| File name: | 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader |
| Full analysis: | https://app.any.run/tasks/8a09e807-04a1-4216-82b0-0c6ef05f6a67 |
| Verdict: | Malicious activity |
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | May 12, 2025, 04:20:52 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 43637CD23DA0511E26C3F3DBB27CABC6 |
| SHA1: | 40F1B9B9D4C5EF305BADD847DC731ECAC94582C9 |
| SHA256: | C56D70051097BD2D186B81177D1E211DFF2FB493DEA37214207CA4085C4F8F8F |
| SSDEEP: | 98304:6YKgYQ2iJIntKffM6z/wudo9jj3vCJbzjCDkZHguw75ODBqtppaxcZZusI9qfjIO:ZLeNQ |
MALICIOUS
DARKCOMET mutex has been found
- SCAM0001338.exe (PID: 5112)
Changes the autorun value in the registry
- SCAM0001338.exe (PID: 5112)
SUSPICIOUS
Starts a Microsoft application from unusual location
- 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe (PID: 2656)
Process drops legitimate windows executable
- 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe (PID: 2656)
Reads security settings of Internet Explorer
- 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe (PID: 2656)
- SCAM00~1.EXE (PID: 5008)
Reads the date of Windows installation
- 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe (PID: 2656)
- SCAM00~1.EXE (PID: 5008)
Executable content was dropped or overwritten
- 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe (PID: 2656)
- SCAM0001341.EXE (PID: 4180)
- SCAM00~1.EXE (PID: 5008)
- SCAM0001338.exe (PID: 5112)
The process creates files with name similar to system file names
- SCAM0001338.exe (PID: 5112)
INFO
The sample compiled with Italian language support
- 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe (PID: 2656)
Creates files or folders in the user directory
- 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe (PID: 2656)
- SCAM0001338.exe (PID: 5112)
- SCAM00~1.EXE (PID: 5008)
Checks proxy server information
- 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe (PID: 2656)
- SCAM00~1.EXE (PID: 5008)
Checks supported languages
- 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe (PID: 2656)
- SCAM0001341.EXE (PID: 4180)
- explorer.exe (PID: 1228)
- SCAM0001338.exe (PID: 5112)
- _iexplore.exe (PID: 4408)
- SCAM00~1.EXE (PID: 5008)
Reads the computer name
- 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe (PID: 2656)
- SCAM0001341.EXE (PID: 4180)
- SCAM0001338.exe (PID: 5112)
- SCAM00~1.EXE (PID: 5008)
Reads the machine GUID from the registry
- 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe (PID: 2656)
- SCAM00~1.EXE (PID: 5008)
Process checks computer location settings
- 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe (PID: 2656)
- SCAM00~1.EXE (PID: 5008)
Create files in a temporary directory
- SCAM0001341.EXE (PID: 4180)
The sample compiled with english language support
- SCAM0001341.EXE (PID: 4180)
- SCAM00~1.EXE (PID: 5008)
Manual execution by a user
- mspaint.exe (PID: 2504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (20.7) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (15) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.1) |
| .exe | | | Win32 Executable (generic) (2.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:11:19 09:11:39+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 16384 |
| InitializedDataSize: | 45056 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4007 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.0.2900.5512 |
| ProductVersionNumber: | 6.0.2900.5512 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Italian |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Programma di autoestrazione di file CAB Win32 |
| FileVersion: | 6.00.2900.5512 (xpsp.080413-2105) |
| InternalName: | Wextract |
| LegalCopyright: | © Microsoft Corporation. Tutti i diritti riservati. |
| OriginalFileName: | WEXTRACT.EXE |
| ProductName: | Sistema operativo Microsoft® Windows® |
| ProductVersion: | 6.00.2900.5512 |
Total processes
138
Monitored processes
10
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1228 | "C:\WINDOWS\explorer.exe" | C:\Users\admin\AppData\Local\Spoon\Sandbox\Roxio ScreenSaver 4\4.539.254.128\local\stubexe\0xBAB7ACF5DA21772B\explorer.exe | — | SCAM0001338.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
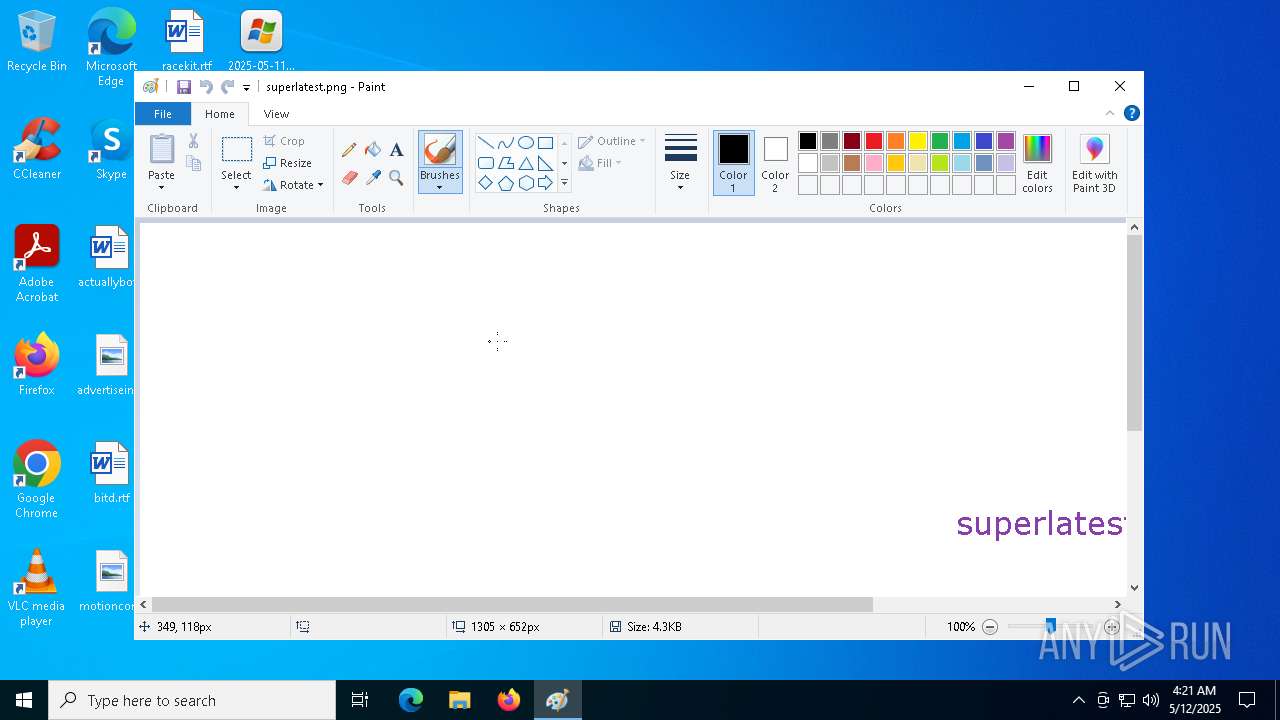
| 2504 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\superlatest.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2656 | "C:\Users\admin\Desktop\2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe" | C:\Users\admin\Desktop\2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Programma di autoestrazione di file CAB Win32 Version: 6.00.2900.5512 (xpsp.080413-2105) Modules
| |||||||||||||||
| 4180 | "C:\Users\admin\Desktop\SCAM0001341.EXE" | C:\Users\admin\AppData\Local\Spoon\Sandbox\WnSoft PicturesToExe\7.5.5.4\local\stubexe\0xAF5DCA131B6C3A5F\SCAM0001341.EXE | 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4408 | "C:\Program Files (x86)\Internet Explorer\iexplore.exe" | C:\Users\admin\AppData\Local\Spoon\Sandbox\Roxio ScreenSaver 4\4.539.254.128\local\stubexe\0x669E9037ADCF49BE\_iexplore.exe | — | SCAM0001338.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4980 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5008 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\SCAM00~1.EXE | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\SCAM00~1.EXE | SCAM0001341.EXE | ||||||||||||
User: admin Company: ROXIO Integrity Level: MEDIUM Description: Remote Service Application Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 5112 | "C:\Users\admin\Desktop\SCAM0001338.exe" | C:\Users\admin\AppData\Local\Spoon\Sandbox\Roxio ScreenSaver 4\4.539.254.128\local\stubexe\0x770423AF92A05AD0\SCAM0001338.exe | SCAM00~1.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5544 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 437
Read events
3 387
Write events
49
Delete events
1
Modification events
| (PID) Process: | (2656) 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2656) 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2656) 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2656) 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (5008) SCAM00~1.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5008) SCAM00~1.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (5008) SCAM00~1.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (5008) SCAM00~1.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (5112) SCAM0001338.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicroUpdate |
Value: C:\Users\admin\Documents\MSDCSC\msdcsc.exe | |||
| (PID) Process: | (2504) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\Text |
| Operation: | write | Name: | CharSet |
Value: 0 | |||
Executable files
8
Suspicious files
8
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2656 | 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe | C:\Users\admin\AppData\Local\Spoon\Sandbox\WnSoft PicturesToExe\7.5.5.4\local\modified\@DESKTOP@\SCAM0001341.EXE | executable | |
