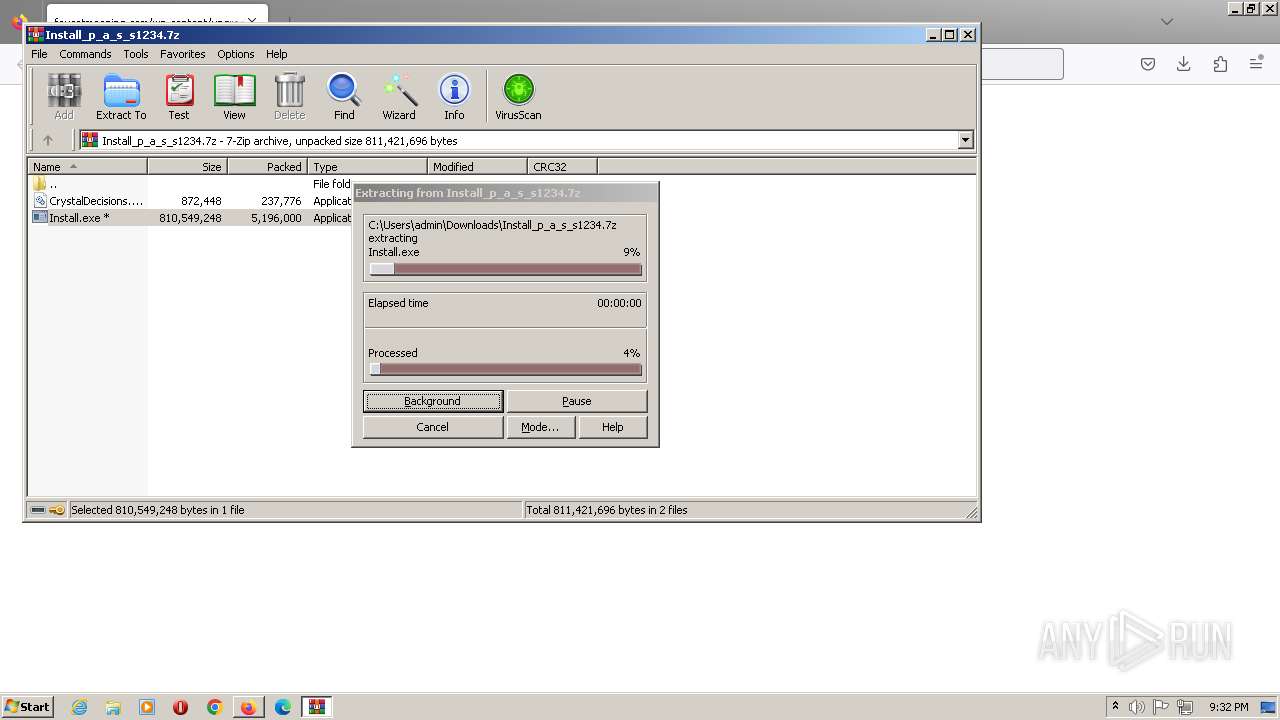
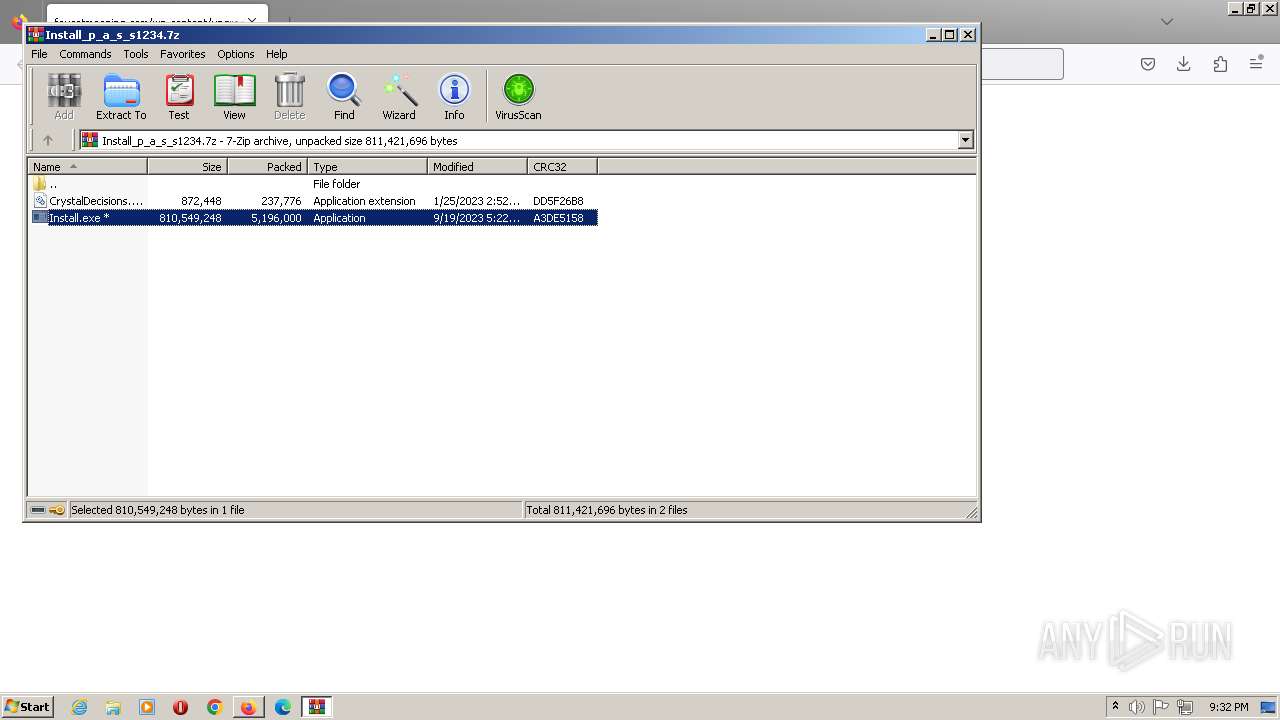
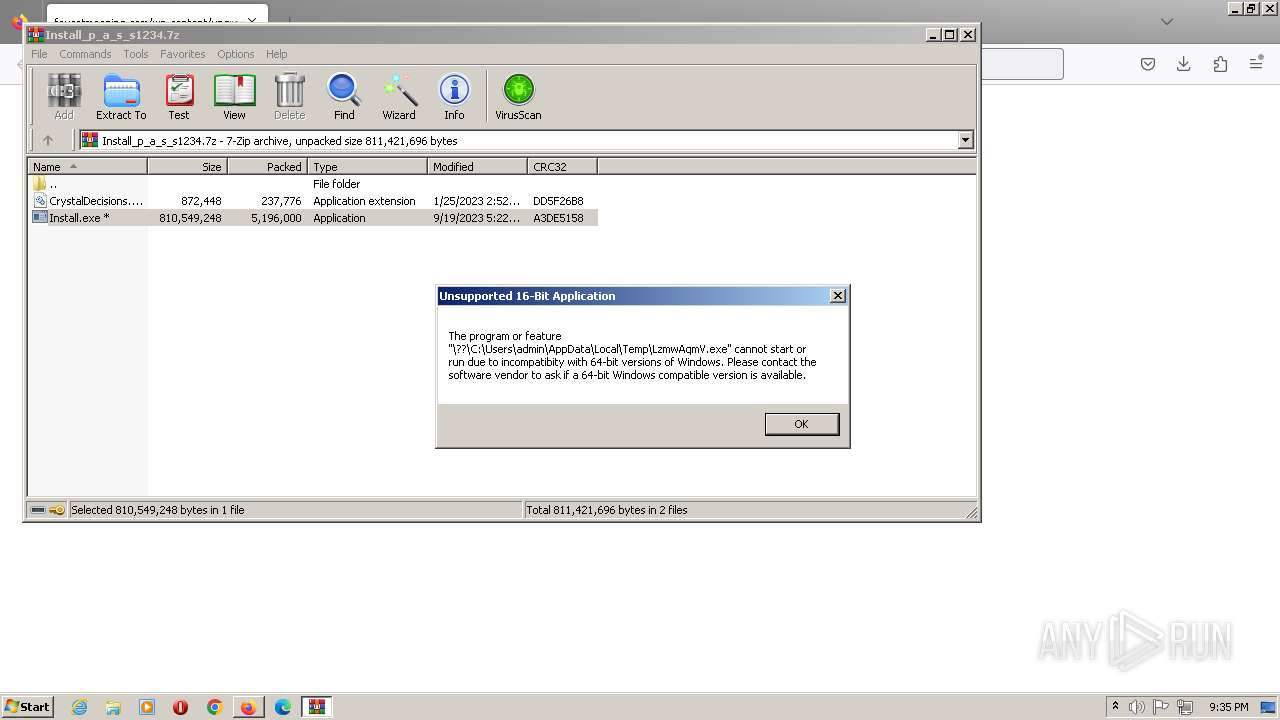
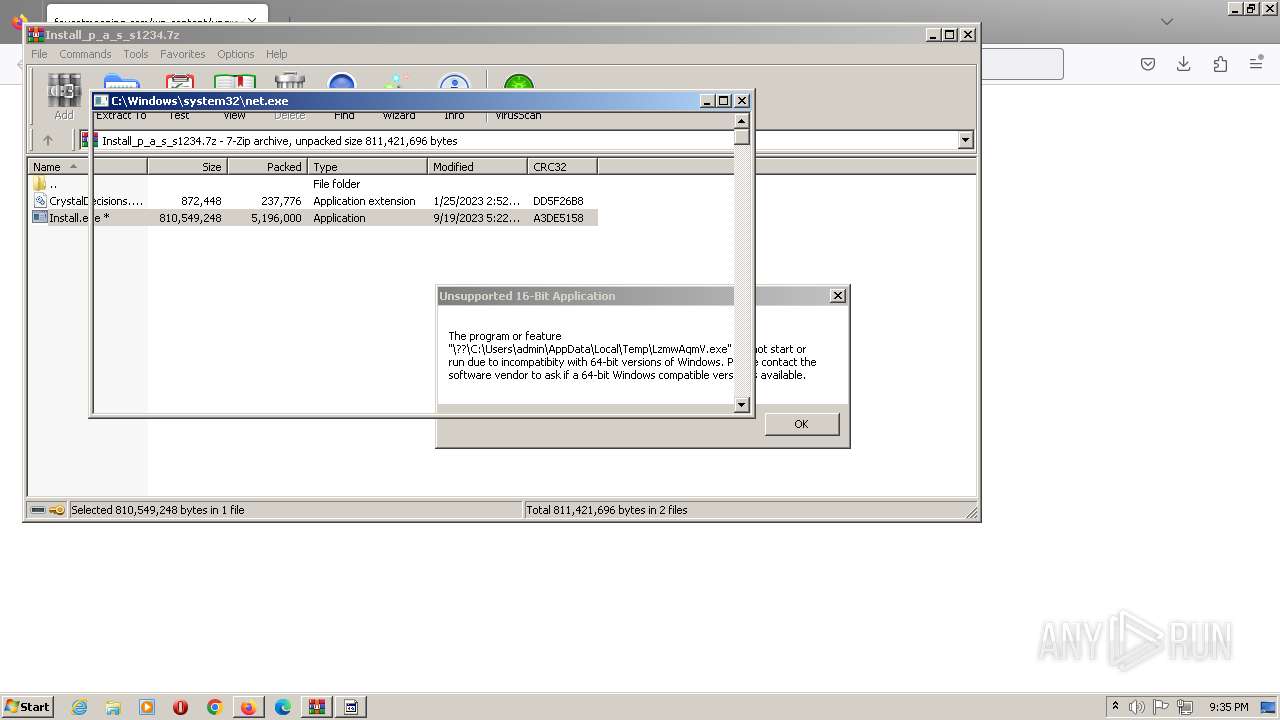
| URL: | https://faucetmeaning.com/wp-content/upgrade/Install_p_a_s_s1234.7z |
| Full analysis: | https://app.any.run/tasks/dbcda7fb-3902-4224-b5bc-3283e0cba405 |
| Verdict: | Malicious activity |
| Threats: | Arkei is a stealer type malware capable of collecting passwords, autosaved forms, cryptocurrency wallet credentials, and files. |
| Analysis date: | September 19, 2023, 21:32:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | F0944A3033642C3763328E2194E62B52 |
| SHA1: | A92A7A6D37088AEBD6293821284A08E6691987A4 |
| SHA256: | C0A51F001E2DC025473A258297FA72A083B30A1B0CF6A97533C9719BE417729F |
| SSDEEP: | 3:N8PvFVOlAQhLWp6bMSfn:2lVOlAuG6bMSfn |
MALICIOUS
Creates a writable file the system directory
- Install.exe (PID: 1896)
Connects to the CnC server
- Install.exe (PID: 1896)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- AFAi_TyaIZqk3YWnatpVYraH.exe (PID: 3208)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- AppLaunch.exe (PID: 2256)
- ZQNo7PHSKBcyLZhb1qKFv2nc.exe (PID: 2856)
- vbc.exe (PID: 1956)
- AppLaunch.exe (PID: 1940)
- sG8cXiu7JNY1smF9He2SCSGn.exe (PID: 2980)
- AppLaunch.exe (PID: 2592)
- 5A3L2ZoV7_n9OkPbNmjiFxO9.exe (PID: 1740)
- explorer.exe (PID: 1924)
- build2.exe (PID: 5044)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- aafg31.exe (PID: 5056)
- jqjsWQVm2aXONVycaGyt0KIJ.exe (PID: 3360)
- vbc.exe (PID: 5704)
- _vbXuFVL7PbRpardnWhipOYA.exe (PID: 4236)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
- _PPPVsCZWCuQ2S4cszbSdmOA.exe (PID: 4340)
- tIzi73bQauJPYLVENV75Tj3d.exe (PID: 4292)
- build2.exe (PID: 4540)
PRIVATELOADER was detected
- Install.exe (PID: 1896)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
Application was dropped or rewritten from another process
- 5A3L2ZoV7_n9OkPbNmjiFxO9.exe (PID: 1740)
- Y56MhtcPcgngA56Qpk7Xz1yR.exe (PID: 552)
- esPyD7Irgy6SzyVOsGf3XT2J.exe (PID: 2396)
- AFAi_TyaIZqk3YWnatpVYraH.exe (PID: 3208)
- sG8cXiu7JNY1smF9He2SCSGn.exe (PID: 2980)
- Jx98dOvw1Su_I6tKATXUlM08.exe (PID: 4080)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- R2T5csoyogKb7ajv22GWjq3s.exe (PID: 3260)
- K6Vu_cZajfv1W3nI4NlZYzbh.exe (PID: 3340)
- KIgzZ8s1_785xe5A_9QIzhfA.exe (PID: 1680)
- 8LT6Vq7lNWhihsyST13sWVT2.exe (PID: 2468)
- hxtidvtb.exe (PID: 4440)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 2816)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 3436)
- HpenOM8oqWCth9mMurN77Fxu.exe (PID: 1760)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 4904)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 1416)
- build2.exe (PID: 4304)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- build3.exe (PID: 5400)
- build2.exe (PID: 5044)
- F921.exe (PID: 5820)
- F921.exe (PID: 5984)
- F921.exe (PID: 4944)
- F921.exe (PID: 2232)
- bDeqhhSqnBxlJYCtvAEtZxPG.exe (PID: 5764)
- toolspub2.exe (PID: 5924)
- toolspub2.exe (PID: 5896)
- build2.exe (PID: 6040)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 2636)
- 266D.exe (PID: 3696)
- build3.exe (PID: 4800)
- kos1.exe (PID: 3408)
- aafg31.exe (PID: 5056)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 6116)
- set16.exe (PID: 4980)
- xZDdU5pql_TUqJHTbOiy5rAX.exe (PID: 4772)
- NiIqH6ivYkmMPpP4S4zy7GNy.exe (PID: 2832)
- mA8reEJShwkAWqA5Ic5bzSMv.exe (PID: 4632)
- jqjsWQVm2aXONVycaGyt0KIJ.exe (PID: 3360)
- kos.exe (PID: 2736)
- K8zm6o6gMji4elFAqugAFfSF.exe (PID: 5444)
- mstsca.exe (PID: 3824)
- previewer.exe (PID: 5340)
- previewer.exe (PID: 4800)
- 6G0qbEivOJjIpPaiLB_CQcOl.exe (PID: 3200)
- toolspub2.exe (PID: 2856)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 2316)
- toolspub2.exe (PID: 3316)
- kos1.exe (PID: 5372)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 4060)
- build2.exe (PID: 4540)
Actions looks like stealing of personal data
- Install.exe (PID: 1896)
- 8LT6Vq7lNWhihsyST13sWVT2.exe (PID: 2468)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- 5A3L2ZoV7_n9OkPbNmjiFxO9.exe (PID: 1740)
- sG8cXiu7JNY1smF9He2SCSGn.exe (PID: 2980)
- AppLaunch.exe (PID: 1940)
- ZQNo7PHSKBcyLZhb1qKFv2nc.exe (PID: 2856)
- vbc.exe (PID: 1956)
- AppLaunch.exe (PID: 2592)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
- jqjsWQVm2aXONVycaGyt0KIJ.exe (PID: 3360)
- _PPPVsCZWCuQ2S4cszbSdmOA.exe (PID: 4340)
- aafg31.exe (PID: 5056)
- _vbXuFVL7PbRpardnWhipOYA.exe (PID: 4236)
- tIzi73bQauJPYLVENV75Tj3d.exe (PID: 4292)
- vbc.exe (PID: 5704)
- build2.exe (PID: 4540)
- build2.exe (PID: 5044)
Registers / Runs the DLL via REGSVR32.EXE
- K6Vu_cZajfv1W3nI4NlZYzbh.exe (PID: 3340)
- explorer.exe (PID: 1924)
- NiIqH6ivYkmMPpP4S4zy7GNy.exe (PID: 2832)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 3472)
- regsvr32.exe (PID: 5128)
- build2.exe (PID: 5044)
- WerFault.exe (PID: 5368)
- is-TDC7F.tmp (PID: 5280)
- regsvr32.exe (PID: 6016)
- WerFault.exe (PID: 3936)
- build2.exe (PID: 4540)
STEALC was detected
- AFAi_TyaIZqk3YWnatpVYraH.exe (PID: 3208)
- AppLaunch.exe (PID: 2256)
Runs injected code in another process
- Y56MhtcPcgngA56Qpk7Xz1yR.exe (PID: 552)
Application was injected by another process
- explorer.exe (PID: 1924)
Create files in the Startup directory
- HpenOM8oqWCth9mMurN77Fxu.exe (PID: 1760)
Uses Task Scheduler to run other applications
- HpenOM8oqWCth9mMurN77Fxu.exe (PID: 1760)
- build3.exe (PID: 5400)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- build3.exe (PID: 4800)
- mstsca.exe (PID: 3824)
RISEPRO was detected
- HpenOM8oqWCth9mMurN77Fxu.exe (PID: 1760)
PRIVATELOADER detected by memory dumps
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
Uses Task Scheduler to autorun other applications
- HpenOM8oqWCth9mMurN77Fxu.exe (PID: 1760)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
REDLINE was detected
- sG8cXiu7JNY1smF9He2SCSGn.exe (PID: 2980)
- ZQNo7PHSKBcyLZhb1qKFv2nc.exe (PID: 2856)
- vbc.exe (PID: 1956)
- AppLaunch.exe (PID: 1940)
- AppLaunch.exe (PID: 2592)
- vbc.exe (PID: 5704)
- _vbXuFVL7PbRpardnWhipOYA.exe (PID: 4236)
- _PPPVsCZWCuQ2S4cszbSdmOA.exe (PID: 4340)
- tIzi73bQauJPYLVENV75Tj3d.exe (PID: 4292)
REDLINE detected by memory dumps
- sG8cXiu7JNY1smF9He2SCSGn.exe (PID: 2980)
- AppLaunch.exe (PID: 1940)
- ZQNo7PHSKBcyLZhb1qKFv2nc.exe (PID: 2856)
- vbc.exe (PID: 1956)
- vbc.exe (PID: 5704)
- _PPPVsCZWCuQ2S4cszbSdmOA.exe (PID: 4340)
- _vbXuFVL7PbRpardnWhipOYA.exe (PID: 4236)
- tIzi73bQauJPYLVENV75Tj3d.exe (PID: 4292)
POVERTYSTEALER was detected
- 8LT6Vq7lNWhihsyST13sWVT2.exe (PID: 2468)
Stop is detected
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 1416)
- F921.exe (PID: 2232)
FABOOKIE was detected
- 5A3L2ZoV7_n9OkPbNmjiFxO9.exe (PID: 1740)
- aafg31.exe (PID: 5056)
- jqjsWQVm2aXONVycaGyt0KIJ.exe (PID: 3360)
Unusual connection from system programs
- vbc.exe (PID: 1956)
- vbc.exe (PID: 5704)
Steals credentials from Web Browsers
- vbc.exe (PID: 1956)
- AppLaunch.exe (PID: 2592)
- AppLaunch.exe (PID: 1940)
- ZQNo7PHSKBcyLZhb1qKFv2nc.exe (PID: 2856)
- build2.exe (PID: 5044)
- _vbXuFVL7PbRpardnWhipOYA.exe (PID: 4236)
- tIzi73bQauJPYLVENV75Tj3d.exe (PID: 4292)
- vbc.exe (PID: 5704)
- _PPPVsCZWCuQ2S4cszbSdmOA.exe (PID: 4340)
- build2.exe (PID: 4540)
SMOKE was detected
- explorer.exe (PID: 1924)
ARKEI was detected
- build2.exe (PID: 5044)
- build2.exe (PID: 4540)
VIDAR was detected
- build2.exe (PID: 5044)
- build2.exe (PID: 4540)
Steals credentials
- build2.exe (PID: 5044)
- build2.exe (PID: 4540)
ARKEI detected by memory dumps
- build2.exe (PID: 5044)
RACCOONCLIPPER detected by memory dumps
- build3.exe (PID: 4800)
- mstsca.exe (PID: 3824)
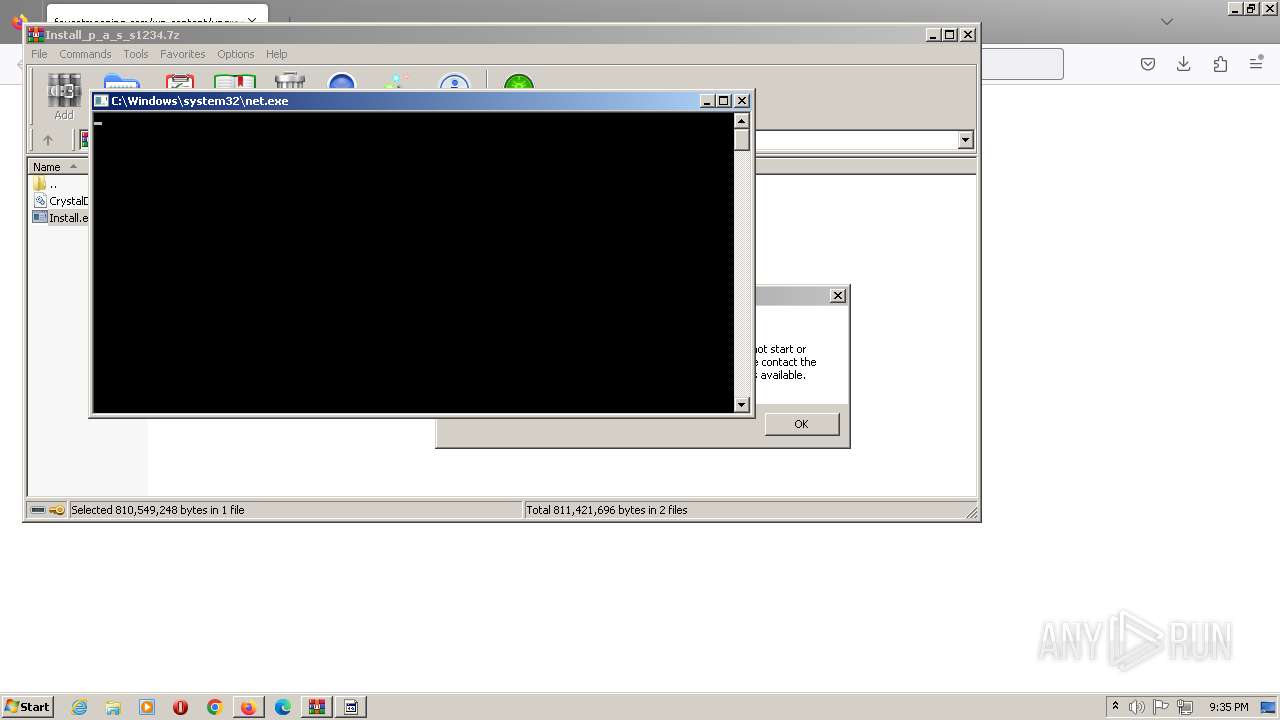
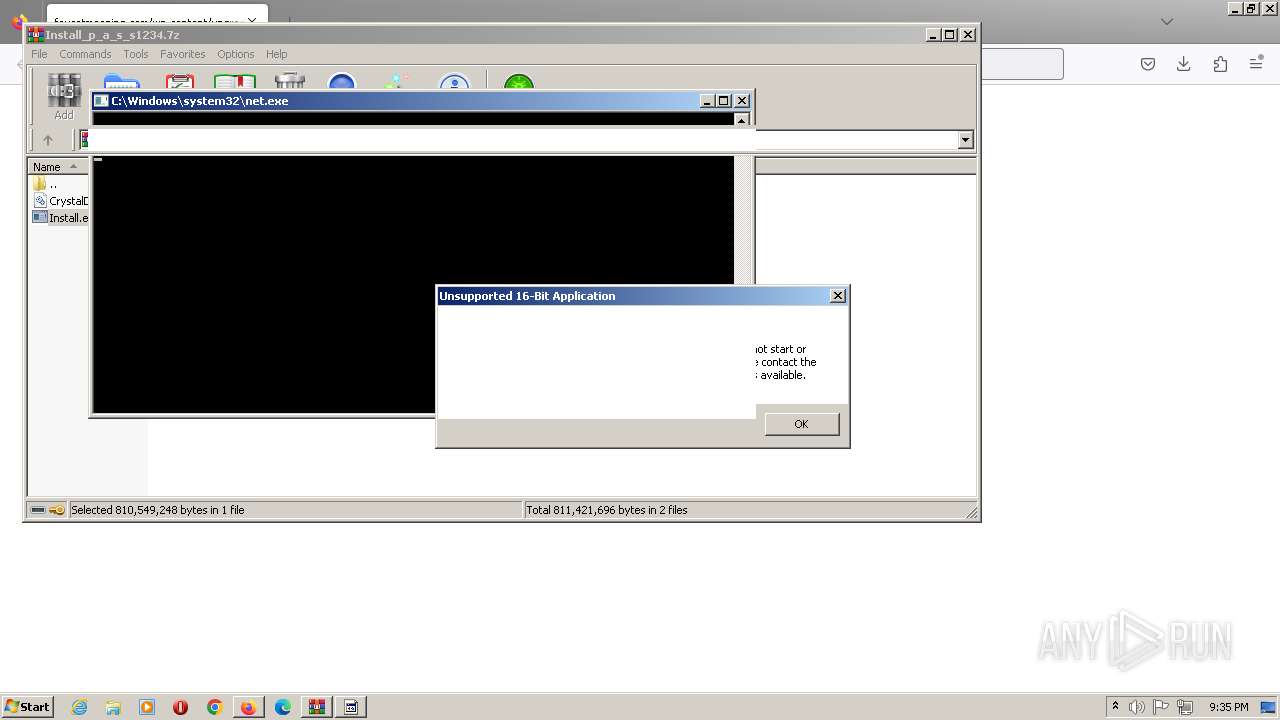
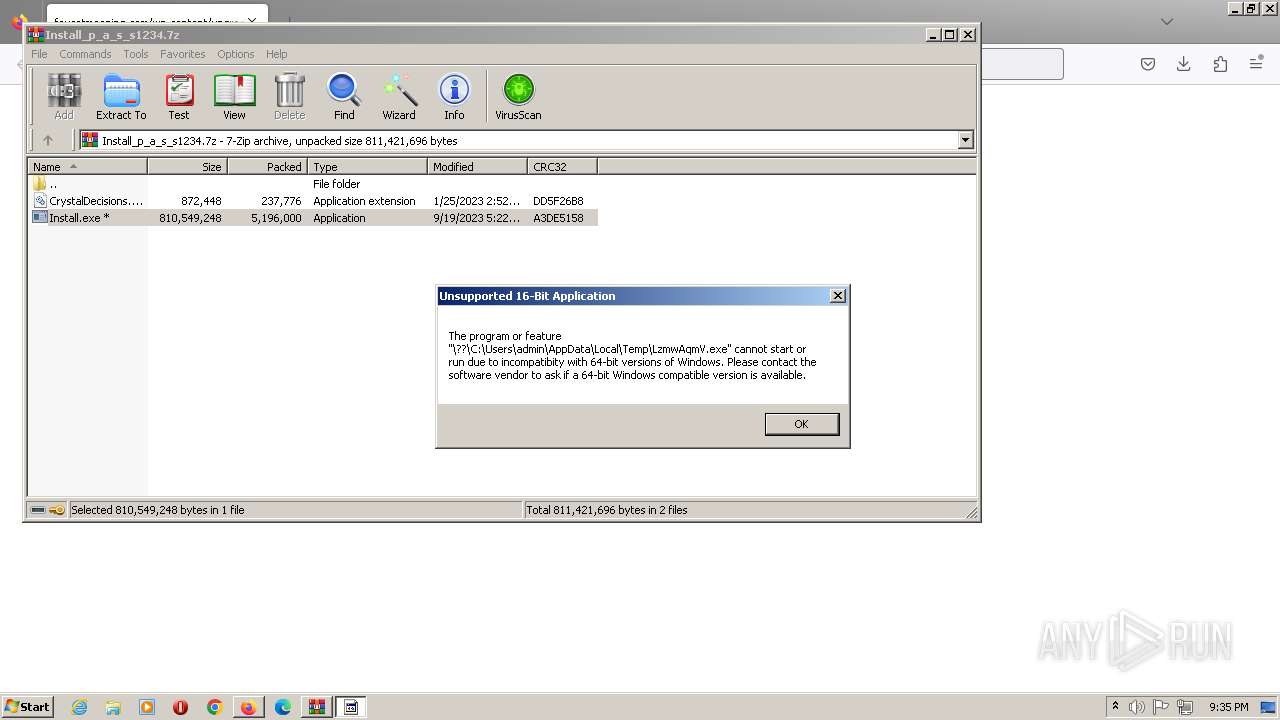
The DLL Hijacking
- WerFault.exe (PID: 5368)
- WerFault.exe (PID: 3936)
SUSPICIOUS
Reads the BIOS version
- Install.exe (PID: 1896)
Executes as Windows Service
- raserver.exe (PID: 1728)
- hxtidvtb.exe (PID: 4440)
- raserver.exe (PID: 5620)
- raserver.exe (PID: 5604)
- raserver.exe (PID: 4088)
Connects to the server without a host name
- Install.exe (PID: 1896)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- AppLaunch.exe (PID: 2256)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- explorer.exe (PID: 1924)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
Reads settings of System Certificates
- Install.exe (PID: 1896)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- 5A3L2ZoV7_n9OkPbNmjiFxO9.exe (PID: 1740)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 2816)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 1416)
- build2.exe (PID: 5044)
- F921.exe (PID: 5984)
- F921.exe (PID: 2232)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- aafg31.exe (PID: 5056)
- kos.exe (PID: 2736)
- jqjsWQVm2aXONVycaGyt0KIJ.exe (PID: 3360)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
- build2.exe (PID: 4540)
Checks Windows Trust Settings
- Install.exe (PID: 1896)
- 5A3L2ZoV7_n9OkPbNmjiFxO9.exe (PID: 1740)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 2816)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 1416)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- build2.exe (PID: 5044)
- F921.exe (PID: 5984)
- F921.exe (PID: 2232)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- aafg31.exe (PID: 5056)
- jqjsWQVm2aXONVycaGyt0KIJ.exe (PID: 3360)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
- build2.exe (PID: 4540)
Reads security settings of Internet Explorer
- Install.exe (PID: 1896)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 2816)
- 5A3L2ZoV7_n9OkPbNmjiFxO9.exe (PID: 1740)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 1416)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- build2.exe (PID: 5044)
- F921.exe (PID: 5984)
- F921.exe (PID: 2232)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- aafg31.exe (PID: 5056)
- jqjsWQVm2aXONVycaGyt0KIJ.exe (PID: 3360)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
- build2.exe (PID: 4540)
Process requests binary or script from the Internet
- Install.exe (PID: 1896)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 1416)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- F921.exe (PID: 2232)
- explorer.exe (PID: 1924)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
Adds/modifies Windows certificates
- WinRAR.exe (PID: 3468)
- Install.exe (PID: 1896)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 3436)
Checks for external IP
- Install.exe (PID: 1896)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
Reads the Internet Settings
- Install.exe (PID: 1896)
- 5A3L2ZoV7_n9OkPbNmjiFxO9.exe (PID: 1740)
- AFAi_TyaIZqk3YWnatpVYraH.exe (PID: 3208)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 2816)
- K6Vu_cZajfv1W3nI4NlZYzbh.exe (PID: 3340)
- KIgzZ8s1_785xe5A_9QIzhfA.exe (PID: 1680)
- AppLaunch.exe (PID: 2256)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 1416)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- build2.exe (PID: 5044)
- F921.exe (PID: 5984)
- F921.exe (PID: 2232)
- bDeqhhSqnBxlJYCtvAEtZxPG.exe (PID: 5764)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- 266D.exe (PID: 3696)
- aafg31.exe (PID: 5056)
- kos1.exe (PID: 3408)
- jqjsWQVm2aXONVycaGyt0KIJ.exe (PID: 3360)
- kos.exe (PID: 2736)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
- NiIqH6ivYkmMPpP4S4zy7GNy.exe (PID: 2832)
- _vbXuFVL7PbRpardnWhipOYA.exe (PID: 4236)
- 6G0qbEivOJjIpPaiLB_CQcOl.exe (PID: 3200)
- build2.exe (PID: 4540)
- previewer.exe (PID: 4800)
Application launched itself
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 3436)
- 4qWayS4NWxNACgKi6RtTDP_u.exe (PID: 3684)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 2816)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 4904)
- build2.exe (PID: 4304)
- F921.exe (PID: 5820)
- F921.exe (PID: 5984)
- F921.exe (PID: 4944)
- toolspub2.exe (PID: 5896)
- toolspub2.exe (PID: 2856)
- build2.exe (PID: 6040)
The process executes VB scripts
- DVNTebtS22luUiiCxmHmtwQ5.exe (PID: 3016)
- mA8reEJShwkAWqA5Ic5bzSMv.exe (PID: 4632)
The process verifies whether the antivirus software is installed
- R2T5csoyogKb7ajv22GWjq3s.exe (PID: 3260)
- GoogleUpdate.exe (PID: 4704)
Starts CMD.EXE for commands execution
- KIgzZ8s1_785xe5A_9QIzhfA.exe (PID: 1680)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- build2.exe (PID: 5044)
- build2.exe (PID: 4540)
Uses NETSH.EXE to add a firewall rule or allowed programs
- KIgzZ8s1_785xe5A_9QIzhfA.exe (PID: 1680)
Detected use of alternative data streams (AltDS)
- svchost.exe (PID: 4132)
Uses ICACLS.EXE to modify access control lists
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 2816)
Connects to unusual port
- HpenOM8oqWCth9mMurN77Fxu.exe (PID: 1760)
- sG8cXiu7JNY1smF9He2SCSGn.exe (PID: 2980)
- ZQNo7PHSKBcyLZhb1qKFv2nc.exe (PID: 2856)
- AppLaunch.exe (PID: 1940)
- AppLaunch.exe (PID: 2592)
- vbc.exe (PID: 1956)
- 8LT6Vq7lNWhihsyST13sWVT2.exe (PID: 2468)
- build2.exe (PID: 5044)
- vbc.exe (PID: 5704)
- _vbXuFVL7PbRpardnWhipOYA.exe (PID: 4236)
- _PPPVsCZWCuQ2S4cszbSdmOA.exe (PID: 4340)
- tIzi73bQauJPYLVENV75Tj3d.exe (PID: 4292)
- build2.exe (PID: 4540)
Reads the date of Windows installation
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 2816)
Creates or modifies Windows services
- svchost.exe (PID: 4132)
Connects to SMTP port
- svchost.exe (PID: 4132)
Searches for installed software
- sG8cXiu7JNY1smF9He2SCSGn.exe (PID: 2980)
- ZQNo7PHSKBcyLZhb1qKFv2nc.exe (PID: 2856)
- vbc.exe (PID: 1956)
- AppLaunch.exe (PID: 2592)
- AppLaunch.exe (PID: 1940)
- build2.exe (PID: 5044)
- vbc.exe (PID: 5704)
- _vbXuFVL7PbRpardnWhipOYA.exe (PID: 4236)
- tIzi73bQauJPYLVENV75Tj3d.exe (PID: 4292)
- _PPPVsCZWCuQ2S4cszbSdmOA.exe (PID: 4340)
- build2.exe (PID: 4540)
Reads browser cookies
- sG8cXiu7JNY1smF9He2SCSGn.exe (PID: 2980)
- ZQNo7PHSKBcyLZhb1qKFv2nc.exe (PID: 2856)
- AppLaunch.exe (PID: 2592)
- AppLaunch.exe (PID: 1940)
- vbc.exe (PID: 1956)
- _vbXuFVL7PbRpardnWhipOYA.exe (PID: 4236)
- tIzi73bQauJPYLVENV75Tj3d.exe (PID: 4292)
- _PPPVsCZWCuQ2S4cszbSdmOA.exe (PID: 4340)
- vbc.exe (PID: 5704)
The process executes via Task Scheduler
- mstsca.exe (PID: 3824)
Reads the Windows owner or organization settings
- is-TDC7F.tmp (PID: 5280)
INFO
Application launched itself
- firefox.exe (PID: 3300)
Checks supported languages
- Install.exe (PID: 1896)
- 5A3L2ZoV7_n9OkPbNmjiFxO9.exe (PID: 1740)
- KIgzZ8s1_785xe5A_9QIzhfA.exe (PID: 1680)
- Y56MhtcPcgngA56Qpk7Xz1yR.exe (PID: 552)
- 8LT6Vq7lNWhihsyST13sWVT2.exe (PID: 2468)
- sG8cXiu7JNY1smF9He2SCSGn.exe (PID: 2980)
- K6Vu_cZajfv1W3nI4NlZYzbh.exe (PID: 3340)
- AFAi_TyaIZqk3YWnatpVYraH.exe (PID: 3208)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 3436)
- ZQNo7PHSKBcyLZhb1qKFv2nc.exe (PID: 2856)
- R_9JrEHEwau4gfRzweY803tp.exe (PID: 2996)
- R2T5csoyogKb7ajv22GWjq3s.exe (PID: 3260)
- DVNTebtS22luUiiCxmHmtwQ5.exe (PID: 3016)
- Jx98dOvw1Su_I6tKATXUlM08.exe (PID: 4080)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 2816)
- 4qWayS4NWxNACgKi6RtTDP_u.exe (PID: 3684)
- esPyD7Irgy6SzyVOsGf3XT2J.exe (PID: 2396)
- vbc.exe (PID: 1956)
- HpenOM8oqWCth9mMurN77Fxu.exe (PID: 1760)
- GoogleUpdate.exe (PID: 3656)
- AppLaunch.exe (PID: 1940)
- AppLaunch.exe (PID: 2592)
- 4qWayS4NWxNACgKi6RtTDP_u.exe (PID: 3744)
- AppLaunch.exe (PID: 2256)
- hxtidvtb.exe (PID: 4440)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 4904)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 1416)
- GoogleUpdate.exe (PID: 4704)
- build2.exe (PID: 4304)
- build3.exe (PID: 5400)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- F921.exe (PID: 5820)
- F921.exe (PID: 5984)
- build2.exe (PID: 5044)
- F921.exe (PID: 4944)
- F921.exe (PID: 2232)
- build2.exe (PID: 6040)
- bDeqhhSqnBxlJYCtvAEtZxPG.exe (PID: 5764)
- toolspub2.exe (PID: 5896)
- toolspub2.exe (PID: 5924)
- build3.exe (PID: 4800)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 2636)
- 266D.exe (PID: 3696)
- kos1.exe (PID: 3408)
- aafg31.exe (PID: 5056)
- set16.exe (PID: 4980)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 6116)
- NiIqH6ivYkmMPpP4S4zy7GNy.exe (PID: 2832)
- xZDdU5pql_TUqJHTbOiy5rAX.exe (PID: 4772)
- K8zm6o6gMji4elFAqugAFfSF.exe (PID: 5444)
- mA8reEJShwkAWqA5Ic5bzSMv.exe (PID: 4632)
- jqjsWQVm2aXONVycaGyt0KIJ.exe (PID: 3360)
- kos.exe (PID: 2736)
- vbc.exe (PID: 5704)
- is-TDC7F.tmp (PID: 5280)
- mstsca.exe (PID: 3824)
- _vbXuFVL7PbRpardnWhipOYA.exe (PID: 4236)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
- _PPPVsCZWCuQ2S4cszbSdmOA.exe (PID: 4340)
- tIzi73bQauJPYLVENV75Tj3d.exe (PID: 4292)
- previewer.exe (PID: 5340)
- 6G0qbEivOJjIpPaiLB_CQcOl.exe (PID: 3200)
- toolspub2.exe (PID: 2856)
- previewer.exe (PID: 4800)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 2316)
- toolspub2.exe (PID: 3316)
- kos1.exe (PID: 5372)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 4060)
- build2.exe (PID: 4540)
Process checks are UAC notifies on
- Install.exe (PID: 1896)
The process uses the downloaded file
- firefox.exe (PID: 3300)
- WinRAR.exe (PID: 3468)
Manual execution by a user
- WinRAR.exe (PID: 3468)
Reads the computer name
- Install.exe (PID: 1896)
- 5A3L2ZoV7_n9OkPbNmjiFxO9.exe (PID: 1740)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- AFAi_TyaIZqk3YWnatpVYraH.exe (PID: 3208)
- K6Vu_cZajfv1W3nI4NlZYzbh.exe (PID: 3340)
- 8LT6Vq7lNWhihsyST13sWVT2.exe (PID: 2468)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 2816)
- R2T5csoyogKb7ajv22GWjq3s.exe (PID: 3260)
- ZQNo7PHSKBcyLZhb1qKFv2nc.exe (PID: 2856)
- sG8cXiu7JNY1smF9He2SCSGn.exe (PID: 2980)
- vbc.exe (PID: 1956)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- KIgzZ8s1_785xe5A_9QIzhfA.exe (PID: 1680)
- AppLaunch.exe (PID: 1940)
- AppLaunch.exe (PID: 2256)
- hxtidvtb.exe (PID: 4440)
- AppLaunch.exe (PID: 2592)
- HpenOM8oqWCth9mMurN77Fxu.exe (PID: 1760)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 1416)
- GoogleUpdate.exe (PID: 4704)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- build2.exe (PID: 5044)
- F921.exe (PID: 5984)
- F921.exe (PID: 2232)
- bDeqhhSqnBxlJYCtvAEtZxPG.exe (PID: 5764)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 2636)
- 266D.exe (PID: 3696)
- kos1.exe (PID: 3408)
- aafg31.exe (PID: 5056)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 6116)
- K8zm6o6gMji4elFAqugAFfSF.exe (PID: 5444)
- vbc.exe (PID: 5704)
- jqjsWQVm2aXONVycaGyt0KIJ.exe (PID: 3360)
- kos.exe (PID: 2736)
- _PPPVsCZWCuQ2S4cszbSdmOA.exe (PID: 4340)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
- _vbXuFVL7PbRpardnWhipOYA.exe (PID: 4236)
- tIzi73bQauJPYLVENV75Tj3d.exe (PID: 4292)
- previewer.exe (PID: 5340)
- is-TDC7F.tmp (PID: 5280)
- NiIqH6ivYkmMPpP4S4zy7GNy.exe (PID: 2832)
- previewer.exe (PID: 4800)
- 6G0qbEivOJjIpPaiLB_CQcOl.exe (PID: 3200)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 4060)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 2316)
- kos1.exe (PID: 5372)
- build2.exe (PID: 4540)
Reads the machine GUID from the registry
- Install.exe (PID: 1896)
- AFAi_TyaIZqk3YWnatpVYraH.exe (PID: 3208)
- 5A3L2ZoV7_n9OkPbNmjiFxO9.exe (PID: 1740)
- sG8cXiu7JNY1smF9He2SCSGn.exe (PID: 2980)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 2816)
- vbc.exe (PID: 1956)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- AppLaunch.exe (PID: 1940)
- AppLaunch.exe (PID: 2592)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- AppLaunch.exe (PID: 2256)
- ZQNo7PHSKBcyLZhb1qKFv2nc.exe (PID: 2856)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 1416)
- build2.exe (PID: 5044)
- F921.exe (PID: 5984)
- F921.exe (PID: 2232)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 2636)
- aafg31.exe (PID: 5056)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 6116)
- 266D.exe (PID: 3696)
- K8zm6o6gMji4elFAqugAFfSF.exe (PID: 5444)
- jqjsWQVm2aXONVycaGyt0KIJ.exe (PID: 3360)
- kos.exe (PID: 2736)
- vbc.exe (PID: 5704)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
- _PPPVsCZWCuQ2S4cszbSdmOA.exe (PID: 4340)
- _vbXuFVL7PbRpardnWhipOYA.exe (PID: 4236)
- tIzi73bQauJPYLVENV75Tj3d.exe (PID: 4292)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 2316)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 4060)
- build2.exe (PID: 4540)
- previewer.exe (PID: 4800)
Create files in a temporary directory
- Install.exe (PID: 1896)
- KIgzZ8s1_785xe5A_9QIzhfA.exe (PID: 1680)
- K6Vu_cZajfv1W3nI4NlZYzbh.exe (PID: 3340)
- R2T5csoyogKb7ajv22GWjq3s.exe (PID: 3260)
- AppLaunch.exe (PID: 2256)
- HpenOM8oqWCth9mMurN77Fxu.exe (PID: 1760)
- explorer.exe (PID: 1924)
- bDeqhhSqnBxlJYCtvAEtZxPG.exe (PID: 5764)
- 266D.exe (PID: 3696)
- kos1.exe (PID: 3408)
- set16.exe (PID: 4980)
- kos.exe (PID: 2736)
- WerFault.exe (PID: 5368)
- is-TDC7F.tmp (PID: 5280)
- NiIqH6ivYkmMPpP4S4zy7GNy.exe (PID: 2832)
- previewer.exe (PID: 5340)
- _vbXuFVL7PbRpardnWhipOYA.exe (PID: 4236)
- 6G0qbEivOJjIpPaiLB_CQcOl.exe (PID: 3200)
- WerFault.exe (PID: 3936)
Creates files or folders in the user directory
- Install.exe (PID: 1896)
- HpenOM8oqWCth9mMurN77Fxu.exe (PID: 1760)
- 5A3L2ZoV7_n9OkPbNmjiFxO9.exe (PID: 1740)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 2816)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 1416)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- build3.exe (PID: 5400)
- explorer.exe (PID: 1924)
- build2.exe (PID: 5044)
- F921.exe (PID: 5984)
- F921.exe (PID: 2232)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- aafg31.exe (PID: 5056)
- jqjsWQVm2aXONVycaGyt0KIJ.exe (PID: 3360)
- WerFault.exe (PID: 5368)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
Checks proxy server information
- Install.exe (PID: 1896)
- 5A3L2ZoV7_n9OkPbNmjiFxO9.exe (PID: 1740)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 2816)
- AFAi_TyaIZqk3YWnatpVYraH.exe (PID: 3208)
- AppLaunch.exe (PID: 2256)
- D_1AG8eMm62Hzp1JDq0QF8kG.exe (PID: 1416)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- build2.exe (PID: 5044)
- F921.exe (PID: 5984)
- F921.exe (PID: 2232)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- aafg31.exe (PID: 5056)
- jqjsWQVm2aXONVycaGyt0KIJ.exe (PID: 3360)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
- build2.exe (PID: 4540)
- previewer.exe (PID: 4800)
Process checks computer location settings
- Install.exe (PID: 1896)
- ohlZqza5vOXhg9oCMlf40qFq.exe (PID: 696)
- YtV6thgoa8nA904dpHO_TwGB.exe (PID: 6136)
- Z9cLloRtSMLmaeD_O89fY43h.exe (PID: 3792)
Reads CPU info
- R2T5csoyogKb7ajv22GWjq3s.exe (PID: 3260)
- GoogleUpdate.exe (PID: 4704)
- build2.exe (PID: 5044)
- build2.exe (PID: 4540)
Reads Windows Product ID
- R2T5csoyogKb7ajv22GWjq3s.exe (PID: 3260)
- GoogleUpdate.exe (PID: 4704)
Creates files in the program directory
- R2T5csoyogKb7ajv22GWjq3s.exe (PID: 3260)
- HpenOM8oqWCth9mMurN77Fxu.exe (PID: 1760)
- bjPiQZPRjdXy1r6R46oBazqv.exe (PID: 1824)
- GoogleUpdate.exe (PID: 4704)
- build2.exe (PID: 5044)
- is-TDC7F.tmp (PID: 5280)
- previewer.exe (PID: 5340)
- build2.exe (PID: 4540)
- previewer.exe (PID: 4800)
Reads Environment values
- R2T5csoyogKb7ajv22GWjq3s.exe (PID: 3260)
- sG8cXiu7JNY1smF9He2SCSGn.exe (PID: 2980)
- ZQNo7PHSKBcyLZhb1qKFv2nc.exe (PID: 2856)
- GoogleUpdate.exe (PID: 4704)
- vbc.exe (PID: 1956)
- AppLaunch.exe (PID: 2592)
- AppLaunch.exe (PID: 1940)
- build2.exe (PID: 5044)
- kos.exe (PID: 2736)
- vbc.exe (PID: 5704)
- _PPPVsCZWCuQ2S4cszbSdmOA.exe (PID: 4340)
- _vbXuFVL7PbRpardnWhipOYA.exe (PID: 4236)
- tIzi73bQauJPYLVENV75Tj3d.exe (PID: 4292)
- build2.exe (PID: 4540)
Reads product name
- R2T5csoyogKb7ajv22GWjq3s.exe (PID: 3260)
- GoogleUpdate.exe (PID: 4704)
- build2.exe (PID: 5044)
- build2.exe (PID: 4540)
Reads the Internet Settings
- explorer.exe (PID: 1924)
Application was dropped or rewritten from another process
- is-TDC7F.tmp (PID: 5280)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
PrivateLoader
(PID) Process(1824) bjPiQZPRjdXy1r6R46oBazqv.exe
C2 (4)193.42.32.118
94.142.138.131
94.142.138.113
208.67.104.60
Strings (62)Unknown
SOFTWARE\Microsoft\Cryptography
MachineGuid
telegram.org
twitter.com
yandex.ru
google.com
/api/tracemap.php
http://
15.5pnp.10.lock
data=
/api/firecom.php
ipinfo.io/widget
country
db-ip.com
data-api-key="
/self
countryCode
www.maxmind.com/geoip/v2.1/city/me
iso_code
GetIP
api.ipgeolocation.io/ipgeo?include=hostname&ip=
country_code2
PowerControl
\PowerControl
\PowerControl_Svc.exe
Power monitoring service for your device.
WININET.dll
WINHTTP.dll
193.42.32.118
94.142.138.131
94.142.138.113
208.67.104.60
GetVersion|
GetUpdateLink
https://
Later
" /tn "PowerControl HR" /sc HOURLY /rl HIGHEST
schtasks /create /f /RU "
" /tn "PowerControl LG" /sc ONLOGON /rl HIGHEST
WinHttpConnect
WinHttpQueryHeaders
WinHttpOpen
WinHttpOpenRequest
WinHttpQueryDataAvailable
WinHttpSendRequest
WinHttpReceiveResponse
WinHttpReadData
WinHttpCloseHandle
WinHttpSetTimeouts
CharNextA
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3729.169 Safari/537.36
InternetOpenA
InternetSetOptionA
HttpOpenRequestA
InternetConnectA
InternetOpenUrlA
HttpQueryInfoA
InternetQueryOptionA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
RedLine
(PID) Process(1940) AppLaunch.exe
C2 (1)51.38.95.107:42494
Botnet
Err_msgLogsDiller Cloud (Telegram: @logsdillabot)
Auth_valuec2955ed3813a798683a185a82e949f88
US (11)
net.tcp://
/
localhost
c2955ed3813a798683a185a82e949f88
Authorization
ns1
HTckGTQpBBQjLQYWLDg4YCwLPQAdJwpc
ByRYAhpjMREOPisPAgU7FwEmVUgJICADLxQ1EjYuNxo4O0llKiQuCjFRBRYjFA8SDj4VCgNfKCM=
Scaly
(PID) Process(1956) vbc.exe
C2 (1)176.123.9.142:14845
Botnet1006
Err_msg
Auth_valueb5da80860b093905c2bba6f9377af704
US (14)
net.tcp://
/
localhost
b5da80860b093905c2bba6f9377af704
Authorization
ns1
ADUNVSMZMRwoF3lUIg0qQzkPChYDJQlXISJJWA==
ADUvECEUSVg=
Mangosteen
(PID) Process(4236) _vbXuFVL7PbRpardnWhipOYA.exe
C2 (1)185.225.74.51:44767
Botnetsq1
Err_msg
Auth_value698af4e4684b19e1acea9a7ebb86fc9b
US (14)
net.tcp://
/
localhost
698af4e4684b19e1acea9a7ebb86fc9b
Authorization
ns1
HzEEUCAGJBwgJ2ZWLSJYXSAxAUQcIQBTIhtQWA==
MVYmGQ==
Recallment
(PID) Process(4292) tIzi73bQauJPYLVENV75Tj3d.exe
C2 (1)176.123.9.142:14845
Botnettrafico
Err_msg
Auth_valueae8f72bc34fc0c248b3abb9f51375751
US (12)
net.tcp://
/
localhost
ae8f72bc34fc0c248b3abb9f51375751
Authorization
ns1
HzEAXTkEMSsoGltAIh4XVS4FGhY6FgJTISRTSQ==
Ni0pBy8DGDgHFFJI
Recount
Arkei
(PID) Process(5044) build2.exe
C2 (2)https://t.me/dastanatg
https://steamcommunity.com/profiles/76561199553369541
Strings (536)kernel32.dll
GetUserNameA
advapi32.dll
GetComputerNameA
LocalAlloc
lstrcmpiW
VirtualFree
VirtualAlloc
VirtualAllocExNuma
GetCurrentProcess
ExitProcess
GetSystemTime
Sleep
GetProcAddress
lstrcatA
LoadLibraryA
JohnDoe
HAL9TH
Ledger Live
\Raven\
Raven Core
\Dogecoin\
Dogecoin
*wallet*.dat
wallet.dat
\Bitcoin\
Bitcoin Core Old
\Bitcoin\wallets\
Bitcoin Core
.finger-print.fp
simple-storage.json
Binance Desktop
loginusers.vdf
libraryfolders.vdf
DialogConfigOverlay*.vdf
DialogConfig.vdf
config.vdf
ssfn*
SteamPath
Software\Valve\Steam
C:\\\Windows\
C:\\Windows\
C:\Windows\
*%DRIVE_REMOVABLE%*
*%DRIVE_FIXED%*
*%RECENT%*
%DRIVE_REMOVABLE%
%DRIVE_FIXED%
%RECENT%
%PROGRAMFILES_86%
%PROGRAMFILES%
%DOCUMENTS%
%DESKTOP%
%USERPROFILE%
%LOCALAPPDATA%
%APPDATA%
\information.txt
[Software]
[Processes]
VideoCard:
RAM:
CPU Count:
Processor:
[Hardware]
TimeZone:
Local Time:
Keyboard Languages:
Display Language:
Display Resolution:
User Name:
Computer Name:
Windows:
Work Dir: In memory
Path:
HWID:
GUID:
MachineID:
Date:
Version:
sqlite3.dll
RoninWalletEdge
kjmoohlgokccodicjjfebfomlbljgfhk
IndexedDB
Sync Extension Settings
Local Extension Settings
UseMasterPassword
Security
Password
UserName
PortNumber
HostName
Soft: WinSCP
\Soft\Authy Desktop\
\Authy Desktop\Local Storage\leveldb\
\Soft\Authy Desktop Old\
\Authy Desktop\Local Storage\
*.localstorage
places.sqlite
formhistory.sqlite
cookies.sqlite
History
SELECT fieldname, value FROM moz_formhistory
SELECT url FROM moz_places
SELECT host, isHttpOnly, path, isSecure, expiry, name, value FROM moz_cookies
Network
Password:
Login:
Host:
Soft:
"os_crypt":{"encrypted_key":"
\passwords.txt
\Soft\Telegram\
F8806DD0C461824F*
A92DAA6EA6F891F2*
A7FDF864FBC10B77*
D877F783D5D3EF8C*
key_datas
\Telegram Desktop\
Thunderbird
\Thunderbird\Profiles\
Brave
\BraveSoftware\Brave-Browser\User Data\
CryptoTab Browser
\CryptoTab Browser\User Data\
\Opera GX Stable\
\Opera Stable\
\Opera Software\
sqlite3_column_blob
sqlite3_column_bytes
sqlite3_close
sqlite3_finalize
sqlite3_column_text
sqlite3_step
sqlite3_prepare_v2
sqlite3_open
GdipFree
GdipDisposeImage
GdipSaveImageToStream
GdiplusShutdown
GdiplusStartup
GdipCreateBitmapFromHBITMAP
GdipGetImageEncoders
GdipGetImageEncodersSize
SymMatchString
PathFindFileNameA
StrStrA
StrCmpCW
StrCmpCA
PathMatchSpecA
PathMatchSpecW
SHGetFolderPathA
SHFileOperationA
ShellExecuteExA
CloseWindow
GetWindowDC
GetWindowRect
GetHGlobalFromStream
CreateStreamOnHGlobal
CoInitialize
InternetCrackUrlA
AccessCheck
MapGenericMask
DuplicateToken
OpenProcessToken
GetFileSecurityA
RegEnumValueA
CryptBinaryToStringA
gdiplus.dll
dbghelp.dll
shlwapi.dll
shell32.dll
GetVolumeInformationA
GetWindowsDirectoryA
Process32Next
Process32First
CreateToolhelp32Snapshot
CreateEventA
OpenEventA
GetTickCount
SetEnvironmentVariableA
GetEnvironmentVariableA
GetFileInformationByHandle
CreateFileMappingA
FileTimeToSystemTime
UnmapViewOfFile
MapViewOfFile
LocalFileTimeToFileTime
GetFileAttributesW
GetFileAttributesA
WriteFile
SetFileTime
GetLocalTime
SystemTimeToFileTime
HeapFree
SetFilePointer
GetCurrentDirectoryA
DeleteFileA
CopyFileA
TzSpecificLocalTimeToSystemTime
GetTimeZoneInformation
GetFileSizeEx
OpenProcess
GetCurrentProcessId
GetLocaleInfoA
FreeLibrary
GlobalSize
GlobalLock
lstrcpynA
GetLastError
FindClose
FindNextFileA
FindFirstFileA
MultiByteToWideChar
lstrcpyA
GetDriveTypeA
lstrlenA
GetLogicalDriveStringsA
CloseHandle
ReadFile
GetFileSize
CreateFileA
GetProcessHeap
HeapAlloc
LocalFree
WideCharToMultiByte
GetSystemInfo
GetUserDefaultLocaleName
IsWow64Process
GlobalMemoryStatusEx
CreateThread
Discord Token:
dQw4w9WgXcQ:
\Soft\Discord\discord_tokens.txt
Session Storage
leveldb
Local Storage
Discord
\discord\
Wasabi Wallet
\WalletWasabi\Client\Wallets\
Blockstream Green
\Blockstream\Green\wallets\
she*.sqlite
Daedalus Mainnet
\Daedalus Mainnet\wallets\
Jaxx_Desktop
\com.liberty.jaxx\IndexedDB\file__0.indexeddb.leveldb\
GAuth Authenticator
ilgcnhelpchnceeipipijaljkblbcobl
EOS Authenticator
oeljdldpnmdbchonielidgobddffflal
Authy
gaedmjdfmmahhbjefcbgaolhhanlaolb
Authenticator
bhghoamapcdpbohphigoooaddinpkbai
jnkelfanjkeadonecabehalmbgpfodjm
Temple
ookjlbkiijinhpmnjffcofjonbfbgaoc
TezBox
mnfifefkajgofkcjkemidiaecocnkjeh
hcflpincpppdclinealmandijcmnkbgn
CyanoWallet
dkdedlpgdmmkkfjabffeganieamfklkm
Solflare
bhhhlbepdkbapadjdnnojkbgioiodbic
WavesKeeper
lpilbniiabackdjcionkobglmddfbcjo
MaiarDeFiWallet
dngmlblcodfobpdpecaadgfbcggfjfnm
NamiWallet
lpfcbjknijpeeillifnkikgncikgfhdo
XdefiWallet
hmeobnfnfcmdkdcmlblgagmfpfboieaf
BoltX
aodkkagnadcbobfpggfnjeongemjbjca
PaliWallet
mgffkfbidihjpoaomajlbgchddlicgpn
Oxygen (Atomic)
fhilaheimglignddkjgofkcbgekhenbh
BraveWallet
odbfpeeihdkbihmopkbjmoonfanlbfcl
ejbalbakoplchlghecdalmeeeajnimhm
Phantom
bfnaelmomeimhlpmgjnjophhpkkoljpa
Rabby
acmacodkjbdgmoleebolmdjonilkdbch
Trezor Password Manager
imloifkgjagghnncjkhggdhalmcnfklk
KardiaChain
pdadjkfkgcafgbceimcpbkalnfnepbnk
EVER Wallet
cgeeodpfagjceefieflmdfphplkenlfk
Coin98
aeachknmefphepccionboohckonoeemg
Harmony
fnnegphlobjdpkhecapkijjdkgcjhkib
ICONex
flpiciilemghbmfalicajoolhkkenfel
PolymeshWallet
jojhfeoedkpkglbfimdfabpdfjaoolaf
AuroWallet
cnmamaachppnkjgnildpdmkaakejnhae
Sollet
fhmfendgdocmcbmfikdcogofphimnkno
Keplr
k|{mn
dmkamcknogkgcdfhhbddcghachkejeap
Terra_Station
aiifbnbfobpmeekipheeijimdpnlpgpp
LiqualityWallet
kpfopkelmapcoipemfendmdcghnegimn
CloverWallet
nhnkbkgjikgcigadomkphalanndcapjk
NeoLine
cphhlgmgameodnhkjdmkpanlelnlohao
RoninWallet
fnjhmkhhmkbjkkabndcnnogagogbneec
GuildWallet
nanjmdknhkinifnkgdcggcfnhdaammmj
MewCx
nlbmnnijcnlegkjjpcfjclmcfggfefdm
Wombat
amkmjjmmflddogmhpjloimipbofnfjih
iWallet
kncchdigobghenbbaddojjnnaogfppfj
BitAppWallet
fihkakfobkmkjojpchpfgcmhfjnmnfpi
JaxxLiberty
cjelfplplebdjjenllpjcblmjkfcffne
EQUALWallet
blnieiiffboillknjnepogjhkgnoapac
Guarda
hpglfhgfnhbgpjdenjgmdgoeiappafln
Coinbase
hnfanknocfeofbddgcijnmhnfnkdnaad
MathWallet
afbcbjpbpfadlkmhmclhkeeodmamcflc
NiftyWallet
jbdaocneiiinmjbjlgalhcelgbejmnid
Yoroi
ffnbelfdoeiohenkjibnmadjiehjhajb
BinanceChainWallet
fhbohimaelbohpjbbldcngcnapndodjp
MetaMask
nkbihfbeogaeaoehlefnkodbefgpgknn
TronLink
ibnejdfjmmkpcnlpebklmnkoeoihofec
EnumProcessModules
GetModuleBaseNameA
GetModuleFileNameExA
GetSystemMetrics
EnumDisplayDevicesA
wsprintfA
GetDC
CharToOemA
GetKeyboardLayoutList
ReleaseDC
GetDesktopWindow
CoUninitialize
CoCreateInstance
CreateCompatibleDC
GetDeviceCaps
CreateDCA
DeleteObject
BitBlt
SelectObject
CreateCompatibleBitmap
DeleteUrlCacheEntry
InternetSetOptionA
InternetOpenUrlA
InternetSetFilePointer
HttpQueryInfoA
HttpAddRequestHeadersA
InternetOpenA
InternetConnectA
HttpOpenRequestA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
wininet.dll
GetCurrentHwProfileA
RegGetValueA
RegEnumKeyExA
RegGetValueW
RegOpenKeyExW
RegCloseKey
RegQueryValueExA
RegOpenKeyExA
PK11SDR_Decrypt
PK11_Authenticate
PK11_FreeSlot
PK11_GetInternalKeySlot
NSS_Shutdown
NSS_Init
C:\ProgramData\nss3.dll
CryptStringToBinaryA
CryptUnprotectData
CRYPT32.DLL
BCryptDecrypt
BCryptGenerateSymmetricKey
BCryptSetProperty
BCryptOpenAlgorithmProvider
BCryptDestroyKey
BCryptCloseAlgorithmProvider
BCRYPT.DLL
psapi.dll
user32.dll
ole32.dll
gdi32.dll
FALSE
Cookies
Local State
\Opera Software\Opera GX Stable\
OperaGX
\Opera Software\Opera Stable\
Opera
\Tencent\QQBrowser\User Data\
QQBrowser
\360Browser\Browser\User Data\
360 Browser
\Microsoft\Edge\User Data\
Microsoft Edge
\7Star\7Star\User Data\
7Star
\brave\
Brave_Old
\Chedot\User Data\
Chedot Browser
\TorBro\Profile\
TorBro Browser
\CentBrowser\User Data\
Cent Browser
\CocCoc\Browser\User Data\
CocCoc
\Vivaldi\User Data\
Vivaldi
\Epic Privacy Browser\User Data\
Epic Privacy Browser
\Comodo\Dragon\User Data\
Comodo Dragon
\Torch\User Data\
Torch
\Amigo\User Data\
Amigo
\Chromium\User Data\
Chromium
\Google\Chrome\User Data\
Google Chrome
\Moonchild Productions\Pale Moon\Profiles\
Pale Moon
\Mozilla\Firefox\Profiles\
Mozilla Firefox
Soft: FileZilla
<Pass encoding="base64">
<User>
<Port>
<Host>
\AppData\Roaming\FileZilla\recentservers.xml
SELECT HOST_KEY, is_httponly, path, is_secure, (expires_utc/1000000)-11644480800, name, encrypted_value from cookies
SELECT url FROM urls
SELECT target_path, tab_url from downloads
SELECT name_on_card, expiration_month, expiration_year, card_number_encrypted FROM credit_cards
"SA^/
SELECT name, value FROM autofill
SELECT origin_url, username_value, password_value FROM logins
encryptedPassword
encryptedUsername
usernameField
formSubmitURL
logins.json
Web Data
Cookies
Login Data
netfulfilled
mnpayments
mncache
governance
banlist
mempool
peers
fee_estimates
Local\Microsoft
Roaming\WinRAR
Local\NuGet
Local\Packages
MicrosoftEdge\Cookies
Recycle.Bin
Local\Temp
Recovery
msdownld.tmp
System Volume Information
Config.Msi
RECYCLE.BIN
C:\ProgramData\
\Monero\
SOFTWARE\monero-project\monero-core
wallet_path
*.config
*.wallet
\Coinomi\Coinomi\wallets\
Coinomi
app-store.json
\Binance\
Binance
0000*
MANIFEST-000001
CURRENT
*.log
\atomic\Local Storage\leveldb\
Atomic
file__0.localstorage
\jaxx\Local Storage\
Jaxx_Desktop_Old
multidoge.wallet
\MultiDoge\
MultiDoge
default_wallet
\ElectronCash\wallets\
ElectronCash
info.seco
seed.seco
passphrase.json
\Exodus\exodus.wallet\
window-state.json
exodus.conf.json
\Exodus\
Exodus
\Electrum-LTC\wallets\
ElectrumLTC
\Electrum\wallets\
Electrum
\Ethereum\
Ethereum"
keystore
Plugins
Wallets
RaccoonClipper
(PID) Process(4800) build3.exe
Wallets (14)Ae2tdPwUPEZDqNhACJ3ZT5NdVjkNffGAwa4Mc9N95udKWYzt1VnFngLMnPE
89SPVUAPHDLSq5pRdf8Eo6SLnKRJ8BNSYYnvPL6iJxGP4FBCBmkeV3CTSLCbk6uydxRnub4gLH6TBRycxSAQN2m1KcnhrSZ
0xa6360e294DfCe4fE4Edf61b170c76770691aA111
t1VQgJMcNsBHsDyu1tXmJZjDpgbm3ftmTGN
42UxohbdHGMYGPvW5Uep45Jt9Rj2WvTV958B5G5vHnawZhA4UwoD53Tafn6GRmcGdoSFUfCQN6Xm37LBZZ6qNBorFw3b6s2
MBD2C8QV7RDrNtSDRe9B2iH5r7yH4iMcxk
bnb136ns6lfw4zs5hg4n85vdthaad7hq5m4gtkgf23
bc1qx8vykfse9s9llguez9cuyjmy092yeqkesl2r5v
DBbgRYaKG993LFJKCWz73PZqveWsnwRmGc
LLiNjWA9h4LxVtDigLQ79xQdGiJYC4oHis
addr1qx4jwm700r2w6fneakg0r5pkg76vu7qkt6qv7zxza3qu3w9tyahu77x5a5n8nmvs78grv3a5eeupvh5qeuyv9mzpezuq60zykl
1My2QNmVqkvN5M13xk8DWftjwC9G1F2w8Z
ltc1qa5lae8k7tzcw5lcjfvfs3n0nhf0z3cgrsz2dym
3NLzE3tXwoagBrgFsjNNkPZfrESydTD8JP
(PID) Process(3824) mstsca.exe
Wallets (14)Ae2tdPwUPEZDqNhACJ3ZT5NdVjkNffGAwa4Mc9N95udKWYzt1VnFngLMnPE
89SPVUAPHDLSq5pRdf8Eo6SLnKRJ8BNSYYnvPL6iJxGP4FBCBmkeV3CTSLCbk6uydxRnub4gLH6TBRycxSAQN2m1KcnhrSZ
0xa6360e294DfCe4fE4Edf61b170c76770691aA111
t1VQgJMcNsBHsDyu1tXmJZjDpgbm3ftmTGN
42UxohbdHGMYGPvW5Uep45Jt9Rj2WvTV958B5G5vHnawZhA4UwoD53Tafn6GRmcGdoSFUfCQN6Xm37LBZZ6qNBorFw3b6s2
MBD2C8QV7RDrNtSDRe9B2iH5r7yH4iMcxk
bnb136ns6lfw4zs5hg4n85vdthaad7hq5m4gtkgf23
bc1qx8vykfse9s9llguez9cuyjmy092yeqkesl2r5v
DBbgRYaKG993LFJKCWz73PZqveWsnwRmGc
LLiNjWA9h4LxVtDigLQ79xQdGiJYC4oHis
addr1qx4jwm700r2w6fneakg0r5pkg76vu7qkt6qv7zxza3qu3w9tyahu77x5a5n8nmvs78grv3a5eeupvh5qeuyv9mzpezuq60zykl
1My2QNmVqkvN5M13xk8DWftjwC9G1F2w8Z
ltc1qa5lae8k7tzcw5lcjfvfs3n0nhf0z3cgrsz2dym
3NLzE3tXwoagBrgFsjNNkPZfrESydTD8JP
Total processes
173
Monitored processes
110
Malicious processes
56
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 552 | "C:\Users\admin\Pictures\Minor Policy\Y56MhtcPcgngA56Qpk7Xz1yR.exe" | C:\Users\admin\Pictures\Minor Policy\Y56MhtcPcgngA56Qpk7Xz1yR.exe | — | Install.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 696 | "C:\Users\admin\Pictures\Minor Policy\ohlZqza5vOXhg9oCMlf40qFq.exe" | C:\Users\admin\Pictures\Minor Policy\ohlZqza5vOXhg9oCMlf40qFq.exe | Install.exe | ||||||||||||
User: admin Company: DarkLab Integrity Level: HIGH Description: DarkLab Exit code: 0 Version: 1.0.1.6 Modules
| |||||||||||||||
| 1064 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3300.0.1940201101\392965828" -parentBuildID 20230710165010 -prefsHandle 1108 -prefMapHandle 1100 -prefsLen 29524 -prefMapSize 244147 -appDir "C:\Program Files\Mozilla Firefox\browser" - {fe3c52e8-c5c1-46bb-8de5-0b900140ae1b} 3300 "\\.\pipe\gecko-crash-server-pipe.3300" 1180 fcd0b58 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1416 | "C:\Users\admin\Pictures\Minor Policy\D_1AG8eMm62Hzp1JDq0QF8kG.exe" --Admin IsNotAutoStart IsNotTask | C:\Users\admin\Pictures\Minor Policy\D_1AG8eMm62Hzp1JDq0QF8kG.exe | D_1AG8eMm62Hzp1JDq0QF8kG.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1476 | "C:\Windows\System32\sc.exe" create mhedjyrl binPath= "C:\Windows\SysWOW64\mhedjyrl\hxtidvtb.exe /d\"C:\Users\admin\Pictures\Minor Policy\KIgzZ8s1_785xe5A_9QIzhfA.exe\"" type= own start= auto DisplayName= "wifi support" | C:\Windows\SysWOW64\sc.exe | — | KIgzZ8s1_785xe5A_9QIzhfA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1492 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3300.6.1293060873\1401924415" -childID 5 -isForBrowser -prefsHandle 3780 -prefMapHandle 3828 -prefsLen 35368 -prefMapSize 244147 -jsInitHandle 856 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {01570433-3519-4c5e-9b32-ca5371225ea3} 3300 "\\.\pipe\gecko-crash-server-pipe.3300" 3944 23738d58 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1680 | "C:\Users\admin\Pictures\Minor Policy\KIgzZ8s1_785xe5A_9QIzhfA.exe" | C:\Users\admin\Pictures\Minor Policy\KIgzZ8s1_785xe5A_9QIzhfA.exe | — | Install.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1728 | C:\Windows\system32\RAServer.exe /offerraupdate | C:\Windows\System32\raserver.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Remote Assistance COM Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1740 | "C:\Users\admin\Pictures\Minor Policy\5A3L2ZoV7_n9OkPbNmjiFxO9.exe" | C:\Users\admin\Pictures\Minor Policy\5A3L2ZoV7_n9OkPbNmjiFxO9.exe | Install.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1760 | "C:\Users\admin\Pictures\Minor Policy\HpenOM8oqWCth9mMurN77Fxu.exe" | C:\Users\admin\Pictures\Minor Policy\HpenOM8oqWCth9mMurN77Fxu.exe | Install.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Atom.SDK.Core Exit code: 0 Version: 4.5.0.12 Modules
| |||||||||||||||
Total events
56 976
Read events
55 550
Write events
1 351
Delete events
75
Modification events
| (PID) Process: | (1924) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000088AF72B0747534094337F63DE35C94A00000000020000000000106600000001000020000000DE596CC00FA0CE6036B57F3745DF211B8CEDC7563B5C7C90E189DFBFE4E216FC000000000E800000000200002000000034A09CAFA8980668BD48169E708CCFDA06F4ADAD9A6D0FF324841FD89016AF6F3000000097B2B3329B62DD4C9AB1E283BD9359B999E8411B9FC15AF795BFA67D05007F5CE28F7E84193A17AFEBE2A486810ADC32400000007E5B4D515AE7EE2B367ED77D5D9A272891BC7B3019A3AA7BC4BF2CA5315073E7F321A33013E44AD95CE9A5E9CA3FF01D3584C54FECFB9C1227BA4AE46F87EAF7 | |||
| (PID) Process: | (3300) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 0000000000000000 | |||
| (PID) Process: | (1924) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | 308046O0NS4N39PO |
Value: 000000000900000011000000C5C20000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFD0D677189BC5D90100000000 | |||
| (PID) Process: | (1924) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000B6000000F200000098A764001500000007000000DB2206007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C0063006D0064002E006500780065000000EA02000000000540008000000000542DADFFFE070000000000000000000068006B02000000005C00010000000000000000000000000000003D0000000000EB1A92770000000068006B020000000000000000FE0700002825B6FFFE070000A08886020000000018006B020000000000000000000000000100000000000000BF1DADFFFE07000060E1EA020000000060B888020000000000000000000000003B9462FDFE070000B00C88020000000008006B02000000005C00010000000000869A807700000000BE313C4A62B00000820200000000000000000000000000005C000100000000000000000000000000820200000000000002000000000000005C000100000000000000000000000000820200000000000080A6E0FF00000000C812D2FF00000000B00C88020000000001000000000000000F0000C000000000AFBD17FEFE070000820200000000000001000000000000008202000000000000DB9B8077000000005C00010000000000000000000000000000000000000000000100000000000000000000000000000081020000000000000000000000000000000000000000000000000000060000002400000067510B004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000000000000000000000000000000008202000000000000010000000000000001000000000000008202000000000000D46905FCFE07000010E2EA020000000016798077000000000000000000000000869A807700000000000000000000000030E14A0000000000010000000000000010E2EA02000000000000000000000000CF41394A62B00000FFFFFFFFFFFFFFFF010000000000000000FF490000000000A0000500000000000000000000000000586705FCFE0700000000000000000000A0000500000000002B10000000000000807580770000000000000000000000000000000000000000000000000000000001000000000000001500000007000000790E06007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C0063006D0064002E006500780065000000EA02000000000540008000000000542D8CFFFE070000000000000000000068006C02000000005C0001000000000000000000000000000000280000000000EB1A6E770000000068006C020000000000000000FE070000282595FFFE070000A00D33000000000018006C02000000001B000000C86719007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C007400610073006B006D00670072002E00650078006500000041003900440043003700300042004200420034007D000000280000000000340000C000000000D48028000000000080BE28000000000000000000000000003E0040000000000060E3EA0200000000E0A4C30700000000350100C000000000C8037C770000000000000000000000007010000000000000A07D28000000000000000000000000001480280000000000D03B2B000000000048DD6F7700000000360038000000000020EBEA0200000000F8DCEA0200000000E905707700000000F1DCEA0200000000E0A4C30700000000140000000600000098E705007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C0063006D0064002E00650078006500000067FEFE0700000000000000000000F012FD020000000000000000000000000000000000000000F012FD020000000012C266FEFE070000010000000000000000000000000000000000000000000000F012FD02000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3300) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 1 | |||
| (PID) Process: | (3300) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (3300) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (3300) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (3300) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 0 | |||
| (PID) Process: | (3300) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
Executable files
88
Suspicious files
627
Text files
1 582
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3300 | firefox.exe | C:\Users\admin\Downloads\Install_p_a_s_s1234.hvv9k34W.7z.part | — | |
MD5:— | SHA256:— | |||
| 3300 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\nltxvmn2.default\startupCache\urlCache-current.bin | binary | |
MD5:4DF9B77C7650AF87B264E535779AE2A4 | SHA256:C57071FCFEF26EE4F08A2029E547848EC015B10045ABAD705195A9F966FEAE58 | |||
| 3300 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3300 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3300 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3300 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3300 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\nltxvmn2.default\startupCache\scriptCache-child-current.bin | binary | |
MD5:3E687F1CDE81D724075D31C078C104E7 | SHA256:ADB1769C7BB3D37001B58B504E1BE58AA6FC1CCC2E8D763BAA58CD69256571FC | |||
| 3300 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\cert9.db | binary | |
MD5:783BC5A97C2F1753A4A4F28DF3D7FC72 | SHA256:A6F6E707EBE342E1A44F5D79D21BFA760564E80B42ED9415E17F7422BA74BA3A | |||
| 3300 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\cert9.db-journal | binary | |
MD5:84AAE40FD928E8E7208372F796C1E743 | SHA256:F057D81FD7A4B9A87C05A1D8341C1FF948B9169EA3186634A5C826D0D33EFFFA | |||
| 3300 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
124
TCP/UDP connections
325
DNS requests
206
Threats
351
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3300 | firefox.exe | POST | 200 | 184.24.77.62:80 | http://r3.o.lencr.org/ | unknown | der | 503 b | unknown |
3300 | firefox.exe | POST | — | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | unknown |
3300 | firefox.exe | POST | 200 | 184.24.77.62:80 | http://r3.o.lencr.org/ | unknown | der | 503 b | unknown |
3300 | firefox.exe | POST | 200 | 52.222.226.205:80 | http://ocsp.r2m02.amazontrust.com/ | unknown | der | 471 b | unknown |
3300 | firefox.exe | POST | 200 | 184.24.77.62:80 | http://r3.o.lencr.org/ | unknown | der | 503 b | unknown |
3300 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
3300 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | text | 90 b | unknown |
3300 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | der | 471 b | unknown |
3300 | firefox.exe | POST | 200 | 184.24.77.62:80 | http://r3.o.lencr.org/ | unknown | der | 503 b | unknown |
3300 | firefox.exe | POST | 200 | 184.24.77.62:80 | http://r3.o.lencr.org/ | unknown | der | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
332 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3300 | firefox.exe | 172.67.209.222:443 | faucetmeaning.com | — | — | unknown |
3300 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
3300 | firefox.exe | 35.244.181.201:443 | aus5.mozilla.org | GOOGLE | US | unknown |
3300 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
3300 | firefox.exe | 34.197.137.200:443 | spocs.getpocket.com | AMAZON-AES | US | unknown |
3300 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | unknown |
3300 | firefox.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
faucetmeaning.com |
| unknown |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
aus5.mozilla.org |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
prod.balrog.prod.cloudops.mozgcp.net |
| whitelisted |
spocs.getpocket.com |
| shared |
proxyserverecs-1736642167.us-east-1.elb.amazonaws.com |
| shared |
content-signature-2.cdn.mozilla.net |
| whitelisted |
prod.content-signature-chains.prod.webservices.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1896 | Install.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/BeamWinHTTP CnC Activity M2 (GET) |
1896 | Install.exe | Device Retrieving External IP Address Detected | ET INFO Observed External IP Lookup Domain in TLS SNI (api .myip .com) |
1896 | Install.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
332 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
332 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
1896 | Install.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 7 |
1896 | Install.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 19 |
1896 | Install.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1896 | Install.exe | A Network Trojan was detected | ET MALWARE Single char EXE direct download likely trojan (multiple families) |
1896 | Install.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
39 ETPRO signatures available at the full report
Process | Message |
|---|---|
AppLaunch.exe | 2023-09-19 21:33:59 [AppLaunch.exe 2256] Trying to connect to http://5.42.92.211/
|
AppLaunch.exe | 2023-09-19 21:34:02 [AppLaunch.exe 2256] ERROR in ..\stealer\stealer.cpp, line 159, function Start. Failed to connect to http://5.42.92.211/
|