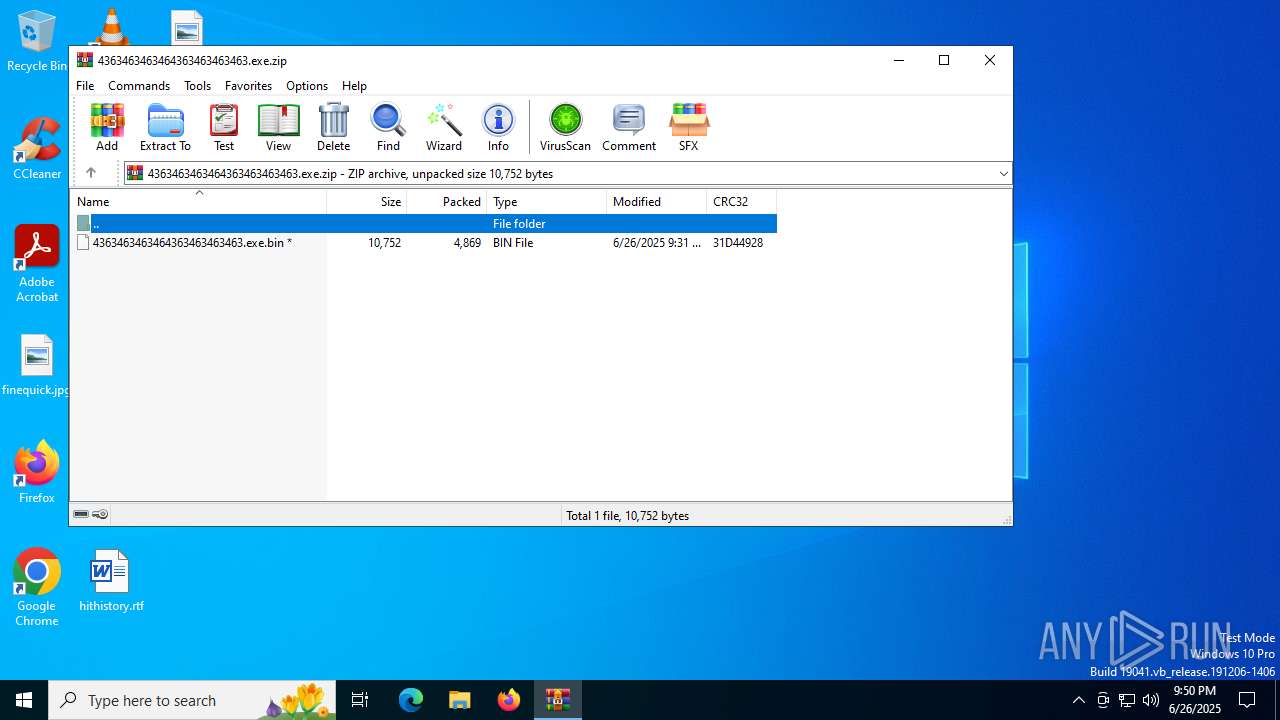
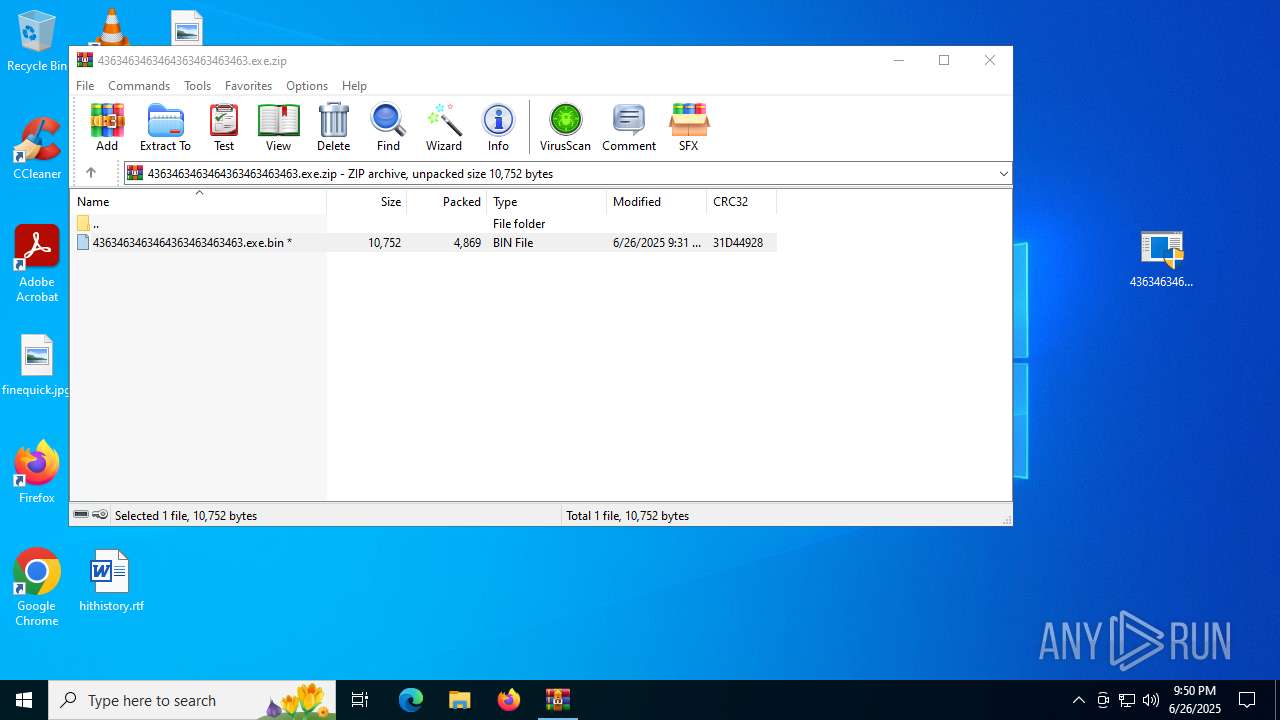
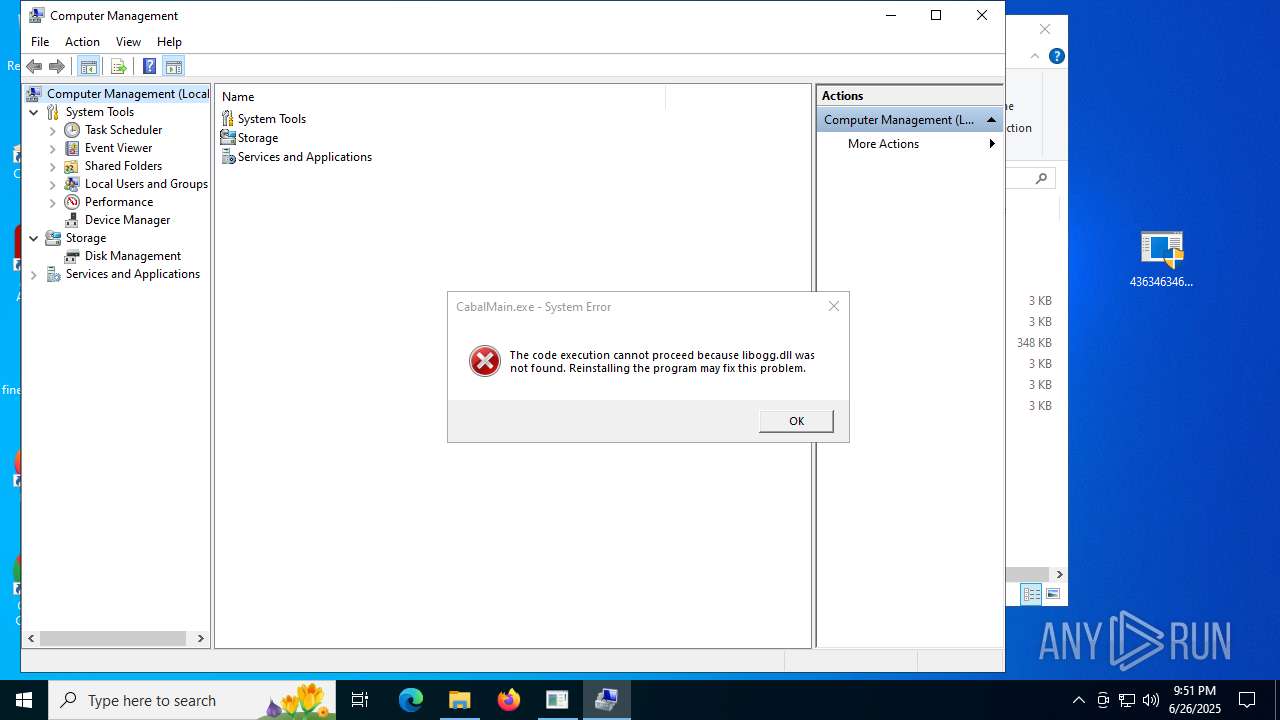
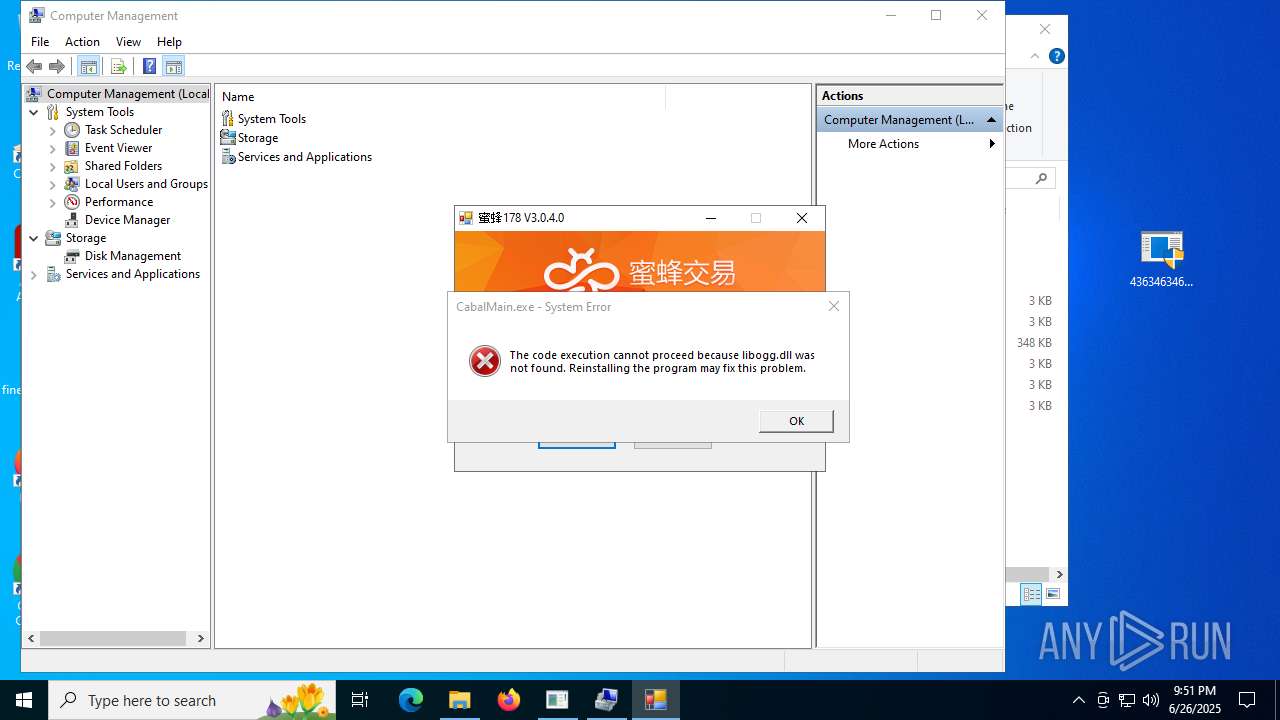
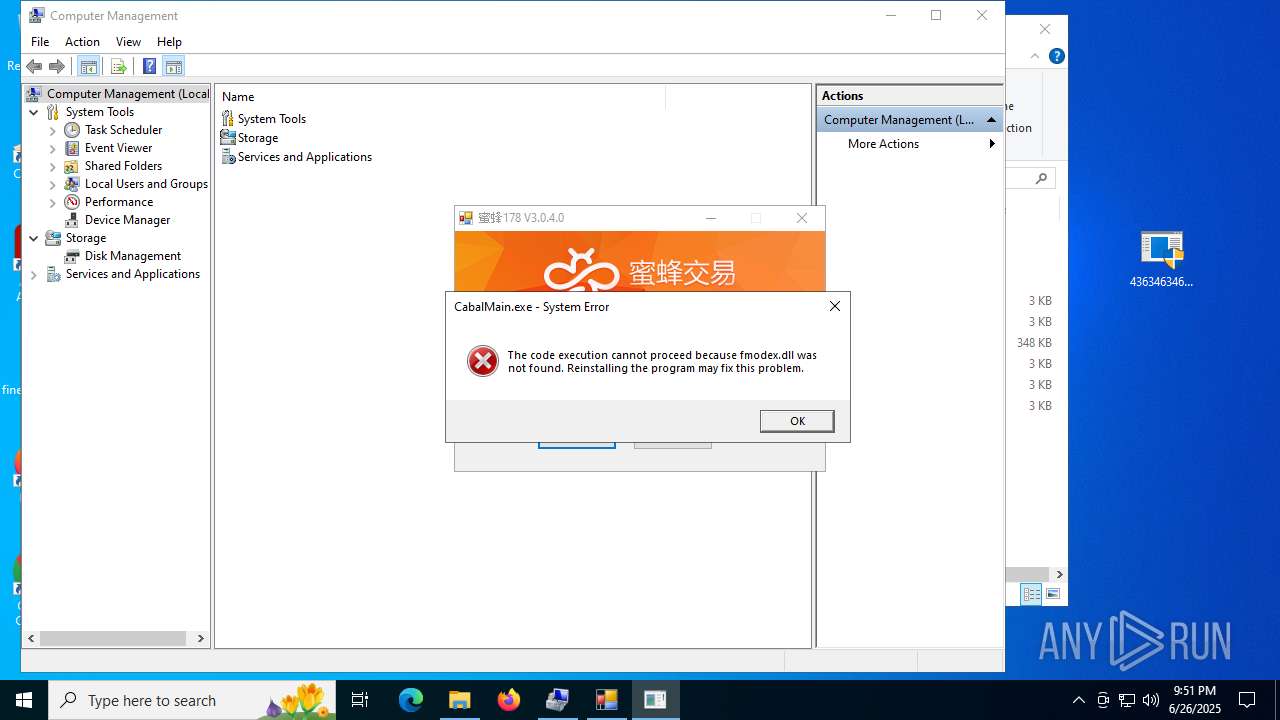
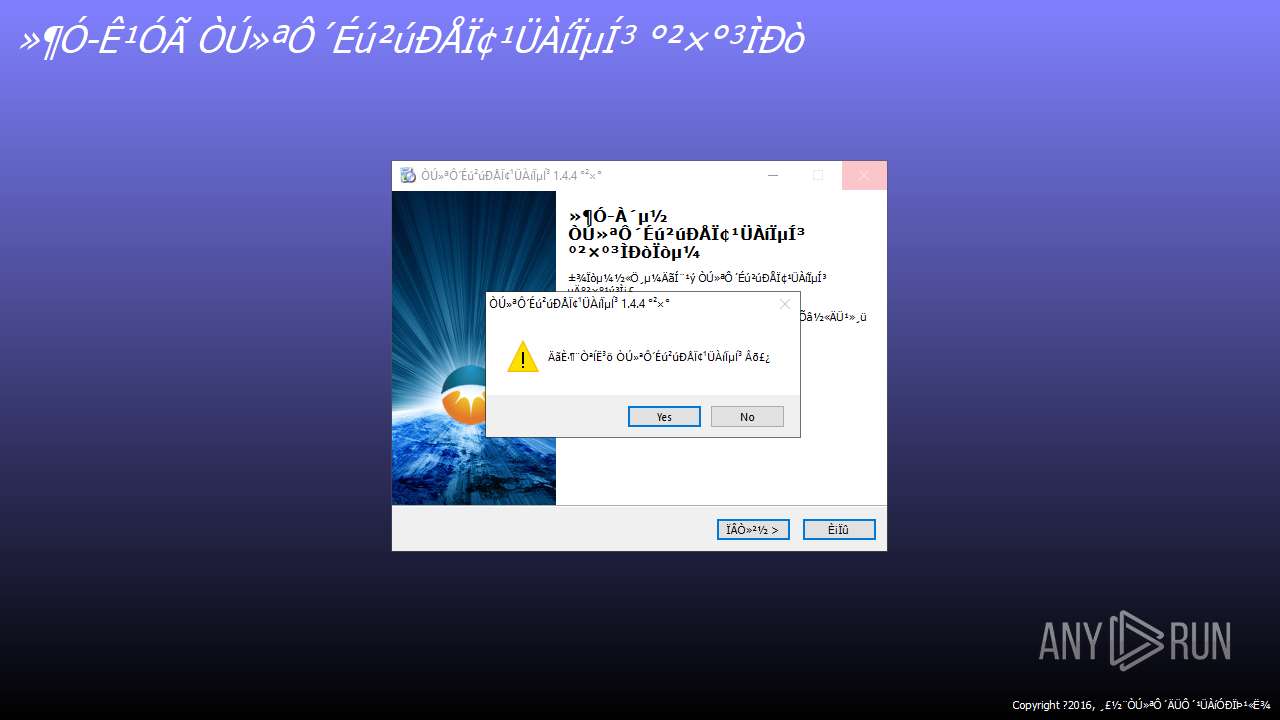
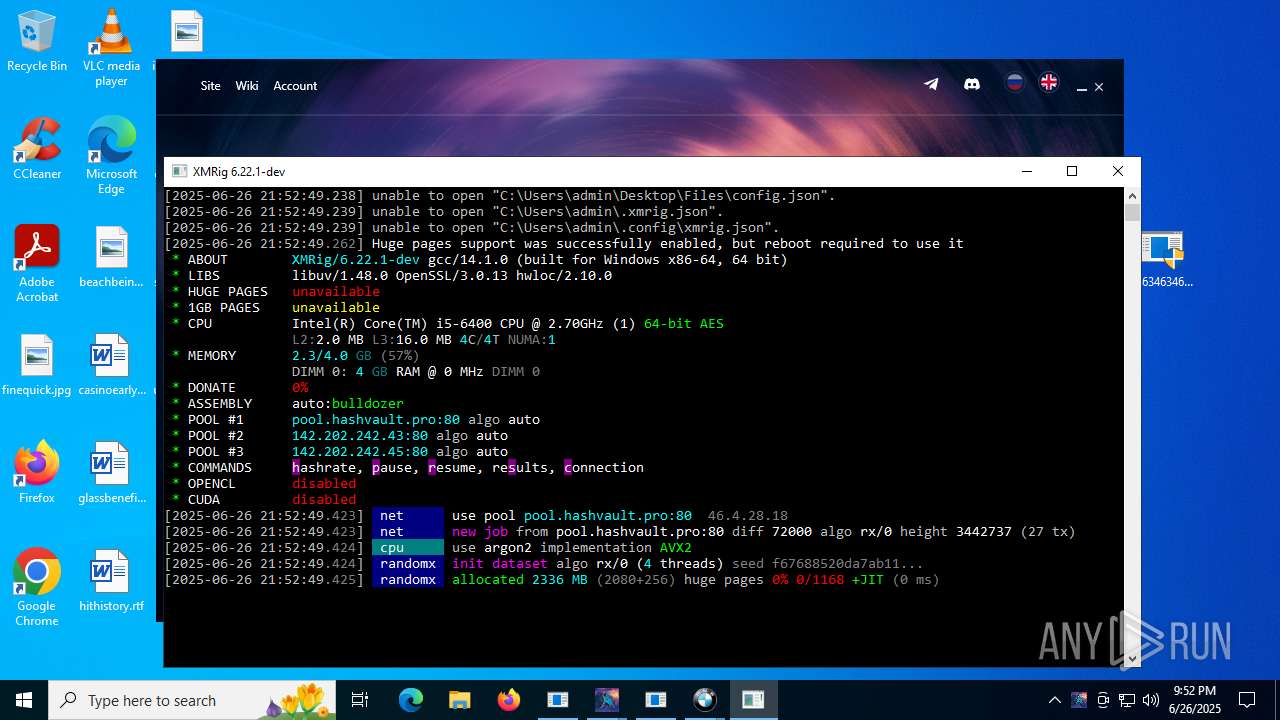
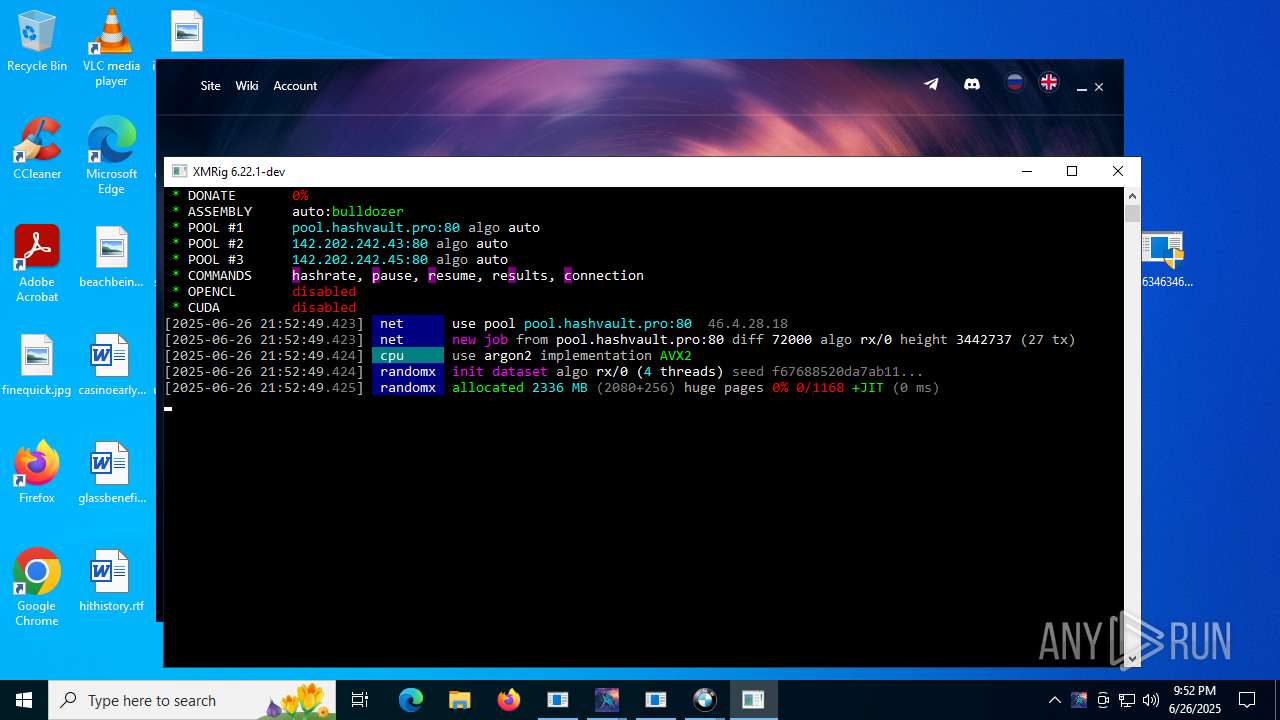
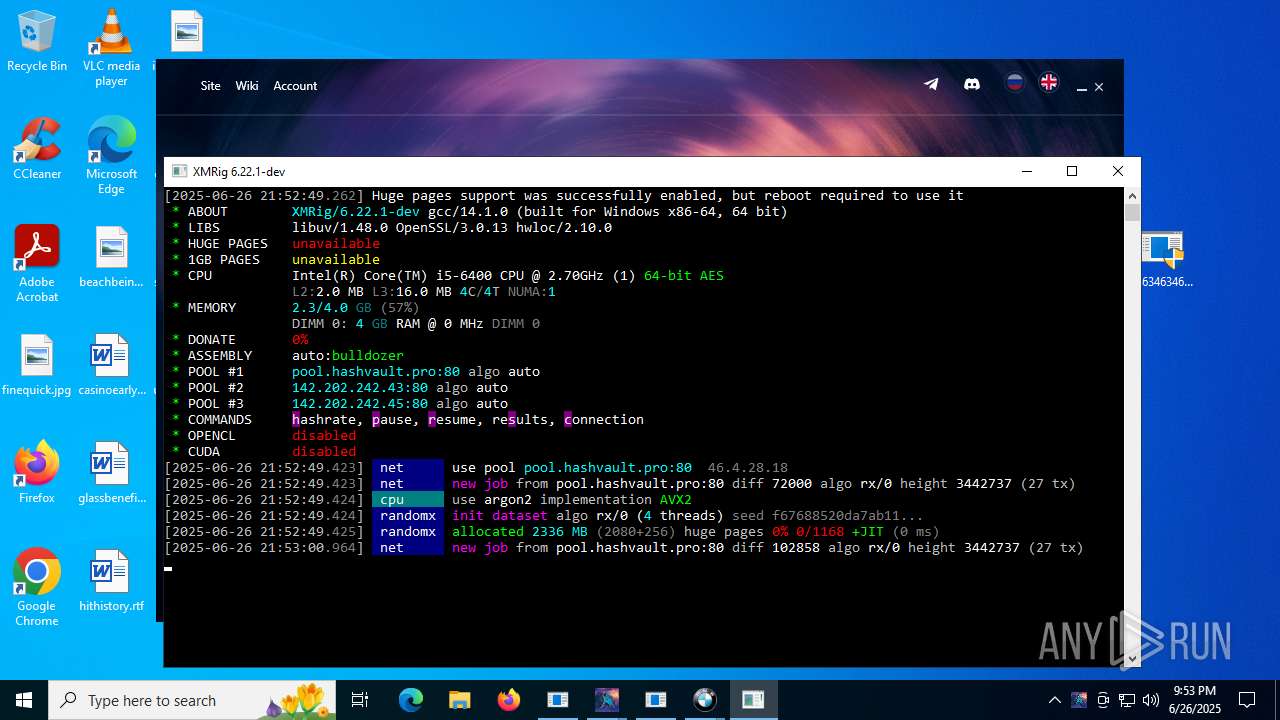
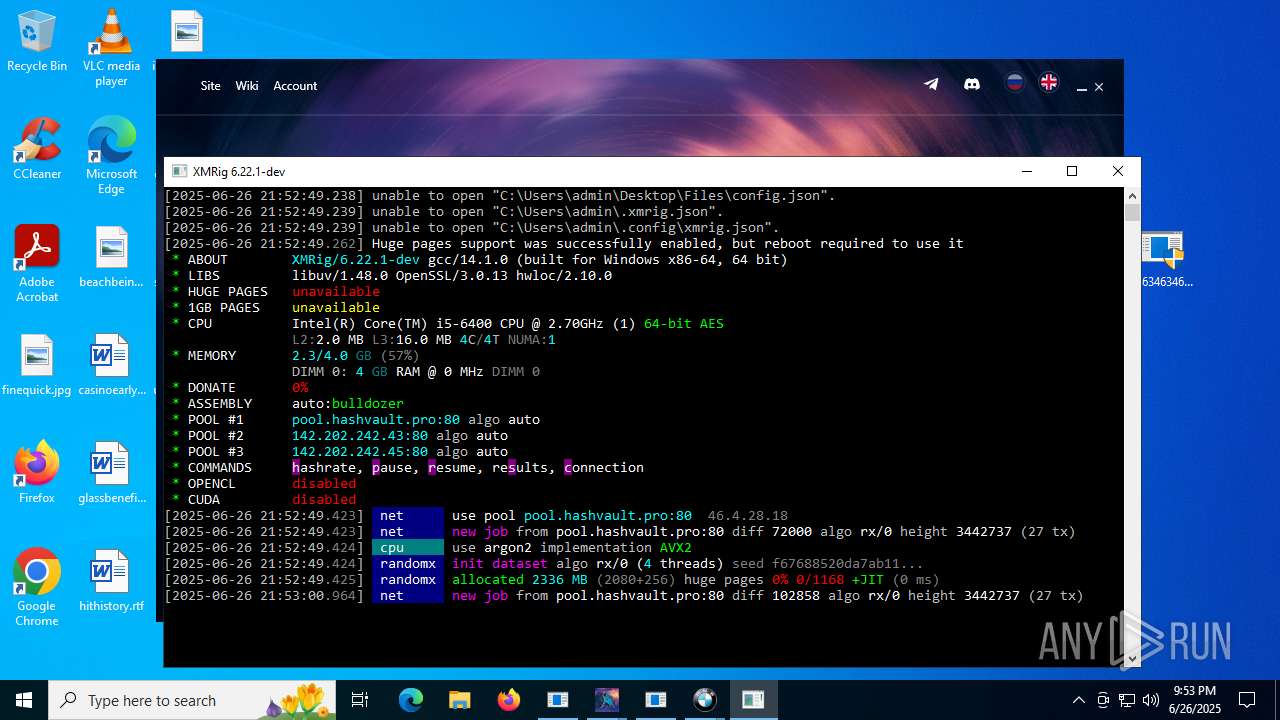
| File name: | 4363463463464363463463463.exe.zip |
| Full analysis: | https://app.any.run/tasks/65460073-67e5-43ef-bf57-573cf2699efa |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | June 26, 2025, 21:49:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
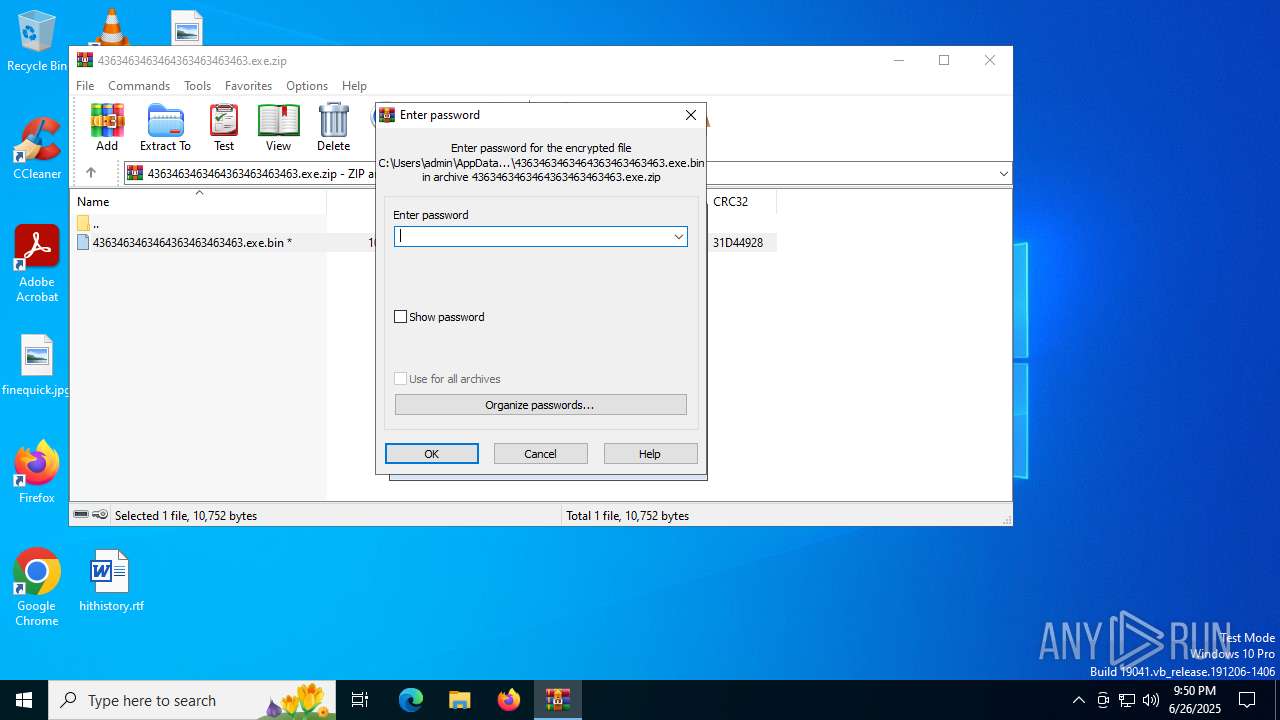
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 4C712F3A263A9EABB939F27B8CCDDF6B |
| SHA1: | A3646B75E9F955CD0225BD5E003F9BB4AFEC4E7A |
| SHA256: | C49C08555180E8DD1900506836FF516E8E52185F56D7487C28B0FC9FB8282D5E |
| SSDEEP: | 96:60OMpWP3p5peb3lugL62tDCOVUkAtQ+hEK7Jap4EYumcwKvqHW84XAsFyyOzqWnt:ejNAVuyDY4UXtQ+qQ5KvJAsFcTt |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3540)
STEALER has been found (auto)
- 4363463463464363463463463.exe (PID: 3672)
STEALC has been detected
- vtoroy.exe (PID: 1944)
STEALC mutex has been found
- vtoroy.exe (PID: 1944)
QUASARRAT has been found (auto)
- Sentil.exe (PID: 1056)
- RuntimeBroker.exe (PID: 7252)
- installer.exe (PID: 7396)
- discord.exe (PID: 7648)
LUMMA has been found (auto)
- 4363463463464363463463463.exe (PID: 3672)
- 4363463463464363463463463.exe (PID: 3672)
- 4363463463464363463463463.exe (PID: 3672)
- powershell.exe (PID: 7172)
- powershell.exe (PID: 3564)
Uses Task Scheduler to autorun other applications
- Sentil.exe (PID: 1056)
- Ul.pif (PID: 6348)
- Client-built.exe (PID: 7304)
- installer.exe (PID: 7396)
- WindowsSecurityCheckWSC.secureapp.exe (PID: 7480)
- Client.exe (PID: 7740)
- Client-built2.exe (PID: 7728)
- discord.exe (PID: 7648)
- Client.exe (PID: 9576)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2200)
- MSBuild.exe (PID: 2272)
- MSBuild.exe (PID: 7460)
- MSBuild.exe (PID: 10424)
- ec5013ad46.exe (PID: 6496)
Connects to the CnC server
- svchost.exe (PID: 2200)
- xblkpfZ8Y4.exe (PID: 7208)
- explorer.exe (PID: 4772)
- dumer.exe (PID: 6304)
LUMMA mutex has been found
- MSBuild.exe (PID: 2272)
- MSBuild.exe (PID: 7460)
- MSBuild.exe (PID: 10424)
- ec5013ad46.exe (PID: 6496)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 2272)
- bryjf.exe (PID: 2124)
- MSBuild.exe (PID: 7460)
- RegSvcs.exe (PID: 7764)
- ceng.exe (PID: 7864)
- MSBuild.exe (PID: 10424)
- ec5013ad46.exe (PID: 6496)
Steals credentials from Web Browsers
- MSBuild.exe (PID: 2272)
- MSBuild.exe (PID: 7460)
- RegSvcs.exe (PID: 7764)
- MSBuild.exe (PID: 10424)
- ec5013ad46.exe (PID: 6496)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 3672)
Create files in the Startup directory
- Fast%20Download.exe (PID: 4700)
- cmd.exe (PID: 5008)
- svchost.exe (PID: 4040)
NJRAT mutex has been found
- Fast%20Download.exe (PID: 4700)
LUMMA has been detected (YARA)
- MSBuild.exe (PID: 2272)
QUASAR has been detected (YARA)
- Client1.exe (PID: 4512)
Executing a file with an untrusted certificate
- brbotnet.exe (PID: 1944)
- LukeJazz.exe (PID: 6700)
- PingInfoView.exe (PID: 9948)
- tomcat8.exe (PID: 684)
- 691d9b712d.exe (PID: 9056)
GENERIC has been found (auto)
- 4363463463464363463463463.exe (PID: 3672)
- 4363463463464363463463463.exe (PID: 3672)
- Tu_Inspector32.exe (PID: 9828)
RAT has been found (auto)
- 4363463463464363463463463.exe (PID: 3672)
- windows.exe (PID: 6420)
RHADAMANTHYS has been found (auto)
- 4363463463464363463463463.exe (PID: 3672)
ASYNCRAT has been detected (MUTEX)
- windows.exe (PID: 6420)
- system.exe (PID: 6516)
FORMBOOK has been found (auto)
- 4363463463464363463463463.exe (PID: 3672)
Bypass execution policy to execute commands
- powershell.exe (PID: 7156)
- powershell.exe (PID: 6376)
- powershell.exe (PID: 5724)
- powershell.exe (PID: 2160)
- powershell.exe (PID: 6700)
Changes powershell execution policy (Bypass)
- bryjf.exe (PID: 2124)
- svchost.exe (PID: 4040)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 2276)
- findstr.exe (PID: 1356)
METASPLOIT has been found (auto)
- 4363463463464363463463463.exe (PID: 3672)
METASPLOIT has been detected (SURICATA)
- 4363463463464363463463463.exe (PID: 3672)
FORMBOOK has been detected
- explorer.exe (PID: 868)
- explorer.exe (PID: 4772)
- explorer.exe (PID: 3936)
NJRAT has been detected (YARA)
- Fast%20Download.exe (PID: 4700)
Adds path to the Windows Defender exclusion list
- svchost.exe (PID: 4040)
Changes Windows Defender settings
- svchost.exe (PID: 4040)
Adds process to the Windows Defender exclusion list
- svchost.exe (PID: 4040)
XWORM has been detected (YARA)
- XClient.exe (PID: 5720)
- svchost.exe (PID: 4040)
Uses Task Scheduler to run other applications
- svchost.exe (PID: 4040)
- Ul.pif (PID: 6348)
Changes the autorun value in the registry
- svchost.exe (PID: 4040)
- Ul.pif (PID: 6348)
- ctfmon.exe (PID: 2804)
- Dark_Brout_ncrypt.exe (PID: 7076)
- msdcsc.exe (PID: 2716)
- explorer.exe (PID: 868)
- klass.exe (PID: 9480)
- kkm.exe (PID: 9384)
- KKMAgent.exe (PID: 8672)
- dumer.exe (PID: 6304)
XWORM has been detected
- svchost.exe (PID: 4040)
ASYNCRAT has been detected (SURICATA)
- bryjf.exe (PID: 2124)
IRC has been detected (SURICATA)
- ctfmon.exe (PID: 1520)
Changes the login/logoff helper path in the registry
- Dark_Brout_ncrypt.exe (PID: 7076)
Changes firewall settings
- msdcsc.exe (PID: 2716)
DARKCOMET mutex has been found
- msdcsc.exe (PID: 2716)
- notepad.exe (PID: 2536)
Disables Windows firewall
- msdcsc.exe (PID: 2716)
UAC/LUA settings modification
- msdcsc.exe (PID: 2716)
Changes Security Center notification settings
- msdcsc.exe (PID: 2716)
FORMBOOK has been detected (YARA)
- explorer.exe (PID: 868)
RHADAMANTHYS has been detected (YARA)
- fontdrvhost.exe (PID: 3652)
QUASAR has been found (auto)
- 4363463463464363463463463.exe (PID: 3672)
- Client-built.exe (PID: 7304)
PUREHVNC has been detected (YARA)
- bryjf.exe (PID: 2124)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 7172)
- powershell.exe (PID: 3564)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7172)
- powershell.exe (PID: 3564)
SNAKEKEYLOGGER has been detected (SURICATA)
- RegSvcs.exe (PID: 7764)
ASYNCRAT has been detected (YARA)
- system.exe (PID: 6516)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2200)
- xblkpfZ8Y4.exe (PID: 7208)
METASPLOIT has been detected (YARA)
- award.pdf.exe (PID: 6716)
FORMBOOK has been detected (SURICATA)
- explorer.exe (PID: 4772)
Creates or modifies Windows services
- svchocl.exe (PID: 10356)
REDDRIVER has been detected (SURICATA)
- svchost.exe (PID: 10620)
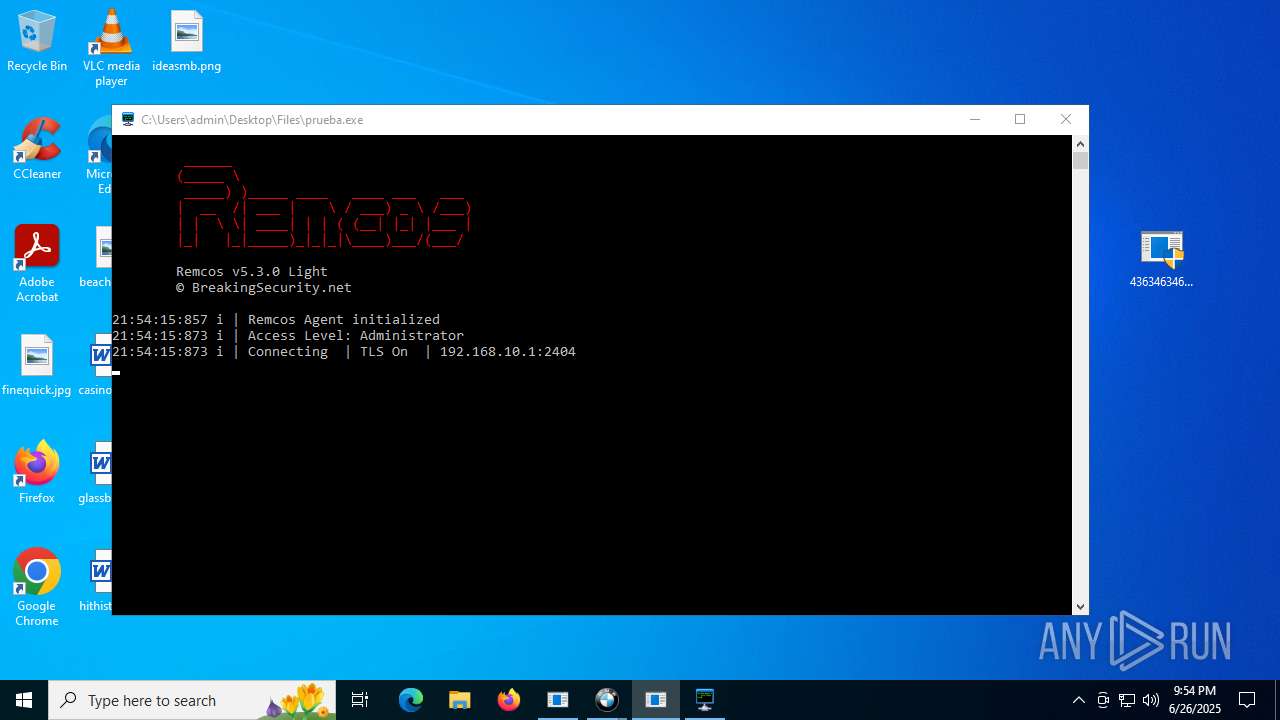
REMCOS mutex has been found
- prueba.exe (PID: 4808)
REMCOS has been detected
- prueba.exe (PID: 4808)
REMCOS has been detected (SURICATA)
- Host.exe (PID: 9252)
AMADEY mutex has been found
- dumer.exe (PID: 6304)
- random.exe (PID: 11004)
- D87N7LBIJLVVU4R0MH.exe (PID: 8292)
- dumer.exe (PID: 11816)
AMADEY has been detected (SURICATA)
- dumer.exe (PID: 6304)
LOKI has been found (auto)
- 4363463463464363463463463.exe (PID: 3672)
Starts Visual C# compiler
- qwalphaqw.exe (PID: 9184)
Application was injected by another process
- control.exe (PID: 9684)
- control.exe (PID: 9780)
Runs injected code in another process
- oSOnryg.exe (PID: 10328)
SUSPICIOUS
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 3672)
- Client1.exe (PID: 4512)
- QQHelper_1540.exe (PID: 4156)
- jd124.exe (PID: 7004)
- JUpdate.exe (PID: 1212)
- x210.exe (PID: 1156)
- windows.exe (PID: 6420)
- LukeJazz.exe (PID: 6700)
- svchost.exe (PID: 4040)
- ShellExperienceHost.exe (PID: 4580)
- Dark_Brout_ncrypt.exe (PID: 7076)
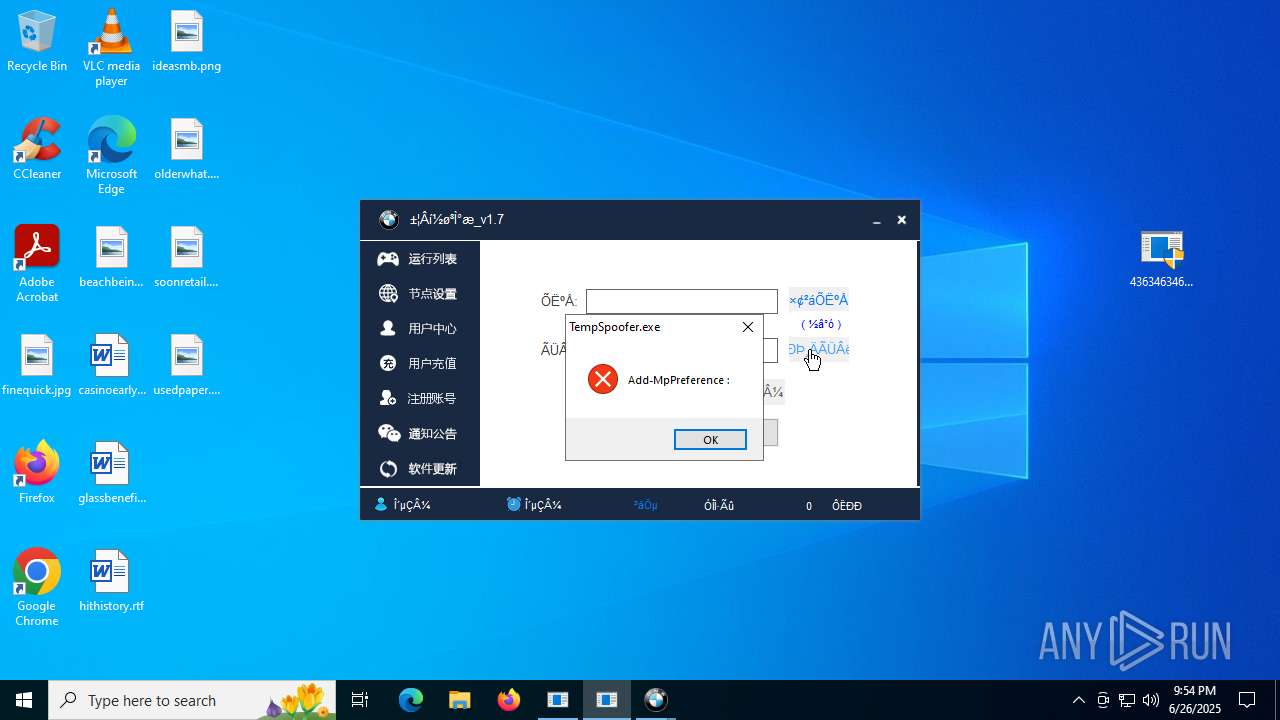
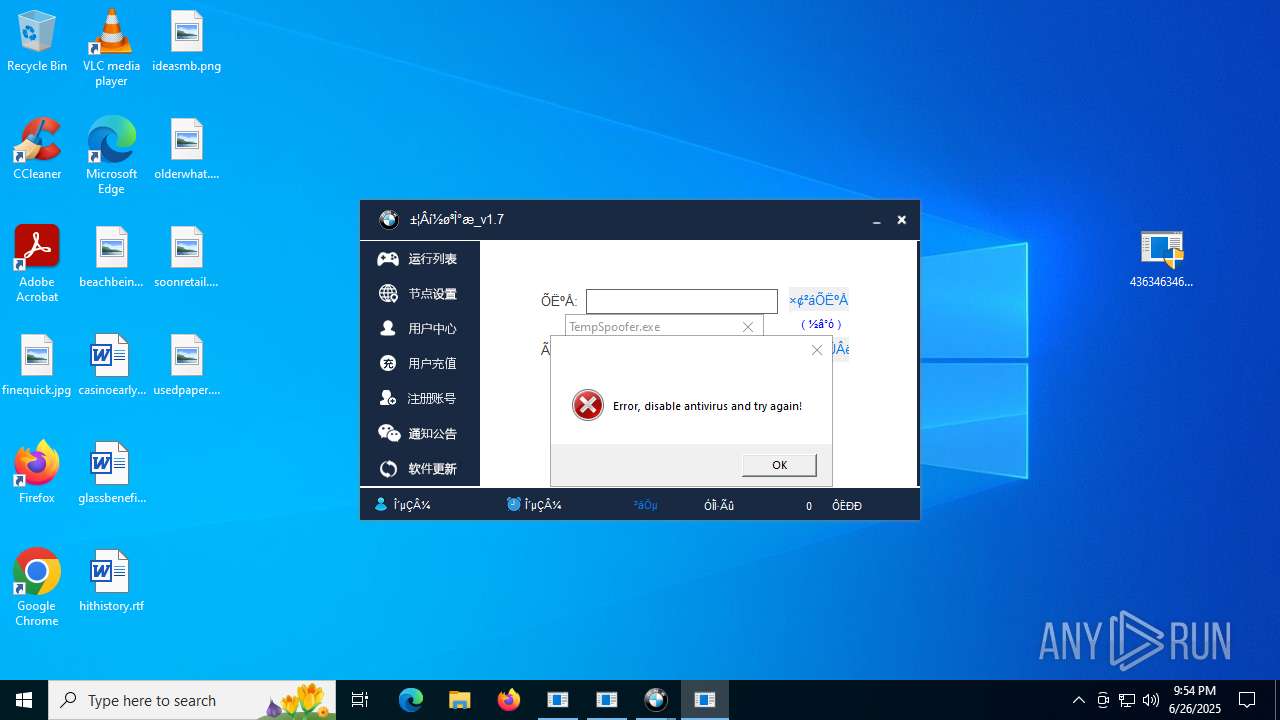
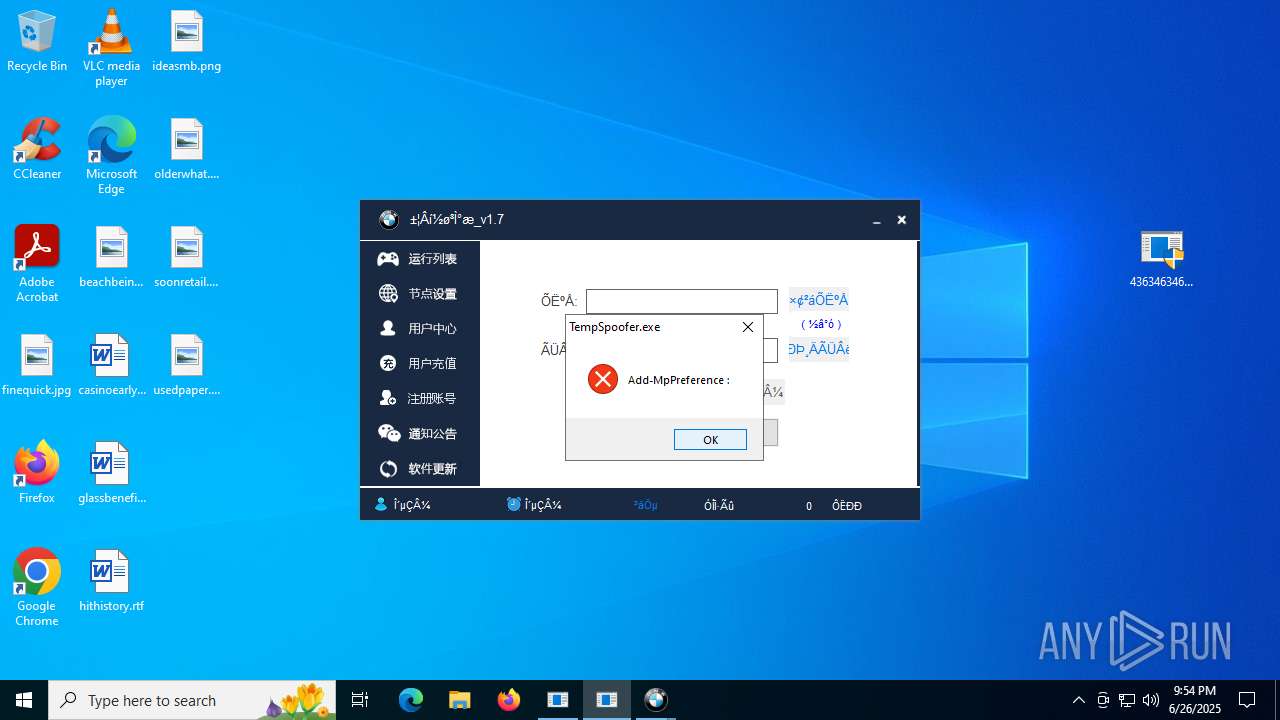
- TempSpoofer.exe (PID: 5848)
- RuntimeBroker.exe (PID: 7344)
- Assiah.exe (PID: 6896)
- RuntimeBroker.exe (PID: 7152)
- bmw_v1.7.exe (PID: 7300)
- RuntimeBroker.exe (PID: 5288)
- RuntimeBroker.exe (PID: 4808)
- RuntimeBroker.exe (PID: 8256)
- RuntimeBroker.exe (PID: 9512)
- RuntimeBroker.exe (PID: 10432)
- svchocl.exe (PID: 10356)
- RuntimeBroker.exe (PID: 10864)
- RuntimeBroker.exe (PID: 2292)
- KKMAgent.exe (PID: 8672)
- RuntimeBroker.exe (PID: 12216)
- Monotone.exe (PID: 8012)
- Host.exe (PID: 9252)
- RuntimeBroker.exe (PID: 10352)
- random.exe (PID: 11004)
- RuntimeBroker.exe (PID: 2140)
- dumer.exe (PID: 6304)
- Hl2dm_Updater.exe (PID: 1588)
- Hl2dm_Updater.exe (PID: 11908)
- RuntimeBroker.exe (PID: 9092)
- RuntimeBroker.exe (PID: 10220)
- sFFG7Wg.exe (PID: 11412)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 3672)
- jd124.exe (PID: 7004)
- JUpdate.exe (PID: 1212)
- %E5%9B%9B%E6%96%B9%E5%B9%B3%E5%8F%B0-%E5%8D%A1%E5%95%86%E7%AB%AF.exe (PID: 6268)
- curl.exe (PID: 8124)
- dumer.exe (PID: 6304)
- Hl2dm_Updater.exe (PID: 1588)
- Hl2dm_Updater.exe (PID: 11908)
- ec5013ad46.exe (PID: 6496)
Windows Defender mutex has been found
- vtoroy.exe (PID: 1944)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 3672)
- Sentil.exe (PID: 1056)
- jd124.exe (PID: 7004)
- JUpdate.exe (PID: 1212)
- x210.exe (PID: 1156)
- windows.exe (PID: 6420)
- cmd.exe (PID: 4580)
- Ul.pif (PID: 4216)
- bryjf.exe (PID: 2124)
- svchost.exe (PID: 4040)
- Ul.pif (PID: 6348)
- ctfmon.exe (PID: 2804)
- Dark_Brout_ncrypt.exe (PID: 7076)
- RuntimeBroker.exe (PID: 7252)
- Client-built.exe (PID: 7304)
- installer.exe (PID: 7396)
- powershell.exe (PID: 7172)
- HDDrive1095_XinAnPlug3030_20230619_inno.exe (PID: 32)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7532)
- darts-wled.exe (PID: 7948)
- Client-built2.exe (PID: 7728)
- explorer.exe (PID: 868)
- file.exe (PID: 8488)
- kkm.exe (PID: 9384)
- Ganja3.exe (PID: 9460)
- tb.exe (PID: 9912)
- svchocl.exe (PID: 10356)
- discord.exe (PID: 7648)
- powershell.exe (PID: 3564)
- %E5%9B%9B%E6%96%B9%E5%B9%B3%E5%8F%B0-%E5%8D%A1%E5%95%86%E7%AB%AF.exe (PID: 6268)
- random.exe (PID: 11004)
- dumer.exe (PID: 6304)
- Hl2dm_Updater.exe (PID: 1588)
- Hl2dm_Updater.exe (PID: 11908)
- ec5013ad46.exe (PID: 6496)
- tktVLbc.tmp (PID: 7496)
- Tu_Inspector32.exe (PID: 9572)
- tktVLbc.exe (PID: 7872)
- Tu_Inspector32.exe (PID: 9828)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 3672)
- dumer.exe (PID: 6304)
- ec5013ad46.exe (PID: 6496)
- control.exe (PID: 9684)
Process drops legitimate windows executable
- 4363463463464363463463463.exe (PID: 3672)
- RuntimeBroker.exe (PID: 7252)
- powershell.exe (PID: 7172)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7532)
- darts-wled.exe (PID: 7948)
- kkm.exe (PID: 9384)
- powershell.exe (PID: 3564)
- dumer.exe (PID: 6304)
- tktVLbc.tmp (PID: 7496)
- Tu_Inspector32.exe (PID: 9572)
Starts a Microsoft application from unusual location
- neploskiy_crypted_LAB.exe (PID: 6472)
- RuntimeBroker.exe (PID: 7252)
- RuntimeBroker.exe (PID: 7344)
- RuntimeBroker.exe (PID: 7152)
- RuntimeBroker.exe (PID: 5288)
- RuntimeBroker.exe (PID: 4808)
- RuntimeBroker.exe (PID: 8256)
- RuntimeBroker.exe (PID: 9512)
- tb.exe (PID: 9912)
- RuntimeBroker.exe (PID: 10432)
- RuntimeBroker.exe (PID: 10864)
- RuntimeBroker.exe (PID: 2292)
- RuntimeBroker.exe (PID: 12216)
- RuntimeBroker.exe (PID: 10352)
- RuntimeBroker.exe (PID: 2140)
- RuntimeBroker.exe (PID: 9092)
- oSOnryg.exe (PID: 10328)
- RuntimeBroker.exe (PID: 10220)
Starts itself from another location
- Sentil.exe (PID: 1056)
- ctfmon.exe (PID: 2804)
- Dark_Brout_ncrypt.exe (PID: 7076)
- RuntimeBroker.exe (PID: 7252)
- Client-built.exe (PID: 7304)
- installer.exe (PID: 7396)
- Client-built2.exe (PID: 7728)
- Ganja3.exe (PID: 9460)
- discord.exe (PID: 7648)
- random.exe (PID: 11004)
- Tu_Inspector32.exe (PID: 9572)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 3672)
- jd124.exe (PID: 7004)
- JUpdate.exe (PID: 1212)
- ctfmon.exe (PID: 1520)
- svchost.exe (PID: 2200)
- xblkpfZ8Y4.exe (PID: 7208)
- Hl2dm_Updater.exe (PID: 1588)
- dumer.exe (PID: 6304)
- Hl2dm_Updater.exe (PID: 11908)
- ec5013ad46.exe (PID: 6496)
Contacting a server suspected of hosting an CnC
- MSBuild.exe (PID: 2272)
- svchost.exe (PID: 2200)
- bryjf.exe (PID: 2124)
- MSBuild.exe (PID: 7460)
- explorer.exe (PID: 4772)
- Host.exe (PID: 9252)
- MSBuild.exe (PID: 10424)
- dumer.exe (PID: 6304)
- ec5013ad46.exe (PID: 6496)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 2272)
- MSBuild.exe (PID: 7460)
- RegSvcs.exe (PID: 7764)
- MSBuild.exe (PID: 10424)
- MSBuild.exe (PID: 9068)
Connects to unusual port
- Client1.exe (PID: 4512)
- Fast%20Download.exe (PID: 4700)
- XClient.exe (PID: 5720)
- 4363463463464363463463463.exe (PID: 3672)
- fontdrvhost.exe (PID: 3652)
- bryjf.exe (PID: 2124)
- system.exe (PID: 6516)
- svchost.exe (PID: 4040)
- Ul.pif (PID: 6348)
- ctfmon.exe (PID: 1520)
- msf.exe (PID: 5684)
- Client.exe (PID: 7740)
- Client.exe (PID: 7632)
- WindowsSecurityCheckWSC.secureapp.exe (PID: 7480)
- explorer.exe (PID: 868)
- tb.exe (PID: 9912)
- svchocl.exe (PID: 10356)
- svchost.exe (PID: 10620)
- tcp_windows_amd64.exe (PID: 7348)
- RegAsm.exe (PID: 4052)
- Host.exe (PID: 9252)
- prueba.exe (PID: 4808)
- Client.exe (PID: 9576)
- %E5%9B%9B%E6%96%B9%E5%B9%B3%E5%8F%B0-%E5%8D%A1%E5%95%86%E7%AB%AF.exe (PID: 6268)
- curl.exe (PID: 8124)
Creates file in the systems drive root
- explorer.exe (PID: 4772)
Uses ATTRIB.EXE to modify file attributes
- Fast%20Download.exe (PID: 4700)
- cmd.exe (PID: 1948)
- cmd.exe (PID: 1128)
Searches for installed software
- MSBuild.exe (PID: 2272)
- MSBuild.exe (PID: 7460)
- MSBuild.exe (PID: 10424)
- ec5013ad46.exe (PID: 6496)
There is functionality for taking screenshot (YARA)
- MSBuild.exe (PID: 2272)
- Client1.exe (PID: 4512)
- explorer.exe (PID: 868)
Drops a system driver (possible attempt to evade defenses)
- x210.exe (PID: 1156)
Starts CMD.EXE for commands execution
- windows.exe (PID: 6420)
- rarx210.exe (PID: 2732)
- LukeJazz.exe (PID: 6700)
- cmd.exe (PID: 4580)
- explorer.exe (PID: 868)
- explorer.exe (PID: 4772)
- Dark_Brout_ncrypt.exe (PID: 7076)
- RuntimeBroker.exe (PID: 7344)
- RuntimeBroker.exe (PID: 7152)
- RuntimeBroker.exe (PID: 5288)
- RuntimeBroker.exe (PID: 4808)
- RuntimeBroker.exe (PID: 8256)
- RuntimeBroker.exe (PID: 9512)
- tb.exe (PID: 9912)
- RuntimeBroker.exe (PID: 10432)
- RuntimeBroker.exe (PID: 10864)
- svchocl.exe (PID: 10356)
- RuntimeBroker.exe (PID: 2292)
- RuntimeBroker.exe (PID: 12216)
- RuntimeBroker.exe (PID: 10352)
- RuntimeBroker.exe (PID: 2140)
- patcher.exe (PID: 1688)
- RuntimeBroker.exe (PID: 9092)
- RuntimeBroker.exe (PID: 10220)
The process creates files with name similar to system file names
- windows.exe (PID: 6420)
- 4363463463464363463463463.exe (PID: 3672)
- svchost.exe (PID: 4040)
- ctfmon.exe (PID: 2804)
- file.exe (PID: 8488)
Executing commands from a ".bat" file
- windows.exe (PID: 6420)
- RuntimeBroker.exe (PID: 7344)
- RuntimeBroker.exe (PID: 7152)
- RuntimeBroker.exe (PID: 5288)
- RuntimeBroker.exe (PID: 4808)
- RuntimeBroker.exe (PID: 8256)
- RuntimeBroker.exe (PID: 9512)
- tb.exe (PID: 9912)
- RuntimeBroker.exe (PID: 10432)
- RuntimeBroker.exe (PID: 10864)
- RuntimeBroker.exe (PID: 2292)
- RuntimeBroker.exe (PID: 12216)
- RuntimeBroker.exe (PID: 10352)
- RuntimeBroker.exe (PID: 2140)
- patcher.exe (PID: 1688)
- RuntimeBroker.exe (PID: 9092)
- RuntimeBroker.exe (PID: 10220)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5708)
- cmd.exe (PID: 4580)
The process checks if it is being run in the virtual environment
- fontdrvhost.exe (PID: 3652)
The process bypasses the loading of PowerShell profile settings
- bryjf.exe (PID: 2124)
Executing commands from ".cmd" file
- LukeJazz.exe (PID: 6700)
BASE64 encoded PowerShell command has been detected
- bryjf.exe (PID: 2124)
- TempSpoofer.exe (PID: 5848)
- Monotone.exe (PID: 8012)
Base64-obfuscated command line is found
- bryjf.exe (PID: 2124)
- TempSpoofer.exe (PID: 5848)
- Monotone.exe (PID: 8012)
Starts POWERSHELL.EXE for commands execution
- bryjf.exe (PID: 2124)
- svchost.exe (PID: 4040)
- TempSpoofer.exe (PID: 5848)
- powershell.exe (PID: 7172)
- Monotone.exe (PID: 8012)
- powershell.exe (PID: 3564)
Application launched itself
- TORRENTOLD-1.exe (PID: 4216)
- cmd.exe (PID: 4580)
- powershell.exe (PID: 7172)
- darts-wled.exe (PID: 7948)
- powershell.exe (PID: 3564)
- control.exe (PID: 9780)
The executable file from the user directory is run by the CMD process
- system.exe (PID: 6516)
- Ul.pif (PID: 4216)
- RuntimeBroker.exe (PID: 7152)
- RuntimeBroker.exe (PID: 5288)
- RuntimeBroker.exe (PID: 4808)
- RuntimeBroker.exe (PID: 8256)
- RuntimeBroker.exe (PID: 9512)
- RuntimeBroker.exe (PID: 10432)
- RuntimeBroker.exe (PID: 10864)
- RuntimeBroker.exe (PID: 2292)
- RuntimeBroker.exe (PID: 12216)
- RuntimeBroker.exe (PID: 10352)
- RuntimeBroker.exe (PID: 2140)
- RuntimeBroker.exe (PID: 9092)
- RuntimeBroker.exe (PID: 10220)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4580)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 4580)
- Ul.pif (PID: 4216)
Suspicious file concatenation
- cmd.exe (PID: 304)
Get information on the list of running processes
- cmd.exe (PID: 4580)
Starts application with an unusual extension
- cmd.exe (PID: 4580)
- explorer.exe (PID: 4772)
- cmd.exe (PID: 7640)
- cmd.exe (PID: 7540)
- cmd.exe (PID: 6528)
- cmd.exe (PID: 7792)
- cmd.exe (PID: 8344)
- cmd.exe (PID: 9664)
- cmd.exe (PID: 10512)
- cmd.exe (PID: 10968)
- cmd.exe (PID: 7712)
- cmd.exe (PID: 11892)
- cmd.exe (PID: 10304)
- cmd.exe (PID: 9220)
- cmd.exe (PID: 8836)
- cmd.exe (PID: 9400)
Starts the AutoIt3 executable file
- cmd.exe (PID: 4580)
- explorer.exe (PID: 4772)
Reads Internet Explorer settings
- jd124.exe (PID: 4084)
- Hl2dm_Updater.exe (PID: 11908)
Reads the date of Windows installation
- svchost.exe (PID: 4040)
- RuntimeBroker.exe (PID: 7344)
- RuntimeBroker.exe (PID: 7152)
- RuntimeBroker.exe (PID: 5288)
- RuntimeBroker.exe (PID: 4808)
- RuntimeBroker.exe (PID: 8256)
- RuntimeBroker.exe (PID: 9512)
- svchocl.exe (PID: 10356)
- RuntimeBroker.exe (PID: 10432)
- RuntimeBroker.exe (PID: 10864)
- RuntimeBroker.exe (PID: 2292)
- RuntimeBroker.exe (PID: 12216)
- RuntimeBroker.exe (PID: 10352)
- RuntimeBroker.exe (PID: 2140)
- RuntimeBroker.exe (PID: 9092)
- RuntimeBroker.exe (PID: 10220)
Script adds exclusion path to Windows Defender
- svchost.exe (PID: 4040)
Checks for external IP
- svchost.exe (PID: 4040)
- svchost.exe (PID: 2200)
- RegSvcs.exe (PID: 7764)
Script adds exclusion process to Windows Defender
- svchost.exe (PID: 4040)
The process executes via Task Scheduler
- svchost.exe (PID: 2212)
- svchost.exe (PID: 7220)
- svchost.exe (PID: 8108)
- svchost.exe (PID: 11372)
- dumer.exe (PID: 11816)
Start notepad (likely ransomware note)
- Dark_Brout_ncrypt.exe (PID: 7076)
- msdcsc.exe (PID: 2716)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7640)
- cmd.exe (PID: 7540)
- cmd.exe (PID: 6528)
- cmd.exe (PID: 7792)
- cmd.exe (PID: 8344)
- cmd.exe (PID: 9664)
- cmd.exe (PID: 9968)
- cmd.exe (PID: 10512)
- cmd.exe (PID: 10968)
- cmd.exe (PID: 7712)
- cmd.exe (PID: 11892)
- cmd.exe (PID: 10304)
- cmd.exe (PID: 9220)
- cmd.exe (PID: 8836)
- cmd.exe (PID: 9400)
Multiple wallet extension IDs have been found
- bryjf.exe (PID: 2124)
Reads the Windows owner or organization settings
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7532)
- tktVLbc.tmp (PID: 7496)
Process drops python dynamic module
- darts-wled.exe (PID: 7948)
The process drops C-runtime libraries
- darts-wled.exe (PID: 7948)
- tktVLbc.tmp (PID: 7496)
- Tu_Inspector32.exe (PID: 9572)
Loads Python modules
- darts-wled.exe (PID: 4880)
The process verifies whether the antivirus software is installed
- RegSvcs.exe (PID: 7764)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2200)
Malware-specific behavior (creating "System.dll" in Temp)
- file.exe (PID: 8488)
Creates a software uninstall entry
- kkm.exe (PID: 9384)
Executes application which crashes
- ntladlklthawd.exe (PID: 9552)
- RedLineStealer.exe (PID: 2128)
Hides command output
- cmd.exe (PID: 10676)
Connects to SMTP port
- ceng.exe (PID: 7864)
Reads the BIOS version
- dumer.exe (PID: 6304)
- random.exe (PID: 11004)
- ec5013ad46.exe (PID: 6496)
- dumer.exe (PID: 11816)
Reads Microsoft Outlook installation path
- Hl2dm_Updater.exe (PID: 11908)
INFO
Manual execution by a user
- 4363463463464363463463463.exe (PID: 4552)
- 4363463463464363463463463.exe (PID: 3672)
- explorer.exe (PID: 868)
- cmd.exe (PID: 5008)
- Ul.pif (PID: 6348)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4772)
- mmc.exe (PID: 1976)
- mmc.exe (PID: 4132)
- explorer.exe (PID: 3936)
- powershell.exe (PID: 7620)
- explorer.exe (PID: 868)
- powershell.exe (PID: 9524)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3540)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 3672)
- Sentil.exe (PID: 1056)
- Client1.exe (PID: 4512)
- MSBuild.exe (PID: 2272)
- Fast%20Download.exe (PID: 4700)
- brbotnet.exe (PID: 1944)
- jd124.exe (PID: 7004)
- XClient.exe (PID: 5720)
- JUpdate.exe (PID: 1212)
- windows.exe (PID: 6420)
- jd124.exe (PID: 4084)
- bryjf.exe (PID: 2124)
- svchost.exe (PID: 4040)
- TORRENTOLD-1.exe (PID: 4216)
- system.exe (PID: 6516)
- ShellExperienceHost.exe (PID: 4580)
- svchost.exe (PID: 2212)
- Assiah.exe (PID: 6896)
- TempSpoofer.exe (PID: 5848)
- RuntimeBroker.exe (PID: 7252)
- RuntimeBroker.exe (PID: 7344)
- Client-built.exe (PID: 7304)
- installer.exe (PID: 7396)
- WindowsSecurityCheckWSC.secureapp.exe (PID: 7480)
- Client.exe (PID: 7740)
- RuntimeBroker.exe (PID: 7152)
- MSBuild.exe (PID: 7460)
- RegSvcs.exe (PID: 7764)
- RuntimeBroker.exe (PID: 5288)
- darts-wled.exe (PID: 4880)
- bmw_v1.7.exe (PID: 7300)
- Client-built2.exe (PID: 7728)
- Client.exe (PID: 7632)
- RuntimeBroker.exe (PID: 4808)
- svchost.exe (PID: 7220)
- RuntimeBroker.exe (PID: 8256)
- RuntimeBroker.exe (PID: 9512)
- RuntimeBroker.exe (PID: 10432)
- RuntimeBroker.exe (PID: 10864)
- svchost.exe (PID: 8108)
- RuntimeBroker.exe (PID: 2292)
- KKMAgent.exe (PID: 8672)
- RegAsm.exe (PID: 4052)
- Monotone.exe (PID: 8012)
- RuntimeBroker.exe (PID: 12216)
- discord.exe (PID: 7648)
- Host.exe (PID: 9252)
- ceng.exe (PID: 7864)
- Client.exe (PID: 9576)
- RuntimeBroker.exe (PID: 10352)
- %E5%9B%9B%E6%96%B9%E5%B9%B3%E5%8F%B0-%E5%8D%A1%E5%95%86%E7%AB%AF.exe (PID: 6268)
- MSBuild.exe (PID: 10424)
- RuntimeBroker.exe (PID: 2140)
- ec5013ad46.exe (PID: 6496)
- RuntimeBroker.exe (PID: 9092)
- RuntimeBroker.exe (PID: 10220)
- MSBuild.exe (PID: 9068)
- svchost.exe (PID: 11372)
- sFFG7Wg.exe (PID: 11412)
Disables trace logs
- 4363463463464363463463463.exe (PID: 3672)
- jd124.exe (PID: 7004)
- JUpdate.exe (PID: 1212)
- jd124.exe (PID: 4084)
- svchost.exe (PID: 4040)
- Assiah.exe (PID: 6896)
- powershell.exe (PID: 7172)
- RegSvcs.exe (PID: 7764)
- KKMAgent.exe (PID: 8672)
- powershell.exe (PID: 3564)
- %E5%9B%9B%E6%96%B9%E5%B9%B3%E5%8F%B0-%E5%8D%A1%E5%95%86%E7%AB%AF.exe (PID: 6268)
Reads the computer name
- 4363463463464363463463463.exe (PID: 3672)
- vtoroy.exe (PID: 1944)
- Sentil.exe (PID: 1056)
- Client1.exe (PID: 4512)
- MSBuild.exe (PID: 2272)
- QQHelper_1540.exe (PID: 4156)
- Fast%20Download.exe (PID: 4700)
- brbotnet.exe (PID: 1944)
- XClient.exe (PID: 5720)
- jd124.exe (PID: 7004)
- JUpdate.exe (PID: 1212)
- windows.exe (PID: 6420)
- x210.exe (PID: 1156)
- jd124.exe (PID: 4084)
- LukeJazz.exe (PID: 6700)
- nbin22.exe (PID: 2348)
- bryjf.exe (PID: 2124)
- TORRENTOLD-1.exe (PID: 4216)
- svchost.exe (PID: 4040)
- TORRENTOLD-1.exe (PID: 6768)
- system.exe (PID: 6516)
- Ul.pif (PID: 4216)
- Ul.pif (PID: 6348)
- ShellExperienceHost.exe (PID: 4580)
- YHY_Setup.exe (PID: 4192)
- svchost.exe (PID: 2212)
- ctfmon.exe (PID: 1520)
- ctfmon.exe (PID: 2804)
- Dark_Brout_ncrypt.exe (PID: 7076)
- msdcsc.exe (PID: 2716)
- nircmd.exe (PID: 6876)
- pm3100.exe (PID: 3588)
- Assiah.exe (PID: 6896)
- TempSpoofer.exe (PID: 5848)
- mimikatz.exe (PID: 7076)
- RuntimeBroker.exe (PID: 7252)
- Client-built.exe (PID: 7304)
- RuntimeBroker.exe (PID: 7344)
- installer.exe (PID: 7396)
- WindowsSecurityCheckWSC.secureapp.exe (PID: 7480)
- Client.exe (PID: 7740)
- MSBuild.exe (PID: 7460)
- RuntimeBroker.exe (PID: 7152)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7532)
- RegSvcs.exe (PID: 7764)
- darts-wled.exe (PID: 7948)
- RuntimeBroker.exe (PID: 5288)
- bmw_v1.7.exe (PID: 7300)
- Client-built2.exe (PID: 7728)
- Client.exe (PID: 7632)
- xblkpfZ8Y4.exe (PID: 7208)
- Ganja168.exe (PID: 2276)
- RuntimeBroker.exe (PID: 4808)
- award.pdf.exe (PID: 6716)
- msf.exe (PID: 5684)
- svchost.exe (PID: 7220)
- identity_helper.exe (PID: 7360)
- RuntimeBroker.exe (PID: 8256)
- identity_helper.exe (PID: 9276)
- kkm.exe (PID: 9384)
- Ganja3.exe (PID: 9460)
- file.exe (PID: 8488)
- RuntimeBroker.exe (PID: 9512)
- ntladlklthawd.exe (PID: 9552)
- klass.exe (PID: 9480)
- tb.exe (PID: 9912)
- PingInfoView.exe (PID: 9948)
- RuntimeBroker.exe (PID: 10432)
- svchocl.exe (PID: 10356)
- RuntimeBroker.exe (PID: 10864)
- svchost.exe (PID: 8108)
- RuntimeBroker.exe (PID: 2292)
- KKMAgent.exe (PID: 8672)
- RedLineStealer.exe (PID: 2128)
- RegAsm.exe (PID: 4052)
- tcp_windows_amd64.exe (PID: 7348)
- RuntimeBroker.exe (PID: 12216)
- Monotone.exe (PID: 8012)
- discord.exe (PID: 7648)
- prueba.exe (PID: 4808)
- ceng.exe (PID: 7864)
- Host.exe (PID: 9252)
- Client.exe (PID: 9576)
- xsh.exe (PID: 10180)
- RuntimeBroker.exe (PID: 10352)
- %E5%9B%9B%E6%96%B9%E5%B9%B3%E5%8F%B0-%E5%8D%A1%E5%95%86%E7%AB%AF.exe (PID: 6268)
- WxWorkMultiOpen.exe (PID: 10664)
- MSBuild.exe (PID: 10424)
- t_vnc.exe (PID: 5268)
- random.exe (PID: 11004)
- dumer.exe (PID: 6304)
- AutoRuns.exe (PID: 12112)
- RuntimeBroker.exe (PID: 2140)
- Hl2dm_Updater.exe (PID: 1588)
- ec5013ad46.exe (PID: 6496)
- Hl2dm_Updater.new.exe (PID: 3880)
- Hl2dm_Updater.exe (PID: 11908)
- qwalphaqw.exe (PID: 9184)
- 691d9b712d.exe (PID: 9056)
- RuntimeBroker.exe (PID: 9092)
- MSBuild.exe (PID: 9068)
- RuntimeBroker.exe (PID: 10220)
- tktVLbc.exe (PID: 7872)
- D87N7LBIJLVVU4R0MH.exe (PID: 8292)
- Tu_Inspector32.exe (PID: 9572)
- tktVLbc.tmp (PID: 7496)
- Tu_Inspector32.exe (PID: 9828)
- svchost.exe (PID: 11372)
- sFFG7Wg.exe (PID: 11412)
Checks proxy server information
- 4363463463464363463463463.exe (PID: 3672)
- QQHelper_1540.exe (PID: 4156)
- jd124.exe (PID: 7004)
- JUpdate.exe (PID: 1212)
- jd124.exe (PID: 4084)
- svchost.exe (PID: 4040)
- slui.exe (PID: 4160)
- Assiah.exe (PID: 6896)
- powershell.exe (PID: 7172)
- RegSvcs.exe (PID: 7764)
- bmw_v1.7.exe (PID: 7300)
- explorer.exe (PID: 868)
- KKMAgent.exe (PID: 8672)
- WerFault.exe (PID: 7588)
- Host.exe (PID: 9252)
- powershell.exe (PID: 3564)
- %E5%9B%9B%E6%96%B9%E5%B9%B3%E5%8F%B0-%E5%8D%A1%E5%95%86%E7%AB%AF.exe (PID: 6268)
- dumer.exe (PID: 6304)
- Hl2dm_Updater.exe (PID: 11908)
- sFFG7Wg.exe (PID: 11412)
Checks supported languages
- 4363463463464363463463463.exe (PID: 3672)
- vtoroy.exe (PID: 1944)
- Client1.exe (PID: 4512)
- neploskiy_crypted_LAB.exe (PID: 6472)
- Sentil.exe (PID: 1056)
- MSBuild.exe (PID: 2272)
- QQHelper_1540.exe (PID: 4156)
- Fast%20Download.exe (PID: 4700)
- mimilove.exe (PID: 6780)
- brbotnet.exe (PID: 1944)
- jd124.exe (PID: 7004)
- XClient.exe (PID: 5720)
- JUpdate.exe (PID: 1212)
- windows.exe (PID: 6420)
- x210.exe (PID: 1156)
- jd124.exe (PID: 4084)
- rarx210.exe (PID: 2732)
- zeropersca.exe (PID: 5716)
- LukeJazz.exe (PID: 6700)
- nbin22.exe (PID: 2348)
- bryjf.exe (PID: 2124)
- TORRENTOLD-1.exe (PID: 4216)
- svchost.exe (PID: 4040)
- TORRENTOLD-1.exe (PID: 6768)
- system.exe (PID: 6516)
- award.pdf.exe (PID: 6716)
- Ul.pif (PID: 4216)
- Ul.pif (PID: 6348)
- ShellExperienceHost.exe (PID: 4580)
- YHY_Setup.exe (PID: 4192)
- ctfmon.exe (PID: 2804)
- ctfmon.exe (PID: 1520)
- svchost.exe (PID: 2212)
- msf.exe (PID: 5684)
- Dark_Brout_ncrypt.exe (PID: 7076)
- msdcsc.exe (PID: 2716)
- pm3100.exe (PID: 3588)
- nircmd.exe (PID: 6876)
- Assiah.exe (PID: 6896)
- rickroll.exe (PID: 4584)
- TempSpoofer.exe (PID: 5848)
- mimikatz.exe (PID: 7076)
- RuntimeBroker.exe (PID: 7252)
- Client-built.exe (PID: 7304)
- RuntimeBroker.exe (PID: 7344)
- installer.exe (PID: 7396)
- WindowsSecurityCheckWSC.secureapp.exe (PID: 7480)
- Client.exe (PID: 7740)
- chcp.com (PID: 7764)
- 4l5b2jwj.o5y0.exe (PID: 8152)
- MSBuild.exe (PID: 7460)
- RuntimeBroker.exe (PID: 7152)
- HDDrive1095_XinAnPlug3030_20230619_inno.exe (PID: 32)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7532)
- chcp.com (PID: 2168)
- catee.exe (PID: 7772)
- RegSvcs.exe (PID: 7764)
- darts-wled.exe (PID: 7948)
- RuntimeBroker.exe (PID: 5288)
- bmw_v1.7.exe (PID: 7300)
- darts-wled.exe (PID: 4880)
- chcp.com (PID: 7060)
- Client-built2.exe (PID: 7728)
- Client.exe (PID: 7632)
- Ganja168.exe (PID: 2276)
- xblkpfZ8Y4.exe (PID: 7208)
- RuntimeBroker.exe (PID: 4808)
- chcp.com (PID: 2276)
- svchost.exe (PID: 7220)
- identity_helper.exe (PID: 7360)
- RuntimeBroker.exe (PID: 8256)
- chcp.com (PID: 8400)
- identity_helper.exe (PID: 9276)
- Ganja3.exe (PID: 9460)
- file.exe (PID: 8488)
- kkm.exe (PID: 9384)
- RuntimeBroker.exe (PID: 9512)
- klass.exe (PID: 9480)
- chcp.com (PID: 9740)
- tb.exe (PID: 9912)
- ntladlklthawd.exe (PID: 9552)
- PingInfoView.exe (PID: 9948)
- svchocl.exe (PID: 10356)
- RuntimeBroker.exe (PID: 10432)
- chcp.com (PID: 10560)
- RuntimeBroker.exe (PID: 10864)
- RuntimeBroker.exe (PID: 2292)
- chcp.com (PID: 11040)
- svchost.exe (PID: 8108)
- chcp.com (PID: 8284)
- KKMAgent.exe (PID: 8672)
- RedLineStealer.exe (PID: 2128)
- tomcat8.exe (PID: 684)
- RegAsm.exe (PID: 4052)
- tcp_windows_amd64.exe (PID: 7348)
- RuntimeBroker.exe (PID: 12216)
- Monotone.exe (PID: 8012)
- discord.exe (PID: 7648)
- prueba.exe (PID: 4808)
- ceng.exe (PID: 7864)
- chcp.com (PID: 8540)
- Host.exe (PID: 9252)
- Client.exe (PID: 9576)
- xsh.exe (PID: 10180)
- gsav3omg.vaj0.exe (PID: 10112)
- RuntimeBroker.exe (PID: 10352)
- chcp.com (PID: 9284)
- %E5%9B%9B%E6%96%B9%E5%B9%B3%E5%8F%B0-%E5%8D%A1%E5%95%86%E7%AB%AF.exe (PID: 6268)
- MSBuild.exe (PID: 10424)
- t_vnc.exe (PID: 5268)
- WxWorkMultiOpen.exe (PID: 10664)
- dumer.exe (PID: 6304)
- AutoRuns.exe (PID: 12112)
- random.exe (PID: 11004)
- RuntimeBroker.exe (PID: 2140)
- chcp.com (PID: 7196)
- patcher.exe (PID: 1688)
- curl.exe (PID: 8124)
- Hl2dm_Updater.exe (PID: 1588)
- kdmapper_Release.exe (PID: 7620)
- ec5013ad46.exe (PID: 6496)
- Hl2dm_Updater.new.exe (PID: 3880)
- Hl2dm_Updater.exe (PID: 11908)
- qwalphaqw.exe (PID: 9184)
- 691d9b712d.exe (PID: 9056)
- voodyy.exe (PID: 8768)
- RuntimeBroker.exe (PID: 9092)
- chcp.com (PID: 9008)
- MSBuild.exe (PID: 9068)
- RuntimeBroker.exe (PID: 10220)
- D87N7LBIJLVVU4R0MH.exe (PID: 8292)
- chcp.com (PID: 7424)
- tktVLbc.exe (PID: 7872)
- Tu_Inspector32.exe (PID: 9572)
- Tu_Inspector32.exe (PID: 9828)
- tktVLbc.tmp (PID: 7496)
- svchost.exe (PID: 11372)
- dumer.exe (PID: 11816)
- sFFG7Wg.exe (PID: 11412)
Process checks computer location settings
- 4363463463464363463463463.exe (PID: 3672)
- jd124.exe (PID: 7004)
- x210.exe (PID: 1156)
- windows.exe (PID: 6420)
- JUpdate.exe (PID: 1212)
- LukeJazz.exe (PID: 6700)
- svchost.exe (PID: 4040)
- ShellExperienceHost.exe (PID: 4580)
- Dark_Brout_ncrypt.exe (PID: 7076)
- RuntimeBroker.exe (PID: 7344)
- RuntimeBroker.exe (PID: 7152)
- RuntimeBroker.exe (PID: 5288)
- RuntimeBroker.exe (PID: 4808)
- RuntimeBroker.exe (PID: 8256)
- RuntimeBroker.exe (PID: 9512)
- RuntimeBroker.exe (PID: 10432)
- RuntimeBroker.exe (PID: 10864)
- svchocl.exe (PID: 10356)
- RuntimeBroker.exe (PID: 2292)
- RuntimeBroker.exe (PID: 12216)
- RuntimeBroker.exe (PID: 10352)
- random.exe (PID: 11004)
- RuntimeBroker.exe (PID: 2140)
- dumer.exe (PID: 6304)
- RuntimeBroker.exe (PID: 9092)
- RuntimeBroker.exe (PID: 10220)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 3672)
- MSBuild.exe (PID: 2272)
- TORRENTOLD-1.exe (PID: 6768)
- bryjf.exe (PID: 2124)
- slui.exe (PID: 4160)
- powershell.exe (PID: 7620)
- MSBuild.exe (PID: 7460)
- RegSvcs.exe (PID: 7764)
- KKMAgent.exe (PID: 8672)
- WerFault.exe (PID: 7588)
- powershell.exe (PID: 9524)
- %E5%9B%9B%E6%96%B9%E5%B9%B3%E5%8F%B0-%E5%8D%A1%E5%95%86%E7%AB%AF.exe (PID: 6268)
- MSBuild.exe (PID: 10424)
- ec5013ad46.exe (PID: 6496)
- MSBuild.exe (PID: 9068)
- sFFG7Wg.exe (PID: 11412)
The sample compiled with english language support
- 4363463463464363463463463.exe (PID: 3672)
- x210.exe (PID: 1156)
- Ul.pif (PID: 4216)
- Ul.pif (PID: 6348)
- Dark_Brout_ncrypt.exe (PID: 7076)
- RuntimeBroker.exe (PID: 7252)
- powershell.exe (PID: 7172)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7532)
- darts-wled.exe (PID: 7948)
- kkm.exe (PID: 9384)
- powershell.exe (PID: 3564)
- dumer.exe (PID: 6304)
- Tu_Inspector32.exe (PID: 9572)
- tktVLbc.tmp (PID: 7496)
Reads Environment values
- Sentil.exe (PID: 1056)
- Client1.exe (PID: 4512)
- svchost.exe (PID: 4040)
- Assiah.exe (PID: 6896)
- TempSpoofer.exe (PID: 5848)
- RuntimeBroker.exe (PID: 7252)
- Client-built.exe (PID: 7304)
- RuntimeBroker.exe (PID: 7344)
- installer.exe (PID: 7396)
- WindowsSecurityCheckWSC.secureapp.exe (PID: 7480)
- Client.exe (PID: 7740)
- RuntimeBroker.exe (PID: 7152)
- RuntimeBroker.exe (PID: 5288)
- Client-built2.exe (PID: 7728)
- Client.exe (PID: 7632)
- RuntimeBroker.exe (PID: 4808)
- identity_helper.exe (PID: 7360)
- RuntimeBroker.exe (PID: 8256)
- identity_helper.exe (PID: 9276)
- RuntimeBroker.exe (PID: 9512)
- RuntimeBroker.exe (PID: 10432)
- RuntimeBroker.exe (PID: 10864)
- RuntimeBroker.exe (PID: 2292)
- RuntimeBroker.exe (PID: 12216)
- Monotone.exe (PID: 8012)
- discord.exe (PID: 7648)
- Client.exe (PID: 9576)
- RuntimeBroker.exe (PID: 10352)
- RuntimeBroker.exe (PID: 2140)
- RuntimeBroker.exe (PID: 9092)
- RuntimeBroker.exe (PID: 10220)
Creates files or folders in the user directory
- Sentil.exe (PID: 1056)
- Fast%20Download.exe (PID: 4700)
- explorer.exe (PID: 4772)
- windows.exe (PID: 6420)
- Ul.pif (PID: 4216)
- svchost.exe (PID: 4040)
- Ul.pif (PID: 6348)
- ctfmon.exe (PID: 2804)
- RuntimeBroker.exe (PID: 7252)
- Client-built.exe (PID: 7304)
- installer.exe (PID: 7396)
- bmw_v1.7.exe (PID: 7300)
- explorer.exe (PID: 868)
- kkm.exe (PID: 9384)
- Assiah.exe (PID: 6896)
- KKMAgent.exe (PID: 8672)
- WerFault.exe (PID: 7588)
- Host.exe (PID: 9252)
- ceng.exe (PID: 7864)
- dumer.exe (PID: 6304)
- Hl2dm_Updater.exe (PID: 11908)
- Tu_Inspector32.exe (PID: 9828)
- sFFG7Wg.exe (PID: 11412)
Uses Task Scheduler to autorun other applications (AUTOMATE)
- Client1.exe (PID: 4512)
- cmd.exe (PID: 6148)
- Client.exe (PID: 7632)
The sample compiled with chinese language support
- 4363463463464363463463463.exe (PID: 3672)
- jd124.exe (PID: 7004)
- x210.exe (PID: 1156)
- HDDrive1095_XinAnPlug3030_20230619_inno.exe (PID: 32)
- kkm.exe (PID: 9384)
- dumer.exe (PID: 6304)
- Tu_Inspector32.exe (PID: 9828)
Create files in a temporary directory
- brbotnet.exe (PID: 1944)
- rarx210.exe (PID: 2732)
- windows.exe (PID: 6420)
- LukeJazz.exe (PID: 6700)
- bryjf.exe (PID: 2124)
- Ul.pif (PID: 6348)
- YHY_Setup.exe (PID: 4192)
- ctfmon.exe (PID: 1520)
- TempSpoofer.exe (PID: 5848)
- RuntimeBroker.exe (PID: 7344)
- powershell.exe (PID: 7620)
- RuntimeBroker.exe (PID: 7152)
- HDDrive1095_XinAnPlug3030_20230619_inno.exe (PID: 32)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7532)
- darts-wled.exe (PID: 7948)
- catee.exe (PID: 7772)
- RuntimeBroker.exe (PID: 5288)
- RuntimeBroker.exe (PID: 4808)
- RuntimeBroker.exe (PID: 8256)
- file.exe (PID: 8488)
- kkm.exe (PID: 9384)
- RuntimeBroker.exe (PID: 9512)
- RuntimeBroker.exe (PID: 10432)
- RuntimeBroker.exe (PID: 10864)
- RuntimeBroker.exe (PID: 2292)
- Monotone.exe (PID: 8012)
- RuntimeBroker.exe (PID: 12216)
- powershell.exe (PID: 9524)
- xsh.exe (PID: 10180)
- RuntimeBroker.exe (PID: 10352)
- random.exe (PID: 11004)
- RuntimeBroker.exe (PID: 2140)
- dumer.exe (PID: 6304)
- RuntimeBroker.exe (PID: 9092)
- ec5013ad46.exe (PID: 6496)
- RuntimeBroker.exe (PID: 10220)
- tktVLbc.tmp (PID: 7496)
- tktVLbc.exe (PID: 7872)
- Tu_Inspector32.exe (PID: 9828)
The sample compiled with korean language support
- 4363463463464363463463463.exe (PID: 3672)
Launching a file from the Startup directory
- Fast%20Download.exe (PID: 4700)
- cmd.exe (PID: 5008)
- svchost.exe (PID: 4040)
Creates files in the program directory
- mmc.exe (PID: 4132)
- Ul.pif (PID: 6348)
- Client-built2.exe (PID: 7728)
- Ganja3.exe (PID: 9460)
- Tu_Inspector32.exe (PID: 9572)
Creates a new folder
- cmd.exe (PID: 5644)
Reads mouse settings
- Ul.pif (PID: 4216)
- catee.exe (PID: 7772)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7156)
- powershell.exe (PID: 6376)
- powershell.exe (PID: 2160)
- powershell.exe (PID: 5724)
- powershell.exe (PID: 6700)
- powershell.exe (PID: 7172)
- powershell.exe (PID: 3564)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6376)
- powershell.exe (PID: 5724)
- powershell.exe (PID: 2160)
- powershell.exe (PID: 6700)
- powershell.exe (PID: 7172)
- powershell.exe (PID: 3564)
Launching a file from a Registry key
- svchost.exe (PID: 4040)
- Ul.pif (PID: 6348)
- ctfmon.exe (PID: 2804)
- Dark_Brout_ncrypt.exe (PID: 7076)
- msdcsc.exe (PID: 2716)
- explorer.exe (PID: 868)
- klass.exe (PID: 9480)
- kkm.exe (PID: 9384)
- KKMAgent.exe (PID: 8672)
- dumer.exe (PID: 6304)
Launching a file from Task Scheduler
- Ul.pif (PID: 6348)
The sample compiled with spanish language support
- 4363463463464363463463463.exe (PID: 3672)
- ctfmon.exe (PID: 2804)
NirSoft software is detected
- nircmd.exe (PID: 6876)
- PingInfoView.exe (PID: 9948)
Changes the display of characters in the console
- cmd.exe (PID: 7640)
- cmd.exe (PID: 7540)
- cmd.exe (PID: 6528)
- cmd.exe (PID: 7792)
- cmd.exe (PID: 8344)
- cmd.exe (PID: 9664)
- cmd.exe (PID: 10968)
- cmd.exe (PID: 7712)
- cmd.exe (PID: 11892)
- cmd.exe (PID: 10304)
- cmd.exe (PID: 9220)
- cmd.exe (PID: 8836)
- cmd.exe (PID: 9400)
- cmd.exe (PID: 10512)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7172)
- powershell.exe (PID: 3564)
.NET Reactor protector has been detected
- bryjf.exe (PID: 2124)
The executable file from the user directory is run by the Powershell process
- 4l5b2jwj.o5y0.exe (PID: 8152)
- gsav3omg.vaj0.exe (PID: 10112)
Application launched itself
- msedge.exe (PID: 8008)
- msedge.exe (PID: 7080)
- msedge.exe (PID: 7564)
- msedge.exe (PID: 8572)
FileZilla executable
- 4363463463464363463463463.exe (PID: 3672)
Process checks whether UAC notifications are on
- dumer.exe (PID: 6304)
- random.exe (PID: 11004)
- dumer.exe (PID: 11816)
Execution of CURL command
- cmd.exe (PID: 9396)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(2272) MSBuild.exe
C2 (11)korxddl.top/qidz
waxnps.live/aoqp
diecam.top/laur
citellcagt.top/gjtu
narrathfpt.top/tekq
https://t.me/vstalnasral555
peppinqikp.xyz/xaow
swenku.xyz/gaok
escczlv.top/bufi
localixbiw.top/zlpa
stochalyqp.xyz/alfp
Quasar
(PID) Process(4512) Client1.exe
Version1.4.1
C2 (2)73.62.14.5:4782
Sub_DirSubDir
Install_NameClient1.exe
Mutex3aaa11be-d135-4877-a61e-c409c29a7a60
StartupStartup
TagOffice04
LogDirLogs
SignatureEdBsB69NrhYROGjMirEw1pe15mwZjJy+fpGVF2aEbnAFOtUvB+inXlq8CBJsHyw2rIpTOfp4iJoePBYs9NdmFCd3gos2x+OqODgudinjtlJ3MQljnn0DPtxxorYuDf5VUKr0n15ASslFNr8Z6jDUIHZBaCbxs4uO8NaqMeStXJzf+YByrEcyZU6gOjyIIGfrpqBLqq1isNVIZONqJkRwLltRhrSgtDWEaDv4HiaDfFr2uEXgYvWN1iOqsoCHi9ioLMItlaTygAnKjrljjlADQAyWj/m8/7eKUkbRes7c3Axb...
CertificateMIIE9DCCAtygAwIBAgIQANfZS7y4agM8ac9WWr3FiTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MDYxMTE4MjE0MFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAivzXGPouAW3xLRhzxtOI9wrlH+Nk0QndGLi3B5yS0nGPq3CY6D/70xUT+I042LxX3VBF1fiU...
NjRat
(PID) Process(4700) Fast%20Download.exe
C2late-lil.at.ply.gg
Ports35022
BotnetCrash
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\Windows
Splitter|-F-|
Versionnull
XWorm
(PID) Process(5720) XClient.exe
C278.142.218.142:5353
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.6
MutexsDpdv2mpksLcLamH
(PID) Process(4040) svchost.exe
C2rates-north.gl.at.ply.gg,second-spyware.gl.at.ply.gg:51537
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.6
MutexgJvMWWdu1fLovptK
Formbook
(PID) Process(868) explorer.exe
C2www.cjc-nm.vip/tu90/
Strings (79)USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
ProgramFiles
CommonProgramFiles
ALLUSERSPROFILE
/c copy "
/c del "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\signons.sqlite
\Microsoft\Vault\
SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins
\Google\Chrome\User Data\Default\Login Data
SELECT origin_url, username_value, password_value FROM logins
.exe
.com
.scr
.pif
.cmd
.bat
ms
win
gdi
mfc
vga
igfx
user
help
config
update
regsvc
chkdsk
systray
audiodg
certmgr
autochk
taskhost
colorcpl
services
IconCache
ThumbCache
Cookies
SeDebugPrivilege
SeShutdownPrivilege
\BaseNamedObjects
config.php
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control: no-cache
Origin: http://
User-Agent: Mozilla Firefox/4.0
Content-Type: application/x-www-form-urlencoded
Accept: */*
Referer: http://
Accept-Language: en-US
Accept-Encoding: gzip, deflate
dat=
f-start
f-end
Decoy C2 (64)952734073.xyz
l2d35efae0yw1rvt9qefw8cfg.net
87445.pizza
idlersinduedinfeft.cloud
whichwe.live
100449.net
chinaclean.xyz
olding-beds-61261.bond
leadmagnetcpa.shop
video-games-97741.bond
marvelterbang.shop
video1.net
perfectdrishti.info
mantispms.net
matalan.jobs
greenblockventures.net
pagamentoseguroficial.pro
leadmagnetppc.shop
77578.shop
tdnimji.buzz
zainnova.shop
roofing-services-34072.bond
topisalpert.shop
cleaning-services-40215.bond
abandoned-houses-38551.bond
59hl.net
fromscratch.top
vincnakliye.xyz
cars-3549835.zone
setpink.life
soggilysootsstative.cloud
thinkhuman.net
estieaaa.xyz
sharelaunch.xyz
simplycandles.shop
ufalosdmsz.shop
influencer-marketing-61296.bond
newcarfi.info
oxvia.homes
cvkisegy.shop
pin-up-slot-fast.buzz
work-abroad-52523.bond
j2st.info
cataract-surgery-63955.bond
pl-oferta2759576.cfd
xinshengyou.xyz
rockystatue.shop
guidacorsa.corsica
jfdjn.autos
roofing-jobs-26086.bond
your-swsolutions.info
xzgdp.autos
0v3py92izrp23yy.xyz
aborteracciteadmetus.cloud
security-jobs-cl-3.today
marpiset.shop
fashionstore1999.shop
knapsackdisplay.shop
whuastp.info
wall-repair-10251.bond
frau-tonis-parfum.shop
binarybingenbiscay.cloud
yuuk1.click
parposaltguide.cyou
Rhadamanthys
(PID) Process(3652) fontdrvhost.exe
C2 (1)https://154.216.20.224:9773/a36090f1390c7cab81330/tauau3xb.nto48
AsyncRat
(PID) Process(6516) system.exe
C2 (1)tuna91.duckdns.org
Ports (1)1604
Version0.5.7B
BotnetSystem Program
Options
AutoRuntrue
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAKhExv8gmkFnvPeZ0hk8+zANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwODE2MTkyNTM3WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAIic+3NLTvw3b0gehT5806CFq2ShxEgQqWuI28vsBCLZ+NWjFPOLBrY1lRN5b/n8CypRPqxsQTll...
Server_SignatureZXHOnE08L81TusUZzv0Za4+/nIXSBcP6Nmv5fosfqTrMhy7mEpEzc7CAN89oOPiTaoU1MhykzWji7VIttu8Pq/LZlg82GncU6rUoNw16njz2r/SzkzCIc8yAx5h42OkdznCKQhQvH8890f+4s2UseUzBu5KJq7bvf59wGWmib9zUeWdB+PSLe7UgEFothE5gaNMKyBA1/7PrAQITZk5GED22tm7hHv8fR/0FLI3FWyC21YticBRx26Vy/JiCNk21i/Y/gReFcI3KQLNWo/oqFrJqwEg3T3G9Y7uukspWIjiB...
Keys
AES95482da6f1a6ef3f62f660597ff853b6340dfb716f65b1f7184105eaaf1c588d
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:06:26 21:31:52 |
| ZipCRC: | 0x31d44928 |
| ZipCompressedSize: | 4869 |
| ZipUncompressedSize: | 10752 |
| ZipFileName: | 4363463463464363463463463.exe.bin |
Total processes
663
Monitored processes
496
Malicious processes
82
Suspicious processes
34
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | "C:\Users\admin\Desktop\Files\HDDrive1095_XinAnPlug3030_20230619_inno.exe" | C:\Users\admin\Desktop\Files\HDDrive1095_XinAnPlug3030_20230619_inno.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Company: LNCA Company, Inc. Integrity Level: HIGH Description: 辽宁CA客户端 Exit code: 2 Version: 3.0.3.0 Modules
| |||||||||||||||
| 304 | cmd /c copy /b Avi + Hits + Joyce + Desk + Cheers + Cleanup + Generate + Hobbies + Possible + Rover + Notifications + Unique + Helpful + Constantly + Namibia + Revolution + Transfers + Index + Colors 437570\b | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 304 | "C:\Program Files (x86)\Internet Explorer\iexplore.exe" | C:\Program Files (x86)\Internet Explorer\iexplore.exe | — | msdcsc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | "C:\Users\admin\Desktop\Files\tomcat8.exe" | C:\Users\admin\Desktop\Files\tomcat8.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: Apache Software Foundation Integrity Level: HIGH Description: Commons Daemon Service Runner Exit code: 2 Version: 1.0.15.0 Modules
| |||||||||||||||
| 724 | timeout 3 | C:\Windows\SysWOW64\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 868 | "C:\Windows\SysWOW64\explorer.exe" | C:\Windows\SysWOW64\explorer.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
Formbook(PID) Process(868) explorer.exe C2www.cjc-nm.vip/tu90/ Strings (79)USERNAME LOCALAPPDATA USERPROFILE APPDATA TEMP ProgramFiles CommonProgramFiles ALLUSERSPROFILE /c copy " /c del " \Run \Policies \Explorer \Registry\User \Registry\Machine \SOFTWARE\Microsoft\Windows\CurrentVersion Office\15.0\Outlook\Profiles\Outlook\ NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\ \SOFTWARE\Mozilla\Mozilla \Mozilla Username: Password: formSubmitURL usernameField encryptedUsername encryptedPassword \logins.json \signons.sqlite \Microsoft\Vault\ SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins \Google\Chrome\User Data\Default\Login Data SELECT origin_url, username_value, password_value FROM logins .exe .com .scr .pif .cmd .bat ms win gdi mfc vga igfx user help config update regsvc chkdsk systray audiodg certmgr autochk taskhost colorcpl services IconCache ThumbCache Cookies SeDebugPrivilege SeShutdownPrivilege \BaseNamedObjects config.php POST HTTP/1.1 Host: Connection: close Content-Length: Cache-Control: no-cache Origin: http:// User-Agent: Mozilla Firefox/4.0 Content-Type: application/x-www-form-urlencoded Accept: */* Referer: http:// Accept-Language: en-US Accept-Encoding: gzip, deflate
dat= f-start f-end Decoy C2 (64)952734073.xyz l2d35efae0yw1rvt9qefw8cfg.net 87445.pizza idlersinduedinfeft.cloud whichwe.live 100449.net chinaclean.xyz olding-beds-61261.bond leadmagnetcpa.shop video-games-97741.bond marvelterbang.shop video1.net perfectdrishti.info mantispms.net matalan.jobs greenblockventures.net pagamentoseguroficial.pro leadmagnetppc.shop 77578.shop tdnimji.buzz zainnova.shop roofing-services-34072.bond topisalpert.shop cleaning-services-40215.bond abandoned-houses-38551.bond 59hl.net fromscratch.top vincnakliye.xyz cars-3549835.zone setpink.life soggilysootsstative.cloud thinkhuman.net estieaaa.xyz sharelaunch.xyz simplycandles.shop ufalosdmsz.shop influencer-marketing-61296.bond newcarfi.info oxvia.homes cvkisegy.shop pin-up-slot-fast.buzz work-abroad-52523.bond j2st.info cataract-surgery-63955.bond pl-oferta2759576.cfd xinshengyou.xyz rockystatue.shop guidacorsa.corsica jfdjn.autos roofing-jobs-26086.bond your-swsolutions.info xzgdp.autos 0v3py92izrp23yy.xyz aborteracciteadmetus.cloud security-jobs-cl-3.today marpiset.shop fashionstore1999.shop knapsackdisplay.shop whuastp.info wall-repair-10251.bond frau-tonis-parfum.shop binarybingenbiscay.cloud yuuk1.click parposaltguide.cyou | |||||||||||||||
| 892 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | mimilove.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | qwalphaqw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1056 | "C:\Users\admin\Desktop\Files\Sentil.exe" | C:\Users\admin\Desktop\Files\Sentil.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Quasar Client Exit code: 3 Version: 1.4.1 Modules
| |||||||||||||||
| 1128 | "C:\Windows\System32\cmd.exe" /k attrib "C:\Users\admin\Desktop\Files\Dark_Brout_ncrypt.exe" +s +h | C:\Windows\SysWOW64\cmd.exe | — | Dark_Brout_ncrypt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
191 846
Read events
190 632
Write events
1 049
Delete events
165
Modification events
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\4363463463464363463463463.exe.zip | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
258
Suspicious files
409
Text files
200
Unknown types
102
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4772 | explorer.exe | C:\Users\admin\Desktop\4363463463464363463463463.exe.bin | executable | |
MD5:2A94F3960C58C6E70826495F76D00B85 | SHA256:2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE | |||
| 4156 | QQHelper_1540.exe | C:\Users\admin\Desktop\Files\xml\JprrFGqH.uTMP | — | |
MD5:— | SHA256:— | |||
| 4156 | QQHelper_1540.exe | C:\Users\admin\Desktop\Files\xml\rGqzXyMQ.uTMP | — | |
MD5:— | SHA256:— | |||
| 4156 | QQHelper_1540.exe | C:\Users\admin\Desktop\Files\xml\CkJyuzaV.uTMP | — | |
MD5:— | SHA256:— | |||
| 4772 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 4772 | explorer.exe | C:\Users\admin\Desktop\4363463463464363463463463.exe | executable | |
MD5:2A94F3960C58C6E70826495F76D00B85 | SHA256:2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE | |||
| 3672 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\QQHelper_1540.exe | executable | |
MD5:5A39D66E2B925F7B7F9F39DE2F9C5FA0 | SHA256:4F91F9C5D3BAF612A1920AE8B2C49A1EE9850D018E308F8E65184A9046138658 | |||
| 4772 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:44DC1A51C8548D0DCEB2EDF29F448012 | SHA256:38B8AE66C578206D0A89F7A3DF37615CE8DA82BF00688B74C6DE2BD724EE87C4 | |||
| 3540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3540.41661\4363463463464363463463463.exe.bin | executable | |
MD5:2A94F3960C58C6E70826495F76D00B85 | SHA256:2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE | |||
| 4156 | QQHelper_1540.exe | C:\Users\admin\Desktop\Files\user.dat | binary | |
MD5:3B0F2D77E15BEB3B85E8EF752D6A3BD3 | SHA256:B171E283C6145ACF2B923098DBBC40FFC39B4F1DB0212928F9869747376C4AC8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
344
TCP/UDP connections
426
DNS requests
216
Threats
544
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2876 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6780 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3672 | 4363463463464363463463463.exe | GET | 301 | 140.82.112.4:80 | http://github.com/ff245185/payload/raw/refs/heads/main/Fast%20Download.exe | unknown | — | — | whitelisted |
4156 | QQHelper_1540.exe | POST | — | 116.255.160.63:80 | http://bakad.qqfarmer.com.cn/login.php?id=p&r=0.948763709748164 | unknown | — | — | unknown |
4156 | QQHelper_1540.exe | POST | 200 | 8.210.224.3:80 | http://ad.qqfarmer.com.cn/login.php?id=p&r=0.326204804237932 | unknown | — | — | unknown |
3672 | 4363463463464363463463463.exe | GET | 200 | 34.240.189.130:80 | http://sg123.net/files/update.exe | unknown | — | — | unknown |
4156 | QQHelper_1540.exe | POST | 200 | 8.210.224.3:80 | http://ad.qqfarmer.com.cn/login.php?id=v&r=0.695673126494512 | unknown | — | — | unknown |
4156 | QQHelper_1540.exe | POST | 200 | 8.210.224.3:80 | http://ad.qqfarmer.com.cn/login.php?id=n&r=0.573710783617571 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4916 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
1268 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2876 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2876 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
3672 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3672 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
3672 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
3672 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
— | — | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
— | — | Misc activity | ET HUNTING EXE Downloaded from Github |
— | — | Misc activity | ET INFO Packed Executable Download |
2272 | MSBuild.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
Process | Message |
|---|---|
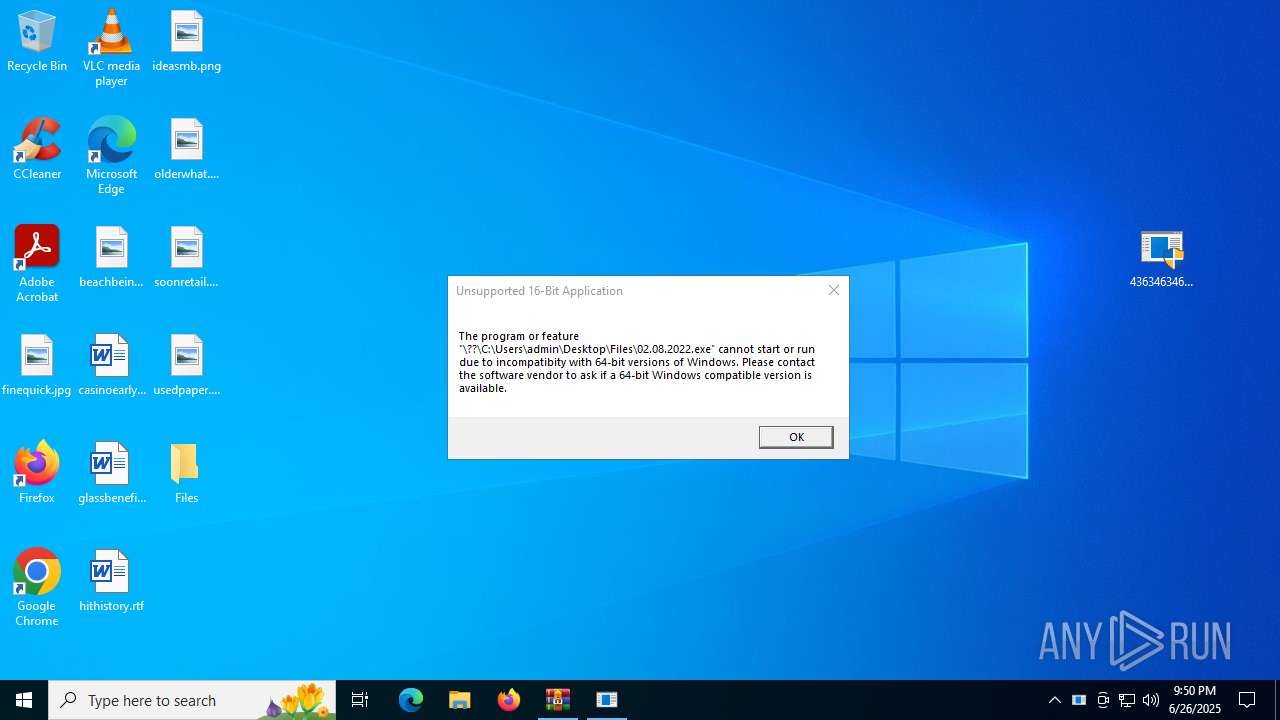
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
mmc.exe | "C:\WINDOWS\system32\compmgmt.msc" "C:\WINDOWS\system32\compmgmt.msc" |
mmc.exe | |
mmc.exe | ViewerAdminViewsPath = 'C:\ProgramData\Microsoft\Event Viewer\Views\ApplicationViewsRootNode': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerConfigPath = 'C:\ProgramData\Microsoft\Event Viewer': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerExternalLogsPath = 'C:\ProgramData\Microsoft\Event Viewer\ExternalLogs': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerViewsFolderPath = 'C:\ProgramData\Microsoft\Event Viewer\Views': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerExtension
|
Assiah.exe | Ready to work
|