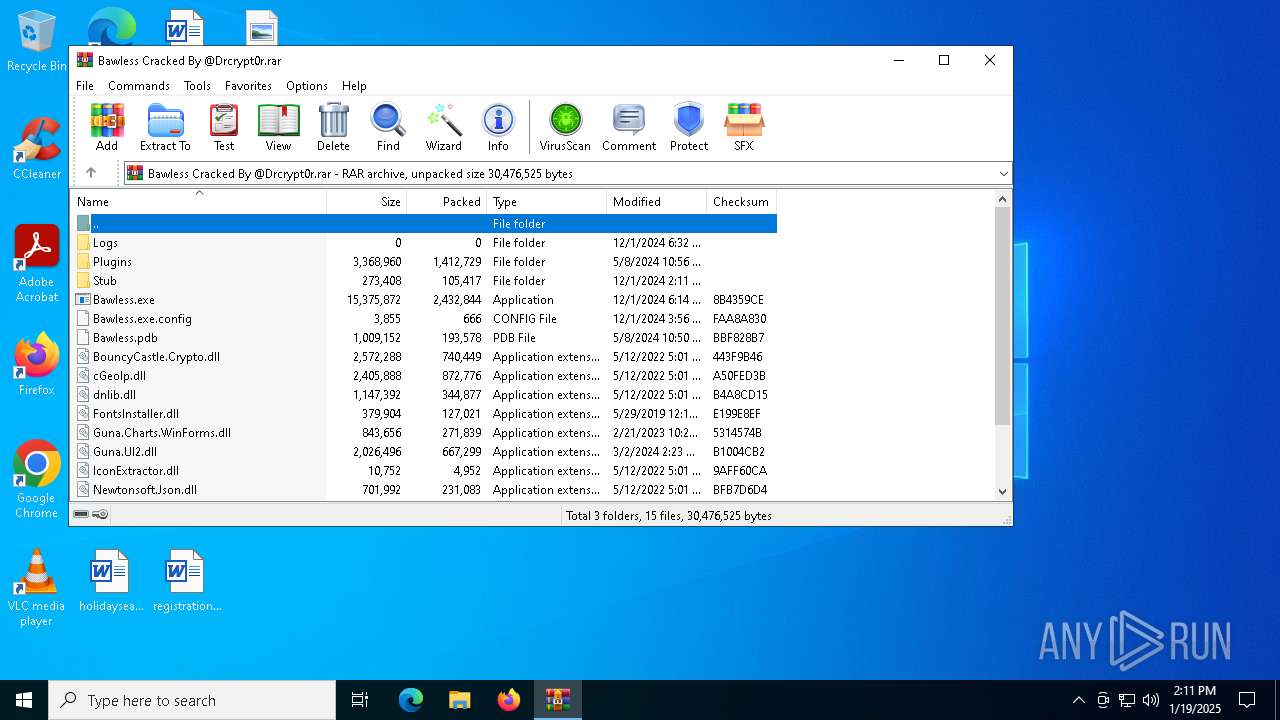
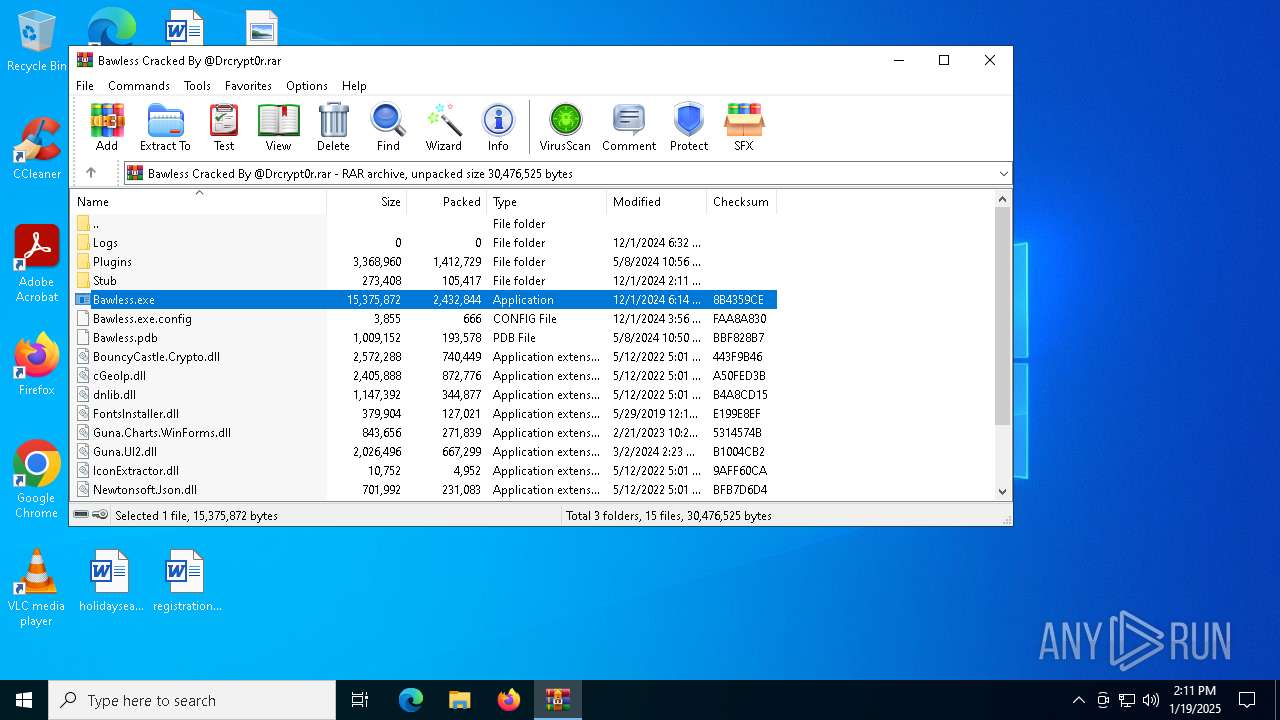
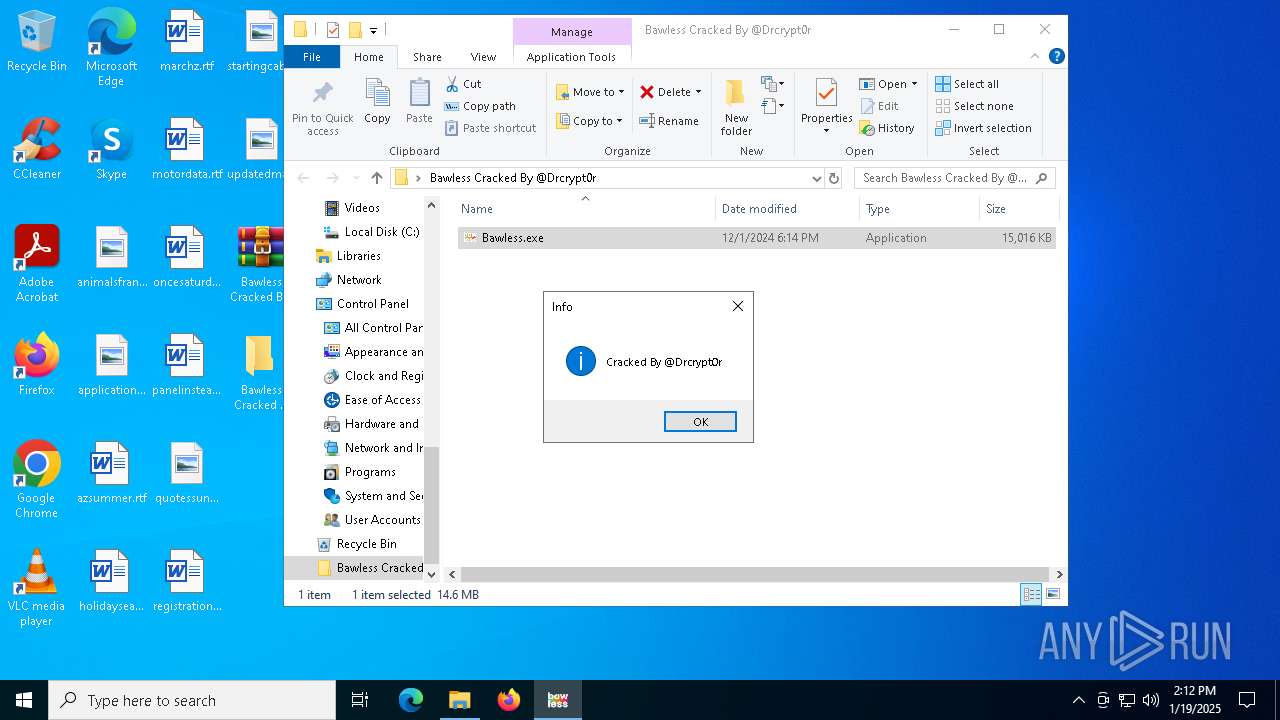
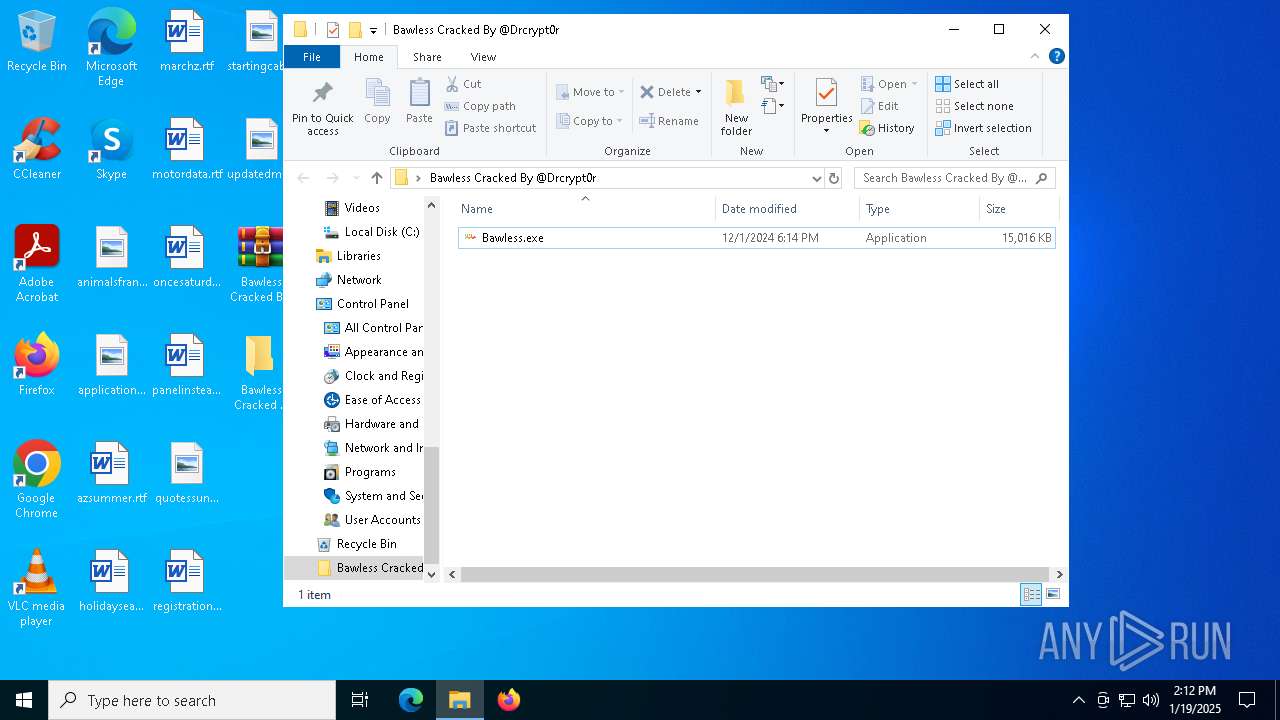
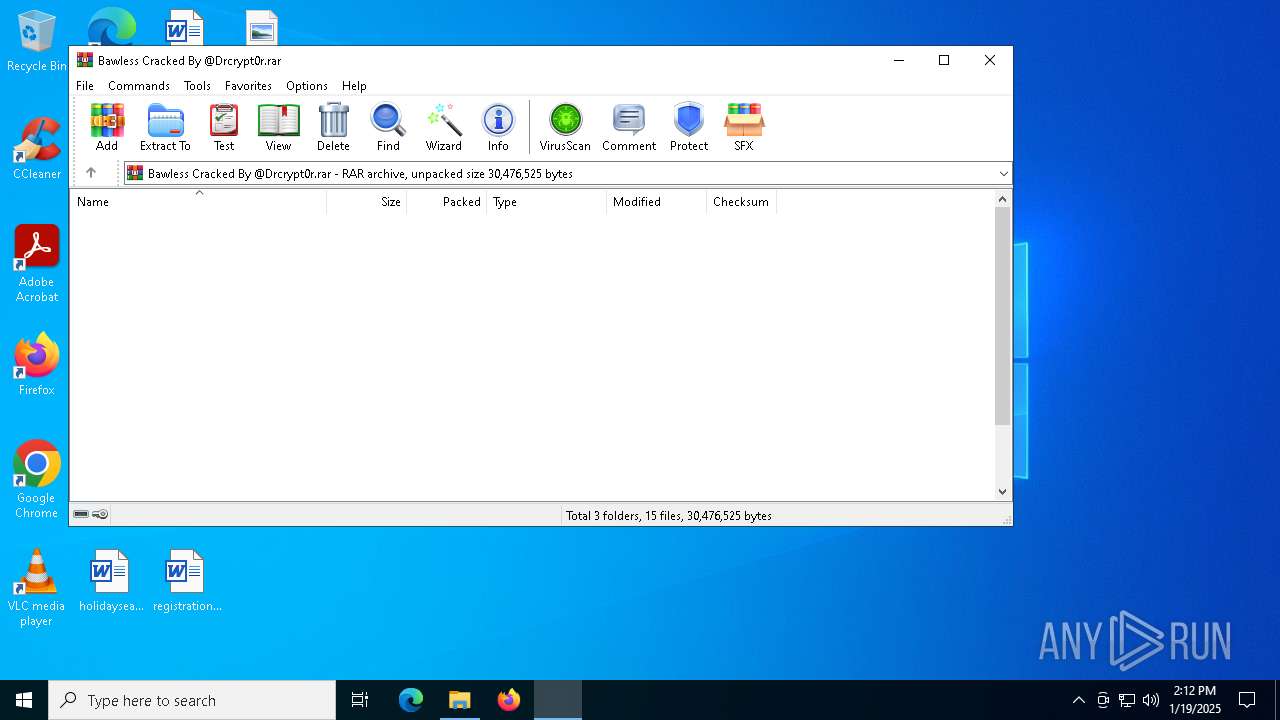
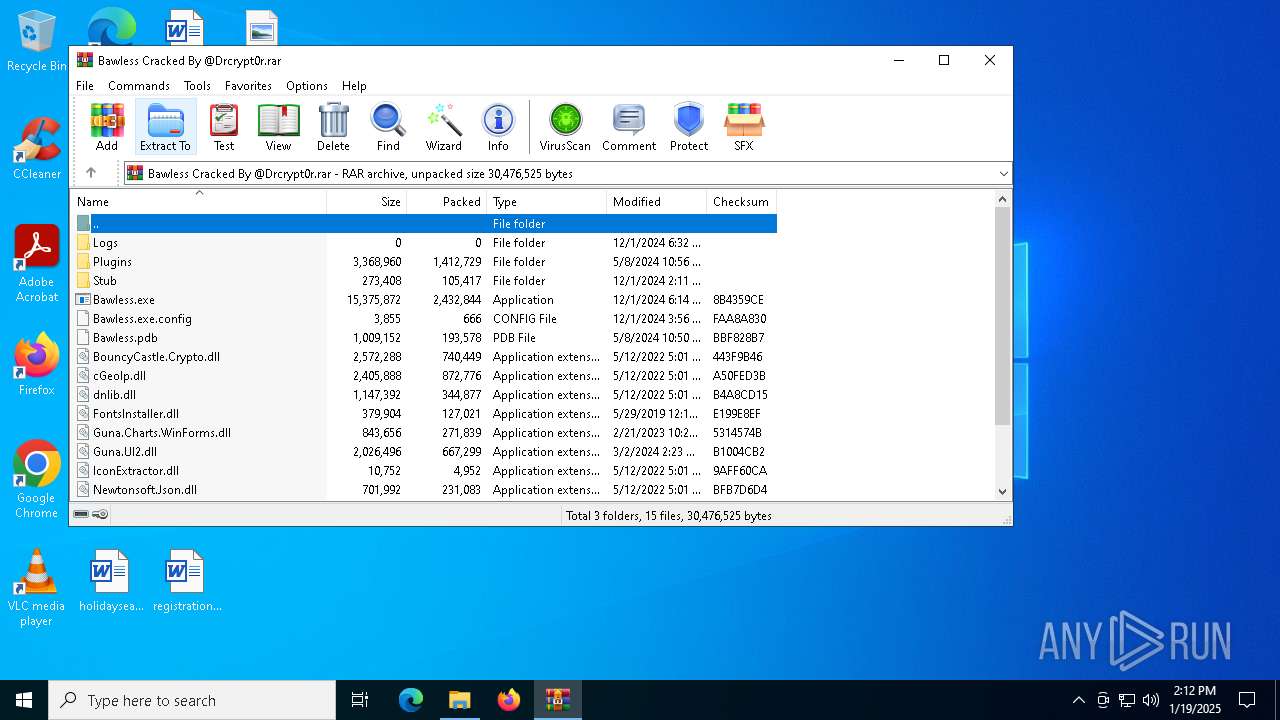
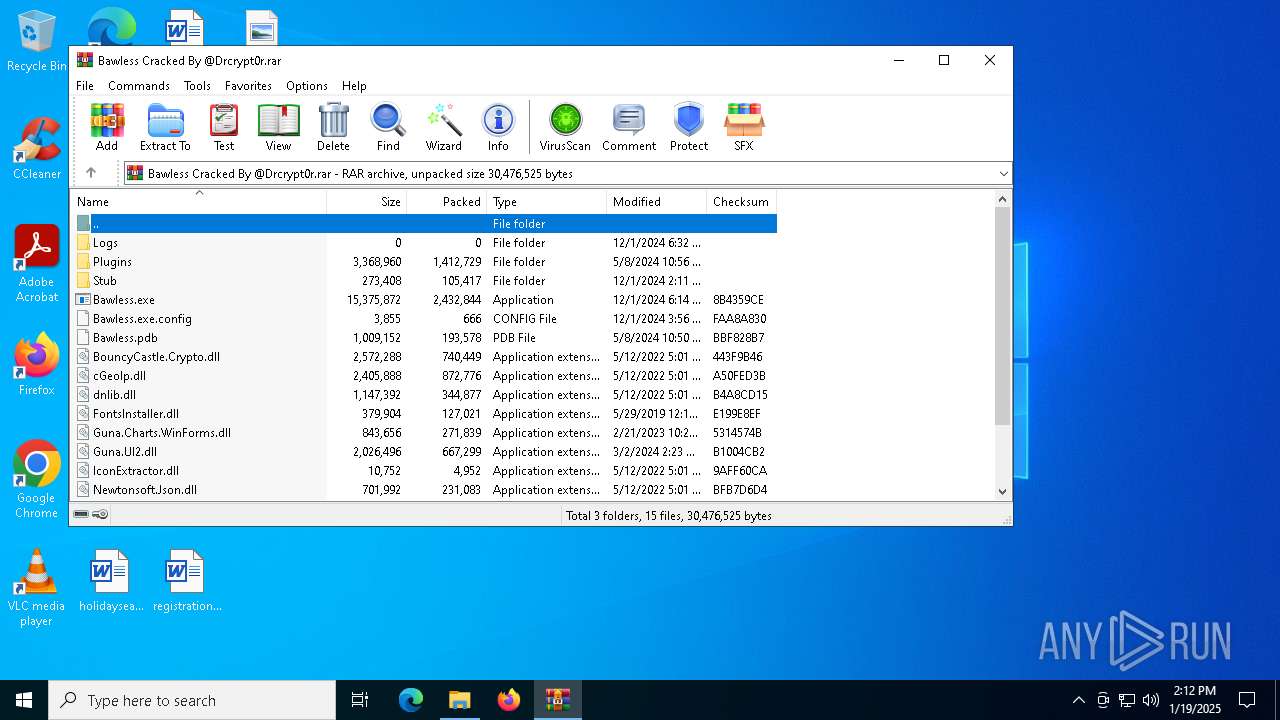
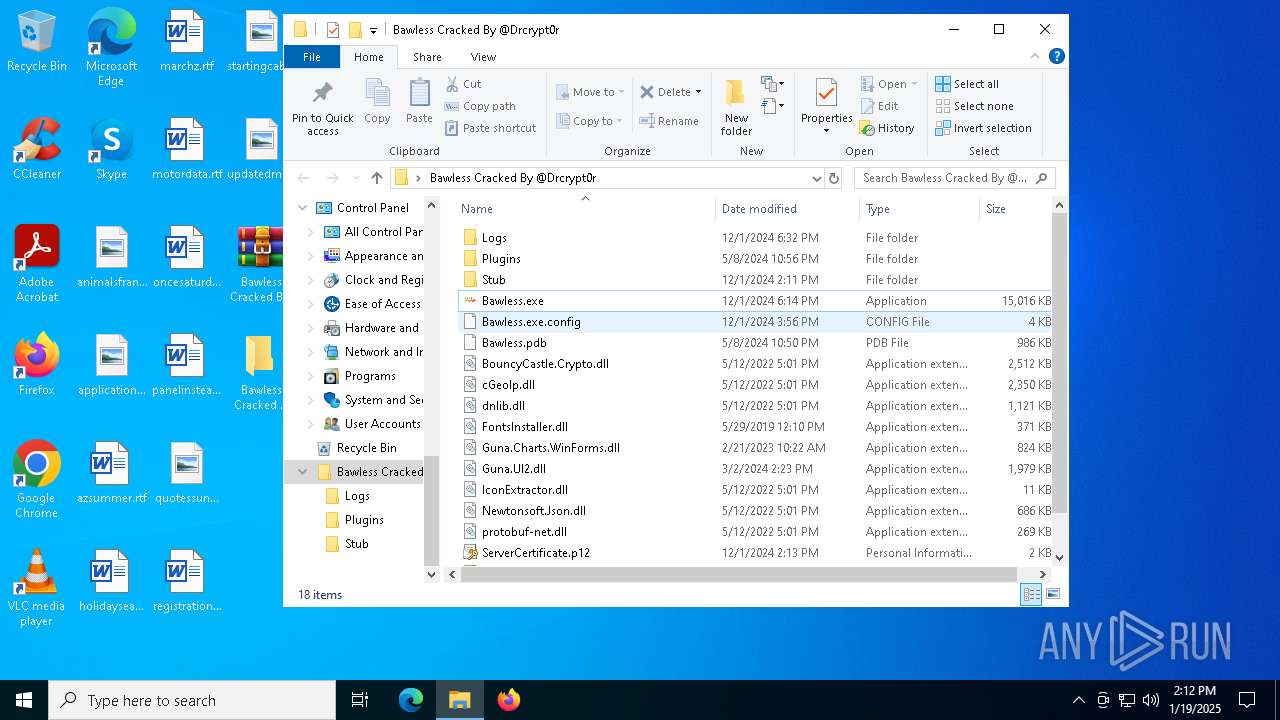
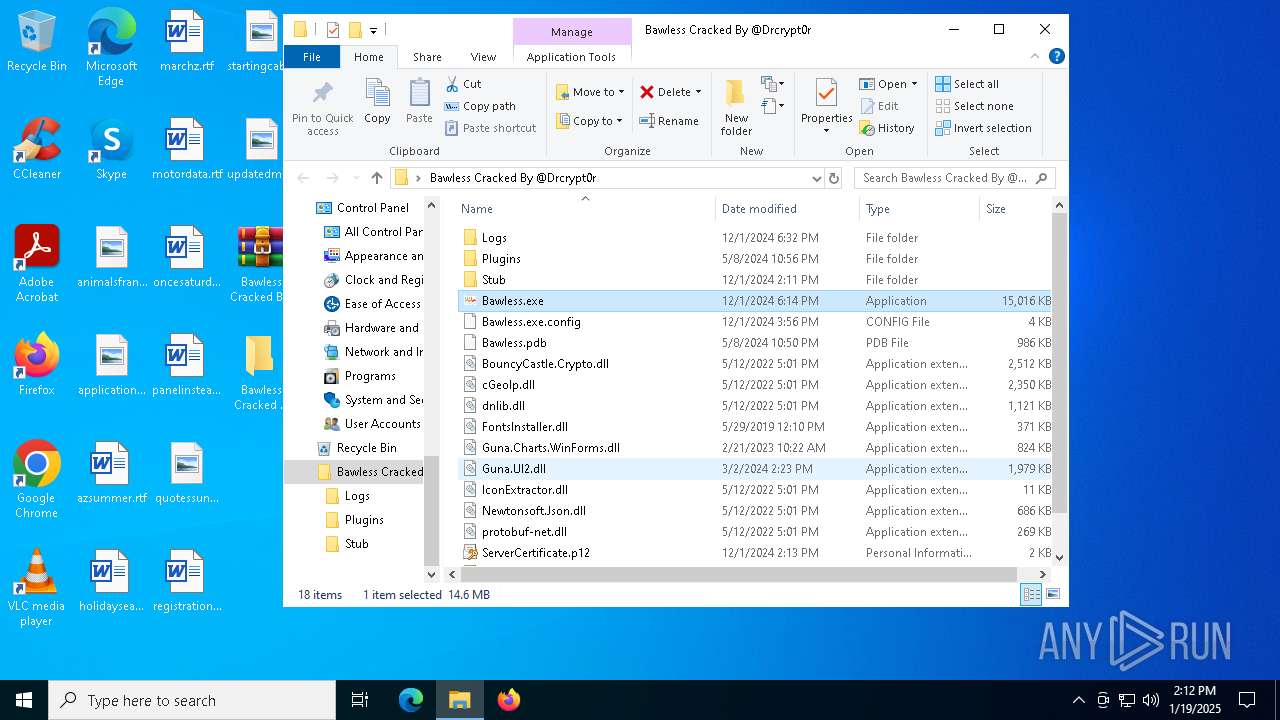
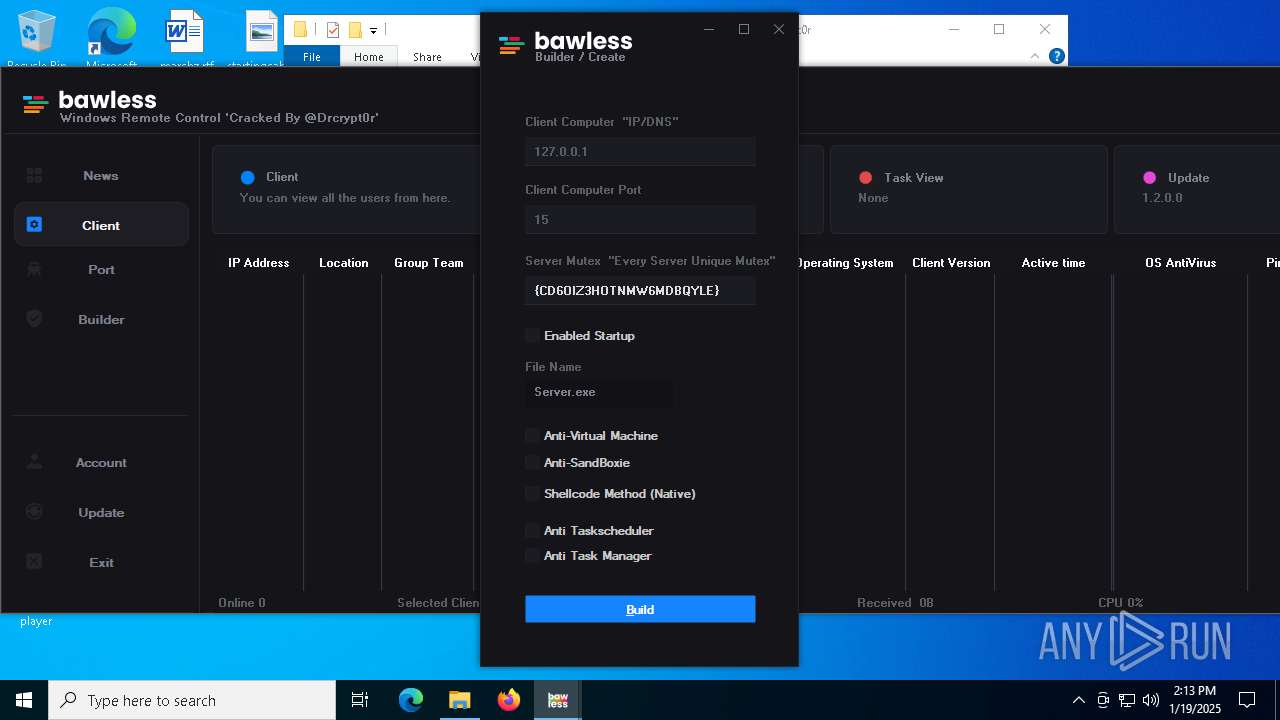
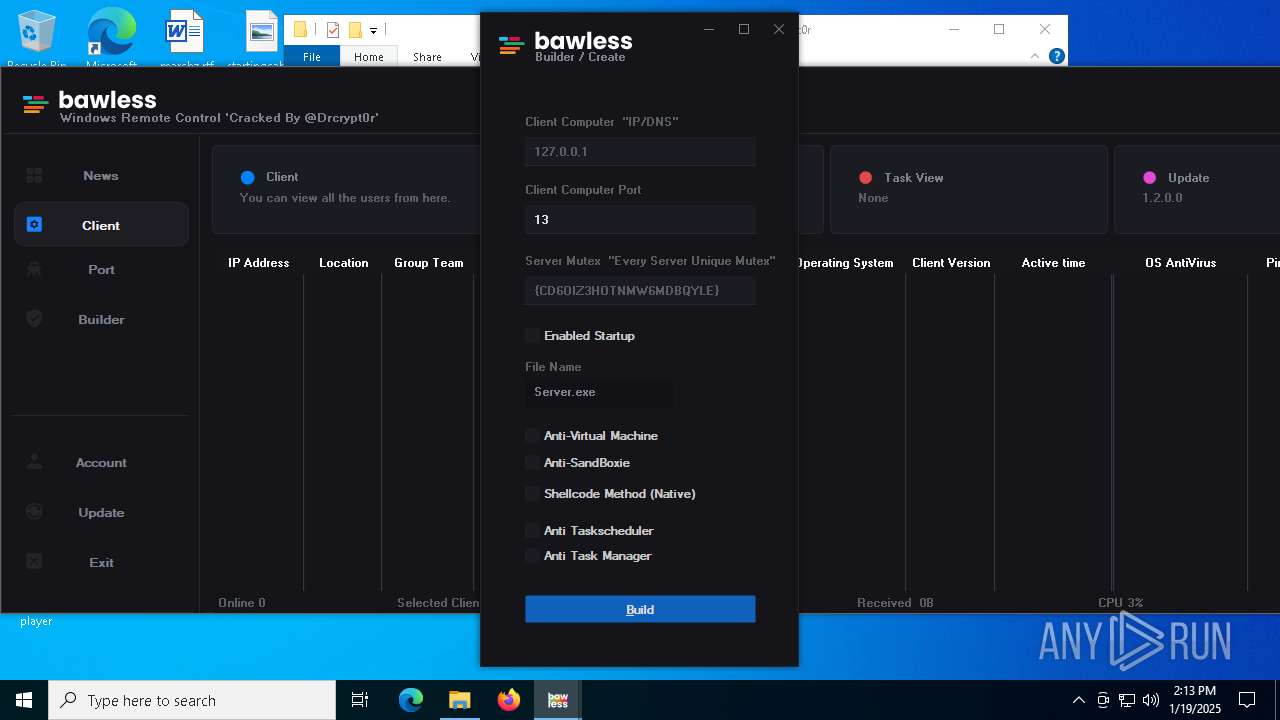
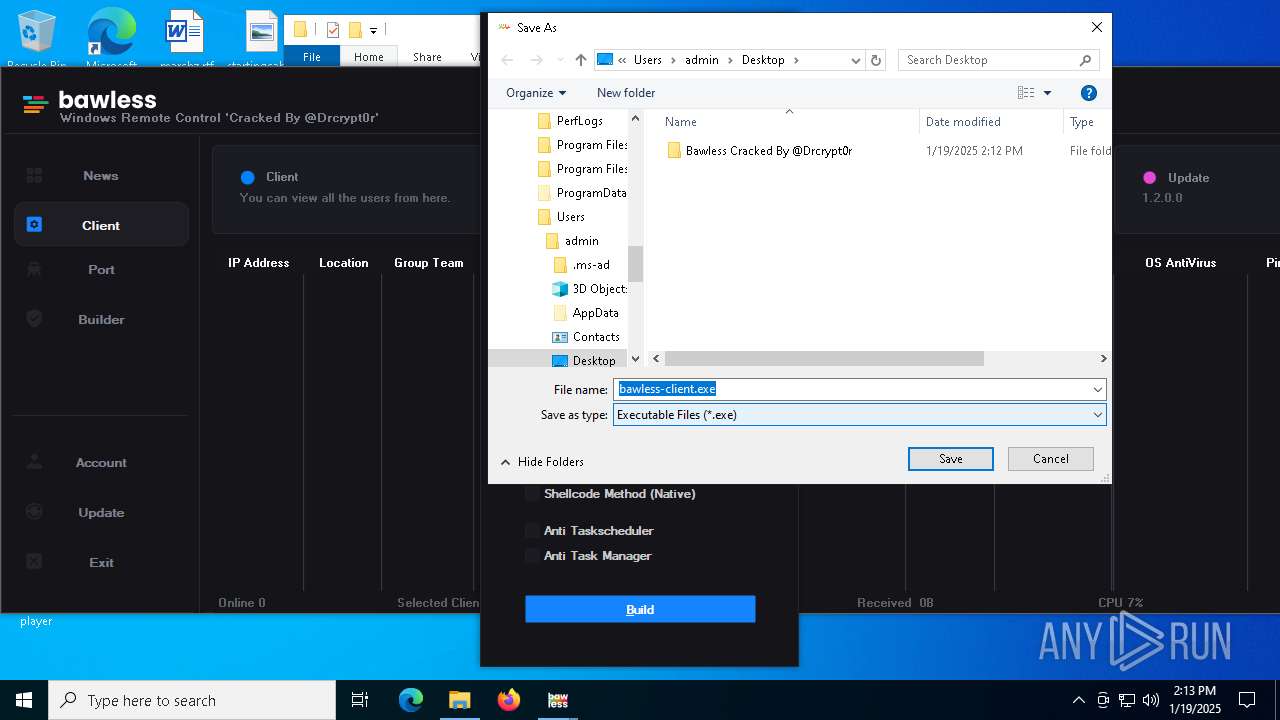
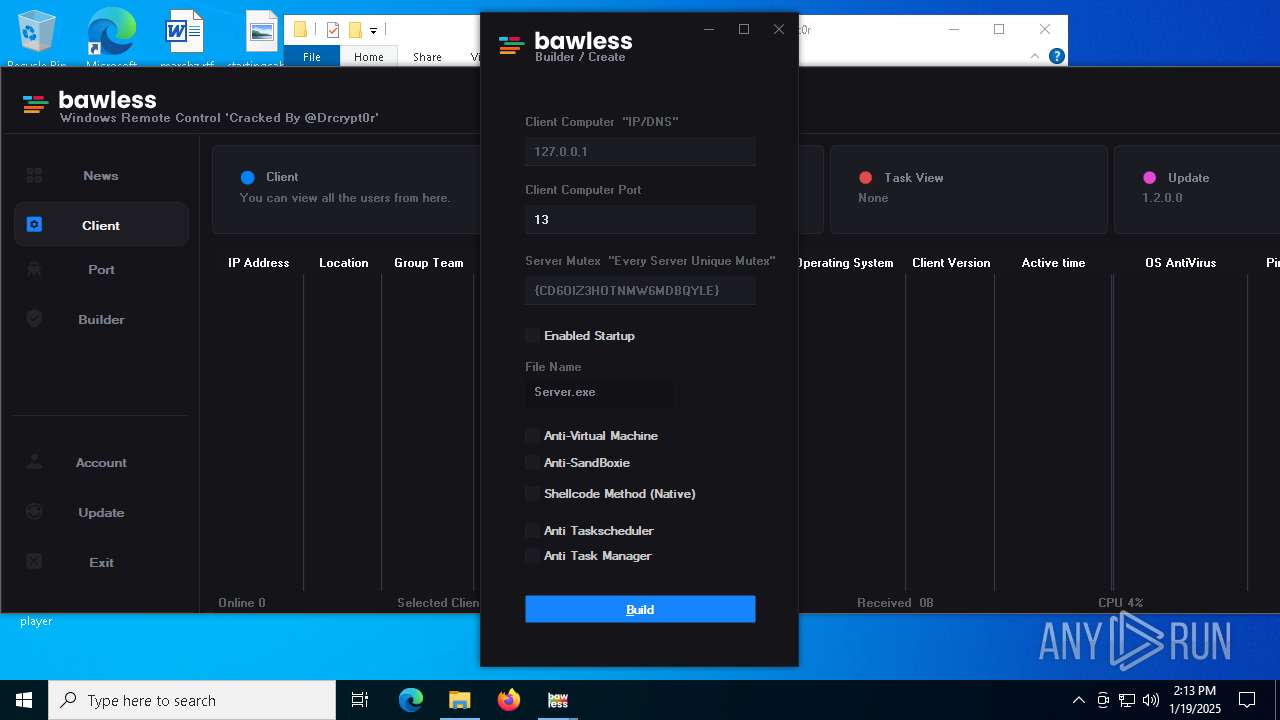
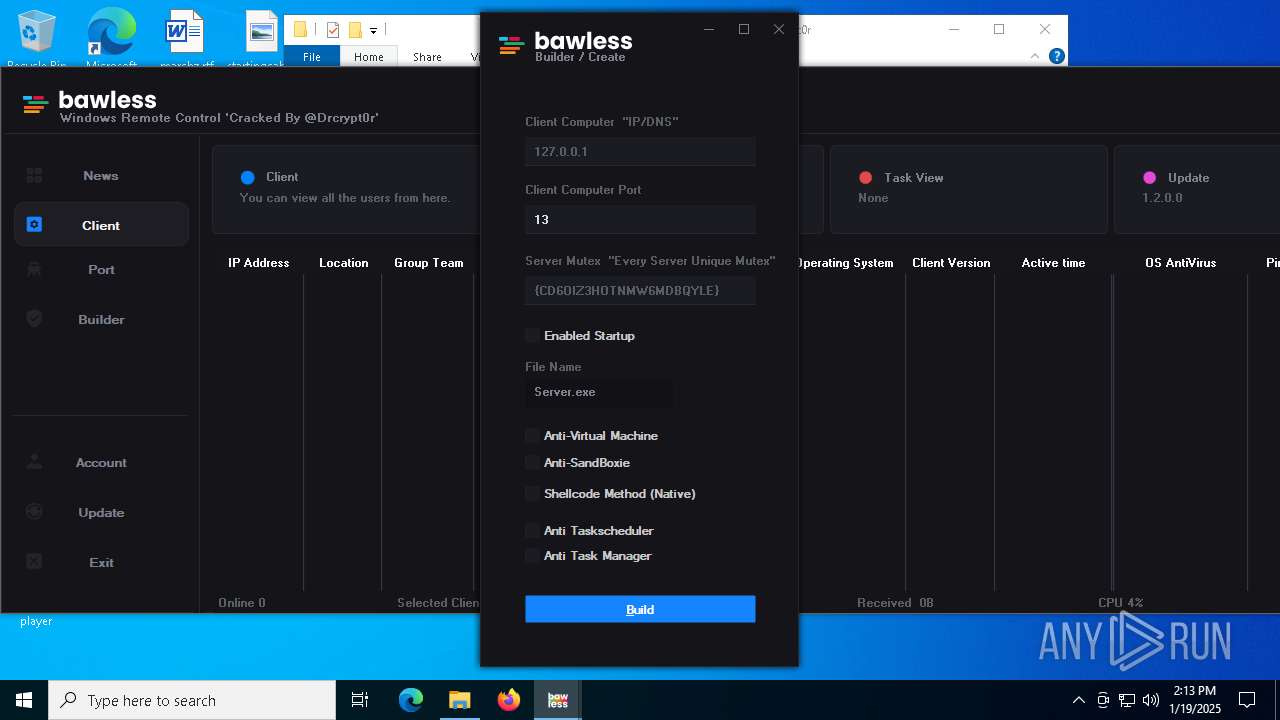
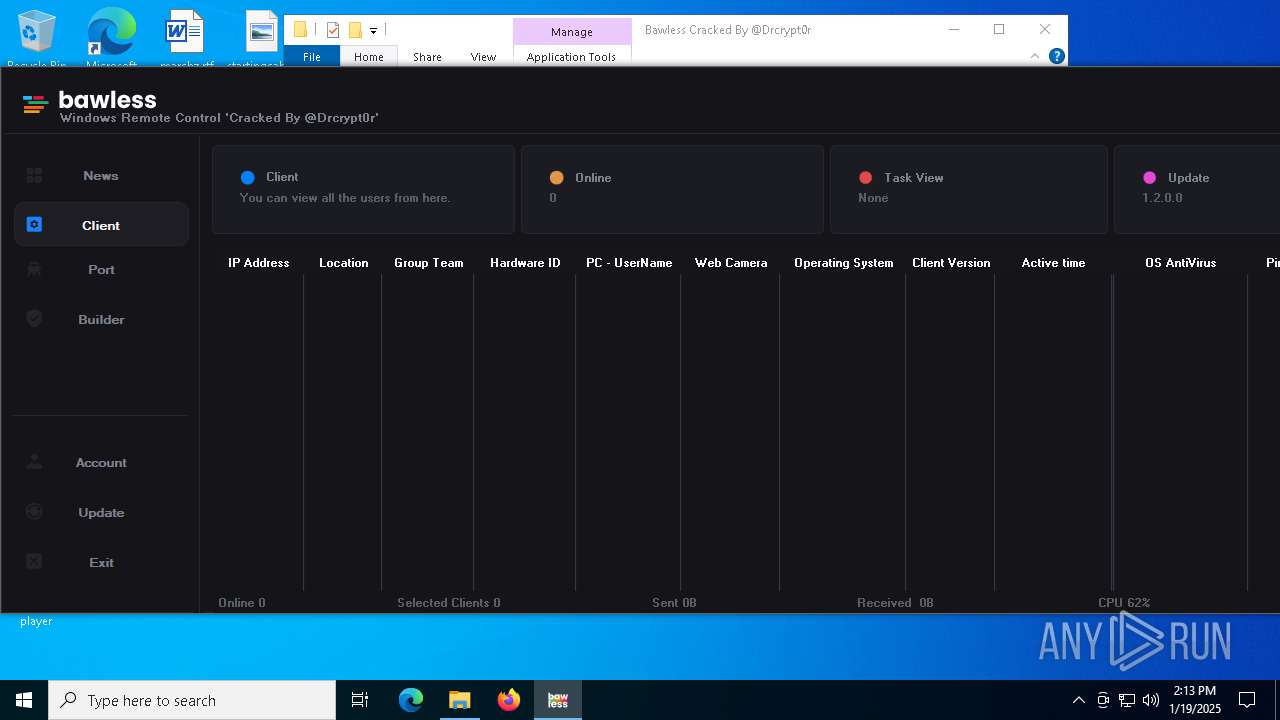
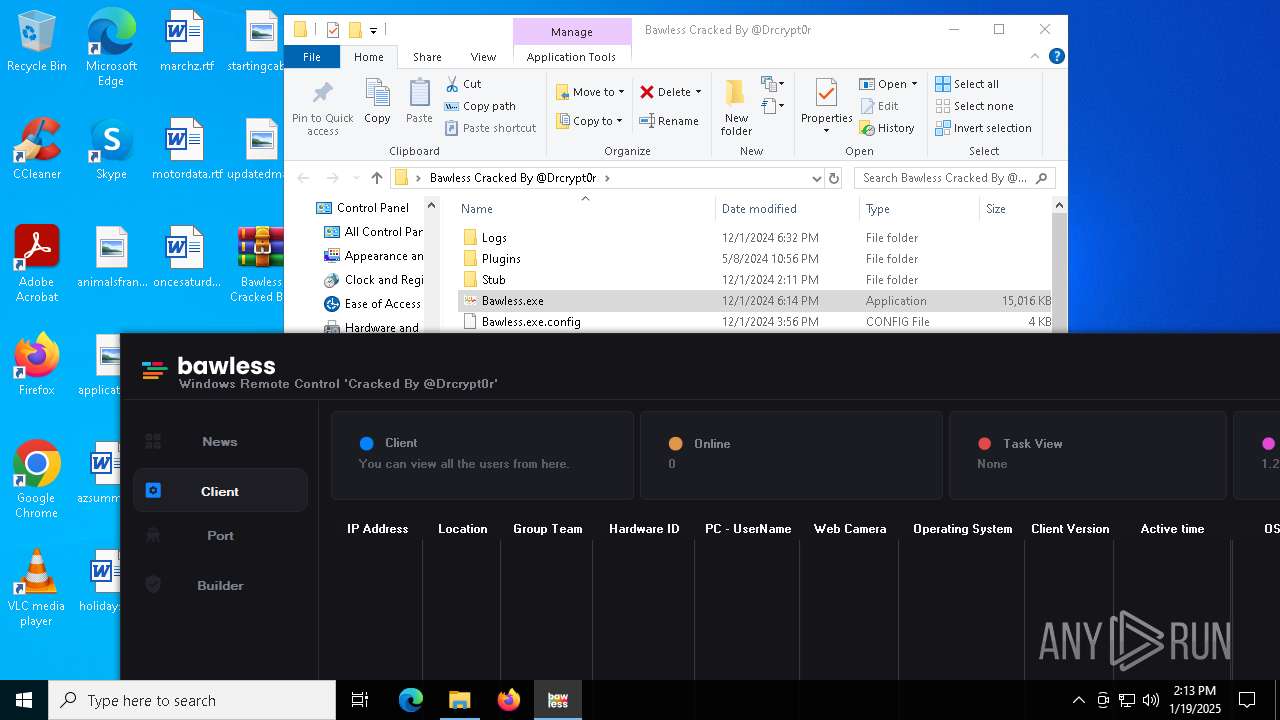
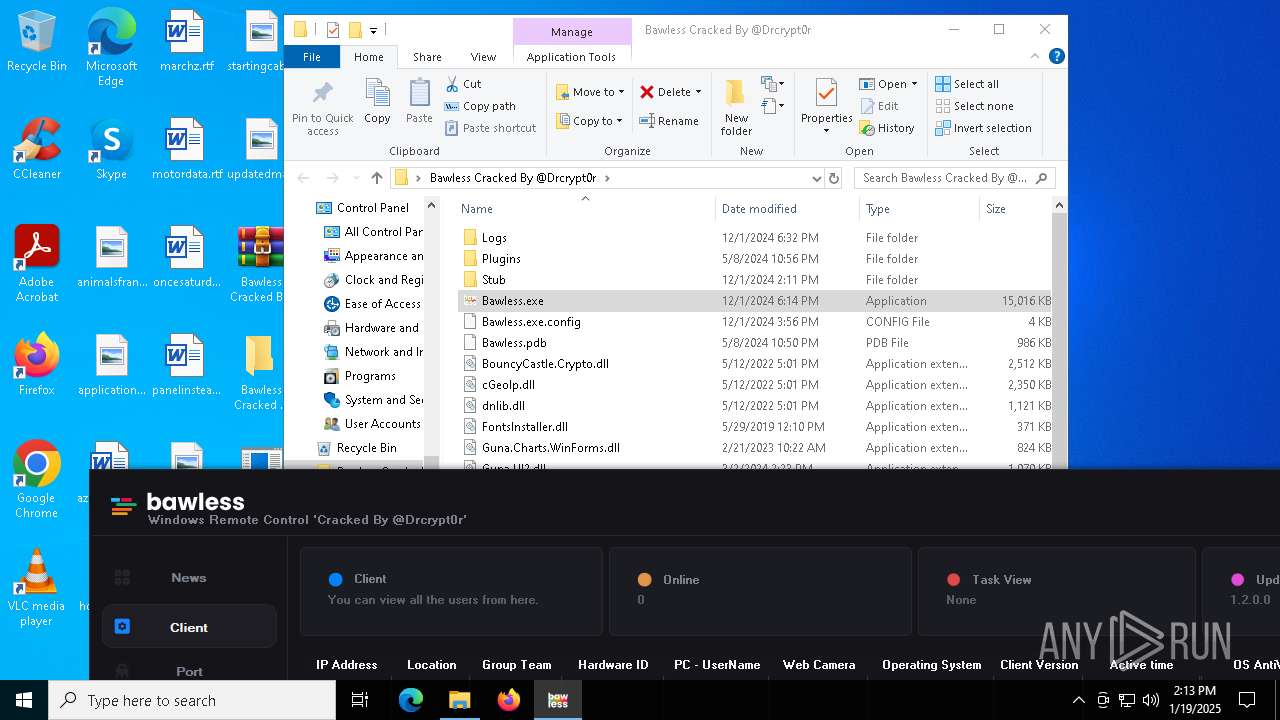
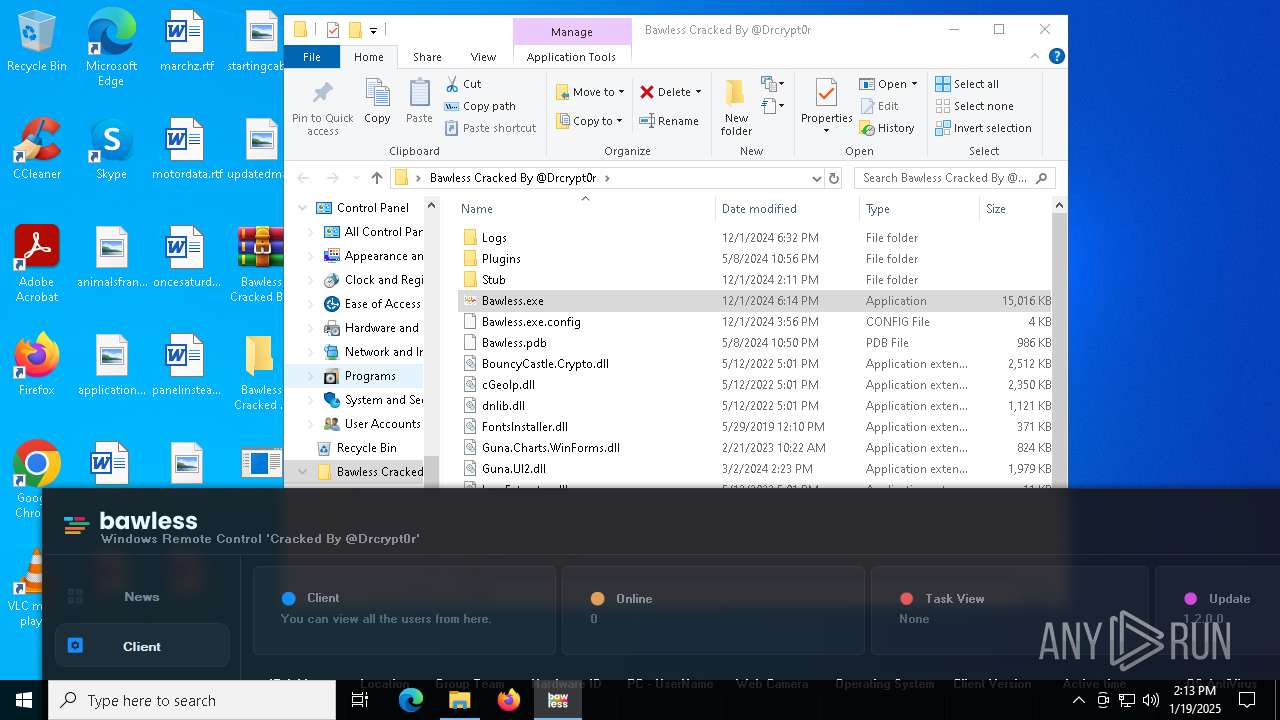
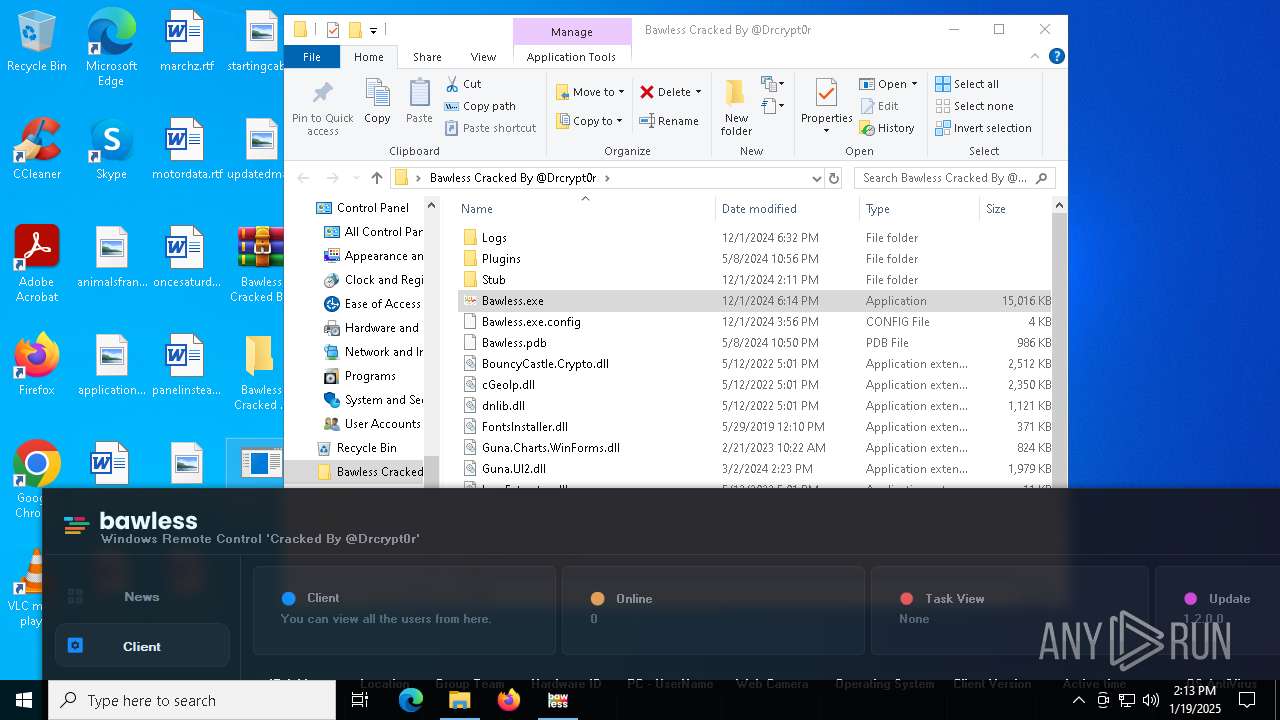
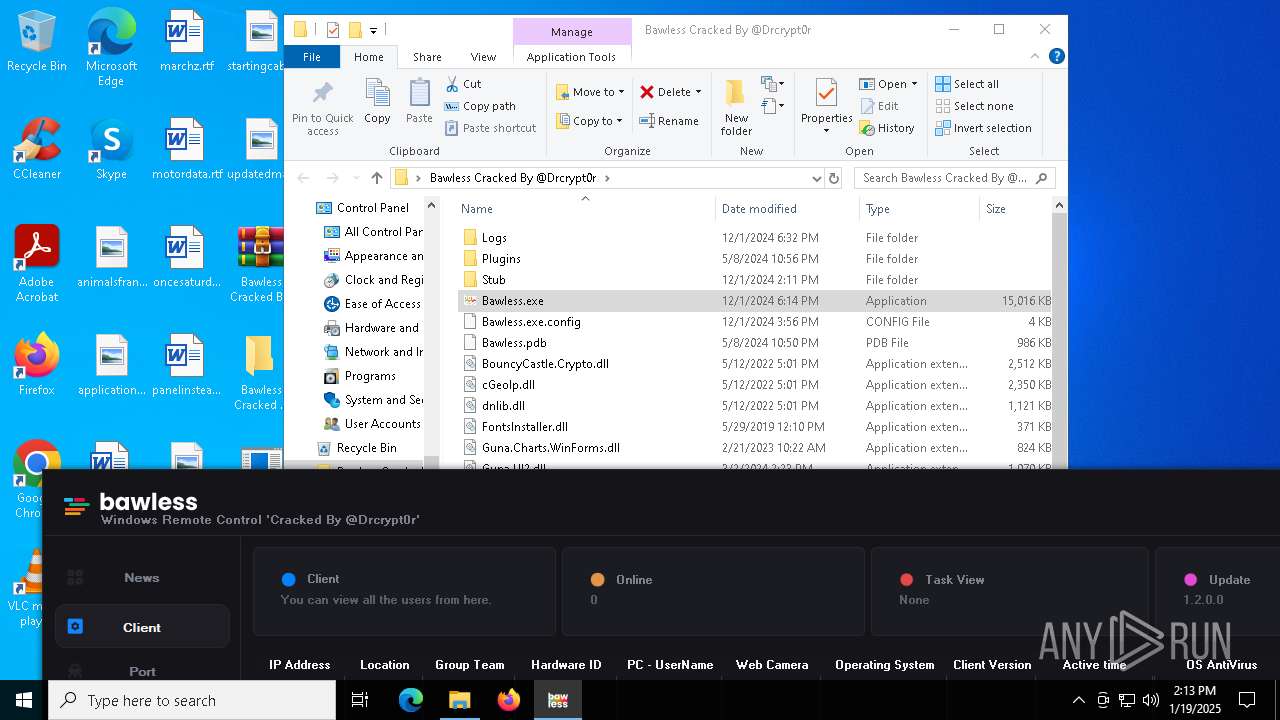
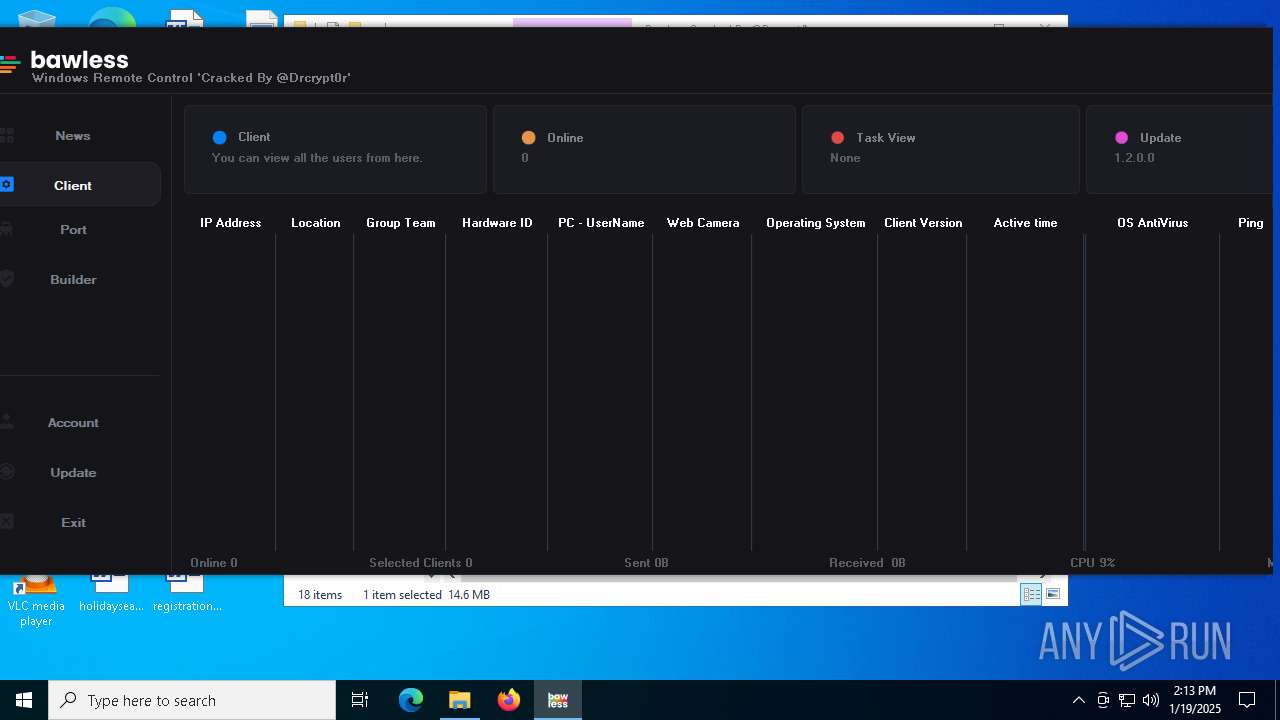
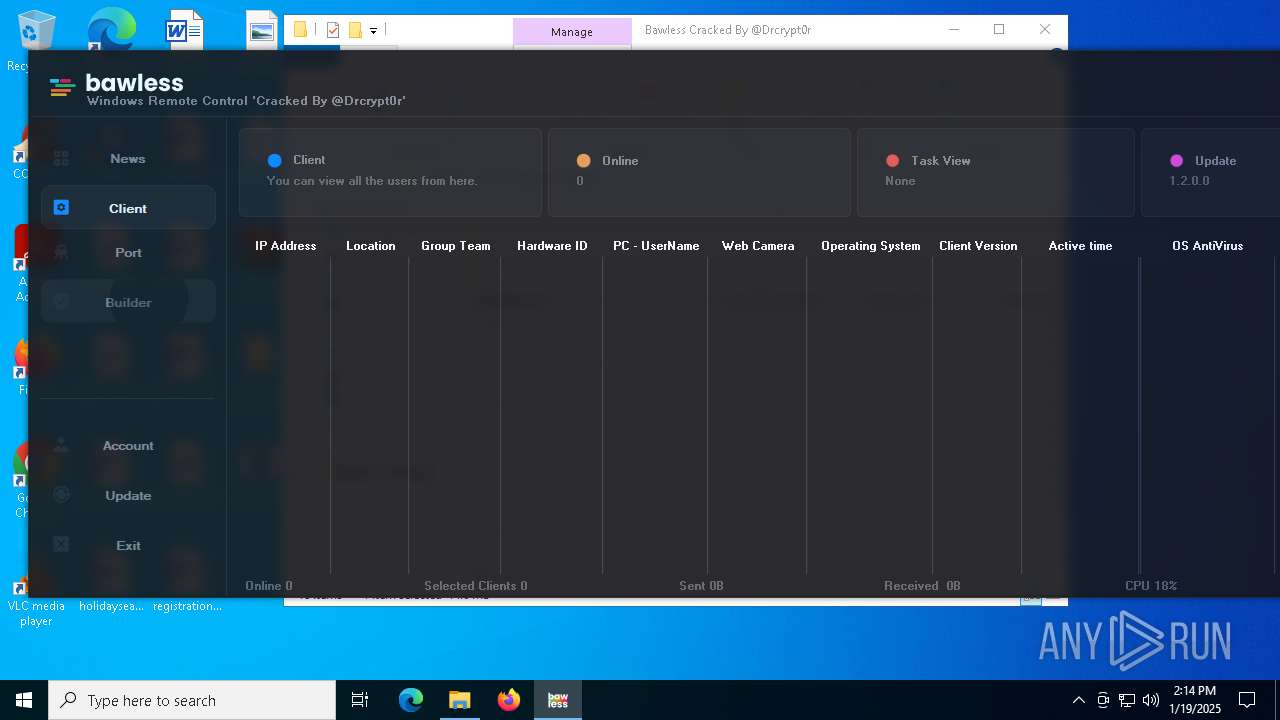
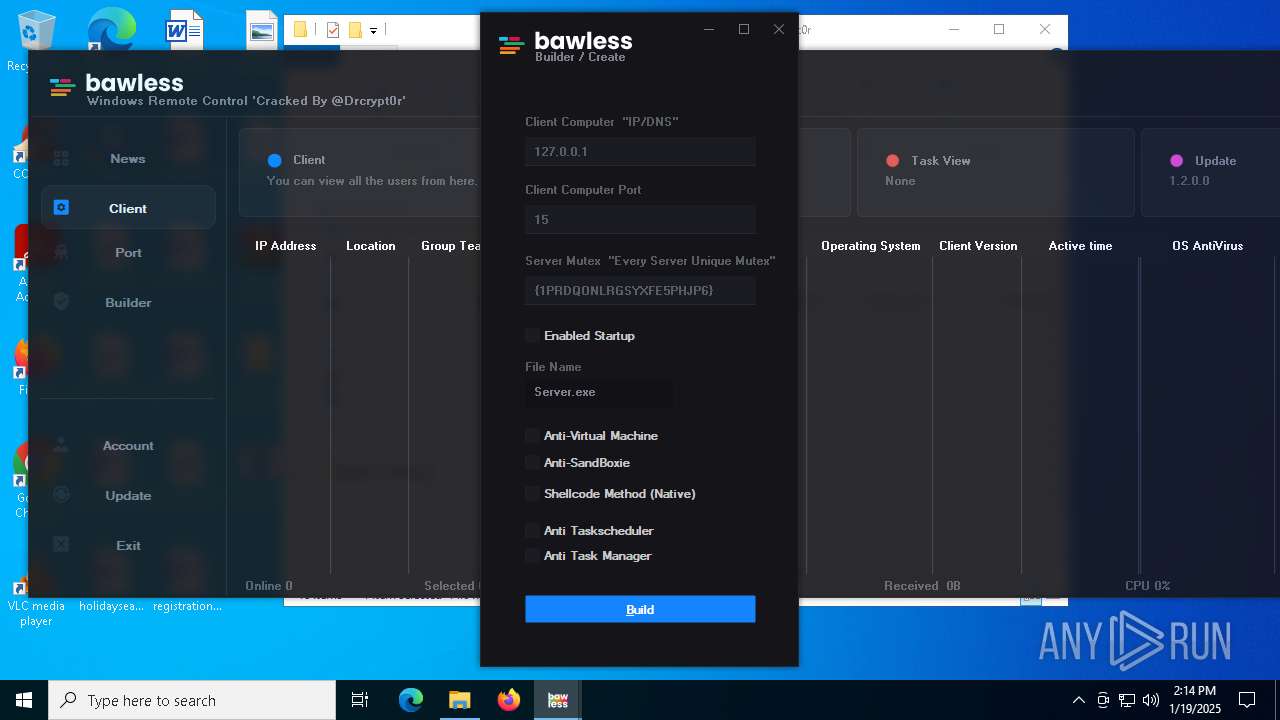
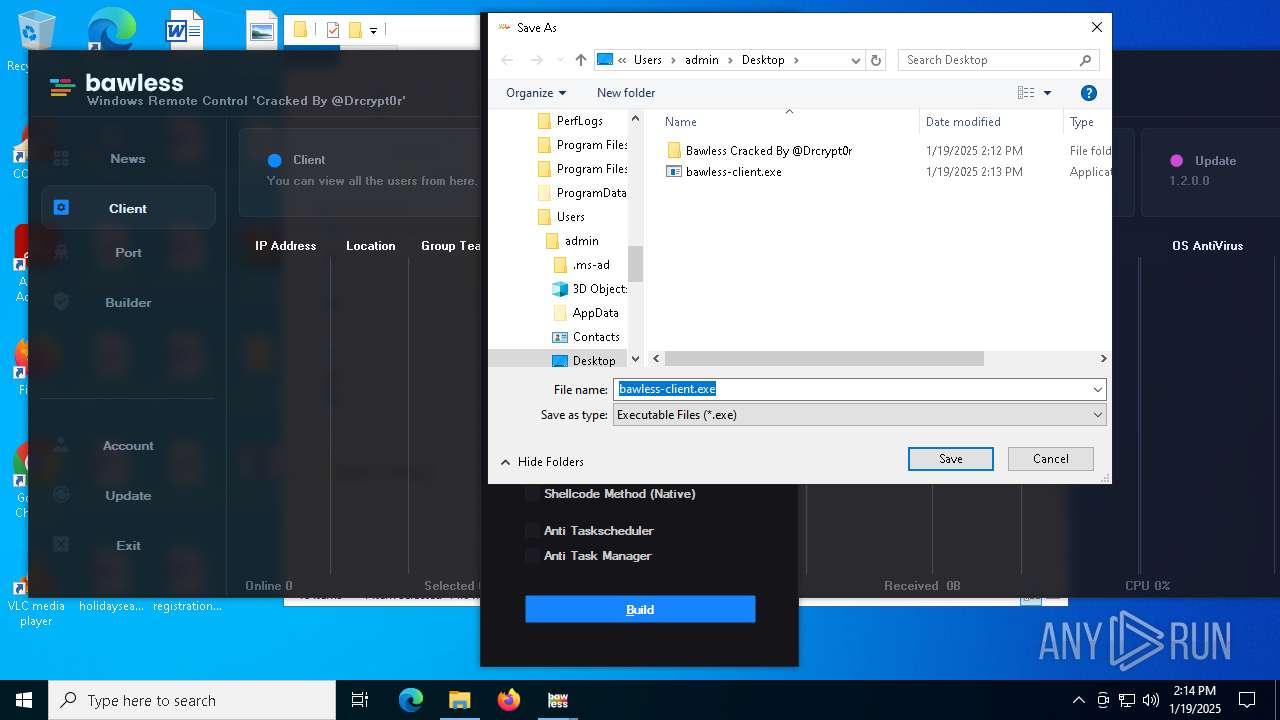
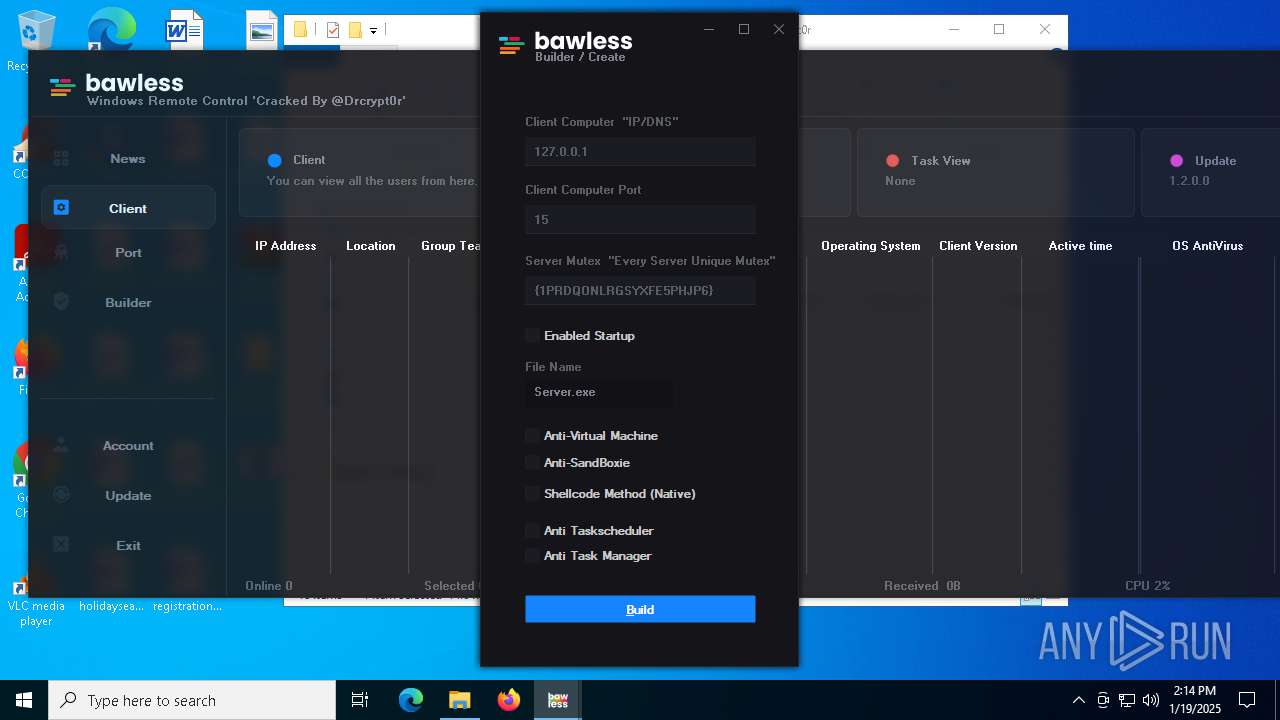
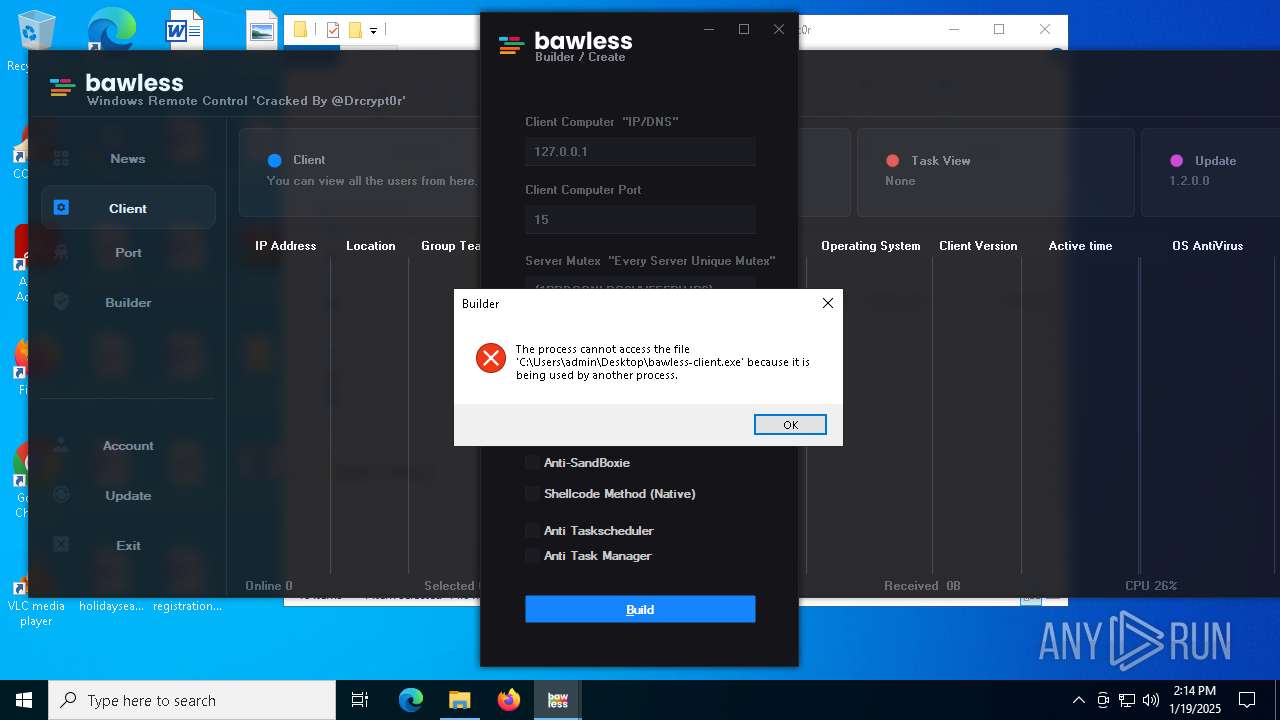
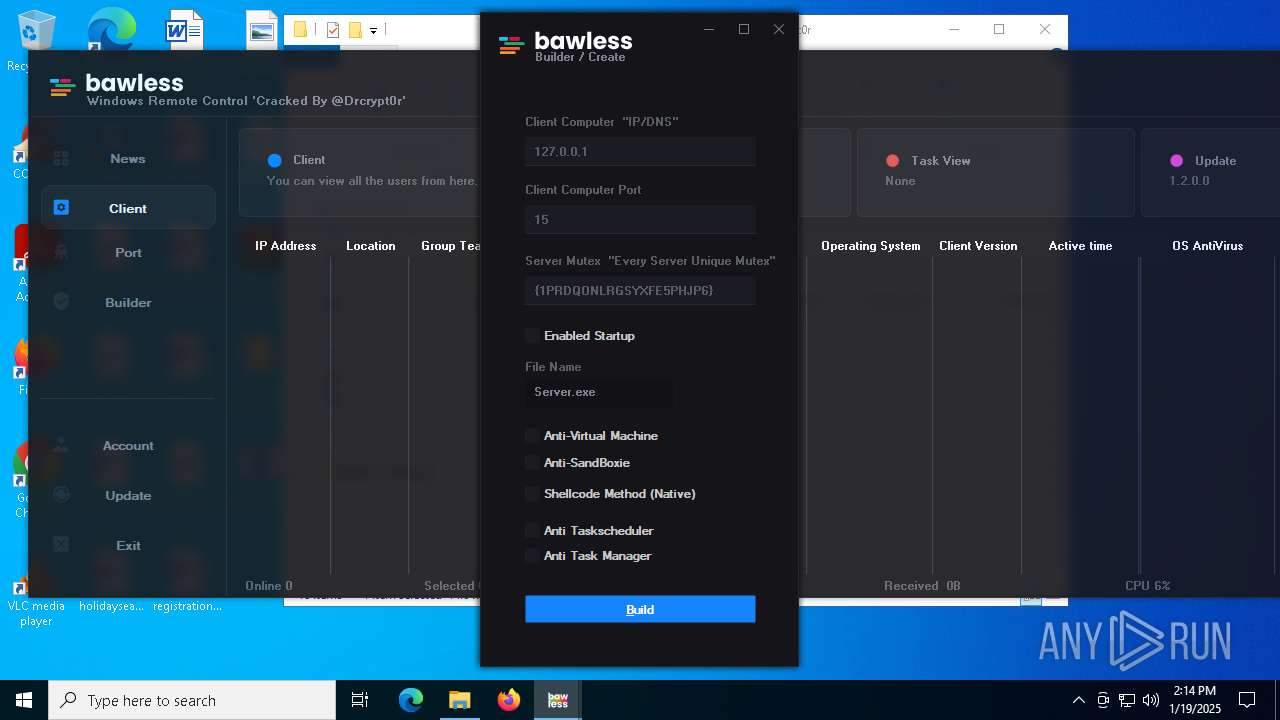
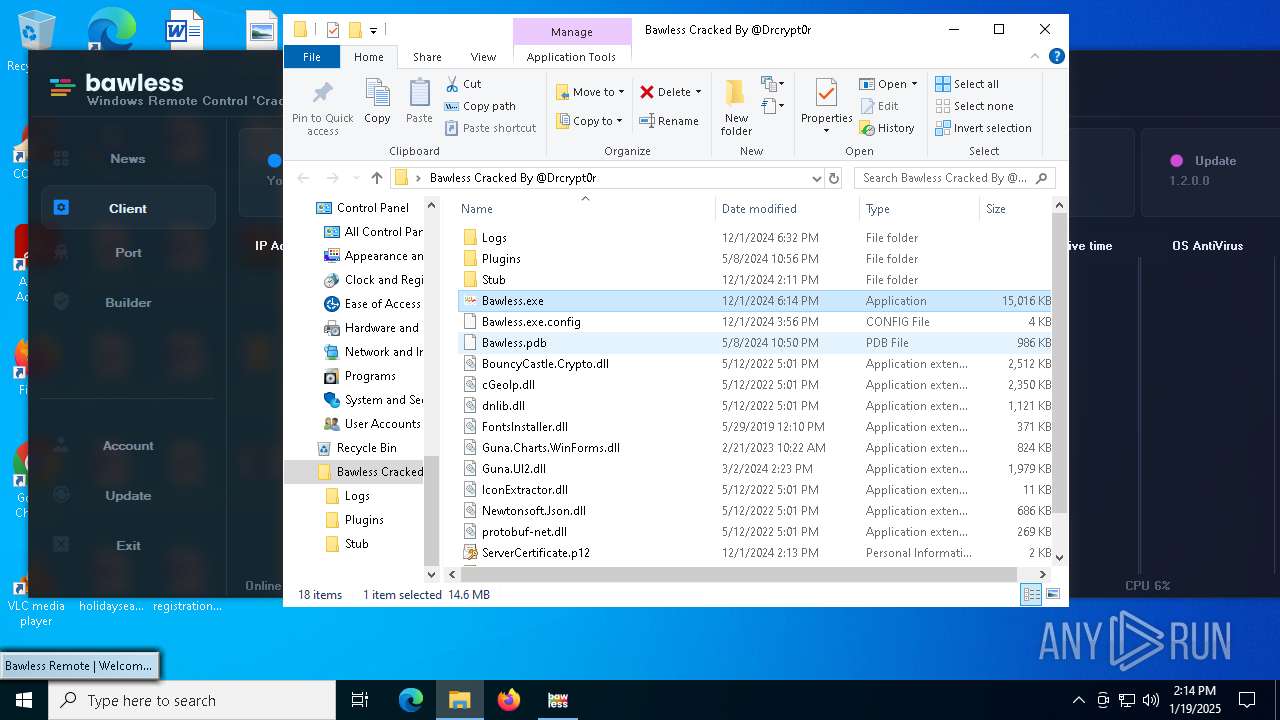
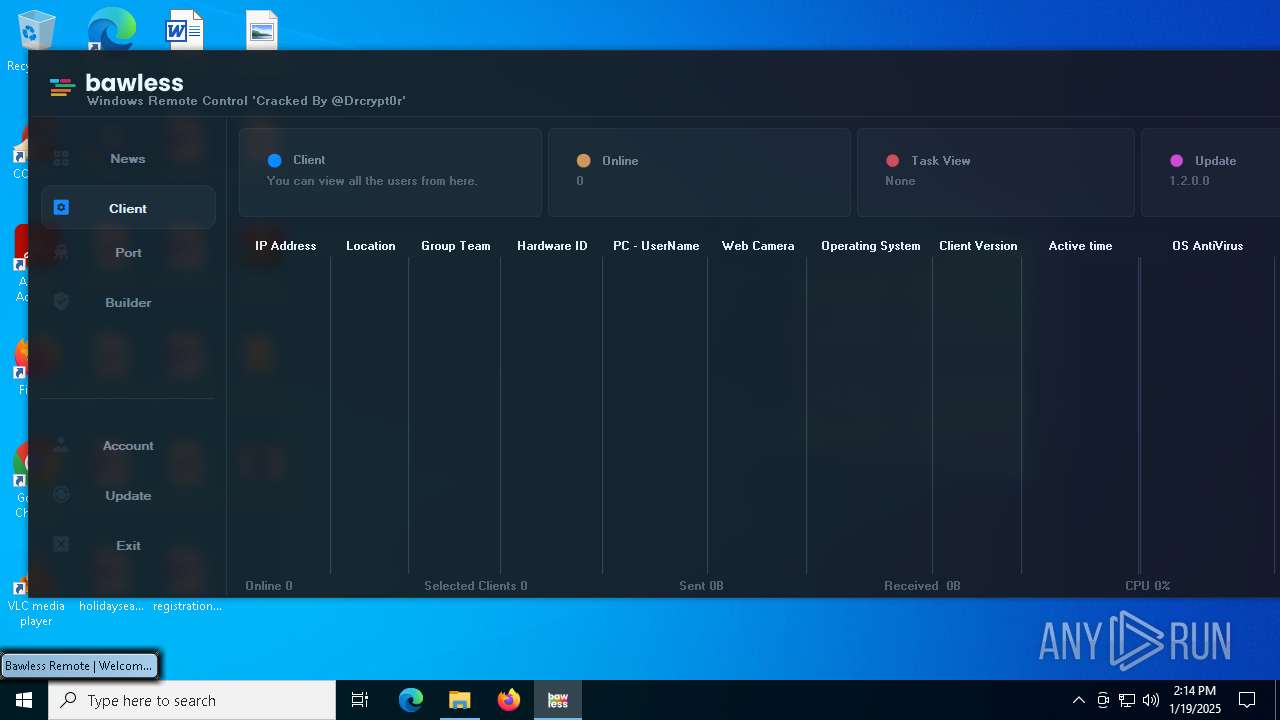
| File name: | Bawless Cracked By @Drcrypt0r.rar |
| Full analysis: | https://app.any.run/tasks/f25e8bbf-2d59-4cbd-b7fd-84f9f65cce98 |
| Verdict: | Malicious activity |
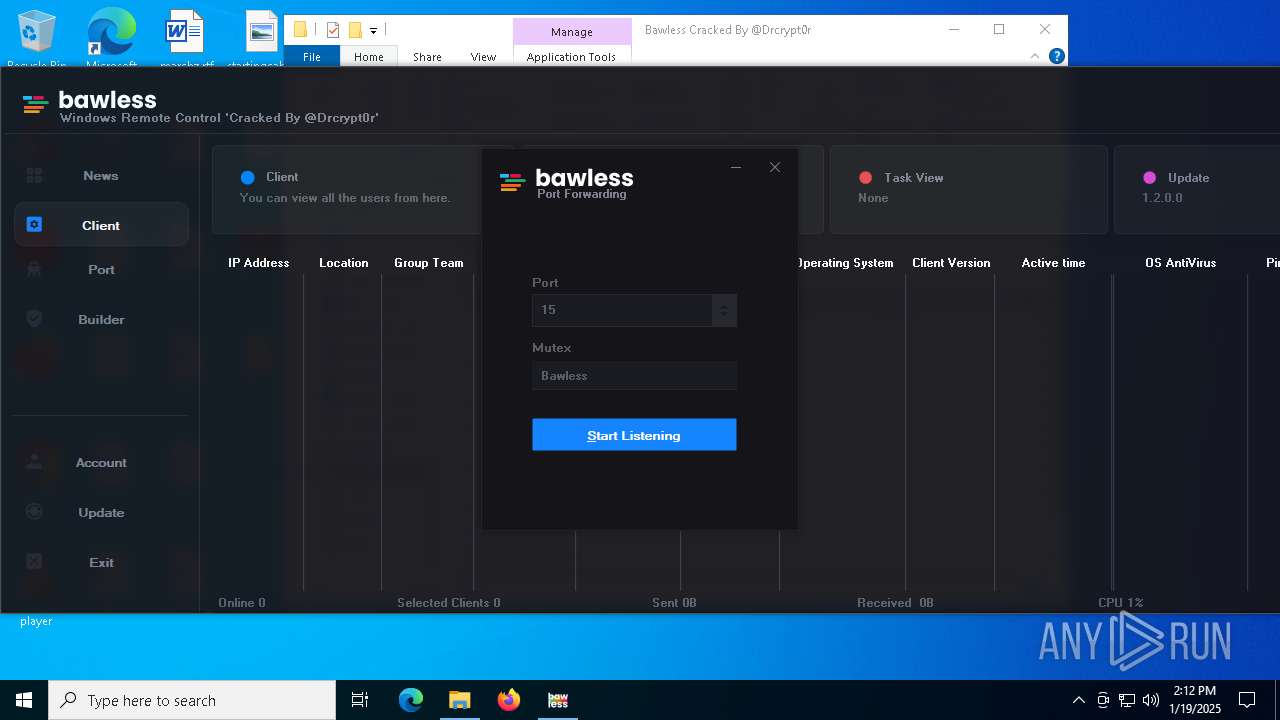
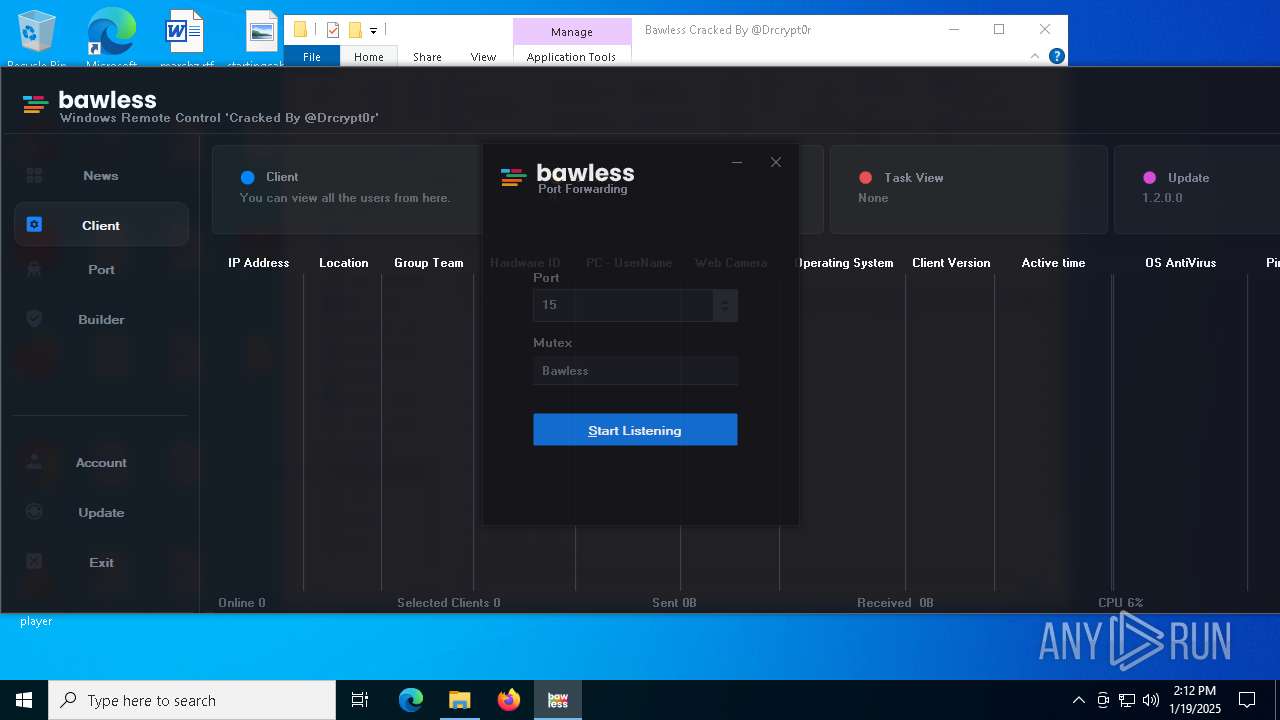
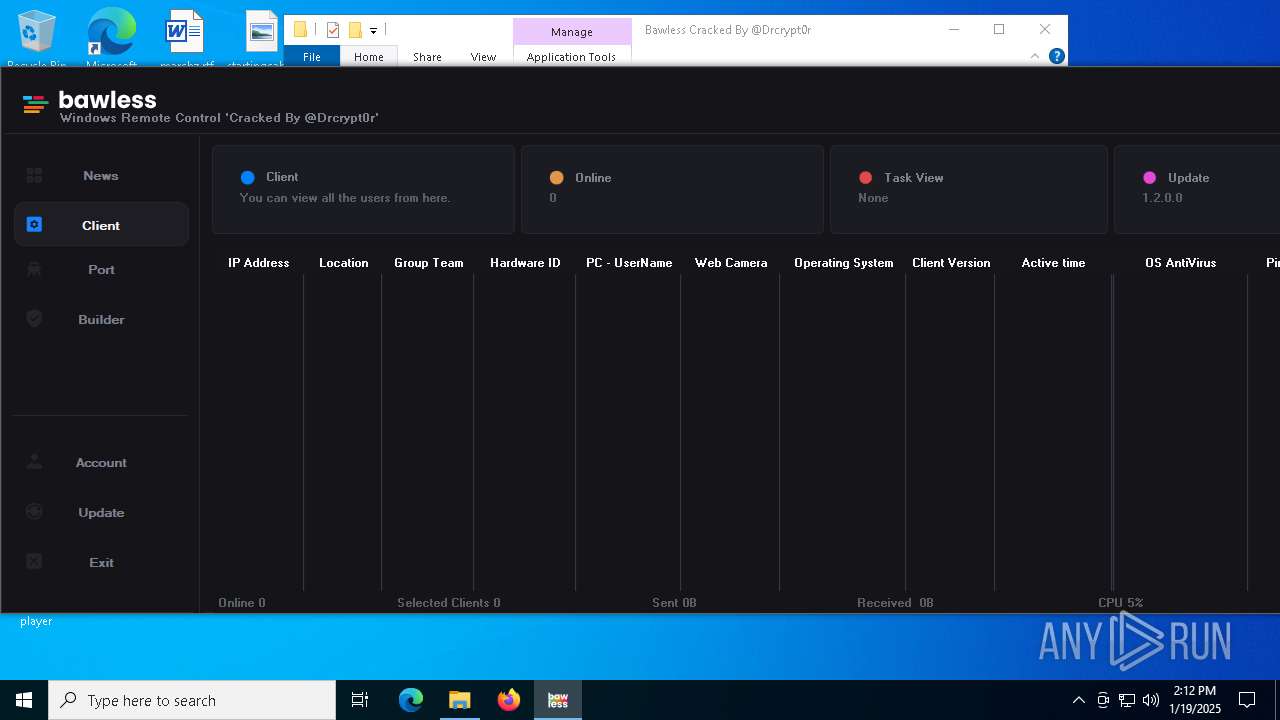
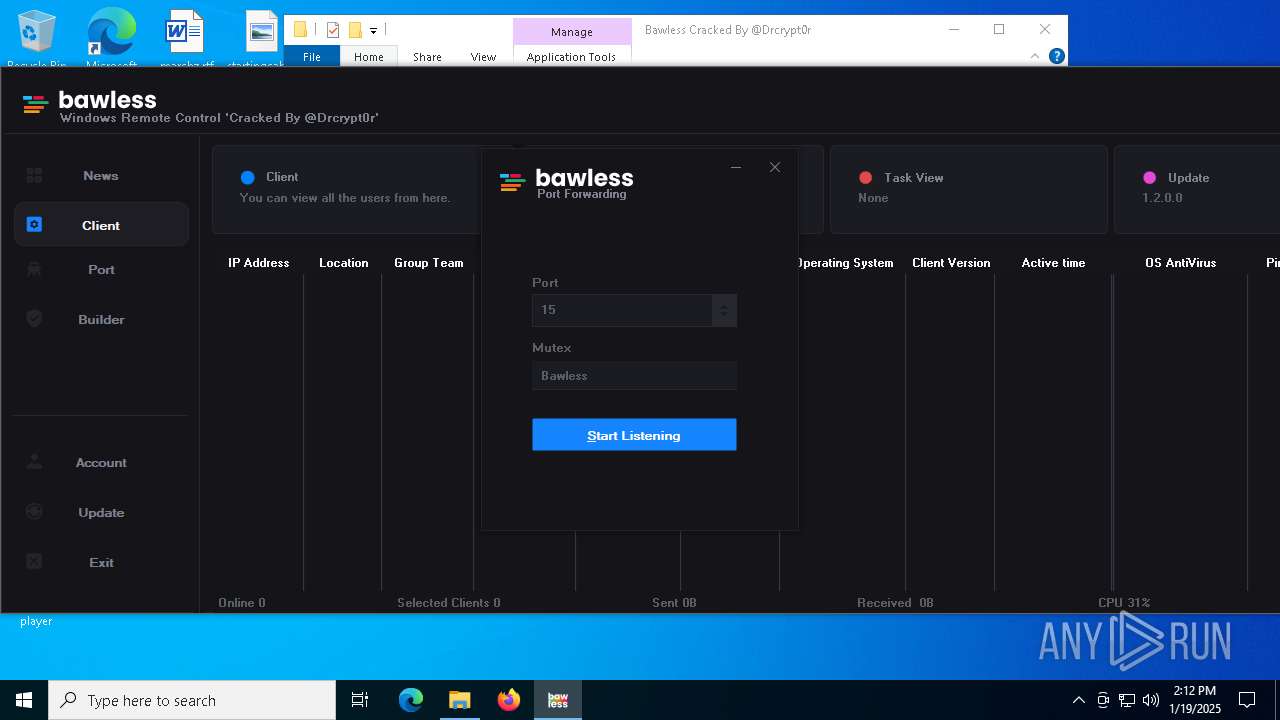
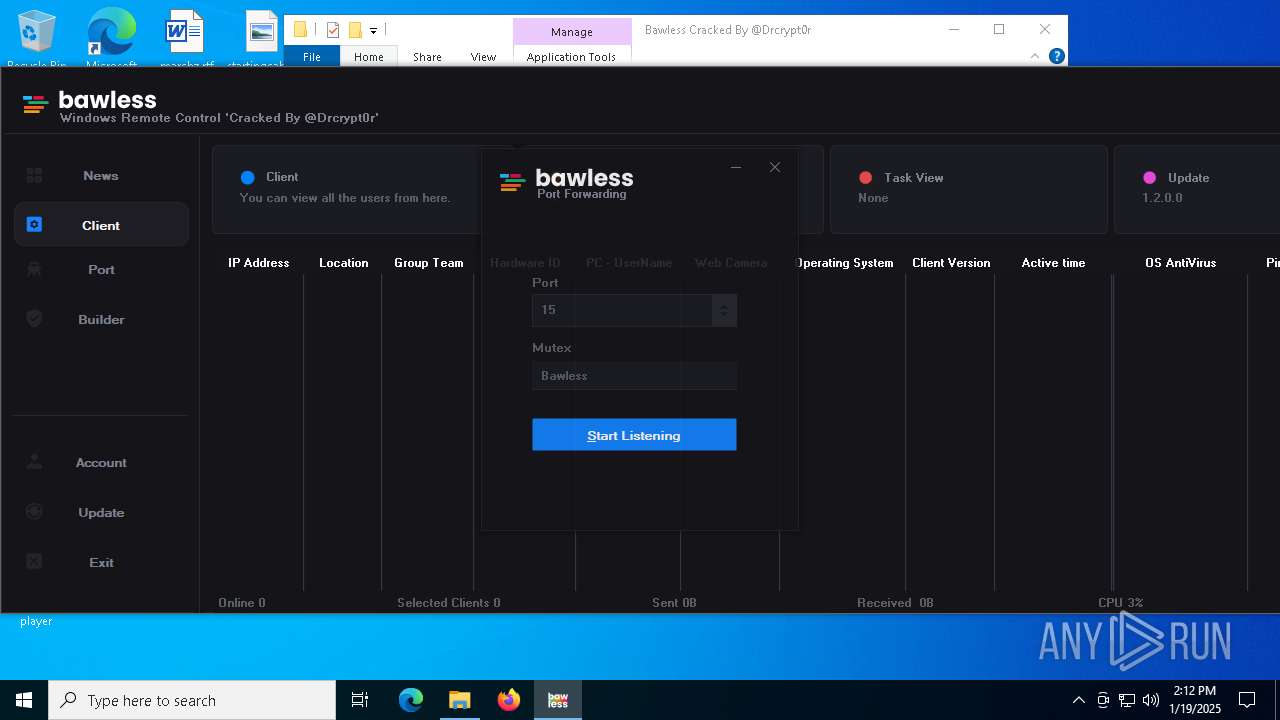
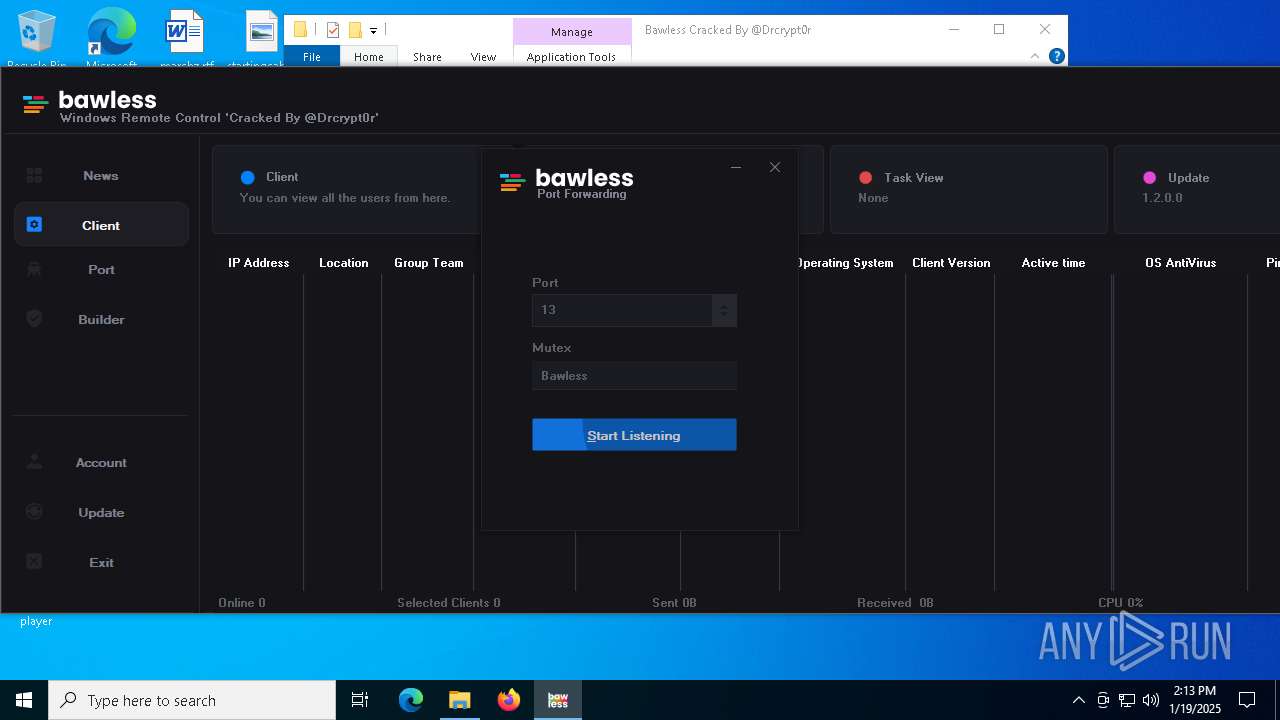
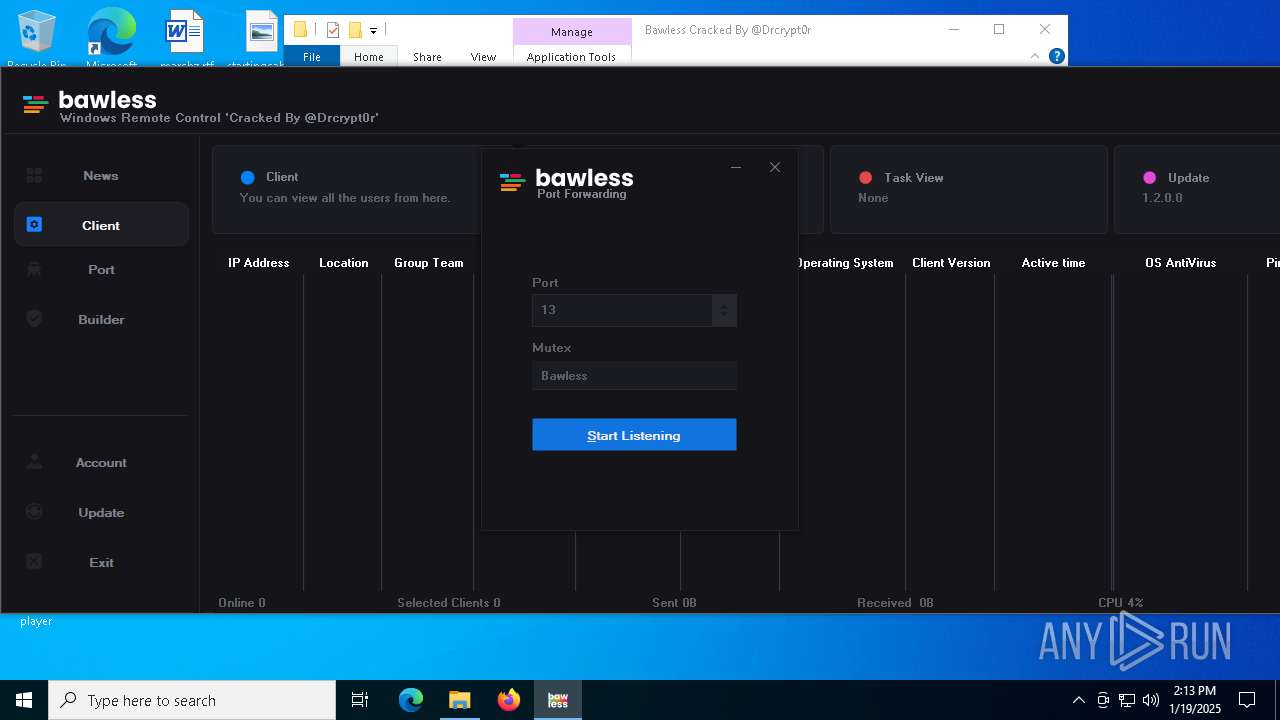
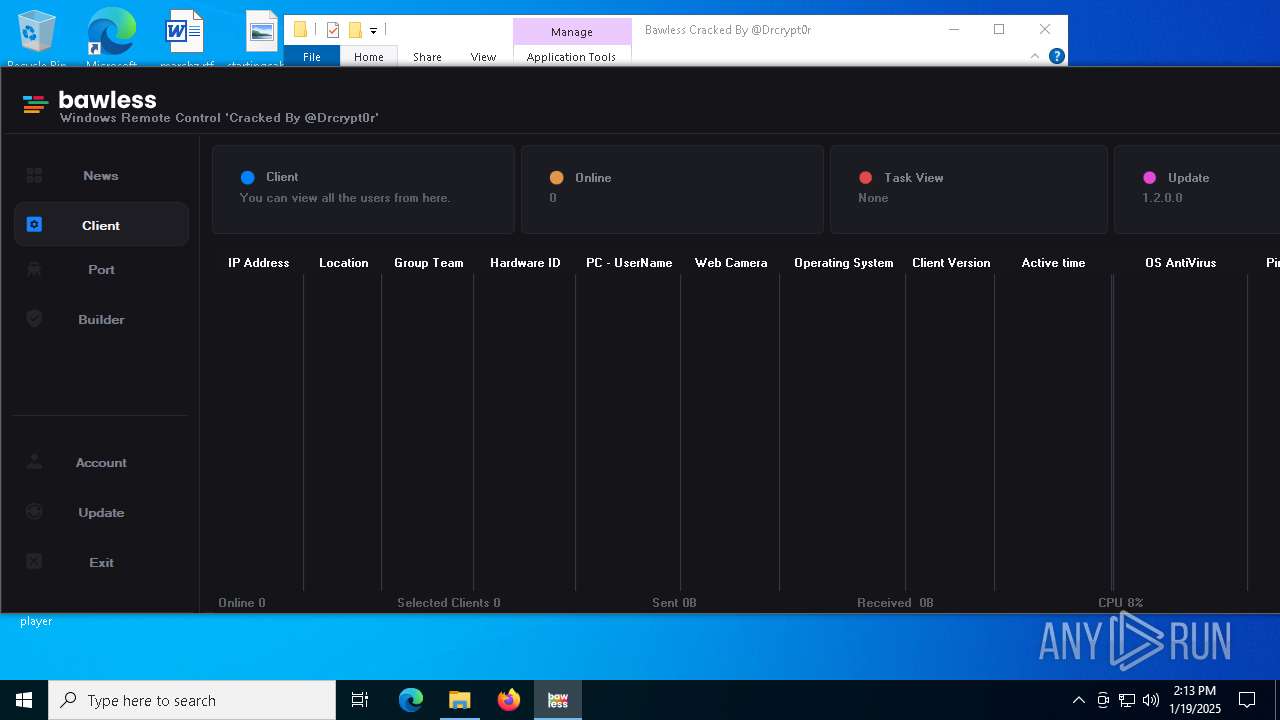
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | January 19, 2025, 14:11:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 246CC39EA43377D516318ABC5B20793B |
| SHA1: | 75B24BD1E92BC0F246A099107B6C1C10FB5E4768 |
| SHA256: | C54403022C42B42367502611961498E31867F08B4EEC3B81F2C38323A18A039F |
| SSDEEP: | 98304:kc4lVh0HSpJFQV6Owx7+I15oNA5zbZiPO1Bm7R5KUC4F7gx6TDXyb3D7cIM8IB84:A35PbspX0Wpf |
MALICIOUS
ASYNCRAT has been detected (YARA)
- Bawless.exe (PID: 4976)
- bawless-client.exe (PID: 3920)
SUSPICIOUS
Executes application which crashes
- Bawless.exe (PID: 732)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 5268)
Reads security settings of Internet Explorer
- Bawless.exe (PID: 4976)
The process checks if it is being run in the virtual environment
- Bawless.exe (PID: 4976)
Creates file in the systems drive root
- Bawless.exe (PID: 4976)
There is functionality for taking screenshot (YARA)
- Bawless.exe (PID: 4976)
INFO
Checks supported languages
- Bawless.exe (PID: 732)
- Bawless.exe (PID: 4976)
- bawless-client.exe (PID: 3920)
Manual execution by a user
- Bawless.exe (PID: 732)
- WinRAR.exe (PID: 5268)
- Bawless.exe (PID: 4976)
- bawless-client.exe (PID: 3920)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2672)
- WinRAR.exe (PID: 5268)
The process uses the downloaded file
- WinRAR.exe (PID: 2672)
- Bawless.exe (PID: 4976)
- WinRAR.exe (PID: 5268)
Reads the computer name
- Bawless.exe (PID: 4976)
- Bawless.exe (PID: 732)
- bawless-client.exe (PID: 3920)
Creates files or folders in the user directory
- WerFault.exe (PID: 3836)
- Bawless.exe (PID: 4976)
Checks proxy server information
- WerFault.exe (PID: 3836)
Reads the software policy settings
- WerFault.exe (PID: 3836)
Reads the machine GUID from the registry
- Bawless.exe (PID: 732)
- Bawless.exe (PID: 4976)
- bawless-client.exe (PID: 3920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 2432844 |
| UncompressedSize: | 15375872 |
| OperatingSystem: | Win32 |
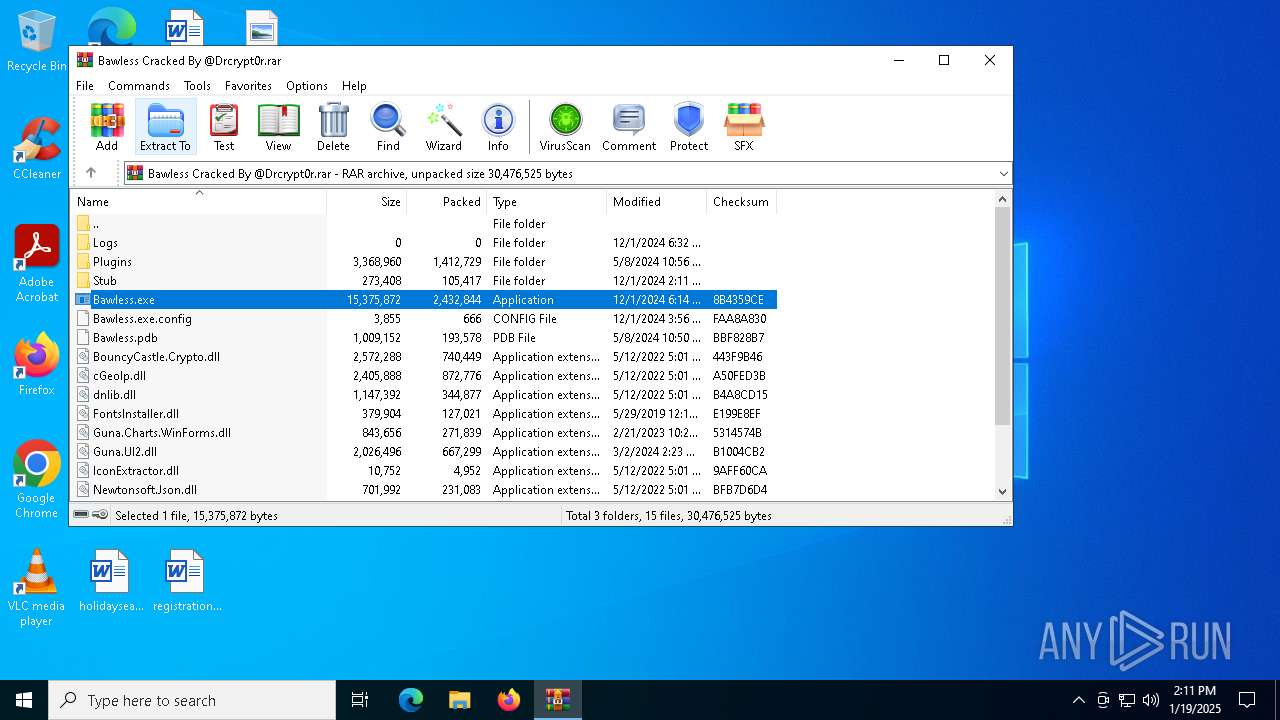
| ArchivedFileName: | Bawless.exe |
Total processes
137
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 732 | "C:\Users\admin\Desktop\Bawless Cracked By @Drcrypt0r\Bawless.exe" | C:\Users\admin\Desktop\Bawless Cracked By @Drcrypt0r\Bawless.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Bawless Exit code: 3762504530 Version: 1.0.0 Modules
| |||||||||||||||
| 2672 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Bawless Cracked By @Drcrypt0r.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3836 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 732 -s 1140 | C:\Windows\SysWOW64\WerFault.exe | Bawless.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3920 | "C:\Users\admin\Desktop\bawless-client.exe" | C:\Users\admin\Desktop\bawless-client.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 5.0.0.3 Modules
| |||||||||||||||
| 4628 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4976 | "C:\Users\admin\Desktop\Bawless Cracked By @Drcrypt0r\Bawless.exe" | C:\Users\admin\Desktop\Bawless Cracked By @Drcrypt0r\Bawless.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Bawless Version: 1.0.0 Modules
| |||||||||||||||
| 5268 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Bawless Cracked By @Drcrypt0r.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
14 129
Read events
14 006
Write events
107
Delete events
16
Modification events
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Bawless Cracked By @Drcrypt0r.rar | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
35
Suspicious files
12
Text files
34
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3836 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_Bawless.exe_f3ed497eb31eae66681c12c94d78b3fd0bc22dc_51272107_245f8b2f-9ab4-4119-b62f-b51d62be23b6\Report.wer | — | |
MD5:— | SHA256:— | |||
| 3836 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Bawless.exe.732.dmp | — | |
MD5:— | SHA256:— | |||
| 3836 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FA84E4BCC92AA5DB735AB50711040CDE | SHA256:6D7205E794FDE4219A62D9692ECDDF612663A5CF20399E79BE87B851FCA4CA33 | |||
| 3836 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERE2A3.tmp.dmp | binary | |
MD5:F2464F330D2FD9D63534DCF73A14FF50 | SHA256:648638A4C57F32A6884DB0FEB60BF592457F0D098D4EB843B5554FAFA29930D4 | |||
| 3836 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:B40DF53F877D71FC900A4CAC8A7D30D6 | SHA256:20F626A2E3DFBE3B6264A2CAEABDAEED438988F67AA2CF60873F273162D0BB07 | |||
| 2672 | WinRAR.exe | C:\Users\admin\Desktop\Bawless Cracked By @Drcrypt0r\Bawless.exe | executable | |
MD5:2FD36877F3C0F74CB98FDD041C06C5E2 | SHA256:C39C732ACCFAFC55F30D9E6CD8352731D66752886C054D75811B1581739B22CD | |||
| 3836 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:F6F53CD09A41E968C363419B279D3112 | SHA256:6D2BB01CC7A9BADE2113B219CAC1BDA86B2733196B7E1BD0C807CE1E396B1892 | |||
| 5268 | WinRAR.exe | C:\Users\admin\Desktop\Bawless Cracked By @Drcrypt0r\cGeoIp.dll | executable | |
MD5:6D6E172E7965D1250A4A6F8A0513AA9F | SHA256:D1DDD15E9C727A5ECF78D3918C17AEE0512F5B181AD44952686BEB89146E6BD0 | |||
| 5268 | WinRAR.exe | C:\Users\admin\Desktop\Bawless Cracked By @Drcrypt0r\Bawless.pdb | binary | |
MD5:84B95AD0748456F4015E55EEEA5661CB | SHA256:94618C5EB581E7DF0B9552D35B6031BC475617BCCD1B388C35505DECE28483C6 | |||
| 5268 | WinRAR.exe | C:\Users\admin\Desktop\Bawless Cracked By @Drcrypt0r\BouncyCastle.Crypto.dll | executable | |
MD5:3551343FAB213740BBB022E3A6DCF27B | SHA256:5530DFF976BC0C889076B97CA695BDB97EF07F63449D32F893ED32398ED8BFE6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
38
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2940 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3836 | WerFault.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3836 | WerFault.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2940 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3732 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.16.204.138:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
3220 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
736 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |