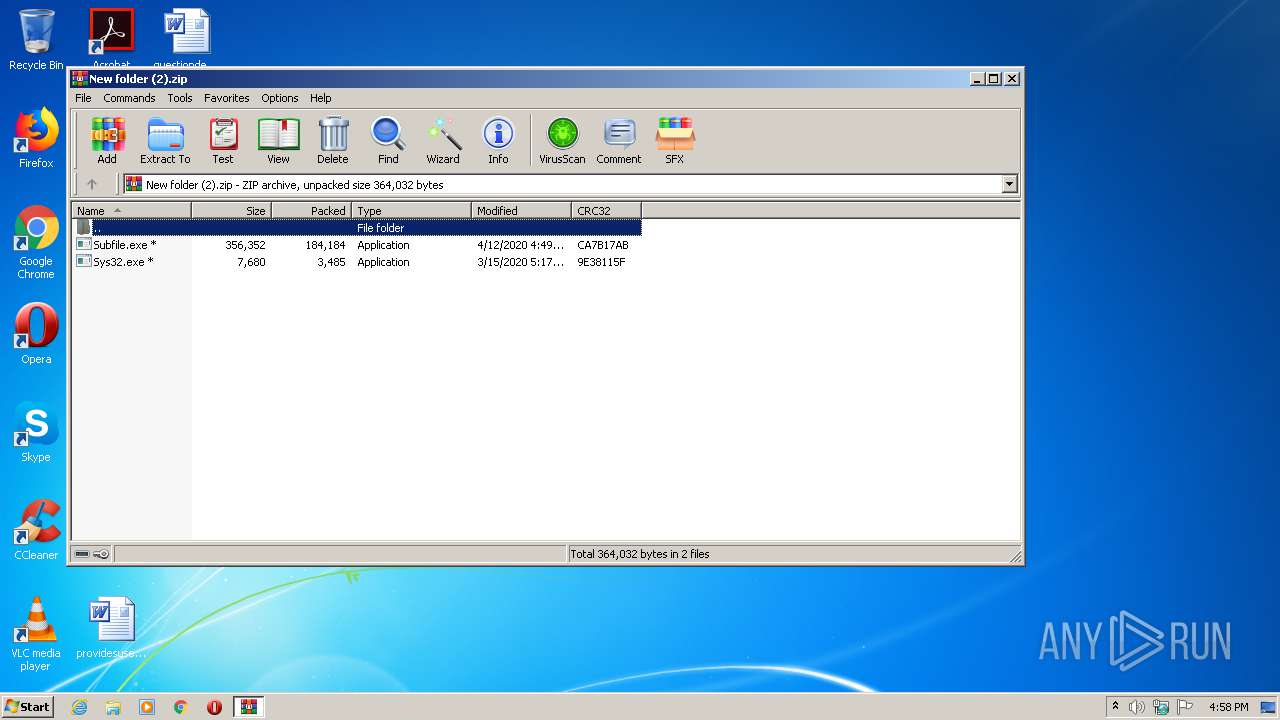
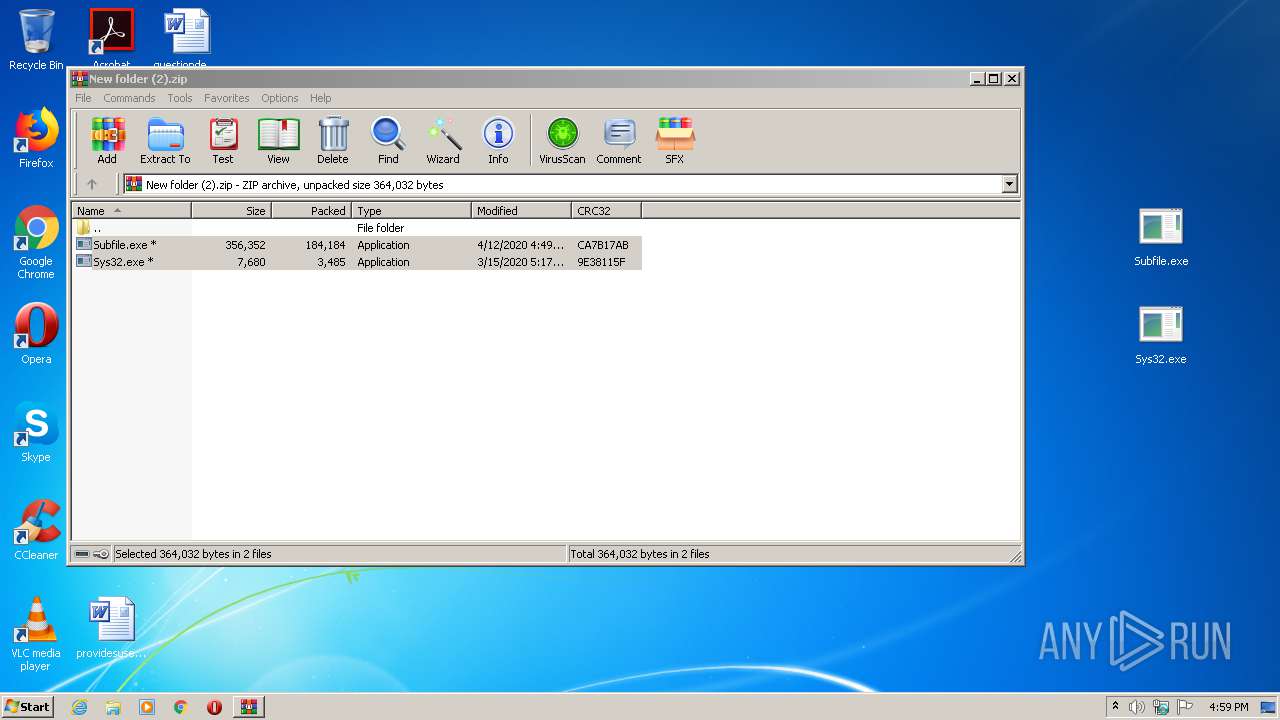
| File name: | New folder (2).zip |
| Full analysis: | https://app.any.run/tasks/1dc3566b-7852-4e0f-8fab-42b8d2f5b8c8 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | July 12, 2020, 15:58:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 52DB15D48A6807EDC9A0CE8AF4ADCC46 |
| SHA1: | 2E59A16A0D485EA539CDA56163EAA6302C960206 |
| SHA256: | C5B861C2995D96F9AC8545FBDE4F2B2E3EBFA0E078B4C839089561240F0DAE5F |
| SSDEEP: | 3072:z1DWXjEctaotj9F830BfBwYT0ewkjEqOWyoMjsuojjd0caBTuWpRdAO8qp8u:z1WzEvotj9F8ofc6ENonj5HagA6u |
MALICIOUS
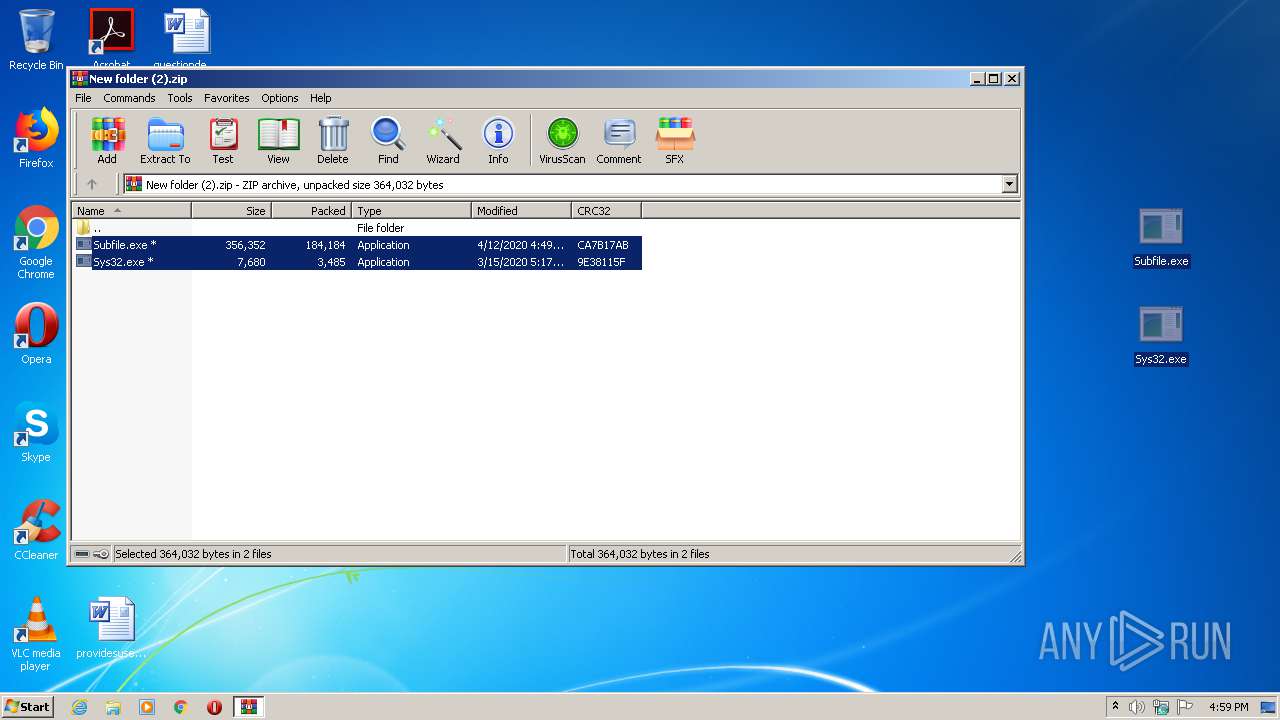
Drops/Copies Quasar RAT executable
- WinRAR.exe (PID: 1816)
QUASAR was detected
- Subfile.exe (PID: 2252)
Application was dropped or rewritten from another process
- Subfile.exe (PID: 2252)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1816)
Checks for external IP
- Subfile.exe (PID: 2252)
Creates files in the user directory
- Subfile.exe (PID: 2252)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 1816)
Manual execution by user
- Subfile.exe (PID: 2252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2020:04:12 10:49:06 |
| ZipCRC: | 0xca7b17ab |
| ZipCompressedSize: | 184184 |
| ZipUncompressedSize: | 356352 |
| ZipFileName: | Subfile.exe |
Total processes
36
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1816 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\New folder (2).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2252 | "C:\Users\admin\Desktop\Subfile.exe" | C:\Users\admin\Desktop\Subfile.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
Total events
473
Read events
451
Write events
22
Delete events
0
Modification events
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\New folder (2).zip | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
2
Suspicious files
0
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2252 | Subfile.exe | C:\Users\admin\AppData\Roaming\Logs\07-12-2020 | gpg | |
MD5:— | SHA256:— | |||
| 1816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1816.36678\Sys32.exe | executable | |
MD5:— | SHA256:— | |||
| 1816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1816.36678\Subfile.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
1
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2252 | Subfile.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | text | 281 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2252 | Subfile.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
2252 | Subfile.exe | 45.80.151.39:60002 | — | — | — | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2252 | Subfile.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
2252 | Subfile.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2252 | Subfile.exe | A Network Trojan was detected | REMOTE [PTsecurity] Quasar.RAT IP Lookup |
1 ETPRO signatures available at the full report