| File name: | QuantumHacks v2.exe |
| Full analysis: | https://app.any.run/tasks/b577c544-9b43-492c-99c6-077d0a8e4c76 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 29, 2025, 01:58:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | AC2040D78A083A189723E1392A3428EE |
| SHA1: | AA8FE9D0108323673F8BA5D6043B3FA324A264CB |
| SHA256: | C1D24472DC3C469D7DBDA5CB07D46D22307C8D4F1118E498524E579F15EA9C35 |
| SSDEEP: | 98304:CbnKllghKmvuBPLIp0/o5Wt8COrAJEYk4ytWxuvQQWfgMnIhg4d25/aRh8WbsmvD:iPLXgQ |
MALICIOUS
LUMMA has been detected (YARA)
- calc.exe (PID: 1628)
LUMMA mutex has been found
- calc.exe (PID: 1628)
- calc.exe (PID: 5156)
Actions looks like stealing of personal data
- calc.exe (PID: 1628)
- calc.exe (PID: 5156)
SUSPICIOUS
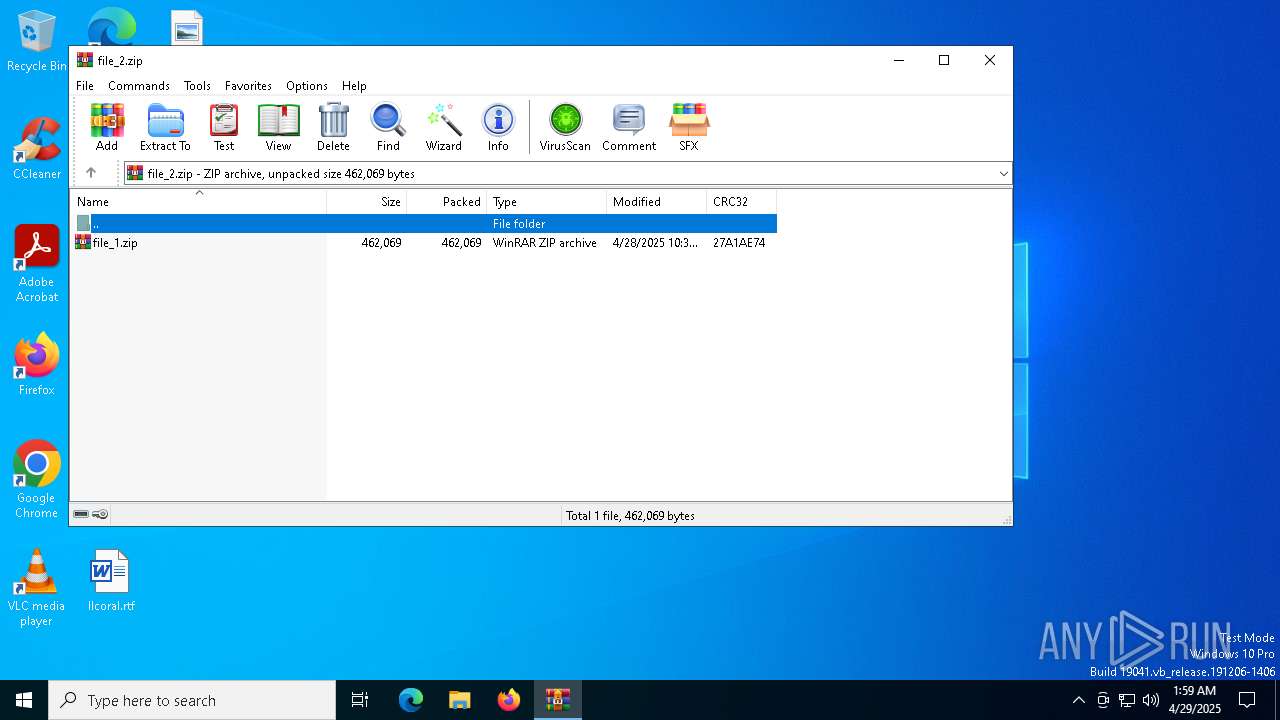
Drops 7-zip archiver for unpacking
- QuantumHacks v2.exe (PID: 4652)
Executable content was dropped or overwritten
- QuantumHacks v2.exe (PID: 4652)
- 7z.exe (PID: 1812)
- cmd.exe (PID: 4448)
Reads security settings of Internet Explorer
- QuantumHacks v2.exe (PID: 4652)
- WinRAR.exe (PID: 904)
Executing commands from a ".bat" file
- QuantumHacks v2.exe (PID: 4652)
Starts CMD.EXE for commands execution
- QuantumHacks v2.exe (PID: 4652)
The executable file from the user directory is run by the CMD process
- 7z.exe (PID: 2392)
- 7z.exe (PID: 5072)
- 7z.exe (PID: 2800)
- 7z.exe (PID: 1812)
- svchost64.exe (PID: 812)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 4448)
There is functionality for taking screenshot (YARA)
- QuantumHacks v2.exe (PID: 4652)
- calc.exe (PID: 1628)
Searches for installed software
- calc.exe (PID: 1628)
- calc.exe (PID: 5156)
INFO
Checks supported languages
- QuantumHacks v2.exe (PID: 4652)
- mode.com (PID: 3268)
- 7z.exe (PID: 2392)
- 7z.exe (PID: 5072)
- 7z.exe (PID: 2800)
- 7z.exe (PID: 1812)
- svchost64.exe (PID: 812)
- svchost64.exe (PID: 5056)
Create files in a temporary directory
- QuantumHacks v2.exe (PID: 4652)
- 7z.exe (PID: 2392)
- 7z.exe (PID: 5072)
- 7z.exe (PID: 2800)
- 7z.exe (PID: 1812)
The sample compiled with english language support
- QuantumHacks v2.exe (PID: 4652)
Reads the computer name
- QuantumHacks v2.exe (PID: 4652)
- 7z.exe (PID: 2392)
- 7z.exe (PID: 5072)
- 7z.exe (PID: 2800)
- 7z.exe (PID: 1812)
Process checks computer location settings
- QuantumHacks v2.exe (PID: 4652)
Starts MODE.COM to configure console settings
- mode.com (PID: 3268)
Reads the software policy settings
- calc.exe (PID: 1628)
- calc.exe (PID: 5156)
- slui.exe (PID: 516)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 1020)
Manual execution by a user
- OpenWith.exe (PID: 1020)
- WinRAR.exe (PID: 904)
- svchost64.exe (PID: 5056)
- WinRAR.exe (PID: 3332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(1628) calc.exe
C2 (9)mobitront.run/dsiu
parakehjet.run/kewk
buzzarddf.live/ktnt
zenithcorde.top/auid
bearjk.live/benj
techguidet.digital/apdo
techsyncq.run/riid
btcgeared.live/lbak
fishgh.digital/tequ
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:05:28 09:05:18+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 102400 |
| InitializedDataSize: | 38400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1945f |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.67.1.0 |
| ProductVersionNumber: | 3.67.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | FileZilla Project |
| LegalCopyright: | Copyright (C) 2006-2024 |
| OriginalFileName: | filezilla.exe |
| Comments: | Version 3.67.1 |
| FileVersion: | 3.67.1.0 |
| ProductName: | FileZilla |
| ProductVersion: | 3.67.1.0 |
| InternalName: | FileZilla 3 |
| FileDescription: | FileZilla FTP Client |
| Created: | 7z SFX Constructor v4.6.0.0 (http://usbtor.ru/viewtopic.php?t=798) |
| Builder: | ahileeeeeess 00:40:20 29/04/2025 |
Total processes
147
Monitored processes
20
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | "svchost64.exe" | C:\Users\admin\AppData\Local\Temp\main\svchost64.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 904 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\file_1.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
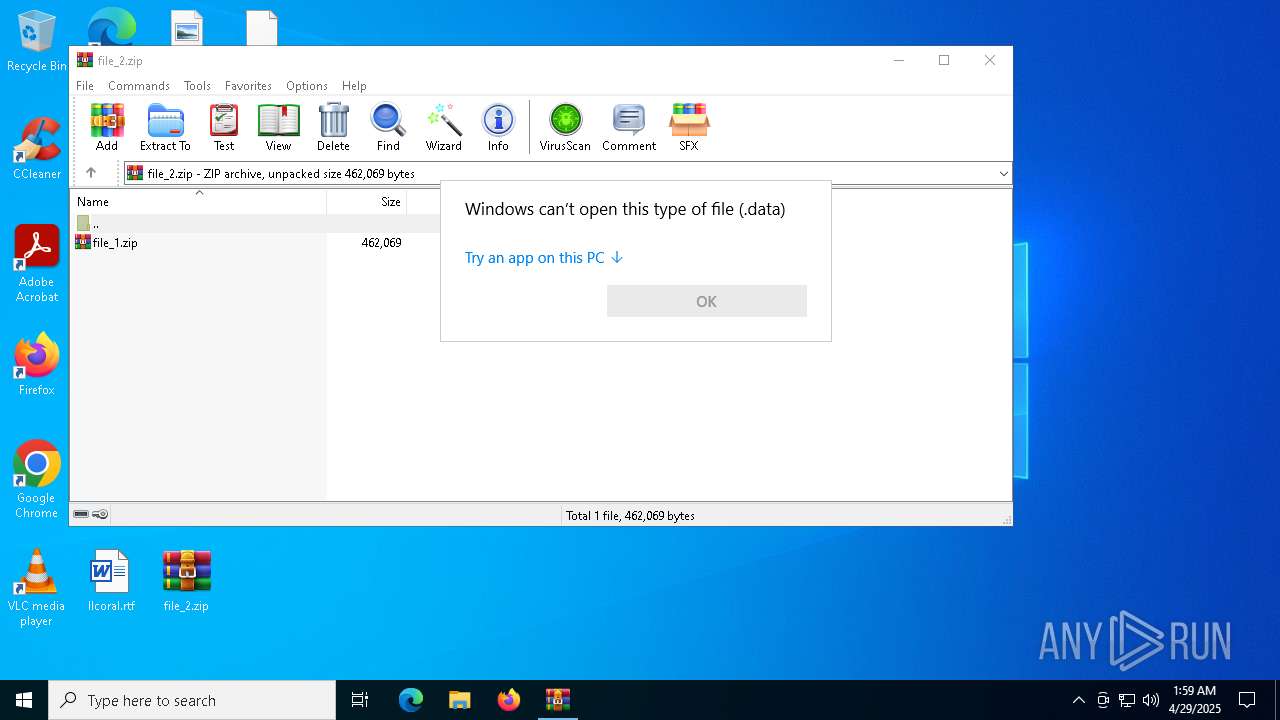
| 1020 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\AntiAV.data | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1628 | "C:\windows\syswow64\calc.exe" | C:\Windows\SysWOW64\calc.exe | svchost64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Calculator Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
Lumma(PID) Process(1628) calc.exe C2 (9)mobitront.run/dsiu parakehjet.run/kewk buzzarddf.live/ktnt zenithcorde.top/auid bearjk.live/benj techguidet.digital/apdo techsyncq.run/riid btcgeared.live/lbak fishgh.digital/tequ | |||||||||||||||
| 1812 | 7z.exe e extracted/file_1.zip -oextracted | C:\Users\admin\AppData\Local\Temp\main\7z.exe | cmd.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 0 Version: 19.00 Modules
| |||||||||||||||
| 2100 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2392 | 7z.exe e file.zip -p16966188608751287252160032340 -oextracted | C:\Users\admin\AppData\Local\Temp\main\7z.exe | — | cmd.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 0 Version: 19.00 Modules
| |||||||||||||||
| 2800 | 7z.exe e extracted/file_2.zip -oextracted | C:\Users\admin\AppData\Local\Temp\main\7z.exe | — | cmd.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 0 Version: 19.00 Modules
| |||||||||||||||
Total events
5 563
Read events
5 539
Write events
24
Delete events
0
Modification events
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\file_2.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (904) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
Executable files
4
Suspicious files
6
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5072 | 7z.exe | C:\Users\admin\AppData\Local\Temp\main\extracted\AntiAV.data | text | |
MD5:91281AB5814EDD87B7A77F3E754389AD | SHA256:51559F5FB63803D8D4FF81519FAD1E4BA4EAE18AC57976A1FD922702F879F040 | |||
| 4652 | QuantumHacks v2.exe | C:\Users\admin\AppData\Local\Temp\main\KillDuplicate.cmd | text | |
MD5:68CECDF24AA2FD011ECE466F00EF8450 | SHA256:64929489DC8A0D66EA95113D4E676368EDB576EA85D23564D53346B21C202770 | |||
| 4652 | QuantumHacks v2.exe | C:\Users\admin\AppData\Local\Temp\main\main.bat | text | |
MD5:AD15EC748259F4BD9686ABBBA5B29307 | SHA256:20D797B8D9D9F6C14C53DAE00B16397885E3DA8A9A95FA1CA5B34B79414C8944 | |||
| 4652 | QuantumHacks v2.exe | C:\Users\admin\AppData\Local\Temp\main\7z.dll | executable | |
MD5:72491C7B87A7C2DD350B727444F13BB4 | SHA256:34AD9BB80FE8BF28171E671228EB5B64A55CAA388C31CB8C0DF77C0136735891 | |||
| 4652 | QuantumHacks v2.exe | C:\Users\admin\AppData\Local\Temp\main\7z.exe | executable | |
MD5:619F7135621B50FD1900FF24AADE1524 | SHA256:344F076BB1211CB02ECA9E5ED2C0CE59BCF74CCBC749EC611538FA14ECB9AAD2 | |||
| 2392 | 7z.exe | C:\Users\admin\AppData\Local\Temp\main\extracted\file_3.zip | compressed | |
MD5:8AA480752BB572C28DD981096D85C8C8 | SHA256:6E706719F1472F6D96A8C675064E82AC75300940151ECE70E774734C0DCAED17 | |||
| 4652 | QuantumHacks v2.exe | C:\Users\admin\AppData\Local\Temp\main\file.bin | compressed | |
MD5:94E17ACF936E453C0CFE3B76420D7FCF | SHA256:6D501C1F888870561B450B6CEAC0ADF18050F52D012CEA1C4FE036916BACE9E3 | |||
| 4448 | cmd.exe | C:\Users\admin\AppData\Local\Temp\main\file.zip | compressed | |
MD5:94E17ACF936E453C0CFE3B76420D7FCF | SHA256:6D501C1F888870561B450B6CEAC0ADF18050F52D012CEA1C4FE036916BACE9E3 | |||
| 1812 | 7z.exe | C:\Users\admin\AppData\Local\Temp\main\extracted\svchost64.exe | executable | |
MD5:5E36978CE37CD85EE2DCFF0E330685EC | SHA256:7E5DD8554E22DCB9FEC7ACA7AAA6B5A61DC8B2A8C1E66B6A95CE99FC723F1CE1 | |||
| 2800 | 7z.exe | C:\Users\admin\AppData\Local\Temp\main\extracted\file_1.zip | compressed | |
MD5:CEA188BAA09A3AAEBD7A921F6632AD80 | SHA256:16B98F523CDF8A6AD515437329662E010AEB1807B86850D5B3BB4DAD32750DDB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
37
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5968 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5968 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1628 | calc.exe | 188.114.97.3:443 | mobitront.run | CLOUDFLARENET | NL | malicious |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
mobitront.run |
| malicious |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
zenithcorde.top |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |