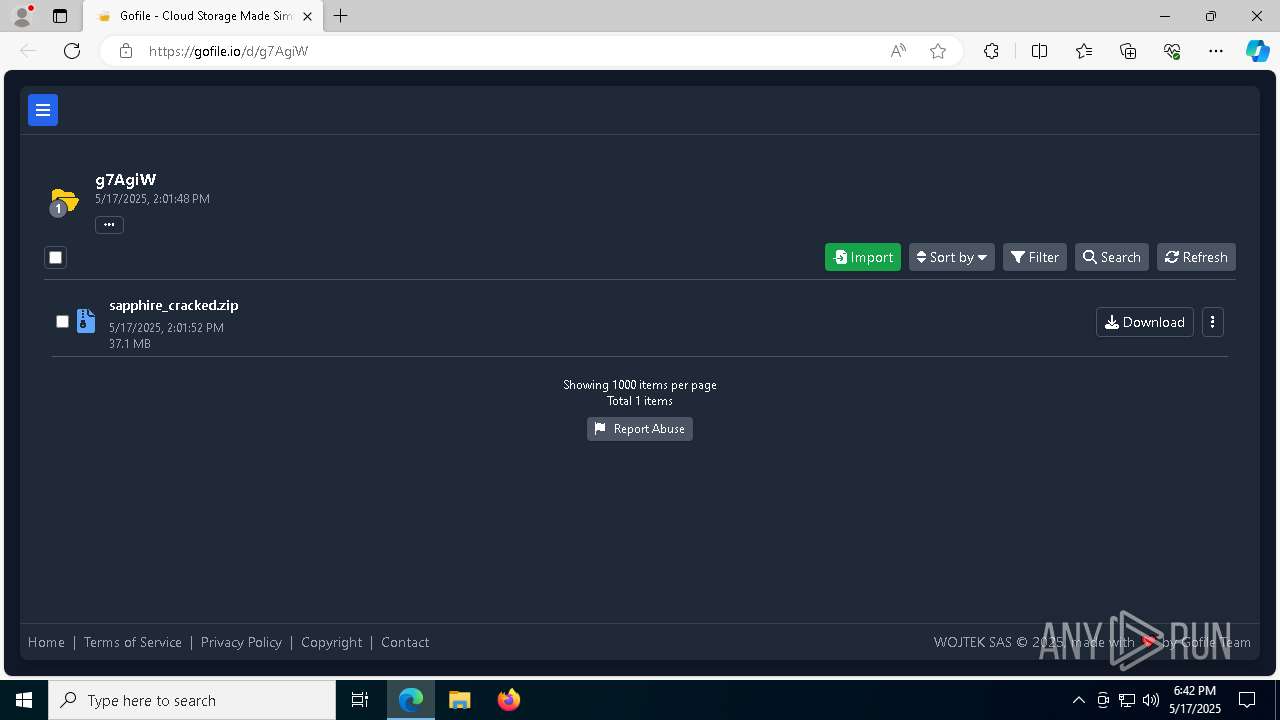
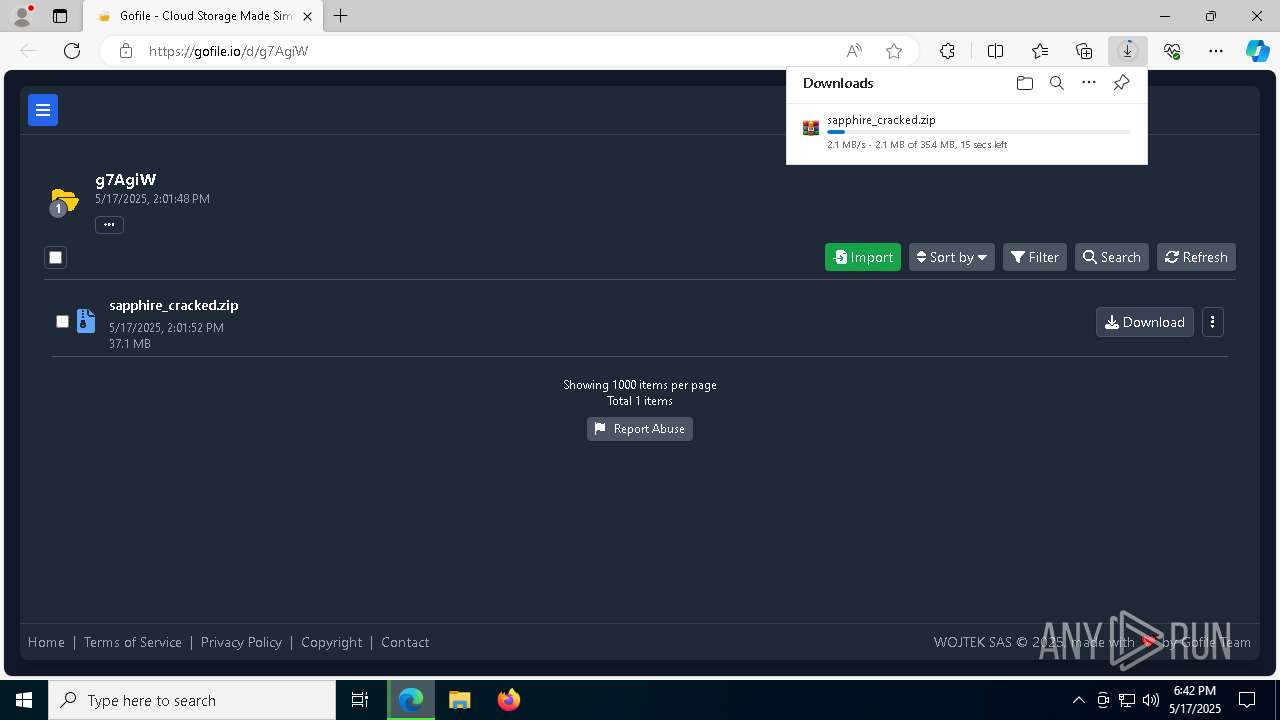
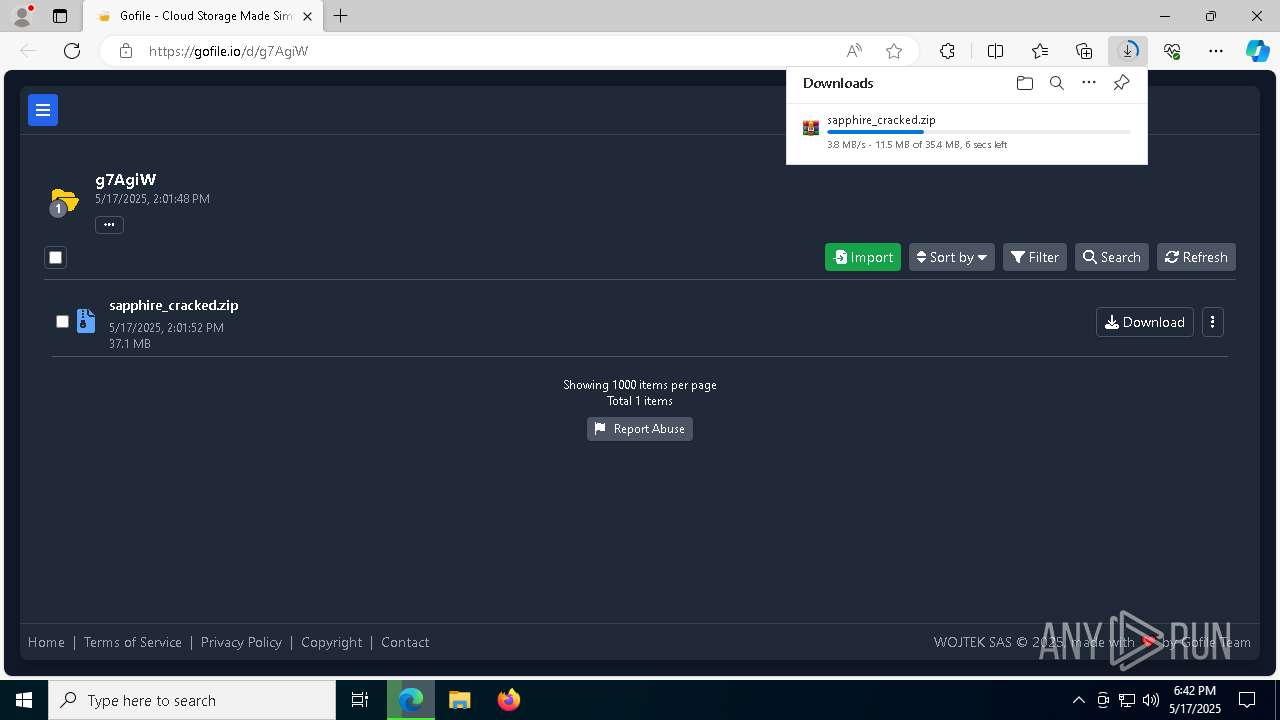
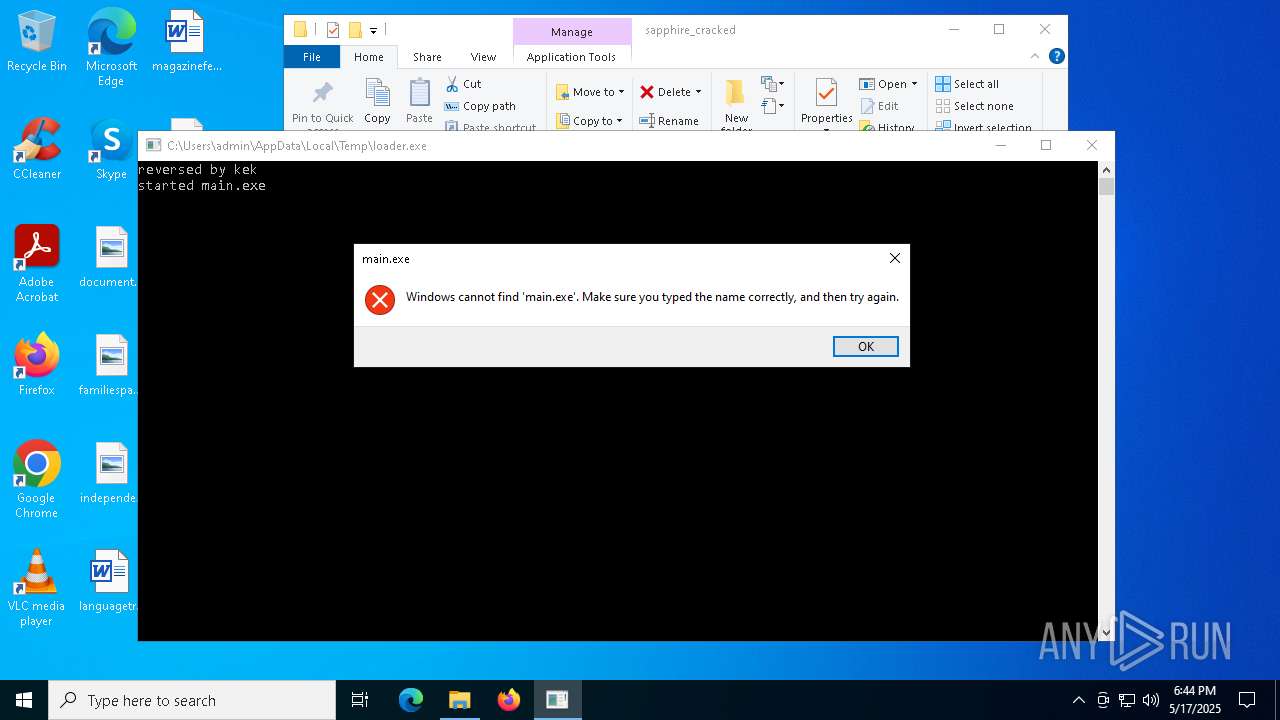
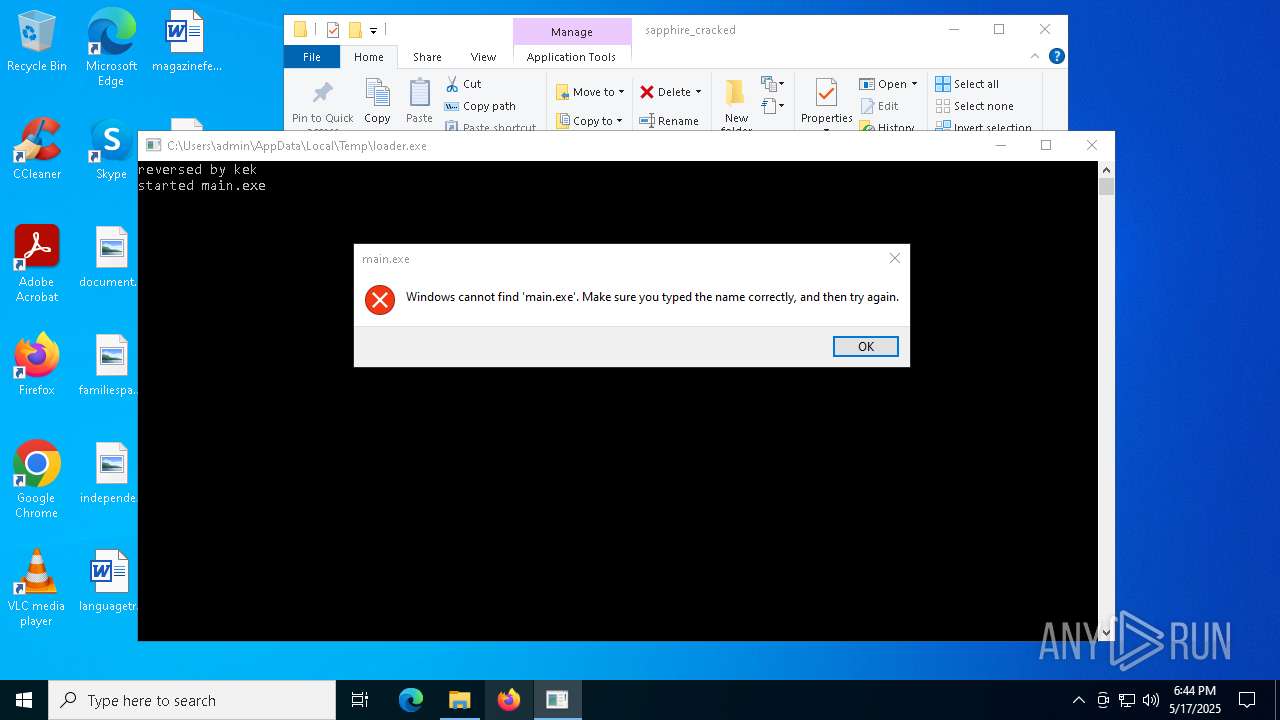
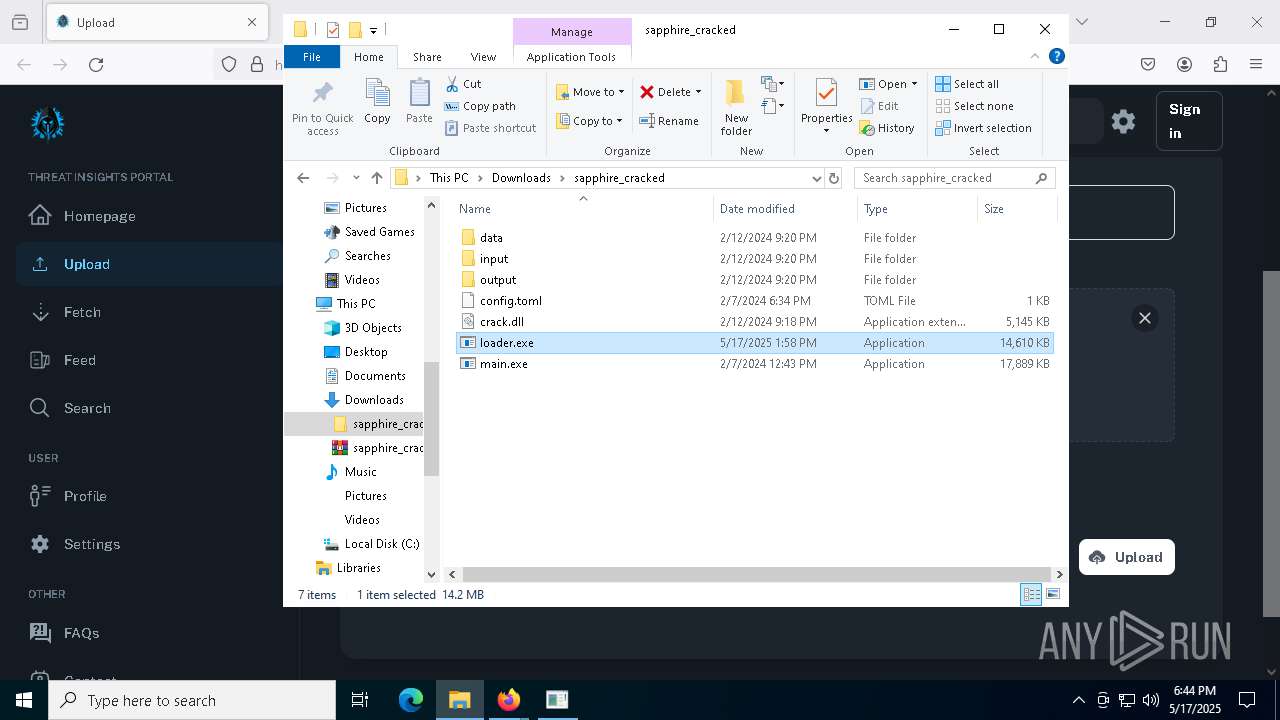
| URL: | https://gofile.io/d/g7AgiW |
| Full analysis: | https://app.any.run/tasks/57327bdd-6b17-4692-9aa5-4ad6cf716d38 |
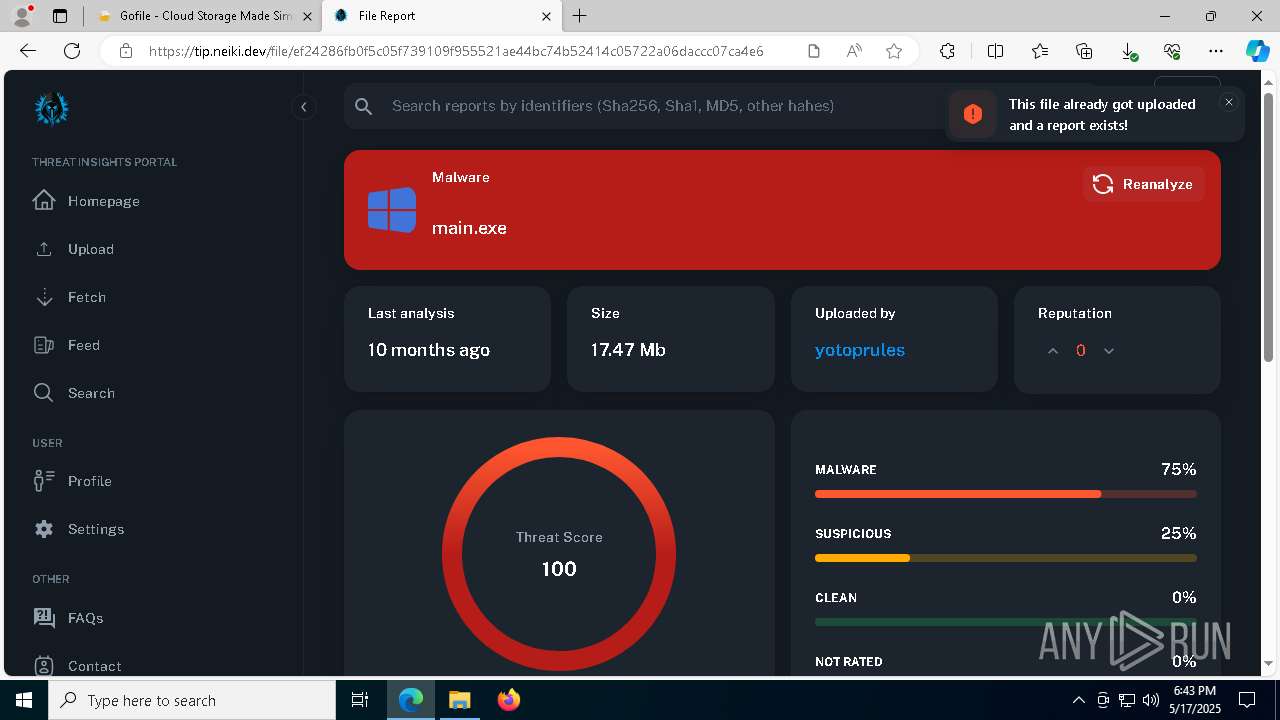
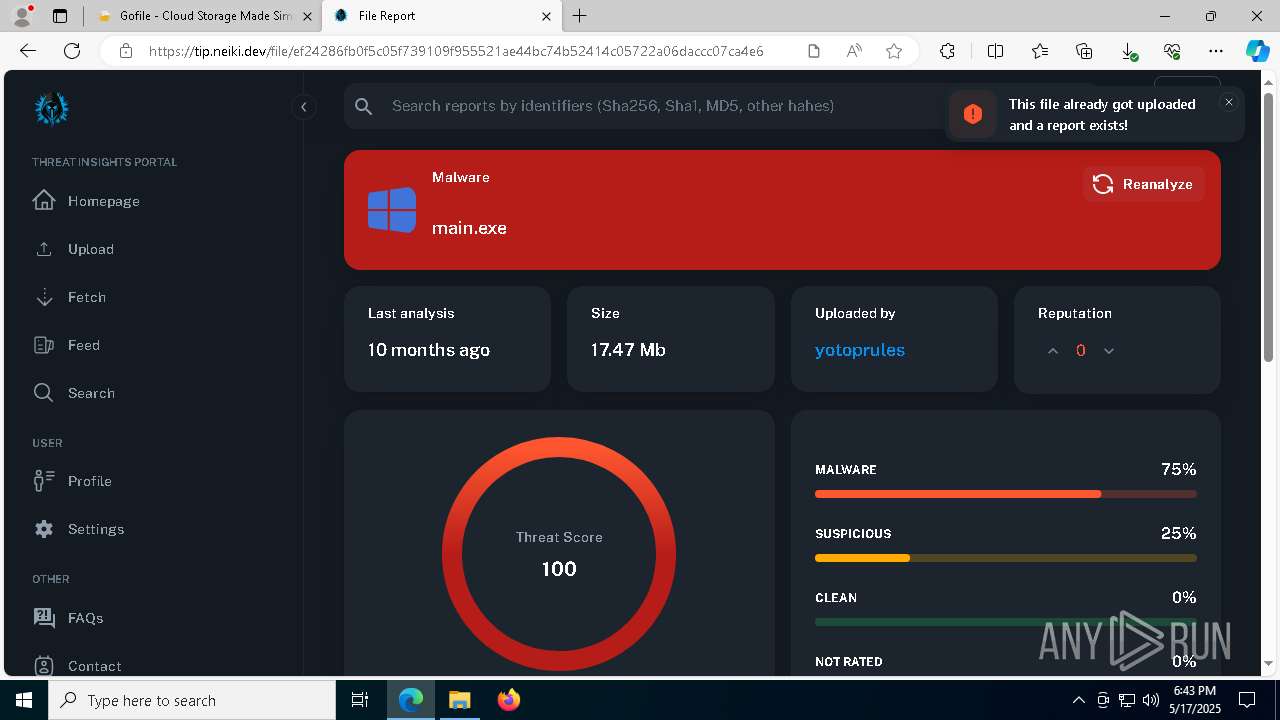
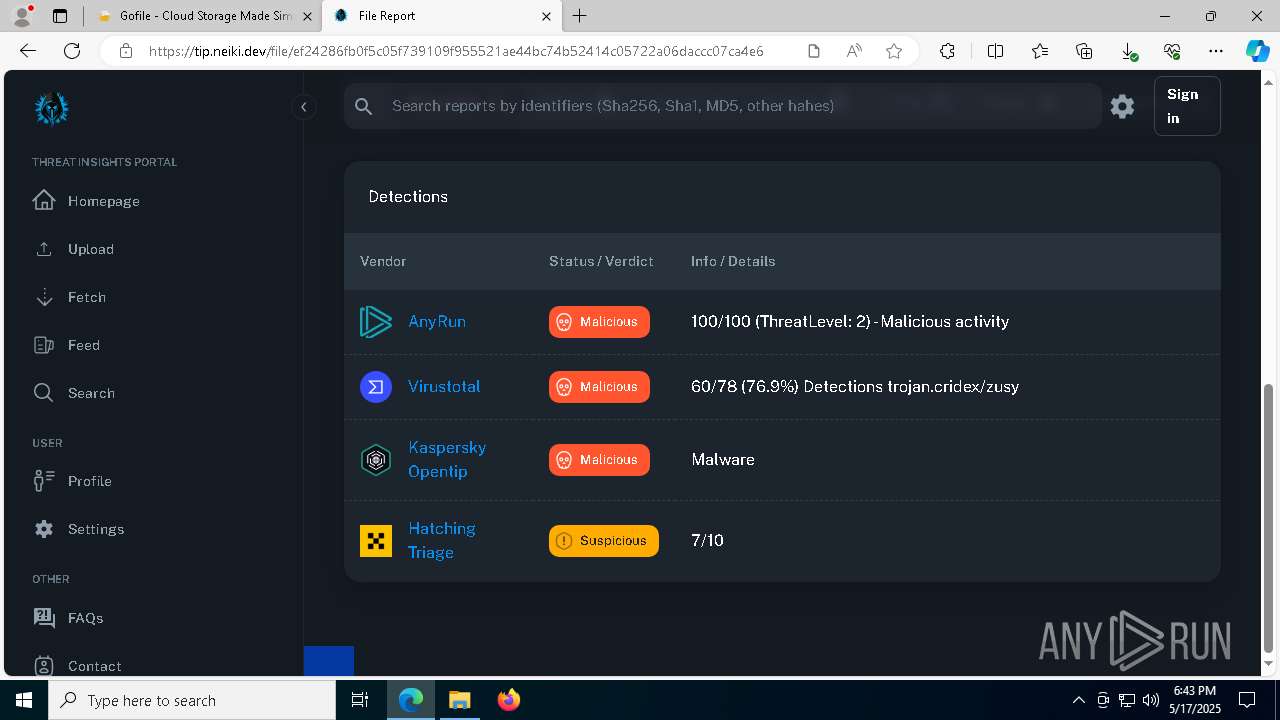
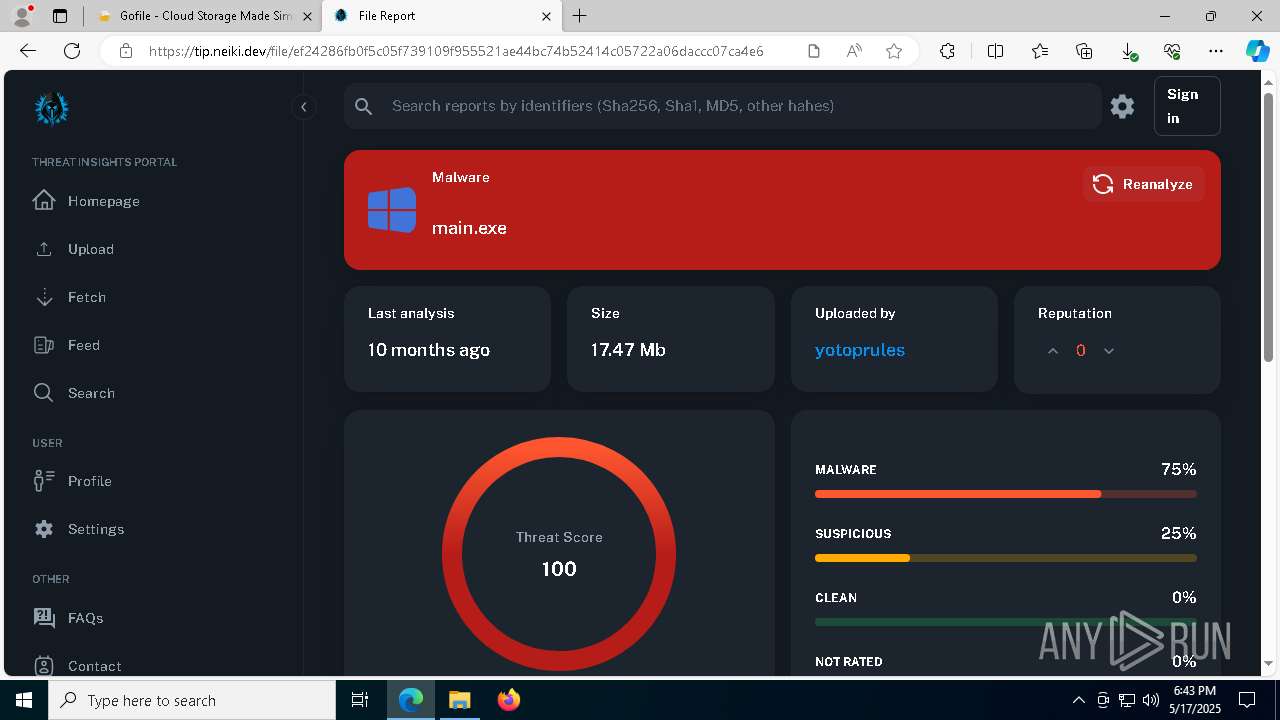
| Verdict: | Malicious activity |
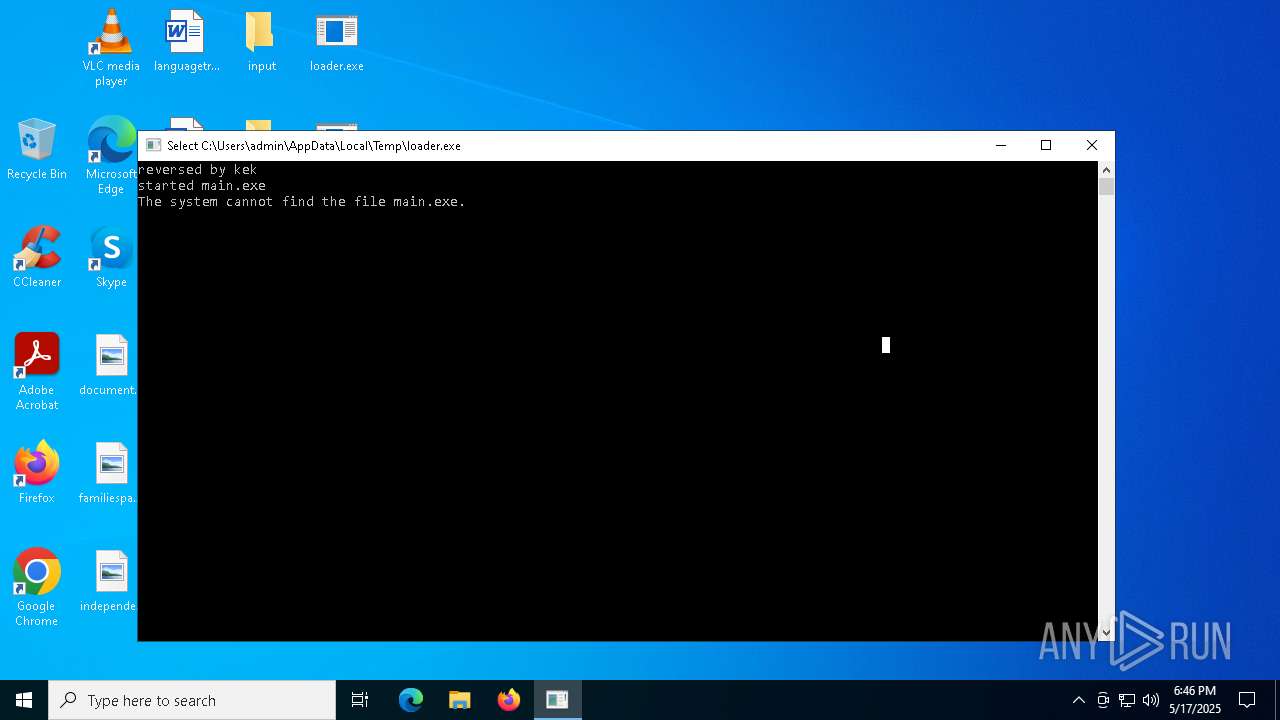
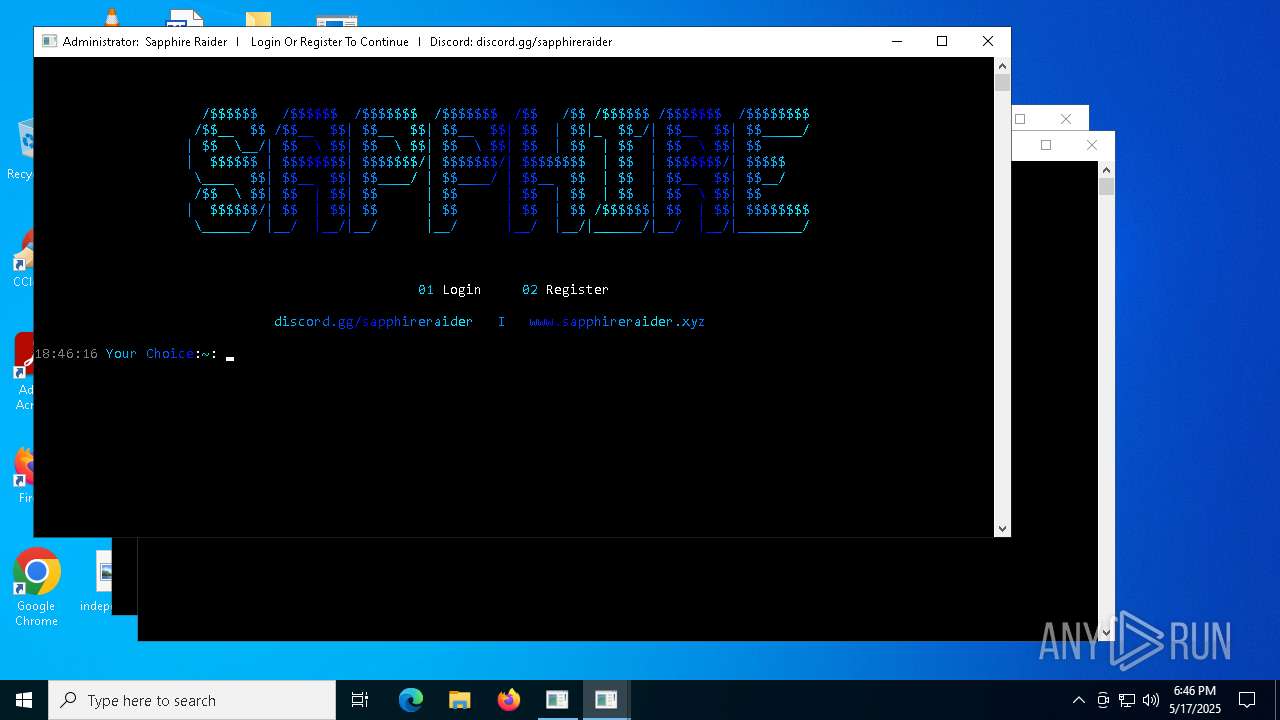
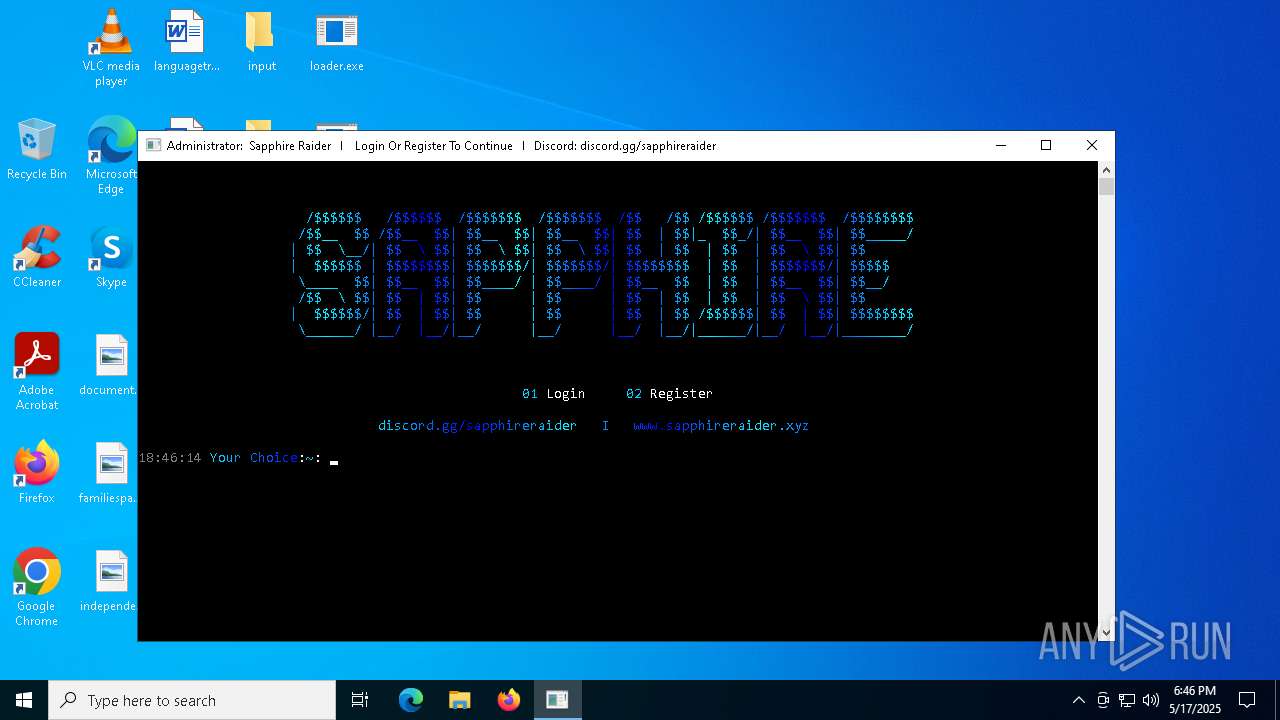
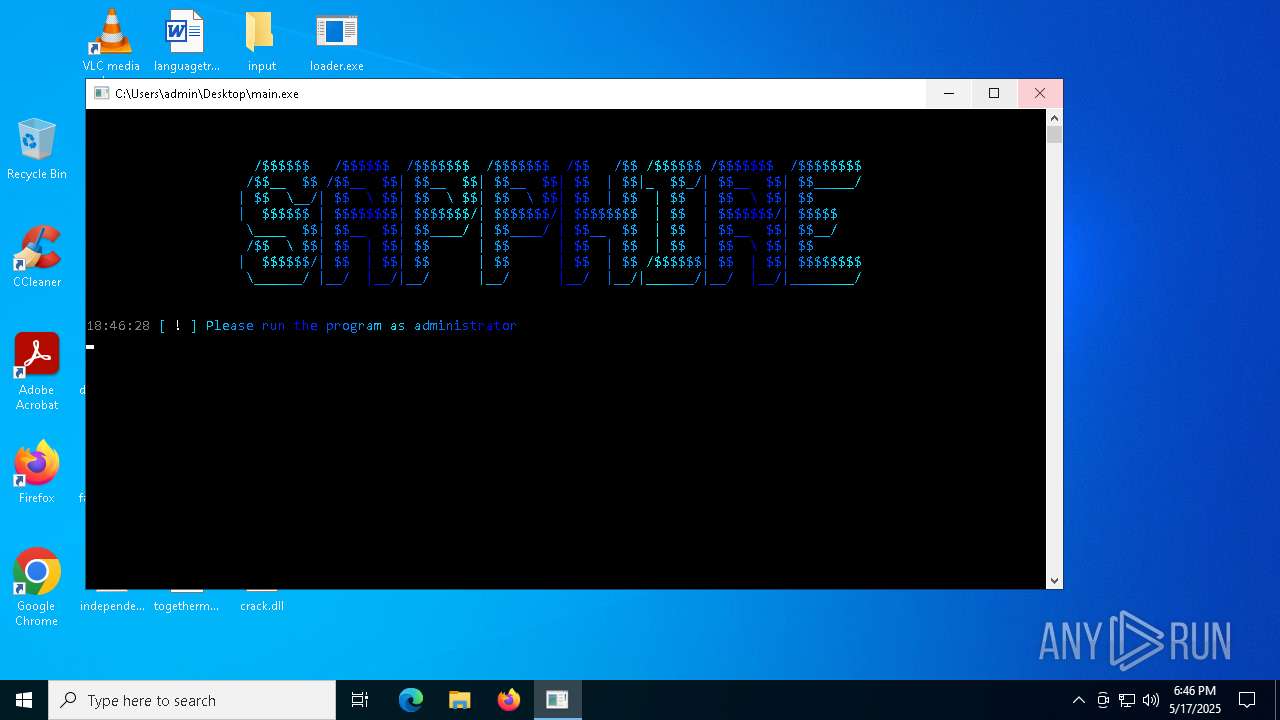
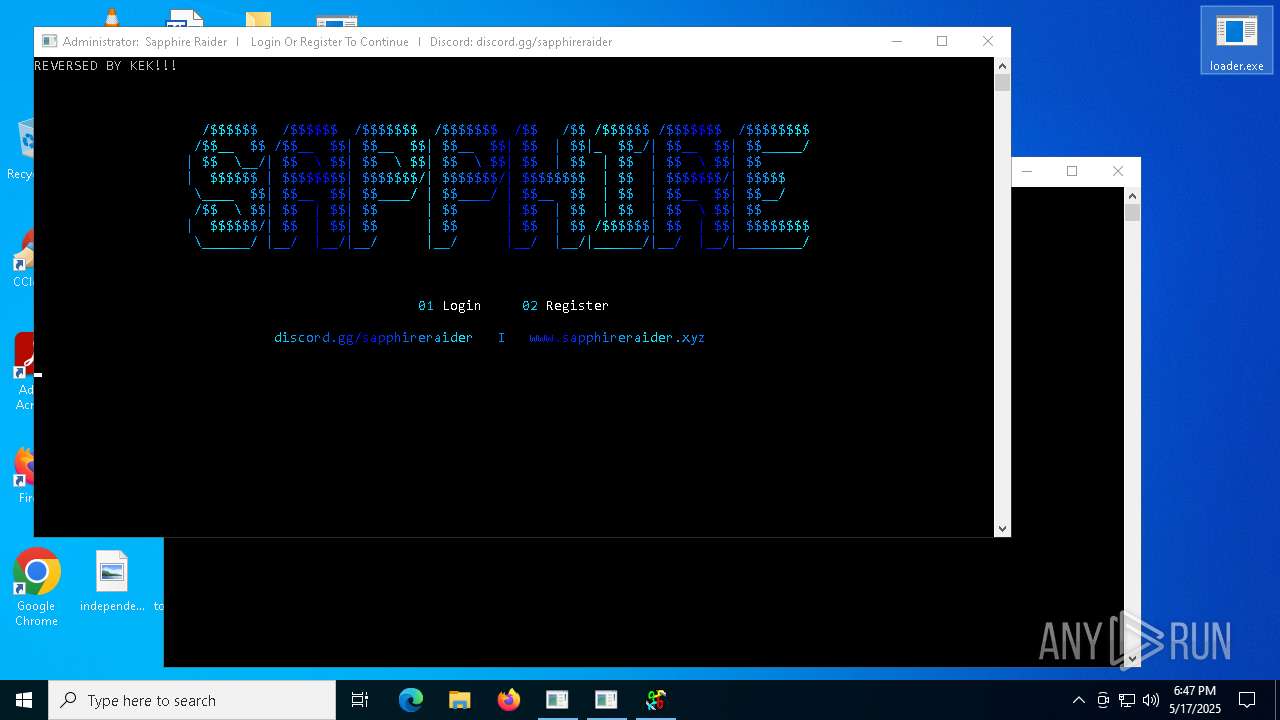
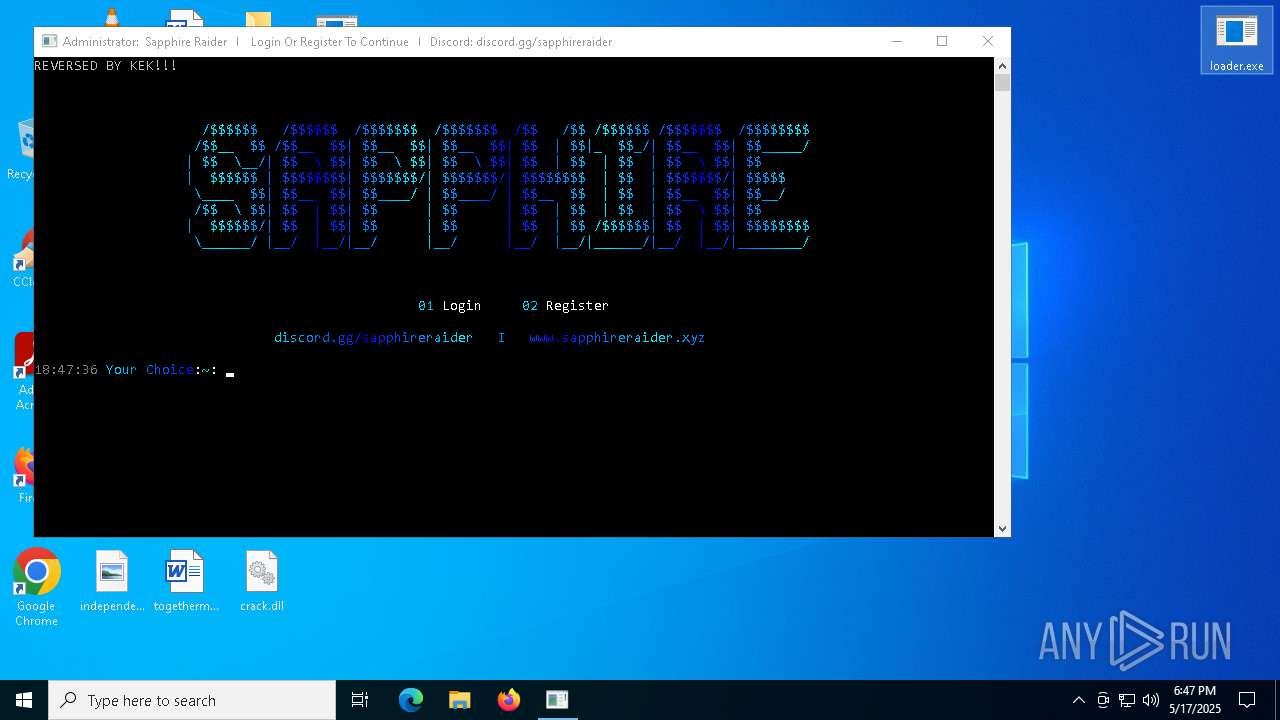
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | May 17, 2025, 18:42:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 209A7B0FAF516D74E1FAF1DADA066D9A |
| SHA1: | E5F178E72A284753F228D82AA92B78D4E73C9AAB |
| SHA256: | C1274945325BA1EAACC47951D5082F1F39A622A219061D2D4605DDCE29E761FC |
| SSDEEP: | 3:N8rxL16yn:2ZX |
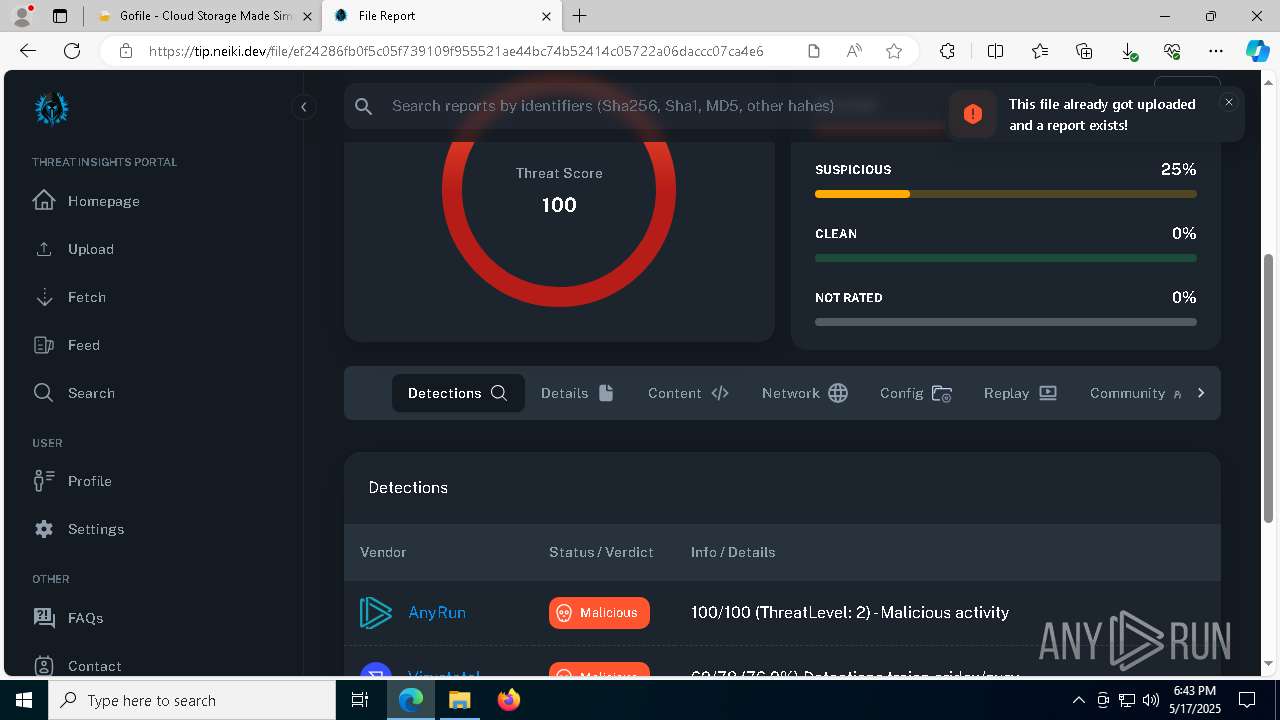
MALICIOUS
Known privilege escalation attack
- dllhost.exe (PID: 2596)
TROX has been detected
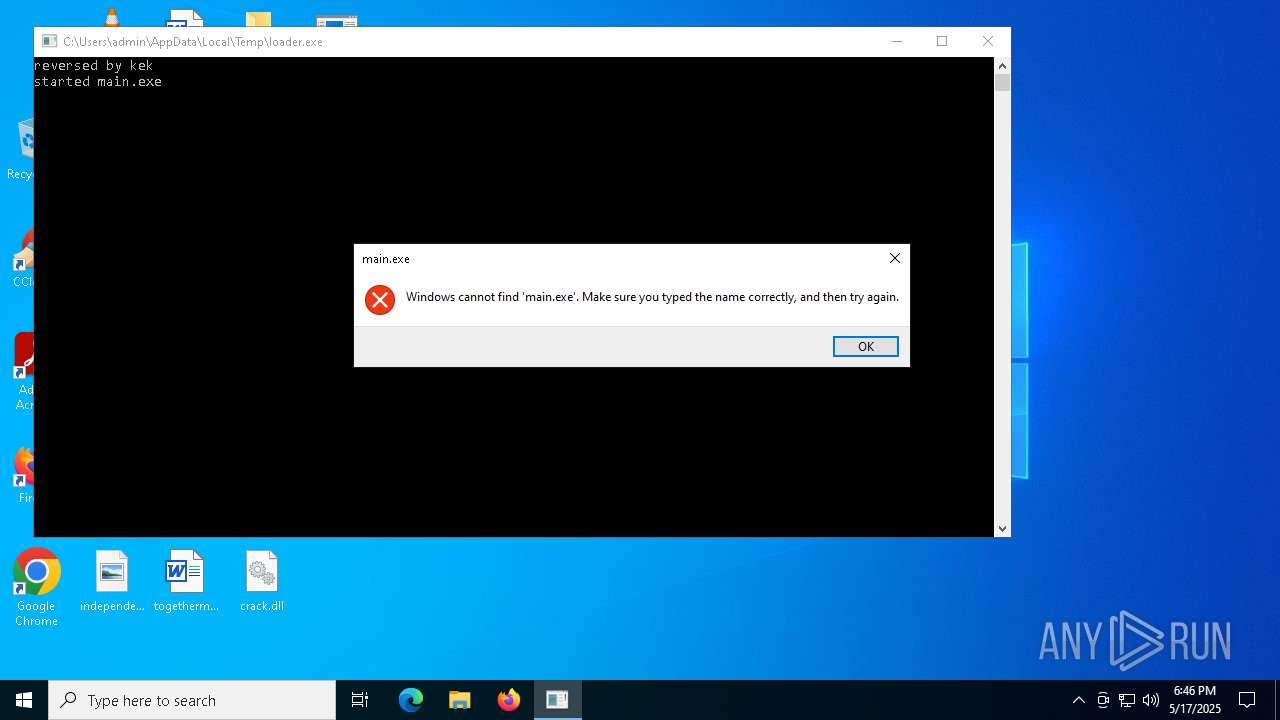
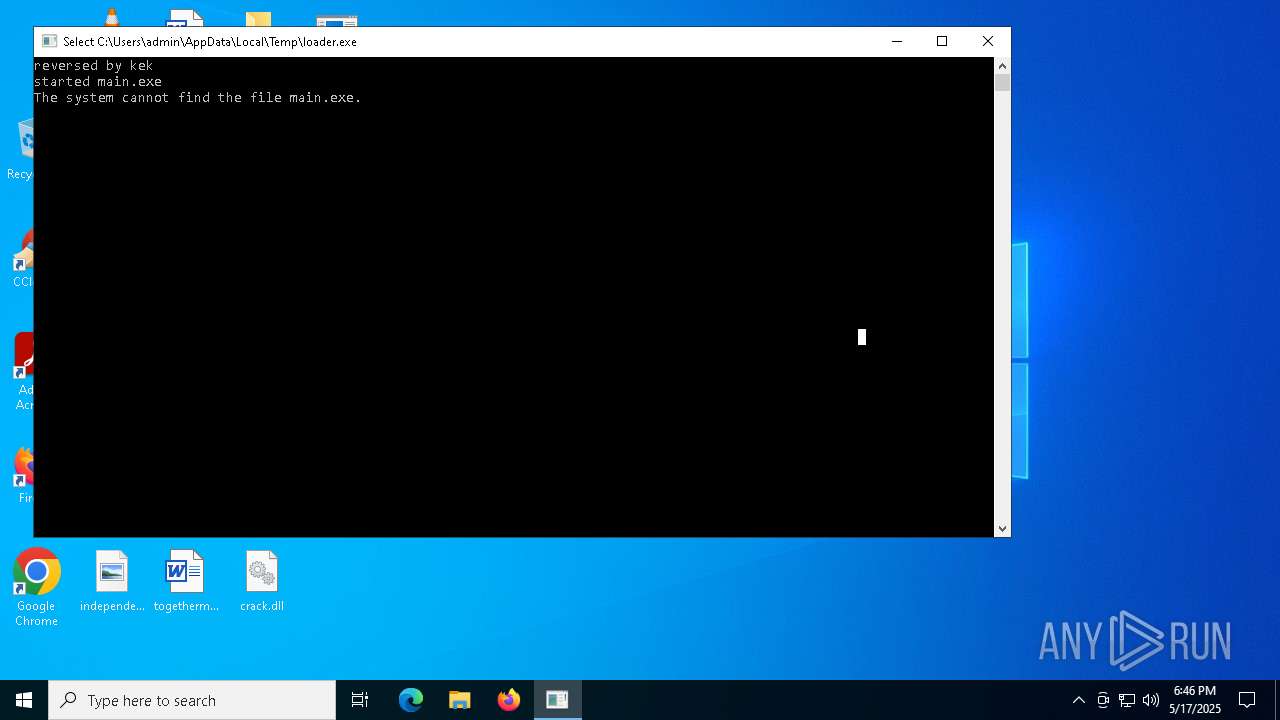
- loader.exe (PID: 7900)
- main.exe (PID: 6124)
- loader.exe (PID: 9004)
- main.exe (PID: 7804)
- main.exe (PID: 6372)
- loader.exe (PID: 8976)
- main.exe (PID: 6872)
- main.exe (PID: 4620)
- main.exe (PID: 8300)
- main.exe (PID: 7932)
- loader.exe (PID: 1040)
- main.exe (PID: 7268)
Executing a file with an untrusted certificate
- Built.exe (PID: 5364)
- Built.exe (PID: 5360)
- Built.exe (PID: 744)
- Built.exe (PID: 2316)
- Built.exe (PID: 8864)
- Built.exe (PID: 7540)
- Built.exe (PID: 1164)
- Built.exe (PID: 4572)
- Built.exe (PID: 2476)
- Built.exe (PID: 8188)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 8188)
- cmd.exe (PID: 8668)
- cmd.exe (PID: 3124)
- cmd.exe (PID: 6652)
Adds path to the Windows Defender exclusion list
- Built.exe (PID: 5364)
- cmd.exe (PID: 4012)
- cmd.exe (PID: 1088)
- Built.exe (PID: 2316)
- cmd.exe (PID: 8828)
- cmd.exe (PID: 8680)
- cmd.exe (PID: 6744)
- Built.exe (PID: 7540)
- cmd.exe (PID: 9212)
- Built.exe (PID: 8188)
- cmd.exe (PID: 8036)
- cmd.exe (PID: 4756)
Changes Windows Defender settings
- cmd.exe (PID: 4012)
- cmd.exe (PID: 8188)
- cmd.exe (PID: 1088)
- cmd.exe (PID: 8668)
- cmd.exe (PID: 8828)
- cmd.exe (PID: 8680)
- cmd.exe (PID: 6744)
- cmd.exe (PID: 3124)
- cmd.exe (PID: 9212)
- cmd.exe (PID: 6652)
- cmd.exe (PID: 8036)
- cmd.exe (PID: 4756)
Changes Controlled Folder Access settings
- powershell.exe (PID: 5260)
- powershell.exe (PID: 4428)
- powershell.exe (PID: 8572)
- powershell.exe (PID: 5380)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 5260)
- powershell.exe (PID: 4428)
- powershell.exe (PID: 8572)
- powershell.exe (PID: 5380)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 5260)
- powershell.exe (PID: 4428)
- powershell.exe (PID: 8572)
- powershell.exe (PID: 5380)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 5260)
- powershell.exe (PID: 4428)
- powershell.exe (PID: 8572)
- powershell.exe (PID: 5380)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 5260)
- powershell.exe (PID: 4428)
- powershell.exe (PID: 8572)
- powershell.exe (PID: 5380)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 5260)
- powershell.exe (PID: 4428)
- powershell.exe (PID: 8572)
- powershell.exe (PID: 5380)
Changes settings for real-time protection
- powershell.exe (PID: 5260)
- powershell.exe (PID: 4428)
- powershell.exe (PID: 8572)
- powershell.exe (PID: 5380)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 8540)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 6852)
- cmd.exe (PID: 8912)
Bypass execution policy to execute commands
- powershell.exe (PID: 8728)
- powershell.exe (PID: 8328)
- powershell.exe (PID: 8024)
- powershell.exe (PID: 6572)
Resets Windows Defender malware definitions to the base version
- MpCmdRun.exe (PID: 236)
- MpCmdRun.exe (PID: 5308)
- MpCmdRun.exe (PID: 8788)
- MpCmdRun.exe (PID: 6272)
BLANKGRABBER has been detected (SURICATA)
- Built.exe (PID: 5364)
- Built.exe (PID: 2316)
- Built.exe (PID: 7540)
Stealers network behavior
- Built.exe (PID: 5364)
SUSPICIOUS
Probably UAC bypass using CMSTP.exe (Connection Manager service profile)
- loader.exe (PID: 3176)
- loader.exe (PID: 9032)
- loader.exe (PID: 7356)
- loader.exe (PID: 8324)
- loader.exe (PID: 2692)
- loader.exe (PID: 8716)
- loader.exe (PID: 8968)
Executable content was dropped or overwritten
- loader.exe (PID: 8092)
- loader.exe (PID: 7900)
- dwm.exe (PID: 6656)
- Built.exe (PID: 5360)
- Built.exe (PID: 5364)
- csc.exe (PID: 9108)
- main.exe (PID: 6124)
- Built.exe (PID: 744)
- loader.exe (PID: 9004)
- main.exe (PID: 7804)
- Built.exe (PID: 2316)
- main.exe (PID: 6372)
- csc.exe (PID: 5624)
- loader.exe (PID: 8976)
- Built.exe (PID: 8864)
- Built.exe (PID: 7540)
- Built.exe (PID: 1164)
- csc.exe (PID: 7340)
- main.exe (PID: 7932)
- main.exe (PID: 6872)
- main.exe (PID: 8300)
- main.exe (PID: 4620)
- loader.exe (PID: 1040)
- main.exe (PID: 7268)
- Built.exe (PID: 2476)
- Built.exe (PID: 8188)
- csc.exe (PID: 7276)
Process drops python dynamic module
- loader.exe (PID: 7900)
- Built.exe (PID: 5360)
- loader.exe (PID: 9004)
- Built.exe (PID: 744)
- main.exe (PID: 6124)
- main.exe (PID: 7804)
- main.exe (PID: 6372)
- loader.exe (PID: 8976)
- Built.exe (PID: 8864)
- Built.exe (PID: 1164)
- main.exe (PID: 7932)
- main.exe (PID: 6872)
- main.exe (PID: 8300)
- main.exe (PID: 4620)
- loader.exe (PID: 1040)
- main.exe (PID: 7268)
- Built.exe (PID: 2476)
Process drops legitimate windows executable
- loader.exe (PID: 7900)
- dwm.exe (PID: 6656)
- Built.exe (PID: 5360)
- Built.exe (PID: 5364)
- main.exe (PID: 6124)
- loader.exe (PID: 9004)
- Built.exe (PID: 744)
- main.exe (PID: 7804)
- Built.exe (PID: 2316)
- loader.exe (PID: 8976)
- main.exe (PID: 6372)
- Built.exe (PID: 8864)
- Built.exe (PID: 7540)
- Built.exe (PID: 1164)
- main.exe (PID: 7932)
- main.exe (PID: 6872)
- main.exe (PID: 8300)
- main.exe (PID: 4620)
- loader.exe (PID: 1040)
- main.exe (PID: 7268)
- Built.exe (PID: 2476)
- Built.exe (PID: 8188)
Starts CMD.EXE for commands execution
- loader.exe (PID: 7012)
- Built.exe (PID: 5364)
- main.exe (PID: 976)
- loader.exe (PID: 2568)
- Built.exe (PID: 2316)
- main.exe (PID: 8664)
- main.exe (PID: 3828)
- loader.exe (PID: 8052)
- Built.exe (PID: 7540)
- main.exe (PID: 8360)
- main.exe (PID: 2896)
- main.exe (PID: 7704)
- main.exe (PID: 7660)
- loader.exe (PID: 9148)
- main.exe (PID: 5244)
- Built.exe (PID: 8188)
Uses TASKKILL.EXE to kill process
- mshta.exe (PID: 3032)
- cmd.exe (PID: 8768)
- cmd.exe (PID: 8852)
- cmd.exe (PID: 9136)
- cmd.exe (PID: 6072)
- cmd.exe (PID: 1096)
- cmd.exe (PID: 8732)
- cmd.exe (PID: 8224)
- cmd.exe (PID: 8628)
- cmd.exe (PID: 8276)
- cmd.exe (PID: 8884)
- cmd.exe (PID: 5608)
- cmd.exe (PID: 7652)
- cmd.exe (PID: 4376)
- mshta.exe (PID: 3480)
- mshta.exe (PID: 9140)
- mshta.exe (PID: 8592)
- mshta.exe (PID: 9104)
The process drops C-runtime libraries
- loader.exe (PID: 7900)
- Built.exe (PID: 5360)
- Built.exe (PID: 744)
- main.exe (PID: 6124)
- loader.exe (PID: 9004)
- main.exe (PID: 7804)
- loader.exe (PID: 8976)
- main.exe (PID: 6372)
- Built.exe (PID: 1164)
- Built.exe (PID: 8864)
- main.exe (PID: 7932)
- main.exe (PID: 6872)
- main.exe (PID: 4620)
- main.exe (PID: 8300)
- loader.exe (PID: 1040)
- main.exe (PID: 7268)
- Built.exe (PID: 2476)
Starts a Microsoft application from unusual location
- Built.exe (PID: 5360)
- Built.exe (PID: 5364)
- Built.exe (PID: 744)
- Built.exe (PID: 2316)
- Built.exe (PID: 7540)
- Built.exe (PID: 8864)
- Built.exe (PID: 1164)
- Built.exe (PID: 4572)
- Built.exe (PID: 2476)
- Built.exe (PID: 8188)
Found strings related to reading or modifying Windows Defender settings
- Built.exe (PID: 5364)
- Built.exe (PID: 2316)
- Built.exe (PID: 7540)
- Built.exe (PID: 8188)
Application launched itself
- Built.exe (PID: 5360)
- Built.exe (PID: 744)
- Built.exe (PID: 8864)
- Built.exe (PID: 1164)
- Built.exe (PID: 2476)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4012)
- cmd.exe (PID: 8188)
- cmd.exe (PID: 1088)
- cmd.exe (PID: 8328)
- cmd.exe (PID: 8540)
- cmd.exe (PID: 8900)
- cmd.exe (PID: 4608)
- cmd.exe (PID: 7284)
- cmd.exe (PID: 8668)
- cmd.exe (PID: 8828)
- cmd.exe (PID: 8324)
- cmd.exe (PID: 2088)
- cmd.exe (PID: 8680)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 9208)
- cmd.exe (PID: 8700)
- cmd.exe (PID: 236)
- cmd.exe (PID: 7836)
- cmd.exe (PID: 6744)
- cmd.exe (PID: 3124)
- cmd.exe (PID: 9212)
- cmd.exe (PID: 5172)
- cmd.exe (PID: 6852)
- cmd.exe (PID: 1132)
- cmd.exe (PID: 7592)
- cmd.exe (PID: 1280)
- cmd.exe (PID: 5800)
- cmd.exe (PID: 6652)
- cmd.exe (PID: 8036)
- cmd.exe (PID: 4756)
- cmd.exe (PID: 8468)
- cmd.exe (PID: 8912)
- cmd.exe (PID: 8632)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 4012)
- cmd.exe (PID: 1088)
- cmd.exe (PID: 8828)
- cmd.exe (PID: 8680)
- cmd.exe (PID: 6744)
- cmd.exe (PID: 9212)
- cmd.exe (PID: 8036)
- cmd.exe (PID: 4756)
Get information on the list of running processes
- cmd.exe (PID: 7100)
- cmd.exe (PID: 3156)
- cmd.exe (PID: 8024)
- Built.exe (PID: 5364)
- cmd.exe (PID: 8336)
- Built.exe (PID: 2316)
- cmd.exe (PID: 7488)
- cmd.exe (PID: 8496)
- cmd.exe (PID: 7704)
- cmd.exe (PID: 8276)
- Built.exe (PID: 7540)
- cmd.exe (PID: 7276)
- cmd.exe (PID: 3156)
- cmd.exe (PID: 616)
- cmd.exe (PID: 3676)
- Built.exe (PID: 8188)
- cmd.exe (PID: 6124)
- cmd.exe (PID: 8348)
- cmd.exe (PID: 7180)
- cmd.exe (PID: 8344)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 8188)
- cmd.exe (PID: 8668)
- cmd.exe (PID: 3124)
- cmd.exe (PID: 6652)
Script disables Windows Defender's IPS
- cmd.exe (PID: 8188)
- cmd.exe (PID: 8668)
- cmd.exe (PID: 3124)
- cmd.exe (PID: 6652)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 2316)
- cmd.exe (PID: 8224)
- cmd.exe (PID: 9108)
- cmd.exe (PID: 3156)
- cmd.exe (PID: 2616)
- cmd.exe (PID: 9172)
- cmd.exe (PID: 8952)
- cmd.exe (PID: 7856)
- cmd.exe (PID: 7436)
- cmd.exe (PID: 8776)
- cmd.exe (PID: 7640)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 3956)
- cmd.exe (PID: 456)
- cmd.exe (PID: 9200)
- cmd.exe (PID: 8832)
- cmd.exe (PID: 5380)
- cmd.exe (PID: 1088)
- cmd.exe (PID: 6032)
- cmd.exe (PID: 8488)
- cmd.exe (PID: 7648)
- cmd.exe (PID: 8232)
- cmd.exe (PID: 6476)
Checks for external IP
- Built.exe (PID: 5364)
- svchost.exe (PID: 2196)
- Built.exe (PID: 2316)
- Built.exe (PID: 7540)
- Built.exe (PID: 8188)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 8540)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 6852)
- cmd.exe (PID: 8912)
Base64-obfuscated command line is found
- cmd.exe (PID: 8540)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 6852)
- cmd.exe (PID: 8912)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 8540)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 6852)
- cmd.exe (PID: 8912)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 8444)
- cmd.exe (PID: 4884)
- cmd.exe (PID: 8660)
- cmd.exe (PID: 7704)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 8396)
- cmd.exe (PID: 720)
- cmd.exe (PID: 7544)
- cmd.exe (PID: 8336)
Starts application with an unusual extension
- cmd.exe (PID: 8356)
- cmd.exe (PID: 9108)
- cmd.exe (PID: 8588)
- cmd.exe (PID: 8976)
- cmd.exe (PID: 8288)
- cmd.exe (PID: 9124)
- cmd.exe (PID: 616)
- cmd.exe (PID: 8492)
- cmd.exe (PID: 8256)
- cmd.exe (PID: 4268)
- cmd.exe (PID: 7964)
- cmd.exe (PID: 7184)
- cmd.exe (PID: 5228)
- cmd.exe (PID: 7936)
- cmd.exe (PID: 208)
- cmd.exe (PID: 5044)
- cmd.exe (PID: 6108)
- cmd.exe (PID: 4628)
CSC.EXE is used to compile C# code
- csc.exe (PID: 9108)
- csc.exe (PID: 5624)
- csc.exe (PID: 7340)
- csc.exe (PID: 7276)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 7948)
- cmd.exe (PID: 6656)
- cmd.exe (PID: 9168)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Built.exe (PID: 5364)
- Built.exe (PID: 2316)
- Built.exe (PID: 7540)
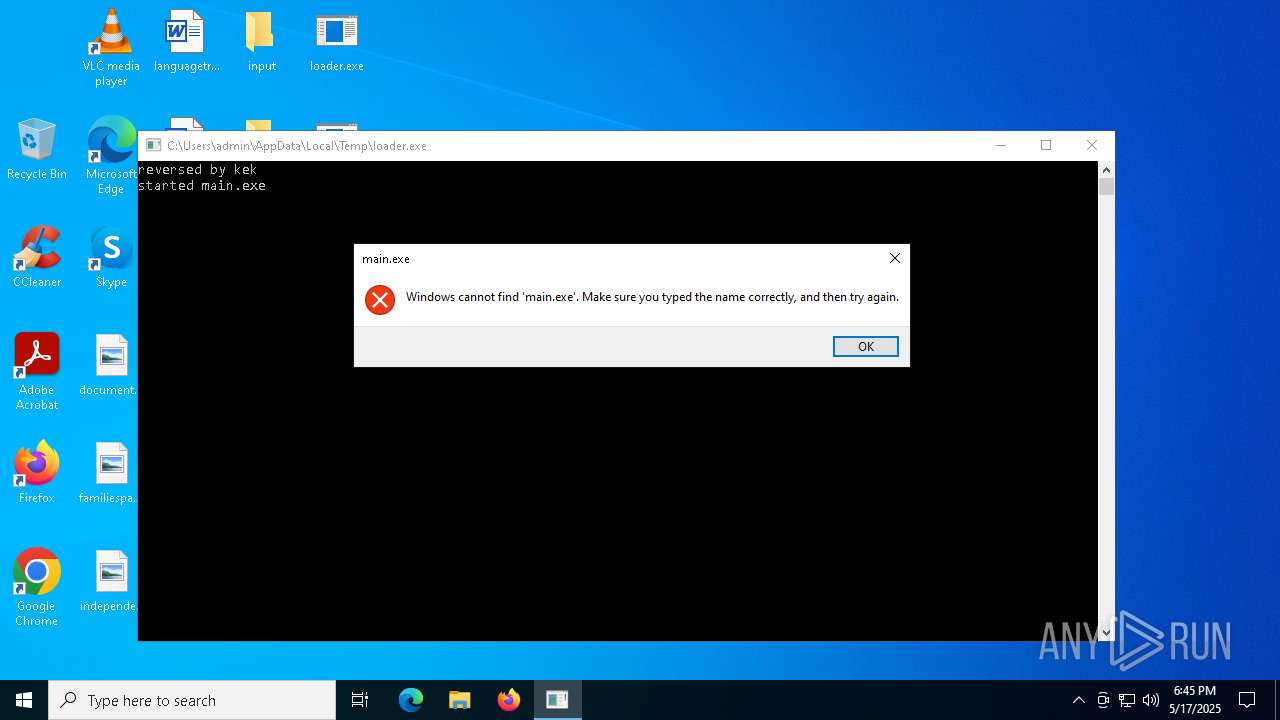
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 728)
- rar.exe (PID: 1300)
- rar.exe (PID: 8600)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 8296)
- cmd.exe (PID: 9200)
- cmd.exe (PID: 3032)
INFO
Checks supported languages
- identity_helper.exe (PID: 4120)
Manual execution by a user
- WinRAR.exe (PID: 6112)
- loader.exe (PID: 3176)
- loader.exe (PID: 8056)
- main.exe (PID: 6124)
- firefox.exe (PID: 7908)
- main.exe (PID: 6372)
- loader.exe (PID: 9032)
- loader.exe (PID: 7356)
- main.exe (PID: 6872)
- main.exe (PID: 7932)
- main.exe (PID: 8300)
- main.exe (PID: 4620)
- loader.exe (PID: 444)
- loader.exe (PID: 7036)
- loader.exe (PID: 7468)
- loader.exe (PID: 8324)
- loader.exe (PID: 776)
- loader.exe (PID: 9116)
- loader.exe (PID: 5588)
- loader.exe (PID: 8620)
- loader.exe (PID: 7236)
- loader.exe (PID: 8520)
- loader.exe (PID: 2772)
- loader.exe (PID: 7956)
- loader.exe (PID: 7824)
- loader.exe (PID: 8984)
- loader.exe (PID: 7964)
- loader.exe (PID: 8056)
- loader.exe (PID: 4980)
- loader.exe (PID: 7828)
- loader.exe (PID: 7352)
- loader.exe (PID: 1616)
- loader.exe (PID: 8544)
- loader.exe (PID: 7424)
- loader.exe (PID: 4608)
- loader.exe (PID: 472)
- loader.exe (PID: 1132)
- loader.exe (PID: 7224)
- loader.exe (PID: 7292)
- loader.exe (PID: 7204)
- loader.exe (PID: 8736)
- loader.exe (PID: 1244)
- loader.exe (PID: 5084)
- loader.exe (PID: 3992)
- loader.exe (PID: 3888)
- loader.exe (PID: 8332)
- loader.exe (PID: 4424)
- loader.exe (PID: 8868)
- loader.exe (PID: 9164)
- loader.exe (PID: 7008)
- loader.exe (PID: 8988)
- loader.exe (PID: 2340)
- loader.exe (PID: 7792)
- loader.exe (PID: 8420)
- loader.exe (PID: 7464)
- loader.exe (PID: 7836)
- loader.exe (PID: 8336)
- loader.exe (PID: 3488)
- loader.exe (PID: 9136)
- loader.exe (PID: 8920)
- loader.exe (PID: 1012)
- loader.exe (PID: 5744)
- loader.exe (PID: 2780)
- loader.exe (PID: 2840)
- loader.exe (PID: 8224)
- loader.exe (PID: 7564)
- loader.exe (PID: 6124)
- loader.exe (PID: 8412)
- loader.exe (PID: 4304)
- loader.exe (PID: 6132)
- loader.exe (PID: 5308)
- loader.exe (PID: 5188)
- loader.exe (PID: 8260)
- loader.exe (PID: 3896)
- loader.exe (PID: 5484)
- loader.exe (PID: 5944)
- loader.exe (PID: 9072)
- loader.exe (PID: 1516)
- loader.exe (PID: 4052)
- loader.exe (PID: 7576)
- loader.exe (PID: 8840)
- loader.exe (PID: 5360)
- loader.exe (PID: 7780)
- loader.exe (PID: 1088)
- loader.exe (PID: 8116)
- loader.exe (PID: 7216)
- loader.exe (PID: 7680)
- loader.exe (PID: 7920)
- loader.exe (PID: 9068)
- loader.exe (PID: 8724)
- loader.exe (PID: 6476)
- loader.exe (PID: 1056)
- loader.exe (PID: 7928)
- loader.exe (PID: 7188)
- loader.exe (PID: 7940)
- loader.exe (PID: 240)
- loader.exe (PID: 7428)
- loader.exe (PID: 7372)
- loader.exe (PID: 6264)
- loader.exe (PID: 2408)
- loader.exe (PID: 8040)
- loader.exe (PID: 8660)
- loader.exe (PID: 5348)
- loader.exe (PID: 7352)
- loader.exe (PID: 8284)
- loader.exe (PID: 1748)
- loader.exe (PID: 1152)
- loader.exe (PID: 4692)
- loader.exe (PID: 7736)
- loader.exe (PID: 3960)
- loader.exe (PID: 8300)
- loader.exe (PID: 5364)
- loader.exe (PID: 2692)
- loader.exe (PID: 208)
- loader.exe (PID: 3364)
- loader.exe (PID: 7552)
- loader.exe (PID: 7584)
- loader.exe (PID: 3992)
- loader.exe (PID: 4000)
- loader.exe (PID: 7600)
- loader.exe (PID: 7848)
- loader.exe (PID: 4308)
- loader.exe (PID: 1852)
- loader.exe (PID: 8972)
- loader.exe (PID: 8488)
- loader.exe (PID: 7492)
- loader.exe (PID: 8636)
- loader.exe (PID: 5232)
- loader.exe (PID: 7792)
- loader.exe (PID: 8984)
- loader.exe (PID: 7836)
- loader.exe (PID: 8796)
- loader.exe (PID: 3900)
- loader.exe (PID: 8652)
- loader.exe (PID: 7944)
- loader.exe (PID: 7764)
- loader.exe (PID: 7932)
- loader.exe (PID: 8072)
- loader.exe (PID: 9188)
- loader.exe (PID: 2088)
- loader.exe (PID: 3888)
- loader.exe (PID: 6208)
- loader.exe (PID: 7284)
- loader.exe (PID: 448)
- loader.exe (PID: 8032)
- loader.exe (PID: 2812)
- loader.exe (PID: 4016)
- loader.exe (PID: 2420)
- loader.exe (PID: 5280)
- loader.exe (PID: 3100)
- loader.exe (PID: 1388)
- loader.exe (PID: 2616)
- loader.exe (PID: 8512)
- loader.exe (PID: 7008)
- loader.exe (PID: 7036)
- loader.exe (PID: 6416)
- loader.exe (PID: 3744)
- loader.exe (PID: 3480)
- loader.exe (PID: 5508)
- loader.exe (PID: 8552)
- loader.exe (PID: 7464)
- loader.exe (PID: 7172)
- loader.exe (PID: 8548)
- loader.exe (PID: 6184)
- loader.exe (PID: 8392)
- loader.exe (PID: 7624)
- loader.exe (PID: 8864)
- loader.exe (PID: 9028)
- loader.exe (PID: 6392)
- loader.exe (PID: 7928)
- loader.exe (PID: 9212)
- loader.exe (PID: 7204)
- loader.exe (PID: 9072)
- loader.exe (PID: 436)
- loader.exe (PID: 3160)
- loader.exe (PID: 7304)
- loader.exe (PID: 7812)
- loader.exe (PID: 8832)
- loader.exe (PID: 4696)
- loader.exe (PID: 7920)
- loader.exe (PID: 6964)
- loader.exe (PID: 3156)
- loader.exe (PID: 7860)
- loader.exe (PID: 8368)
- loader.exe (PID: 7412)
- loader.exe (PID: 3804)
- loader.exe (PID: 8756)
- loader.exe (PID: 1088)
- loader.exe (PID: 5800)
- loader.exe (PID: 4784)
- loader.exe (PID: 6244)
- loader.exe (PID: 9000)
- loader.exe (PID: 3900)
- loader.exe (PID: 7944)
- loader.exe (PID: 6068)
- loader.exe (PID: 8852)
- loader.exe (PID: 8300)
- loader.exe (PID: 3364)
- loader.exe (PID: 7416)
- loader.exe (PID: 8448)
- loader.exe (PID: 6960)
- loader.exe (PID: 2088)
- loader.exe (PID: 7952)
- loader.exe (PID: 8824)
- loader.exe (PID: 5384)
- loader.exe (PID: 8280)
- loader.exe (PID: 2104)
- loader.exe (PID: 7236)
- loader.exe (PID: 8716)
- loader.exe (PID: 9016)
- loader.exe (PID: 8456)
- loader.exe (PID: 7524)
- loader.exe (PID: 7328)
- loader.exe (PID: 7656)
- loader.exe (PID: 3300)
- loader.exe (PID: 5624)
- loader.exe (PID: 6344)
- loader.exe (PID: 8452)
- loader.exe (PID: 5744)
- loader.exe (PID: 5536)
- loader.exe (PID: 3264)
- loader.exe (PID: 908)
- loader.exe (PID: 7036)
- loader.exe (PID: 5680)
- loader.exe (PID: 2136)
- loader.exe (PID: 7716)
- loader.exe (PID: 8436)
- loader.exe (PID: 8356)
- loader.exe (PID: 6388)
- loader.exe (PID: 8256)
- loader.exe (PID: 5776)
- loader.exe (PID: 3276)
- loader.exe (PID: 6072)
- loader.exe (PID: 7776)
- loader.exe (PID: 7732)
- loader.exe (PID: 5360)
- loader.exe (PID: 6944)
- loader.exe (PID: 5756)
- loader.exe (PID: 7908)
- loader.exe (PID: 8864)
- loader.exe (PID: 6700)
- loader.exe (PID: 7464)
- loader.exe (PID: 2504)
- loader.exe (PID: 8480)
- loader.exe (PID: 1096)
- loader.exe (PID: 8108)
- loader.exe (PID: 8644)
- loader.exe (PID: 7432)
- loader.exe (PID: 744)
- loader.exe (PID: 6656)
- loader.exe (PID: 7500)
- loader.exe (PID: 776)
- loader.exe (PID: 7280)
- loader.exe (PID: 8064)
- loader.exe (PID: 7292)
- loader.exe (PID: 4688)
- loader.exe (PID: 7304)
- loader.exe (PID: 1004)
- loader.exe (PID: 2408)
- loader.exe (PID: 1660)
- loader.exe (PID: 5348)
- loader.exe (PID: 7452)
- loader.exe (PID: 4068)
- loader.exe (PID: 2108)
- loader.exe (PID: 7372)
- loader.exe (PID: 232)
- loader.exe (PID: 7920)
- loader.exe (PID: 8280)
- loader.exe (PID: 7876)
- loader.exe (PID: 7900)
- loader.exe (PID: 3888)
- loader.exe (PID: 8724)
- loader.exe (PID: 5036)
- loader.exe (PID: 7412)
- loader.exe (PID: 7720)
- loader.exe (PID: 8752)
- loader.exe (PID: 8048)
- loader.exe (PID: 3804)
- loader.exe (PID: 1072)
- loader.exe (PID: 8968)
- loader.exe (PID: 6708)
- loader.exe (PID: 2612)
- loader.exe (PID: 2088)
- loader.exe (PID: 8512)
- loader.exe (PID: 7084)
- loader.exe (PID: 7584)
- loader.exe (PID: 8892)
- loader.exe (PID: 7956)
- loader.exe (PID: 6040)
- loader.exe (PID: 1328)
- loader.exe (PID: 8796)
- loader.exe (PID: 8044)
- loader.exe (PID: 8760)
- loader.exe (PID: 4304)
- loader.exe (PID: 8788)
- loader.exe (PID: 8356)
- loader.exe (PID: 2216)
- loader.exe (PID: 9104)
- loader.exe (PID: 6072)
- loader.exe (PID: 7648)
- loader.exe (PID: 9048)
- loader.exe (PID: 3024)
- loader.exe (PID: 8000)
- loader.exe (PID: 5084)
- loader.exe (PID: 8704)
- loader.exe (PID: 7468)
- loader.exe (PID: 7420)
- loader.exe (PID: 2656)
- loader.exe (PID: 2504)
- loader.exe (PID: 8088)
- loader.exe (PID: 9012)
- loader.exe (PID: 6228)
- loader.exe (PID: 8864)
- loader.exe (PID: 8444)
- loader.exe (PID: 7840)
- loader.exe (PID: 7428)
- loader.exe (PID: 776)
- loader.exe (PID: 744)
- loader.exe (PID: 7316)
- loader.exe (PID: 8904)
- loader.exe (PID: 5112)
- loader.exe (PID: 8624)
- loader.exe (PID: 7792)
- loader.exe (PID: 2800)
- loader.exe (PID: 8408)
- loader.exe (PID: 7732)
- loader.exe (PID: 5772)
- loader.exe (PID: 8424)
- loader.exe (PID: 5556)
- loader.exe (PID: 3332)
Reads Environment values
- identity_helper.exe (PID: 4120)
Application launched itself
- msedge.exe (PID: 1812)
- firefox.exe (PID: 7908)
- firefox.exe (PID: 8380)
Reads the computer name
- identity_helper.exe (PID: 4120)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6112)
Attempting to use file storage service
- msedge.exe (PID: 7364)
Reads the software policy settings
- slui.exe (PID: 7684)
The sample compiled with english language support
- loader.exe (PID: 7900)
- dwm.exe (PID: 6656)
- Built.exe (PID: 5360)
- Built.exe (PID: 5364)
- main.exe (PID: 6124)
- Built.exe (PID: 744)
- loader.exe (PID: 9004)
- main.exe (PID: 7804)
- main.exe (PID: 6372)
- loader.exe (PID: 8976)
- Built.exe (PID: 8864)
- Built.exe (PID: 7540)
- Built.exe (PID: 2316)
- Built.exe (PID: 1164)
- main.exe (PID: 7932)
- main.exe (PID: 4620)
- main.exe (PID: 8300)
- main.exe (PID: 6872)
- loader.exe (PID: 1040)
- main.exe (PID: 7268)
- Built.exe (PID: 2476)
- Built.exe (PID: 8188)
The Powershell gets current clipboard
- powershell.exe (PID: 8720)
- powershell.exe (PID: 8364)
- powershell.exe (PID: 2236)
- powershell.exe (PID: 7736)
Checks the directory tree
- tree.com (PID: 9056)
- tree.com (PID: 8816)
- tree.com (PID: 4868)
- tree.com (PID: 8988)
- tree.com (PID: 8528)
- tree.com (PID: 9152)
- tree.com (PID: 5968)
- tree.com (PID: 4424)
- tree.com (PID: 8756)
- tree.com (PID: 8168)
- tree.com (PID: 6760)
- tree.com (PID: 7348)
- tree.com (PID: 4464)
- tree.com (PID: 8592)
- tree.com (PID: 7552)
- tree.com (PID: 6820)
- tree.com (PID: 8624)
- tree.com (PID: 2064)
Themida protector has been detected
- loader.exe (PID: 7900)
PyInstaller has been detected (YARA)
- Built.exe (PID: 5360)
Attempting to use instant messaging service
- svchost.exe (PID: 2196)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 6980)
- getmac.exe (PID: 5404)
- getmac.exe (PID: 7636)
- getmac.exe (PID: 8384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
1 085
Monitored processes
937
Malicious processes
48
Suspicious processes
15
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | C:\WINDOWS\system32\cmd.exe /c "tree /A /F" | C:\Windows\System32\cmd.exe | — | Built.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | "C:\Users\admin\Desktop\loader.exe" | C:\Users\admin\Desktop\loader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 208 | "C:\Users\admin\Desktop\loader.exe" | C:\Users\admin\Desktop\loader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 232 | "C:\Users\admin\Desktop\loader.exe" | C:\Users\admin\Desktop\loader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -RemoveDefinitions -All | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Malware Protection Command Line Utility Exit code: 0 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | C:\WINDOWS\system32\cmd.exe /c "powershell Get-ItemPropertyValue -Path 'HKLM:System\CurrentControlSet\Control\Session Manager\Environment' -Name PROCESSOR_IDENTIFIER" | C:\Windows\System32\cmd.exe | — | Built.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | "C:\Users\admin\Desktop\loader.exe" | C:\Users\admin\Desktop\loader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
267 725
Read events
267 554
Write events
168
Delete events
3
Modification events
| (PID) Process: | (1812) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1812) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1812) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1812) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1812) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 2E5B8E8CEF932F00 | |||
| (PID) Process: | (1812) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 3E79968CEF932F00 | |||
| (PID) Process: | (1812) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328332 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {64C7A123-9CFE-4B9E-967A-1EF7F6D7A94D} | |||
| (PID) Process: | (1812) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328332 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {36F79B97-3996-440C-A2C6-618A04D52C4D} | |||
| (PID) Process: | (1812) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328332 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {22F2DE77-73FA-432C-8D08-A9FA72456397} | |||
| (PID) Process: | (1812) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328332 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C431E2B8-0763-4F15-89E7-4C2201D970A6} | |||
Executable files
574
Suspicious files
809
Text files
306
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1812 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10ad97.TMP | — | |
MD5:— | SHA256:— | |||
| 1812 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1812 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10ada7.TMP | — | |
MD5:— | SHA256:— | |||
| 1812 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1812 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10adb6.TMP | — | |
MD5:— | SHA256:— | |||
| 1812 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10ada7.TMP | — | |
MD5:— | SHA256:— | |||
| 1812 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1812 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1812 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10adc6.TMP | — | |
MD5:— | SHA256:— | |||
| 1812 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
51
TCP/UDP connections
211
DNS requests
274
Threats
61
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5744 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1747803060&P2=404&P3=2&P4=fCZdco5KzMeaWmWGCzlCC0%2fRnmc6TcCW28KK%2f1wqPTkdQo5NiWPglP6NIj6wzWsXL8a%2fPnAXSXj%2b0t8h%2fJMy%2fQ%3d%3d | unknown | — | — | whitelisted |
3332 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5744 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1747803060&P2=404&P3=2&P4=fCZdco5KzMeaWmWGCzlCC0%2fRnmc6TcCW28KK%2f1wqPTkdQo5NiWPglP6NIj6wzWsXL8a%2fPnAXSXj%2b0t8h%2fJMy%2fQ%3d%3d | unknown | — | — | whitelisted |
3332 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5744 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/3aeadfbf-fadd-43ac-a5d9-c143db5f63d8?P1=1747803066&P2=404&P3=2&P4=maoD1x7X2ahIJwDUEe3Vk%2biPMlXwlw9kiEmfu%2bVqhU4BgsH%2bf24cRSn4u0VWpMvpBGCn6xeTNW%2fQxSIxsRaYow%3d%3d | unknown | — | — | whitelisted |
5744 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1747803060&P2=404&P3=2&P4=fCZdco5KzMeaWmWGCzlCC0%2fRnmc6TcCW28KK%2f1wqPTkdQo5NiWPglP6NIj6wzWsXL8a%2fPnAXSXj%2b0t8h%2fJMy%2fQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1812 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7364 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7364 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7364 | msedge.exe | 13.107.253.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
gofile.io |
| whitelisted |
business.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7364 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7364 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7364 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
7364 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7364 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7364 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
7364 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7364 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7364 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7364 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |