| File name: | Pe32-v4.0.1.exe |
| Full analysis: | https://app.any.run/tasks/93a94856-9c3a-4e23-84a1-2cd83f0fe3a8 |
| Verdict: | Malicious activity |
| Threats: | Ransomware is a type of malicious software that locks users out of their system or data using different methods to force them to pay a ransom. Most often, such programs encrypt files on an infected machine and demand a fee to be paid in exchange for the decryption key. Additionally, such programs can be used to steal sensitive information from the compromised computer and even conduct DDoS attacks against affected organizations to pressure them into paying. |
| Analysis date: | February 12, 2025, 13:57:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 5 sections |
| MD5: | 1289A867FAFE321B51A93AA47AFAFFC9 |
| SHA1: | 221D0CBD5C7A0C84BB86B4351C552F6EFCD4F3B6 |
| SHA256: | C6DDC9C2852EDDF30F945A50183E28D38F6B9B1BBAD01AAC52E9D9539482A433 |
| SSDEEP: | 49152:WkpV7eOOhjIXwUJkrKddtJi8F4+uhH2en:pb7efjLF0i8G5Ae |
MALICIOUS
RANSOMWARE has been detected
- Pe32-v4.0.1.exe (PID: 6308)
SUSPICIOUS
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Pe32-v4.0.1.exe (PID: 6308)
Creates file in the systems drive root
- Pe32-v4.0.1.exe (PID: 6308)
Possible usage of Discord/Telegram API has been detected (YARA)
- Pe32-v4.0.1.exe (PID: 6308)
INFO
Reads the computer name
- Pe32-v4.0.1.exe (PID: 6308)
Reads the software policy settings
- Pe32-v4.0.1.exe (PID: 6308)
Checks supported languages
- Pe32-v4.0.1.exe (PID: 6308)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(6308) Pe32-v4.0.1.exe
Telegram-Responses
oktrue
result
message_id1516
from
id8179978828
is_bottrue
first_namemypersonalbot
usernamemypersonal83247bot
chat
id-4785122270
titlePe32 Reports Armin
typegroup
all_members_are_administratorstrue
date1739368694
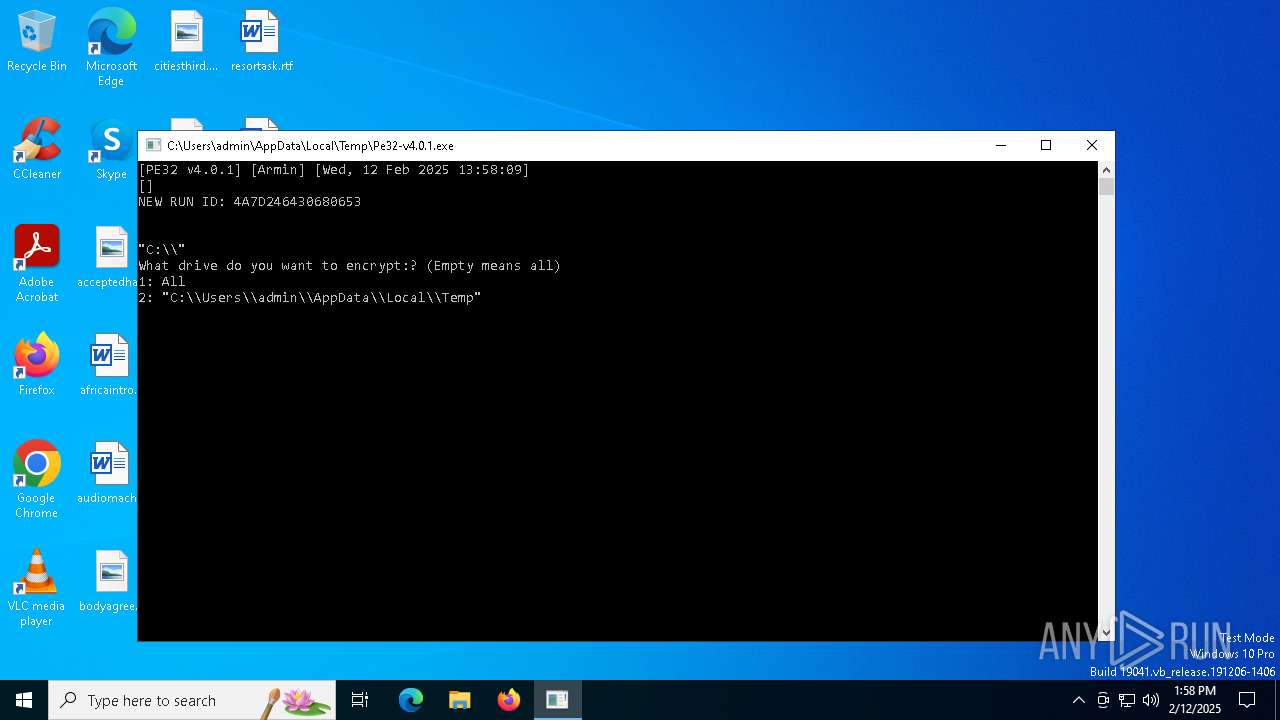
text[PE32 v4.0.1] [Armin] [Wed, 12 Feb 2025 13:58:09]
[]
NEW RUN ID: 4A7D246430680653
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:02:10 05:32:16+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 1605632 |
| InitializedDataSize: | 568832 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16fc50 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
132
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2756 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3812 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6308 | "C:\Users\admin\AppData\Local\Temp\Pe32-v4.0.1.exe" | C:\Users\admin\AppData\Local\Temp\Pe32-v4.0.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
ims-api(PID) Process(6308) Pe32-v4.0.1.exe Telegram-Responses oktrue result message_id1516 from id8179978828 is_bottrue first_namemypersonalbot usernamemypersonal83247bot chat id-4785122270 titlePe32 Reports Armin typegroup all_members_are_administratorstrue date1739368694 text[PE32 v4.0.1] [Armin] [Wed, 12 Feb 2025 13:58:09]
[]
NEW RUN ID: 4A7D246430680653 | |||||||||||||||
| 6316 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Pe32-v4.0.1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 296
Read events
1 296
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
666
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6308 | Pe32-v4.0.1.exe | C:\PE32-KEY\context.pe32c | — | |
MD5:— | SHA256:— | |||
| 6308 | Pe32-v4.0.1.exe | C:\Program Files\Mozilla Firefox\omni.ja | — | |
MD5:— | SHA256:— | |||
| 6308 | Pe32-v4.0.1.exe | C:\bootTel.dat | binary | |
MD5:FAC66F845222C23F99332B9AE21762FF | SHA256:DF3DA1E4F4F4792A4781DFFC3D020E6F5125C3C859C31FE9A835A98BCEC6B088 | |||
| 6308 | Pe32-v4.0.1.exe | C:\ProgramData\Mozilla-1de4eec8-1241-4177-a864-e594e8d1fb38\profile_count_308046B0AF4A39CB.json | binary | |
MD5:E1CB8A67FA9D918B9DA8E609A692902D | SHA256:15986884642653B382EA7195147FD1852C0700E32F0E02114B28617D5BB9E2C5 | |||
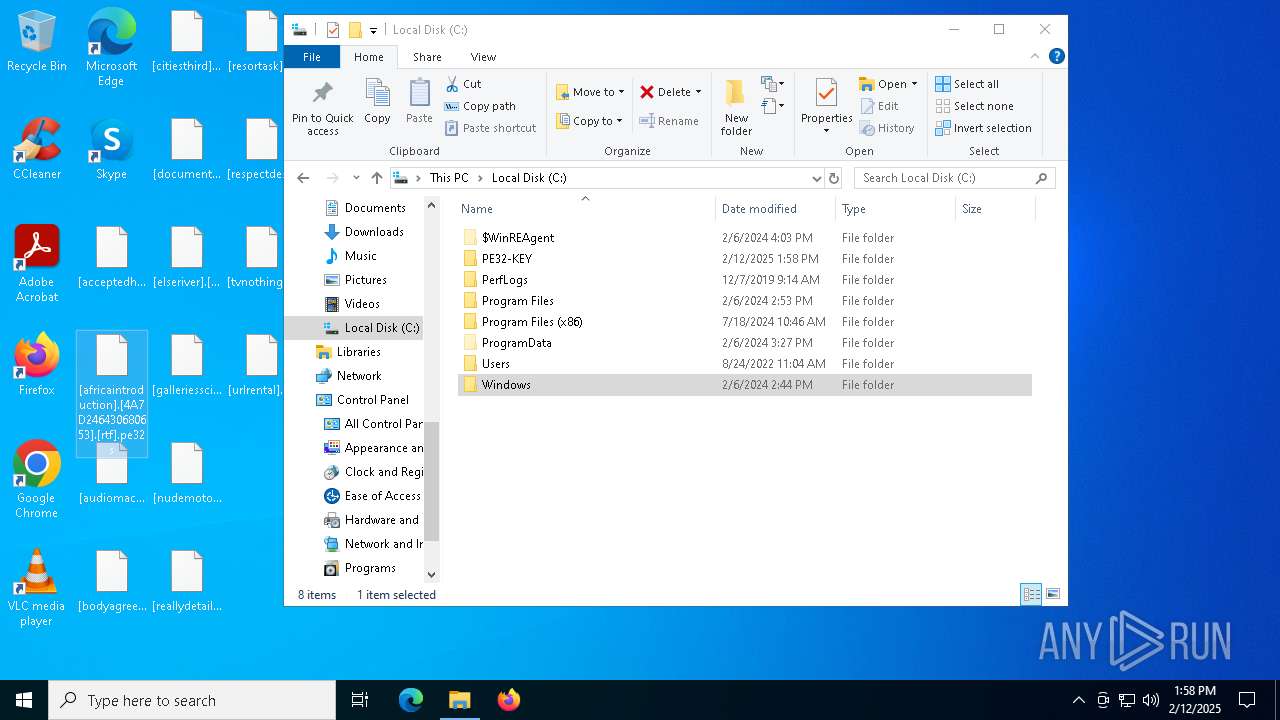
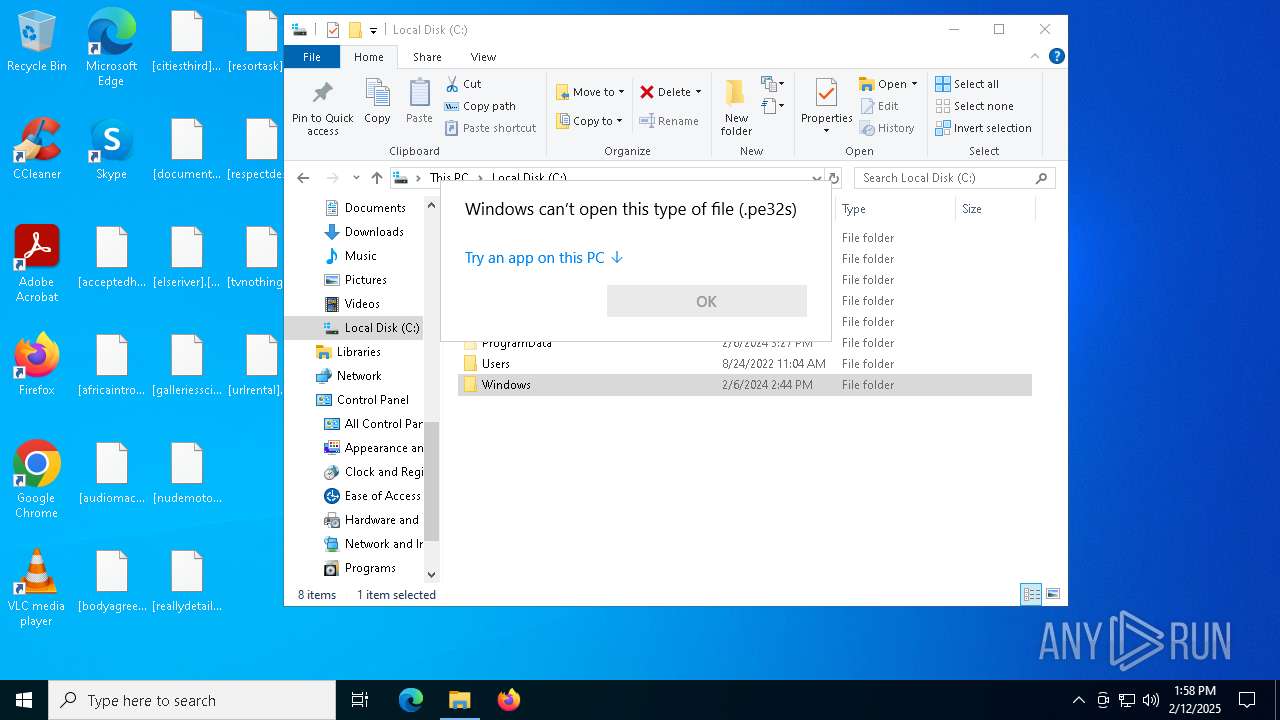
| 6308 | Pe32-v4.0.1.exe | C:\ProgramData\Mozilla-1de4eec8-1241-4177-a864-e594e8d1fb38\[UpdateLock-308046B0AF4A39CB].[4A7D246430680653].[].pe32s | binary | |
MD5:721EAFFD1F5B05E2D8D889758114C20C | SHA256:66BB93A76D12118A031576F78584DD3F9A50933B41DAA6BECE08699ACBFBD489 | |||
| 6308 | Pe32-v4.0.1.exe | C:\PE32-KEY\ID | text | |
MD5:8E4CBEEA267DF5BA76317BF0AFC8A761 | SHA256:B045AD78209596C8A19B86B268860EF9EA9CEEBBB37D4BBBACA43E011C5E78D6 | |||
| 6308 | Pe32-v4.0.1.exe | C:\ProgramData\Mozilla-1de4eec8-1241-4177-a864-e594e8d1fb38\UpdateLock-308046B0AF4A39CB | binary | |
MD5:721EAFFD1F5B05E2D8D889758114C20C | SHA256:66BB93A76D12118A031576F78584DD3F9A50933B41DAA6BECE08699ACBFBD489 | |||
| 6308 | Pe32-v4.0.1.exe | C:\ProgramData\Microsoft\User Account Pictures\admin.dat | binary | |
MD5:8C4C3ADFD0CE992E23271D00A393952F | SHA256:95B8ED7053C95F15A9C271F497BC70B8F4064C5F6FAE1C8792B4F5761379C30D | |||
| 6308 | Pe32-v4.0.1.exe | C:\Users\admin\Desktop\[africaintroduction].[4A7D246430680653].[rtf].pe32s | binary | |
MD5:46A2EE703C758FE887D42A3178FAB312 | SHA256:EF0A0F8D927051D639F176A58D923F024F00EC94C3EE855556324E8A418D2489 | |||
| 6308 | Pe32-v4.0.1.exe | C:\Users\admin\Desktop\audiomachine.rtf | binary | |
MD5:C0CBEC596025BEDF2AAA7C6839FD2724 | SHA256:0B6621FF31C92003B13AF4C1B6549BD410C94F68743EBF6BA9F7A2B0AD4678C7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
30
DNS requests
15
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6172 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 23.40.158.218:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 23.40.158.218:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6172 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6572 | backgroundTaskHost.exe | GET | 200 | 23.40.158.218:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.110.171:443 | — | Akamai International B.V. | DE | unknown |
6308 | Pe32-v4.0.1.exe | 149.154.167.220:443 | api.telegram.org | Telegram Messenger Inc | GB | whitelisted |
1864 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.16.110.202:443 | — | Akamai International B.V. | DE | unknown |
1176 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 23.40.158.218:80 | ocsp.digicert.com | AKAMAI-AS | MX | whitelisted |
5064 | SearchApp.exe | 23.40.158.218:80 | ocsp.digicert.com | AKAMAI-AS | MX | whitelisted |
1076 | svchost.exe | 2.18.97.227:443 | go.microsoft.com | Akamai International B.V. | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
api.telegram.org |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
6308 | Pe32-v4.0.1.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
6308 | Pe32-v4.0.1.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
6308 | Pe32-v4.0.1.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
6308 | Pe32-v4.0.1.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |