| File name: | file.msi |
| Full analysis: | https://app.any.run/tasks/c4eb704a-4838-452c-bf14-6e35c40ed407 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | June 25, 2025, 18:55:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
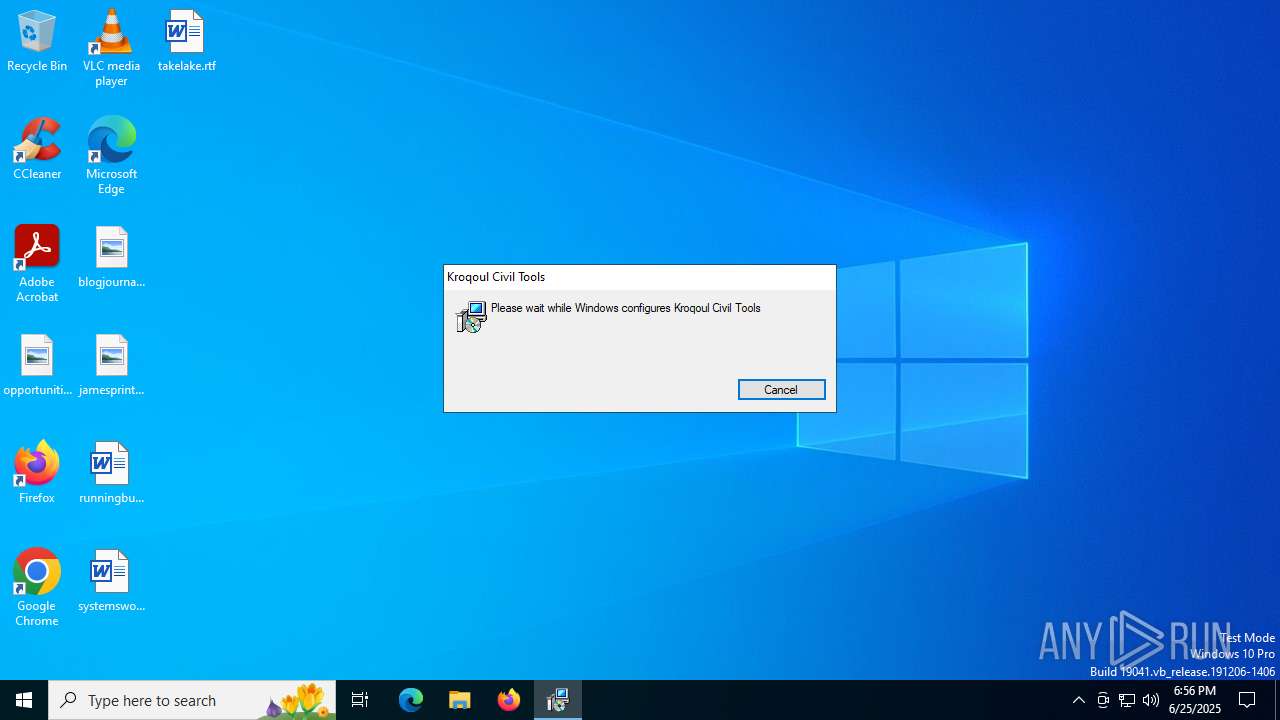
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Security: 0, Code page: 1252, Revision Number: {77F5DC10-3957-4841-AD8D-14F5F765476F}, Number of Words: 10, Subject: Kroqoul Civil Tools, Author: Werqos Livina, Name of Creating Application: Kroqoul Civil Tools, Template: x64;1033, Comments: This installer database contains the logic and data required to install Kroqoul Civil Tools., Title: Installation Database, Keywords: Installer, MSI, Database, Create Time/Date: Tue Jun 24 20:49:43 2025, Last Saved Time/Date: Tue Jun 24 20:49:43 2025, Last Printed: Tue Jun 24 20:49:43 2025, Number of Pages: 450 |
| MD5: | AD93D6D2230A3432388567E8F0E9359E |
| SHA1: | EB0408475D847F83FE202EB5AF341EAE1C2280D2 |
| SHA256: | BF365D2F847EC59345C5DB8292274BD07836DD4C6DB692BFB04231C4B7DE4A62 |
| SSDEEP: | 393216:kcEhndyL/8/aDzj9U82/PVoATjN2h0objZMdmYxIg2AZky5+lC1:cdij9RcVoATjN2h0objZB2IflGGC |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 4372)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6408)
Process drops python dynamic module
- msiexec.exe (PID: 4372)
Process drops legitimate windows executable
- msiexec.exe (PID: 4372)
The process drops C-runtime libraries
- msiexec.exe (PID: 4372)
Drops 7-zip archiver for unpacking
- msiexec.exe (PID: 4372)
Executing commands from a ".bat" file
- msiexec.exe (PID: 4372)
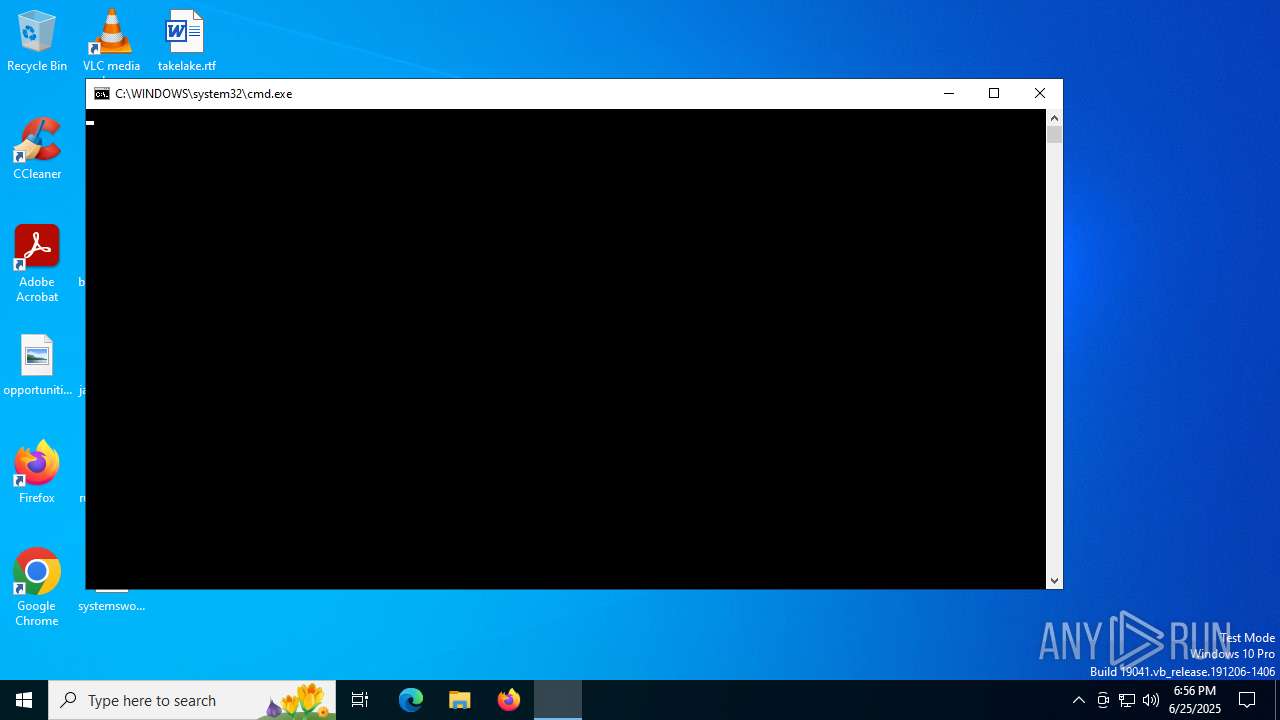
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 4372)
The executable file from the user directory is run by the CMD process
- 7z.exe (PID: 6388)
- openvpn.exe (PID: 3740)
INFO
An automatically generated document
- msiexec.exe (PID: 4512)
Reads the computer name
- msiexec.exe (PID: 4372)
- msiexec.exe (PID: 6408)
- 7z.exe (PID: 6388)
Checks supported languages
- msiexec.exe (PID: 6408)
- msiexec.exe (PID: 4372)
- 7z.exe (PID: 6388)
Reads Environment values
- msiexec.exe (PID: 6408)
The sample compiled with english language support
- msiexec.exe (PID: 4372)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4372)
Checks proxy server information
- msiexec.exe (PID: 6408)
- slui.exe (PID: 2148)
Creates files or folders in the user directory
- msiexec.exe (PID: 6408)
- msiexec.exe (PID: 4372)
Reads the software policy settings
- msiexec.exe (PID: 6408)
- slui.exe (PID: 2148)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6408)
Creates a software uninstall entry
- msiexec.exe (PID: 4372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (88.6) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (10) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {77F5DC10-3957-4841-AD8D-14F5F765476F} |
| Words: | 10 |
| Subject: | Kroqoul Civil Tools |
| Author: | Werqos Livina |
| LastModifiedBy: | - |
| Software: | Kroqoul Civil Tools |
| Template: | x64;1033 |
| Comments: | This installer database contains the logic and data required to install Kroqoul Civil Tools. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2025:06:24 20:49:43 |
| ModifyDate: | 2025:06:24 20:49:43 |
| LastPrinted: | 2025:06:24 20:49:43 |
| Pages: | 450 |
Total processes
138
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1036 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\xupdate.bat" "C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\" 0" | C:\Windows\System32\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225781 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2464 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3740 | "C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\\openvpn.exe" 0 | C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\openvpn.exe | — | cmd.exe | |||||||||||
User: admin Company: The OpenVPN Project Integrity Level: MEDIUM Description: OpenVPN Daemon Exit code: 3221225781 Version: 2.6.11.0 Modules
| |||||||||||||||
| 4372 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4512 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\file.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6388 | "C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\\7z.exe" x "C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\\xlicense.dat" -o"C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\" -y -p0 | C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\7z.exe | — | cmd.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 2 Version: 24.09 Modules
| |||||||||||||||
| 6408 | C:\Windows\syswow64\MsiExec.exe -Embedding 1661F4993CF7EC879B297A1D90A67F6A | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 590
Read events
3 261
Write events
320
Delete events
9
Modification events
| (PID) Process: | (6408) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6408) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4372) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 1411000093A04ECD02E6DB01 | |||
| (PID) Process: | (4372) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 53EB74C259F829D219A18B735714B906471498D7C05FEA92E3A0EA60ED681746 | |||
| (PID) Process: | (4372) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6408) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4372) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Users\admin\AppData\Roaming\Microsoft\Installer\ |
Value: | |||
| (PID) Process: | (4372) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\EE517F264941A23449C811419D3E65FF |
| Operation: | write | Name: | 2924AEDF1F179D8488FD5E7C106B347F |
Value: C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\ | |||
| (PID) Process: | (4372) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\825033A6A7F99AF4ABD0055DFD47DE0D |
| Operation: | write | Name: | 2924AEDF1F179D8488FD5E7C106B347F |
Value: 21:\Software\Werqos Livina\Kroqoul Civil Tools\Version | |||
| (PID) Process: | (4372) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\083E538AEB4D6AA4CAE0D26CFEF6E4C3 |
| Operation: | write | Name: | 2924AEDF1F179D8488FD5E7C106B347F |
Value: C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\_socket.pyd | |||
Executable files
119
Suspicious files
167
Text files
99
Unknown types
100
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4372 | msiexec.exe | C:\Windows\Installer\178647.msi | — | |
MD5:— | SHA256:— | |||
| 4372 | msiexec.exe | C:\Windows\Installer\MSI8E7A.tmp | binary | |
MD5:771AD4CB3224BB1854323E5846894ADD | SHA256:BEBCE53A0180D043F6898AA54A5056CCA609C3BB3A7308EBE41721A73C45AFF9 | |||
| 6408 | msiexec.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\diagnostics[1].htm | binary | |
MD5:CFCD208495D565EF66E7DFF9F98764DA | SHA256:5FECEB66FFC86F38D952786C6D696C79C2DBC239DD4E91B46729D73A27FB57E9 | |||
| 4372 | msiexec.exe | C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\_socket.pyd | executable | |
MD5:07789A8C23BCEBE32F8BFD4CE4AF5FFB | SHA256:235CC97584C3D31E5F3146121F64699D30CF372A86868EA755A9A0AFA6C56144 | |||
| 4372 | msiexec.exe | C:\Windows\Installer\MSI880D.tmp | executable | |
MD5:B717117EB31436F2FBD8182C3AAB267A | SHA256:4516899C2D5369CAC039258668E5AEF2651B33502849C1FA0778D3D63654CE9E | |||
| 4372 | msiexec.exe | C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\_ssl.pyd | executable | |
MD5:12FB0BCC8B79ECADD52BA8D97E08BFED | SHA256:360B506DF81FFC0B49AC15924314FA549084227B998B202572EED90B695DFD3A | |||
| 4372 | msiexec.exe | C:\Windows\Installer\MSI8760.tmp | executable | |
MD5:B717117EB31436F2FBD8182C3AAB267A | SHA256:4516899C2D5369CAC039258668E5AEF2651B33502849C1FA0778D3D63654CE9E | |||
| 4372 | msiexec.exe | C:\Windows\Installer\MSI8939.tmp | executable | |
MD5:805680BE3B2F96DDD652257156481EBB | SHA256:B5D0C2958F7C59410EB7E255E978563403A71B17D2105498005E1CED7F643489 | |||
| 4372 | msiexec.exe | C:\Windows\Installer\MSI889B.tmp | executable | |
MD5:B717117EB31436F2FBD8182C3AAB267A | SHA256:4516899C2D5369CAC039258668E5AEF2651B33502849C1FA0778D3D63654CE9E | |||
| 6408 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\3554D6D68D8291652D7FDC994BCEF253 | binary | |
MD5:98BF40AD9F2DD8D2B97A33999FFA79EA | SHA256:FE25FE11B533148F15488526F08143FEDC7B65C94824AB2637770DD1C956A964 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
26
DNS requests
22
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.151:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1636 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1204 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1204 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
6408 | msiexec.exe | GET | 200 | 104.18.20.213:80 | http://r10.c.lencr.org/52.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.48.23.151:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1636 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1636 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6408 | msiexec.exe | 169.150.247.38:443 | salsawynwood.com | — | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
salsawynwood.com |
| unknown |
r10.c.lencr.org |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Possibly Unwanted Program Detected | ADWARE [ANY.RUN] AdvancedInstaller User-Agent |
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |