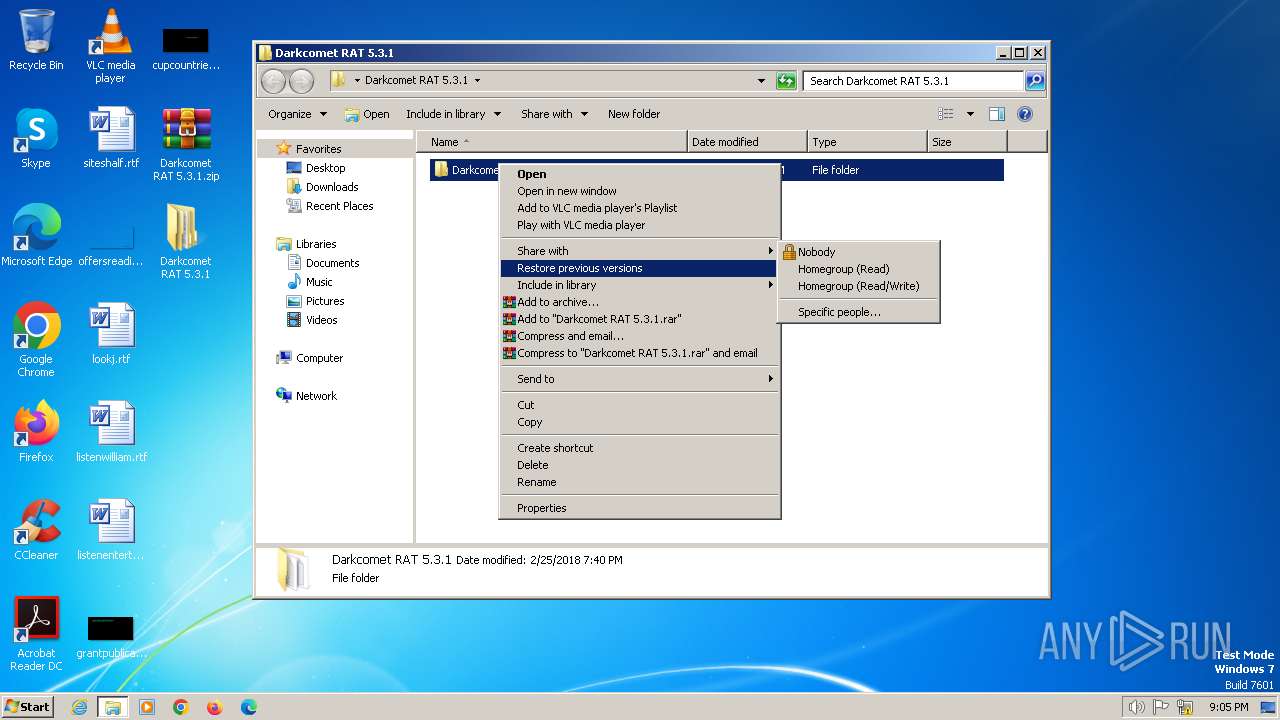
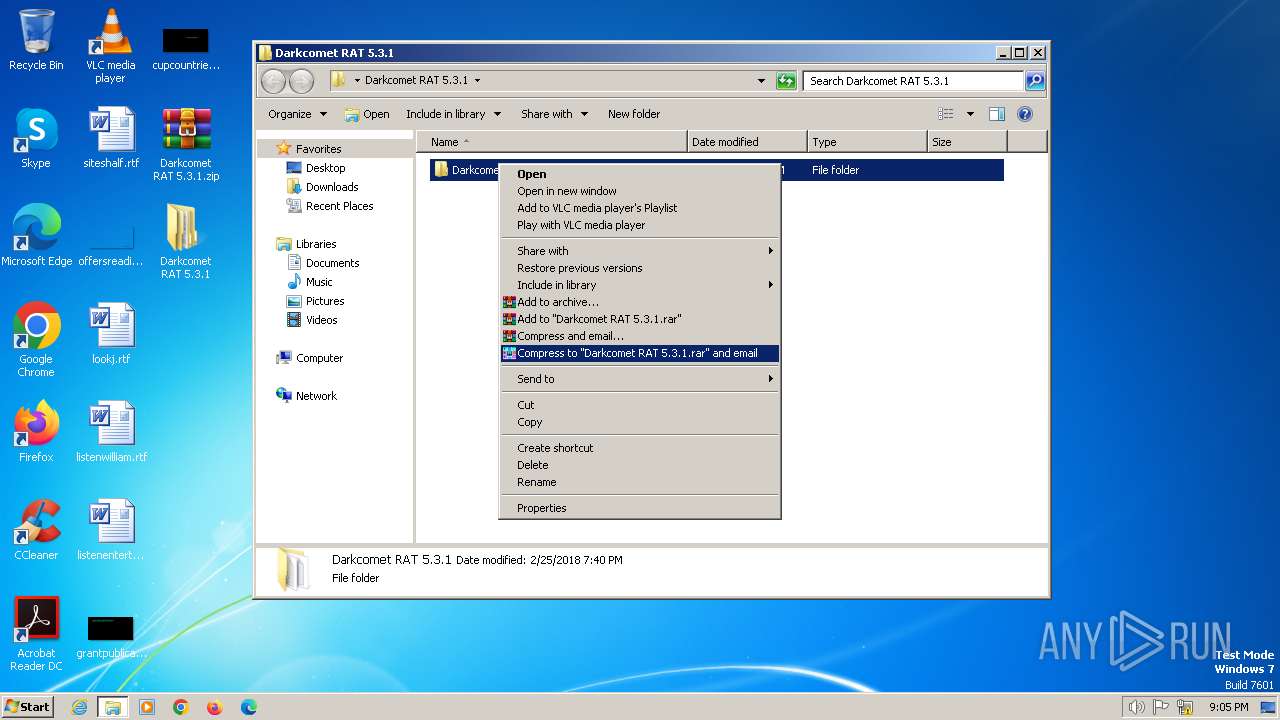
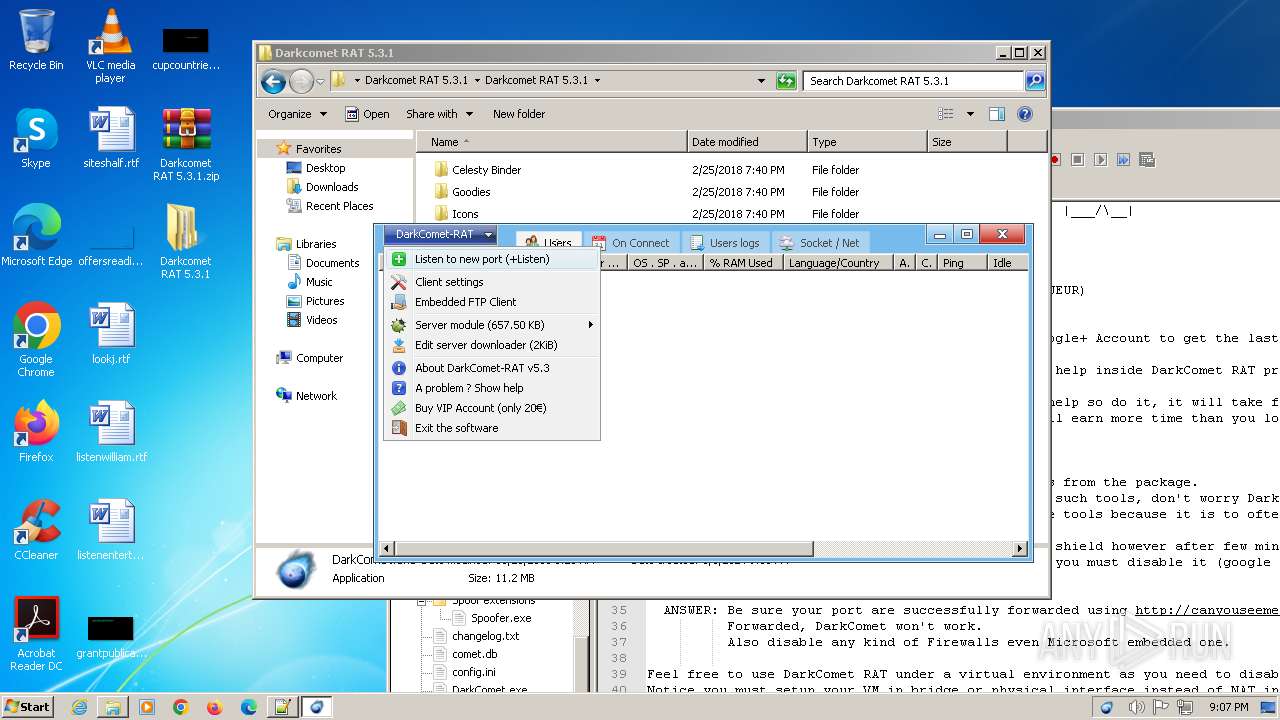
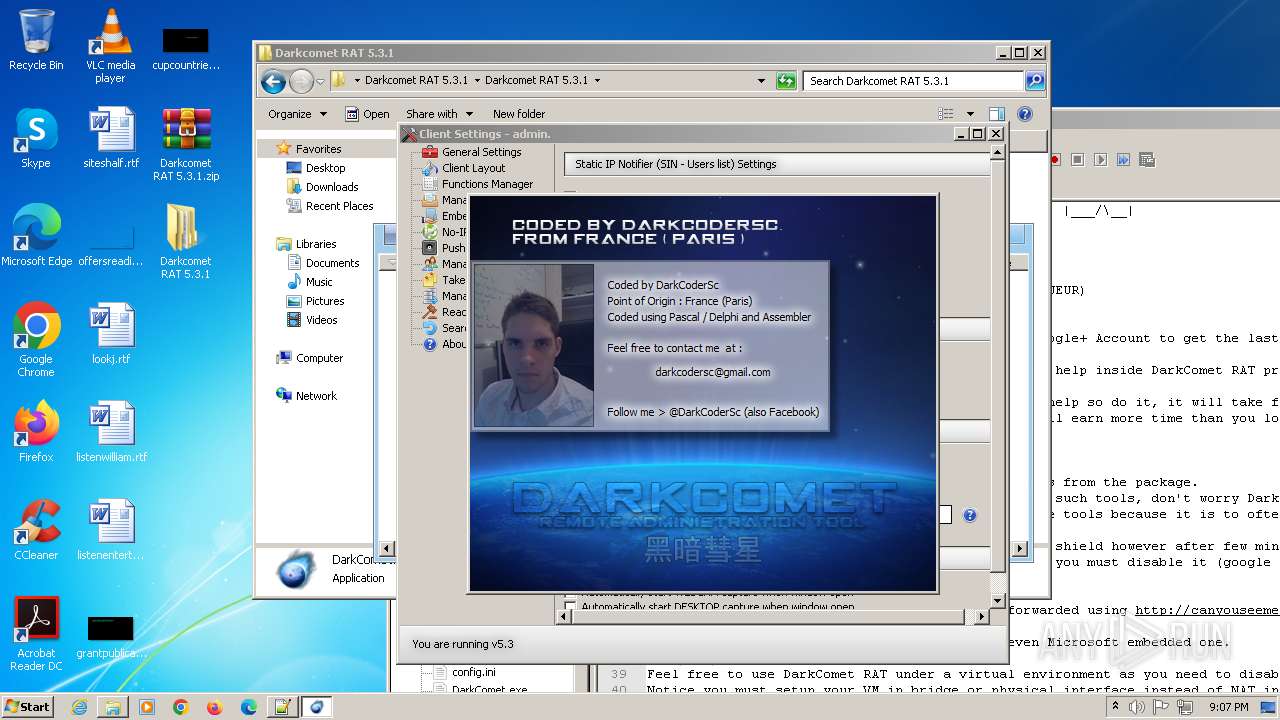
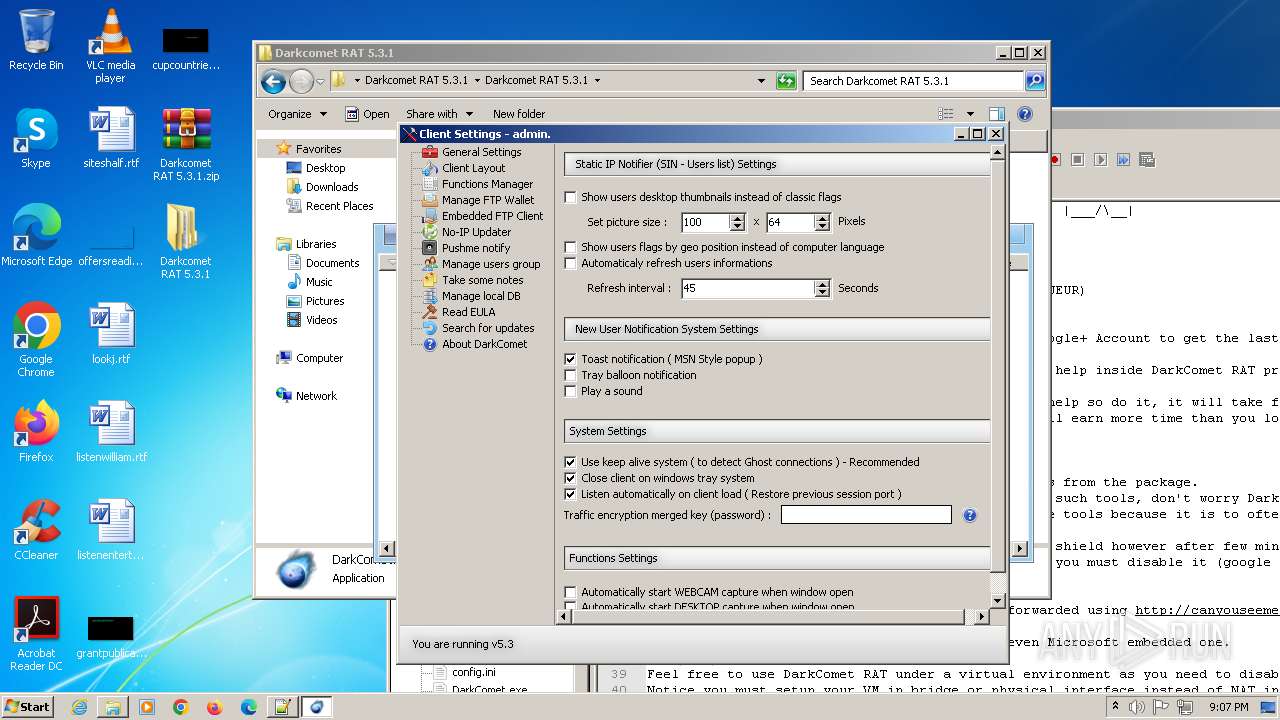
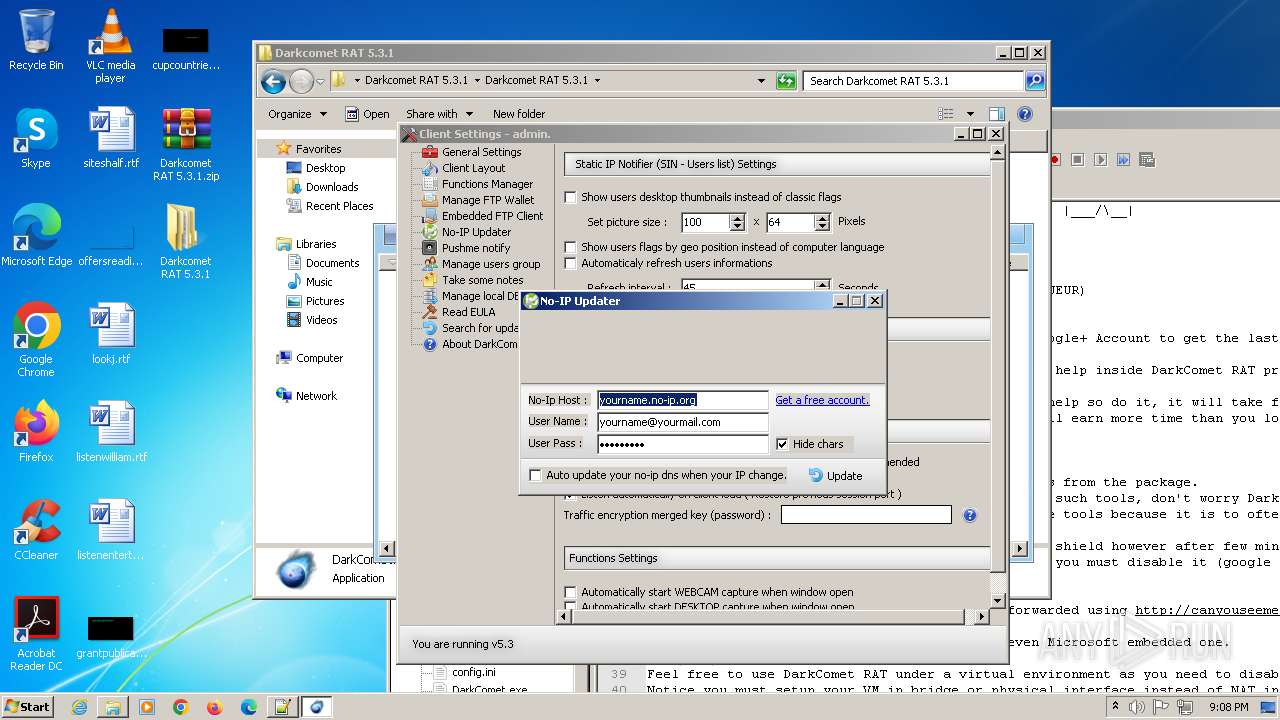
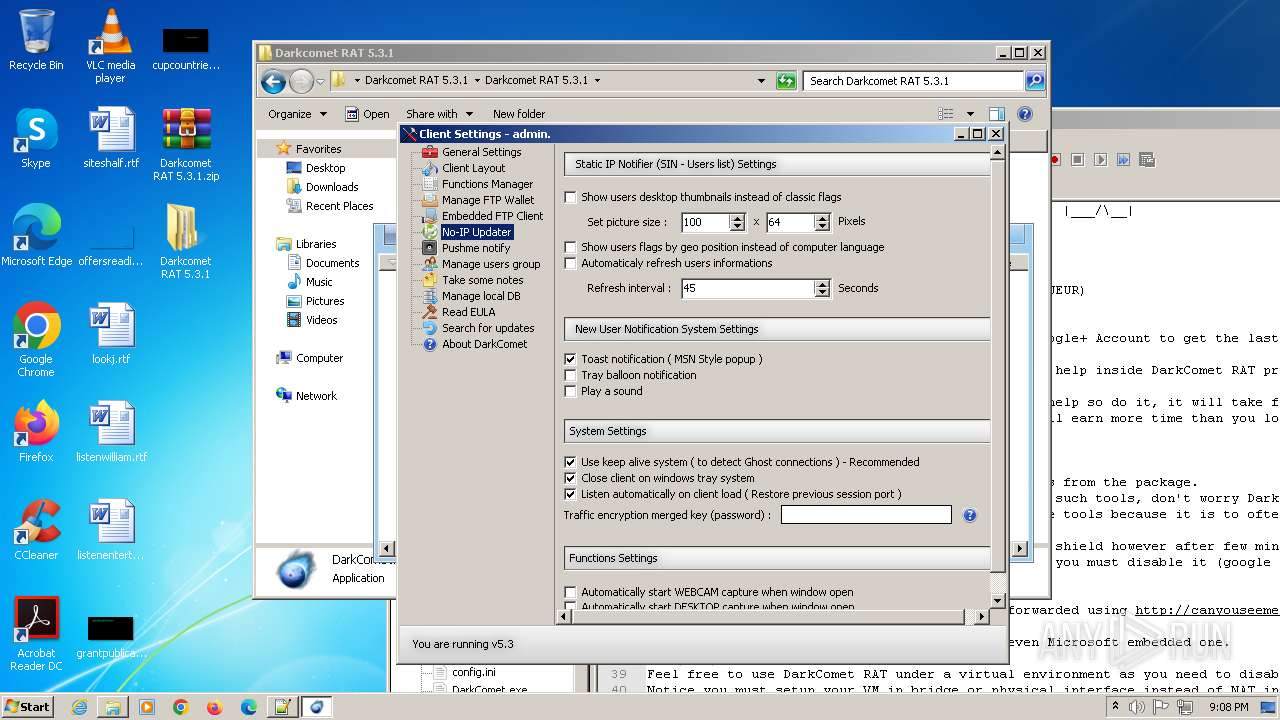
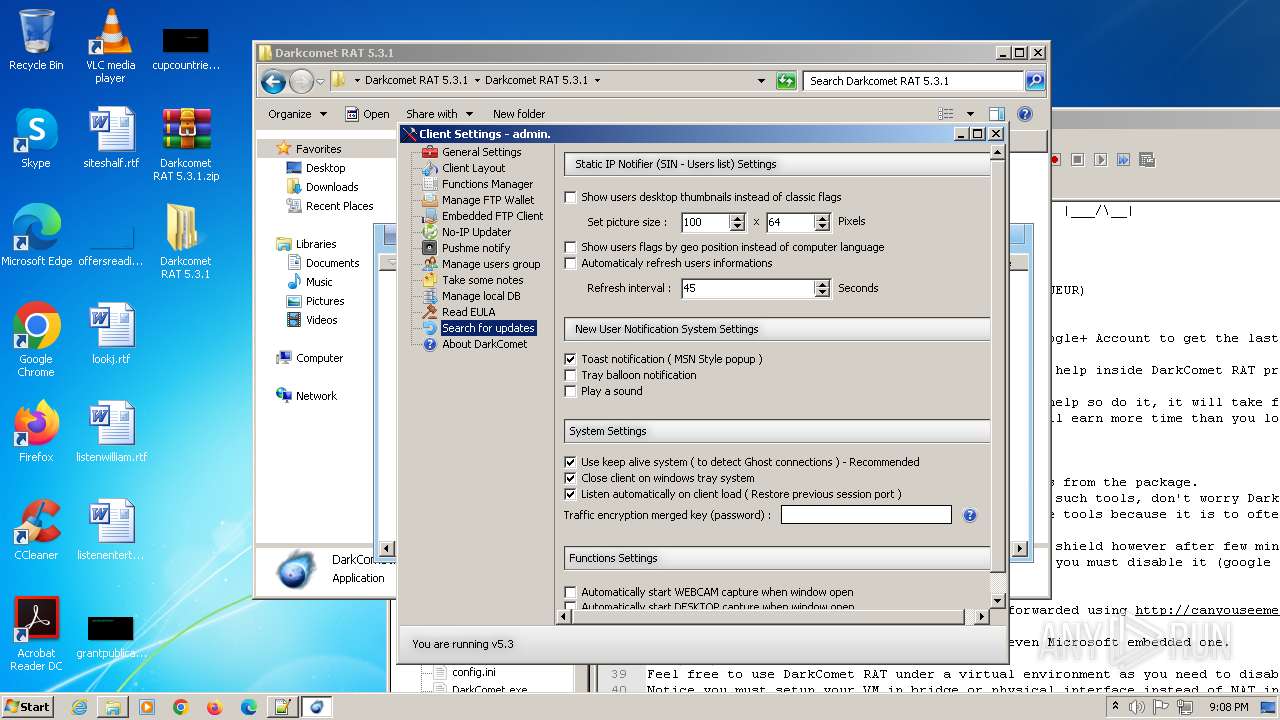
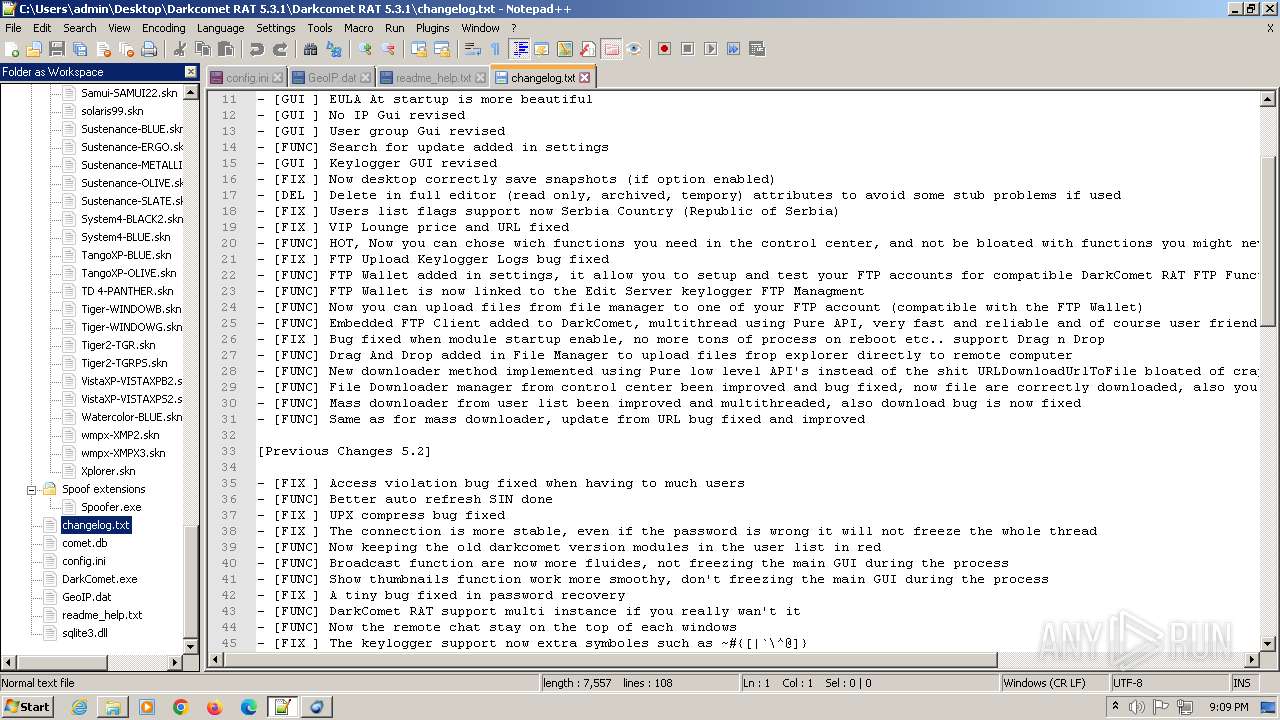
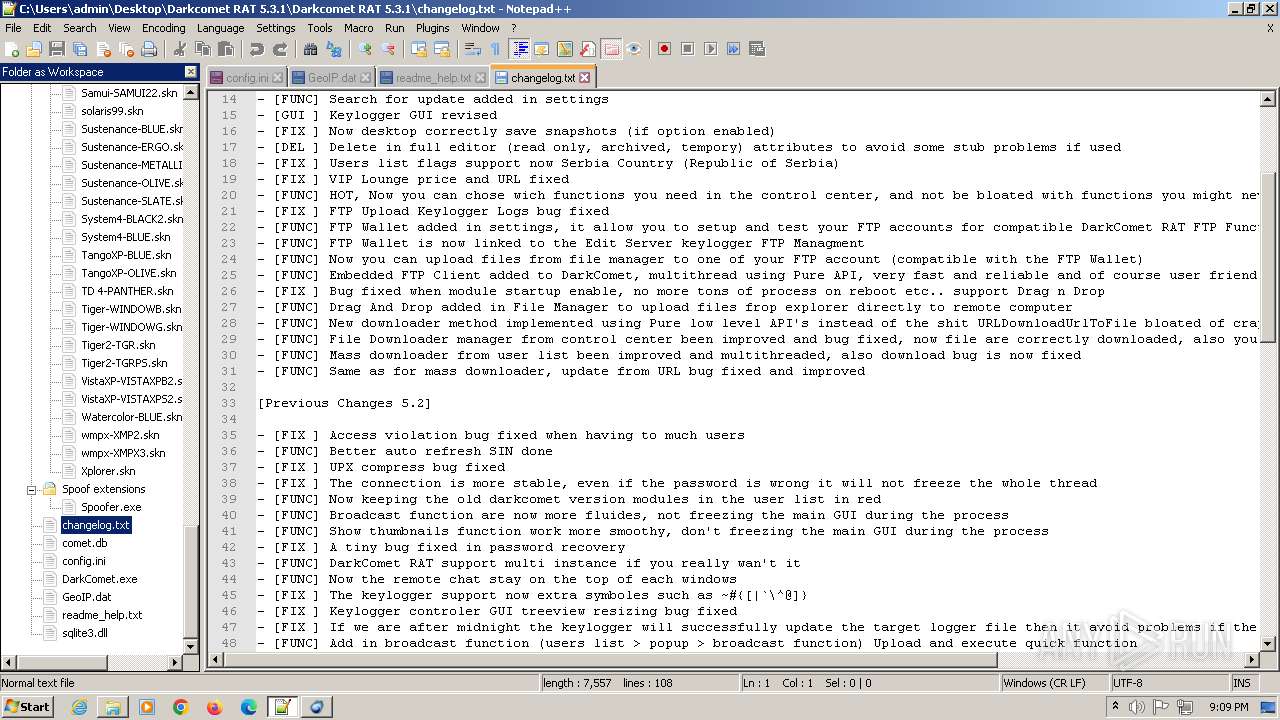
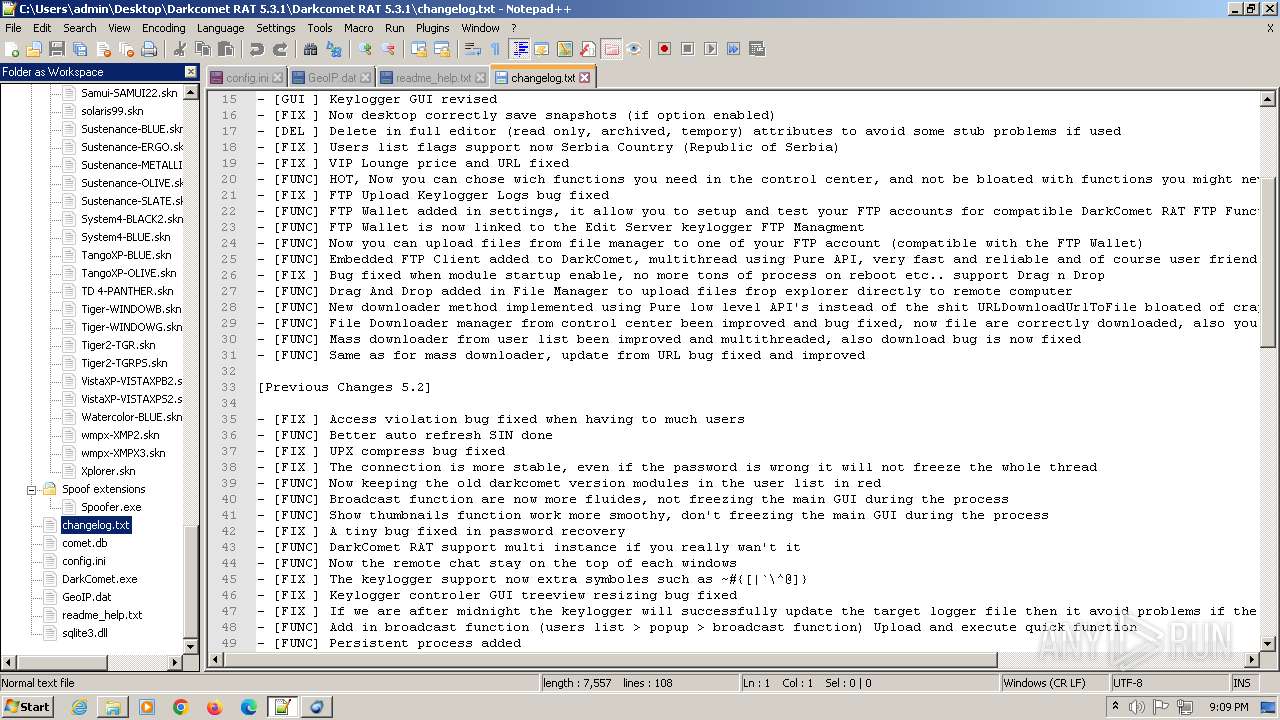
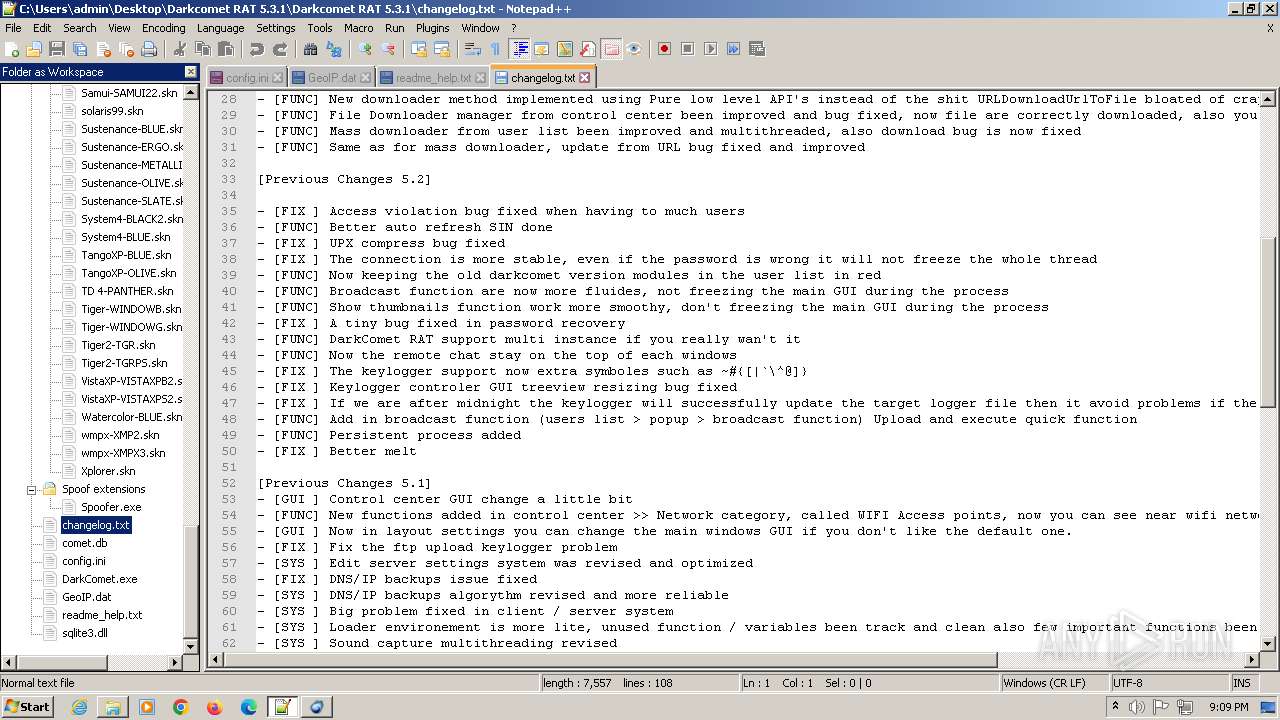
| File name: | Darkcomet RAT 5.3.1.zip |
| Full analysis: | https://app.any.run/tasks/c29086e5-5e04-43c2-8761-9e0167e3a0c0 |
| Verdict: | Malicious activity |
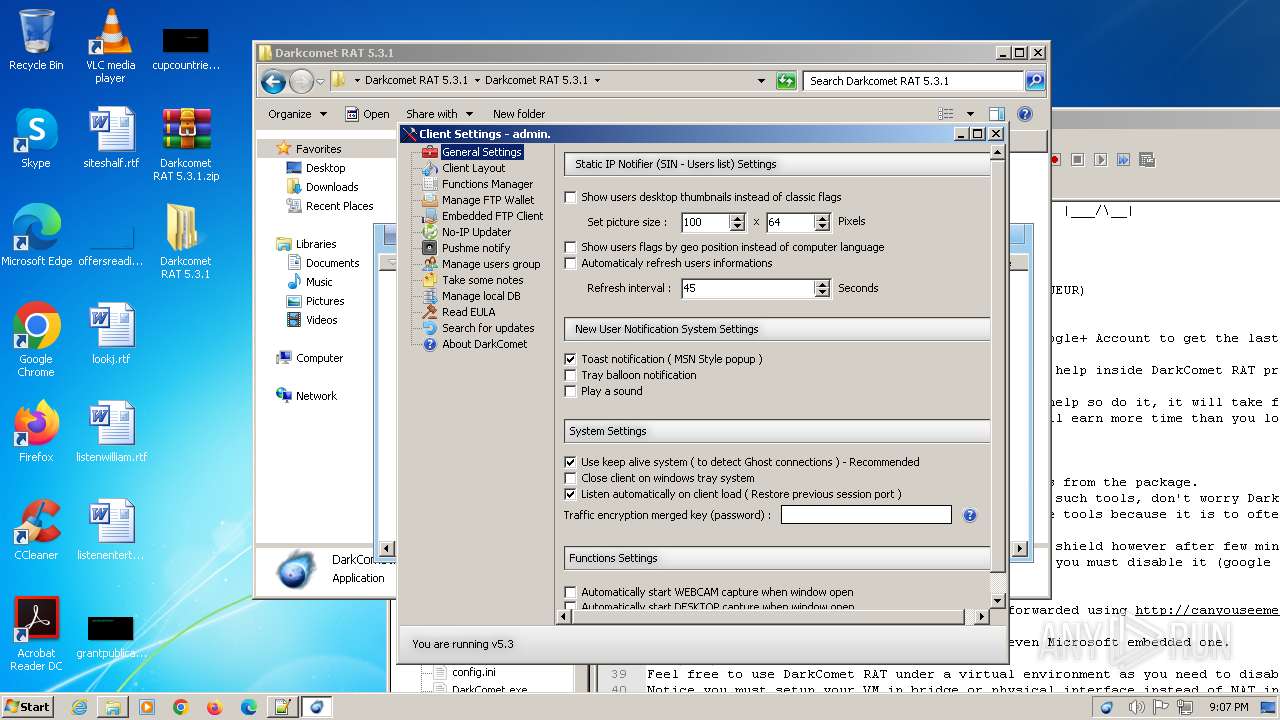
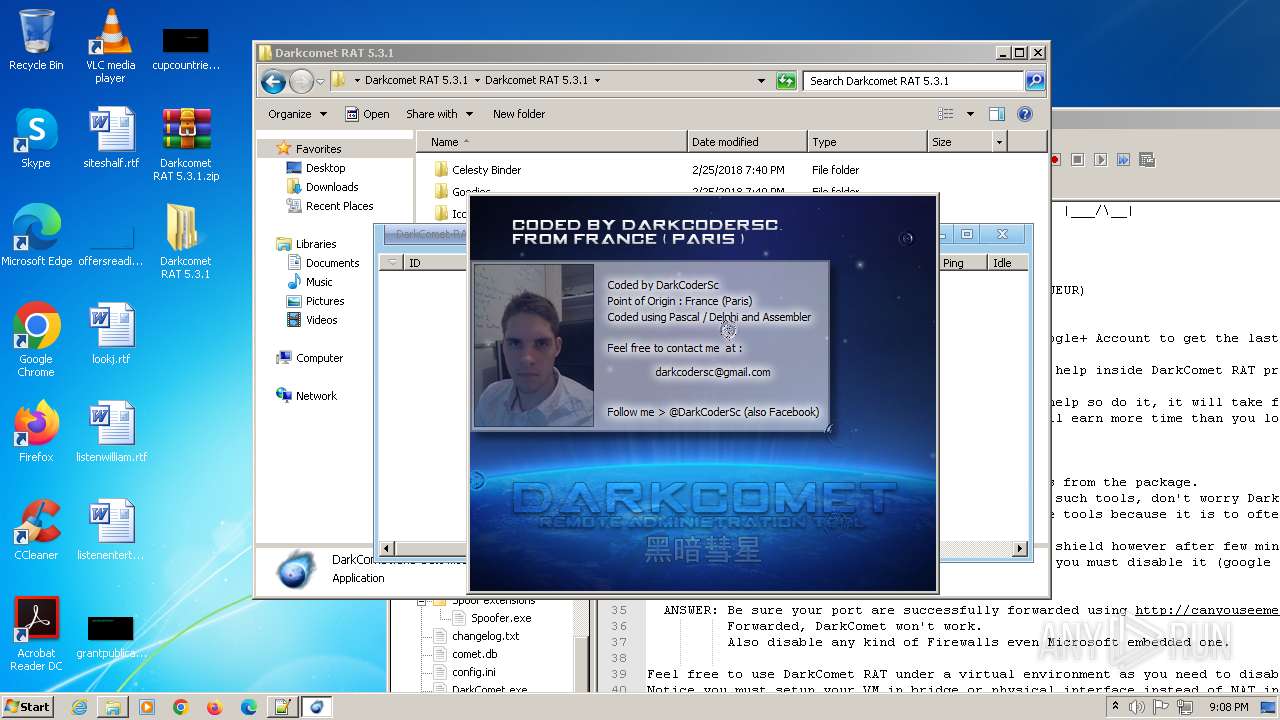
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | January 05, 2024, 21:05:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 9F9347ECF2CC6541FB64ACD6FC0A5749 |
| SHA1: | 6C0D454EC2068D1C7D502A167CA02C8DAFD0B244 |
| SHA256: | BFE9A76229E6E502B7C542007CD976DD3B5E0D26190CDF7CC8A5E5AAB0A63F7D |
| SSDEEP: | 393216:Yia1rsEqp8mxBktqBEH3JM/qbxhbRLEJt5RXtW3hg:Yl1rsEqJxChH3coxhbePK3hg |
MALICIOUS
DARKCOMET has been detected (YARA)
- DarkComet.exe (PID: 1740)
SUSPICIOUS
Reads settings of System Certificates
- msdt.exe (PID: 2464)
Reads the Internet Settings
- sdiagnhost.exe (PID: 1148)
Check the default browser
- notepad++.exe (PID: 1504)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2020)
- msdt.exe (PID: 2464)
Drops a (possible) Coronavirus decoy
- WinRAR.exe (PID: 2020)
Process drops legitimate windows executable
- msdt.exe (PID: 2464)
Manual execution by a user
- notepad++.exe (PID: 1504)
- DarkComet.exe (PID: 1740)
Reads security settings of Internet Explorer
- sdiagnhost.exe (PID: 1148)
- msdt.exe (PID: 2464)
Create files in a temporary directory
- msdt.exe (PID: 2464)
Checks supported languages
- DarkComet.exe (PID: 1740)
Reads the computer name
- DarkComet.exe (PID: 1740)
Creates files or folders in the user directory
- msdt.exe (PID: 2464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:02:25 11:40:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Darkcomet RAT 5.3.1/ |
Total processes
43
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1148 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1504 | "C:\Program Files\Notepad++\notepad++.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 1740 | "C:\Users\admin\Desktop\Darkcomet RAT 5.3.1\Darkcomet RAT 5.3.1\DarkComet.exe" | C:\Users\admin\Desktop\Darkcomet RAT 5.3.1\Darkcomet RAT 5.3.1\DarkComet.exe | explorer.exe | ||||||||||||
User: admin Company: Unremote.org Integrity Level: MEDIUM Description: A remote administration tool from the cosmos Exit code: 0 Version: 4.2.0.28 Modules
| |||||||||||||||
| 2020 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Darkcomet RAT 5.3.1.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2152 | "C:\Program Files\Internet Explorer\iexplore.exe" http://www.darkcomet-source.tk/ | C:\Program Files\Internet Explorer\iexplore.exe | notepad++.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2464 | -modal 131714 -skip TRUE -path C:\Windows\diagnostics\system\networking -af C:\Users\admin\AppData\Local\Temp\NDFB2A3.tmp -ep NetworkDiagnosticsWeb | C:\Windows\System32\msdt.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2700 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:2152 CREDAT:267521 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3032 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 -px64 | C:\Program Files\Notepad++\updater\GUP.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 4294967295 Version: 4.1 Modules
| |||||||||||||||
Total events
5 046
Read events
4 918
Write events
126
Delete events
2
Modification events
| (PID) Process: | (2020) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\15A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2020) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2020) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7AndW2K8R2-KB3191566-x64.zip | |||
| (PID) Process: | (2020) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2020) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_3-win64-mingw.zip | |||
| (PID) Process: | (2020) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2020) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2020) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2020) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2020) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF1600000016000000D60300000B020000 | |||
Executable files
6
Suspicious files
150
Text files
70
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2020 | WinRAR.exe | C:\Users\admin\Desktop\Darkcomet RAT 5.3.1\Darkcomet RAT 5.3.1\Celesty Binder\Lang\EN.ini | text | |
MD5:D5B95D8DBCDCC5BE0290067BE9043009 | SHA256:48A43817F513A7DE5F033F842EA71DCEC7CFE45E2EDC87BE844E461D99E2572E | |||
| 2020 | WinRAR.exe | C:\Users\admin\Desktop\Darkcomet RAT 5.3.1\Darkcomet RAT 5.3.1\Celesty Binder\Lang\FR.ini | text | |
MD5:A8568B41DF3F0A47F875964E8FEEFA70 | SHA256:F515EE7D43CF301FE771599C60E2771DB6F27E614AF6A4403771A0D99CB19BC7 | |||
| 2020 | WinRAR.exe | C:\Users\admin\Desktop\Darkcomet RAT 5.3.1\Darkcomet RAT 5.3.1\Celesty Binder\Lang\ES.ini | text | |
MD5:4745B84E71D23454D2535CC608DE57D0 | SHA256:EB0553309ACD121B01566C1CA297ED46E896E3AD11C486971E8FA7275A1FF061 | |||
| 2020 | WinRAR.exe | C:\Users\admin\Desktop\Darkcomet RAT 5.3.1\Darkcomet RAT 5.3.1\Celesty Binder\Lang\GR.ini | text | |
MD5:8B35CDF90F3D89D2502E1F61B2BBF631 | SHA256:FCA01673CB23ABD479B6D54D19A40A87E9D72B90ECC7F5D59AF14D192CC07C7C | |||
| 2020 | WinRAR.exe | C:\Users\admin\Desktop\Darkcomet RAT 5.3.1\Darkcomet RAT 5.3.1\Celesty Binder\Lang\AR.ini | text | |
MD5:4276808F92D3EFE8359CB03F9C45C9E1 | SHA256:C4E0CD4D29594C9CB188DEAB7BB5F73FC6B3ED832468322ABC05B4E981C306C4 | |||
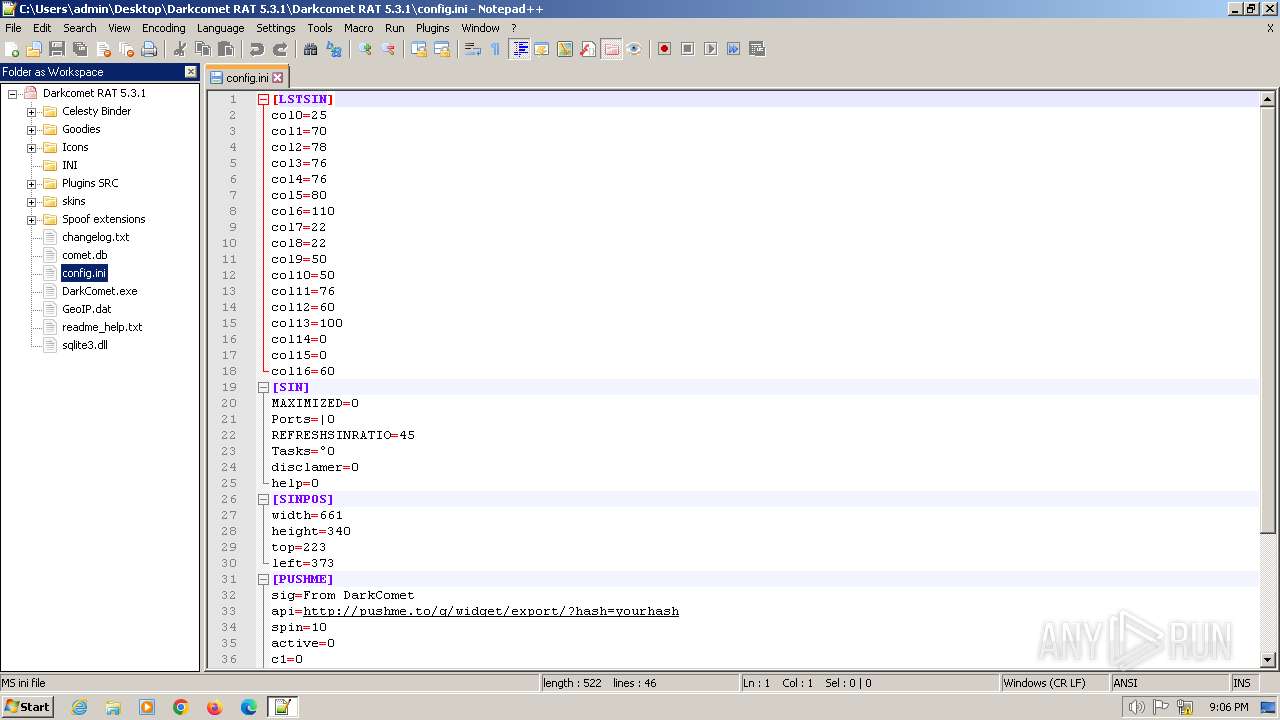
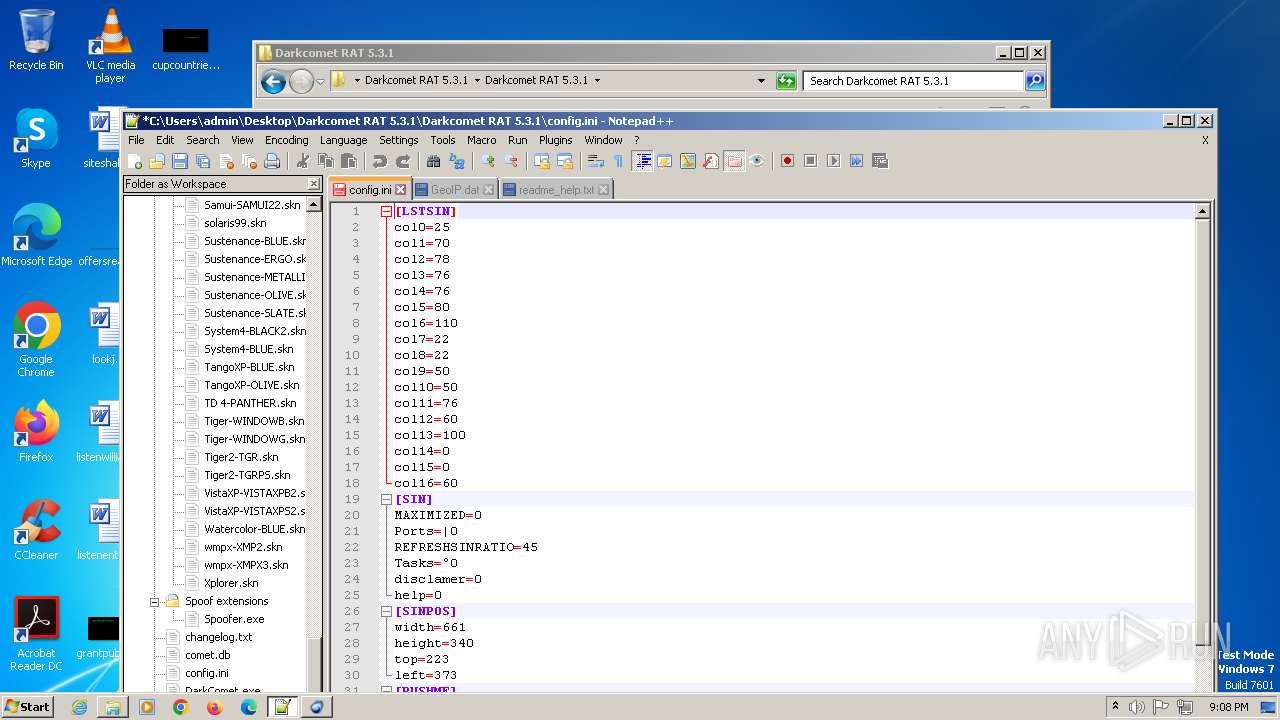
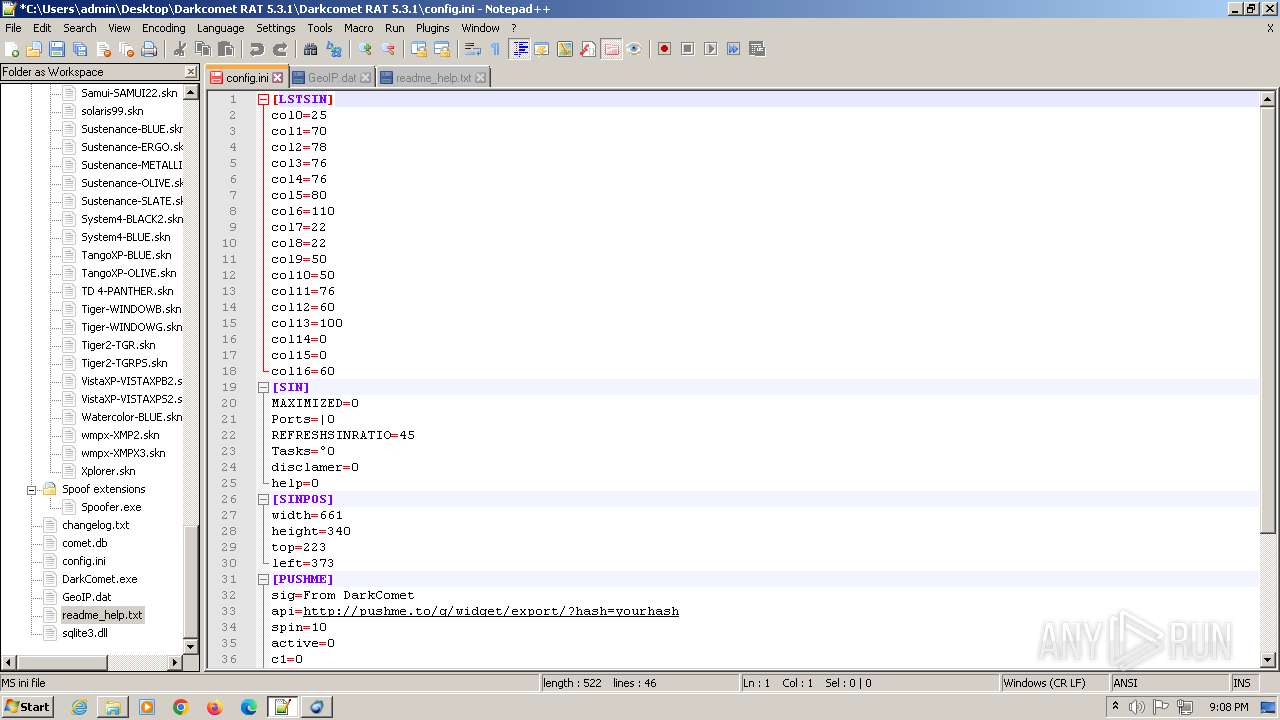
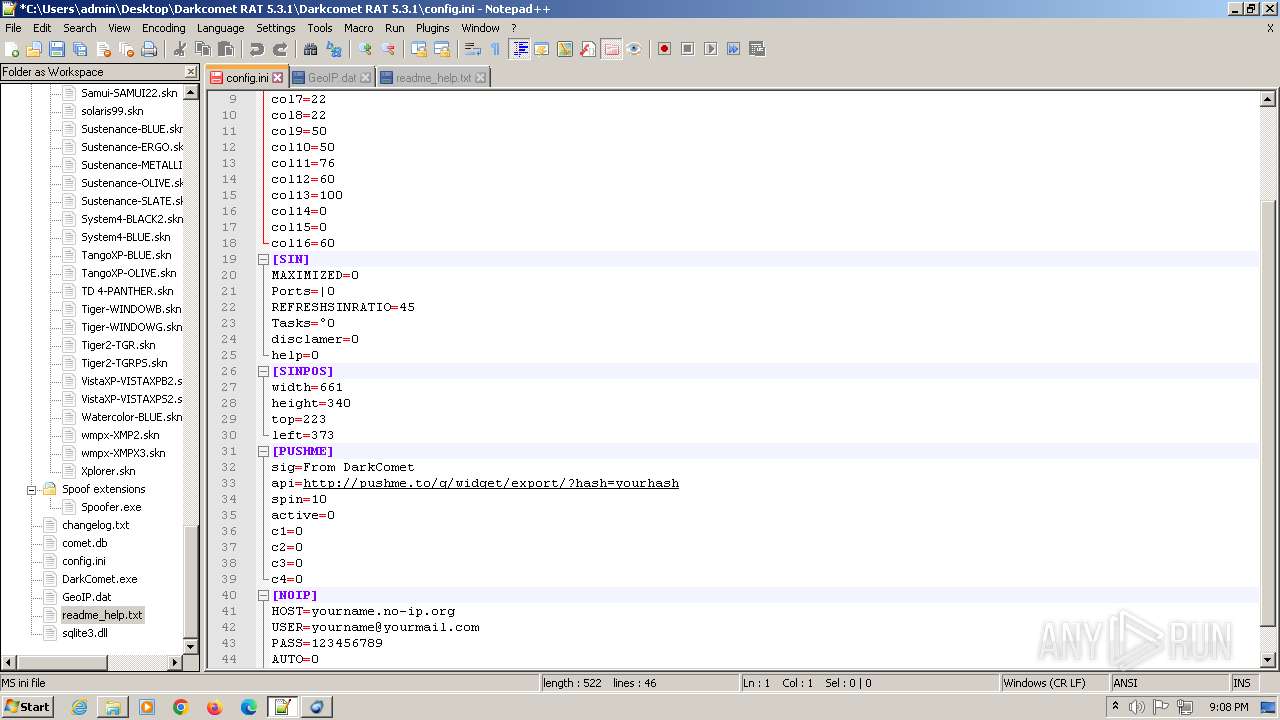
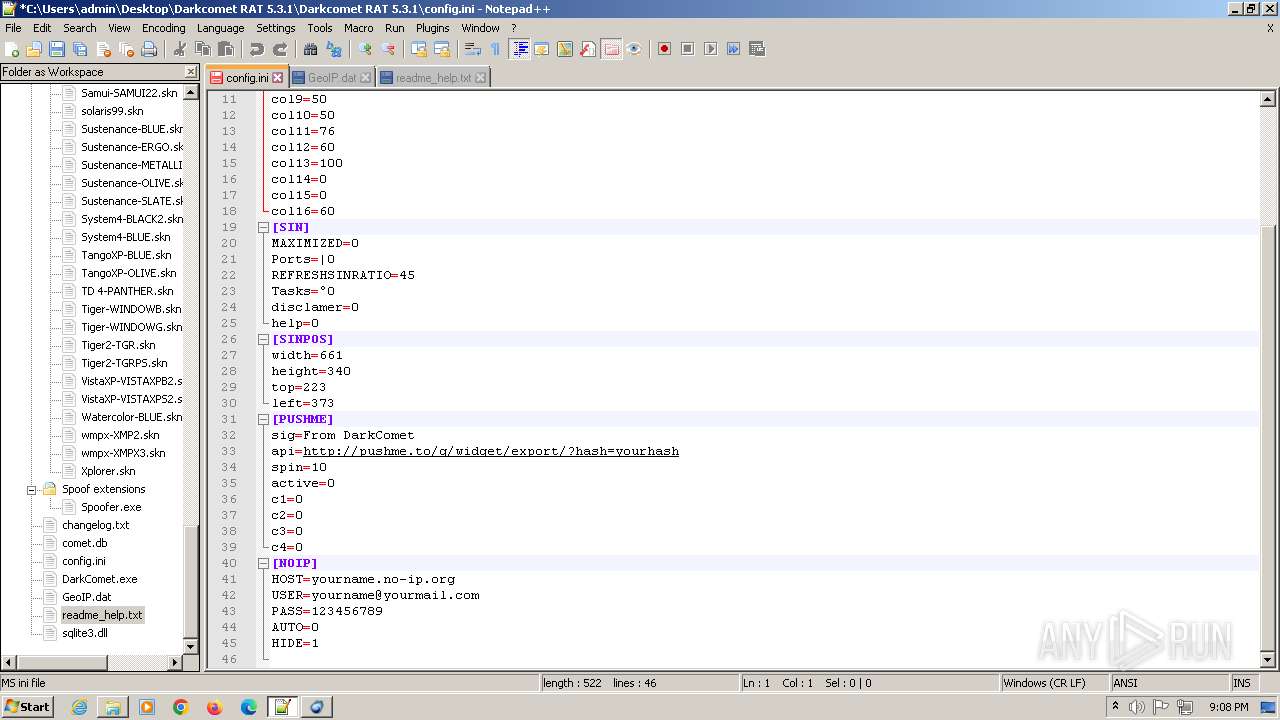
| 2020 | WinRAR.exe | C:\Users\admin\Desktop\Darkcomet RAT 5.3.1\Darkcomet RAT 5.3.1\Celesty Binder\config.ini | ini | |
MD5:FACE4F2A1F63AB5DAF4456E3A46F62DC | SHA256:E529BCDCCA95735AEE7020A3B26312560584B78394CE971B3A729823DD148AAA | |||
| 2020 | WinRAR.exe | C:\Users\admin\Desktop\Darkcomet RAT 5.3.1\Darkcomet RAT 5.3.1\Celesty Binder\Lang\LV.ini | text | |
MD5:84E0FF162036F454D019B48BA6AF5F7A | SHA256:78F24B0B140943912A1130DA1ED3A20EB71126EE077793D19F990566FF633C3F | |||
| 2020 | WinRAR.exe | C:\Users\admin\Desktop\Darkcomet RAT 5.3.1\Darkcomet RAT 5.3.1\Celesty Binder\Lang\SR.ini | text | |
MD5:FDFC0EE3AD0F395E3078F600ED9BA689 | SHA256:37DCDA2CD0682A3EDFE354111E0DD637BE6581A71E6C240AE5729CE9F6A05EF9 | |||
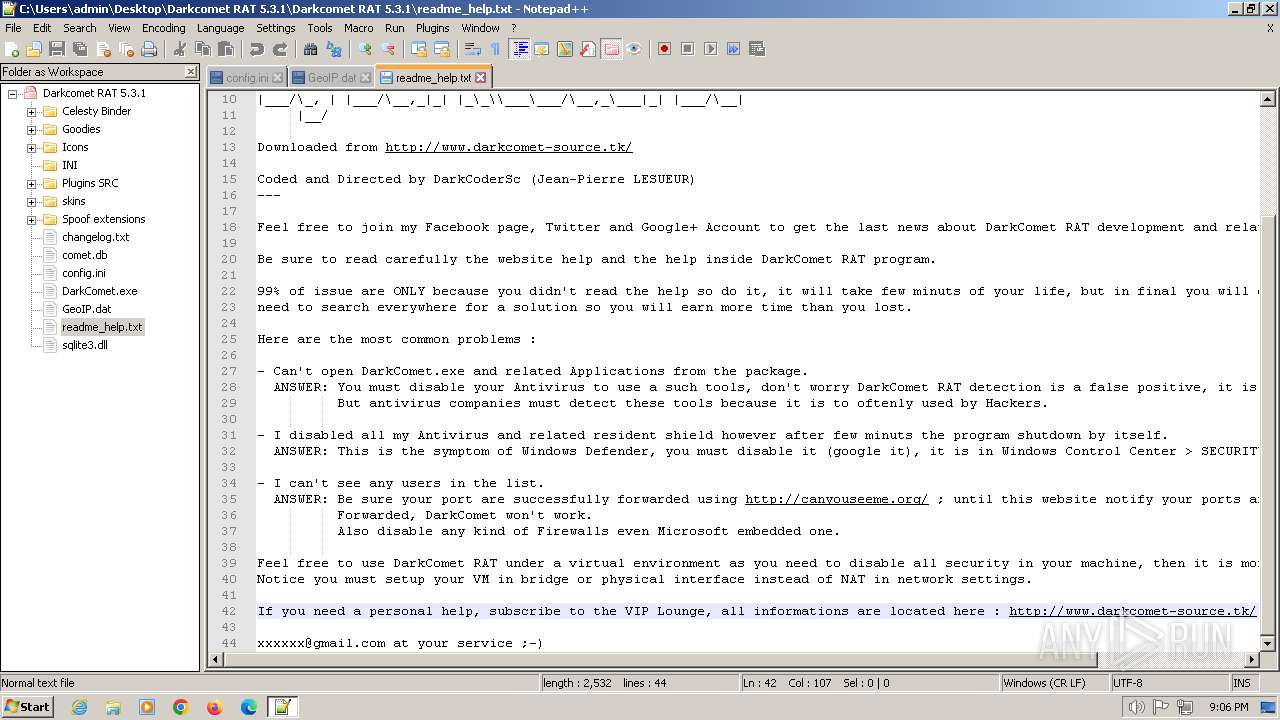
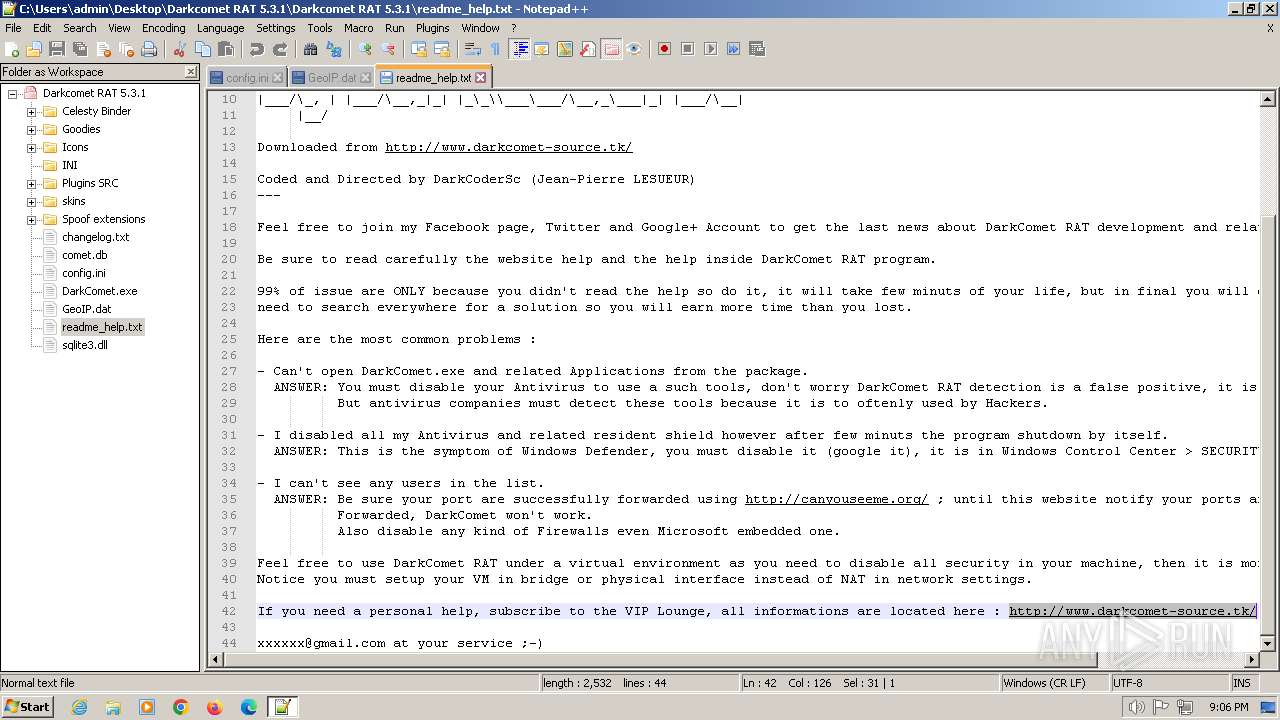
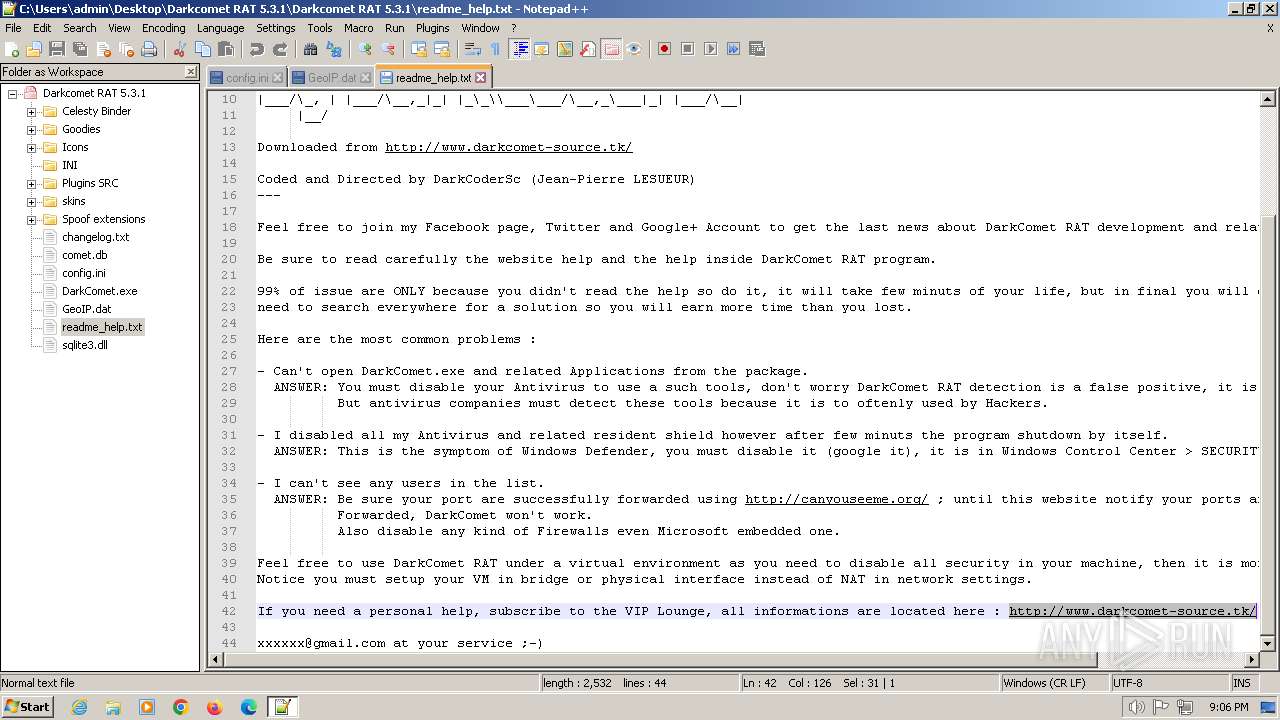
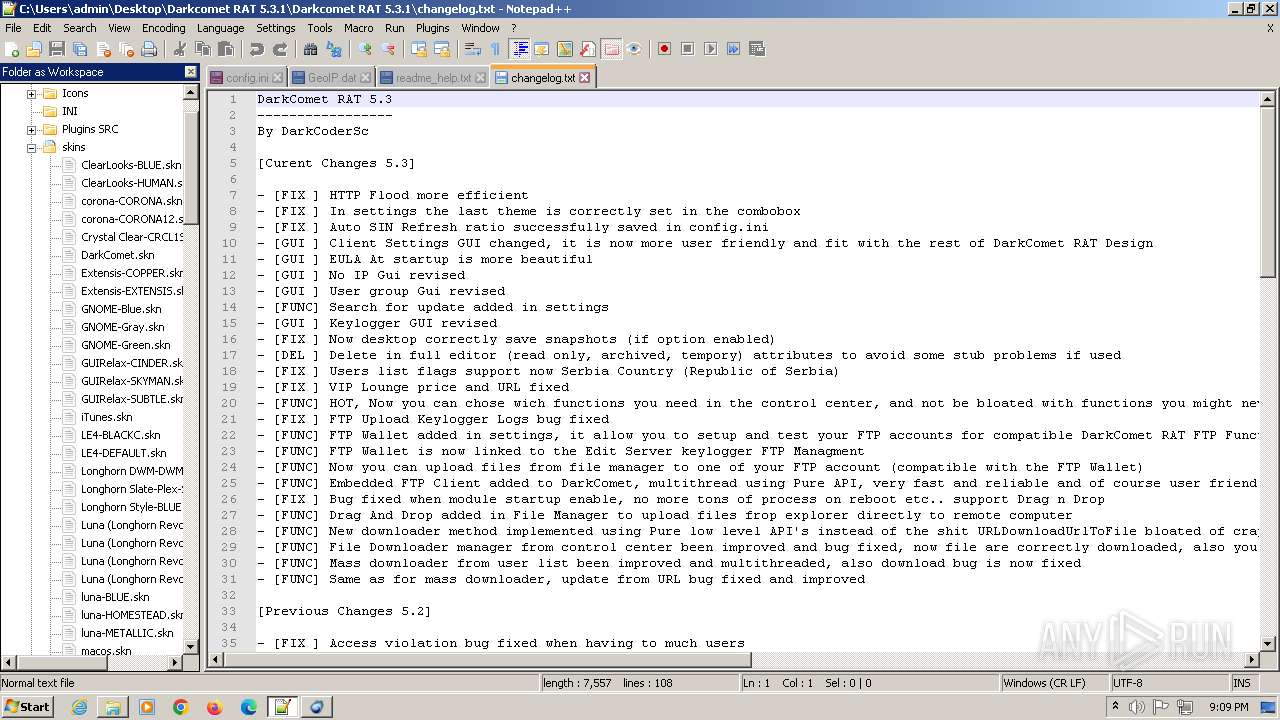
| 2020 | WinRAR.exe | C:\Users\admin\Desktop\Darkcomet RAT 5.3.1\Darkcomet RAT 5.3.1\Celesty Binder\readme.txt | text | |
MD5:EC0EB4AD970DC1D264BC6C6E7471428D | SHA256:BEC0F54669D35669D4E90E4AA588B96002B8A4E85048CE1CBF707F7F86AC250D | |||
| 2020 | WinRAR.exe | C:\Users\admin\Desktop\Darkcomet RAT 5.3.1\Darkcomet RAT 5.3.1\Celesty Binder\Lang\VN.ini | text | |
MD5:24874C298B575AE2AC496765AA5F3F6B | SHA256:B0B6AD746697E54CC76DCE834D963885D0284CCEEEB24DE62BE9EAF4BEE47EDD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
13
DNS requests
12
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
352 | svchost.exe | GET | 304 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
492 | lsass.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d08926ec3acba225 | unknown | compressed | 4.66 Kb | unknown |
2152 | iexplore.exe | GET | 304 | 152.199.19.161:443 | https://iecvlist.microsoft.com/ie11blocklist/1401746408/versionlistWin7.xml | unknown | — | — | unknown |
2152 | iexplore.exe | GET | 200 | 152.199.19.161:443 | https://r20swj13mr.microsoft.com/ieblocklist/v1/urlblockindex.bin | unknown | binary | 16 b | unknown |
2152 | iexplore.exe | GET | 200 | 152.199.19.161:443 | https://iecvlist.microsoft.com/IE11/1479242656000/iecompatviewlist.xml | unknown | xml | 340 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1220 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
352 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3032 | GUP.exe | 154.41.249.60:443 | notepad-plus-plus.org | COGENT-174 | US | unknown |
492 | lsass.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
352 | svchost.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
2152 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
2152 | iexplore.exe | 72.21.81.200:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notepad-plus-plus.org |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
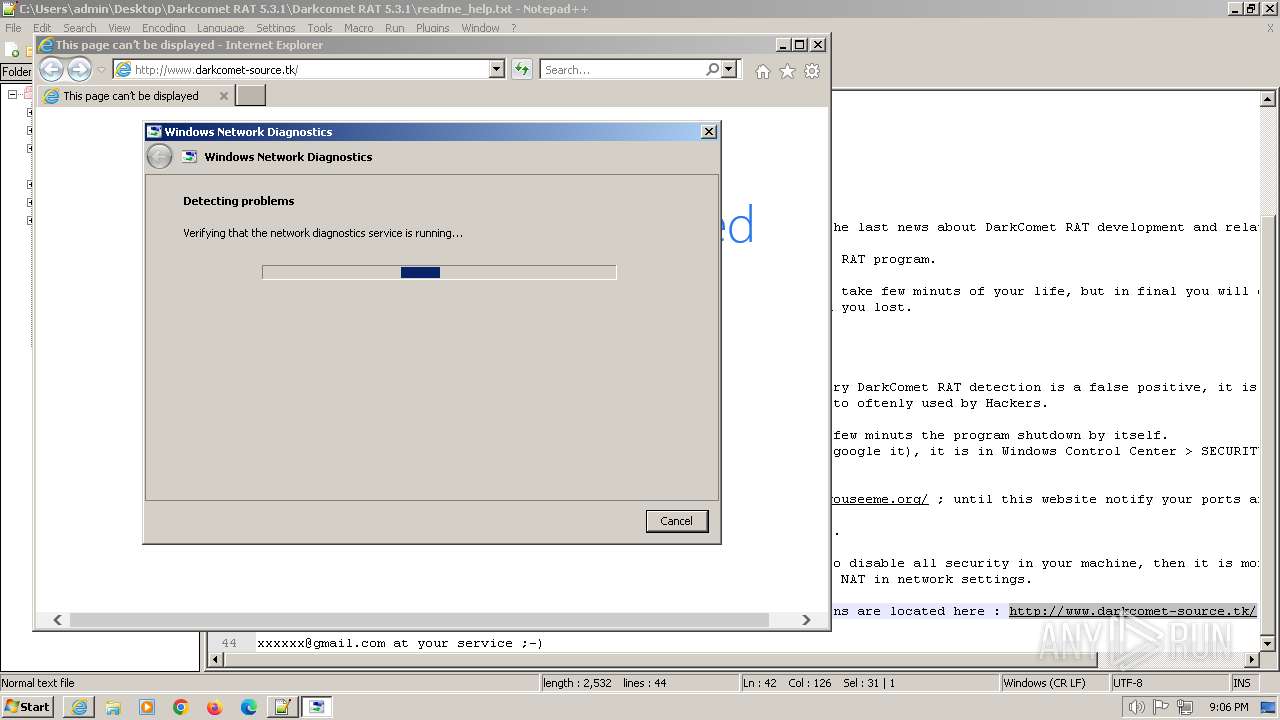
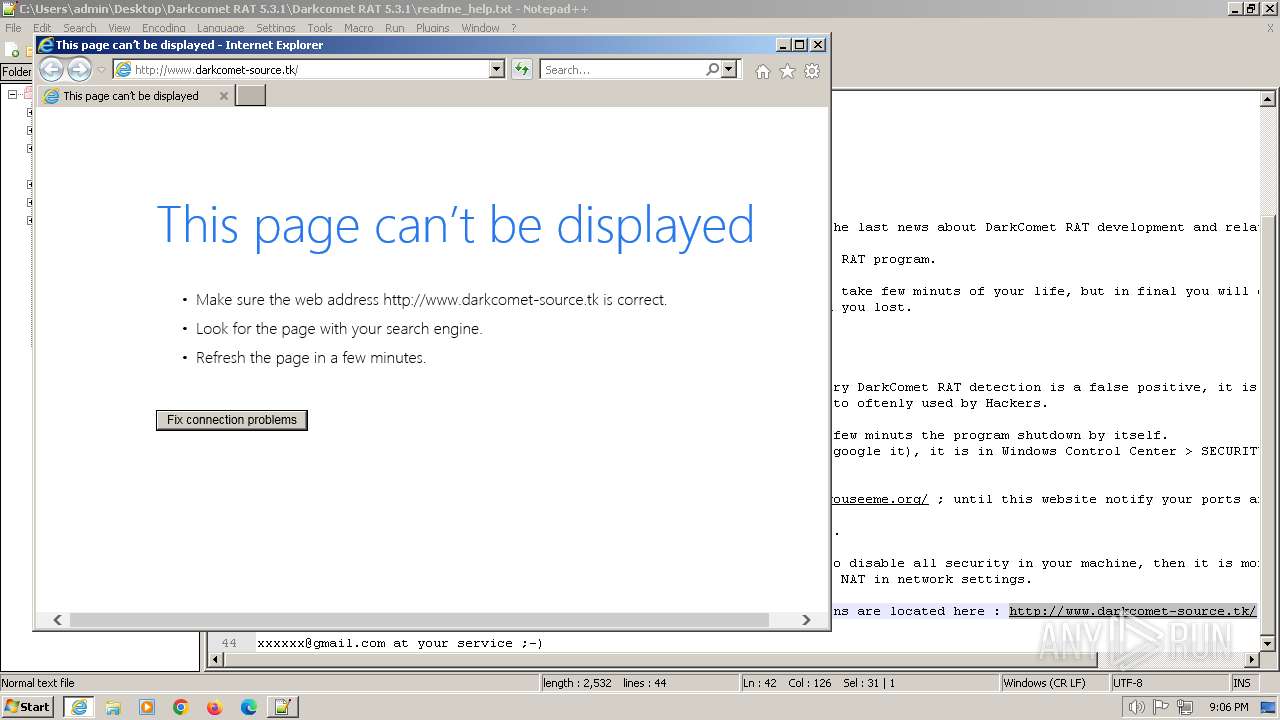
www.darkcomet-source.tk |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
352 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|