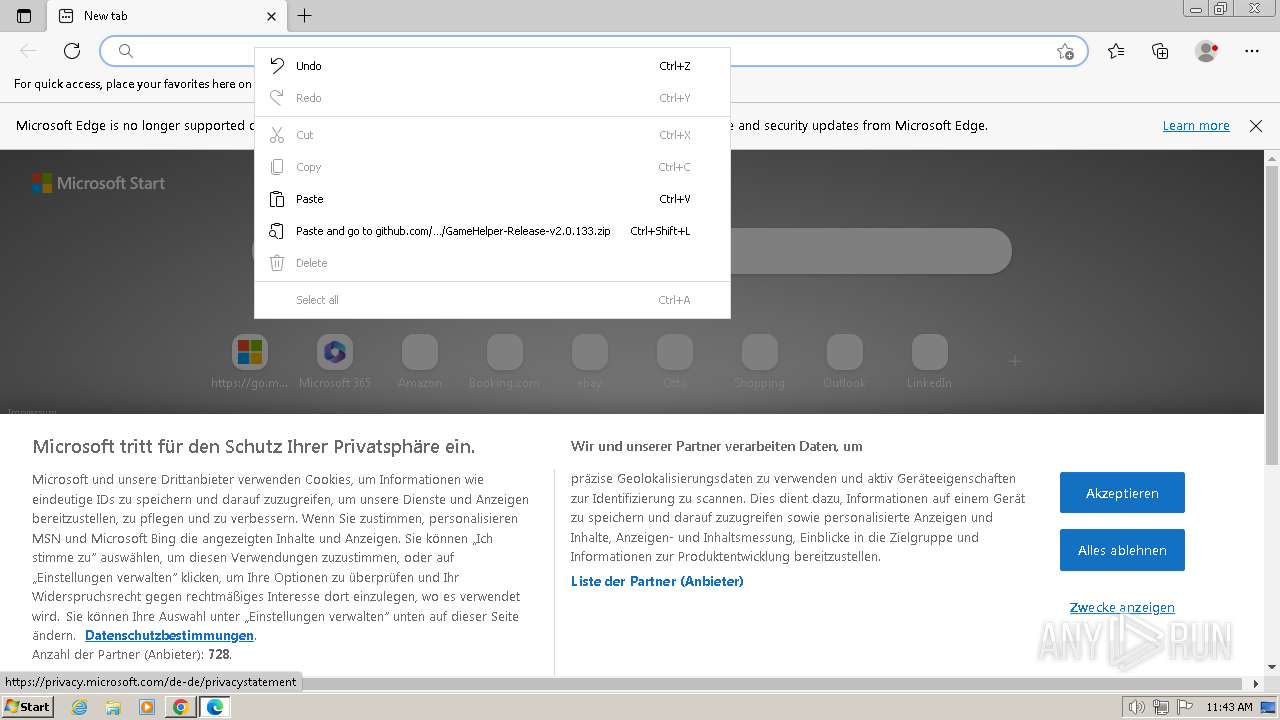
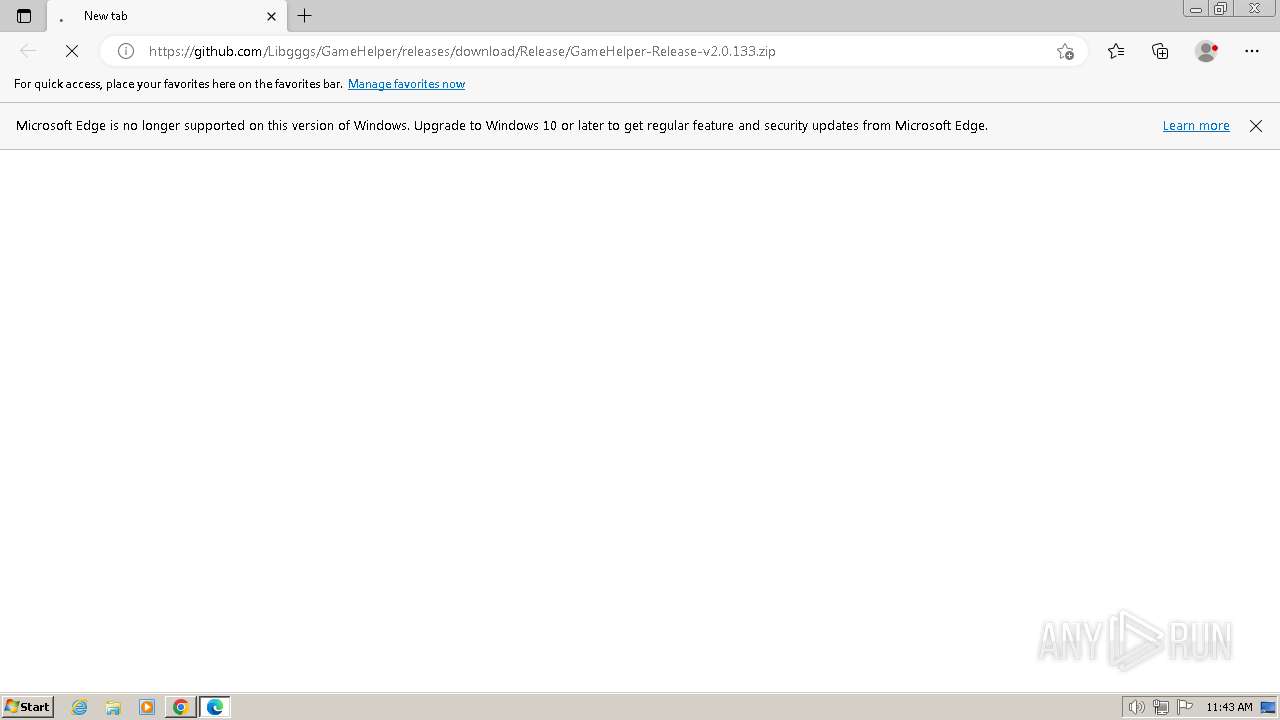
| URL: | https://github.com/Libgggs/GameHelper/releases/download/Release/GameHelper-Release-v2.0.133.zip |
| Full analysis: | https://app.any.run/tasks/1dd0cf20-1a53-481e-97ad-d52795fcf013 |
| Verdict: | Malicious activity |
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | January 02, 2024, 11:42:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 4948509F50C353B8602A06681BC1DD97 |
| SHA1: | EB48BA136CE78DD4A561EE3CC22D3E852BEF84BC |
| SHA256: | C19EBAE249FC22E55F4AC70A4EF7818D2D4C4450FE87A6919ED9394E8759F104 |
| SSDEEP: | 3:N8tEdmhIBAE2kC8AEqiE9tFO/tbL/:2uVBAr2A3PFO13 |
MALICIOUS
Orcus is detected
- GameHelpers.exe (PID: 2928)
- GameHelpers.exe (PID: 1784)
- defaultpoll.exe (PID: 3020)
- installutil.exe (PID: 3512)
- defaultpoll.exe (PID: 2396)
- defaultpoll.exe (PID: 2976)
- defaultpoll.exe (PID: 3368)
- defaultpoll.exe (PID: 1936)
- defaultpoll.exe (PID: 3844)
ORCUS has been detected (YARA)
- installutil.exe (PID: 3512)
SUSPICIOUS
Reads the BIOS version
- GameHelpers.exe (PID: 1376)
Reads the Internet Settings
- GameHelpers.exe (PID: 1376)
- GameHelpers.exe (PID: 2928)
- GameHelpers.exe (PID: 1784)
Starts CMD.EXE for commands execution
- GameHelpers.exe (PID: 1376)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1904)
INFO
Drops the executable file immediately after the start
- chrome.exe (PID: 1528)
- WinRAR.exe (PID: 2584)
- GameHelpers.exe (PID: 1376)
- GameHelpers.exe (PID: 1784)
- chrome.exe (PID: 116)
- chrome.exe (PID: 3180)
Manual execution by a user
- msedge.exe (PID: 2504)
Application launched itself
- msedge.exe (PID: 2504)
- chrome.exe (PID: 116)
- GameHelpers.exe (PID: 2928)
The process uses the downloaded file
- msedge.exe (PID: 4032)
- WinRAR.exe (PID: 2584)
Checks supported languages
- GameHelpers.exe (PID: 1376)
- GameHelpers.exe (PID: 2928)
- GameHelpers.exe (PID: 1784)
- defaultpoll.exe (PID: 3020)
- installutil.exe (PID: 3512)
- defaultpoll.exe (PID: 2976)
- defaultpoll.exe (PID: 3368)
- defaultpoll.exe (PID: 2396)
- defaultpoll.exe (PID: 1936)
- defaultpoll.exe (PID: 3844)
Reads the computer name
- GameHelpers.exe (PID: 1376)
- GameHelpers.exe (PID: 2928)
- GameHelpers.exe (PID: 1784)
- defaultpoll.exe (PID: 3020)
- installutil.exe (PID: 3512)
- defaultpoll.exe (PID: 2976)
- defaultpoll.exe (PID: 2396)
- defaultpoll.exe (PID: 3368)
- defaultpoll.exe (PID: 1936)
- defaultpoll.exe (PID: 3844)
Create files in a temporary directory
- GameHelpers.exe (PID: 1376)
Reads the machine GUID from the registry
- GameHelpers.exe (PID: 2928)
- GameHelpers.exe (PID: 1376)
- GameHelpers.exe (PID: 1784)
- defaultpoll.exe (PID: 3020)
- defaultpoll.exe (PID: 2976)
- installutil.exe (PID: 3512)
- defaultpoll.exe (PID: 2396)
- defaultpoll.exe (PID: 3368)
- defaultpoll.exe (PID: 1936)
- defaultpoll.exe (PID: 3844)
Creates files or folders in the user directory
- GameHelpers.exe (PID: 1784)
Starts itself from another location
- GameHelpers.exe (PID: 1784)
The process executes via Task Scheduler
- defaultpoll.exe (PID: 2976)
- defaultpoll.exe (PID: 2396)
- defaultpoll.exe (PID: 3368)
- defaultpoll.exe (PID: 1936)
- defaultpoll.exe (PID: 3844)
Connects to unusual port
- installutil.exe (PID: 3512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Orcus
(PID) Process(3512) installutil.exe
C2 (3)49810.client.sudorat.top:49810
49810.client.sudorat.ru:49810
31.44.184.52:49810
Keys
AES9c50022dd3337baebd4331d3985699b51b5ddf6826d37ac4261856ef368c8359
Salt
Options
AutostartBuilderProperty
AutostartMethodDisable
TaskSchedulerTaskNamesudik
TaskHighestPrivilegestrue
AutoStealtrue
Injecttrue
RegistryHiddenStarttrue
RegistryKeyNameSudik
TryAllAutostartMethodsOnFailtrue
ChangeAssemblyInformationBuilderProperty
ChangeAssemblyInformationfalse
AssemblyTitlenull
AssemblyDescriptionnull
AssemblyCompanyNamenull
AssemblyProductNamenull
AssemblyCopyrightnull
AssemblyTrademarksnull
AssemblyProductVersion1.0.0.0
AssemblyFileVersion1.0.0.0
ChangeCreationDateBuilderProperty
IsEnabledfalse
NewCreationDate2016-11-05T21:17:40
ChangeIconBuilderProperty
ChangeIconfalse
IconPathnull
ClientTagBuilderProperty
ClientTagP1
DataFolderBuilderProperty
Path%appdata%\pollcentral\
DefaultPrivilegesBuilderProperty
RequireAdministratorRightstrue
DisableInstallationPromptBuilderProperty
IsDisabledtrue
FrameworkVersionBuilderProperty
FrameworkVersionNET35
HideFileBuilderProperty
HideFiletrue
InstallationLocationBuilderProperty
Path%appdata%\pollcentral\defaultpoll.exe
InstallBuilderProperty
Installtrue
KeyloggerBuilderProperty
IsEnabledfalse
MutexBuilderProperty
Mutexsudo_c82hh4lspes0mr053lqsldxgtdyrf0sk
ProxyBuilderProperty