MD5:868389745C0A5300A7FB5CF3C25F7278 | SHA256:4DBCC28E121E64325A83B50BB9CDAA91343F3C4A3E06BB3C406ABE65E46013F9 | |||
| 5008 | SCAM00~1.EXE | C:\Users\admin\AppData\Local\Spoon\Sandbox\Roxio ScreenSaver 4\4.539.254.128\local\meta\@DESKTOP@\SCAM0001338.exe.__meta__ | binary | |
MD5:3EEBFC7B5C2A776FB04B925EFB0DC4BE | SHA256:CC71D1CB97AA3A5A510A57A8501FE58D1670E719173FB5AA3AA7D202297C4C4D | |||
| 5008 | SCAM00~1.EXE | C:\Users\admin\AppData\Local\Spoon\Sandbox\Roxio ScreenSaver 4\4.539.254.128\xsandbox.bin | binary | |
MD5:EC3D19E8E9B05D025CB56C2A98EAD8E7 | SHA256:EDB7BE3EF6098A1E24D0C72BBC6F968DEA773951A0DD07B63BAD6D9009AE3BF4 | |||
| 4180 | SCAM0001341.EXE | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\SCAM00~1.EXE | executable | |
MD5:E7C5F8D76D47ECA23FCFDA58C718C6BD | SHA256:4A160717B0165A880F75CDC97D6D3CABB8AA1BC7131B677270021DF45B824D21 | |||
| 5008 | SCAM00~1.EXE | C:\Users\admin\AppData\Local\Spoon\Sandbox\Roxio ScreenSaver 4\4.539.254.128\local\modified\@DESKTOP@\SCAM0001338.exe | executable | |
MD5:8497938F0F0D134F1A1F2FCD69F92EE0 | SHA256:4206B0CD1C5D511C40C4E41B414CC6D9DB6E3981BF4B3D267C60D2DC1AFA41F9 | |||
| 5112 | SCAM0001338.exe | C:\Users\admin\AppData\Local\Spoon\Sandbox\Roxio ScreenSaver 4\4.539.254.128\local\stubexe\0xBAB7ACF5DA21772B\explorer.exe | executable | |
MD5:68FDD5726AD02F78D763883C090D7803 | SHA256:307455EE59743AB436987AFB164964AC3D516035E5FDB3FBCBBE3D485271D22D | |||
| 2656 | 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe | C:\Users\admin\AppData\Local\Spoon\Sandbox\WnSoft PicturesToExe\7.5.5.4\xsandbox.bin | binary | |
MD5:EC3D19E8E9B05D025CB56C2A98EAD8E7 | SHA256:EDB7BE3EF6098A1E24D0C72BBC6F968DEA773951A0DD07B63BAD6D9009AE3BF4 | |||
| 2656 | 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe | C:\Users\admin\AppData\Local\Spoon\Sandbox\WnSoft PicturesToExe\7.5.5.4\local\stubexe\0xAF5DCA131B6C3A5F\SCAM0001341.EXE | executable | |
MD5:2F0662E216E1F71D495A75D210ED2684 | SHA256:F91039CB312249BA5ED342DAAA7FB280E111C15213BF82531C5A6BF2D6CCC18A | |||
| 2656 | 2025-05-11_43637cd23da0511e26c3f3dbb27cabc6_amadey_elex_smoke-loader.exe | C:\Users\admin\AppData\Local\Spoon\Sandbox\WnSoft PicturesToExe\7.5.5.4\local\meta\@DESKTOP@\SCAM0001341.EXE.__meta__ | binary | |
MD5:9E4E39FC5E109CACE16A2DF788417FA3 | SHA256:3E7D87313E58DE817F6793ADC8938E316EA512577EE1789CBB3DE9E17F098491 | |||
| 5008 | SCAM00~1.EXE | C:\Users\admin\AppData\Local\Spoon\Sandbox\Roxio ScreenSaver 4\4.539.254.128\local\stubexe\0x770423AF92A05AD0\SCAM0001338.exe | executable | |
MD5:DE67C4B66C0B9C24A9AE0A1862F06799 | SHA256:B03E7A0FF4029C30F2A79047ACEC145D5D7692F1C6F437AFEEF13656ACDA9B42 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
20
DNS requests
21
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6272 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6272 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
start.spoon.net |
| unknown |
logic32.no-ip.org |
| malicious |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a Suspicious no-ip Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a Suspicious no-ip Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a Suspicious no-ip Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a Suspicious no-ip Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a Suspicious no-ip Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a Suspicious no-ip Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a Suspicious no-ip Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a Suspicious no-ip Domain |