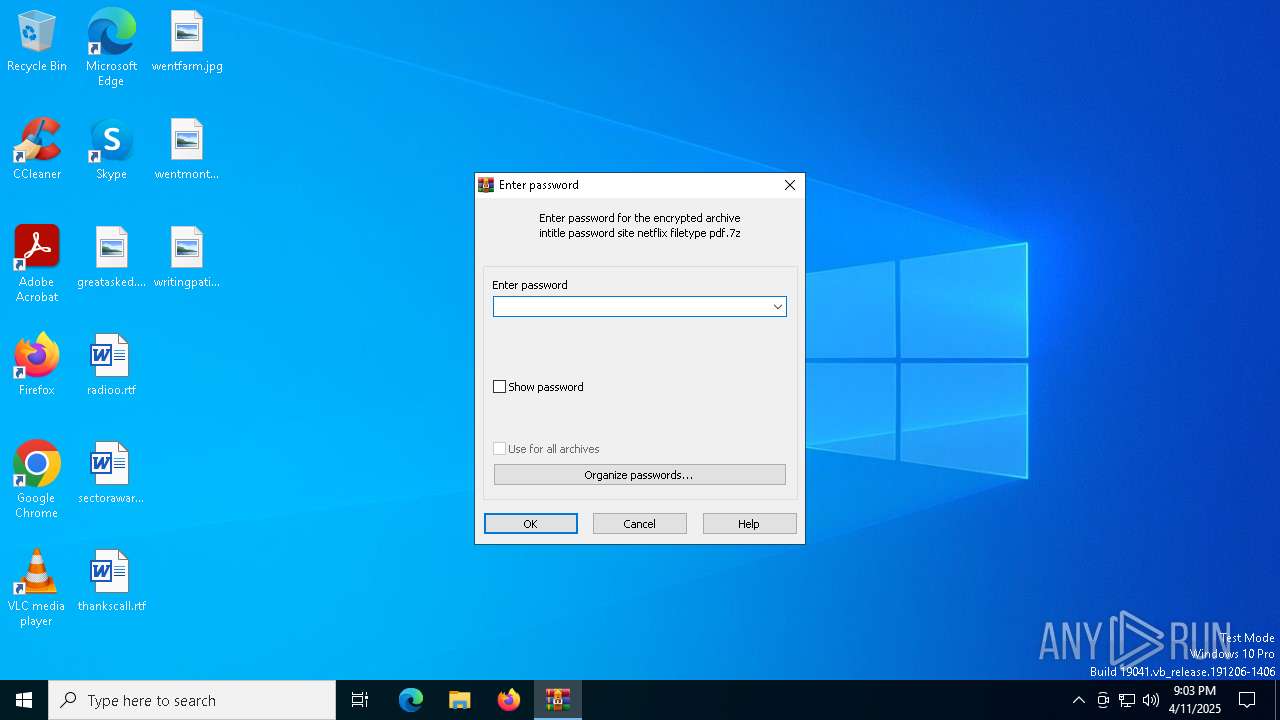
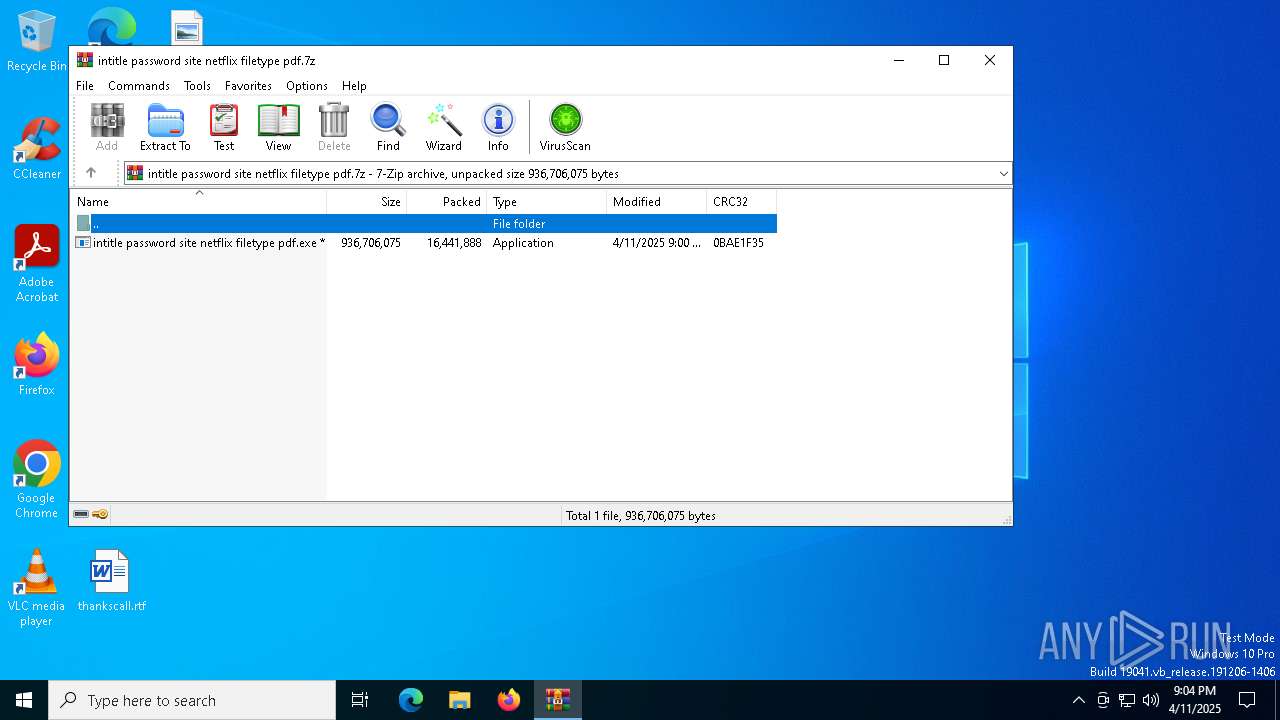
| File name: | intitle password site netflix filetype pdf.7z |
| Full analysis: | https://app.any.run/tasks/df2bdf9a-3fb6-4b80-ae5f-2b976be31b86 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | April 11, 2025, 21:03:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 3317340204A5527B3A94F4D8008C3CE3 |
| SHA1: | 133858758B775088CC44ED761BCD780348773D71 |
| SHA256: | C1D3D9809E40C834D24AB7BDBF0B805ABD39DB59CFD494488CA479E4C16FDDBA |
| SSDEEP: | 196608:jZW5VEYmksjjOGUDm40OTGUXobEmINHXP:j4EjjiDQOGUXobgP |
MALICIOUS
LUMMA mutex has been found
- Council.com (PID: 7036)
Actions looks like stealing of personal data
- Council.com (PID: 7036)
Steals credentials from Web Browsers
- Council.com (PID: 7036)
AutoIt loader has been detected (YARA)
- Council.com (PID: 7036)
AMADEY has been detected (SURICATA)
- tgvazx.exe (PID: 680)
Connects to the CnC server
- tgvazx.exe (PID: 680)
Run PowerShell with an invisible window
- powershell.exe (PID: 7100)
SUSPICIOUS
Reads security settings of Internet Explorer
- intitle password site netflix filetype pdf.exe (PID: 6392)
- 71YARTCUCXH40X7163Z9.exe (PID: 4560)
- tgvazx.exe (PID: 680)
Executing commands from a ".bat" file
- intitle password site netflix filetype pdf.exe (PID: 6392)
Starts CMD.EXE for commands execution
- intitle password site netflix filetype pdf.exe (PID: 6392)
- cmd.exe (PID: 4268)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4268)
Get information on the list of running processes
- cmd.exe (PID: 4268)
Application launched itself
- cmd.exe (PID: 4268)
The executable file from the user directory is run by the CMD process
- Council.com (PID: 7036)
There is functionality for taking screenshot (YARA)
- Council.com (PID: 7036)
- intitle password site netflix filetype pdf.exe (PID: 6392)
Potential Corporate Privacy Violation
- Council.com (PID: 7036)
- tgvazx.exe (PID: 680)
Process requests binary or script from the Internet
- Council.com (PID: 7036)
- tgvazx.exe (PID: 680)
Searches for installed software
- Council.com (PID: 7036)
Connects to the server without a host name
- Council.com (PID: 7036)
- tgvazx.exe (PID: 680)
- rundll32.exe (PID: 2772)
Executable content was dropped or overwritten
- 71YARTCUCXH40X7163Z9.exe (PID: 4560)
- Council.com (PID: 7036)
- tgvazx.exe (PID: 680)
Starts itself from another location
- 71YARTCUCXH40X7163Z9.exe (PID: 4560)
Starts POWERSHELL.EXE for commands execution
- 22WQHXJG2QPB34PPI95MU.exe (PID: 896)
The process executes via Task Scheduler
- tgvazx.exe (PID: 3020)
Connects to unusual port
- 22WQHXJG2QPB34PPI95MU.exe (PID: 896)
Contacting a server suspected of hosting an CnC
- tgvazx.exe (PID: 680)
Starts the AutoIt3 executable file
- cmd.exe (PID: 4268)
Starts application with an unusual extension
- cmd.exe (PID: 4268)
INFO
Create files in a temporary directory
- intitle password site netflix filetype pdf.exe (PID: 6392)
- extrac32.exe (PID: 5228)
- 71YARTCUCXH40X7163Z9.exe (PID: 4560)
- Council.com (PID: 7036)
Checks supported languages
- intitle password site netflix filetype pdf.exe (PID: 6392)
- extrac32.exe (PID: 5228)
- tgvazx.exe (PID: 680)
- 22WQHXJG2QPB34PPI95MU.exe (PID: 896)
- 71YARTCUCXH40X7163Z9.exe (PID: 4560)
- tgvazx.exe (PID: 3020)
- Council.com (PID: 7036)
Reads the computer name
- intitle password site netflix filetype pdf.exe (PID: 6392)
- extrac32.exe (PID: 5228)
- Council.com (PID: 7036)
- 71YARTCUCXH40X7163Z9.exe (PID: 4560)
- tgvazx.exe (PID: 680)
Manual execution by a user
- intitle password site netflix filetype pdf.exe (PID: 6392)
- WINWORD.EXE (PID: 6488)
Process checks computer location settings
- intitle password site netflix filetype pdf.exe (PID: 6392)
- 71YARTCUCXH40X7163Z9.exe (PID: 4560)
- tgvazx.exe (PID: 680)
Creates a new folder
- cmd.exe (PID: 208)
Reads the software policy settings
- Council.com (PID: 7036)
- slui.exe (PID: 1164)
- slui.exe (PID: 5600)
Reads mouse settings
- Council.com (PID: 7036)
Creates files or folders in the user directory
- 22WQHXJG2QPB34PPI95MU.exe (PID: 896)
- tgvazx.exe (PID: 680)
Checks proxy server information
- slui.exe (PID: 5600)
- tgvazx.exe (PID: 680)
- rundll32.exe (PID: 2772)
Changes the registry key values via Powershell
- 22WQHXJG2QPB34PPI95MU.exe (PID: 896)
Drops encrypted JS script (Microsoft Script Encoder)
- 22WQHXJG2QPB34PPI95MU.exe (PID: 896)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 2772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
163
Monitored processes
27
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | cmd /c md 646867 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Users\admin\AppData\Local\Temp\90876749ec\tgvazx.exe" | C:\Users\admin\AppData\Local\Temp\90876749ec\tgvazx.exe | 71YARTCUCXH40X7163Z9.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 896 | "C:\Users\admin\AppData\Local\Temp\22WQHXJG2QPB34PPI95MU.exe" | C:\Users\admin\AppData\Local\Temp\22WQHXJG2QPB34PPI95MU.exe | Council.com | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1164 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | "C:\Windows\System32\rundll32.exe" C:\Users\admin\AppData\Roaming\8de4e43376be4f\clip64.dll, Main | C:\Windows\SysWOW64\rundll32.exe | tgvazx.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3020 | "C:\Users\admin\AppData\Local\Temp\90876749ec\tgvazx.exe" | C:\Users\admin\AppData\Local\Temp\90876749ec\tgvazx.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3896 | findstr /V "STEEL" Softball | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4268 | "C:\WINDOWS\System32\cmd.exe" /c copy Circles.wbk Circles.wbk.bat & Circles.wbk.bat | C:\Windows\SysWOW64\cmd.exe | — | intitle password site netflix filetype pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 253
Read events
17 954
Write events
275
Delete events
24
Modification events
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\intitle password site netflix filetype pdf.7z | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
6
Suspicious files
51
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5364.26942\intitle password site netflix filetype pdf.exe | — | |
MD5:— | SHA256:— | |||
| 6392 | intitle password site netflix filetype pdf.exe | C:\Users\admin\AppData\Local\Temp\Digital.wbk | binary | |
MD5:D324AD203EBC06EB5C12D5091ED39F04 | SHA256:C561AAE89D6B53BE242317151A140AD06B27BD409598A99EBEE7FF440EE23372 | |||
| 6392 | intitle password site netflix filetype pdf.exe | C:\Users\admin\AppData\Local\Temp\Millions.wbk | binary | |
MD5:D6F3F678E1A2AA6B6FD199111F7B35F8 | SHA256:894527BF3E0AC9B464118DA4F9E0216FE117EC4A267CA8D4187E7BA0F2D8FD3F | |||
| 6392 | intitle password site netflix filetype pdf.exe | C:\Users\admin\AppData\Local\Temp\Governance.wbk | compressed | |
MD5:EBFC4BECD4FCA3D174E745B09AD519AA | SHA256:DA2A07466924938E72DA1DC3E4F9ABBD1018AC4B5FC548D803A009E841021875 | |||
| 6392 | intitle password site netflix filetype pdf.exe | C:\Users\admin\AppData\Local\Temp\Circles.wbk | text | |
MD5:8287AA6E639598557F27C0A107EE922A | SHA256:B93F322980DDCC9F695C92EF8C863E5DC3E88238D5E2DF98231D003047458517 | |||
| 6392 | intitle password site netflix filetype pdf.exe | C:\Users\admin\AppData\Local\Temp\Repeat.wbk | binary | |
MD5:3597CB5A9FF49EAD43749EA6B3BB9DA2 | SHA256:981AA130B1FEC736354E08C9DD27BC86D7A26BE12F032448196C503D7EB2993F | |||
| 5228 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Wit | binary | |
MD5:74F05A1533C8788740FB86E05FC5481D | SHA256:C87916BD7EE6D4A2FD750DED92B6F47F31FC72A4D088F14D839E35C4A18D28C3 | |||
| 5228 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Softball | binary | |
MD5:91D1A7BC164B5C1460D8F28E1D4CB2BE | SHA256:DC008D9176BBFD1377DE6B64D8A544297B66F4AB8019BE61CAAA445A8EBA6C41 | |||
| 5228 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Loop | binary | |
MD5:A72EECF058FBE46220DD4B12F1BAAD0D | SHA256:72A68384F0604CA3FCC8549CCEFAF0022761EF522C110790B8F4F783704FCBF0 | |||
| 5228 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Corporation | binary | |
MD5:E0F195E1CA24C4CC301FF9BFB3B1990B | SHA256:370688E9889B26387904456C3F2044DDB56FAB5642A354809E6FE1C19A3AEB45 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
49
DNS requests
29
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5428 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5428 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7036 | Council.com | GET | 200 | 195.82.146.34:80 | http://195.82.146.34/888.exe | unknown | — | — | unknown |
6488 | WINWORD.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7036 | Council.com | GET | 200 | 195.82.146.34:80 | http://195.82.146.34/AMA.exe | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6488 | WINWORD.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5352 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
680 | tgvazx.exe | POST | 200 | 195.82.147.98:80 | http://195.82.147.98/0Bdh3sQpbD/index.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5428 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5428 | SIHClient.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5428 | SIHClient.exe | 52.165.164.15:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7036 | Council.com | 104.21.48.1:443 | brightplf.digital | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
FRwWOmoAYaanjLlyvULB.FRwWOmoAYaanjLlyvULB |
| unknown |
brightplf.digital |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7036 | Council.com | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7036 | Council.com | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7036 | Council.com | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
7036 | Council.com | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
7036 | Council.com | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
680 | tgvazx.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
680 | tgvazx.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
680 | tgvazx.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
680 | tgvazx.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
680 | tgvazx.exe | Misc activity | ET INFO Packed Executable Download |