| File name: | c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c |
| Full analysis: | https://app.any.run/tasks/e1d5223b-02c4-434d-b4f7-42f32b38f2cb |
| Verdict: | Malicious activity |
| Threats: | Gh0st RAT is a malware with advanced trojan functionality that enables attackers to establish full control over the victim’s system. The spying capabilities of Gh0st RAT made it a go-to tool for numerous criminal groups in high-profile attacks against government and corporate organizations. The most common vector of attack involving this malware begins with spam and phishing emails. |
| Analysis date: | December 13, 2024, 20:19:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | AD82832C1A32A2A9BB8244152A4A9F59 |
| SHA1: | 3D7BAE9027450B08C46615867FA17D4F9A17E530 |
| SHA256: | C3E64C8B17AA6B12E28392A1479C54C6268C973B71A06C01C1B8A702D339DD3C |
| SSDEEP: | 12288:urRK1SnVKdUkMaeCk5niB2pdWGhTskpP+cJPG1gktS4:urRwSVKdUk+Ck5iB2pdWGhNpWci7tS |
MALICIOUS
GH0ST has been detected (SURICATA)
- tbtool.exe (PID: 6092)
SUSPICIOUS
Executable content was dropped or overwritten
- c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe (PID: 4328)
Process drops legitimate windows executable
- c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe (PID: 4328)
The process drops C-runtime libraries
- c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe (PID: 4328)
Reads security settings of Internet Explorer
- c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe (PID: 4328)
Likely accesses (executes) a file from the Public directory
- tbtool.exe (PID: 4576)
- tbtool.exe (PID: 6092)
Contacting a server suspected of hosting an CnC
- tbtool.exe (PID: 6092)
Connects to unusual port
- tbtool.exe (PID: 6092)
INFO
Reads the computer name
- c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe (PID: 4328)
Checks supported languages
- c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe (PID: 4328)
- tbtool.exe (PID: 6092)
The sample compiled with english language support
- c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe (PID: 4328)
The sample compiled with chinese language support
- c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe (PID: 4328)
The process uses the downloaded file
- c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe (PID: 4328)
Process checks computer location settings
- c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe (PID: 4328)
Reads CPU info
- tbtool.exe (PID: 6092)
Sends debugging messages
- tbtool.exe (PID: 6092)
Manual execution by a user
- notepad.exe (PID: 2008)
- notepad.exe (PID: 4128)
- notepad.exe (PID: 1804)
- notepad.exe (PID: 2928)
- notepad.exe (PID: 5640)
- notepad.exe (PID: 2144)
- OpenWith.exe (PID: 4244)
Reads security settings of Internet Explorer
- notepad.exe (PID: 2008)
- notepad.exe (PID: 2928)
- notepad.exe (PID: 2144)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (52.5) |
|---|---|---|
| .scr | | | Windows screen saver (22) |
| .dll | | | Win32 Dynamic Link Library (generic) (11) |
| .exe | | | Win32 Executable (generic) (7.5) |
| .exe | | | Generic Win/DOS Executable (3.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:11:28 10:38:52+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 413696 |
| InitializedDataSize: | 221184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x13d65 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
127
Monitored processes
11
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1804 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\opencv license.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
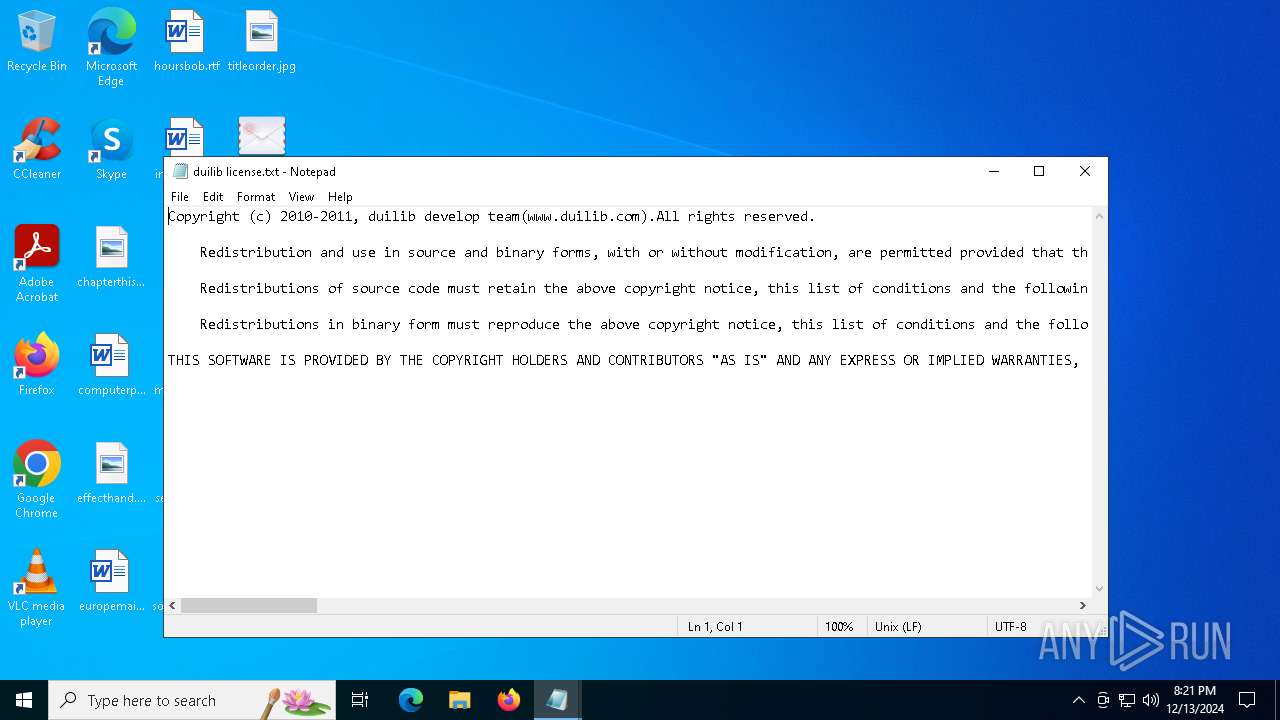
| 2008 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\duilib license.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2144 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Config.ini | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
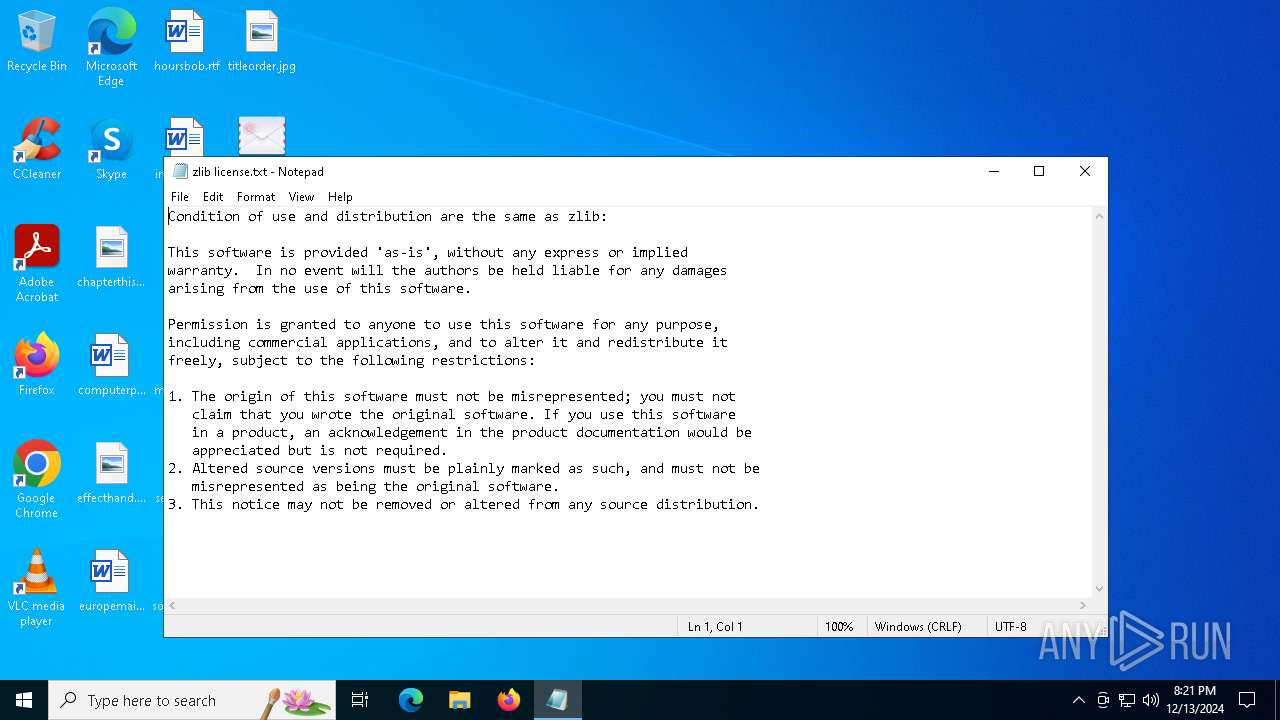
| 2928 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\zlib license.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
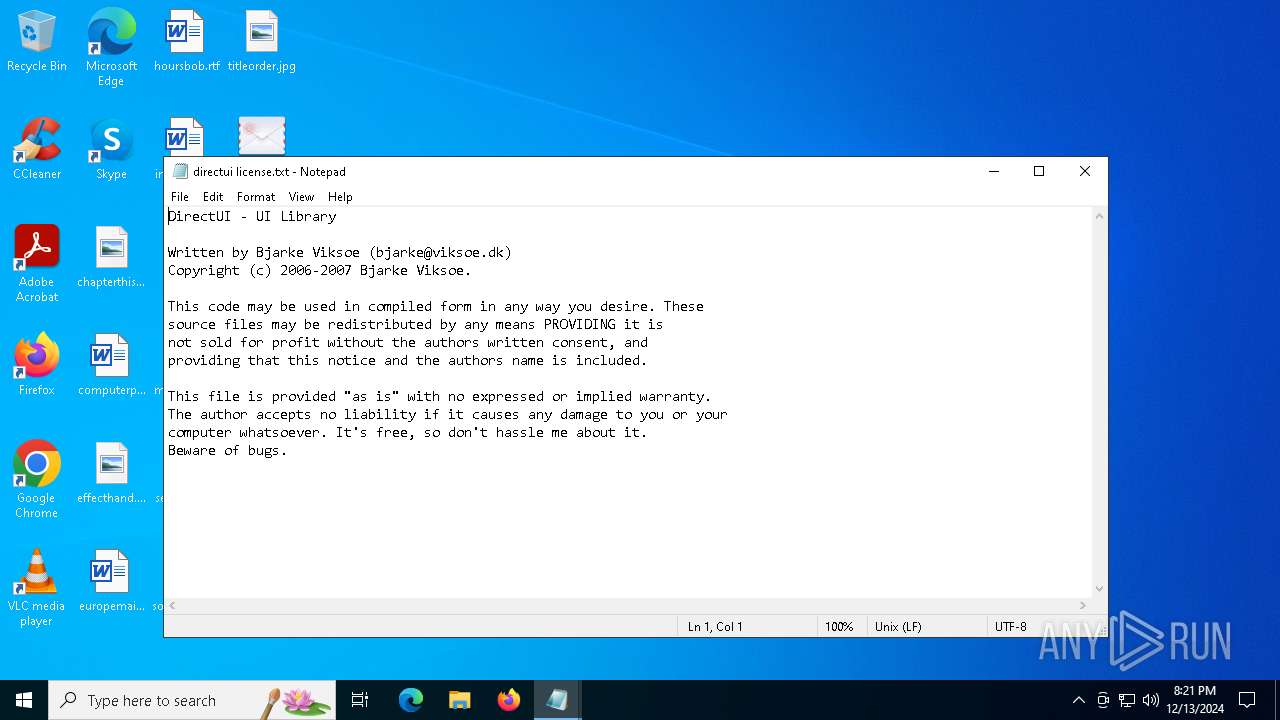
| 4128 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\directui license.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4244 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\task.dat | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4328 | "C:\Users\admin\Desktop\c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe" | C:\Users\admin\Desktop\c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4576 | "C:\Users\Public\lsb_release\tbtool.exe" | C:\Users\Public\lsb_release\tbtool.exe | — | c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe | |||||||||||
User: admin Company: 巧课教育科技(深圳)有限公司 Integrity Level: MEDIUM Description: 巧课客户端 Exit code: 3221226540 Version: 2.0.0.0 Modules
| |||||||||||||||
| 5640 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\duilib license troy.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 414
Read events
2 414
Write events
0
Delete events
0
Modification events
Executable files
44
Suspicious files
2
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4328 | c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe | C:\Users\Public\Downloads\7696.xml | — | |
MD5:— | SHA256:— | |||
| 4328 | c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe | C:\Users\Public\lsb_release\0f40fc17.ppf | fli | |
MD5:D02D246642A3047D48B99DB0D562BA7D | SHA256:3E3CCEDBEBD4EECAFE953AB6B87BAA594210D1528F5E074C8EBA571355363BC4 | |||
| 4328 | c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe | C:\Users\Public\lsb_release\api-ms-win-core-processthreads-l1-1-1.dll | executable | |
MD5:95C5B49AF7F2C7D3CD0BC14B1E9EFACB | SHA256:FF9B51AFF7FBEC8D7FE5CC478B12492A59B38B068DC2B518324173BB3179A0E1 | |||
| 4328 | c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe | C:\Users\Public\lsb_release\api-ms-win-core-synch-l1-2-0.dll | executable | |
MD5:6E704280D632C2F8F2CADEFCAE25AD85 | SHA256:758A2F9EF6908B51745DB50D89610FE1DE921D93B2DBEA919BFDBA813D5D8893 | |||
| 4328 | c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe | C:\Users\Public\lsb_release\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:79EE4A2FCBE24E9A65106DE834CCDA4A | SHA256:9F7BDA59FAAFC8A455F98397A63A7F7D114EFC4E8A41808C791256EBF33C7613 | |||
| 4328 | c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe | C:\Users\Public\lsb_release\api-ms-win-crt-time-l1-1-0.dll | executable | |
MD5:9B79FDA359A269C63DCAC69B2C81CAA4 | SHA256:4D0F0EA6E8478132892F9E674E27E2BC346622FC8989C704E5B2299A18C1D138 | |||
| 4328 | c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe | C:\Users\Public\lsb_release\api-ms-win-crt-heap-l1-1-0.dll | executable | |
MD5:1776A2B85378B27825CF5E5A3A132D9A | SHA256:675B1B82DD485CC8C8A099272DB9241D0D2A7F45424901F35231B79186EC47EE | |||
| 4328 | c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe | C:\Users\Public\lsb_release\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:3F224766FE9B090333FDB43D5A22F9EA | SHA256:AE5E73416EB64BC18249ACE99F6847024ECEEA7CE9C343696C84196460F3A357 | |||
| 4328 | c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe | C:\Users\Public\lsb_release\api-ms-win-core-localization-l1-2-0.dll | executable | |
MD5:23BD405A6CFD1E38C74C5150EEC28D0A | SHA256:A7FA48DE6C06666B80184AFEE7E544C258E0FB11399AB3FE47D4E74667779F41 | |||
| 4328 | c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe | C:\Users\Public\lsb_release\api-ms-win-crt-math-l1-1-0.dll | executable | |
MD5:8DA414C3524A869E5679C0678D1640C1 | SHA256:39723E61C98703034B264B97EE0FE12E696C6560483D799020F9847D8A952672 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
25
DNS requests
11
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4328 | c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe | GET | 200 | 27.124.47.7:80 | http://download.linuxroot.site/download/8358.dat | unknown | — | — | unknown |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2220 | svchost.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2220 | svchost.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6092 | tbtool.exe | GET | 200 | 142.250.186.36:80 | http://www.google.com/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2220 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.212.110.162:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4328 | c3e64c8b17aa6b12e28392a1479c54c6268c973b71a06c01c1b8a702d339dd3c.exe | 27.124.47.7:80 | download.linuxroot.site | BGPNET Global ASN | SG | unknown |
2220 | svchost.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2220 | svchost.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
download.linuxroot.site |
| unknown |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
book3.cookielive.top |
| unknown |
redhat.linuxroot.site |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
6092 | tbtool.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] Gh0stRAT TCP Packet |
Process | Message |
|---|---|
tbtool.exe | tbtool.exe |