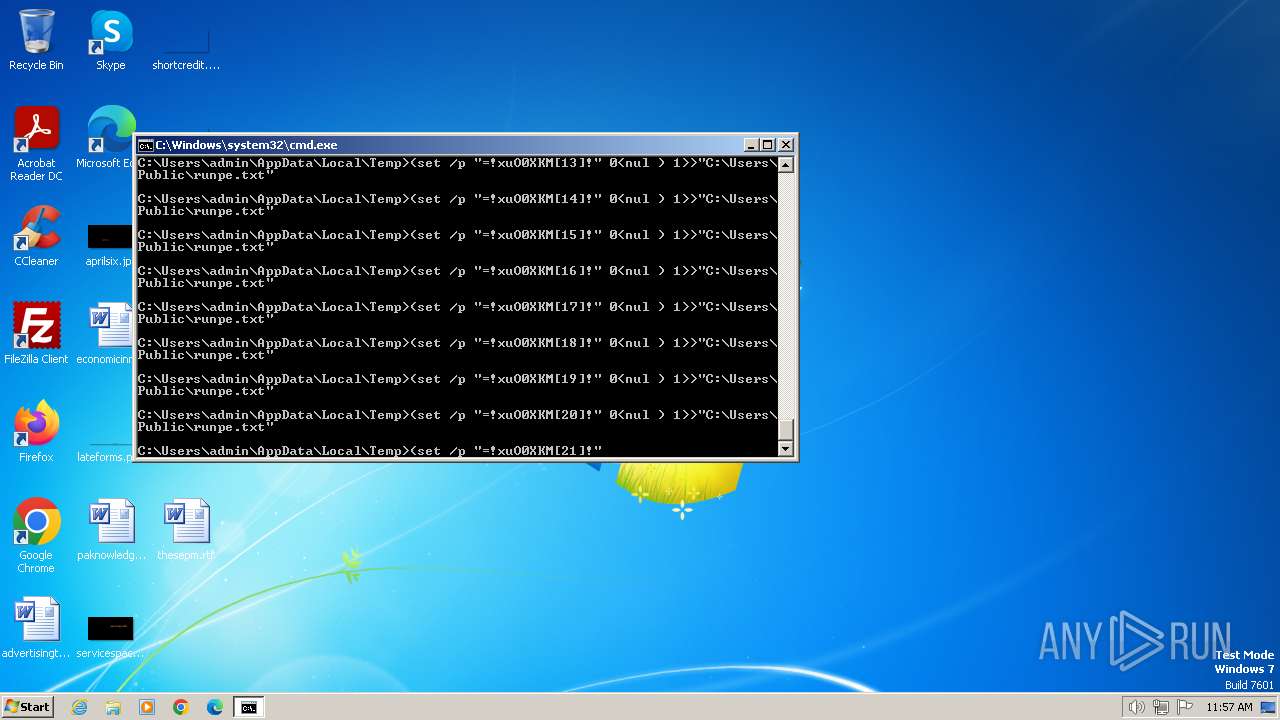
| File name: | ty.bat |
| Full analysis: | https://app.any.run/tasks/b32c12e3-1d80-492f-be8f-00784073e4f9 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | April 08, 2024, 10:57:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 945FED7A19341B8B4E30BF66FE1B2F52 |
| SHA1: | 818BBD3DA4483F5B62306BDFF1F4FB098C444196 |
| SHA256: | C7A0052E565AD38F3CE40D85F05664EB5FB32A22C2670AD758DA35B416DFAF27 |
| SSDEEP: | 1536:fBv3k0z5ZKK9nyk4YSZzCp82Y3FozTZvsLQJGVTGb37b+YsXkrfq1tAtG3rHodnv:d3P82Y3FozTZYJhWm88m |
MALICIOUS
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 292)
- cmd.exe (PID: 2320)
- cmd.exe (PID: 2424)
Bypass execution policy to execute commands
- powershell.exe (PID: 4040)
- powershell.exe (PID: 2804)
- powershell.exe (PID: 3260)
ASYNCRAT has been detected (MUTEX)
- aspnet_compiler.exe (PID: 4044)
- aspnet_compiler.exe (PID: 3028)
- aspnet_compiler.exe (PID: 3192)
ASYNCRAT has been detected (YARA)
- aspnet_compiler.exe (PID: 4044)
Actions looks like stealing of personal data
- aspnet_compiler.exe (PID: 4044)
SUSPICIOUS
Reads the Internet Settings
- cmd.exe (PID: 2340)
- wscript.exe (PID: 4020)
- wscript.exe (PID: 3832)
- aspnet_compiler.exe (PID: 4044)
- wscript.exe (PID: 1308)
- wscript.exe (PID: 664)
The process executes JS scripts
- cmd.exe (PID: 2340)
Executing commands from a ".bat" file
- wscript.exe (PID: 3832)
- wscript.exe (PID: 4020)
- wscript.exe (PID: 1308)
- wscript.exe (PID: 664)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 3832)
- wscript.exe (PID: 4020)
- wscript.exe (PID: 1308)
- wscript.exe (PID: 664)
Likely accesses (executes) a file from the Public directory
- wscript.exe (PID: 3832)
- wscript.exe (PID: 4020)
- cmd.exe (PID: 2836)
- cmd.exe (PID: 292)
- powershell.exe (PID: 4040)
- powershell.exe (PID: 2476)
- powershell.exe (PID: 2804)
- wscript.exe (PID: 1308)
- cmd.exe (PID: 2320)
- wscript.exe (PID: 664)
- cmd.exe (PID: 2424)
- powershell.exe (PID: 3260)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3832)
- wscript.exe (PID: 4020)
- wscript.exe (PID: 1308)
- wscript.exe (PID: 664)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 292)
- cmd.exe (PID: 2836)
- cmd.exe (PID: 2320)
- cmd.exe (PID: 2424)
The process executes Powershell scripts
- cmd.exe (PID: 292)
- cmd.exe (PID: 2320)
- cmd.exe (PID: 2424)
Creates a scheduled task using COM
- powershell.exe (PID: 2476)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 4040)
- powershell.exe (PID: 2804)
- powershell.exe (PID: 3260)
Connects to unusual port
- aspnet_compiler.exe (PID: 4044)
Reads settings of System Certificates
- aspnet_compiler.exe (PID: 4044)
The process executes via Task Scheduler
- wscript.exe (PID: 1308)
- wscript.exe (PID: 664)
INFO
Gets data length (POWERSHELL)
- powershell.exe (PID: 4040)
- powershell.exe (PID: 2804)
- powershell.exe (PID: 3260)
Checks supported languages
- aspnet_compiler.exe (PID: 4044)
- aspnet_compiler.exe (PID: 3028)
- aspnet_compiler.exe (PID: 3192)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 4040)
- powershell.exe (PID: 2804)
- powershell.exe (PID: 3260)
Reads the machine GUID from the registry
- aspnet_compiler.exe (PID: 4044)
- aspnet_compiler.exe (PID: 3028)
- aspnet_compiler.exe (PID: 3192)
Reads the computer name
- aspnet_compiler.exe (PID: 4044)
- aspnet_compiler.exe (PID: 3028)
- aspnet_compiler.exe (PID: 3192)
Reads Environment values
- aspnet_compiler.exe (PID: 4044)
Reads the software policy settings
- aspnet_compiler.exe (PID: 4044)
Create files in a temporary directory
- aspnet_compiler.exe (PID: 4044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(4044) aspnet_compiler.exe
C2 (1)5ra.webredirect.org
Ports (1)70
Botnetssss
VersionAWS | 3Losh
Options
AutoRunfalse
MutexAsyncMutex_alosh
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignatureK1BUq5QVwMX4HSAeMk2eI5AdugvzNLeIrimEJyLkZGEqHoYCiw8wSdjKisV1TDUghX4TjTuC7Re/MSdqemR49IHe6Z6OpjaqEoOi3E29xHK3emjiDmSFnYOJP2+zVjG3zvUpcsv7XkW6f+8PyFZIr72H5owh+ZmN6L4fMap1zzLYbt7OLfApR3/bET05oJm85+Y2CEZr7hXBiG/V53QU155RTHdUnqJsJdKK+6pOS5zqZwauuwnnfvI2bJ/pg9ZLdAlrRfC6NIOuYLnH52C36Wn0xKqj1k3OzDAZjIU0hHML...
Keys
AEScdd6ae0a4ae911d3f93672d3f9bfb815f4c55e8df82a3fcb8b8d196faeea619e
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Total processes
93
Monitored processes
16
Malicious processes
10
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | C:\Windows\system32\cmd.exe /c ""C:\Users\Public\run.bat" C:\Users\Public\" | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 664 | C:\Windows\System32\WScript.exe "C:\Users\Public\app.js" | C:\Windows\System32\wscript.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1308 | C:\Windows\System32\WScript.exe "C:\Users\Public\app.js" | C:\Windows\System32\wscript.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2320 | C:\Windows\system32\cmd.exe /c ""C:\Users\Public\run.bat" C:\Users\Public\" | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2340 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\ty.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2424 | C:\Windows\system32\cmd.exe /c ""C:\Users\Public\run.bat" C:\Users\Public\" | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2476 | PowerShell -Command "$tr = New-Object -ComObject Schedule.Service; $tr.Connect(); $ta = $tr.NewTask(0); $ta.RegistrationInfo.Description = 'Runs a script every 2 minutes'; $ta.Settings.Enabled = $true; $ta.Settings.DisallowStartIfOnBatteries = $false; $st = $ta.Triggers.Create(1); $st.StartBoundary = [DateTime]::Now.ToString('yyyy-MM-ddTHH:mm:ss'); $st.Repetition.Interval = 'PT2M'; $md = $ta.Actions.Create(0); $md.Path = 'C:\Users\Public\app.js'; $ns = $tr.GetFolder('\'); $ns.RegisterTaskDefinition('BTime', $ta, 6, $null, $null, 3);" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2804 | Powershell.exe -ExecutionPolicy Bypass -File "C:\Users\Public\run.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2836 | C:\Windows\system32\cmd.exe /c ""C:\Users\Public\node.bat" C:\Users\Public\" | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3028 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_compiler.exe Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
Total events
15 785
Read events
15 695
Write events
90
Delete events
0
Modification events
| (PID) Process: | (2340) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2340) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2340) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2340) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3832) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3832) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3832) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3832) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4020) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4020) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
9
Text files
17
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2340 | cmd.exe | C:\Users\Public\byet.txt | text | |
MD5:— | SHA256:— | |||
| 2340 | cmd.exe | C:\Users\Public\run.ps1 | text | |
MD5:— | SHA256:— | |||
| 2340 | cmd.exe | C:\Users\Public\app.js | text | |
MD5:— | SHA256:— | |||
| 2340 | cmd.exe | C:\Users\Public\basta.js | text | |
MD5:— | SHA256:— | |||
| 2340 | cmd.exe | C:\Users\Public\node.bat | text | |
MD5:— | SHA256:— | |||
| 2340 | cmd.exe | C:\Users\Public\run.bat | text | |
MD5:— | SHA256:— | |||
| 2340 | cmd.exe | C:\Users\Public\ali1.txt | text | |
MD5:— | SHA256:— | |||
| 2340 | cmd.exe | C:\Users\Public\ali3.txt | text | |
MD5:— | SHA256:— | |||
| 2340 | cmd.exe | C:\Users\Public\ali4.txt | text | |
MD5:— | SHA256:— | |||
| 2340 | cmd.exe | C:\Users\Public\Execute.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
9
DNS requests
5
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4044 | aspnet_compiler.exe | GET | — | 23.36.76.161:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?42edeb9f357a2990 | unknown | — | — | unknown |
4044 | aspnet_compiler.exe | GET | 200 | 173.222.108.226:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?5a58c5d49dcd53d9 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4044 | aspnet_compiler.exe | 149.102.147.106:70 | 5ra.webredirect.org | Contabo GmbH | GB | unknown |
4044 | aspnet_compiler.exe | 23.36.76.161:80 | ctldl.windowsupdate.com | Akamai International B.V. | NO | unknown |
4044 | aspnet_compiler.exe | 173.222.108.226:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
5ra.webredirect.org |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.webredirect .org Domain |
— | — | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.webredirect .org Domain |
— | — | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
— | — | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
— | — | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
— | — | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.webredirect .org Domain |