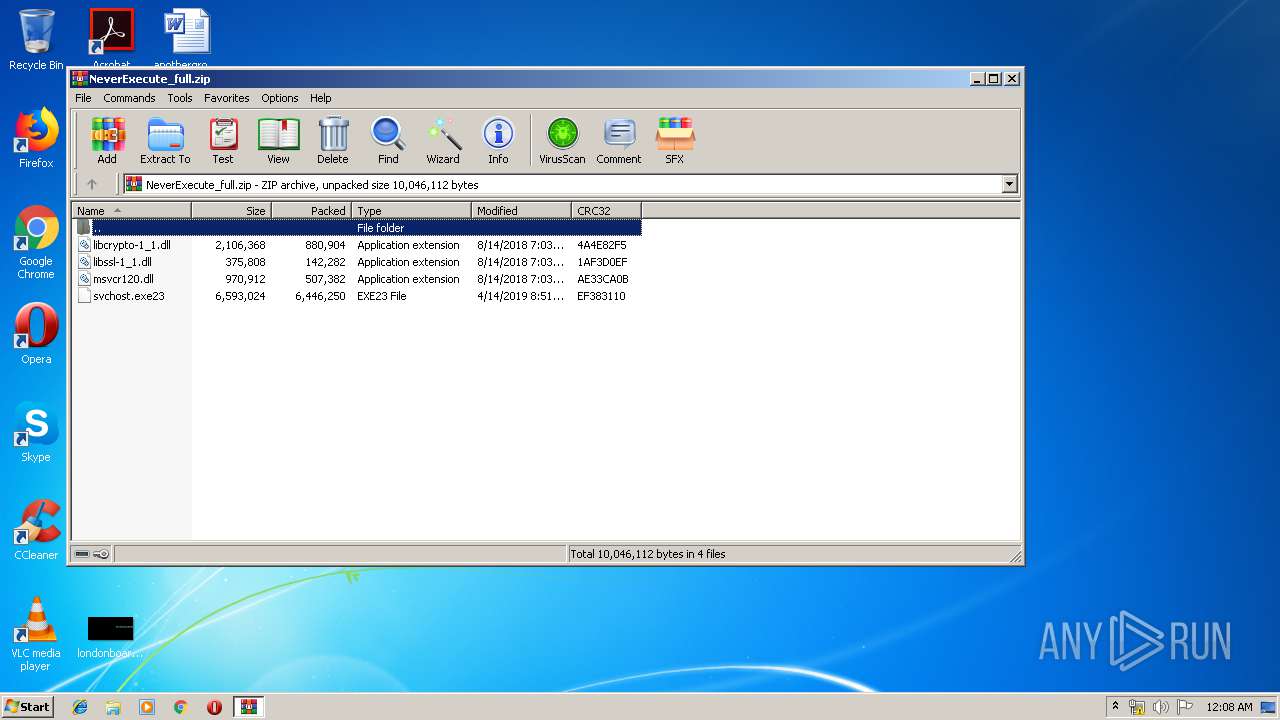
| File name: | NeverExecute_full.zip |
| Full analysis: | https://app.any.run/tasks/0d7af65b-06a6-4163-858c-8fc90eeb6979 |
| Verdict: | Malicious activity |
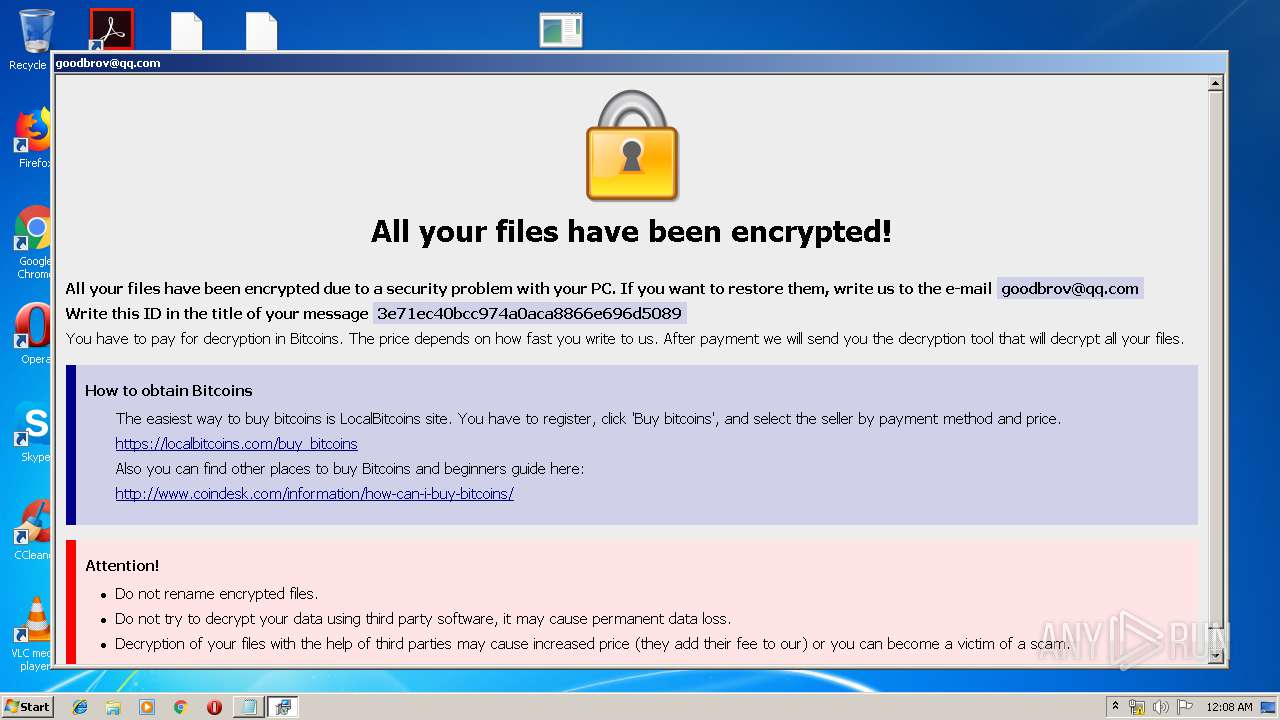
| Threats: | Dharma is advanced ransomware that has been observed in the wild since 2016. It is considered to be the second most profitable RaaS operation by the FBI. The malware targets hospitals and state organizations, encrypts files, and demands a payment to restore access to lost information. |
| Analysis date: | April 23, 2019, 23:07:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 8FDBE051302788C37848C4F0E92CE355 |
| SHA1: | 310A45411971C240205F6AC6D8B7DBB975A0259E |
| SHA256: | BFD978EA2866A725F0CF981A3809A4EACF40829D86B41D99BEE30DEDE2FE0D37 |
| SSDEEP: | 196608:dG0oq4jGNQzIrxgL3/KcaMqMR0AcoD9eUKZM9PffpoI7:dGfqYmxKaGhK+9fG0 |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2880)
- svchost.exe (PID: 1672)
Application was dropped or rewritten from another process
- svchost.exe (PID: 1672)
Actions looks like stealing of personal data
- svchost.exe (PID: 1672)
Renames files like Ransomware
- svchost.exe (PID: 1672)
Dropped file may contain instructions of ransomware
- svchost.exe (PID: 1672)
Modifies files in Chrome extension folder
- svchost.exe (PID: 1672)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3572)
Creates executable files which already exist in Windows
- WinRAR.exe (PID: 3572)
Reads the cookies of Google Chrome
- svchost.exe (PID: 1672)
Connects to server without host name
- svchost.exe (PID: 1672)
Reads the cookies of Mozilla Firefox
- svchost.exe (PID: 1672)
Creates files like Ransomware instruction
- svchost.exe (PID: 1672)
Starts MSHTA.EXE for opening HTA or HTMLS files
- svchost.exe (PID: 1672)
Creates files in the program directory
- svchost.exe (PID: 1672)
Creates files in the user directory
- svchost.exe (PID: 1672)
INFO
Reads internet explorer settings
- mshta.exe (PID: 1380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:08:14 01:03:23 |
| ZipCRC: | 0x4a4e82f5 |
| ZipCompressedSize: | 880904 |
| ZipUncompressedSize: | 2106368 |
| ZipFileName: | libcrypto-1_1.dll |
Total processes
37
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
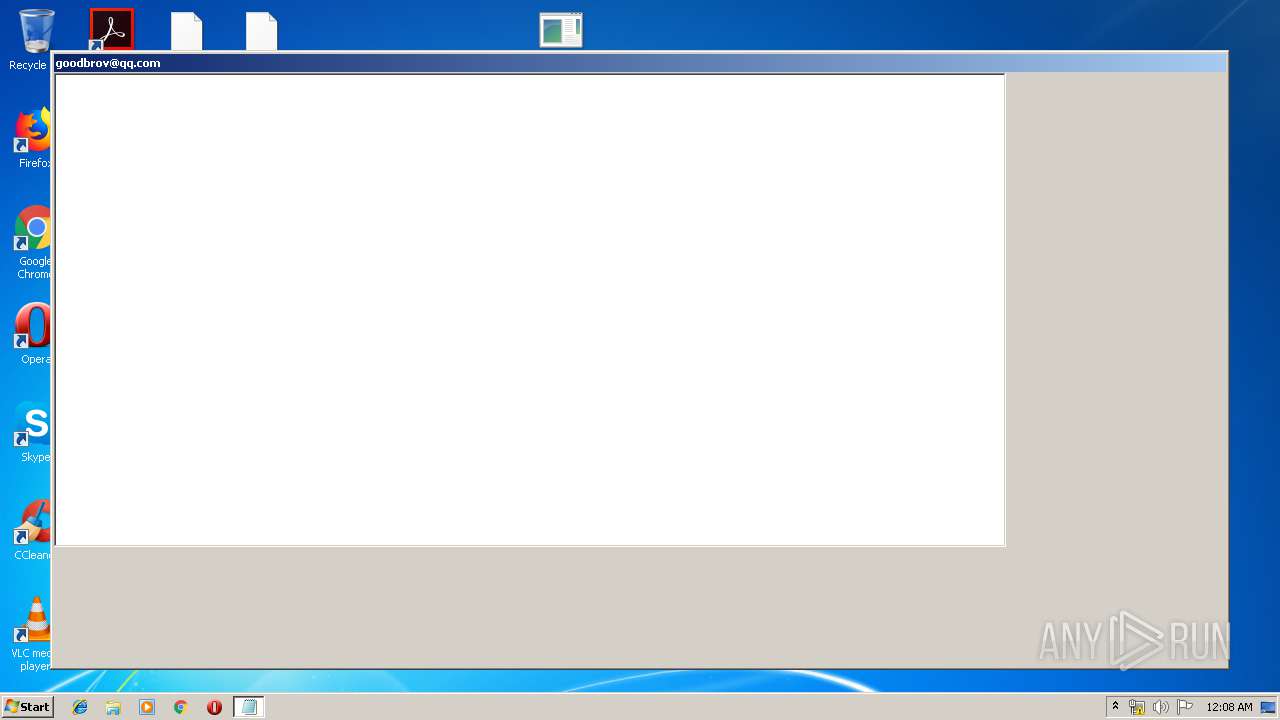
| 1336 | C:\Windows\system32\notepad.exe "C:\Users\admin\Host Process for Windows Services\HOW TO DECRYPT FILES.txt" | C:\Windows\system32\notepad.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1380 | C:\Windows\system32\mshta.exe "C:\Users\admin\Host Process for Windows Services\HOW TO DECRYPT FILES.hta" | C:\Windows\system32\mshta.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1672 | "C:\Users\admin\Desktop\svchost.exe" | C:\Users\admin\Desktop\svchost.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.15175.1 Modules
| |||||||||||||||
| 2880 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3572 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\NeverExecute_full.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
882
Read events
827
Write events
55
Delete events
0
Modification events
| (PID) Process: | (3572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3572) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\NeverExecute_full.zip | |||
| (PID) Process: | (3572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
4
Suspicious files
1 336
Text files
1 876
Unknown types
35
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1672 | svchost.exe | C:\Users\admin\AppData\Local\VirtualStore\ProgramData\Adobe\Setup\{AC76BA86-7AD7-FFFF-7B44-AC0F074E4100}\ABCPY.INI | — | |
MD5:— | SHA256:— | |||
| 1672 | svchost.exe | \Device\HarddiskVolume2\ProgramData\Adobe\Setup\{AC76BA86-7AD7-FFFF-7B44-AC0F074E4100}\ABCPY.INI.COLORIT | — | |
MD5:— | SHA256:— | |||
| 1672 | svchost.exe | C:\Users\admin\AppData\Local\VirtualStore\ProgramData\Adobe\Setup\{AC76BA86-7AD7-FFFF-7B44-AC0F074E4100}\Data1.cab | — | |
MD5:— | SHA256:— | |||
| 1672 | svchost.exe | \Device\HarddiskVolume2\ProgramData\Adobe\Setup\{AC76BA86-7AD7-FFFF-7B44-AC0F074E4100}\Data1.cab.COLORIT | — | |
MD5:— | SHA256:— | |||
| 1672 | svchost.exe | C:\Users\admin\AppData\Local\VirtualStore\ProgramData\Adobe\Setup\{AC76BA86-7AD7-FFFF-7B44-AC0F074E4100}\setup.ini | — | |
MD5:— | SHA256:— | |||
| 1672 | svchost.exe | \Device\HarddiskVolume2\ProgramData\Adobe\Setup\{AC76BA86-7AD7-FFFF-7B44-AC0F074E4100}\setup.ini.COLORIT | — | |
MD5:— | SHA256:— | |||
| 1672 | svchost.exe | C:\Users\admin\AppData\Local\VirtualStore\ProgramData\Microsoft Help\Hx.hxn | — | |
MD5:— | SHA256:— | |||
| 1672 | svchost.exe | \Device\HarddiskVolume2\Users\admin\AppData\Local\VirtualStore\ProgramData\Microsoft Help\Hx.hxn.COLORIT | — | |
MD5:— | SHA256:— | |||
| 1672 | svchost.exe | C:\Users\admin\AppData\Local\VirtualStore\ProgramData\Microsoft Help\Hx_1033_MKWD_K.HxW | — | |
MD5:— | SHA256:— | |||
| 1672 | svchost.exe | \Device\HarddiskVolume2\Users\admin\AppData\Local\VirtualStore\ProgramData\Microsoft Help\Hx_1033_MKWD_K.HxW.COLORIT | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
7
DNS requests
1
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1672 | svchost.exe | POST | 200 | 45.227.252.62:80 | http://45.227.252.62/register/3e71ec40bcc974a0aca8866e696d5089 | unknown | text | 492 b | malicious |
1672 | svchost.exe | POST | 200 | 45.227.252.62:80 | http://45.227.252.62/metrics/3e71ec40bcc974a0aca8866e696d5089 | unknown | text | 16 b | malicious |
1672 | svchost.exe | POST | 200 | 45.227.252.62:80 | http://45.227.252.62/metrics/3e71ec40bcc974a0aca8866e696d5089 | unknown | text | 16 b | malicious |
1672 | svchost.exe | POST | 200 | 45.227.252.62:80 | http://45.227.252.62/metrics/3e71ec40bcc974a0aca8866e696d5089 | unknown | text | 16 b | malicious |
1672 | svchost.exe | POST | 200 | 45.227.252.62:80 | http://45.227.252.62/sharedFolders/3e71ec40bcc974a0aca8866e696d5089 | unknown | text | 264 b | malicious |
1672 | svchost.exe | POST | 200 | 45.227.252.62:80 | http://45.227.252.62/metrics/3e71ec40bcc974a0aca8866e696d5089 | unknown | text | 16 b | malicious |
1672 | svchost.exe | POST | 200 | 45.227.252.62:80 | http://45.227.252.62/finish/3e71ec40bcc974a0aca8866e696d5089 | unknown | text | 16 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1672 | svchost.exe | 45.227.252.62:80 | — | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
2.100.168.192.in-addr.arpa |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1672 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan-Ransom.Rapid |