| File name: | c5e3edafdfda1ca0f0554802bbe32a8b09e8cc48161ed275b8fec6d74208171f.bin |
| Full analysis: | https://app.any.run/tasks/7a722a39-8b12-419d-b852-02a79bf8e691 |
| Verdict: | Malicious activity |
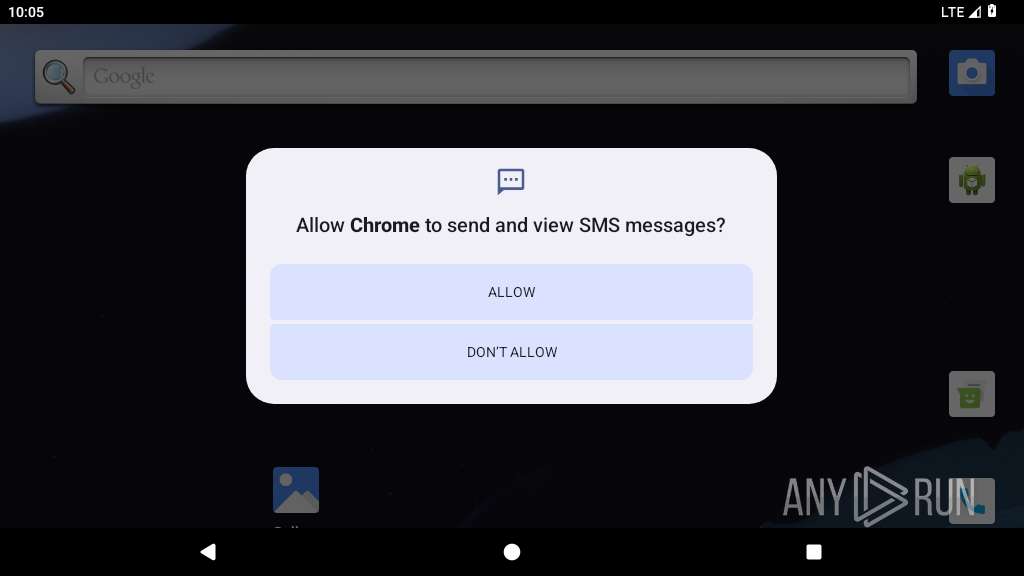
| Threats: | Crocodilus is a highly sophisticated Android banking Trojan that emerged in March 2025, designed for full device takeover. Disguised as legitimate apps, it steals banking credentials, cryptocurrency wallet data, and enables remote control, rapidly evolving into a global threat targeting financial users across Europe, South America, and Asia. |
| Analysis date: | May 11, 2025, 22:04:58 |
| OS: | Android 14 |
| Tags: | |
| MIME: | application/vnd.android.package-archive |
| File info: | Android package (APK), with APK Signing Block |
| MD5: | E80C4FFA4ACD192981D142C435C52C49 |
| SHA1: | 009FD7FAF9DC52FD96BBFDE826BBB4058409B8B8 |
| SHA256: | C5E3EDAFDFDA1CA0F0554802BBE32A8B09E8CC48161ED275B8FEC6D74208171F |
| SSDEEP: | 98304:+qnLJpNeAbQnaxdAcgpwBxKTo3vb+u2hZalP0Nus89Ne+Li3b7Fl30HPaef0k8mX:vggtJN |
MALICIOUS
Hides app icon from display
- app_process64 (PID: 2266)
CROCODILUS has been detected
- app_process64 (PID: 2266)
Returns the phone's primary line number (MSISDN)
- app_process64 (PID: 2266)
SUSPICIOUS
Launches a new activity
- app_process64 (PID: 2266)
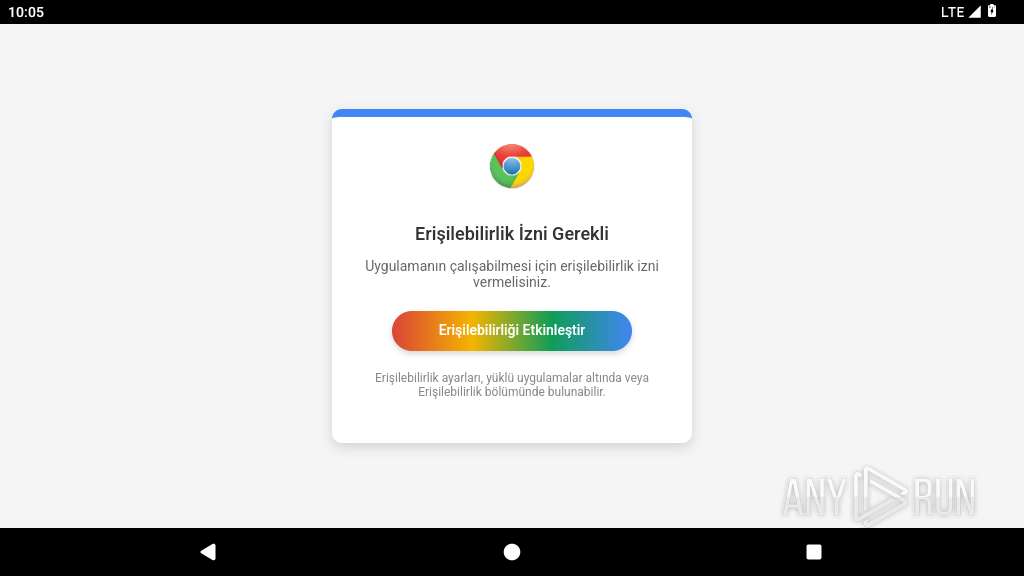
Requests access to accessibility settings
- app_process64 (PID: 2266)
Intercepts events for accessibility services
- app_process64 (PID: 2266)
Checks if the device's lock screen is showing
- app_process64 (PID: 2266)
Performs UI accessibility actions without user input
- app_process64 (PID: 2266)
Starts a service
- app_process64 (PID: 2266)
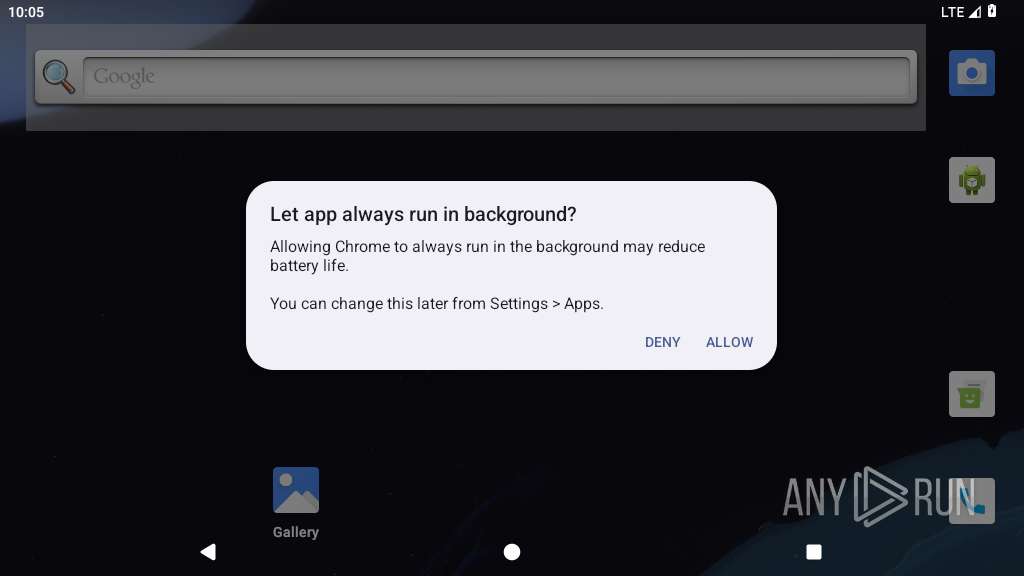
Prevents its uninstallation by user
- app_process64 (PID: 2266)
Scans for installed antivirus apps
- app_process64 (PID: 2266)
Establishing a connection
- app_process64 (PID: 2266)
Updates data in the storage of application settings (SharedPreferences)
- app_process64 (PID: 2266)
Retrieves a list of running services
- app_process64 (PID: 2266)
Uses encryption API functions
- app_process64 (PID: 2266)
Returns the name of the current network operator
- app_process64 (PID: 2266)
Leverages accessibility to control apps
- app_process64 (PID: 2266)
Checks exemption from battery optimization
- app_process64 (PID: 2266)
INFO
Retrieves data from storage of application settings (SharedPreferences)
- app_process64 (PID: 2266)
Retrieves the value of a secure system setting
- app_process64 (PID: 2266)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .apk | | | Android Package (73.9) |
|---|---|---|
| .jar | | | Java Archive (20.4) |
| .zip | | | ZIP compressed archive (5.6) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | None |
| ZipModifyDate: | 2025:03:05 20:04:12 |
| ZipCRC: | 0x37aba7f7 |
| ZipCompressedSize: | 250304 |
| ZipUncompressedSize: | 250304 |
| ZipFileName: | resources.arsc |
Total processes
131
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2266 | quizzical.washbowl.calamity | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2301 | zygote | /system/bin/app_process32 | app_process32 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2317 | webview_zygote | /system/bin/app_process32 | — | app_process32 |
User: webview_zygote Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2353 | zygote | /system/bin/app_process32 | app_process32 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2446 | com.android.settings | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 9 | ||||
| 2467 | com.android.systemui.accessibility.accessibilitymenu | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2541 | com.android.settings | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
23
Text files
26
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2266 | app_process64 | /data/data/quizzical.washbowl.calamity/code_cache/decrypted.dex | dex | |
MD5:— | SHA256:— | |||
| 2266 | app_process64 | /data/data/quizzical.washbowl.calamity/code_cache/oat/arm64/decrypted.vdex | binary | |
MD5:— | SHA256:— | |||
| 2266 | app_process64 | /data/data/quizzical.washbowl.calamity/shared_prefs/FilesSettings.xml | xml | |
MD5:— | SHA256:— | |||
| 2266 | app_process64 | /data/data/quizzical.washbowl.calamity/shared_prefs/WebViewChromiumPrefs.xml | xml | |
MD5:— | SHA256:— | |||
| 2266 | app_process64 | /data/data/quizzical.washbowl.calamity/app_webview/Default/Local Storage/leveldb/MANIFEST-000001 | binary | |
MD5:— | SHA256:— | |||
| 2266 | app_process64 | /data/data/quizzical.washbowl.calamity/app_webview/Default/Local Storage/leveldb/000001.dbtmp | text | |
MD5:— | SHA256:— | |||
| 2266 | app_process64 | /data/data/quizzical.washbowl.calamity/app_webview/Default/Local Storage/leveldb/CURRENT | text | |
MD5:— | SHA256:— | |||
| 2266 | app_process64 | /data/data/quizzical.washbowl.calamity/cache/WebView/Default/HTTP Cache/Code Cache/webui_js/index | binary | |
MD5:— | SHA256:— | |||
| 2266 | app_process64 | /data/data/quizzical.washbowl.calamity/cache/WebView/Default/HTTP Cache/Code Cache/js/index | binary | |
MD5:— | SHA256:— | |||
| 2266 | app_process64 | /data/data/quizzical.washbowl.calamity/cache/WebView/Default/HTTP Cache/Code Cache/wasm/index | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
10
DNS requests
10
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 142.250.186.35:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
449 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 216.239.35.0:123 | time.android.com | — | — | whitelisted |
— | — | 142.250.184.228:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.35:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 142.251.31.81:443 | staging-remoteprovisioning.sandbox.googleapis.com | GOOGLE | US | whitelisted |
2301 | app_process32 | 216.58.206.35:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2353 | app_process32 | 142.250.185.67:443 | update.googleapis.com | GOOGLE | US | whitelisted |
2353 | app_process32 | 142.250.186.78:443 | dl.google.com | GOOGLE | US | whitelisted |
2266 | app_process64 | 185.15.59.240:443 | upload.wikimedia.org | WIKIMEDIA | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| whitelisted |
connectivitycheck.gstatic.com |
| whitelisted |
google.com |
| whitelisted |
time.android.com |
| whitelisted |
staging-remoteprovisioning.sandbox.googleapis.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
dl.google.com |
| whitelisted |
upload.wikimedia.org |
| whitelisted |
register-buzzy.store |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |