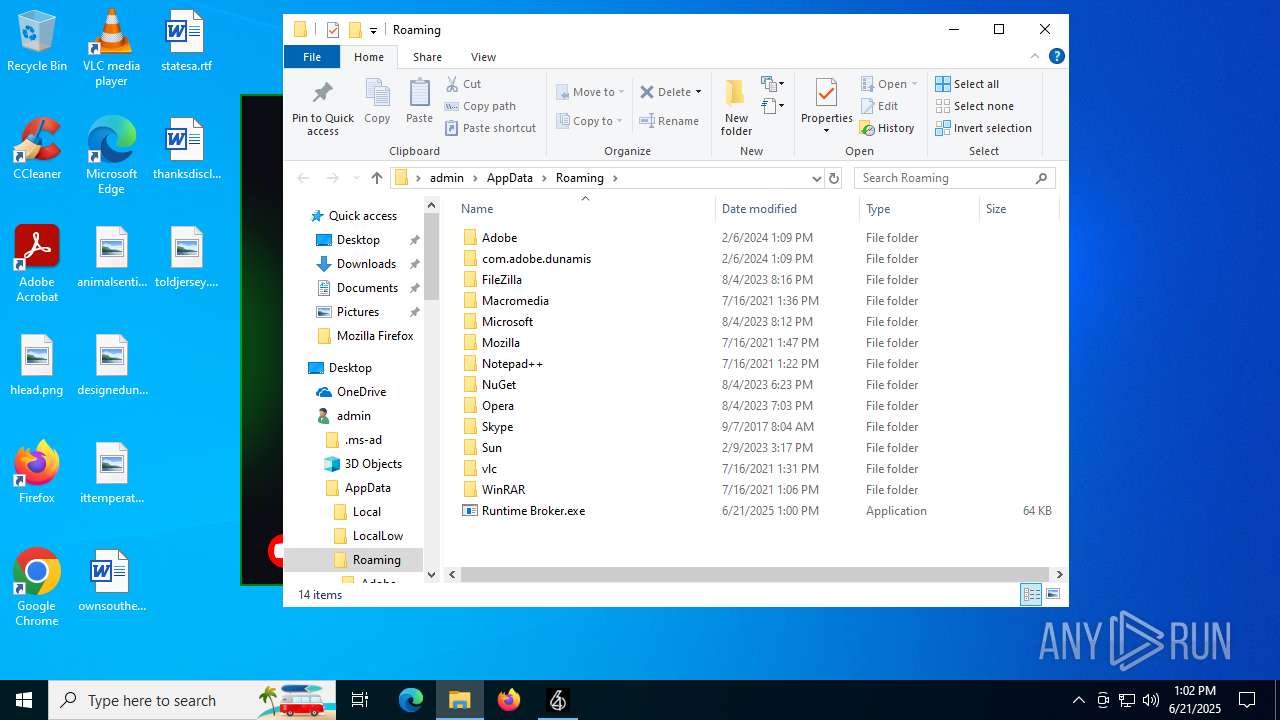
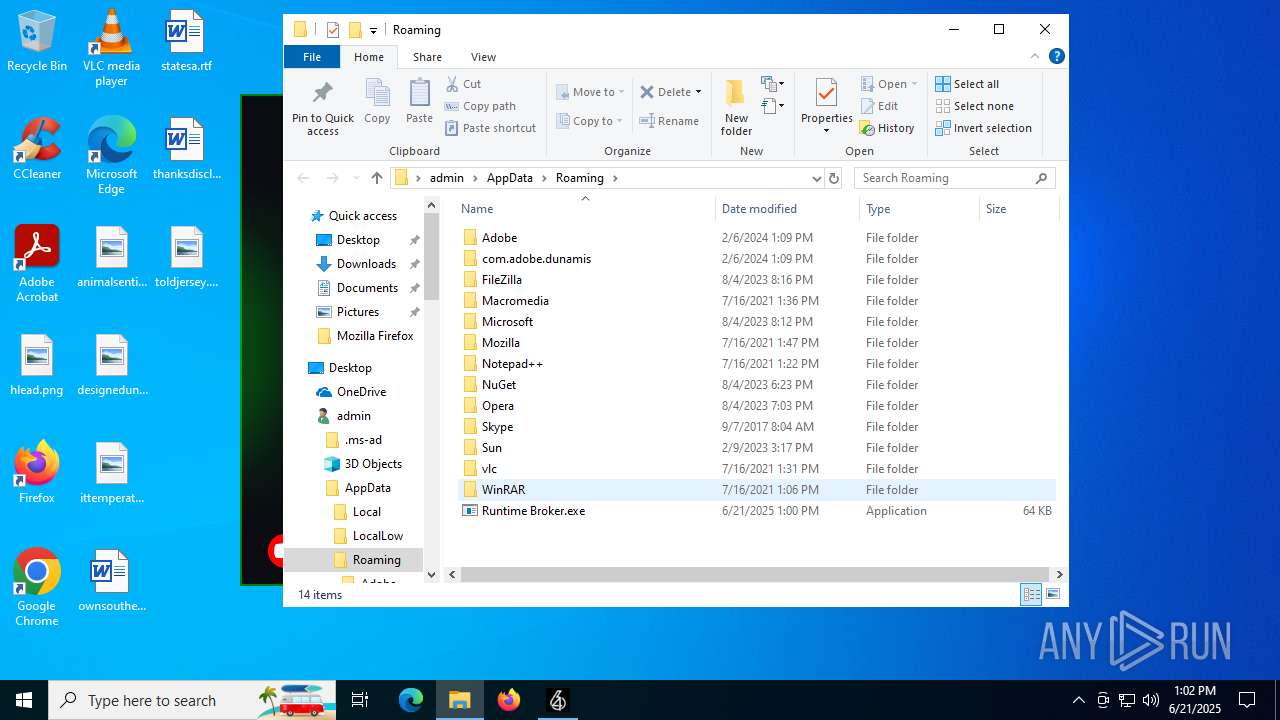
| File name: | 64_Service (1).exe |
| Full analysis: | https://app.any.run/tasks/967299c5-9e33-463d-80b7-cf440b1e6d2b |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | June 21, 2025, 13:00:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 13DD953D30085824457696DB3DC7CDE3 |
| SHA1: | 3B4EC8CDEB0662BBAC587278264583F09D9B10E9 |
| SHA256: | C032A110EA3A36BEB548A3BD5D1D9957AF4644E974AED610BBA36A3A6A3EF2E1 |
| SSDEEP: | 3072:RN1vgxeyHPlK3rRRb8PlZngmhY6zHffpg:NgxeB3DglV9Zffp |
MALICIOUS
Downloads the requested resource (POWERSHELL)
- 64_Service (1).exe (PID: 504)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 6404)
ASYNCRAT has been detected (YARA)
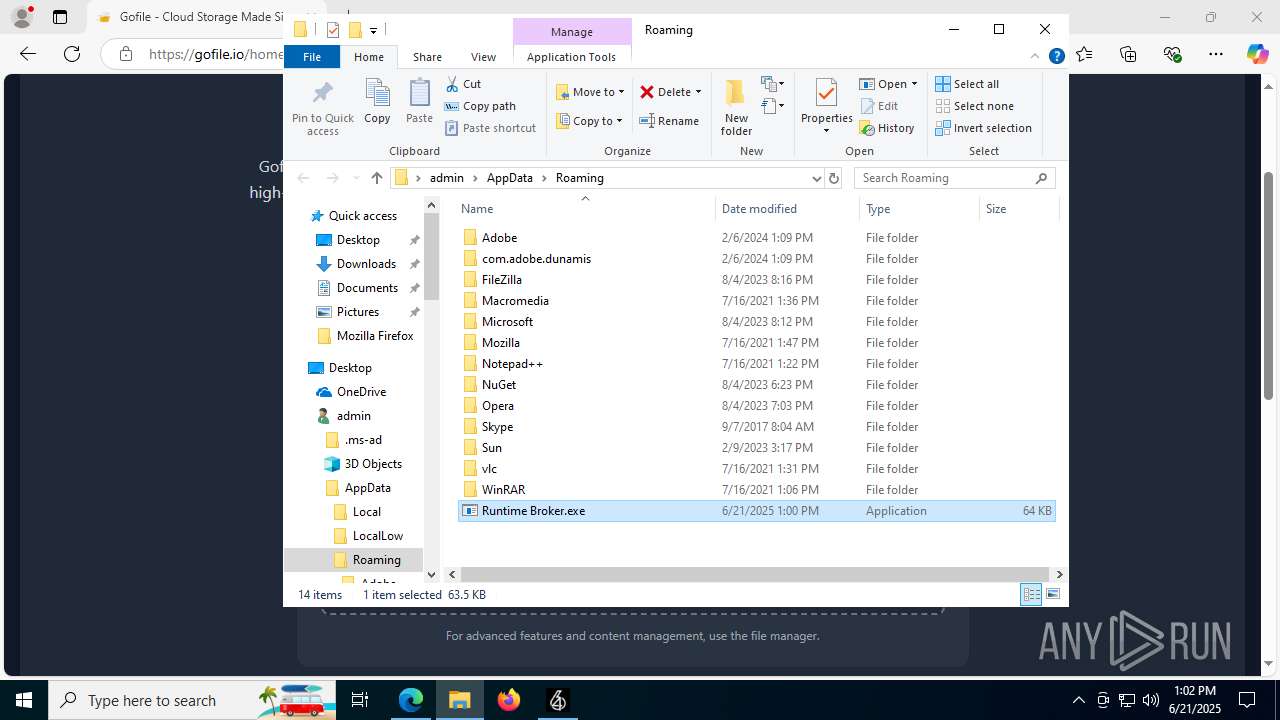
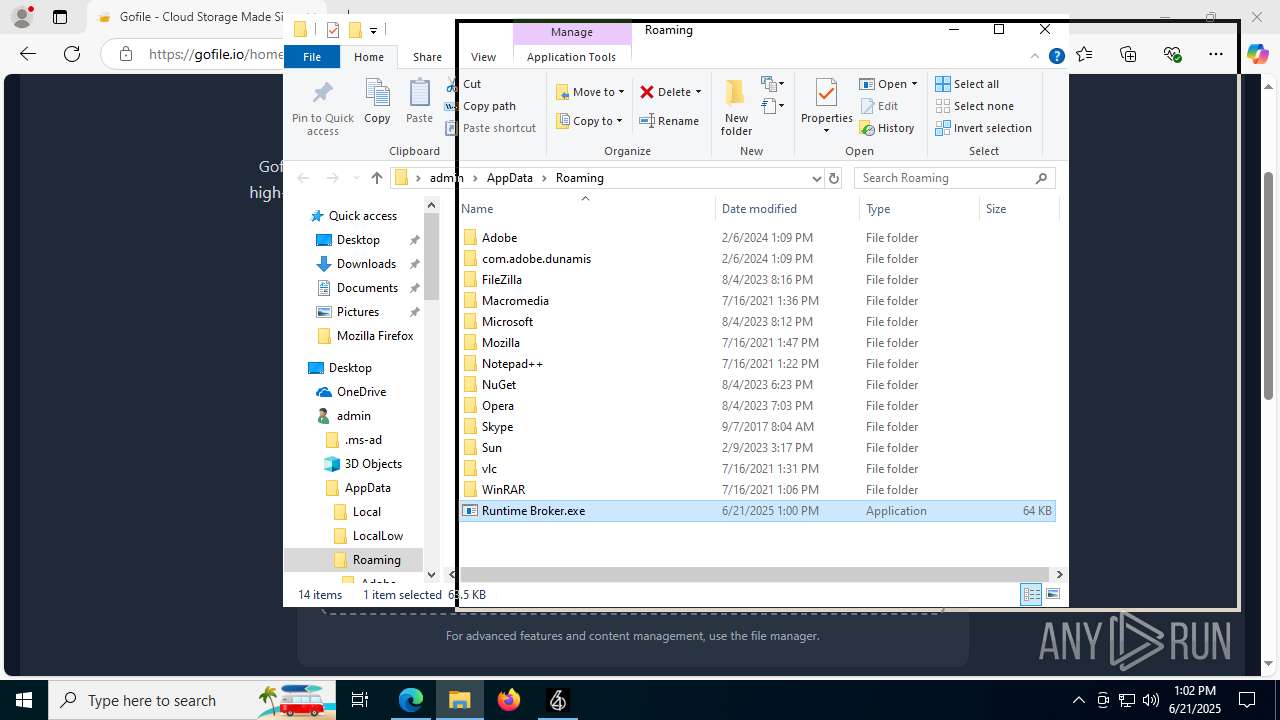
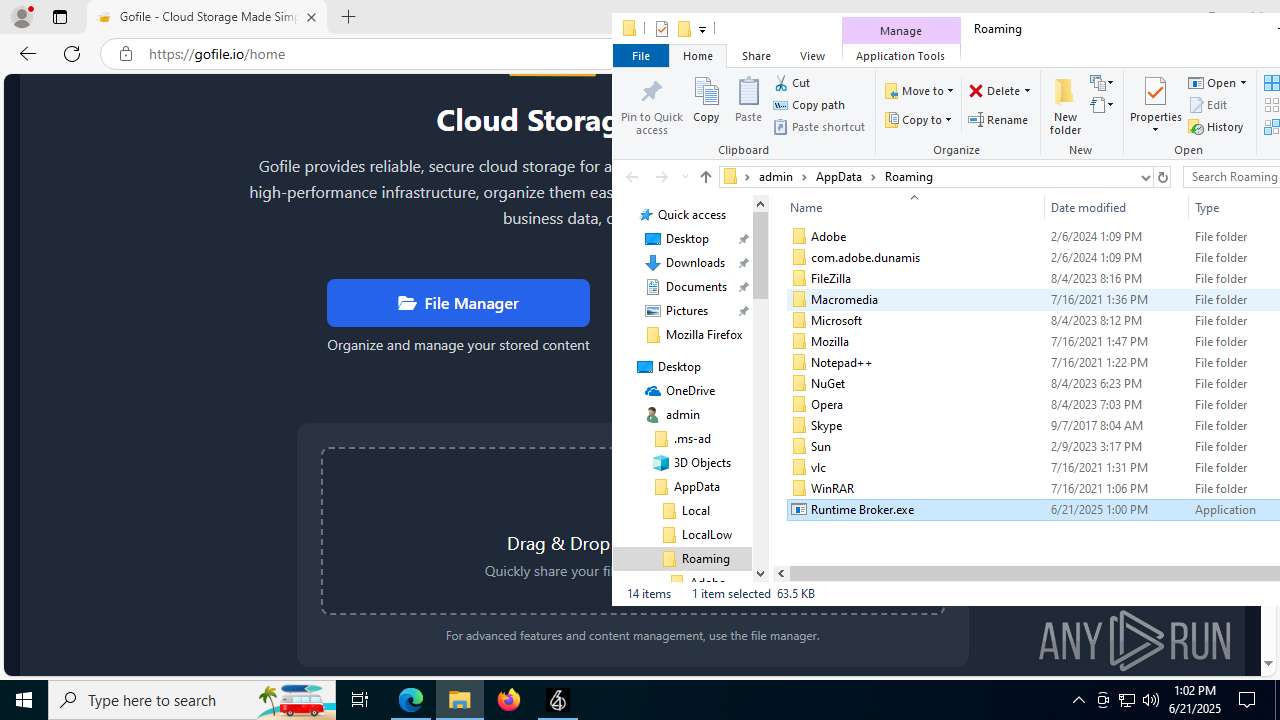
- Runtime Broker.exe (PID: 2664)
SUSPICIOUS
Reads security settings of Internet Explorer
- 64_Service (1).exe (PID: 504)
- tmp7B0C.exe (PID: 3844)
- Runtime Broker.exe (PID: 5644)
- Runtime Broker.exe (PID: 1180)
Writes data into a file (POWERSHELL)
- 64_Service (1).exe (PID: 504)
Executable content was dropped or overwritten
- 64_Service (1).exe (PID: 504)
- tmp7B0C.exe (PID: 3844)
- Runtime Broker.exe (PID: 5644)
- Runtime Broker.exe (PID: 1180)
Reads the date of Windows installation
- 64_Service (1).exe (PID: 504)
- tmp7B0C.exe (PID: 3844)
- Runtime Broker.exe (PID: 5644)
- Runtime Broker.exe (PID: 1180)
Process drops legitimate windows executable
- tmp7B0C.exe (PID: 3844)
- Runtime Broker.exe (PID: 5644)
- Runtime Broker.exe (PID: 1180)
Executing commands from a ".bat" file
- Runtime Broker.exe (PID: 5644)
- Runtime Broker.exe (PID: 1180)
Starts CMD.EXE for commands execution
- Runtime Broker.exe (PID: 5644)
- Runtime Broker.exe (PID: 1180)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1896)
- cmd.exe (PID: 3672)
The executable file from the user directory is run by the CMD process
- Runtime Broker.exe (PID: 1192)
- Runtime Broker.exe (PID: 2664)
There is functionality for taking screenshot (YARA)
- tmp7B0C.exe (PID: 3844)
INFO
Checks supported languages
- 64_Service (1).exe (PID: 504)
- Runtime Broker.exe (PID: 5644)
- tmp7B0C.exe (PID: 3844)
- Runtime Broker.exe (PID: 1180)
- Runtime Broker.exe (PID: 1192)
- Runtime Broker.exe (PID: 2664)
- identity_helper.exe (PID: 1192)
Create files in a temporary directory
- 64_Service (1).exe (PID: 504)
- tmp7B0C.exe (PID: 3844)
- Runtime Broker.exe (PID: 5644)
- Runtime Broker.exe (PID: 1180)
Reads the machine GUID from the registry
- 64_Service (1).exe (PID: 504)
- tmp7B0C.exe (PID: 3844)
- Runtime Broker.exe (PID: 1180)
- Runtime Broker.exe (PID: 5644)
- Runtime Broker.exe (PID: 2664)
Reads the computer name
- 64_Service (1).exe (PID: 504)
- tmp7B0C.exe (PID: 3844)
- Runtime Broker.exe (PID: 1192)
- Runtime Broker.exe (PID: 1180)
- Runtime Broker.exe (PID: 5644)
- Runtime Broker.exe (PID: 2664)
- identity_helper.exe (PID: 1192)
Reads Environment values
- 64_Service (1).exe (PID: 504)
- tmp7B0C.exe (PID: 3844)
- identity_helper.exe (PID: 1192)
Reads the software policy settings
- 64_Service (1).exe (PID: 504)
- tmp7B0C.exe (PID: 3844)
- slui.exe (PID: 1508)
Checks if a key exists in the options dictionary (POWERSHELL)
- 64_Service (1).exe (PID: 504)
Disables trace logs
- 64_Service (1).exe (PID: 504)
- tmp7B0C.exe (PID: 3844)
Checks proxy server information
- 64_Service (1).exe (PID: 504)
- tmp7B0C.exe (PID: 3844)
- slui.exe (PID: 1508)
Process checks computer location settings
- tmp7B0C.exe (PID: 3844)
- 64_Service (1).exe (PID: 504)
- Runtime Broker.exe (PID: 5644)
- Runtime Broker.exe (PID: 1180)
Creates files in the program directory
- tmp7B0C.exe (PID: 3844)
Creates files or folders in the user directory
- Runtime Broker.exe (PID: 5644)
- Runtime Broker.exe (PID: 1180)
Uses Task Scheduler to autorun other applications (AUTOMATE)
- cmd.exe (PID: 5992)
Confuser has been detected (YARA)
- tmp7B0C.exe (PID: 3844)
Application launched itself
- msedge.exe (PID: 6404)
Manual execution by a user
- msedge.exe (PID: 6404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(2664) Runtime Broker.exe
C2 (1)157.97.11.134
Ports (1)8080
Version1.0.7
Options
AutoRuntrue
MutexRuntime Broker
InstallFolder%AppData%
Certificates
Cert1MIICMDCCAZmgAwIBAgIVAI7IWFdXoYnjjoSxMJDHb6HBFJn1MA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDERjUmF0IFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTI0MDQxODEzMjEwOVoXDTM1MDEyNjEzMjEwOVowEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A...
Server_SignatureNLqOIqgiYwv0g0nLgMUhjxjc71I6fkPc77aTDWkm3zNL92/PeiWTrdOrOybtJMVQmrFIN40qUVws1ryr+92aSPXkDoCz46QVp32YBU3y7wZWsHGMtWaAysXOgtMLPr6bcFnovhCioLqaLRQt4uJPANRHQfks4XZ3H+oVb6DnfEA=
Keys
AES00df1dd8c6e7a780af0500903c623e5cb651b6dcb246a4d3df97b3fe3fdf5c72
SaltDcRatByqwqdanchun
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:23 20:32:00+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 25600 |
| InitializedDataSize: | 190464 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x827e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.1.1.1 |
| ProductVersionNumber: | 1.1.1.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 1.1.1.1 |
| InternalName: | 769F - Copy.exe |
| LegalCopyright: | |
| OriginalFileName: | 769F - Copy.exe |
| ProductName: | 64 Service |
| ProductVersion: | 1.1.1.1 |
| AssemblyVersion: | 1.1.1.1 |
Total processes
191
Monitored processes
49
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 504 | "C:\Users\admin\AppData\Local\Temp\64_Service (1).exe" | C:\Users\admin\AppData\Local\Temp\64_Service (1).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 1.1.1.1 Modules
| |||||||||||||||
| 620 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2792,i,6341009034245481136,4751900109052363890,262144 --variations-seed-version --mojo-platform-channel-handle=2848 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1036 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --always-read-main-dll --field-trial-handle=6844,i,6341009034245481136,4751900109052363890,262144 --variations-seed-version --mojo-platform-channel-handle=6836 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1180 | "C:\ProgramData\SystemCache64\Runtime Broker.exe" | C:\ProgramData\SystemCache64\Runtime Broker.exe | tmp7B0C.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Runtime Broker Exit code: 0 Version: 6.2.19041.3636 Modules
| |||||||||||||||
| 1192 | "C:\Users\admin\AppData\Roaming\Runtime Broker.exe" | C:\Users\admin\AppData\Roaming\Runtime Broker.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Runtime Broker Exit code: 4294967295 Version: 6.2.19041.3636 Modules
| |||||||||||||||
| 1192 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6644,i,6341009034245481136,4751900109052363890,262144 --variations-seed-version --mojo-platform-channel-handle=6660 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1208 | "C:\Users\admin\AppData\Local\Temp\64_Service (1).exe" | C:\Users\admin\AppData\Local\Temp\64_Service (1).exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 1.1.1.1 Modules
| |||||||||||||||
| 1508 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1896 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\tmp86C4.tmp.bat"" | C:\Windows\System32\cmd.exe | — | Runtime Broker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 173
Read events
20 055
Write events
115
Delete events
3
Modification events
| (PID) Process: | (504) 64_Service (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service (1)_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (504) 64_Service (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service (1)_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (504) 64_Service (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service (1)_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (504) 64_Service (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service (1)_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (504) 64_Service (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service (1)_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (504) 64_Service (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service (1)_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (504) 64_Service (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service (1)_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (504) 64_Service (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service (1)_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (504) 64_Service (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service (1)_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (504) 64_Service (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service (1)_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
36
Suspicious files
468
Text files
85
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6404 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF18e402.TMP | — | |
MD5:— | SHA256:— | |||
| 6404 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6404 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF18e412.TMP | — | |
MD5:— | SHA256:— | |||
| 6404 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6404 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF18e412.TMP | — | |
MD5:— | SHA256:— | |||
| 6404 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6404 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF18e421.TMP | — | |
MD5:— | SHA256:— | |||
| 6404 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6404 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:CDDDC745A8C954DC438C931889999BDB | SHA256:3DC9043838386F5363AC96A01477CF3163B5118B80191576A11B32CE9894314C | |||
| 1180 | Runtime Broker.exe | C:\Users\admin\AppData\Roaming\Runtime Broker.exe | executable | |
MD5:03D6F540DABC52C2B6764C7F9E37E6F4 | SHA256:3536D24588D5363B1C6BAACC2EC62054004860F950425EA26CDAAEEB8CE8EA1E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
131
DNS requests
109
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7020 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3580 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3580 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
7764 | svchost.exe | HEAD | 200 | 2.19.11.120:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751024771&P2=404&P3=2&P4=Kl9s2HBbC0ccZn5xiFP7jDUEpClz%2f2OIXwSY%2fHhEV3FgtBNF%2fAU7qhsaYbw8aqz2xcAac6qGWklTIXYP%2fbilNg%3d%3d | unknown | — | — | whitelisted |
4752 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:IIHu_whClFm14s1RtXeqBmqjnbQHIBQ_MhNtXgDpMUo&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
7764 | svchost.exe | GET | 206 | 2.19.11.120:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751024771&P2=404&P3=2&P4=Kl9s2HBbC0ccZn5xiFP7jDUEpClz%2f2OIXwSY%2fHhEV3FgtBNF%2fAU7qhsaYbw8aqz2xcAac6qGWklTIXYP%2fbilNg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4844 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
504 | 64_Service (1).exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
504 | 64_Service (1).exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
7020 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7020 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3844 | tmp7B0C.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
prod.keyauth.com |
| malicious |
nexusrules.officeapps.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
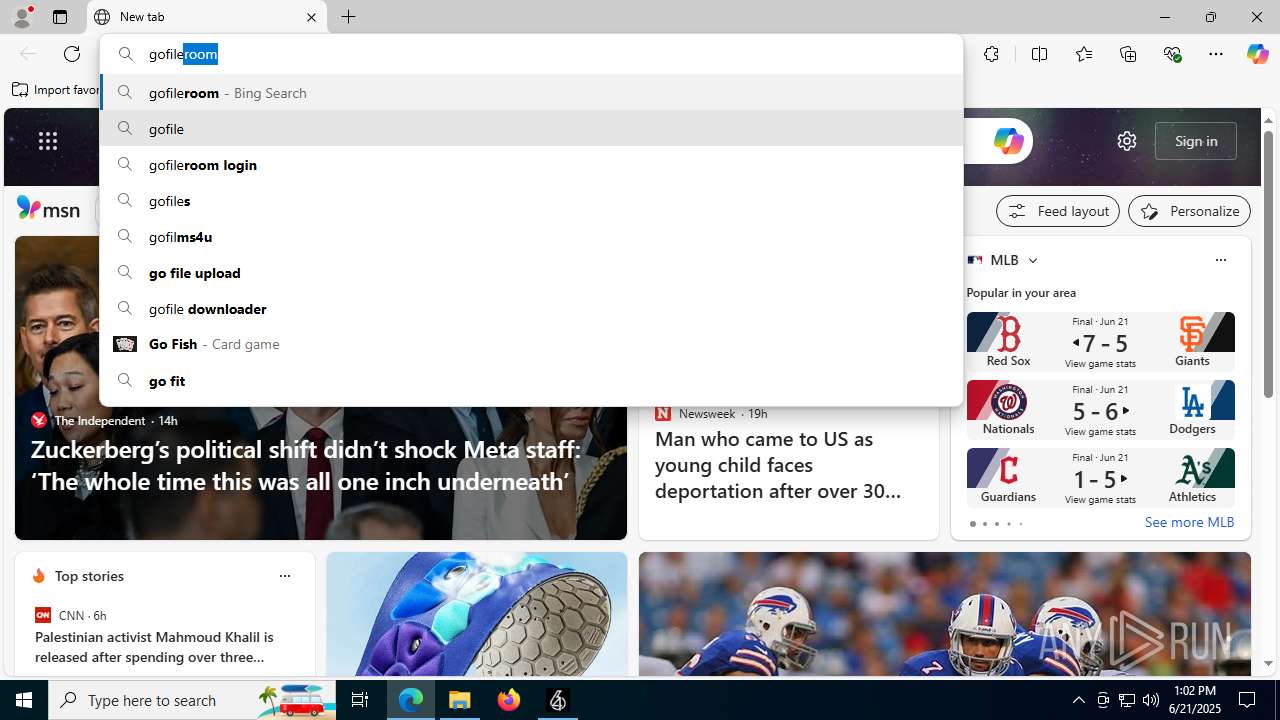
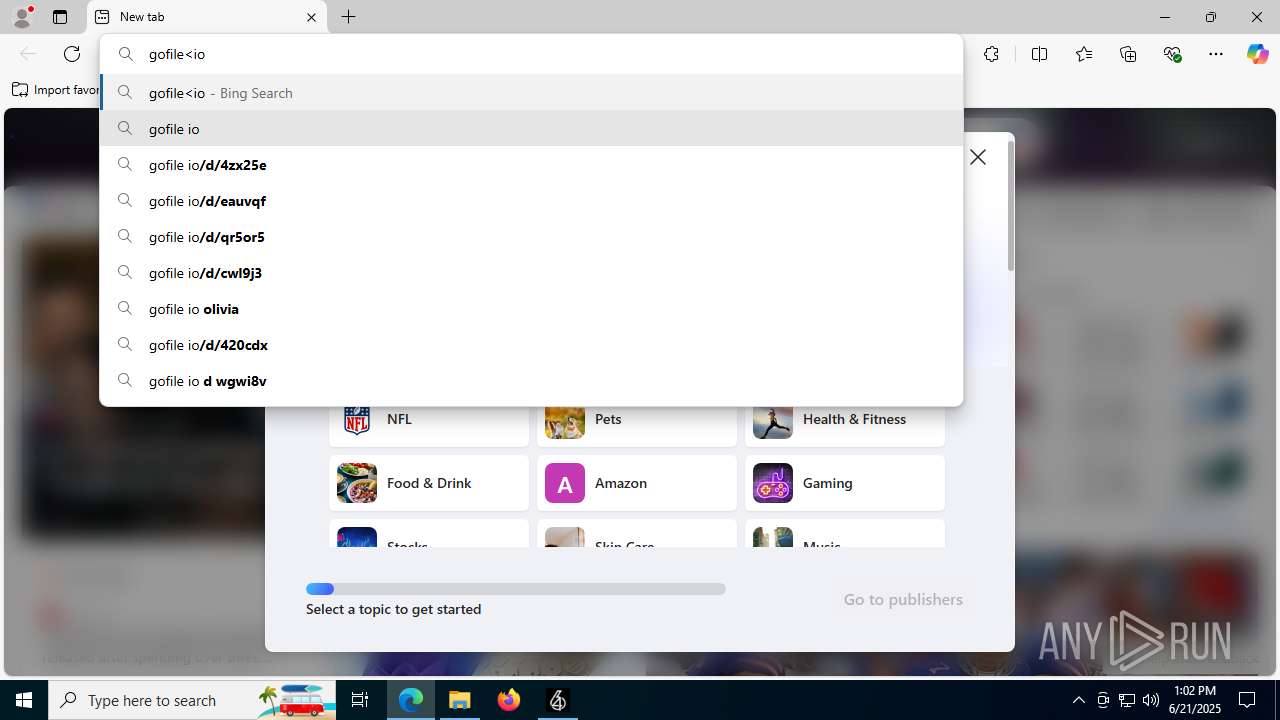
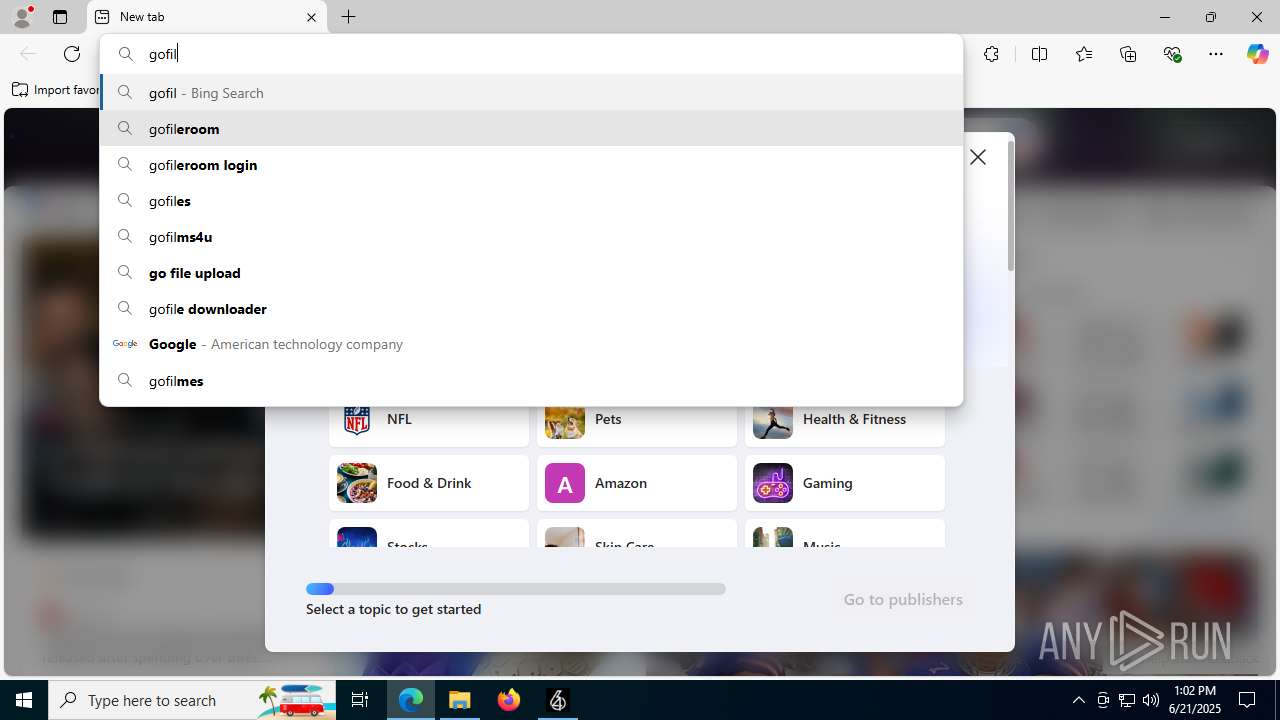
4752 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
4752 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
4752 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
4752 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
4752 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
4752 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
4752 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
4752 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
4752 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |