet Cache Settings
- EXCEL.EXE (PID: 1960)
Creates files in the user directory
- EXCEL.EXE (PID: 1960)
Dropped object may contain Bitcoin addresses
- cmd.exe (PID: 3932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:10:19 16:24:17 |
| ZipCRC: | 0x84f024ac |
| ZipCompressedSize: | 21418 |
| ZipUncompressedSize: | 26682 |
| ZipFileName: | Calculation-429853930-10162020.xlsb |
Total processes
43
Monitored processes
9
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1864 | C:\Users\admin\AppData\Roaming\Microsoft\Zulycjadyc\ytfovlym.exe /C | C:\Users\admin\AppData\Roaming\Microsoft\Zulycjadyc\ytfovlym.exe | — | ytfovlym.exe | |||||||||||
User: admin Company: QIHU 360 SOFTWARE CO. LIMITED Integrity Level: MEDIUM Description: 360 SystemRegistryClean Exit code: 0 Version: 1, 0, 0, 1003 Modules
| |||||||||||||||
| 1932 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Calculation-429853930-10162020.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1960 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2096 | C:\Hromo\Nivadalo\nosto.exe /C | C:\Hromo\Nivadalo\nosto.exe | — | nosto.exe | |||||||||||
User: admin Company: QIHU 360 SOFTWARE CO. LIMITED Integrity Level: MEDIUM Description: 360 SystemRegistryClean Exit code: 0 Version: 1, 0, 0, 1003 Modules
| |||||||||||||||
| 3396 | C:\Users\admin\AppData\Roaming\Microsoft\Zulycjadyc\ytfovlym.exe | C:\Users\admin\AppData\Roaming\Microsoft\Zulycjadyc\ytfovlym.exe | — | nosto.exe | |||||||||||
User: admin Company: QIHU 360 SOFTWARE CO. LIMITED Integrity Level: MEDIUM Description: 360 SystemRegistryClean Exit code: 0 Version: 1, 0, 0, 1003 Modules
| |||||||||||||||
| 3768 | ping.exe -n 6 127.0.0.1 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3928 | "C:\Hromo\Nivadalo\nosto.exe" | C:\Hromo\Nivadalo\nosto.exe | EXCEL.EXE | ||||||||||||
User: admin Company: QIHU 360 SOFTWARE CO. LIMITED Integrity Level: MEDIUM Description: 360 SystemRegistryClean Exit code: 0 Version: 1, 0, 0, 1003 Modules
| |||||||||||||||
| 3932 | "C:\Windows\System32\cmd.exe" /c ping.exe -n 6 127.0.0.1 & type "C:\Windows\System32\calc.exe" > "C:\Hromo\Nivadalo\nosto.exe" | C:\Windows\System32\cmd.exe | nosto.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 4032 | C:\Windows\explorer.exe | C:\Windows\explorer.exe | — | ytfovlym.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 149
Read events
1 083
Write events
55
Delete events
11
Modification events
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Calculation-429853930-10162020.zip | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | EXCELFiles |
Value: 1364459553 | |||
| (PID) Process: | (1960) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | ~l; |
Value: 7E6C3B00A8070000010000000000000000000000 | |||
Executable files
4
Suspicious files
4
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1960 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR6C5E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1932 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa1932.36724\Calculation-429853930-10162020.xlsb | document | |
MD5:— | SHA256:— | |||
| 1960 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\C5KEP792.txt | text | |
MD5:— | SHA256:— | |||
| 3928 | nosto.exe | C:\Users\admin\AppData\Roaming\Microsoft\Zulycjadyc\ytfovlym.exe | executable | |
MD5:— | SHA256:— | |||
| 1960 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\3415201[1].png | executable | |
MD5:— | SHA256:— | |||
| 1960 | EXCEL.EXE | C:\Hromo\Nivadalo\nosto.exe | executable | |
MD5:— | SHA256:— | |||
| 3928 | nosto.exe | C:\Users\admin\AppData\Roaming\Microsoft\Zulycjadyc\ytfovlym.dat | binary | |
MD5:— | SHA256:— | |||
| 4032 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Zulycjadyc\ytfovlym.dat | binary | |
MD5:— | SHA256:— | |||
| 3932 | cmd.exe | C:\Hromo\Nivadalo\nosto.exe | executable | |
MD5:60B7C0FEAD45F2066E5B805A91F4F0FC | SHA256:80C10EE5F21F92F89CBC293A59D2FD4C01C7958AACAD15642558DB700943FA22 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1960 | EXCEL.EXE | GET | 200 | 104.27.183.167:80 | http://cinefreak.info/dzvkbppmkym/3415201.png | US | executable | 1.02 Mb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1960 | EXCEL.EXE | 104.27.183.167:80 | cinefreak.info | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cinefreak.info |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1960 | EXCEL.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1960 | EXCEL.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from MSXMLHTTP non-exe extension M2 |
1960 | EXCEL.EXE | A Network Trojan was detected | ET TROJAN JS/WSF Downloader Dec 08 2016 M4 |
1960 | EXCEL.EXE | A Network Trojan was detected | AV POLICY EXE or DLL in HTTP Image Content Inbound - Likely Malicious |
1960 | EXCEL.EXE | Misc activity | ET INFO EXE - Served Attached HTTP |
1960 | EXCEL.EXE | Misc activity | SUSPICIOUS [PTsecurity] PE as Image Content type mismatch |