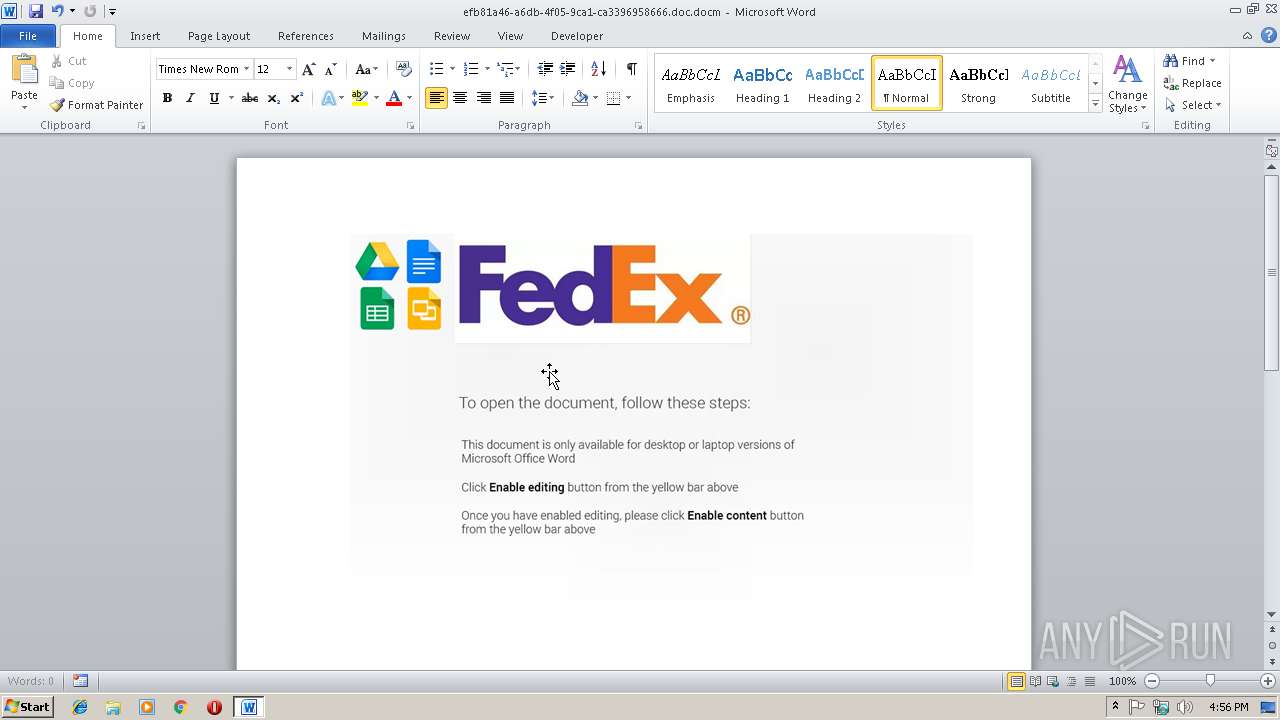
| File name: | 6e3409145d99f5d3bf14772427ba917ed0214d6f|invoice_519834.doc |
| Full analysis: | https://app.any.run/tasks/c16e2c9b-c5fe-4a35-90f2-05efd28b3cc5 |
| Verdict: | Malicious activity |
| Threats: | Hancitor was created in 2014 to drop other malware on infected machines. It is also known as Tordal and Chanitor. This malware is available as a service which makes it accessible tools to criminals and contributes to the popularity of this virus. |
| Analysis date: | December 06, 2018, 16:56:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
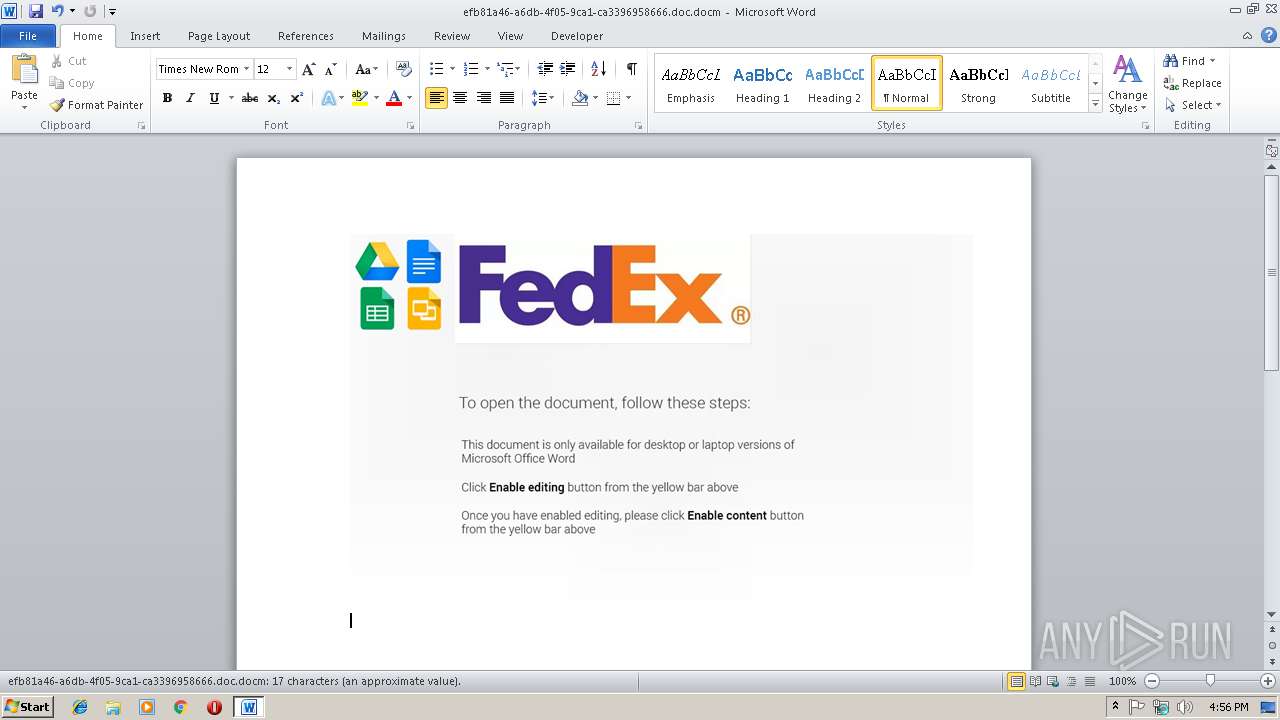
| File info: | Microsoft Word 2007+ |
| MD5: | 216272021F421D0222D1EAB86D362C1E |
| SHA1: | 6E3409145D99F5D3BF14772427BA917ED0214D6F |
| SHA256: | C1086F8F8C7600FC384E3FBDF89CEA316F6746C1D0D50DCDE2724679733F3343 |
| SSDEEP: | 6144:tBpplRadx9txUgx6IOc0YBHldKruHv0TAyFuR+goXK:fpp6d5xUgnOytldTHv+uUK |
MALICIOUS
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2968)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2968)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2968)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 2744)
Application was dropped or rewritten from another process
- 6.pif (PID: 3472)
HANCITOR was detected
- 6.pif (PID: 3472)
Connects to CnC server
- 6.pif (PID: 3472)
SUSPICIOUS
Starts application with an unusual extension
- cmd.exe (PID: 2744)
Checks for external IP
- 6.pif (PID: 3472)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2968)
Dropped object may contain Bitcoin addresses
- WINWORD.EXE (PID: 2968)
Creates files in the user directory
- WINWORD.EXE (PID: 2968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x112fb249 |
| ZipCompressedSize: | 476 |
| ZipUncompressedSize: | 2075 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | 8.4 hours |
| Pages: | 1 |
| Words: | 3 |
| Characters: | 18 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 20 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 15 |
| Keywords: | - |
| LastModifiedBy: | user |
| RevisionNumber: | 343 |
| CreateDate: | 2018:10:11 14:43:00Z |
| ModifyDate: | 2018:12:06 14:02:00Z |
XMP
| Title: | |
|---|---|
| Subject: | - |
| Creator: | 444555 |
| Description: | - |
Total processes
37
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2260 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2744 | cmd.exe /c ping localhost -n 100 && C:\Users\admin\AppData\Local\Temp\6.pif | C:\Windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2968 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\efb81a46-a6db-4f05-9ca1-ca3396958666.doc.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3320 | ping localhost -n 100 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3472 | C:\Users\admin\AppData\Local\Temp\6.pif | C:\Users\admin\AppData\Local\Temp\6.pif | cmd.exe | ||||||||||||
User: admin Company: PostgreSQL Global Development Group Integrity Level: MEDIUM Description: initdb - initialize a new database cluster Exit code: 0 Version: 9.1.2 Modules
| |||||||||||||||
Total events
1 388
Read events
964
Write events
413
Delete events
11
Modification events
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | :d? |
Value: 3A643F00980B0000010000000000000000000000 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1300627479 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1300627600 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1300627601 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 980B0000D6D41FAC848DD40100000000 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | be? |
Value: 62653F00980B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | be? |
Value: 62653F00980B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
2
Text files
0
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA83A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\5C.pif | — | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~WRD0000.tmp | — | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\81D98FC9.png | — | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{D474EC15-43CC-46B9-A169-BE006E381D8F}.tmp | — | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{E91EB0B1-4AE1-4197-92A0-BA5C3852708D}.tmp | — | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFFFA29DCCA7D878FE.TMP | — | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{14FDD902-DC1A-4EAA-8EF4-A54138A5EE4F}.tmp | — | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
8
DNS requests
6
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3472 | 6.pif | GET | 404 | 54.204.36.156:80 | http://api.ipify.org/ | US | xml | 345 b | shared |
3472 | 6.pif | POST | 404 | 146.185.254.169:80 | http://howheidnot.ru/4/forum.php | RU | xml | 345 b | malicious |
3472 | 6.pif | POST | 404 | 191.101.20.16:80 | http://tertsahedwith.com/4/forum.php | NL | xml | 345 b | malicious |
3472 | 6.pif | GET | 404 | 54.204.36.156:80 | http://api.ipify.org/ | US | xml | 345 b | shared |
3472 | 6.pif | POST | 404 | 146.185.254.169:80 | http://dingtittohi.ru/4/forum.php | RU | xml | 345 b | malicious |
3472 | 6.pif | POST | 404 | 191.101.20.16:80 | http://tertsahedwith.com/4/forum.php | NL | xml | 345 b | malicious |
3472 | 6.pif | POST | 404 | 146.185.254.169:80 | http://howheidnot.ru/4/forum.php | RU | xml | 345 b | malicious |
3472 | 6.pif | POST | 404 | 146.185.254.169:80 | http://dingtittohi.ru/4/forum.php | RU | xml | 345 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3472 | 6.pif | 54.204.36.156:80 | api.ipify.org | Amazon.com, Inc. | US | malicious |
3472 | 6.pif | 191.101.20.16:80 | tertsahedwith.com | Swiftway Sp. z o.o. | NL | malicious |
3472 | 6.pif | 146.185.254.169:80 | howheidnot.ru | MnogoByte LLC | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.ipify.org |
| shared |
tertsahedwith.com |
| malicious |
howheidnot.ru |
| malicious |
dingtittohi.ru |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3472 | 6.pif | Potential Corporate Privacy Violation | ET POLICY External IP Lookup api.ipify.org |
3472 | 6.pif | A Network Trojan was detected | MALWARE [PTsecurity] Hancitor POST Data send |
3472 | 6.pif | A Network Trojan was detected | MALWARE [PTsecurity] Hancitor POST Data send |
3472 | 6.pif | A Network Trojan was detected | MALWARE [PTsecurity] Hancitor POST Data send |
3472 | 6.pif | A Network Trojan was detected | MALWARE [PTsecurity] Hancitor POST Data send |
3472 | 6.pif | A Network Trojan was detected | MALWARE [PTsecurity] Hancitor POST Data send |
3472 | 6.pif | A Network Trojan was detected | MALWARE [PTsecurity] Hancitor POST Data send |
3472 | 6.pif | Potential Corporate Privacy Violation | ET POLICY External IP Lookup api.ipify.org |
6 ETPRO signatures available at the full report
Process | Message |
|---|---|
6.pif | gIpVG |