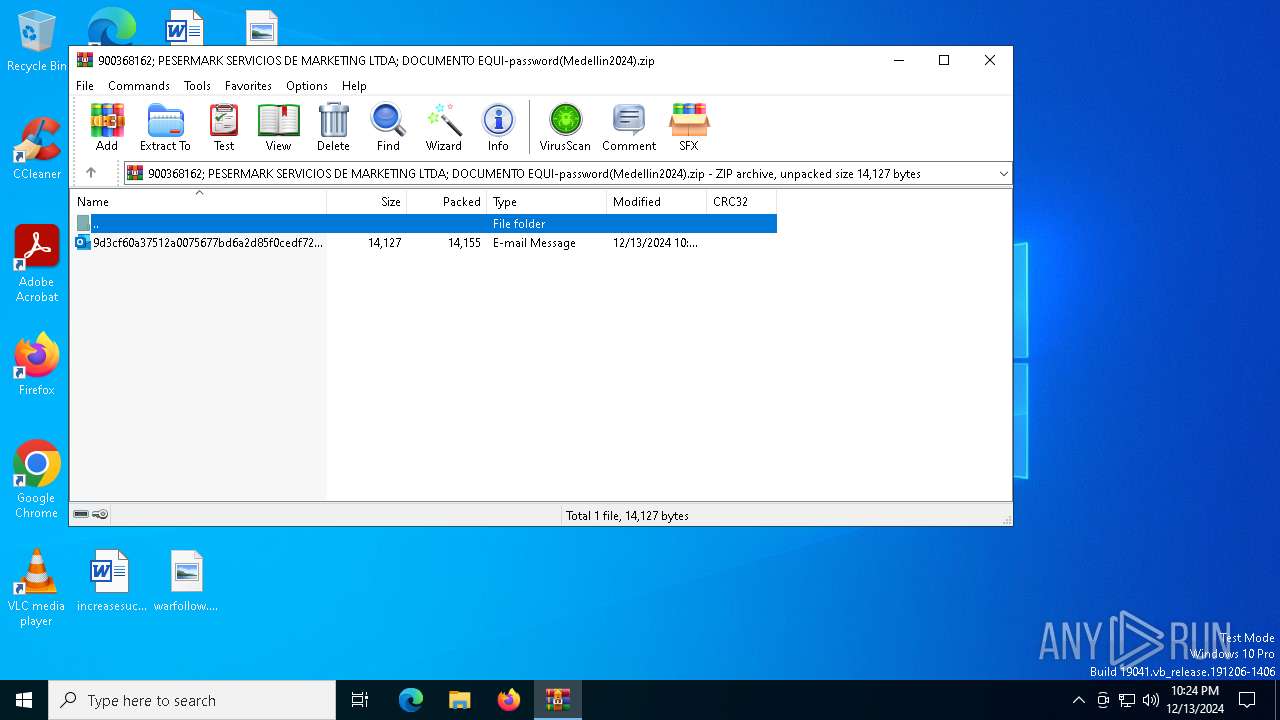
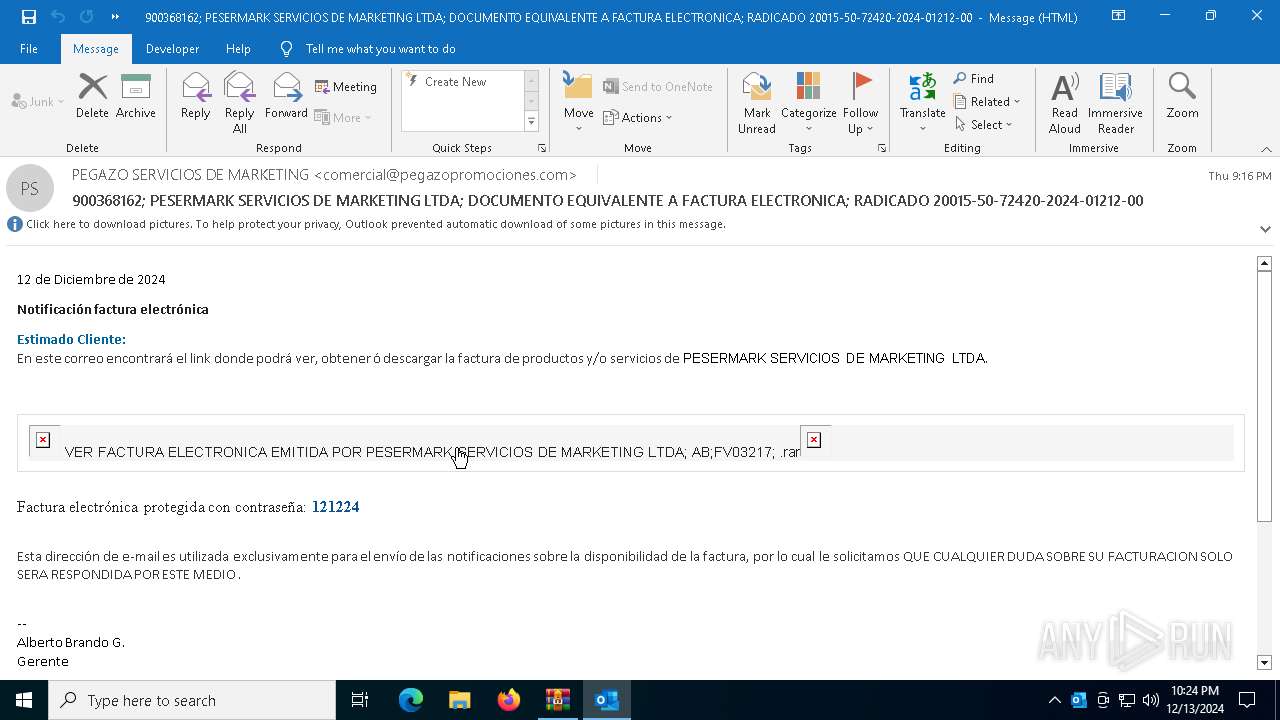
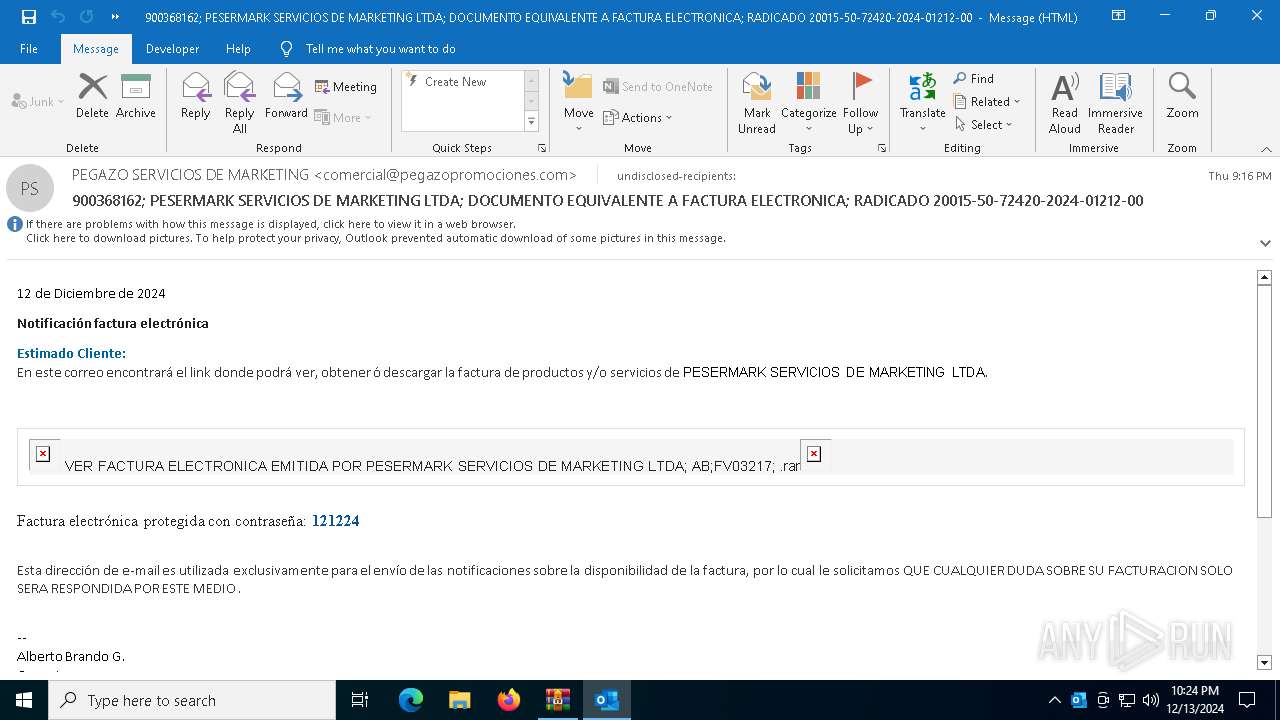
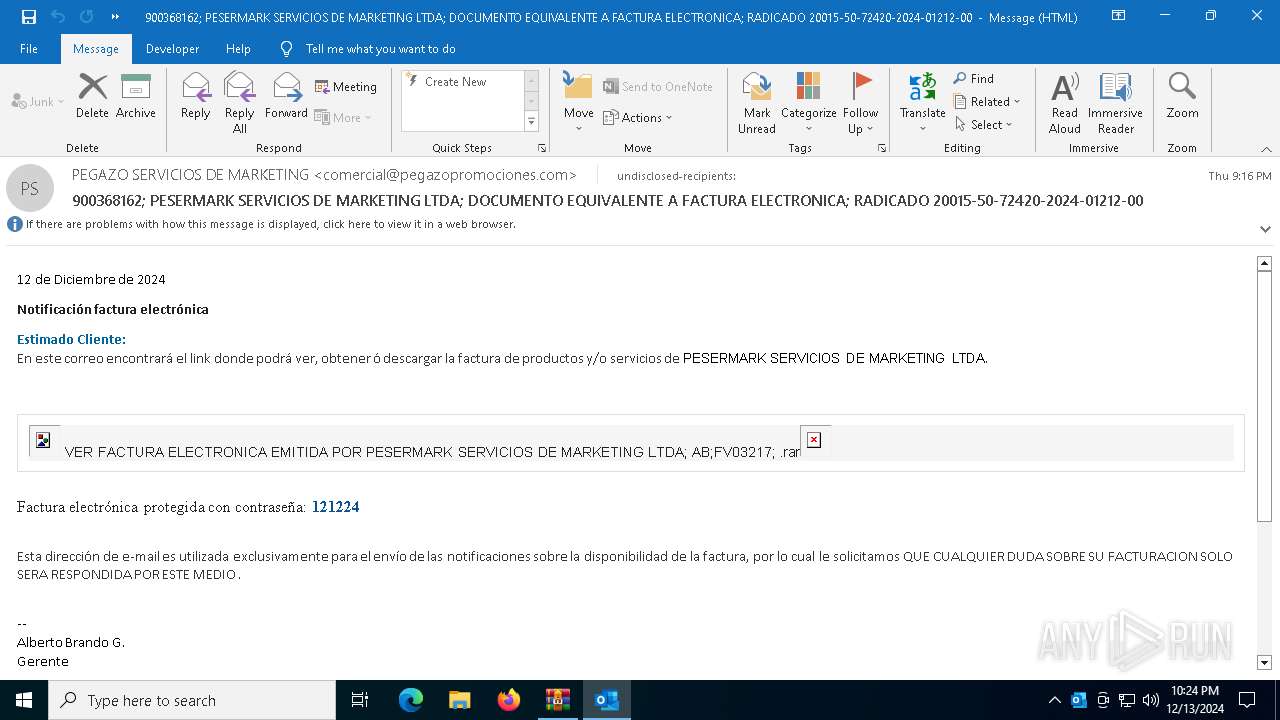
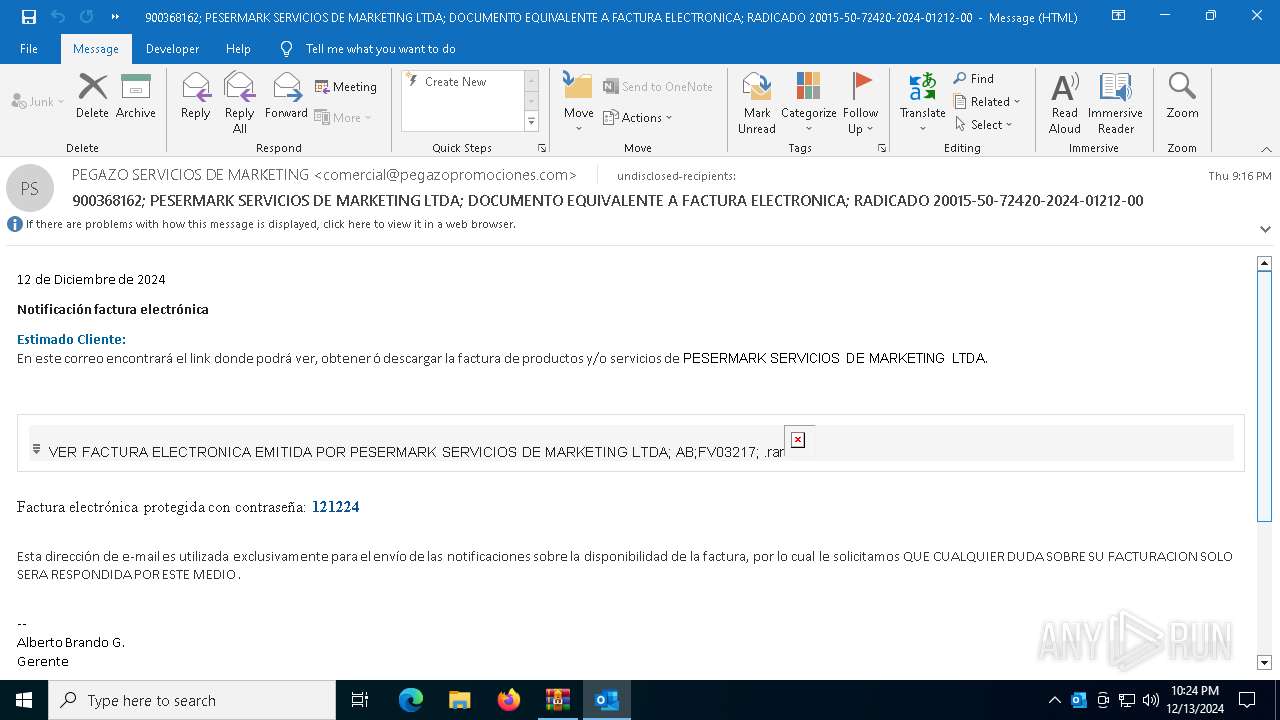
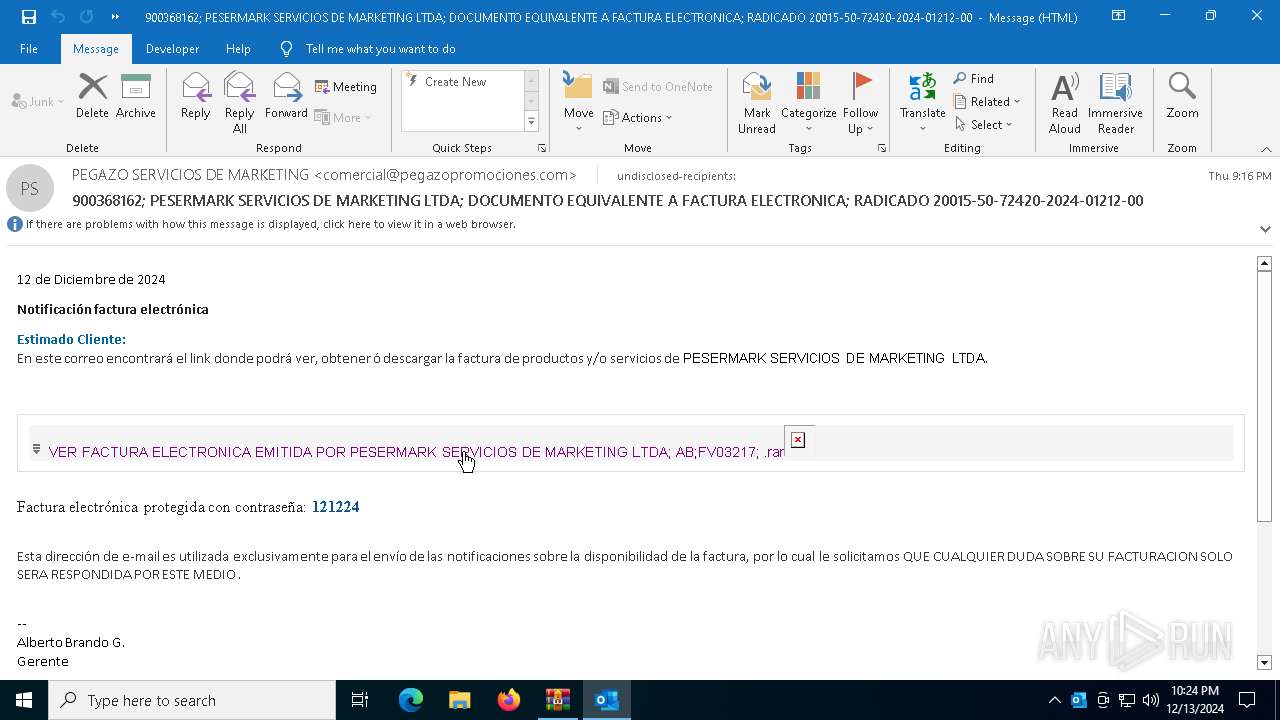
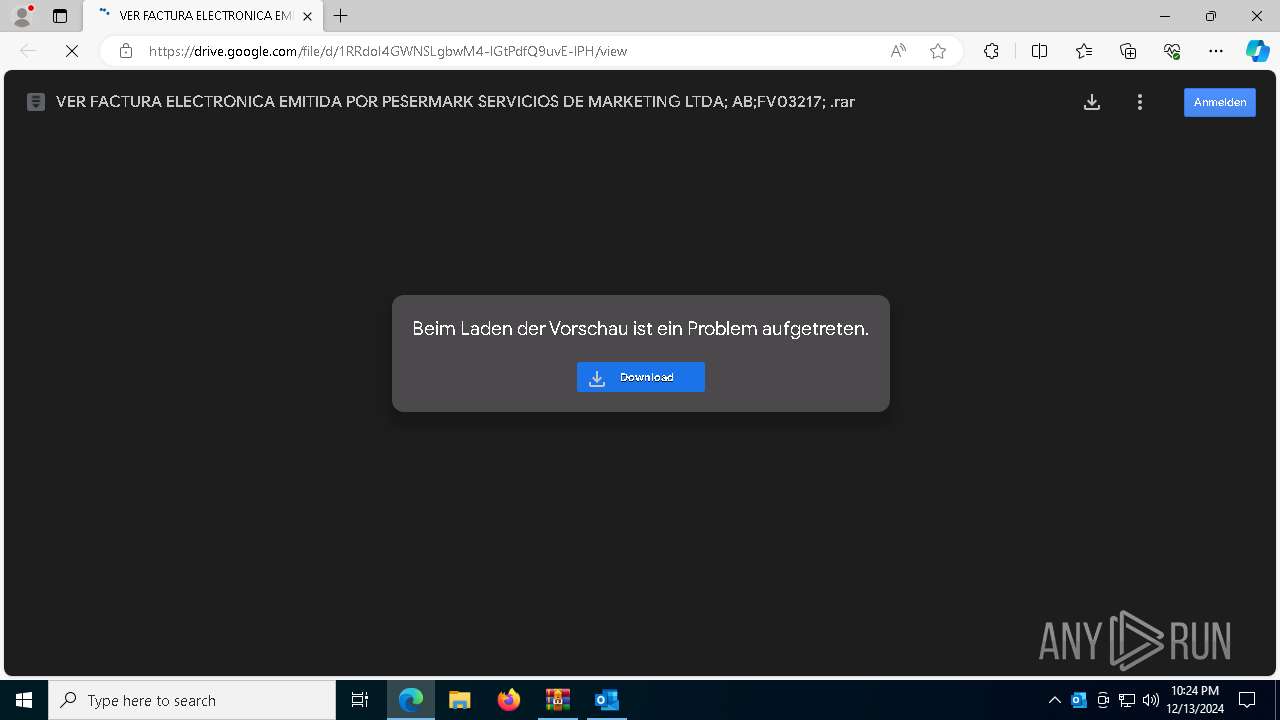
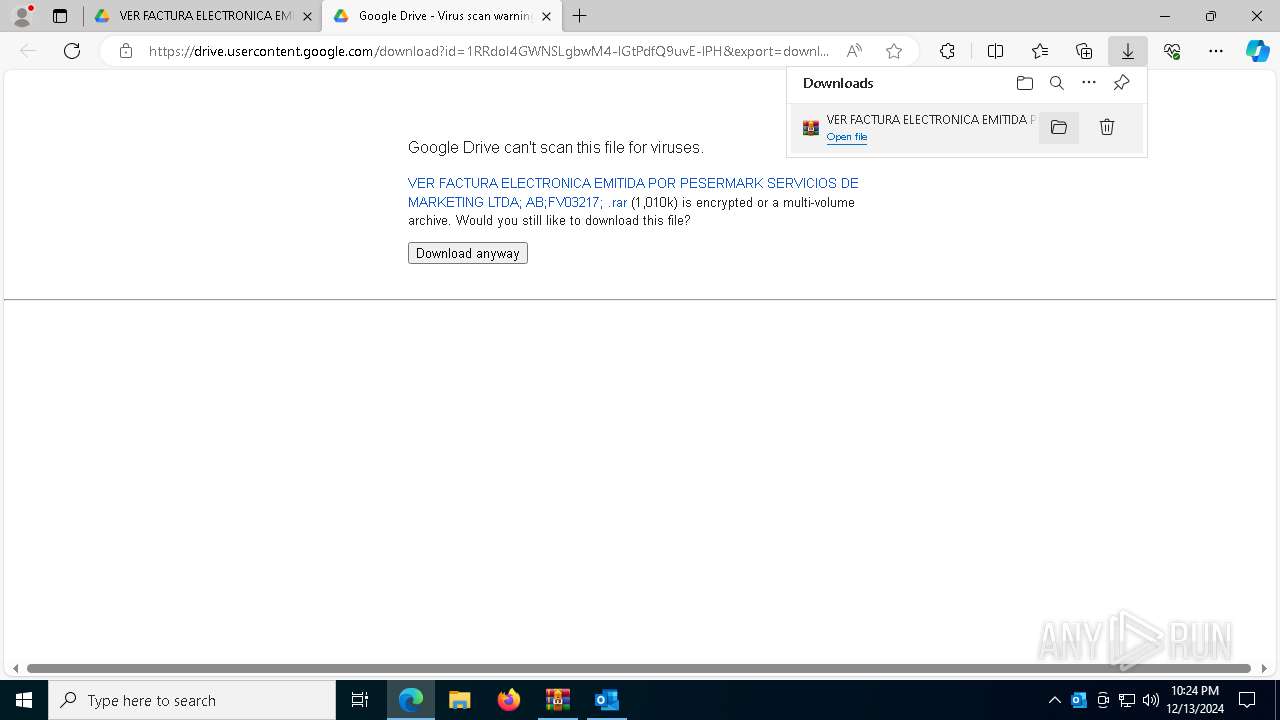
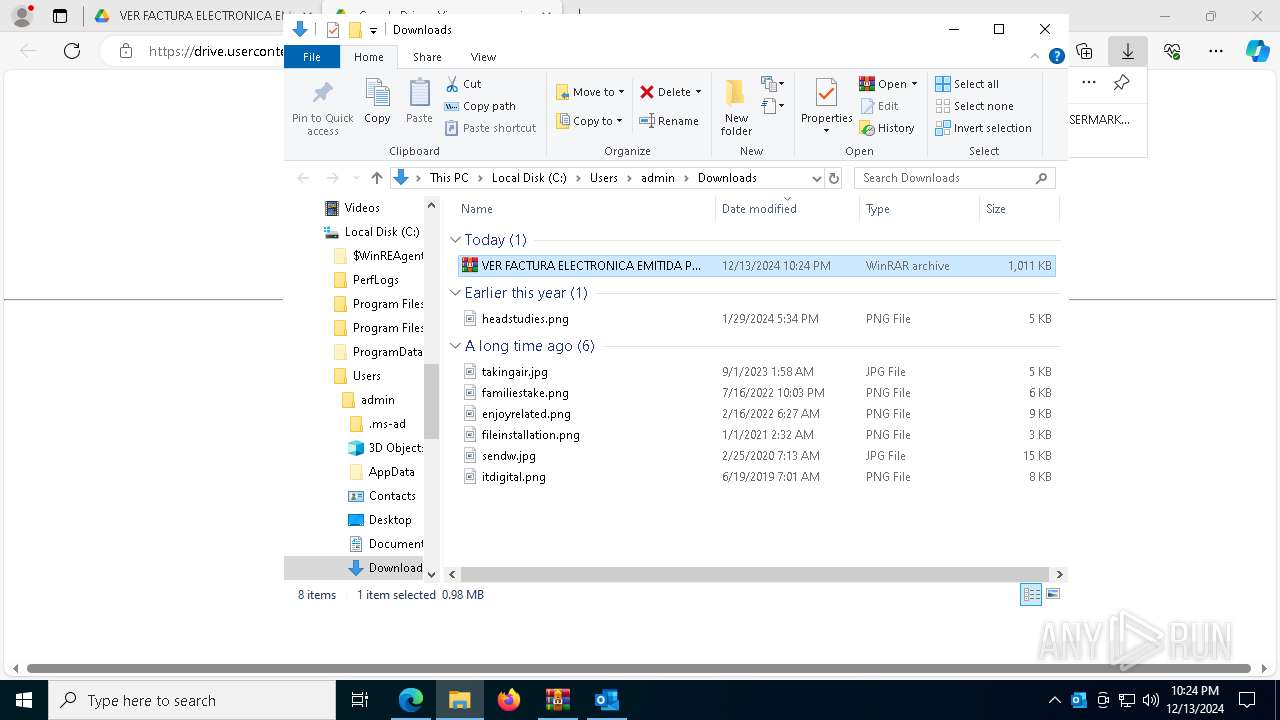
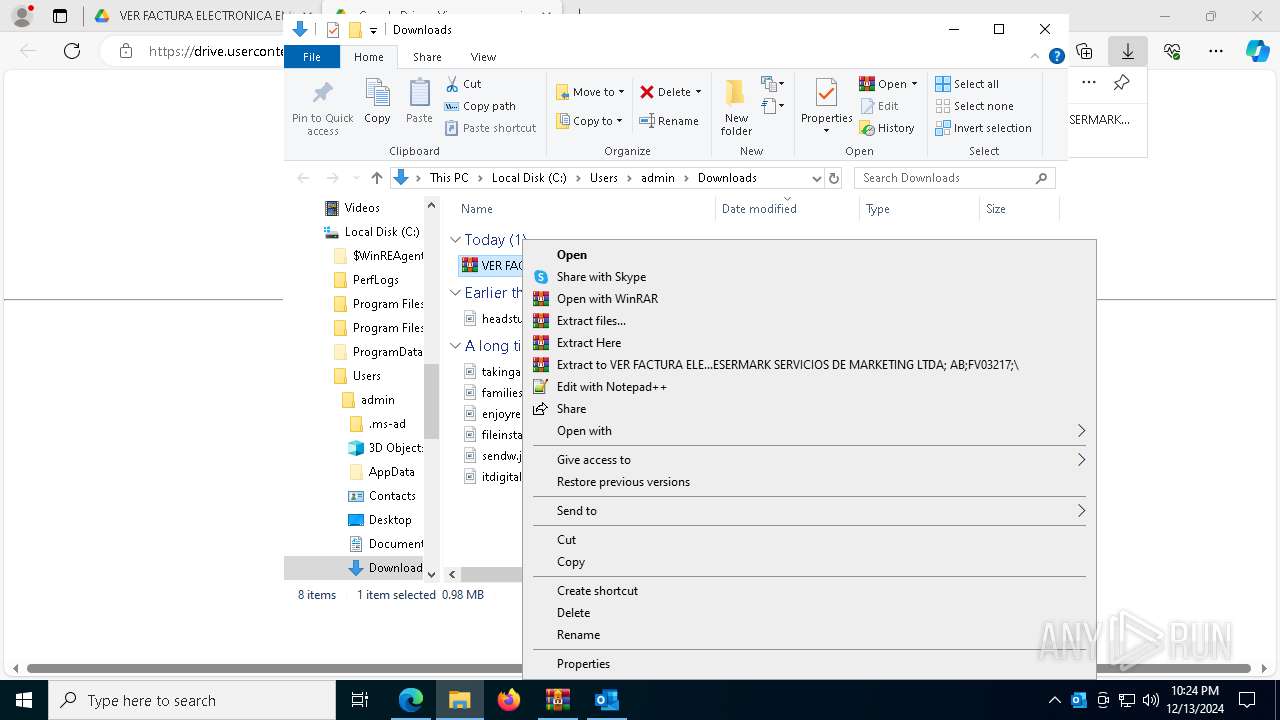
| File name: | 900368162; PESERMARK SERVICIOS DE MARKETING LTDA; DOCUMENTO EQUI-password(Medellin2024).zip |
| Full analysis: | https://app.any.run/tasks/9706d7cb-46d5-4dbc-a28f-c5d845fc26bf |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | December 13, 2024, 22:24:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
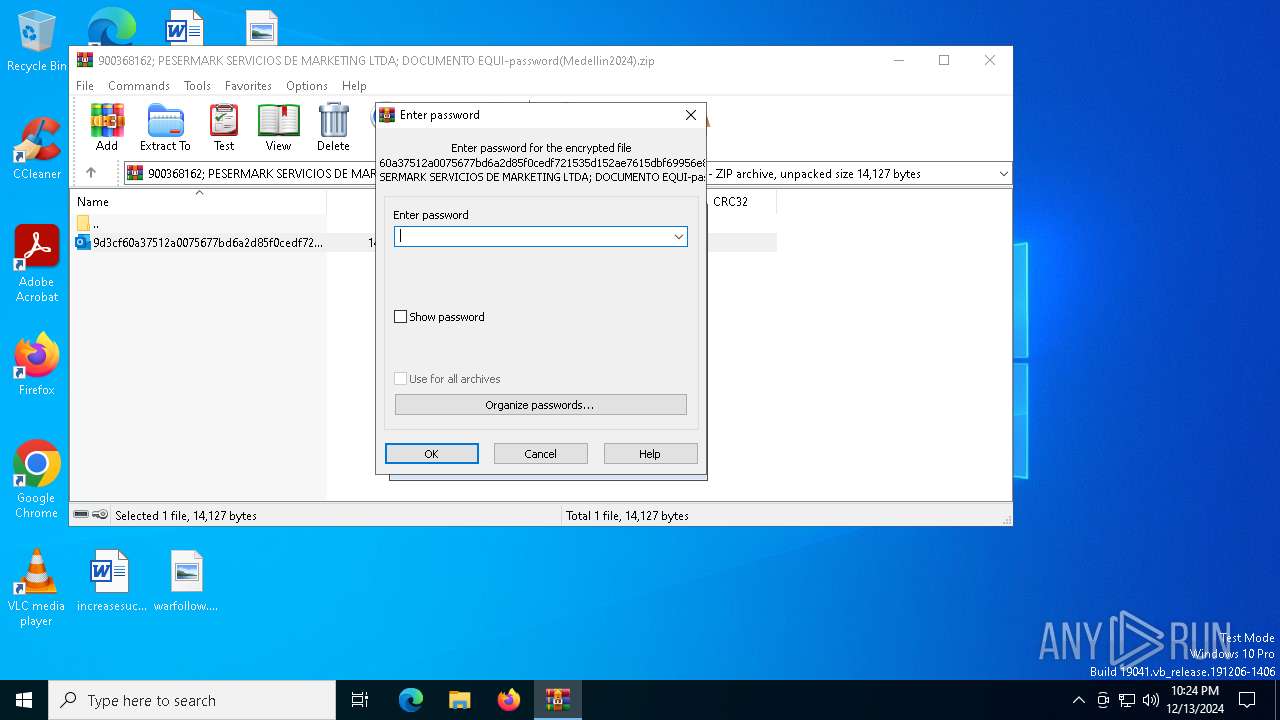
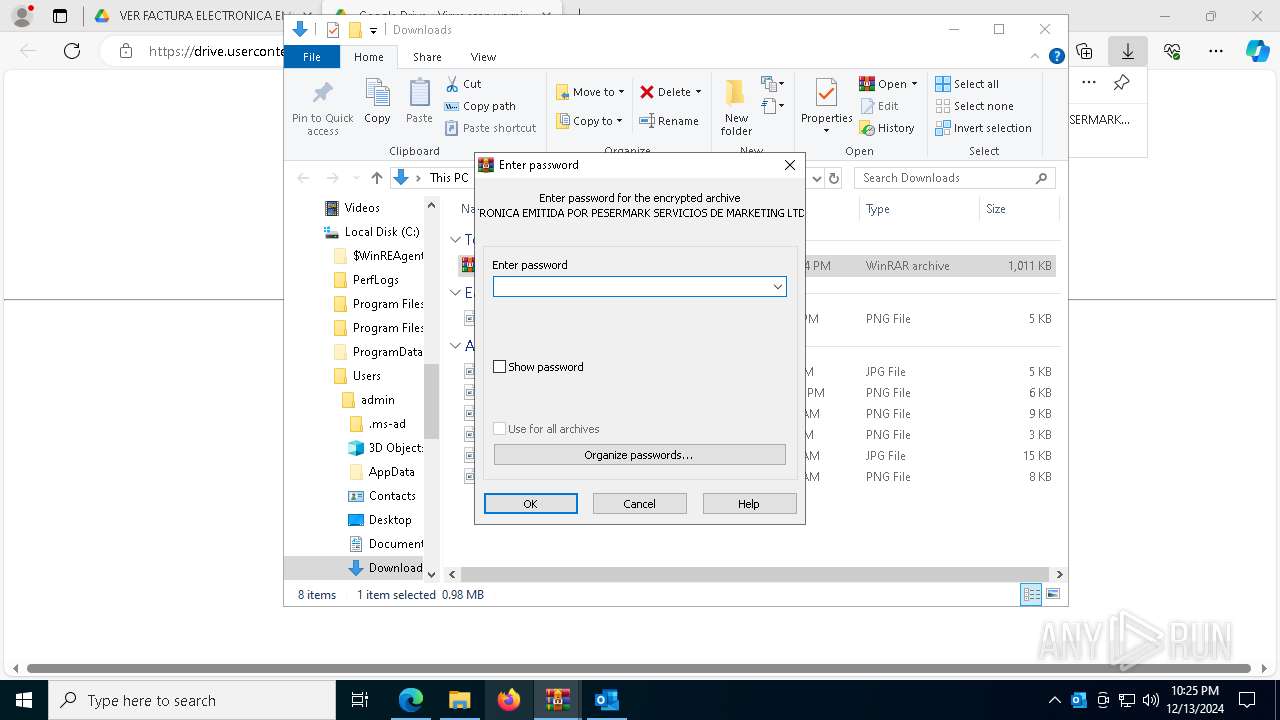
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 1F2A69B3C066AE9F58EF74BDC81BBE2B |
| SHA1: | 94B4E8DCDEAFB30C7BEB32474177EFEFF2559F8D |
| SHA256: | C5A00CDD4E967BBF101D8684EC5A1A2C7C51B5899FA71D26D23A3B92AA76D679 |
| SSDEEP: | 384:UZcNu/+W/6E6lMaHiv8ZD6E+hYtaumKYCSMGqgTNetkr:UX/+7l6kZb+hH65uqgTgt+ |
MALICIOUS
Create files in the Startup directory
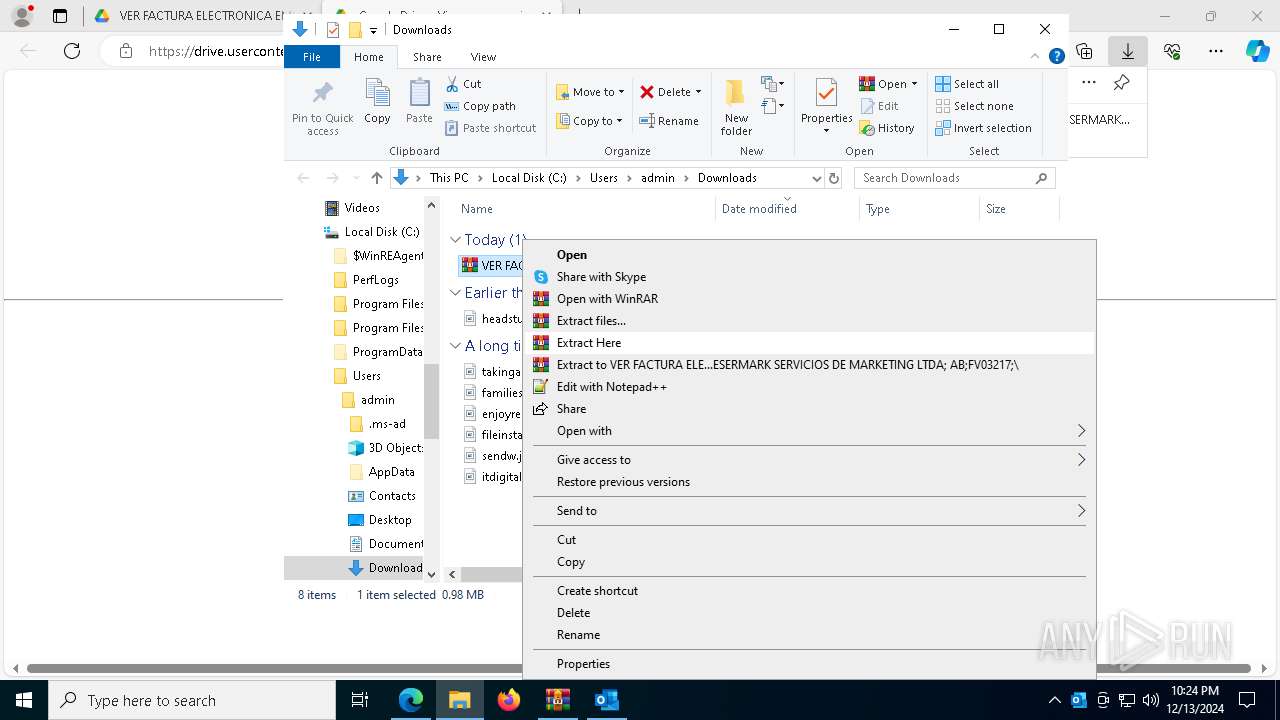
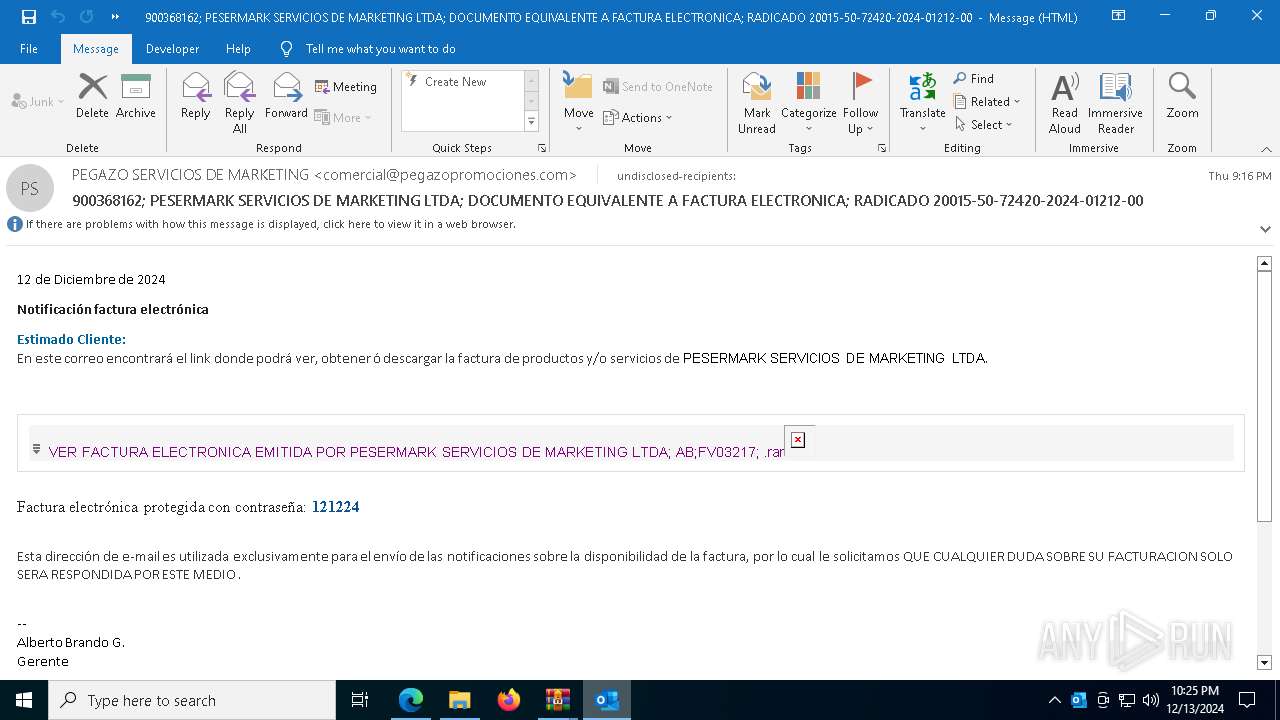
- VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe (PID: 7820)
ASYNCRAT has been detected (MUTEX)
- InstallUtil.exe (PID: 7316)
- InstallUtil.exe (PID: 7088)
PURECRYPTER has been detected (YARA)
- VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe (PID: 7820)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3612)
Reads Microsoft Outlook installation path
- WinRAR.exe (PID: 3612)
Executable content was dropped or overwritten
- VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe (PID: 7820)
Connects to unusual port
- InstallUtil.exe (PID: 7316)
INFO
Checks supported languages
- VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe (PID: 2792)
- identity_helper.exe (PID: 7592)
- InstallUtil.exe (PID: 7316)
- InstallUtil.exe (PID: 7088)
- VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe (PID: 7820)
.NET Reactor protector has been detected
- VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe (PID: 7820)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 3612)
The process uses the downloaded file
- WinRAR.exe (PID: 3612)
- OUTLOOK.EXE (PID: 6824)
- WinRAR.exe (PID: 7284)
Reads the computer name
- identity_helper.exe (PID: 7592)
- VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe (PID: 2792)
- InstallUtil.exe (PID: 7088)
- InstallUtil.exe (PID: 7316)
- VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe (PID: 7820)
Manual execution by a user
- WinRAR.exe (PID: 7284)
- VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe (PID: 2792)
- VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe (PID: 7820)
Reads Environment values
- identity_helper.exe (PID: 7592)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7284)
- msedge.exe (PID: 7284)
Application launched itself
- msedge.exe (PID: 6328)
Reads the machine GUID from the registry
- VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe (PID: 2792)
- InstallUtil.exe (PID: 7316)
- InstallUtil.exe (PID: 7088)
- VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe (PID: 7820)
Creates files or folders in the user directory
- VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe (PID: 7820)
The sample compiled with english language support
- msedge.exe (PID: 7284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0801 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:12:13 22:23:24 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 14155 |
| ZipUncompressedSize: | 14127 |
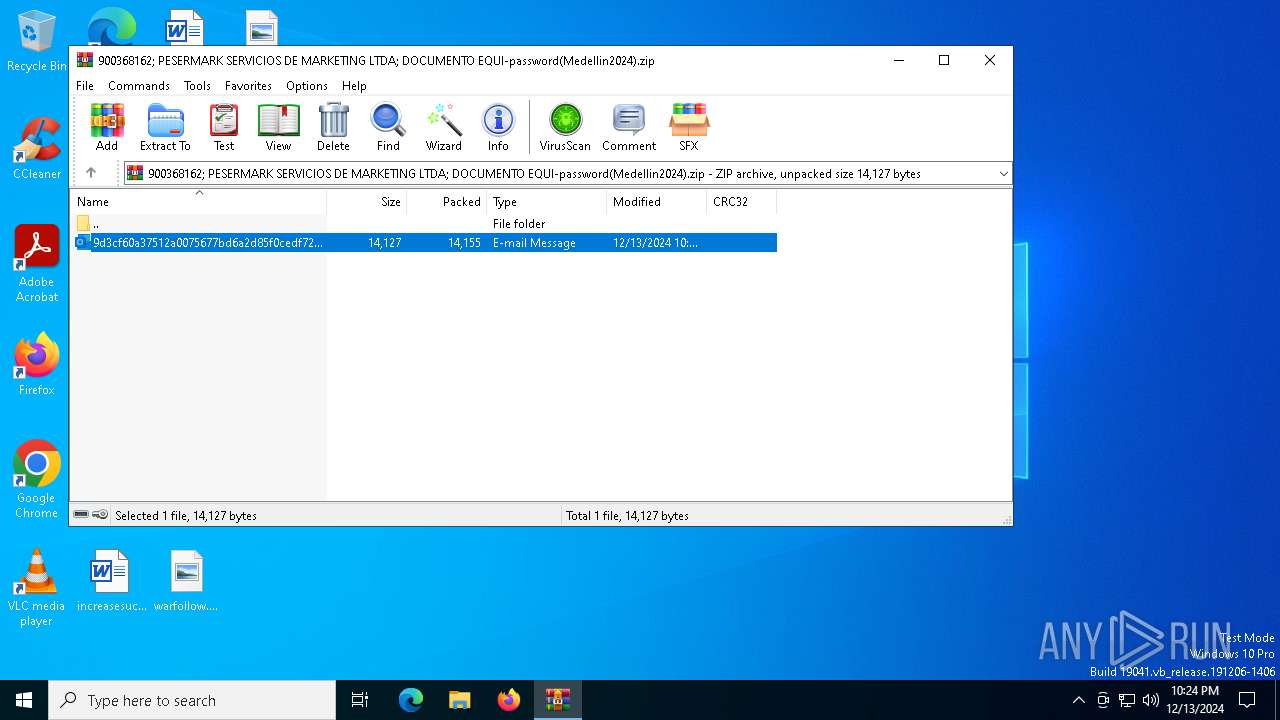
| ZipFileName: | 9d3cf60a37512a0075677bd6a2d85f0cedf721535d152ae7615dbf69956e8c30.eml |
Total processes
192
Monitored processes
60
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1356 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=5264 --field-trial-handle=2352,i,5580149832654451248,10440173939369925340,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2088 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=3524 --field-trial-handle=2352,i,5580149832654451248,10440173939369925340,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2160 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x304,0x308,0x30c,0x300,0x314,0x7ff812ec5fd8,0x7ff812ec5fe4,0x7ff812ec5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2432 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3728 --field-trial-handle=2352,i,5580149832654451248,10440173939369925340,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2548 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7380 --field-trial-handle=2352,i,5580149832654451248,10440173939369925340,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2672 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4100 --field-trial-handle=2352,i,5580149832654451248,10440173939369925340,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2792 | "C:\Users\admin\Downloads\VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217;\VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe" | C:\Users\admin\Downloads\VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217;\VER FACTURA ELECTRONICA EMITIDA POR PESERMARK SERVICIOS DE MARKETING LTDA; AB;FV03217; .exe | explorer.exe | ||||||||||||
User: admin Company: Auslogics Software Pty Ltd. Integrity Level: HIGH Description: Auslogics BoostSpeed v13.0.0.8 Exit code: 4294967295 Version: 13.0.0.8 Modules
| |||||||||||||||
| 2796 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5488 --field-trial-handle=2352,i,5580149832654451248,10440173939369925340,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2800 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "5B95E9F3-CF84-4762-AE0A-13A24CA866F0" "B55BF9D4-4865-47EC-A57C-B690D0BB8DBA" "6824" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
20 131
Read events
19 649
Write events
413
Delete events
69
Modification events
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\900368162; PESERMARK SERVICIOS DE MARKETING LTDA; DOCUMENTO EQUI-password(Medellin2024).zip | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.eml\OpenWithProgids |
| Operation: | write | Name: | Outlook.File.eml.15 |
Value: | |||
Executable files
5
Suspicious files
238
Text files
61
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6824 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 3612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3612.46531\9d3cf60a37512a0075677bd6a2d85f0cedf721535d152ae7615dbf69956e8c30.eml:OECustomProperty | binary | |
MD5:97FC650E1537DC50A7619CD0D0D5CF18 | SHA256:BD11E32EDA8A328991950027272CACBF4541EED7EB6004E0F3143E7480CDC9C7 | |||
| 6824 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_9AA25162313ED8429B4ADF0F3FB4F7A3.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 6824 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:9C404AB427690087A96502DF70818693 | SHA256:D2081D6754C80C25E19B511BB1B61E7D9802DFC35E681DFCABA79E08F902075C | |||
| 6824 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\F1989282-F2BF-4DF9-ACDD-DB6BE895C2DD | xml | |
MD5:1D5B8A7E53F91B7314A25C81DC6F3A23 | SHA256:79FD4D3552D1DB1208DC9BCD284E474B75F097EB3096C6FA338A94C3C03F8FCA | |||
| 6824 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:518804856D97A8639DE17D8FEA3A2B89 | SHA256:4C112AC58363CD44E0480CAF1E99D422E642C975A12301AEC4EFA9D4D288A2A7 | |||
| 6824 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:D0CF2208C22DD66108FC7E1CFA45D0D6 | SHA256:87A25154EEF7FACE20442460D29BC9D6A84A9F415431D6D5904278F75B833D7F | |||
| 6824 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:A5DAA60C6C34DD2B7DE0A23C739D94B6 | SHA256:176185FF8406C36CD44FD684D5D12B51DEA5CBBB9325A76C5FF354E91D974697 | |||
| 3612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3612.46531\9d3cf60a37512a0075677bd6a2d85f0cedf721535d152ae7615dbf69956e8c30.eml | text | |
MD5:A0D3DA5768BF87A2EAB675A5039C78BE | SHA256:2384B199AA0E4FB8E53532A0FF89843E695A3495F1008F6C6294771DF3CBCAEC | |||
| 6824 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:FC581A397CF2F0C7AE9FE962CE6055CA | SHA256:8EEC42FD9FA9BB8BBADEF063C4E51BE95E49B55CACC5F299142208E829897CFF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
49
TCP/UDP connections
122
DNS requests
118
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5004 | svchost.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5004 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6824 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6824 | OUTLOOK.EXE | GET | 200 | 142.250.185.227:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
6824 | OUTLOOK.EXE | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
6824 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6824 | OUTLOOK.EXE | GET | 200 | 142.250.184.195:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEBJQjvg7PbcVEnGOkToQ3qM%3D | unknown | — | — | whitelisted |
6372 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5004 | svchost.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5004 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.149:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2192 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |