| File name: | doomsday.jar |
| Full analysis: | https://app.any.run/tasks/868cf4d1-062b-49fe-b953-ab2b43b3a666 |
| Verdict: | Malicious activity |
| Threats: | Adwind RAT, sometimes also called Unrecom, Sockrat, Frutas, jRat, and JSocket, is a Malware As A Service Remote Access Trojan that attackers can use to collect information from infected machines. It was one of the most popular RATs in the market in 2015. |
| Analysis date: | January 14, 2024, 17:27:55 |
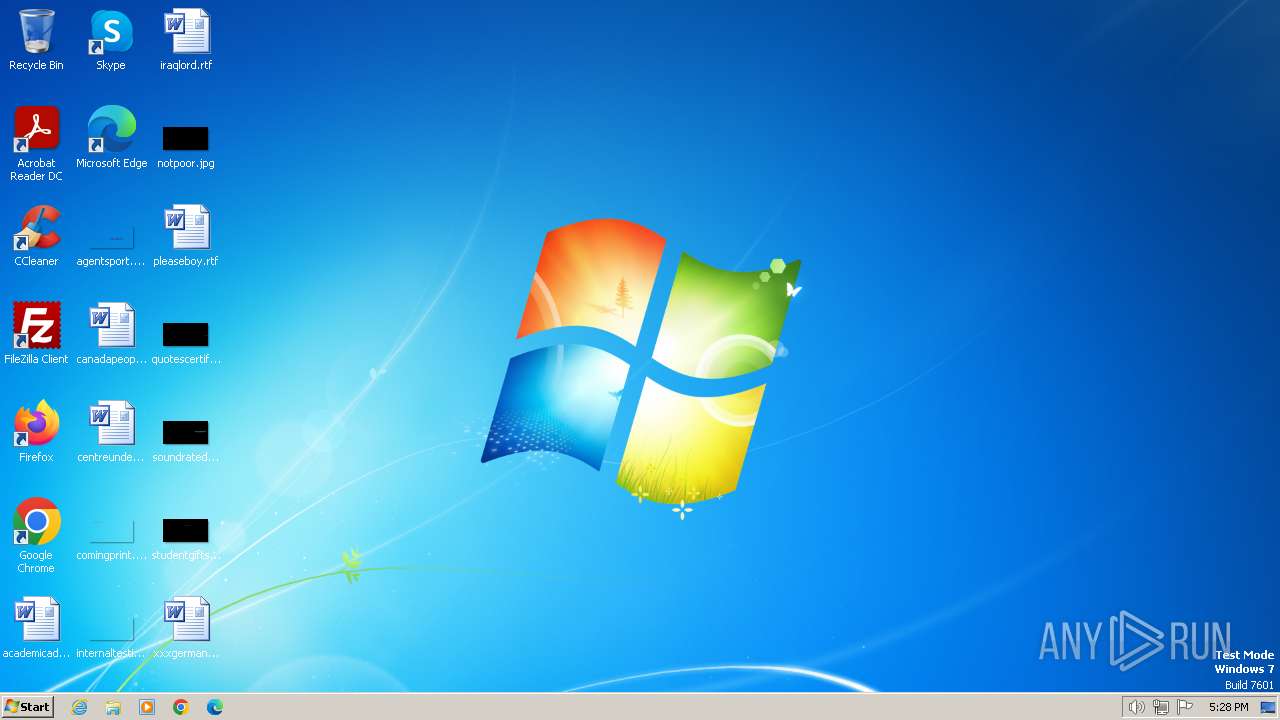
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 5CBF7B76ABF42F9A9EB5C12CC7172384 |
| SHA1: | 630236BFDB25308A874FEC8EF75901A54E712622 |
| SHA256: | C3CE5806756D8EE1CA30D4545BDE442834C8D4AC099894B61593D78384F66513 |
| SSDEEP: | 24576:SA5Ed0VXEV77zqBSItoYIOfLRgupDB7F+KWrbhx/WqQHp9S6PVYTR6ZLyi:SA5Ed0VXEV772BSItoYIOfLRgupDBB+y |
MALICIOUS
ADWIND has been detected (SURICATA)
- javaw.exe (PID: 2036)
Connects to the CnC server
- javaw.exe (PID: 2036)
SUSPICIOUS
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2408)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 2036)
Connects to unusual port
- javaw.exe (PID: 2036)
INFO
Checks supported languages
- javaw.exe (PID: 2036)
Create files in a temporary directory
- javaw.exe (PID: 2036)
Creates files in the program directory
- javaw.exe (PID: 2036)
Reads the computer name
- javaw.exe (PID: 2036)
Reads the machine GUID from the registry
- javaw.exe (PID: 2036)
Creates files or folders in the user directory
- javaw.exe (PID: 2036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jar | | | Java Archive (78.3) |
|---|---|---|
| .zip | | | ZIP compressed archive (21.6) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:01:14 18:19:12 |
| ZipCRC: | 0x1d0db350 |
| ZipCompressedSize: | 14362 |
| ZipUncompressedSize: | 35507 |
| ZipFileName: | IlIIlLllI/lllIlIlIlll/IIlllllIlIIl/lIlIlIIllI/IIllIllllIIlIIII.class |
Total processes
38
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2016 | REG ADD HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run /v Home /d "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe -jar C:\Users\admin\AppData\Roaming\Microsoft\.tmp\1705253284151.tmp" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2036 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\AppData\Local\Temp\doomsday.jar" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2408 | cmd.exe /c "REG ADD HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run /v Home /d "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe -jar C:\Users\admin\AppData\Roaming\Microsoft\.tmp\1705253284151.tmp" /f" | C:\Windows\System32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
860
Read events
860
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2036 | javaw.exe | C:\Users\admin\AppData\Roaming\Microsoft\.tmp\1705253284151.tmp | compressed | |
MD5:5CBF7B76ABF42F9A9EB5C12CC7172384 | SHA256:C3CE5806756D8EE1CA30D4545BDE442834C8D4AC099894B61593D78384F66513 | |||
| 2036 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:637756A416F105DCC4F37B06F4AB6CF9 | SHA256:CAB37396D11F6EB3DED9BD223BC3D71DD923329864655CEBE39D97B6891C6ADC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
2
Threats
4
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2036 | javaw.exe | 104.20.67.143:443 | pastebin.com | CLOUDFLARENET | — | unknown |
2036 | javaw.exe | 147.185.221.18:1253 | anti-pierce.gl.at.ply.gg | PLAYIT-GG | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| shared |
anti-pierce.gl.at.ply.gg |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO playit .gg Tunneling Domain in DNS Lookup |
3 ETPRO signatures available at the full report