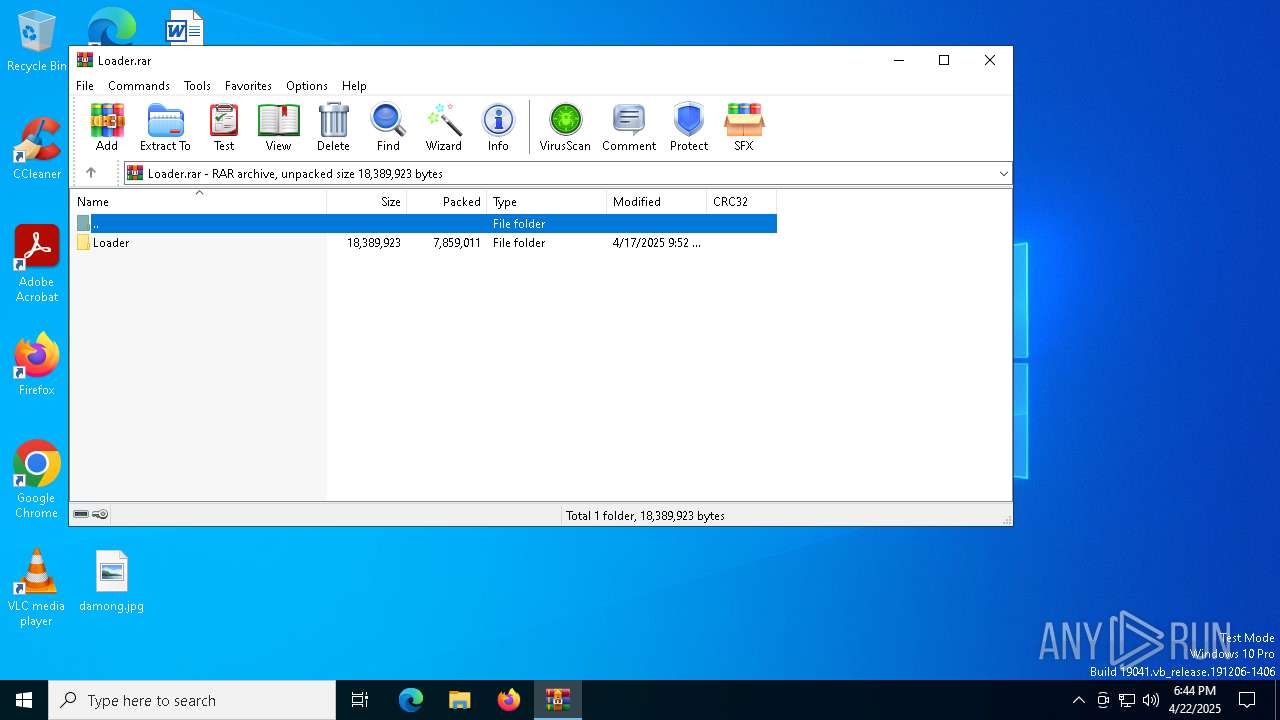
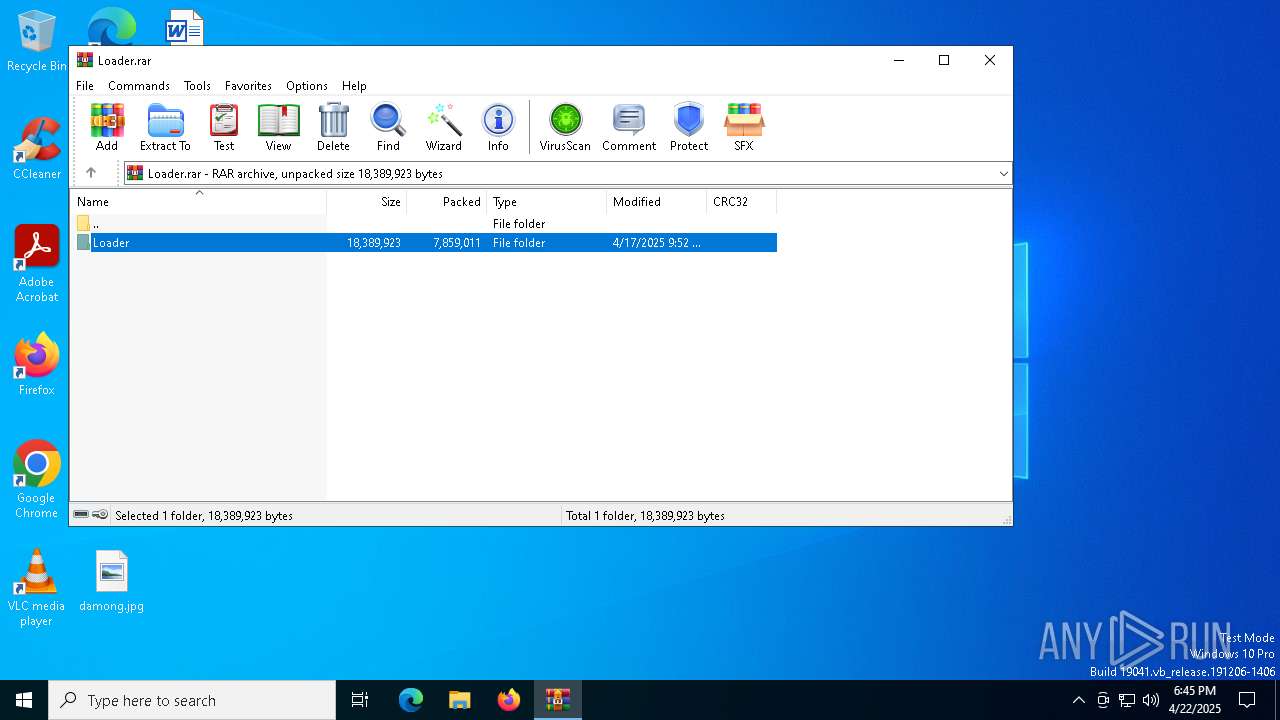
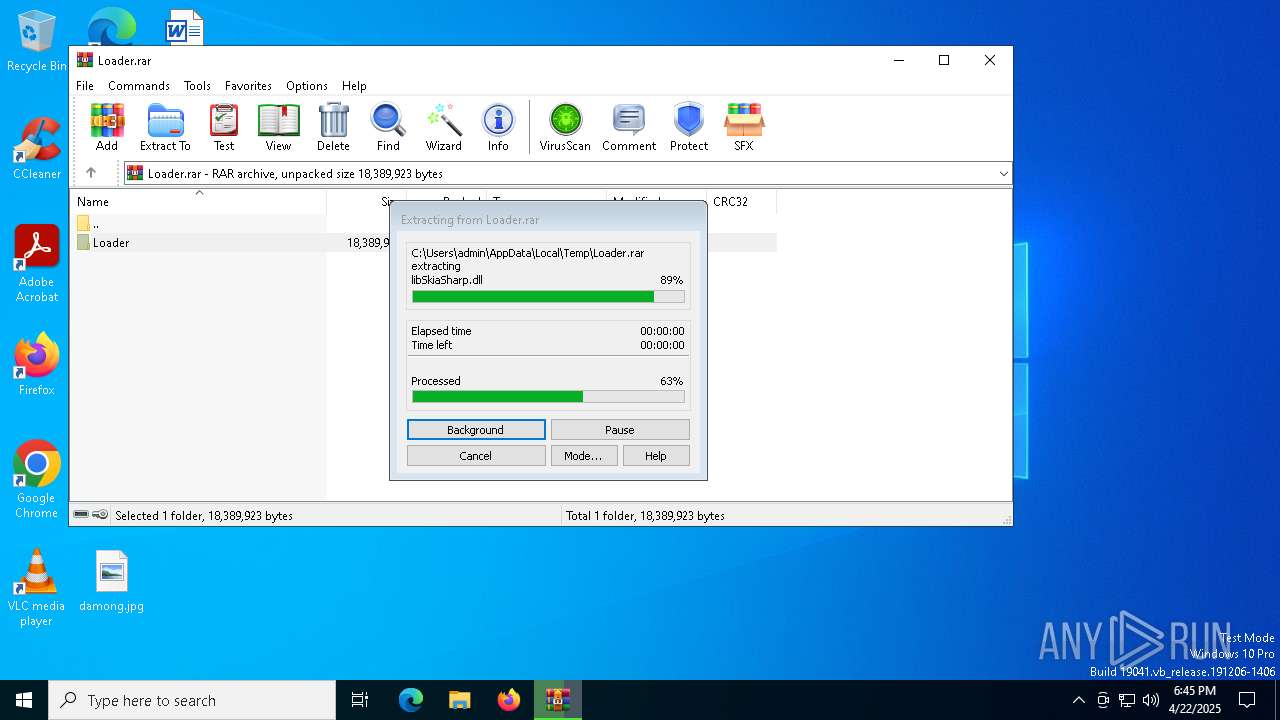
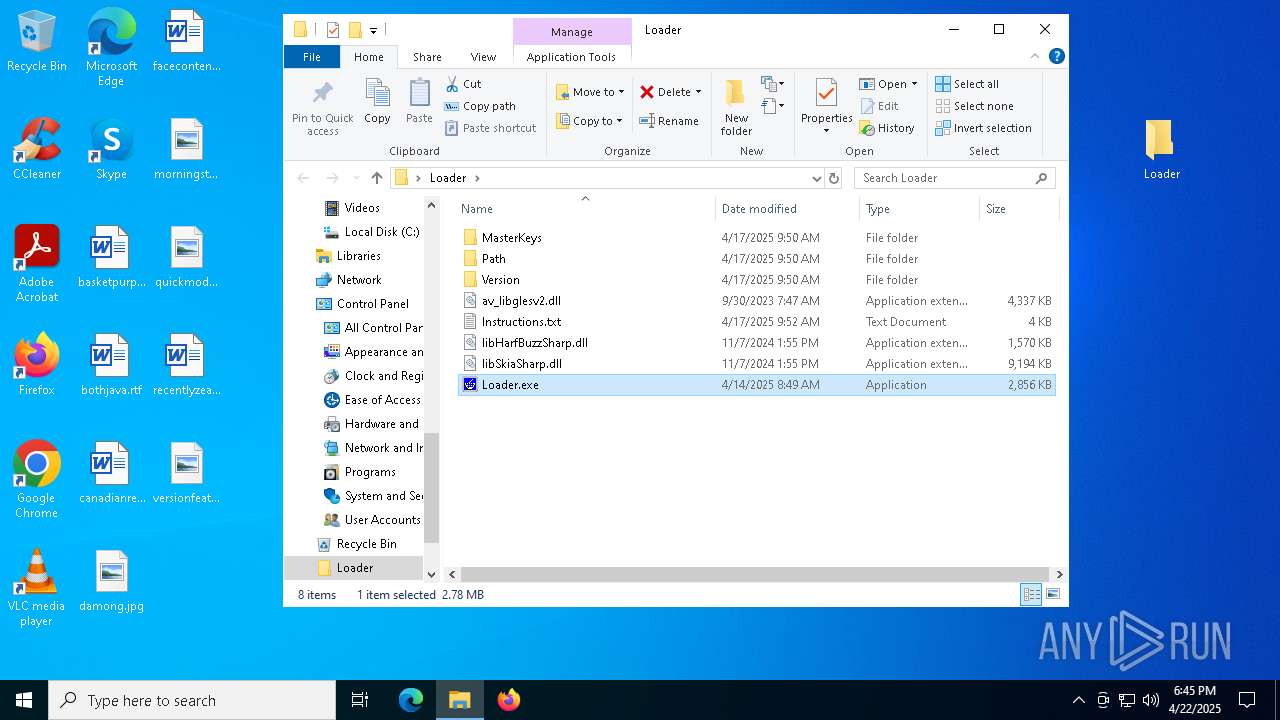
| File name: | Loader.rar |
| Full analysis: | https://app.any.run/tasks/f3cebae6-8297-4b7a-8443-c05f5a299955 |
| Verdict: | Malicious activity |
| Threats: | Rhadamanthys is a C++ information-stealing malware that extracts sensitive data from infiltrated machines. Its layered operational chain and advanced evasion tactics make it a major risk in cybersecurity landscapes. |
| Analysis date: | April 22, 2025, 18:44:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F45CCCC3C89F8DB80B8E6AA1D6F4028B |
| SHA1: | DD44EA685036F3CE8B0C8CCEAF3D263244A9AC6F |
| SHA256: | C749B03DFDF464B26CB121A9FC2ED2AB691C7F5CA794D6114EB1843656C2F2A2 |
| SSDEEP: | 98304:ATMBoc1x45JfHa2L1nVjL/sbUk+kOd1SPADeKqpZnWPyWmVvEJ921Mtr8T5kJ7FF:VLPa2+803PZUi |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7404)
RHADAMANTHYS mutex has been found
- Loader.exe (PID: 8084)
- svchost.exe (PID: 8112)
- svchost.exe (PID: 5008)
- Loader.exe (PID: 1348)
RHADAMANTHYS has been detected (YARA)
- svchost.exe (PID: 6068)
- svchost.exe (PID: 1184)
Scans artifacts that could help determine the target
- msedge.exe (PID: 7732)
SUSPICIOUS
Reads the BIOS version
- Loader.exe (PID: 8084)
- Loader.exe (PID: 1348)
The process checks if it is being run in the virtual environment
- svchost.exe (PID: 8112)
- svchost.exe (PID: 5008)
Multiple wallet extension IDs have been found
- svchost.exe (PID: 6068)
- svchost.exe (PID: 1184)
Reads security settings of Internet Explorer
- msedge.exe (PID: 7732)
Reads Mozilla Firefox installation path
- msedge.exe (PID: 7732)
Searches for installed software
- svchost.exe (PID: 6068)
- svchost.exe (PID: 1184)
Loads DLL from Mozilla Firefox
- svchost.exe (PID: 6068)
- svchost.exe (PID: 1184)
Executable content was dropped or overwritten
- wmlaunch.exe (PID: 7888)
INFO
Checks supported languages
- Loader.exe (PID: 8084)
- Loader.exe (PID: 1348)
- chrome.exe (PID: 5392)
- msedge.exe (PID: 7732)
- chrome.exe (PID: 7852)
- msedge.exe (PID: 8064)
- identity_helper.exe (PID: 7360)
- wmlaunch.exe (PID: 7888)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7404)
- msedge.exe (PID: 2092)
The sample compiled with english language support
- WinRAR.exe (PID: 7404)
- msedge.exe (PID: 2092)
- wmlaunch.exe (PID: 7888)
Manual execution by a user
- Loader.exe (PID: 8084)
- svchost.exe (PID: 8112)
- svchost.exe (PID: 6068)
- Loader.exe (PID: 1348)
- msedge.exe (PID: 6040)
Process checks whether UAC notifications are on
- Loader.exe (PID: 1348)
- msedge.exe (PID: 7732)
Create files in a temporary directory
- svchost.exe (PID: 6068)
- chrome.exe (PID: 5392)
- msedge.exe (PID: 7732)
- svchost.exe (PID: 1184)
- chrome.exe (PID: 7852)
- msedge.exe (PID: 8064)
Reads the computer name
- chrome.exe (PID: 5392)
- msedge.exe (PID: 7732)
- msedge.exe (PID: 8064)
- chrome.exe (PID: 7852)
- identity_helper.exe (PID: 7360)
- wmlaunch.exe (PID: 7888)
Checks proxy server information
- chrome.exe (PID: 5392)
- msedge.exe (PID: 7732)
- chrome.exe (PID: 7852)
- msedge.exe (PID: 8064)
- slui.exe (PID: 5064)
Reads Environment values
- chrome.exe (PID: 5392)
- msedge.exe (PID: 7732)
- chrome.exe (PID: 7852)
- identity_helper.exe (PID: 7360)
- msedge.exe (PID: 8064)
Reads the machine GUID from the registry
- chrome.exe (PID: 5392)
- msedge.exe (PID: 7732)
- chrome.exe (PID: 7852)
- wmlaunch.exe (PID: 7888)
Process checks computer location settings
- chrome.exe (PID: 5392)
- msedge.exe (PID: 7732)
- chrome.exe (PID: 7852)
- msedge.exe (PID: 8064)
Application launched itself
- msedge.exe (PID: 7732)
- chrome.exe (PID: 5392)
- chrome.exe (PID: 7852)
- msedge.exe (PID: 8064)
- msedge.exe (PID: 6040)
- msedge.exe (PID: 7356)
Reads the software policy settings
- slui.exe (PID: 7564)
- slui.exe (PID: 5064)
Creates files or folders in the user directory
- wmlaunch.exe (PID: 7888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 1271158 |
| UncompressedSize: | 4440576 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Loader/av_libglesv2.dll |
Total processes
246
Monitored processes
104
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 812 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5804 --field-trial-handle=2396,i,4289459897583357769,7583604400848656730,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 864 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5236 --field-trial-handle=2396,i,4289459897583357769,7583604400848656730,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1052 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=3672 --field-trial-handle=1964,i,2925207601415945737,9997651913545455158,262144 --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1168 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5028 --field-trial-handle=2396,i,4289459897583357769,7583604400848656730,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1184 | "C:\Windows\System32\svchost.exe" | C:\Windows\System32\svchost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | "C:\Users\admin\Desktop\Loader\Loader.exe" | C:\Users\admin\Desktop\Loader\Loader.exe | explorer.exe | ||||||||||||
User: admin Company: FlashDevelop.org Integrity Level: HIGH Description: FlashDevelop Exit code: 0 Version: 5.0.0.0 Modules
| |||||||||||||||
| 1452 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5976 --field-trial-handle=2396,i,4289459897583357769,7583604400848656730,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1568 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5592 --field-trial-handle=2396,i,4289459897583357769,7583604400848656730,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2064 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4908 --field-trial-handle=2396,i,4289459897583357769,7583604400848656730,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2084 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5224 --field-trial-handle=2396,i,4289459897583357769,7583604400848656730,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
19 116
Read events
19 048
Write events
66
Delete events
2
Modification events
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Loader.rar | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
32
Suspicious files
784
Text files
197
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7404.31623\Loader\Instructions.txt | text | |
MD5:FA8579AE305C38A1B157CCFDE19B2F12 | SHA256:4C8AD75FCFF00D50F65CA929B5D9619EB9207CF7091B76BA159AB39CF570612A | |||
| 5392 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr463D.tmp\Default\README | text | |
MD5:883D62ACD72005F3AD7A14500D482033 | SHA256:C43668EEC4A8D88A5B3A06A84F8846853FE33E54293C2DB56899A5A5DFB4D944 | |||
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7404.31623\Loader\av_libglesv2.dll | executable | |
MD5:0C6D7EF9F90B40FE51E67A2FF9F38244 | SHA256:CAFF1BE1FAEE32F7C5BFBA9162EE617C347AAD40772CAA9A1AFF794E3A191420 | |||
| 5392 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr463D.tmp\Default\Extension Rules\MANIFEST-000001 | binary | |
MD5:5AF87DFD673BA2115E2FCF5CFDB727AB | SHA256:F9D31B278E215EB0D0E9CD709EDFA037E828F36214AB7906F612160FEAD4B2B4 | |||
| 5392 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr463D.tmp\Default\Code Cache\wasm\index-dir\the-real-index | binary | |
MD5:E2986ED7729DE5E553996445DC9253FE | SHA256:AE9EF081E9C8866A2764EC7616A932C4F3A789E07E4240B845B5480A2733AEB5 | |||
| 5392 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr463D.tmp\Default\Code Cache\js\index-dir\temp-index | binary | |
MD5:E2986ED7729DE5E553996445DC9253FE | SHA256:AE9EF081E9C8866A2764EC7616A932C4F3A789E07E4240B845B5480A2733AEB5 | |||
| 5392 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr463D.tmp\Default\28da82f6-548a-4d9c-b309-b5ade99a9fdf.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 5392 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr463D.tmp\Local State | binary | |
MD5:4A1711F275B39B27CCD958E4E57ED969 | SHA256:0FB6E9D65947FA9C2F08B6222FF803D5A3C5A029E1438941EDB3C5C00F0FEC64 | |||
| 5392 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr463D.tmp\Default\Code Cache\wasm\index-dir\temp-index | binary | |
MD5:E2986ED7729DE5E553996445DC9253FE | SHA256:AE9EF081E9C8866A2764EC7616A932C4F3A789E07E4240B845B5480A2733AEB5 | |||
| 5392 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr463D.tmp\Default\Sync Data\LevelDB\MANIFEST-000001 | binary | |
MD5:5AF87DFD673BA2115E2FCF5CFDB727AB | SHA256:F9D31B278E215EB0D0E9CD709EDFA037E828F36214AB7906F612160FEAD4B2B4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
51
TCP/UDP connections
111
DNS requests
102
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.11:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2616 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6516 | svchost.exe | HEAD | 200 | 208.89.74.21:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1745625033&P2=404&P3=2&P4=AcrtHjvNTUzH%2bhJrOpGrMqvSS2ydy84HYeqUo2OeOzeC0PSYDjoXYe3Ue3KoDEF1%2foDts4%2bqKEpEwZQC2JRl4g%3d%3d | unknown | — | — | whitelisted |
2616 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6516 | svchost.exe | GET | 206 | 208.89.74.21:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1745625033&P2=404&P3=2&P4=AcrtHjvNTUzH%2bhJrOpGrMqvSS2ydy84HYeqUo2OeOzeC0PSYDjoXYe3Ue3KoDEF1%2foDts4%2bqKEpEwZQC2JRl4g%3d%3d | unknown | — | — | whitelisted |
6516 | svchost.exe | HEAD | 200 | 208.89.74.21:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1745625034&P2=404&P3=2&P4=L%2bFr8SvToUJQ5DPlC%2blDspLhNbM%2fQ3YiopmRHCNsSfyaVTDLAxQG5AIO0Ce0qx5AOuJhwAlVquOenlY9knZPEw%3d%3d | unknown | — | — | whitelisted |
6516 | svchost.exe | GET | 206 | 208.89.74.21:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1745625033&P2=404&P3=2&P4=AcrtHjvNTUzH%2bhJrOpGrMqvSS2ydy84HYeqUo2OeOzeC0PSYDjoXYe3Ue3KoDEF1%2foDts4%2bqKEpEwZQC2JRl4g%3d%3d | unknown | — | — | whitelisted |
6516 | svchost.exe | GET | 206 | 208.89.74.21:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1745625034&P2=404&P3=2&P4=L%2bFr8SvToUJQ5DPlC%2blDspLhNbM%2fQ3YiopmRHCNsSfyaVTDLAxQG5AIO0Ce0qx5AOuJhwAlVquOenlY9knZPEw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.11:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2616 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
cloudflare-dns.com |
| whitelisted |
radik.kotodoggo.ru |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected Domain Associated with Malware Distribution (kotodoggo .ru) |
8112 | svchost.exe | Misc activity | ET INFO Cloudflare DNS Over HTTPS Certificate Inbound |