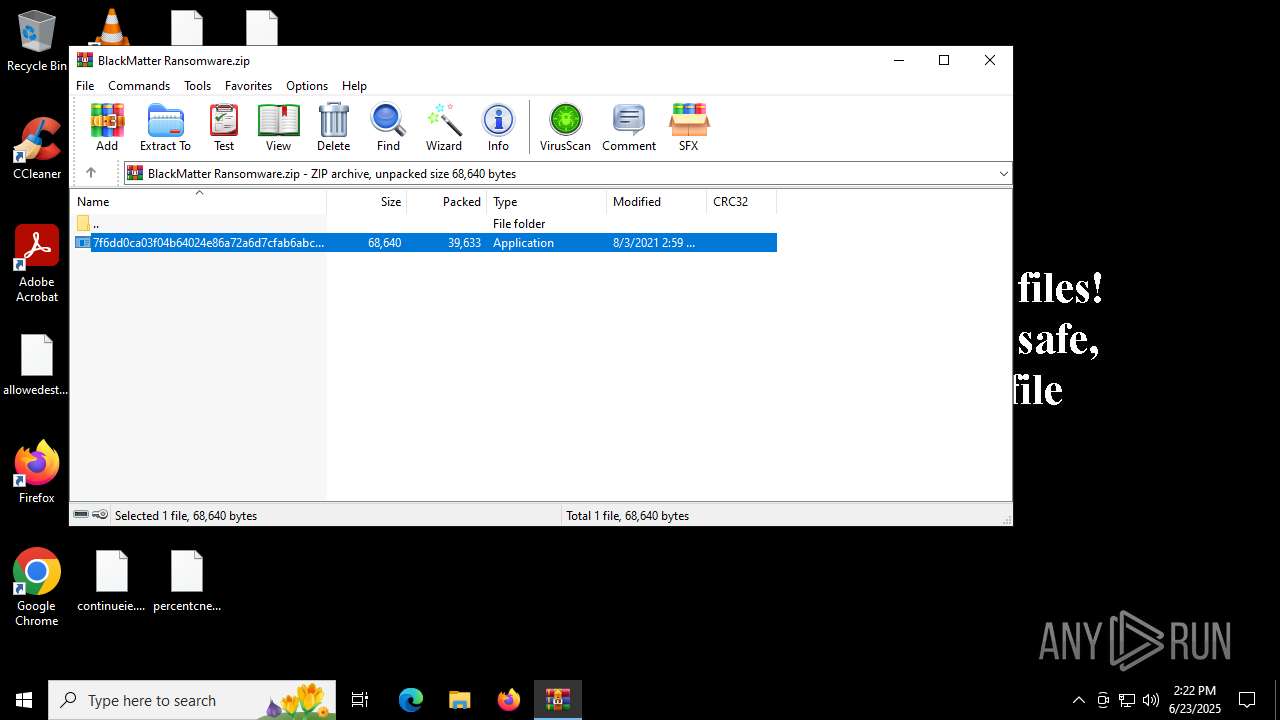
| File name: | BlackMatter Ransomware.zip |
| Full analysis: | https://app.any.run/tasks/c739e35a-55db-4d99-a048-1bff3a36ca46 |
| Verdict: | Malicious activity |
| Threats: | BlackMatter is a ransomware strain operating as a Ransomware-as-a-Service (RaaS), designed to encrypt files, remove recovery options, and extort victims across critical industries. Emerging in 2021, it quickly became a major concern due to its ability to evade defenses, spread across networks, and cause large-scale operational disruption, forcing security teams to act against a highly destructive and persistent threat. |
| Analysis date: | June 23, 2025, 14:22:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
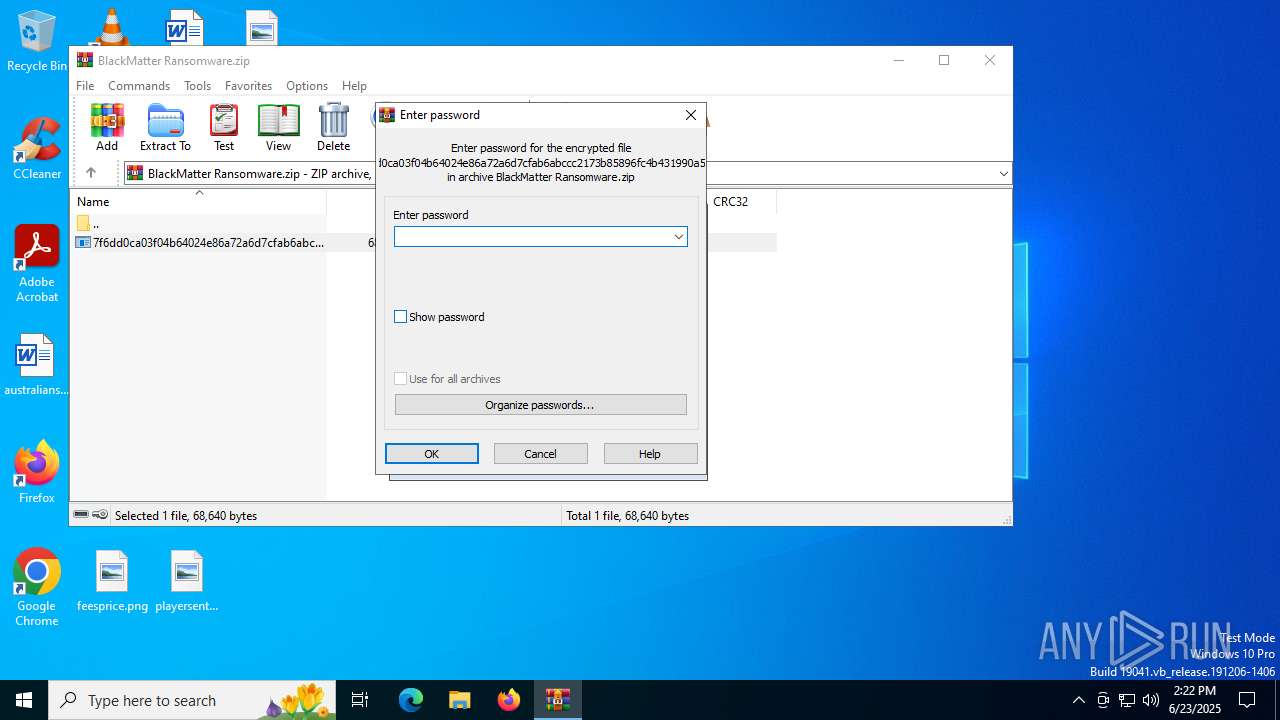
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 7EF63E936B982E986B1E3395A0889E1F |
| SHA1: | BD4CC018219790854C092F18DFD5812E3E0B7A98 |
| SHA256: | BF76962E3592F86EE7CB9F55ED4BFC36FC2AA9B062D3953A3AABCAF770CB91F0 |
| SSDEEP: | 768:Xhsu1fxnMzAtlwLeEaQZ0b9Hqcua0dRYX1BLvTs9nhv143sM1nA+NPSC2oQUfkm:Xh9ZCAtlwLeEVZLYlBL7MhN9+nzXfkm |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3756)
Known privilege escalation attack
- dllhost.exe (PID: 1192)
Connects to the CnC server
- svchost.exe (PID: 2200)
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
Renames files like ransomware
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
RANSOMWARE has been detected
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
BLACKMATTER has been detected (SURICATA)
- svchost.exe (PID: 2200)
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3756)
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
Contacting a server suspected of hosting an CnC
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
- svchost.exe (PID: 2200)
Changes the desktop background image
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
Executes as Windows Service
- VSSVC.exe (PID: 2348)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3756)
Reads the machine GUID from the registry
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 3572)
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
Checks supported languages
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 3572)
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
- identity_helper.exe (PID: 6956)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 1192)
Reads the computer name
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 3572)
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
- identity_helper.exe (PID: 6956)
Reads Environment values
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
- identity_helper.exe (PID: 6956)
Reads product name
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
Checks proxy server information
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
Reads the software policy settings
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
Creates files or folders in the user directory
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
Creates files in the program directory
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe (PID: 5764)
Manual execution by a user
- msedge.exe (PID: 2220)
Application launched itself
- msedge.exe (PID: 2220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2021:08:03 14:59:08 |
| ZipCRC: | 0xb7b11297 |
| ZipCompressedSize: | 39633 |
| ZipUncompressedSize: | 68640 |
| ZipFileName: | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe |
Total processes
163
Monitored processes
23
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1036 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2252,i,1924125902719071291,8270844489485672191,262144 --variations-seed-version --mojo-platform-channel-handle=3292 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1192 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\SysWOW64\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1496 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4280,i,1924125902719071291,8270844489485672191,262144 --variations-seed-version --mojo-platform-channel-handle=4292 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1700 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6124,i,1924125902719071291,8270844489485672191,262144 --variations-seed-version --mojo-platform-channel-handle=6132 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1812 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6296,i,1924125902719071291,8270844489485672191,262144 --variations-seed-version --mojo-platform-channel-handle=6128 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2220 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2348 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2428 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3676,i,1924125902719071291,8270844489485672191,262144 --variations-seed-version --mojo-platform-channel-handle=3692 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2620 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --instant-process --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3696,i,1924125902719071291,8270844489485672191,262144 --variations-seed-version --mojo-platform-channel-handle=3900 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
7 204
Read events
7 173
Write events
30
Delete events
1
Modification events
| (PID) Process: | (3756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\BlackMatter Ransomware.zip | |||
| (PID) Process: | (3756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (5764) 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
1
Suspicious files
432
Text files
197
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | der | |
MD5:233079FEBB8D495D72AFEB81178E9667 | SHA256:759E58DBDAD042C19DBCEFD25E0503A972EDF3860DB94AE5B896DF84E3964E69 | |||
| 5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | C:\Users\Administrator\Searches\winrt--{S-1-5-21-1693682860-607145093-2874071422-500}-.searchconnector-ms.AwlCQEBCC | xml | |
MD5:F26188A4891D18E9C99D55118E1A06AE | SHA256:4EABB8A700B57032952A8AE8353B400D14A688690F92F15F9B84520E016CF5C7 | |||
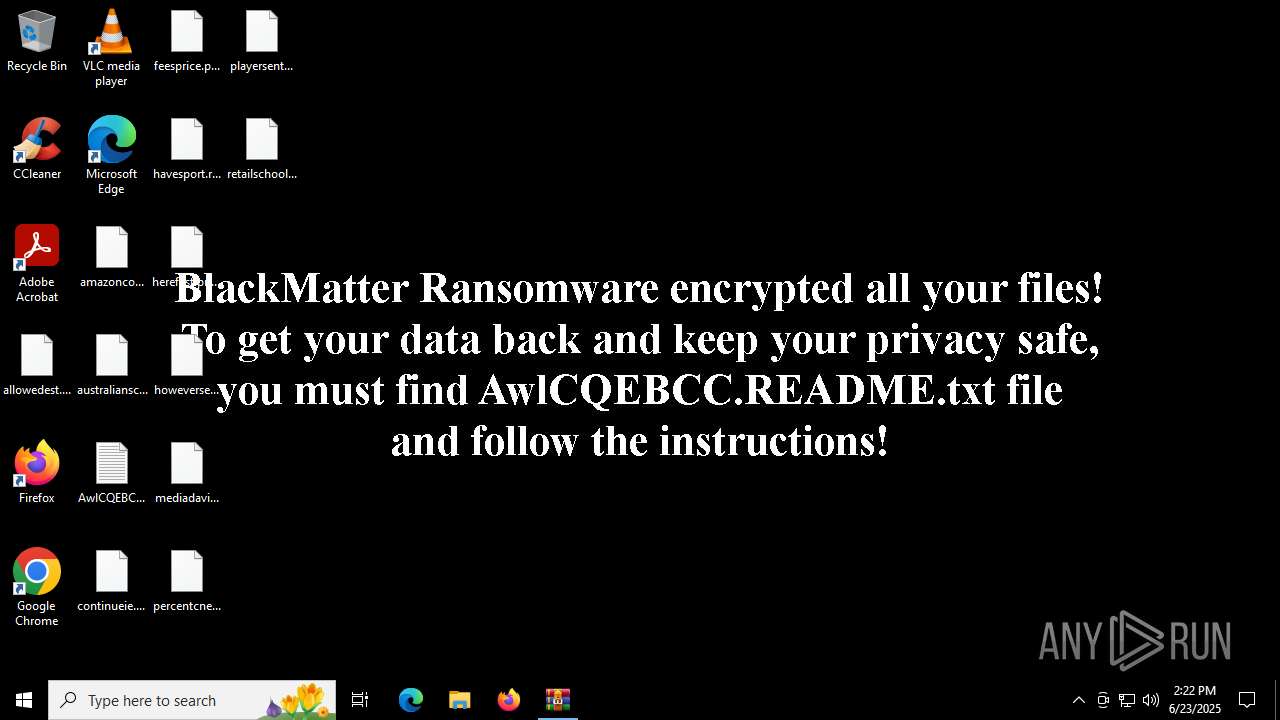
| 5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | C:\AwlCQEBCC.README.txt | text | |
MD5:F66968C47A64569E2281F65A95991BE0 | SHA256:4B950C763006E7C4569DF8742855CEC31BF82F835BD7E2BDCB5F128DB34C82BF | |||
| 5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\85E98AB9E20E0472C146F08ADBCF5FD9_436DD954C48579A90F36D53DDCA5EE35 | der | |
MD5:7183F215BE617D5353F77084F74223D9 | SHA256:CFD9697571D54D249F3B3A4377FC512A40EA581491923048C346053D2DBCAF15 | |||
| 3756 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3756.35181\7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | executable | |
MD5:D0512F2063CBD79FB0F770817CC81AB3 | SHA256:7F6DD0CA03F04B64024E86A72A6D7CFAB6ABCCC2173B85896FC4B431990A5984 | |||
| 5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | C:\Users\Administrator\Videos\AwlCQEBCC.README.txt | text | |
MD5:F66968C47A64569E2281F65A95991BE0 | SHA256:4B950C763006E7C4569DF8742855CEC31BF82F835BD7E2BDCB5F128DB34C82BF | |||
| 5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\85E98AB9E20E0472C146F08ADBCF5FD9_436DD954C48579A90F36D53DDCA5EE35 | binary | |
MD5:D560A80D4A8E1BFD596DA62A5BCA2200 | SHA256:BC7E6E215E5876FB44966178400F926068446D81A0B82D36F52719EC34737CF0 | |||
| 5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | C:\Users\AwlCQEBCC.README.txt | text | |
MD5:F66968C47A64569E2281F65A95991BE0 | SHA256:4B950C763006E7C4569DF8742855CEC31BF82F835BD7E2BDCB5F128DB34C82BF | |||
| 5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | C:\Users\Administrator\Favorites\AwlCQEBCC.README.txt | text | |
MD5:F66968C47A64569E2281F65A95991BE0 | SHA256:4B950C763006E7C4569DF8742855CEC31BF82F835BD7E2BDCB5F128DB34C82BF | |||
| 5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | C:\Users\Administrator\Searches\AwlCQEBCC.README.txt | text | |
MD5:F66968C47A64569E2281F65A95991BE0 | SHA256:4B950C763006E7C4569DF8742855CEC31BF82F835BD7E2BDCB5F128DB34C82BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
89
DNS requests
65
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2520 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCQDVVyUFdQxn%2Fw%3D%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | POST | 405 | 3.33.130.190:80 | http://mojobiden.com/?V5a=jgn8AuQAqytJ&MedAkHvCX=hOx&pHVJ7=7G4&qXsHT=813AoLidlD1Ov&m6NC=enpPKxmCvT9ZNGpbHoW&uIR8wN=pgV&03BQ=ZypyUhMvK9&zIEIeCkk=dVbmR6B&zjSDU=MUqqRS&DUBH=QsU&aYG=phM9fvZJuxFl&ls4VXiYyU=Rl7EHF7fP3xpTi9Vi&CsdvNCm=vm1wxJ&aDZP=79gcEfZg0DD0ne&2ptxE5U=2SwLtYxIg1BkSpM4&rp6VVuivW=zyz9i85MBj6Ef | unknown | — | — | malicious |
5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | POST | 405 | 3.33.130.190:80 | http://mojobiden.com/?y6DqB=ZdLLJORf&ivP6=R0YMxfP0aebaEJ20A&w5fqtzg=6kC20MRWl5d5xBA&qysrStMA=AMy | unknown | — | — | malicious |
1036 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:eWeg1GczTty8V88VVi5mlUiLNAb3kWF53_39W4pRKys&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
4844 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4844 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5348 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2520 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2520 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | 3.33.130.190:443 | mojobiden.com | AMAZON-02 | US | malicious |
5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | 192.124.249.23:80 | ocsp.godaddy.com | SUCURI-SEC | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
paymenthacks.com |
| malicious |
mojobiden.com |
| malicious |
ocsp.godaddy.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE BlackMatter CnC Domain in DNS Lookup (paymenthacks .com) |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE BlackMatter CnC Domain in DNS Lookup (mojobiden .com) |
5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | Malware Command and Control Activity Detected | ET MALWARE BlackMatter CnC Activity |
5764 | 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984.exe | Malware Command and Control Activity Detected | ET MALWARE BlackMatter CnC Activity |