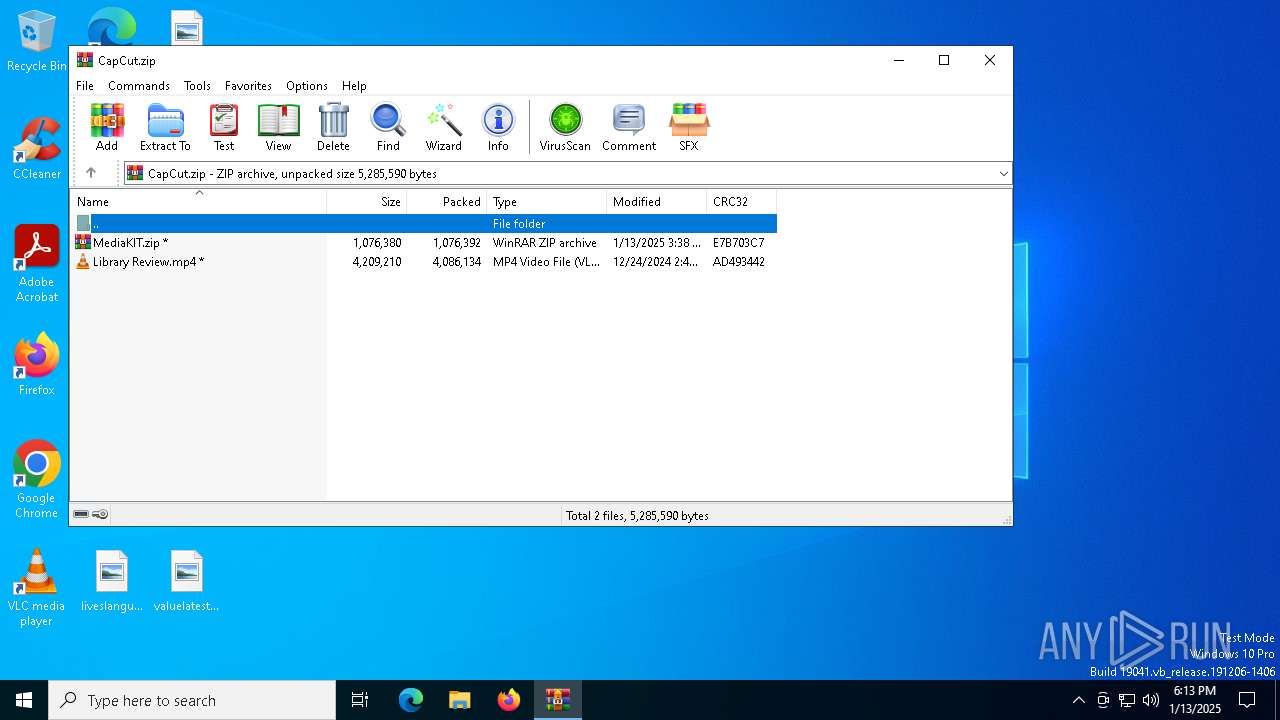
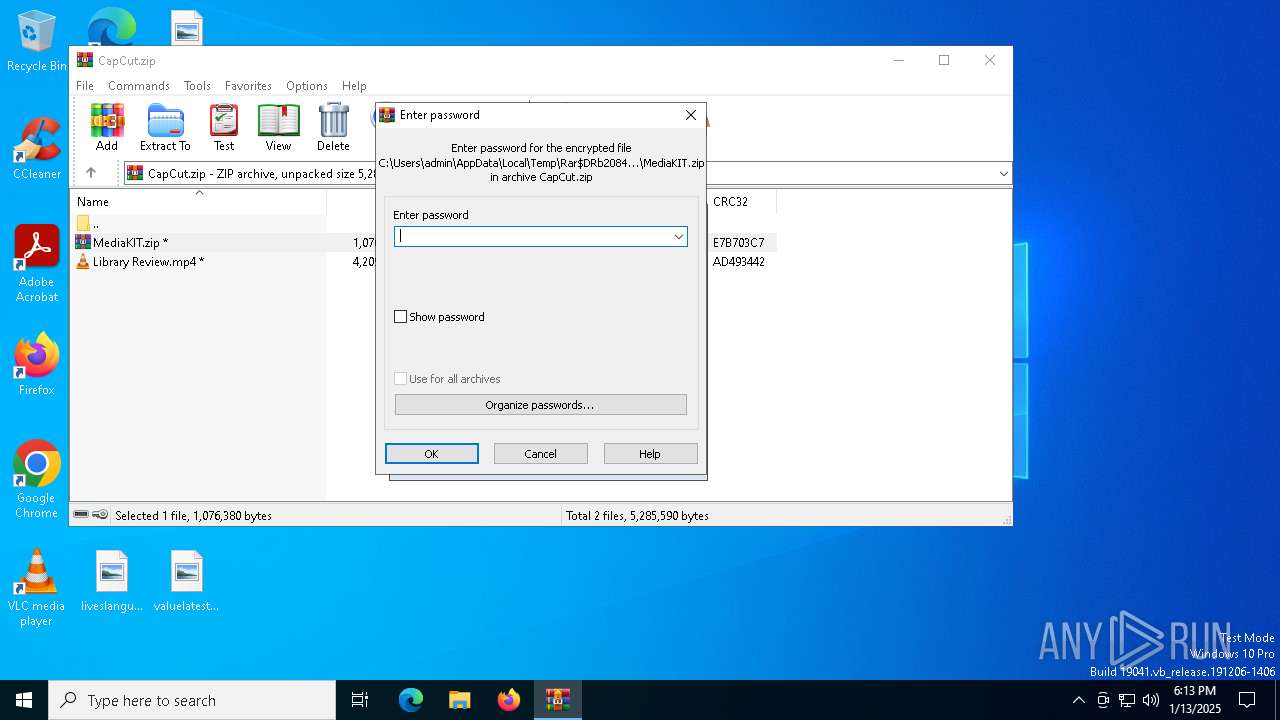
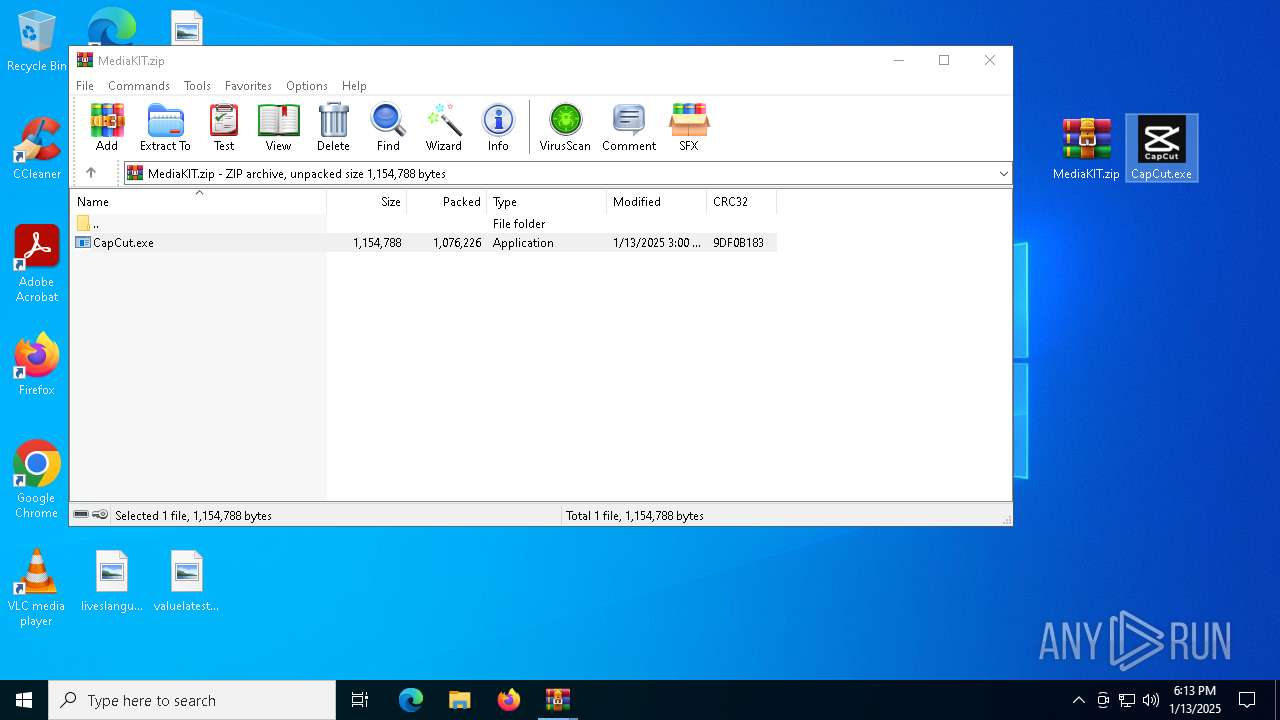
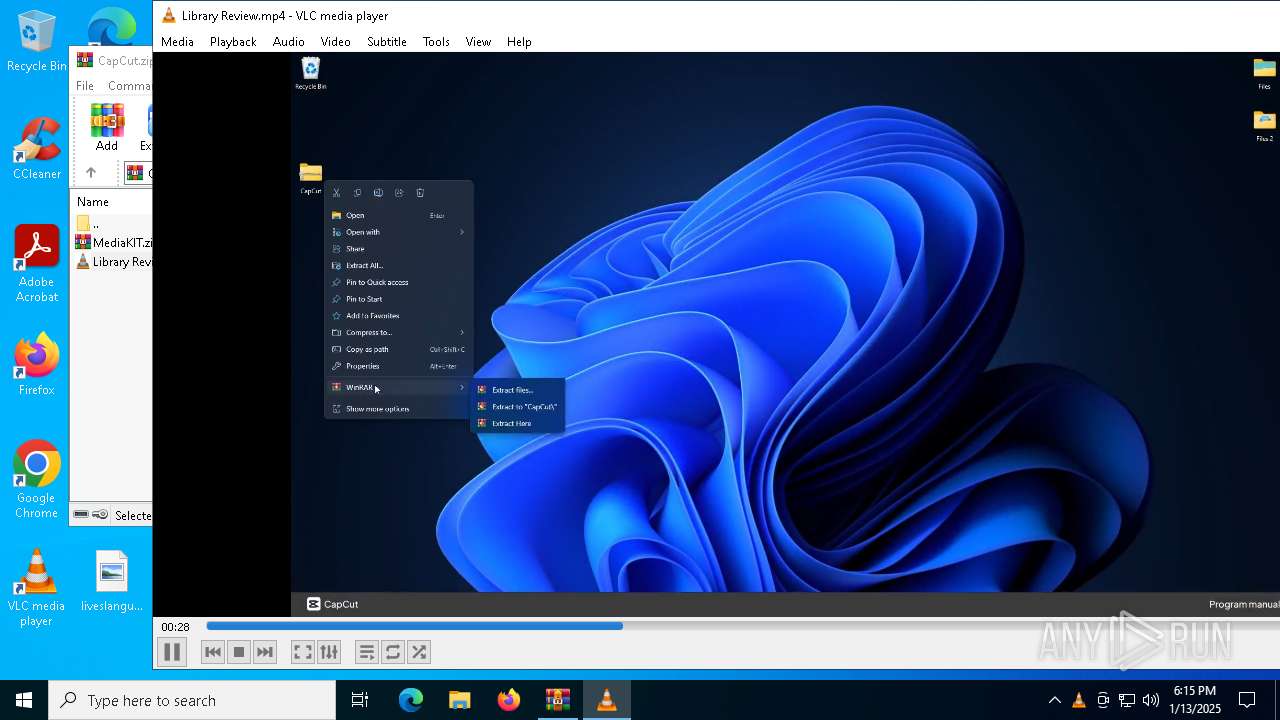
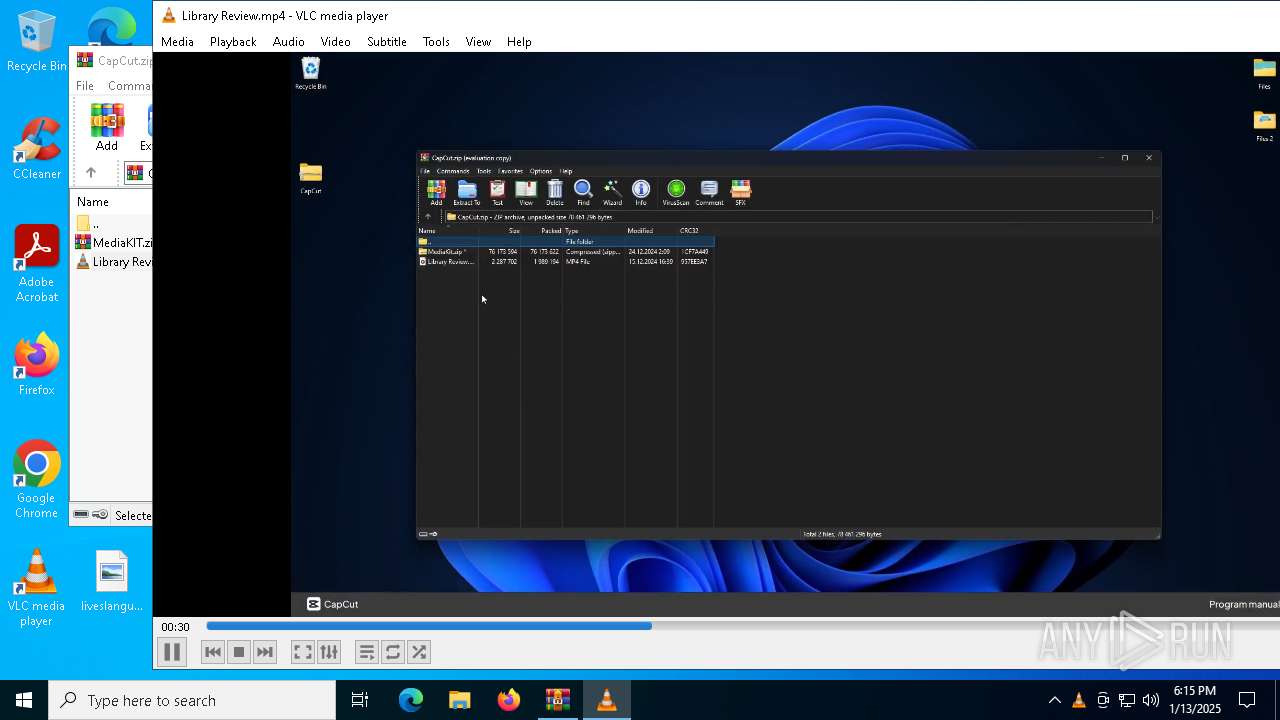
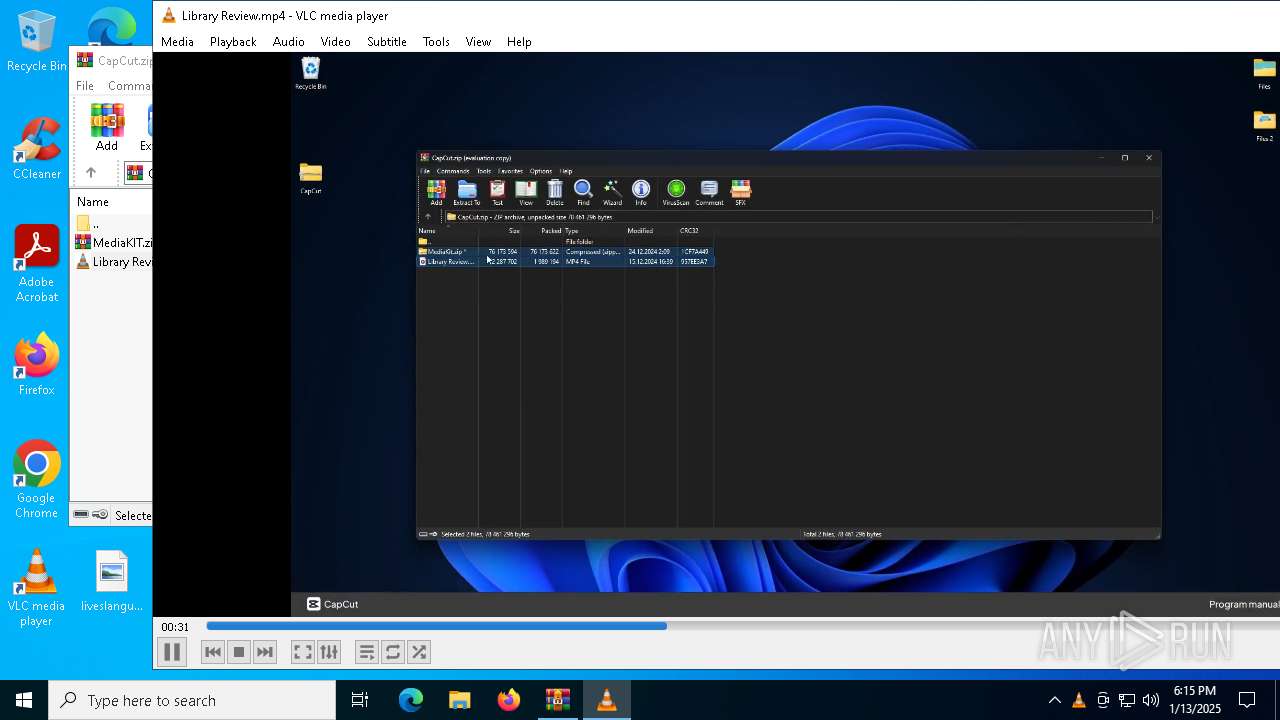
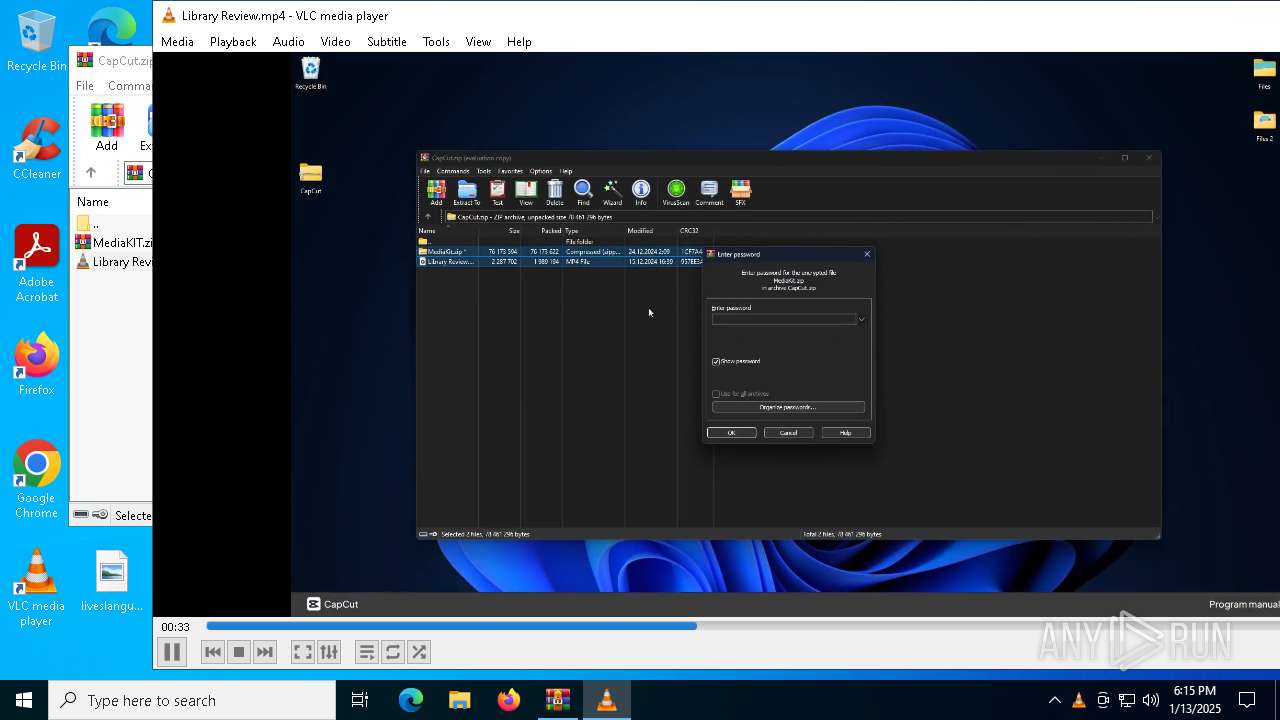
| File name: | CapCut.zip |
| Full analysis: | https://app.any.run/tasks/c0233e9b-2e77-4f62-a32b-13481d362fc8 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | January 13, 2025, 18:12:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 915A286BBC8B5C55F802FA2819D543C4 |
| SHA1: | 4043467D42520F01A5DE2A6D7A0FE3D26718BB54 |
| SHA256: | C1CD7D528046531A499272C377DA360B47C3535348AACA6101E231FB67B7512F |
| SSDEEP: | 98304:b48gq4jDdW1GEcsHhEGjpt+BY3BUQvwLZma6ekzJaeN9T6oBW/SeMFrvKfdR8GII:bDSrESrHbp |
MALICIOUS
Executing a file with an untrusted certificate
- CapCut.exe (PID: 488)
AutoIt loader has been detected (YARA)
- Functioning.com (PID: 6368)
LUMMA mutex has been found
- Functioning.com (PID: 6368)
Actions looks like stealing of personal data
- Functioning.com (PID: 6368)
SUSPICIOUS
Reads security settings of Internet Explorer
- CapCut.exe (PID: 488)
Starts CMD.EXE for commands execution
- CapCut.exe (PID: 488)
- cmd.exe (PID: 3816)
Executing commands from ".cmd" file
- CapCut.exe (PID: 488)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3816)
Application launched itself
- cmd.exe (PID: 3816)
Get information on the list of running processes
- cmd.exe (PID: 3816)
Starts the AutoIt3 executable file
- cmd.exe (PID: 3816)
The executable file from the user directory is run by the CMD process
- Functioning.com (PID: 6368)
Starts application with an unusual extension
- cmd.exe (PID: 3816)
There is functionality for taking screenshot (YARA)
- vlc.exe (PID: 6660)
INFO
Reads the computer name
- CapCut.exe (PID: 488)
- extrac32.exe (PID: 6260)
- Functioning.com (PID: 6368)
- vlc.exe (PID: 6660)
The process uses the downloaded file
- CapCut.exe (PID: 488)
- WinRAR.exe (PID: 1412)
Create files in a temporary directory
- CapCut.exe (PID: 488)
- extrac32.exe (PID: 6260)
Process checks computer location settings
- CapCut.exe (PID: 488)
Creates a new folder
- cmd.exe (PID: 6240)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1412)
Manual execution by a user
- CapCut.exe (PID: 488)
- WinRAR.exe (PID: 1412)
- vlc.exe (PID: 6660)
Checks supported languages
- CapCut.exe (PID: 488)
- Functioning.com (PID: 6368)
- vlc.exe (PID: 6660)
Reads the software policy settings
- Functioning.com (PID: 6368)
Sends debugging messages
- vlc.exe (PID: 6660)
The process uses Lua
- vlc.exe (PID: 6660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:12:24 06:45:52 |
| ZipCRC: | 0xad493442 |
| ZipCompressedSize: | 4086134 |
| ZipUncompressedSize: | 4209210 |
| ZipFileName: | Library Review.mp4 |
Total processes
133
Monitored processes
17
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 488 | "C:\Users\admin\Desktop\CapCut.exe" | C:\Users\admin\Desktop\CapCut.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1412 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\MediaKIT.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1944 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2084 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\CapCut.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3208 | findstr /I "opssvc wrsa" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3816 | "C:\Windows\System32\cmd.exe" /c move Delaware Delaware.cmd & Delaware.cmd | C:\Windows\SysWOW64\cmd.exe | — | CapCut.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4160 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6184 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6192 | findstr "AvastUI AVGUI bdservicehost nsWscSvc ekrn SophosHealth" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6240 | cmd /c md 342886 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 505
Read events
5 477
Write events
28
Delete events
0
Modification events
| (PID) Process: | (2084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CapCut.zip | |||
| (PID) Process: | (2084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
Executable files
3
Suspicious files
22
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 488 | CapCut.exe | C:\Users\admin\AppData\Local\Temp\Richmond | binary | |
MD5:B2FF505B11719F167A4C3B95E63E9446 | SHA256:E887905084448DABA7B58515F68178B647DFA9E4B2C4A21D786DA152DC2779C0 | |||
| 488 | CapCut.exe | C:\Users\admin\AppData\Local\Temp\Keno | binary | |
MD5:F7ABDBE7A90C44DDFD229D7F9C0DC2CF | SHA256:6E9AC75660485C9CDFE4C8CA149C8E3B2841E7FAA5D278DAC898E991BDB433A6 | |||
| 488 | CapCut.exe | C:\Users\admin\AppData\Local\Temp\Beijing | binary | |
MD5:2AD55F9760C40C71952B9941E633CE14 | SHA256:E2844FF6B62A4E72D7C67C6E2E35A9E50536B8B5C47EE672DBE492C336228DBF | |||
| 6260 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Route | binary | |
MD5:8F34FCB3591A4872E3B73F545607A437 | SHA256:1DC61A022619E753A0B7329DC5F510A53337D8559C2502C58726172ADA2B3345 | |||
| 3816 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Delaware.cmd | text | |
MD5:6D40EC9DF91EC554AF14C8E94462F11C | SHA256:1C3129FC5D82DB61EBDAD26C74F10CF0B9B2EC0C00588F816D779D2B24DEEC6D | |||
| 488 | CapCut.exe | C:\Users\admin\AppData\Local\Temp\Filed | binary | |
MD5:073B33B1B651D5F39196B5112A60618E | SHA256:6D4A1B4E7743B0FA88F1314F2A8D12659906595CDC8241032B69189B2355A41E | |||
| 6260 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Ministers | binary | |
MD5:0AEC8A199F0BC77C599E78D4085DF5DB | SHA256:432FF5FBEDBE812A1343445DBDEE9EC974BF5DB88C687BA4045F0DDC7337BDEC | |||
| 2084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2084.37903\Library Review.mp4 | — | |
MD5:— | SHA256:— | |||
| 488 | CapCut.exe | C:\Users\admin\AppData\Local\Temp\Delaware | text | |
MD5:6D40EC9DF91EC554AF14C8E94462F11C | SHA256:1C3129FC5D82DB61EBDAD26C74F10CF0B9B2EC0C00588F816D779D2B24DEEC6D | |||
| 488 | CapCut.exe | C:\Users\admin\AppData\Local\Temp\Speakers | compressed | |
MD5:284F2F0BA9CFBE1E10303A00FA4303AE | SHA256:E67D07027A222C161EE2582E300A6BE6ACAEB0A6A9D824E238C93A02326DD86C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
40
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1380 | svchost.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1380 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6448 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6448 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1380 | svchost.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1380 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 2.16.110.138:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=x86_64-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=x86_64-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x64/contrib/x86_64-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc debug: opening config file (C:\Users\admin\AppData\Roaming\vlc\vlcrc)
|