ProxyOptionNone
ProxyAddressnull
ProxyPort1080
ProxyType2
ReconnectDelayProperty
Delay10000
RequireAdministratorPrivilegesInstallerBuilderProperty
RequireAdministratorPrivilegestrue
RespawnTaskBuilderProperty
IsEnabledtrue
TaskNameDiscordUpdater
ServiceBuilderProperty
Installfalse
SetRunProgramAsAdminFlagBuilderProperty
SetFlagtrue
WatchdogBuilderProperty
IsEnabledfalse
Nameaga.exe
WatchdogLocationAppData
PreventFileDeletionfalse
Plugins (0)
Total processes
92
Monitored processes
53
Malicious processes
12
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://github.com/Libgggs/GameHelper/releases/download/Release/GameHelper-Release-v2.0.133.zip" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=868 --field-trial-handle=1108,i,5046049948865823818,8920797913624799615,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1280 --field-trial-handle=1108,i,5046049948865823818,8920797913624799615,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 712 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2036 --field-trial-handle=1108,i,5046049948865823818,8920797913624799615,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 968 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2296 --field-trial-handle=1292,i,15618547167589342040,2919428139366236654,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1500 --field-trial-handle=1108,i,5046049948865823818,8920797913624799615,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3312 --field-trial-handle=1108,i,5046049948865823818,8920797913624799615,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1376 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2584.28623\GameHelpers.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2584.28623\GameHelpers.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1384 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3444 --field-trial-handle=1108,i,5046049948865823818,8920797913624799615,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1432 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6e558b38,0x6e558b48,0x6e558b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
13 157
Read events
13 002
Write events
153
Delete events
2
Modification events
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
74
Suspicious files
1 105
Text files
105
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RFdfb1a.TMP | — | |
MD5:— | SHA256:— | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:358570F689377CE6838812643E03734B | SHA256:5B41FCC2E1A843AEAB9437B06E27B798870FF10D86A51B163BF48862BCD32590 | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:AD0DB8476493577A67FA94A162B646C4 | SHA256:304FB5B4FD83D4A9FF1EF4CF20232A1783169C148297BFE37ED24A1D22A74F2B | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\24e6f4e1-07c9-4c68-84ff-241145a48184.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old~RFe00e6.TMP | — | |
MD5:— | SHA256:— | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFdfb29.TMP | text | |
MD5:05CF4C3C5148DA6355D3561A9EAA5E8A | SHA256:8D720243F6876898E4F197C8867C4CEE69F1C7335C55B8A29C120B1028D93E41 | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:ECD3386BCC950E73B86EB128A5F57622 | SHA256:C9A068EAFBC587EDFC89392F64DDD350EEB96C5CF195CDB030BAB8F6DD33833B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
111
DNS requests
102
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 111 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 28.8 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 46.9 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 1.15 Mb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 606 Kb | unknown |
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 5.86 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 9.92 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 1.57 Mb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 725 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
316 | chrome.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
116 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
316 | chrome.exe | 74.125.71.84:443 | accounts.google.com | GOOGLE | US | unknown |
316 | chrome.exe | 185.199.111.133:443 | objects.githubusercontent.com | FASTLY | US | unknown |
116 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
316 | chrome.exe | 142.250.185.196:443 | www.google.com | GOOGLE | US | whitelisted |
316 | chrome.exe | 142.250.184.238:443 | sb-ssl.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
accounts.google.com |
| shared |
objects.githubusercontent.com |
| shared |
www.google.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
assets.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |