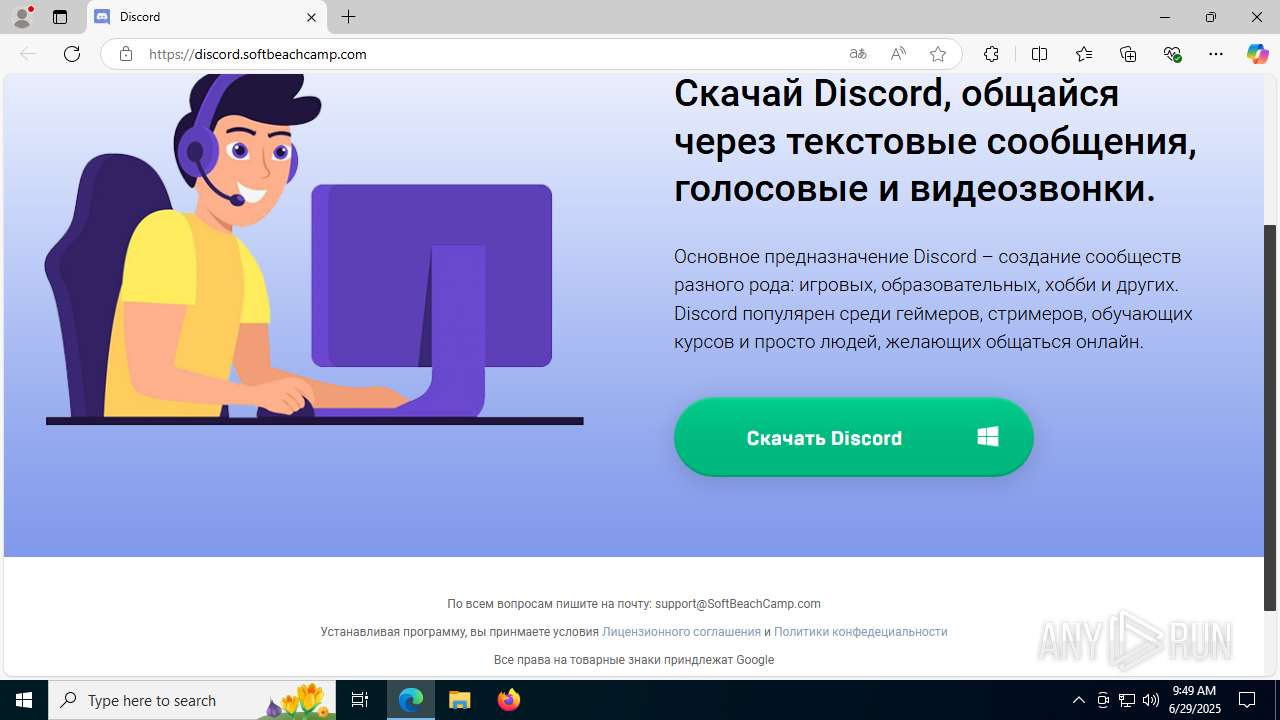
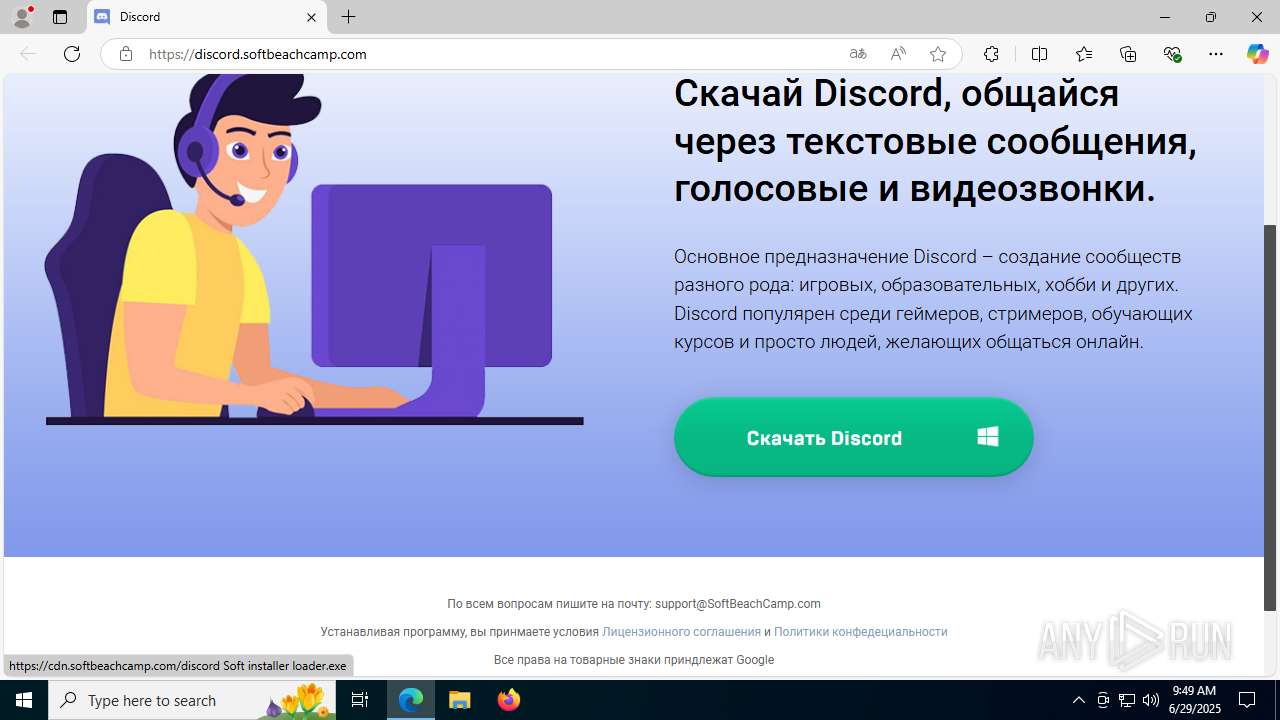
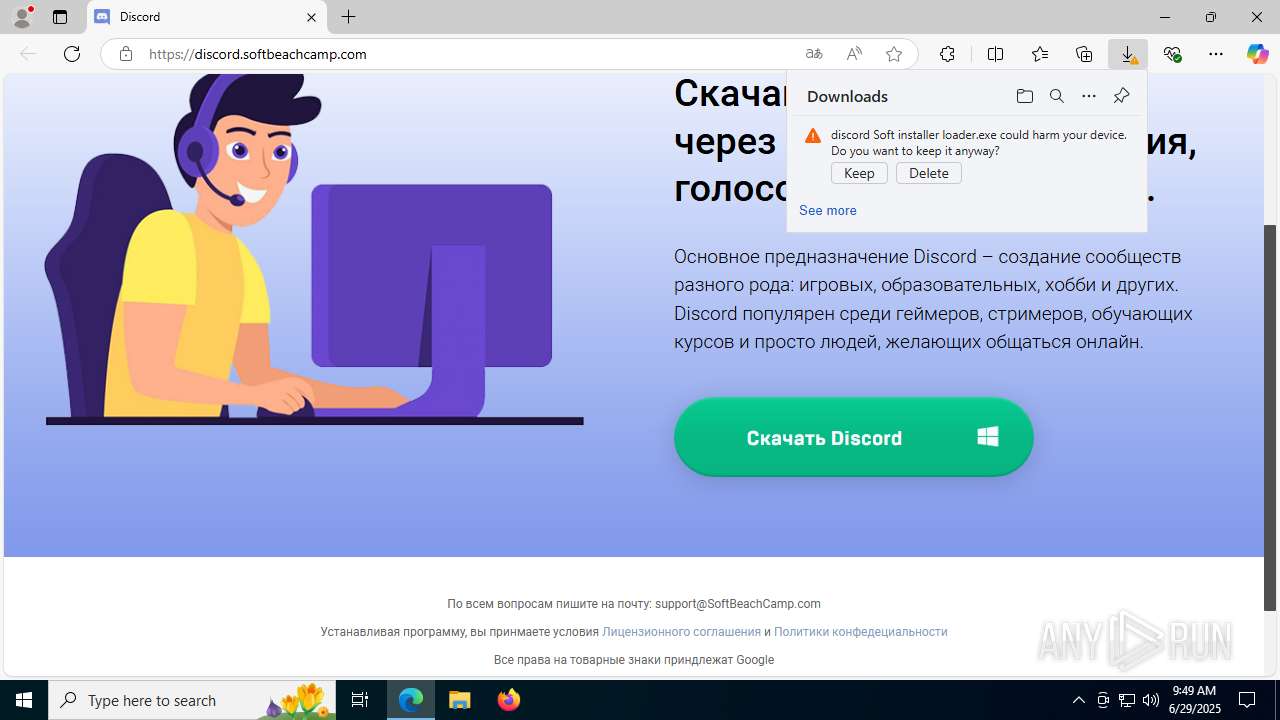
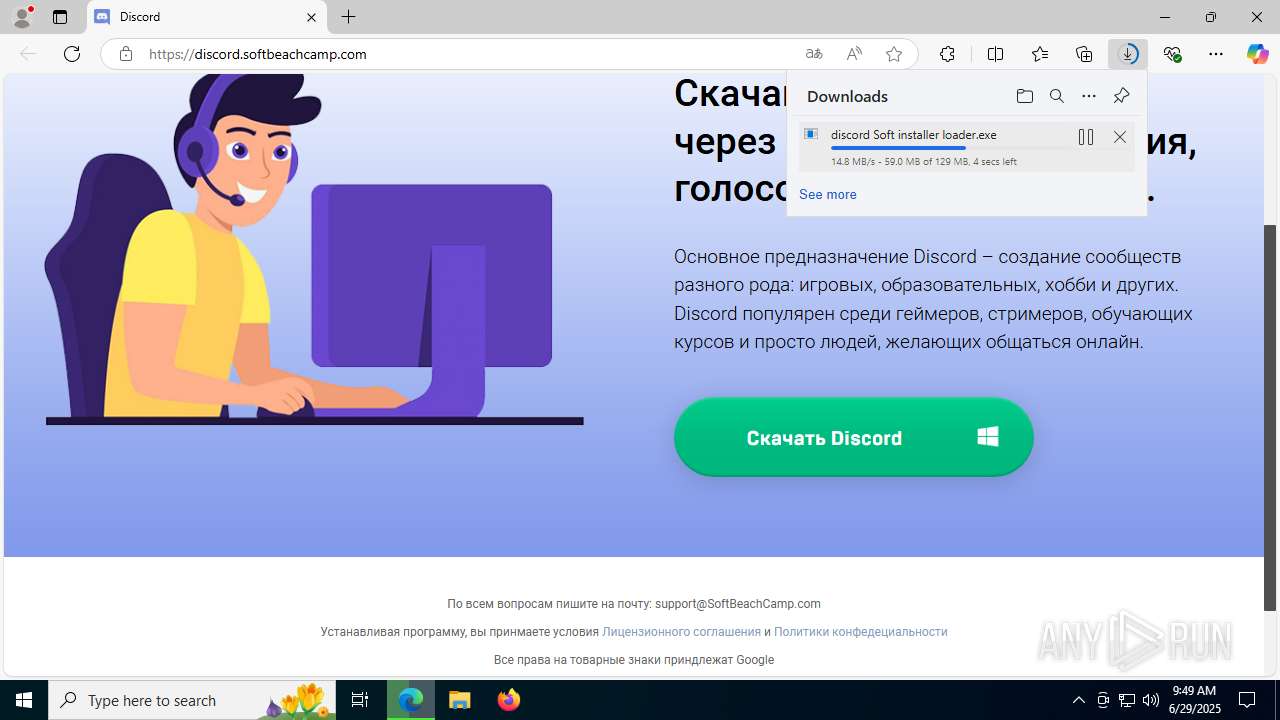
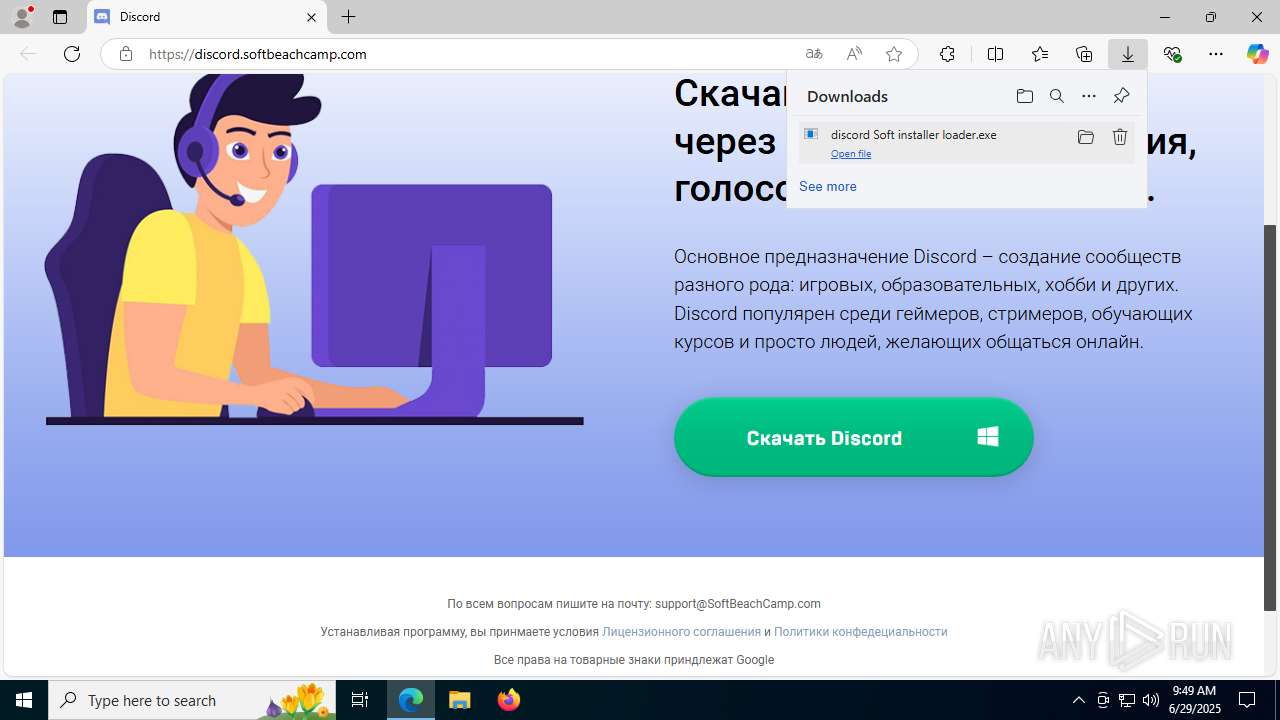
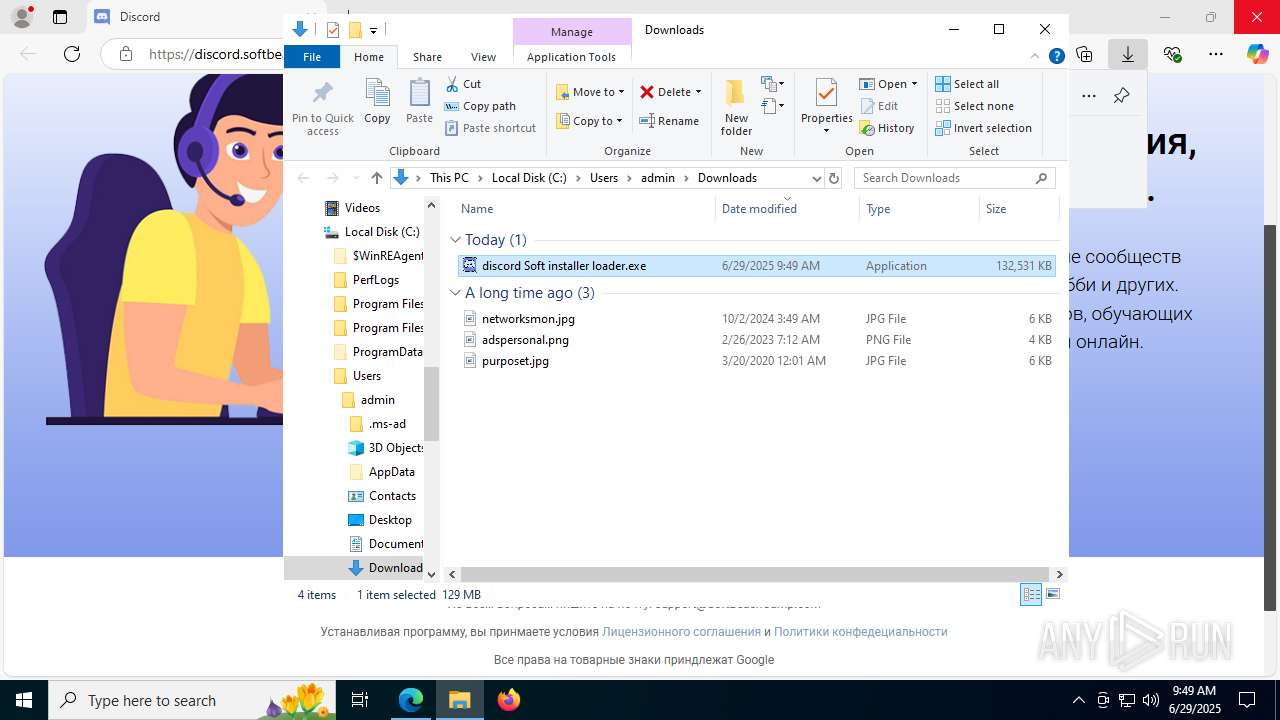
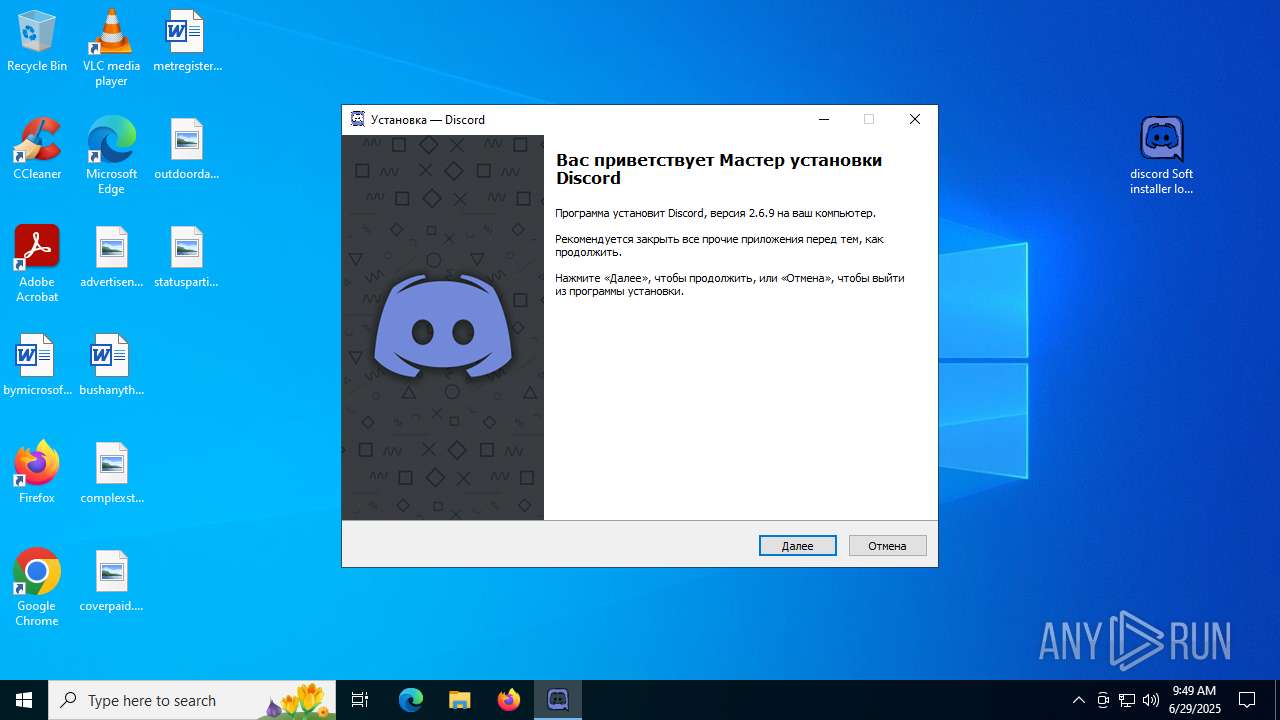
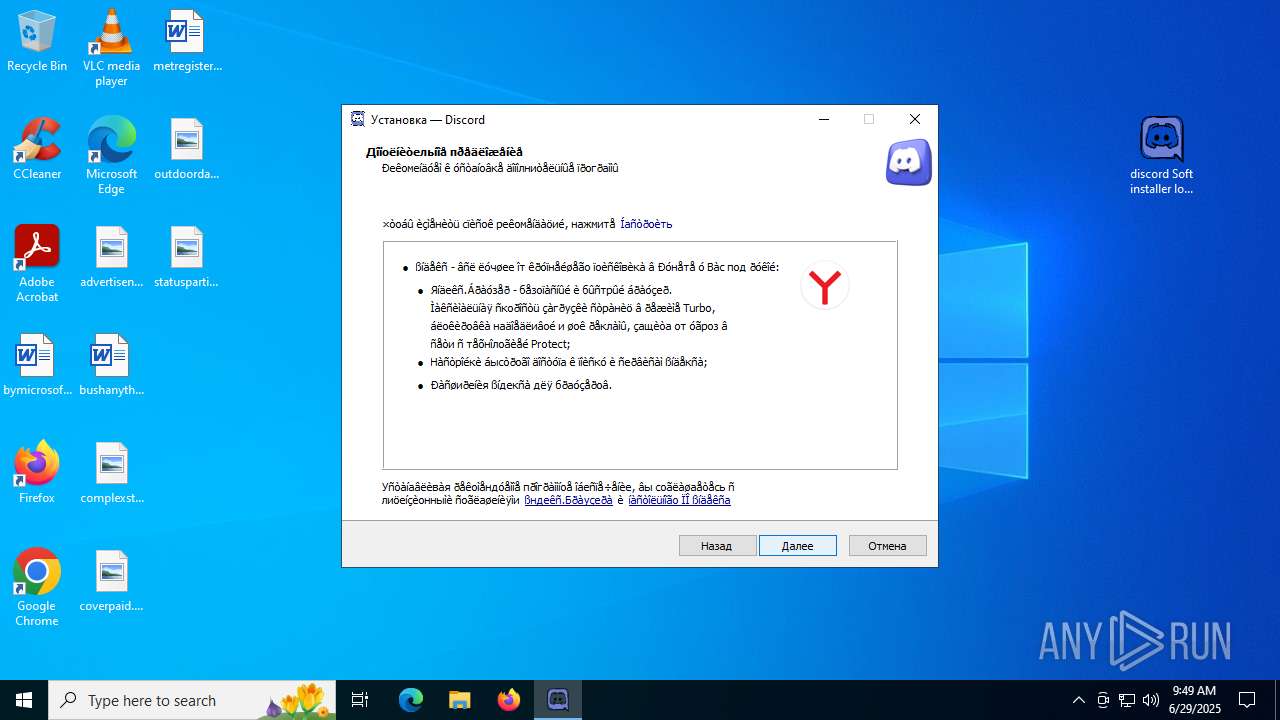
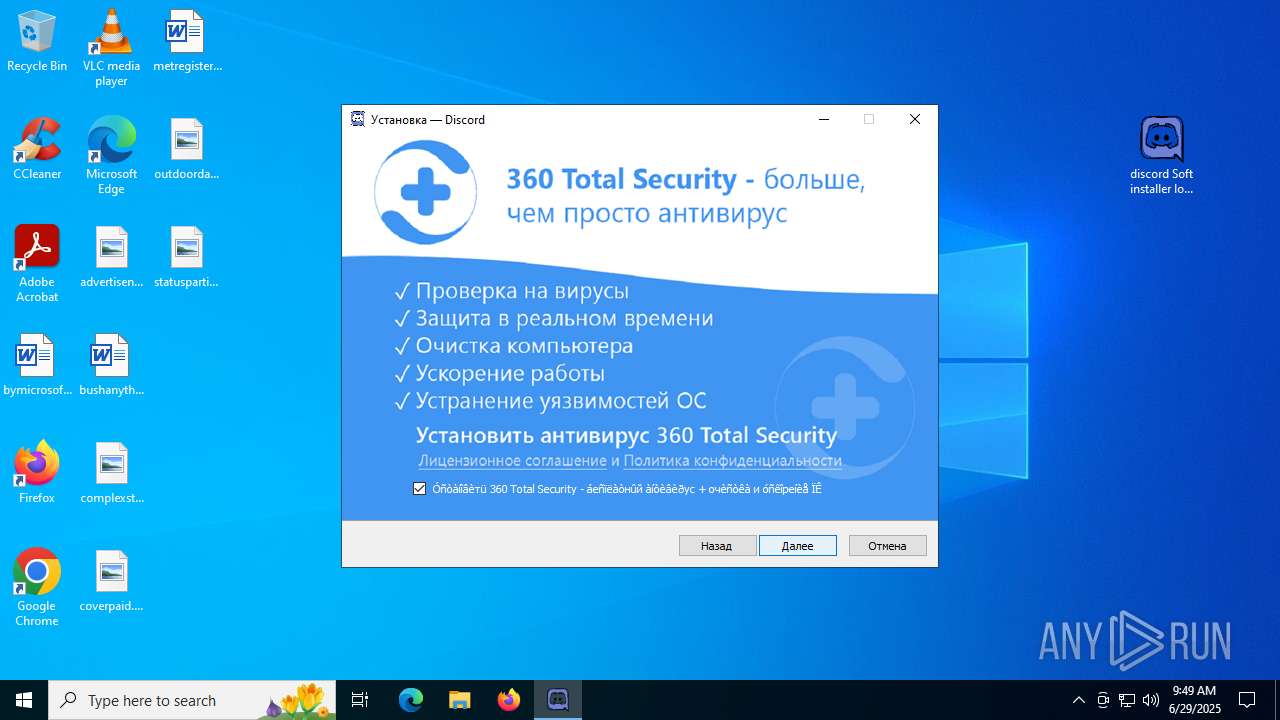
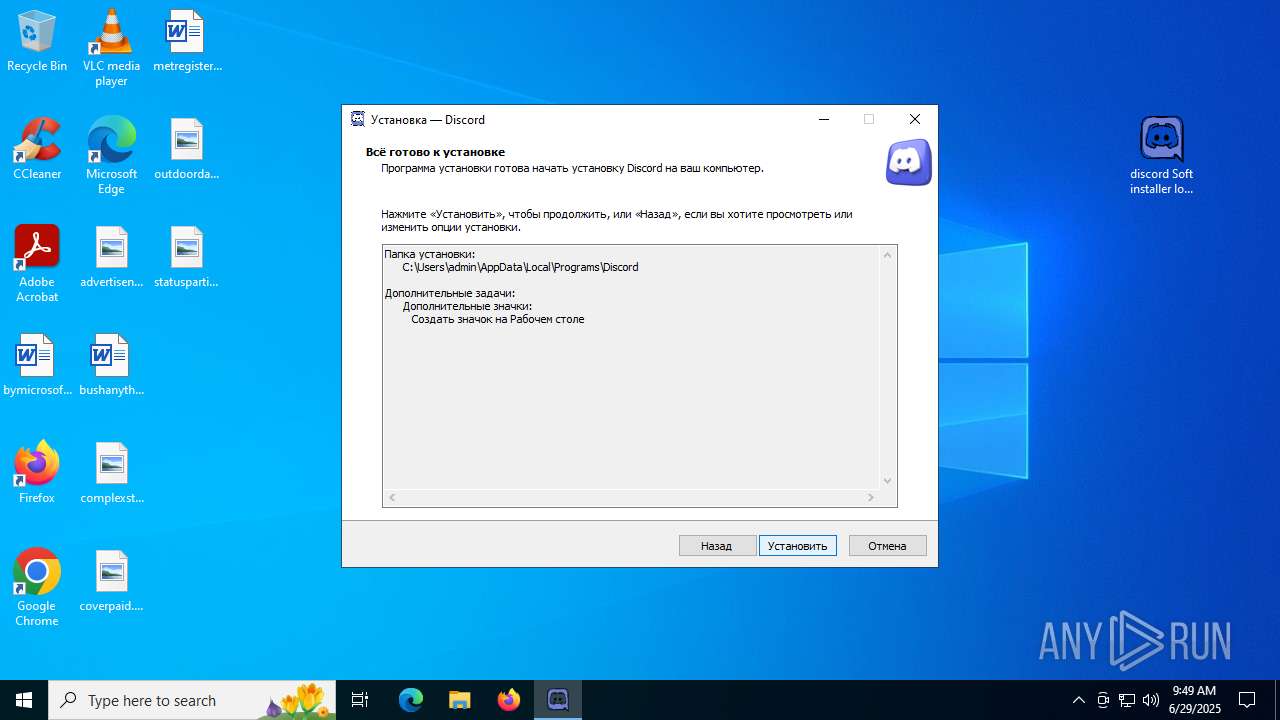
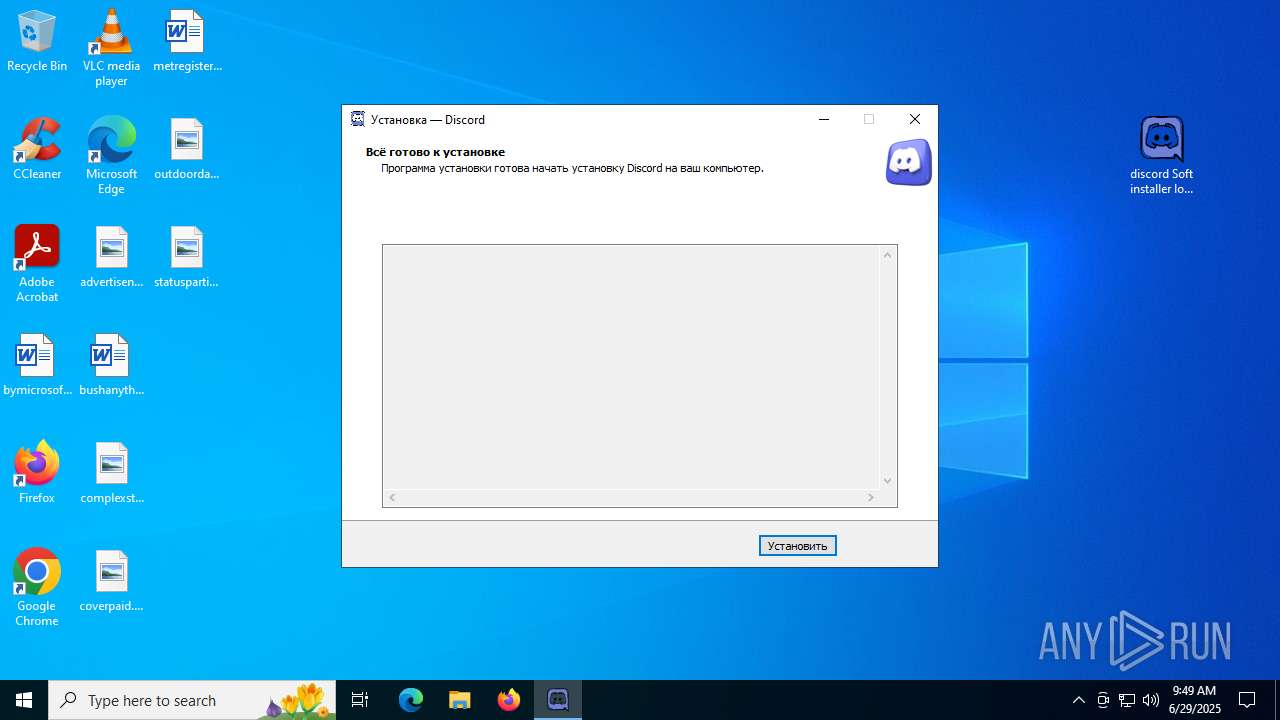
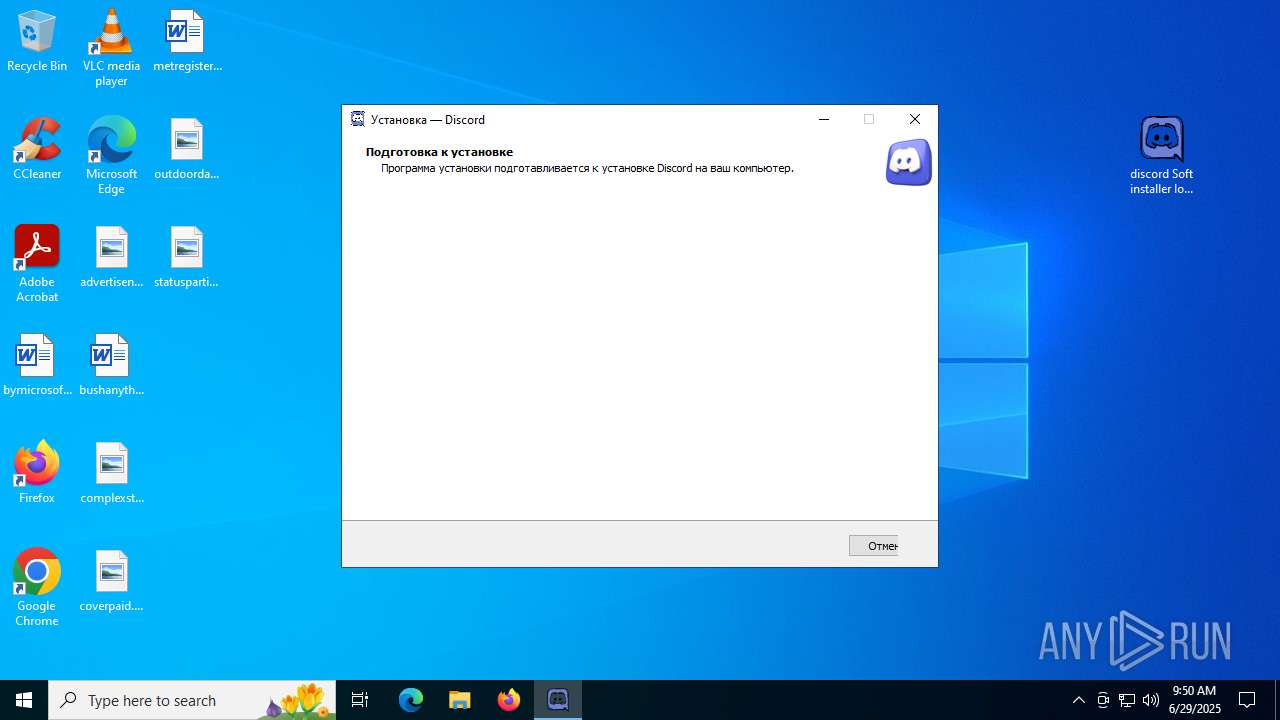
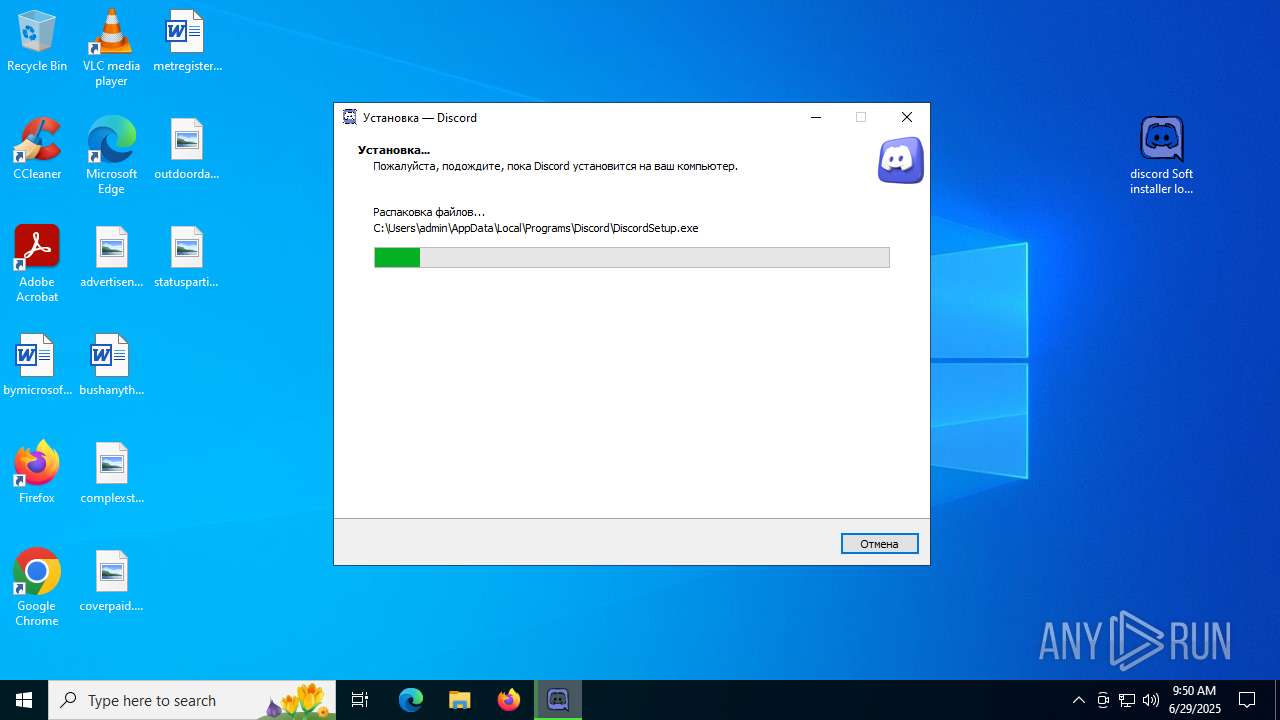
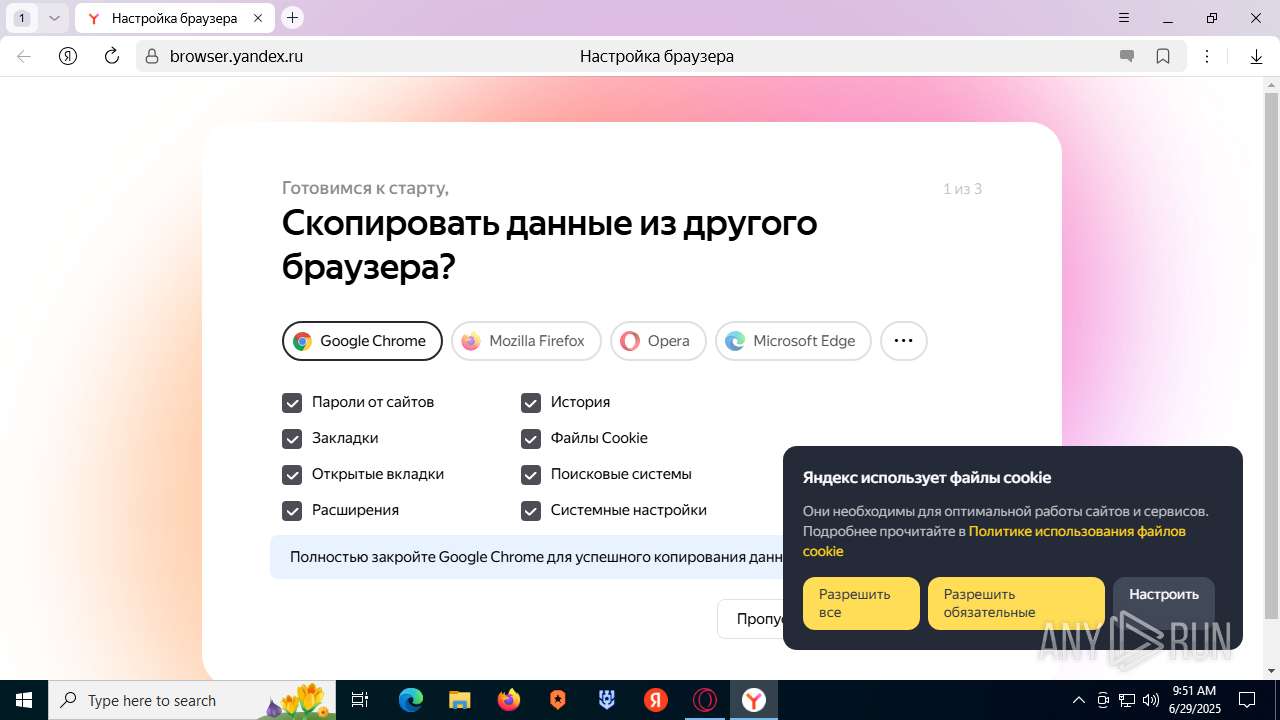
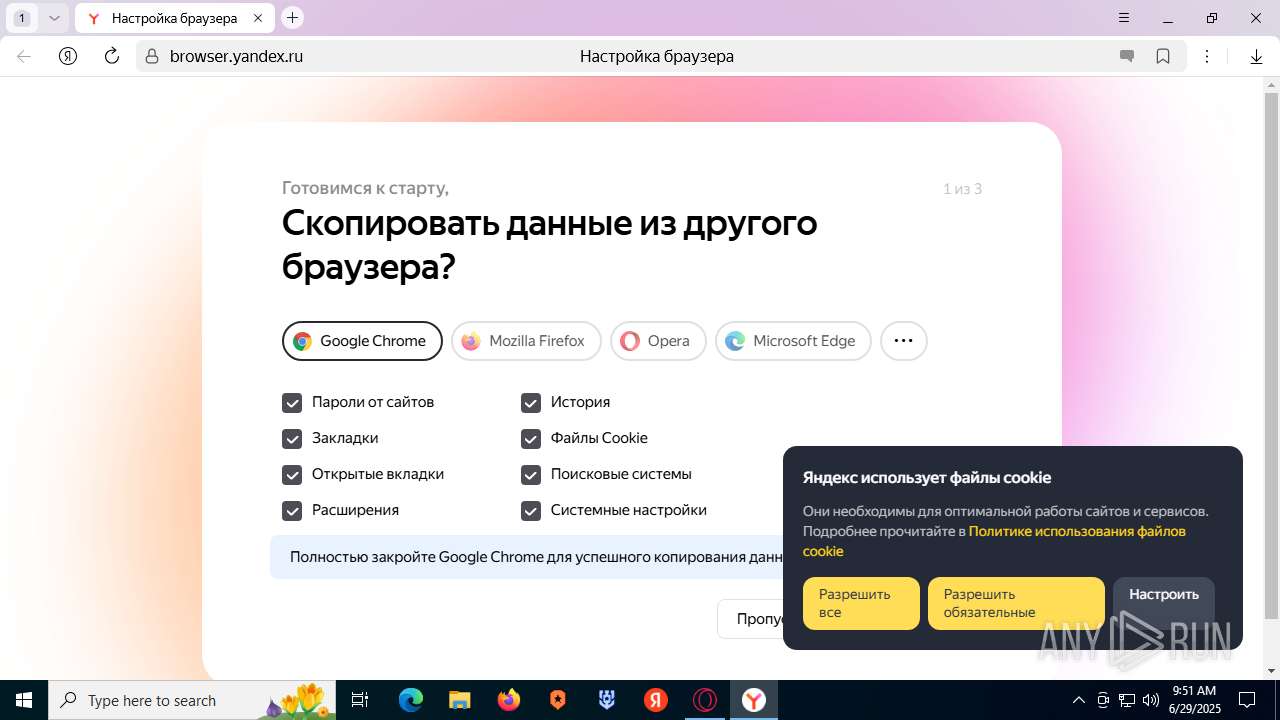
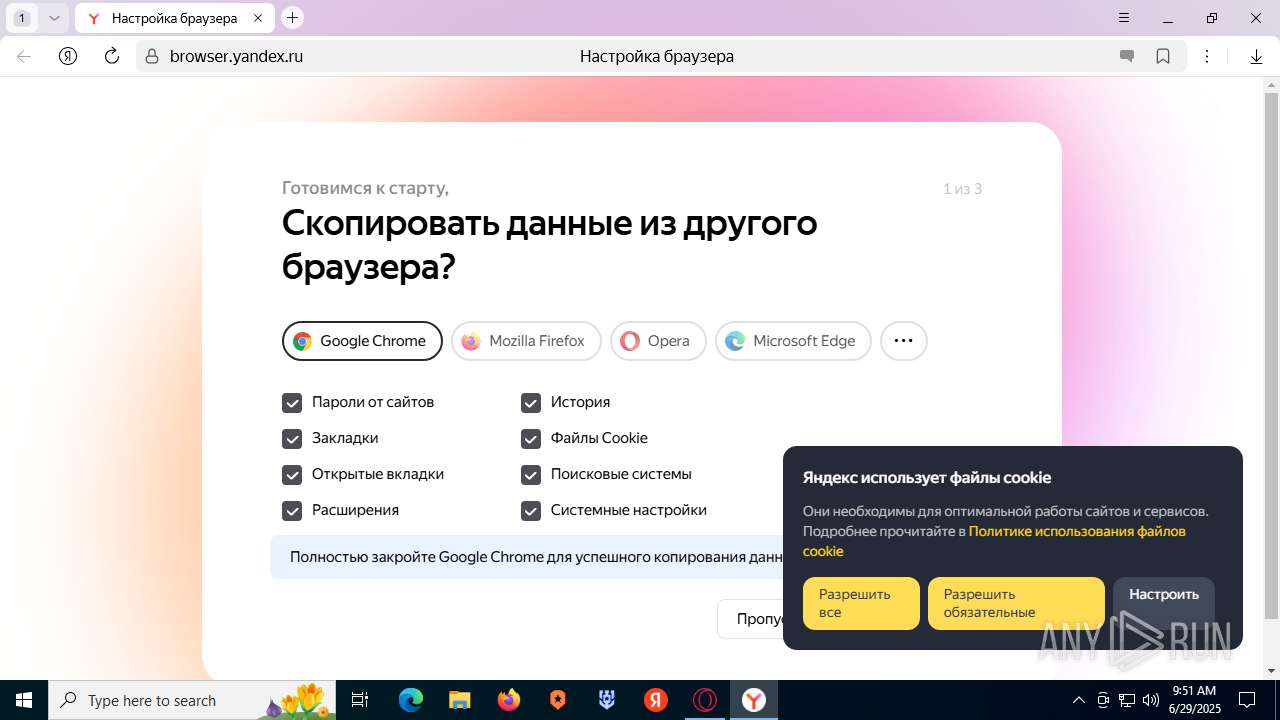
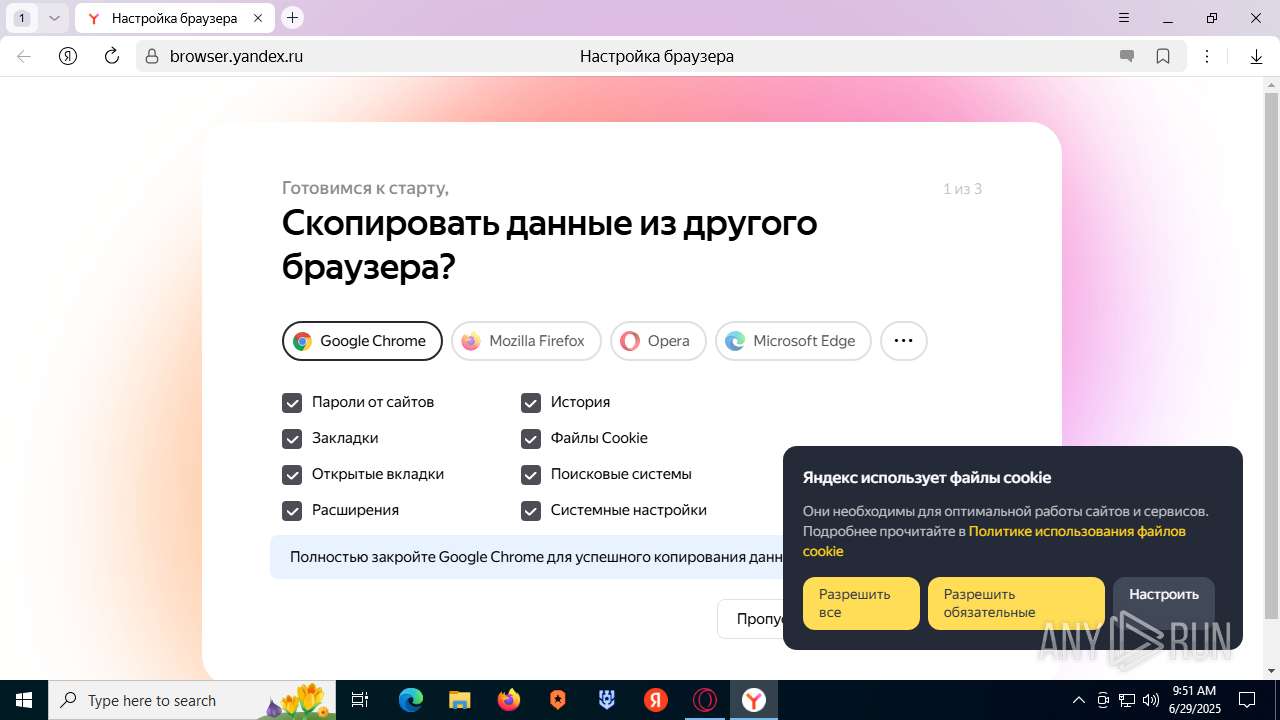
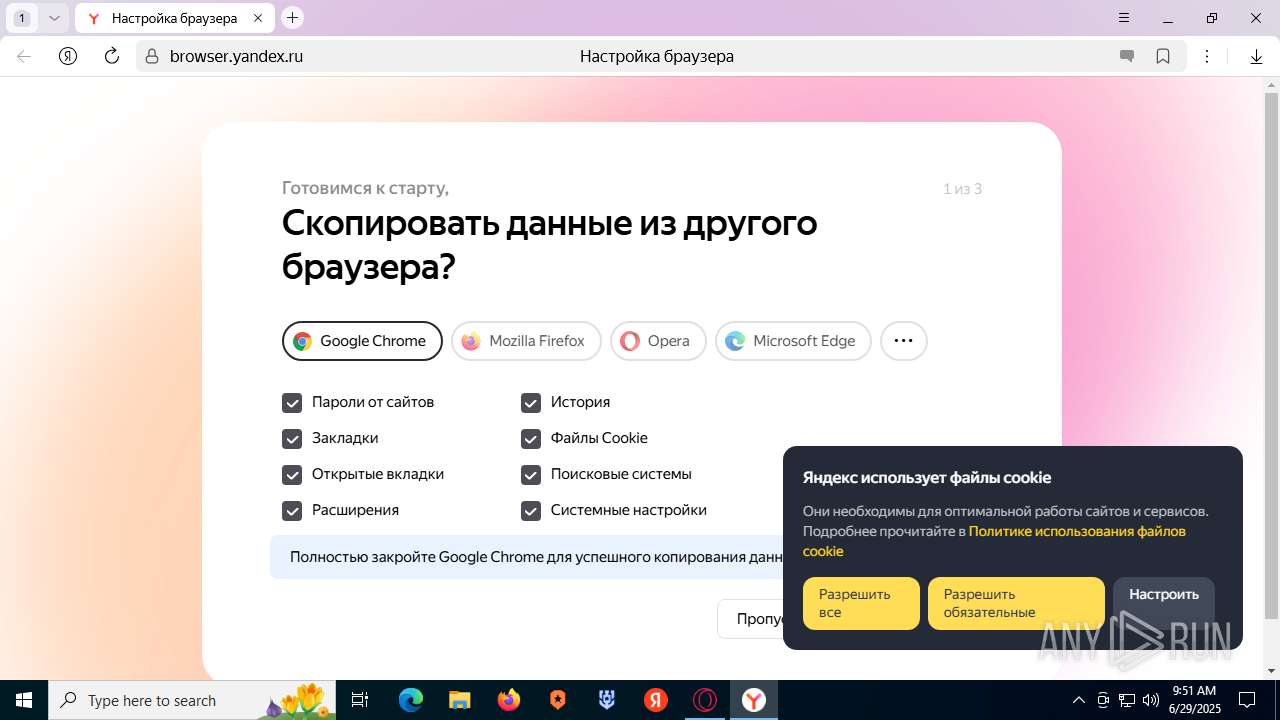
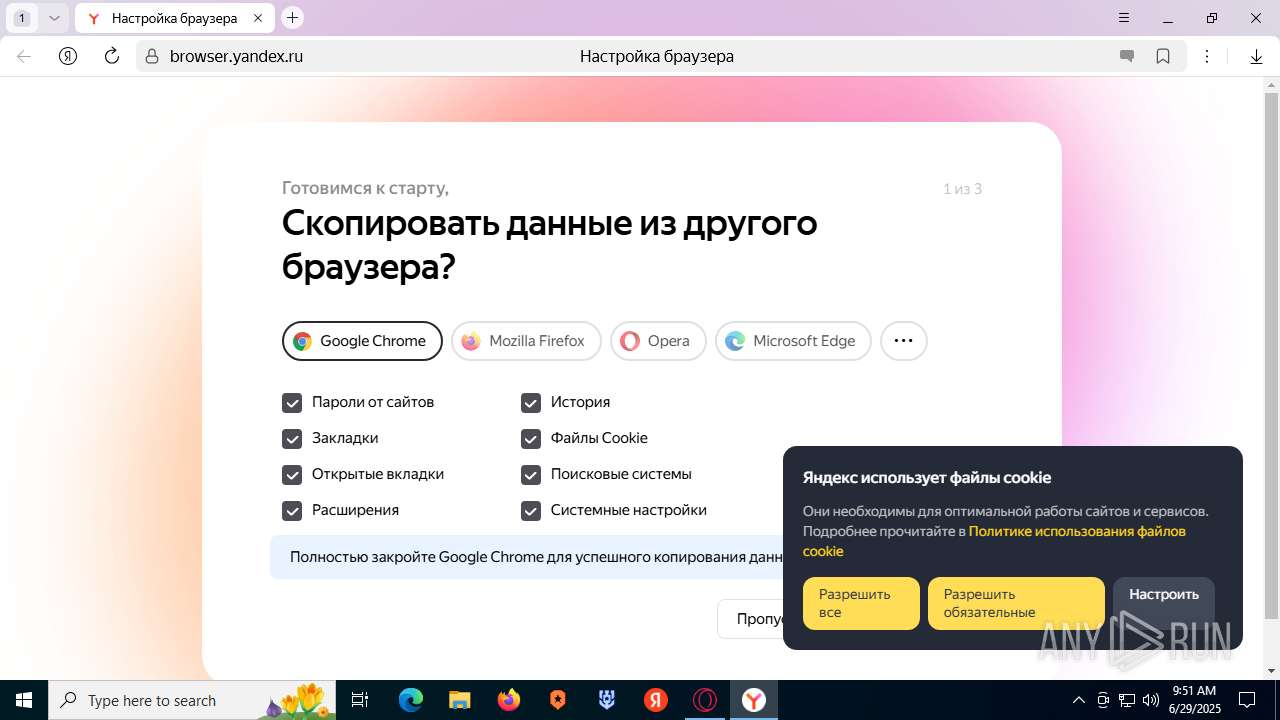
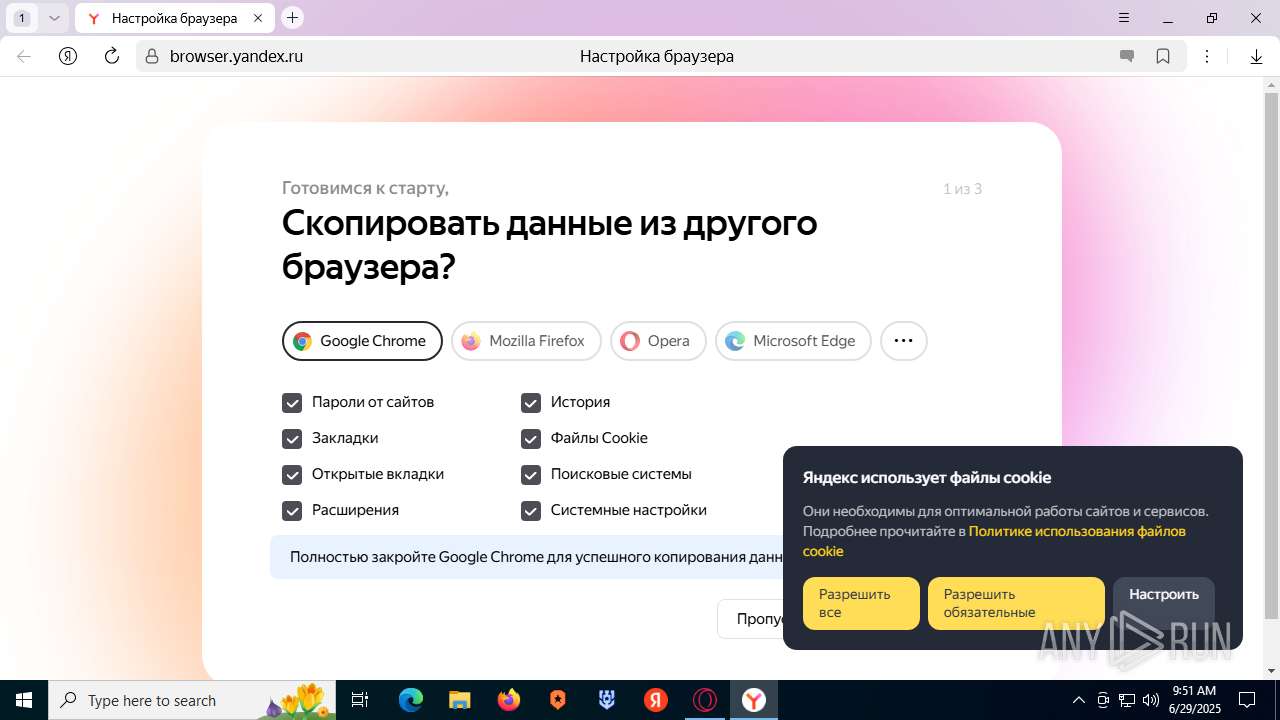
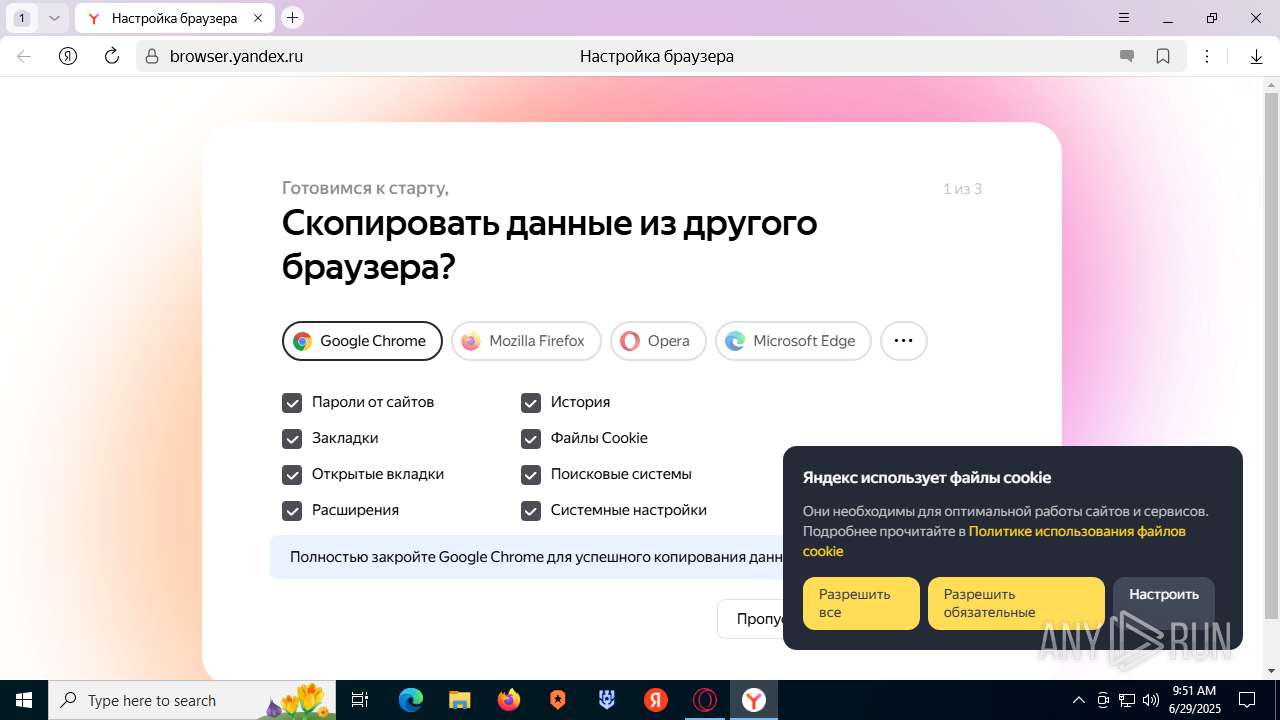
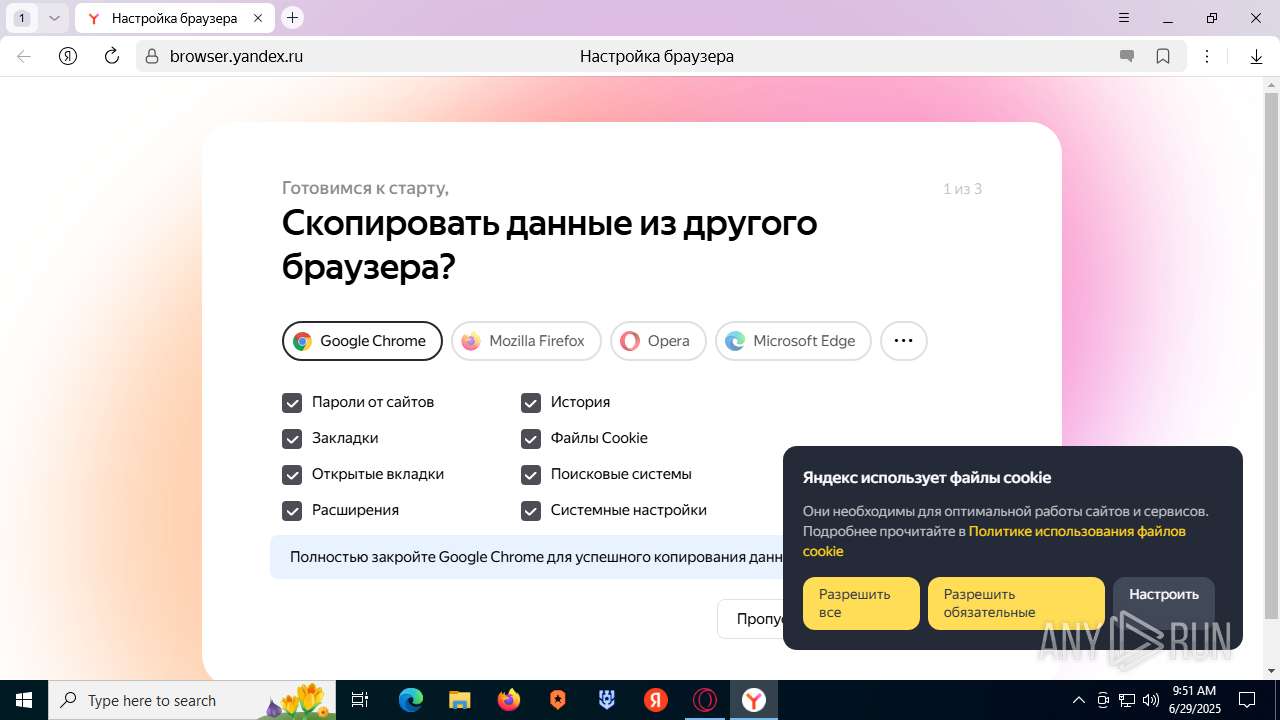
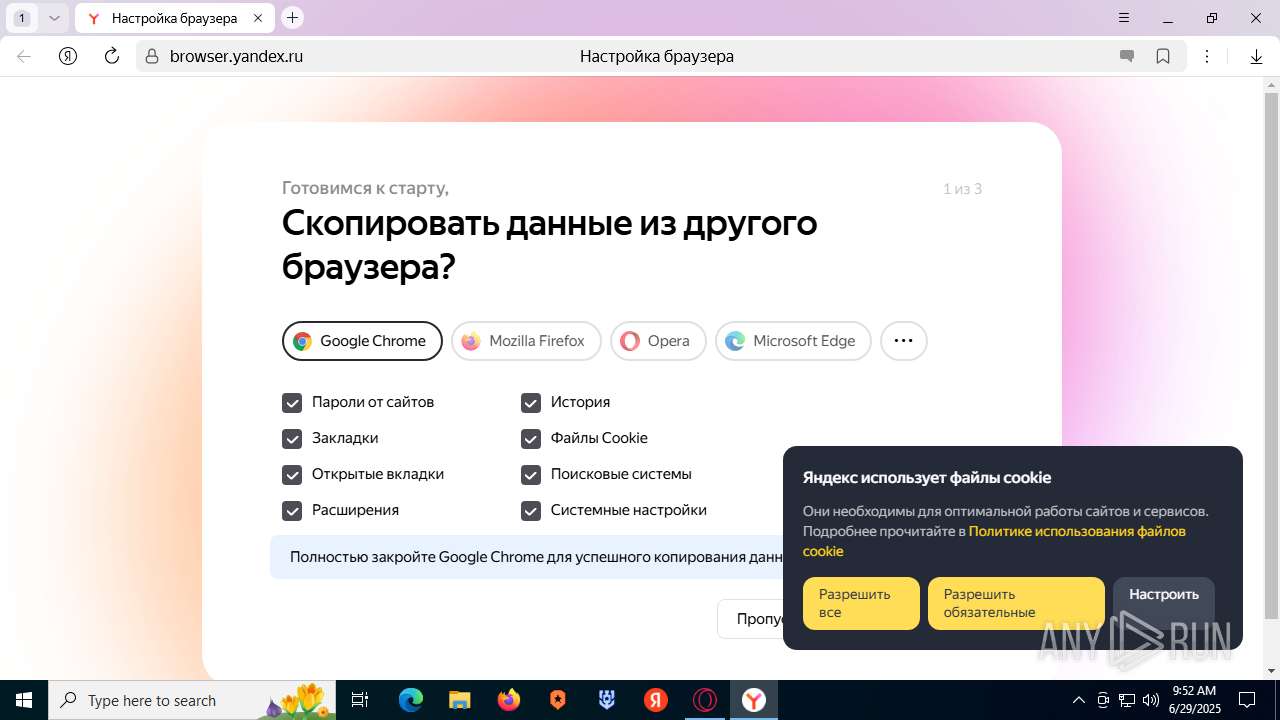
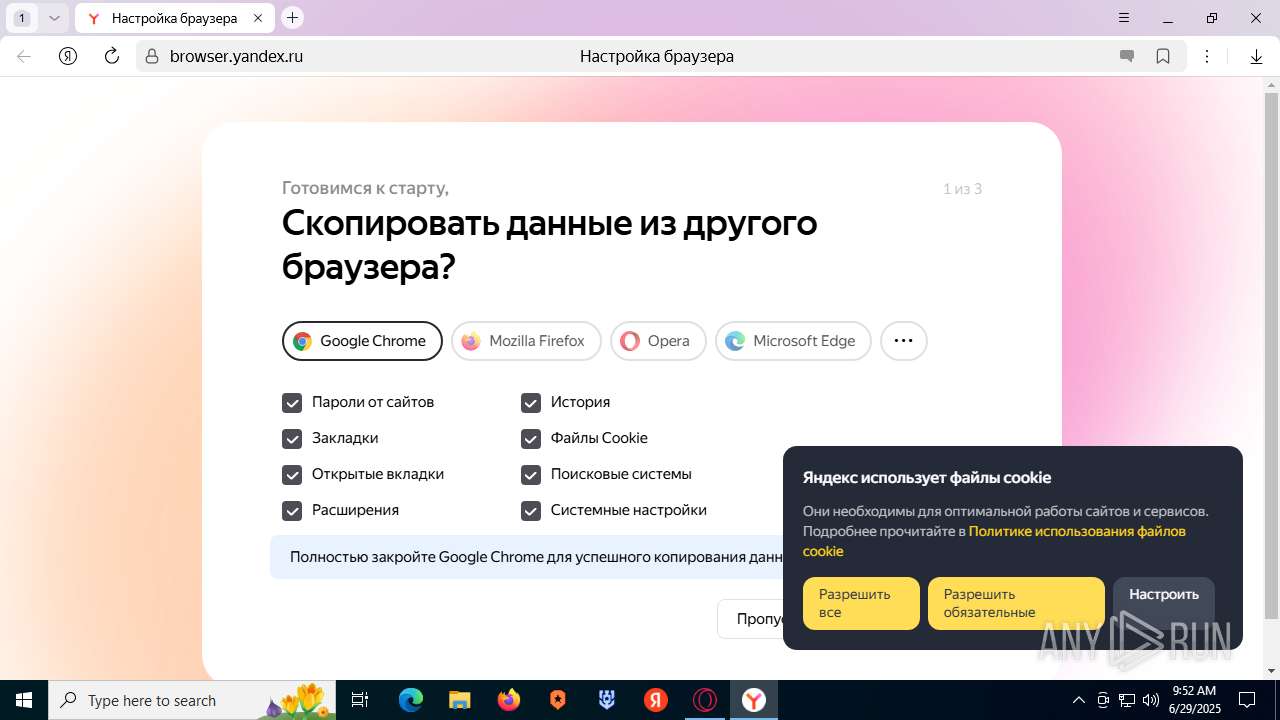
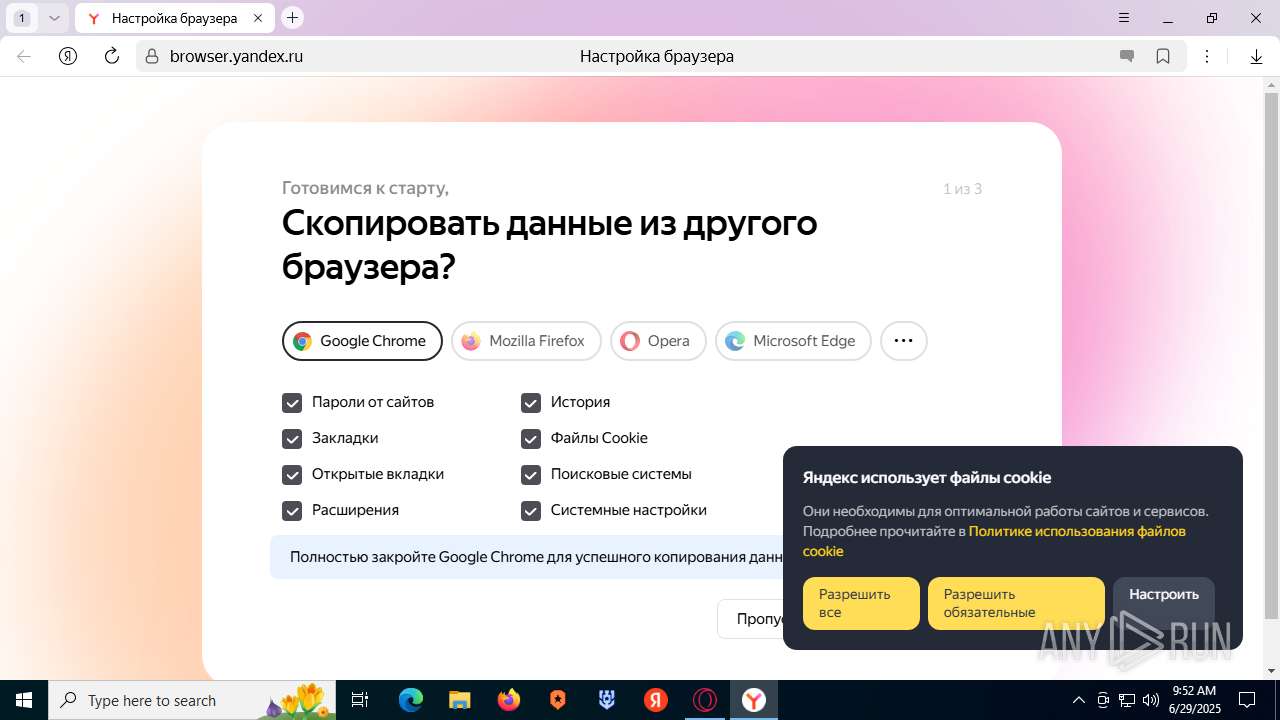
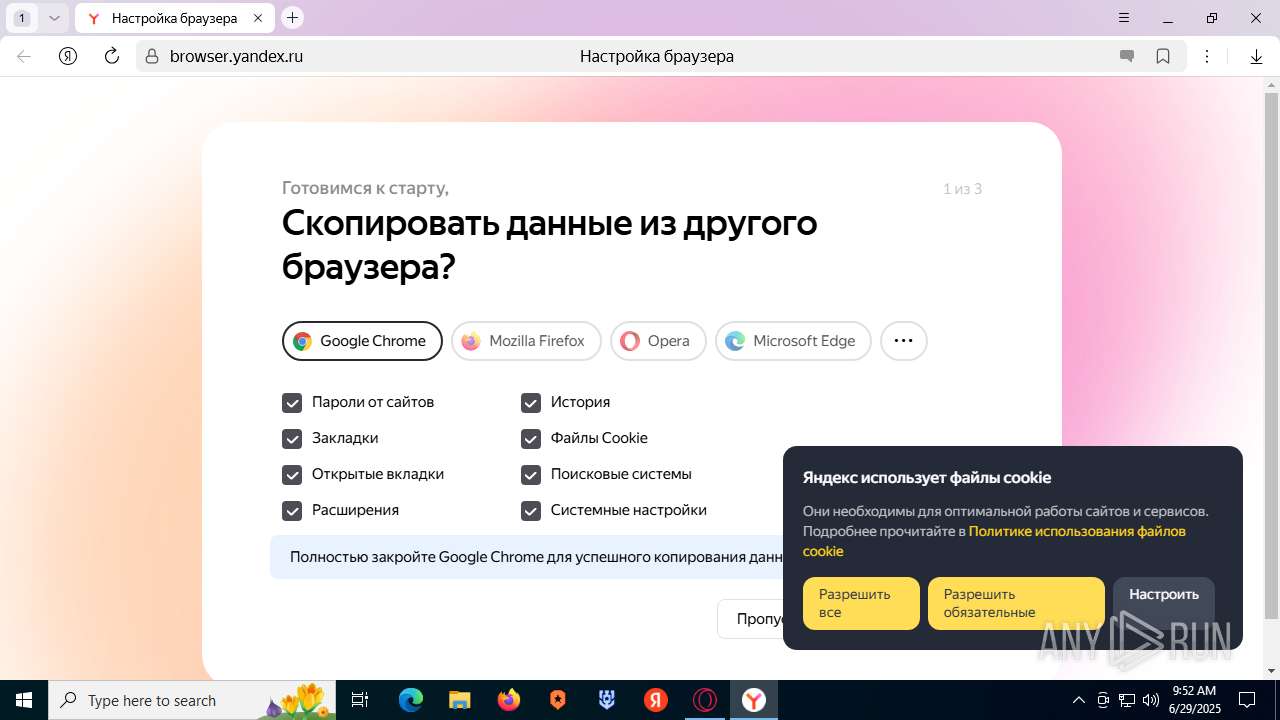
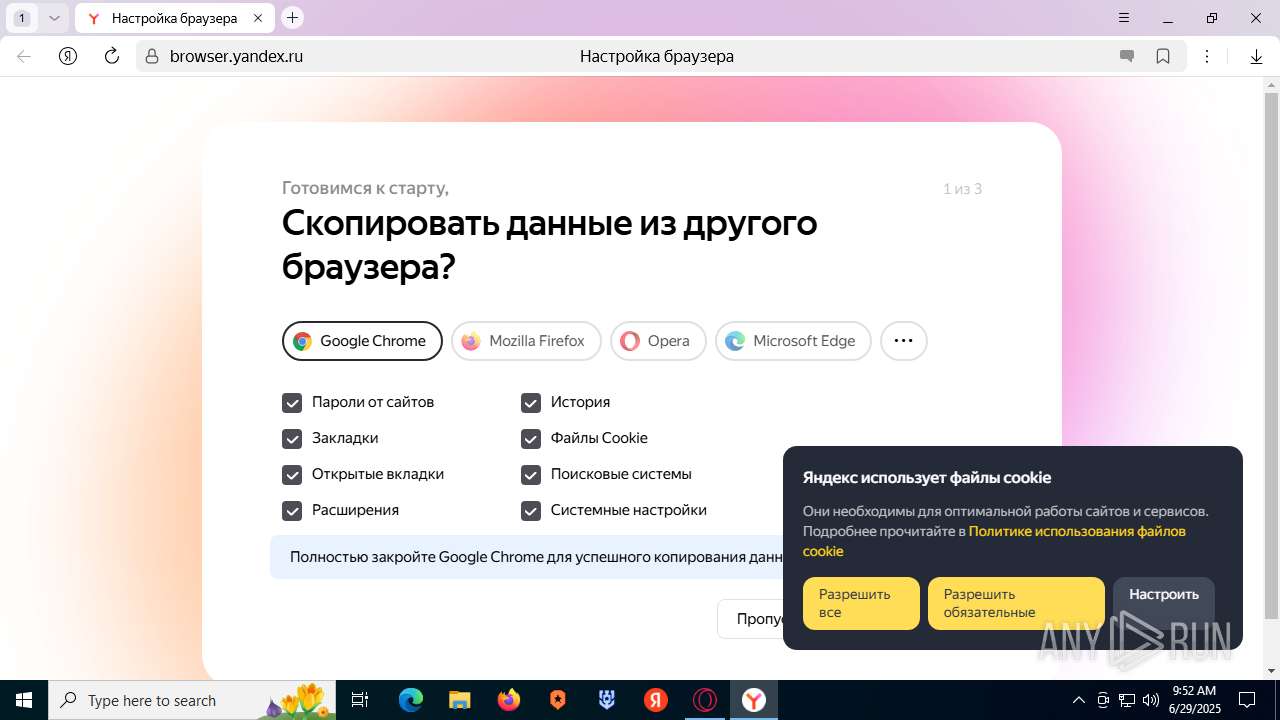
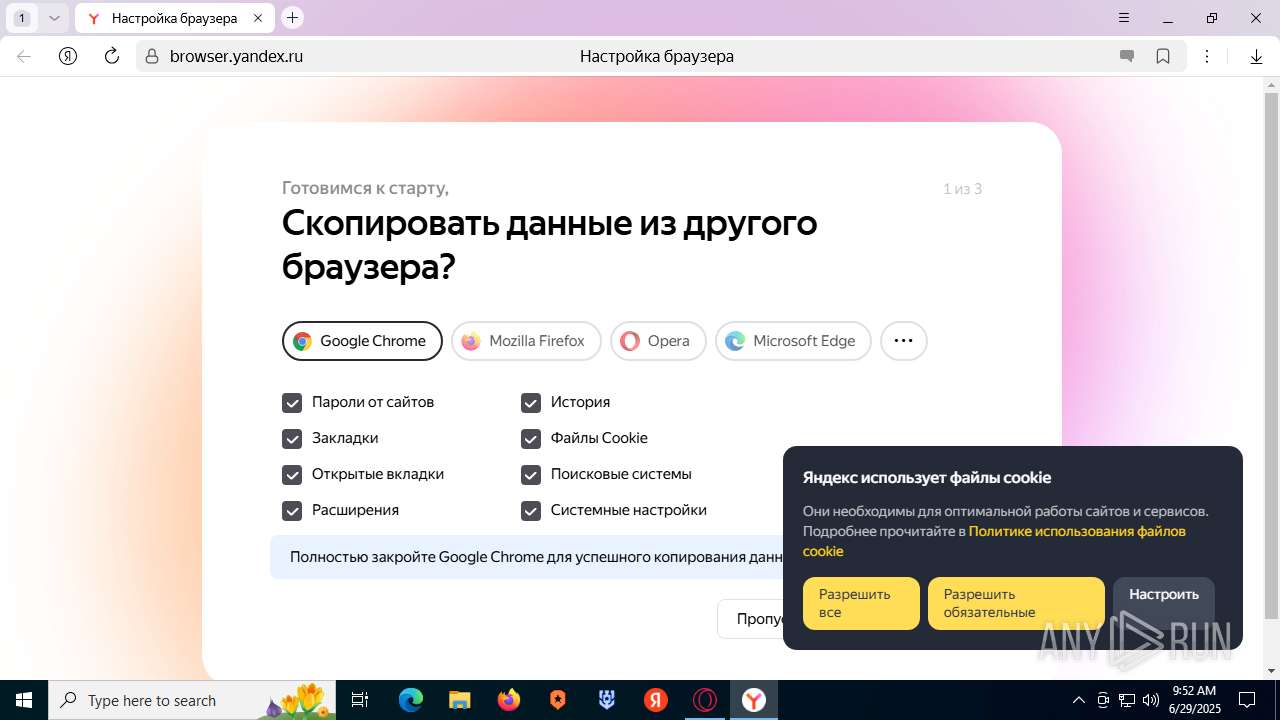
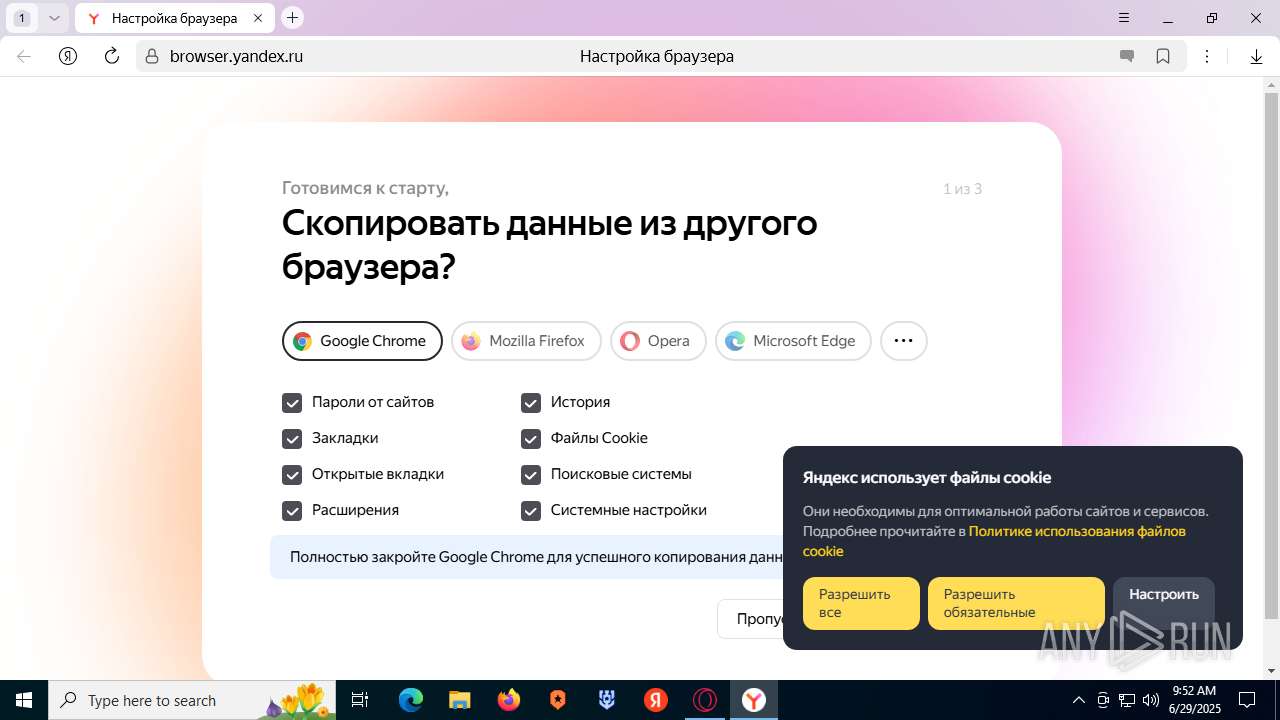
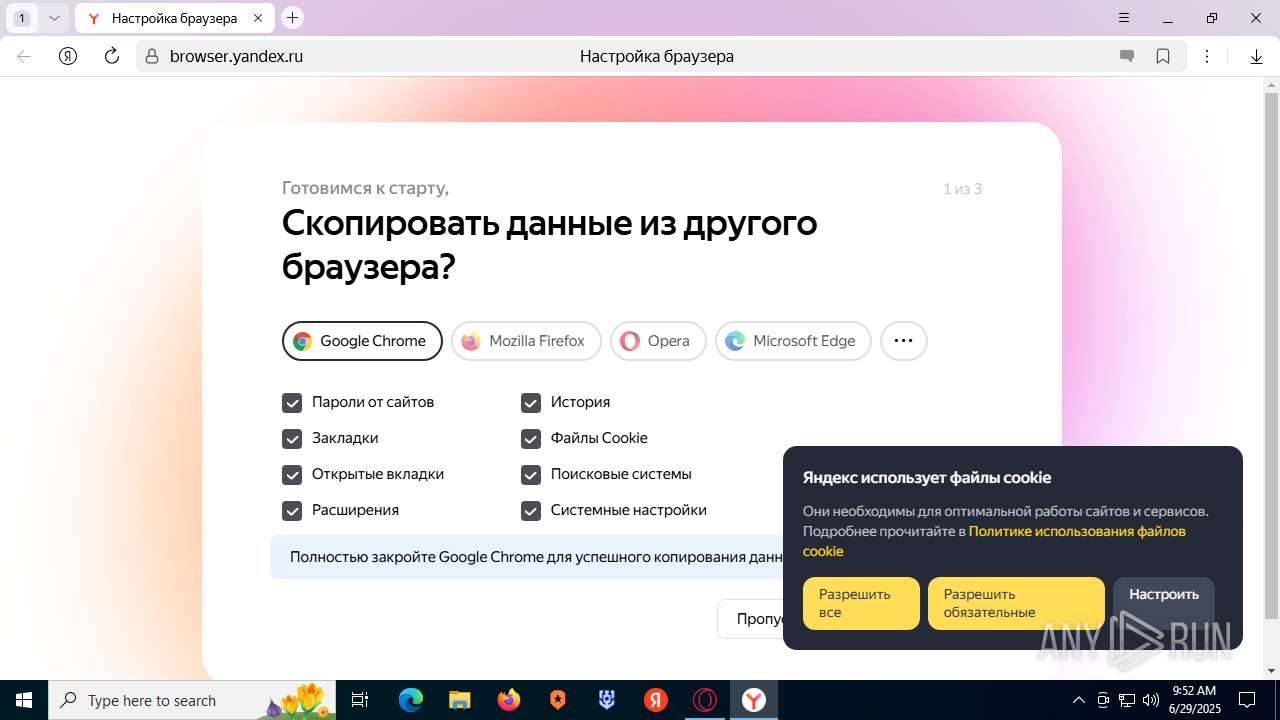
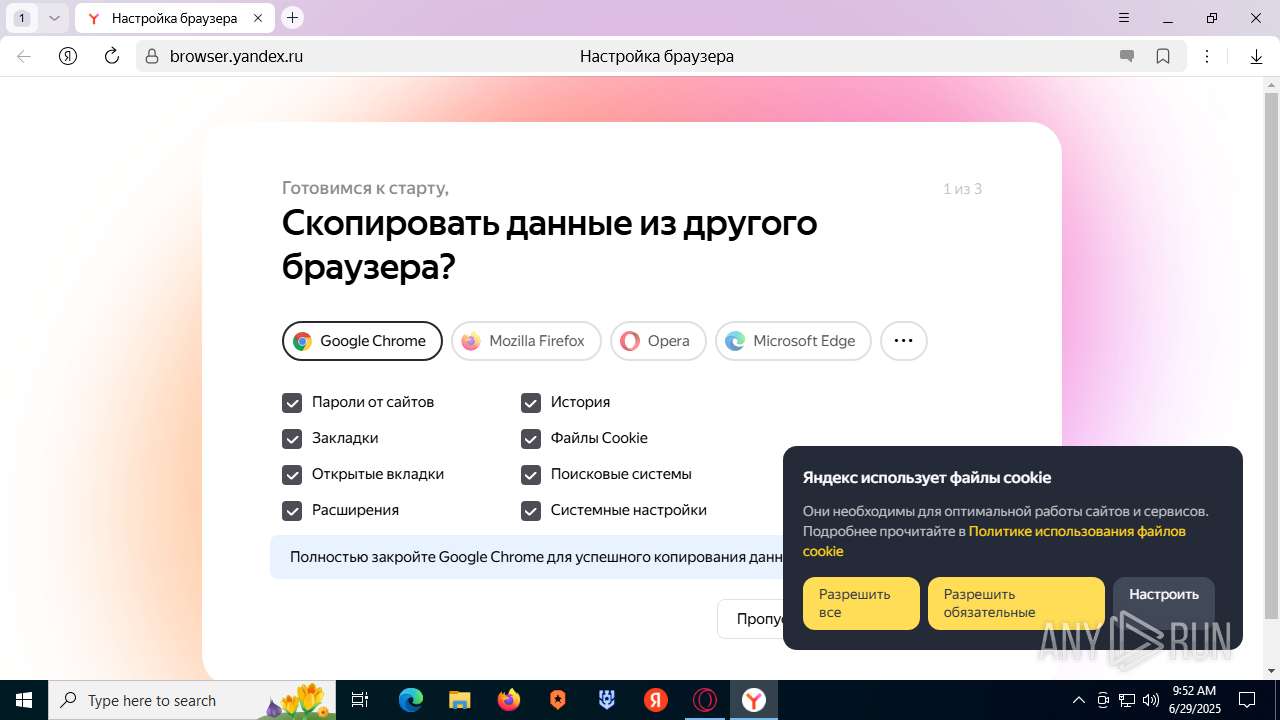
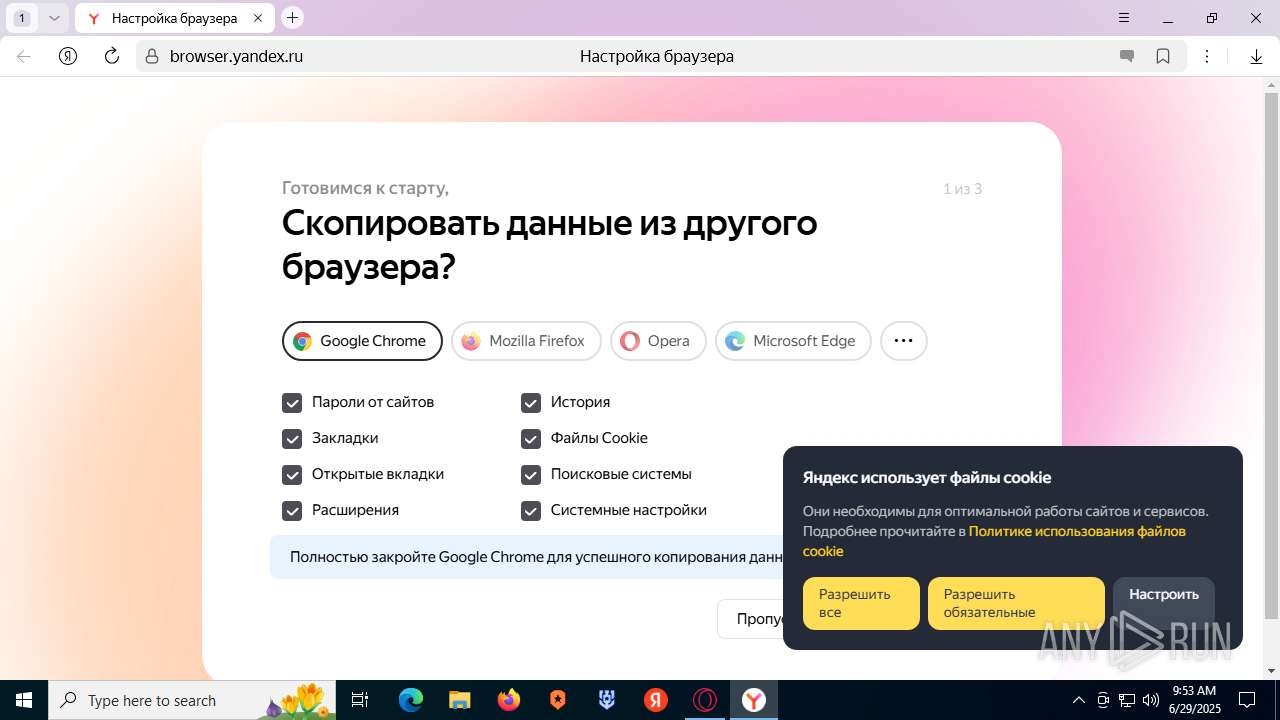
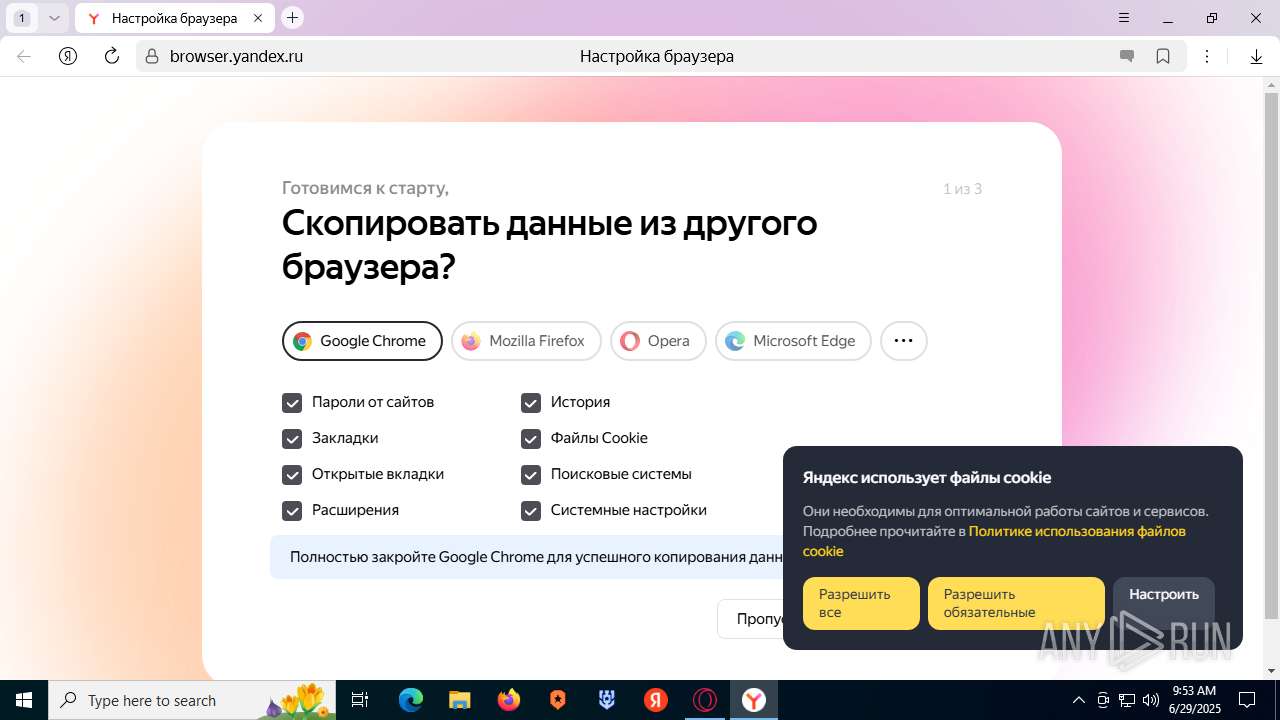
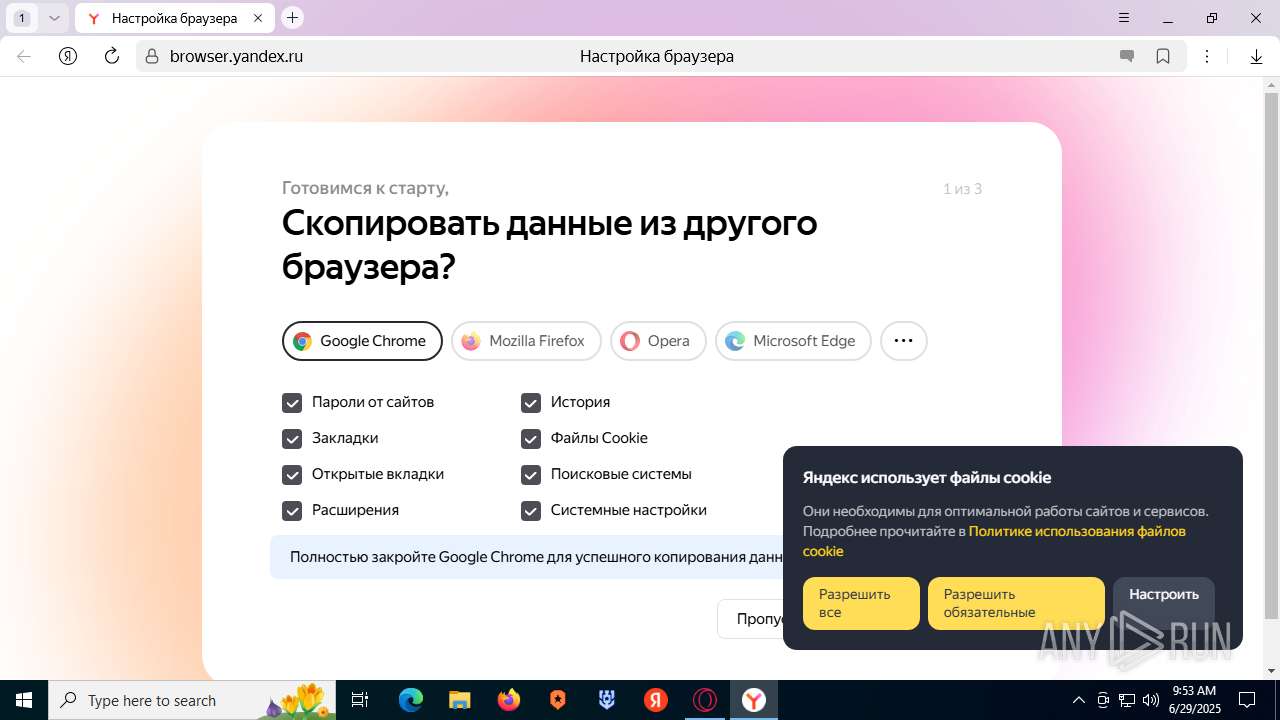
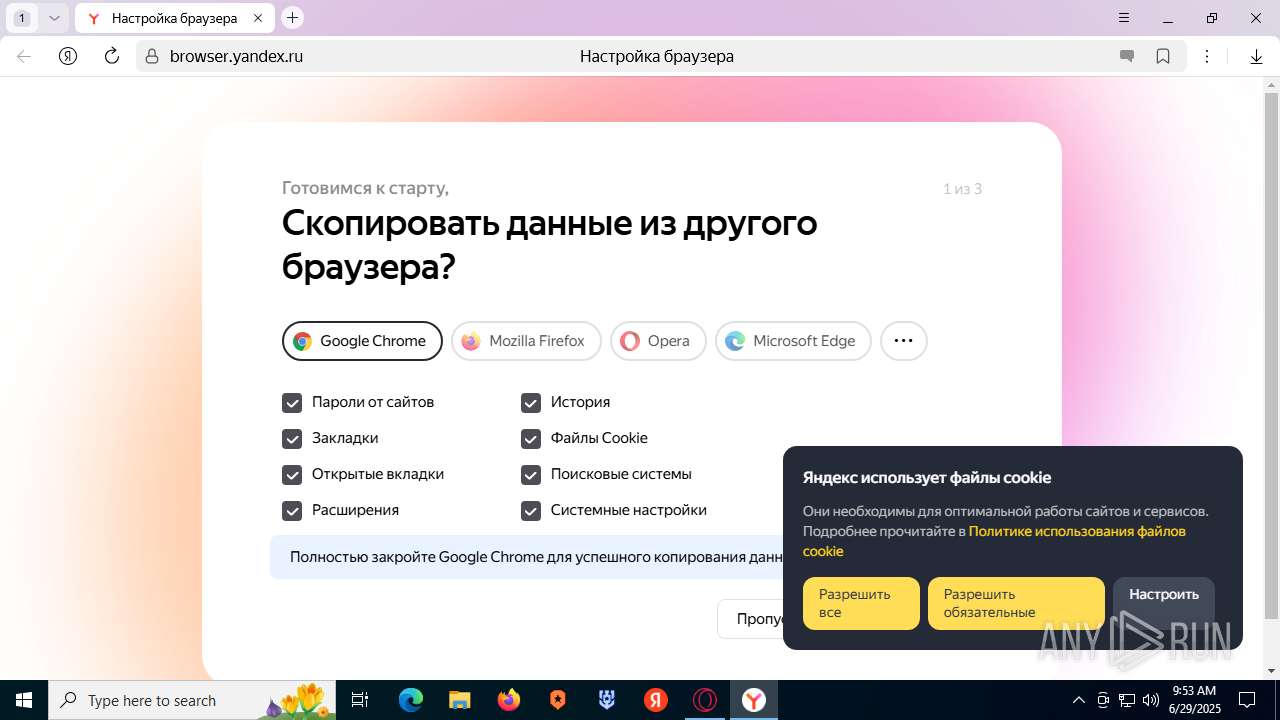
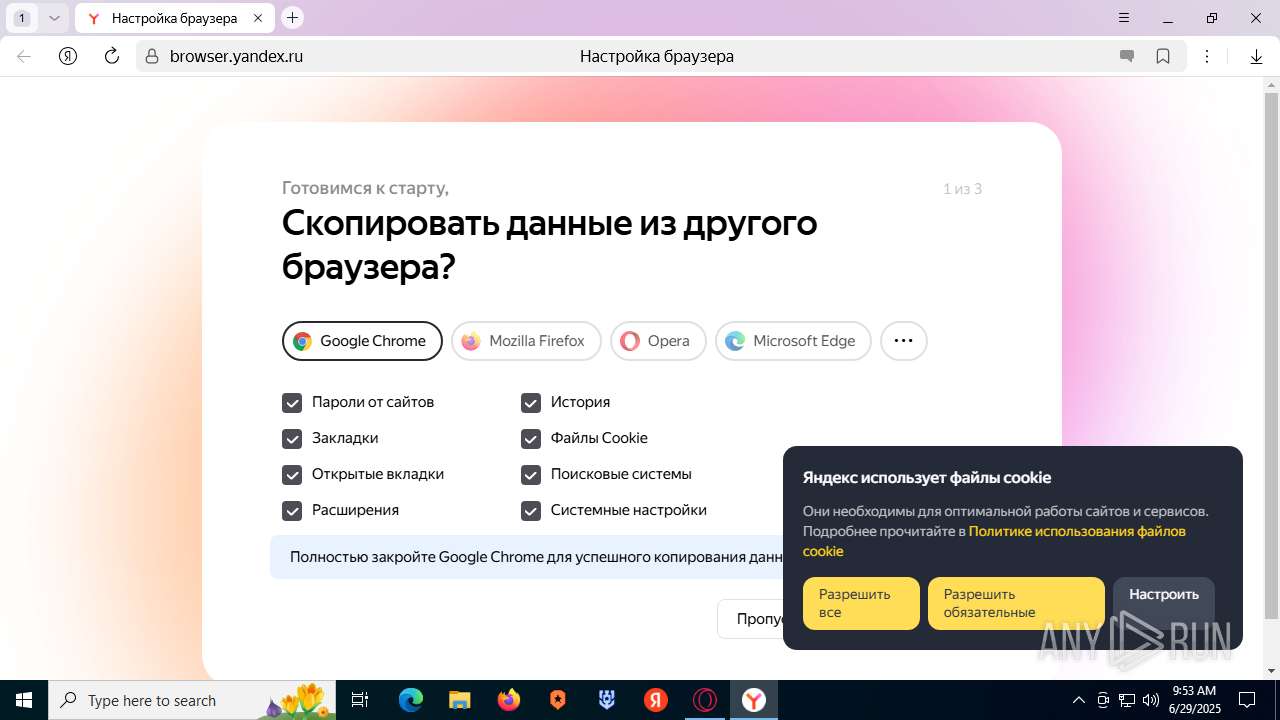
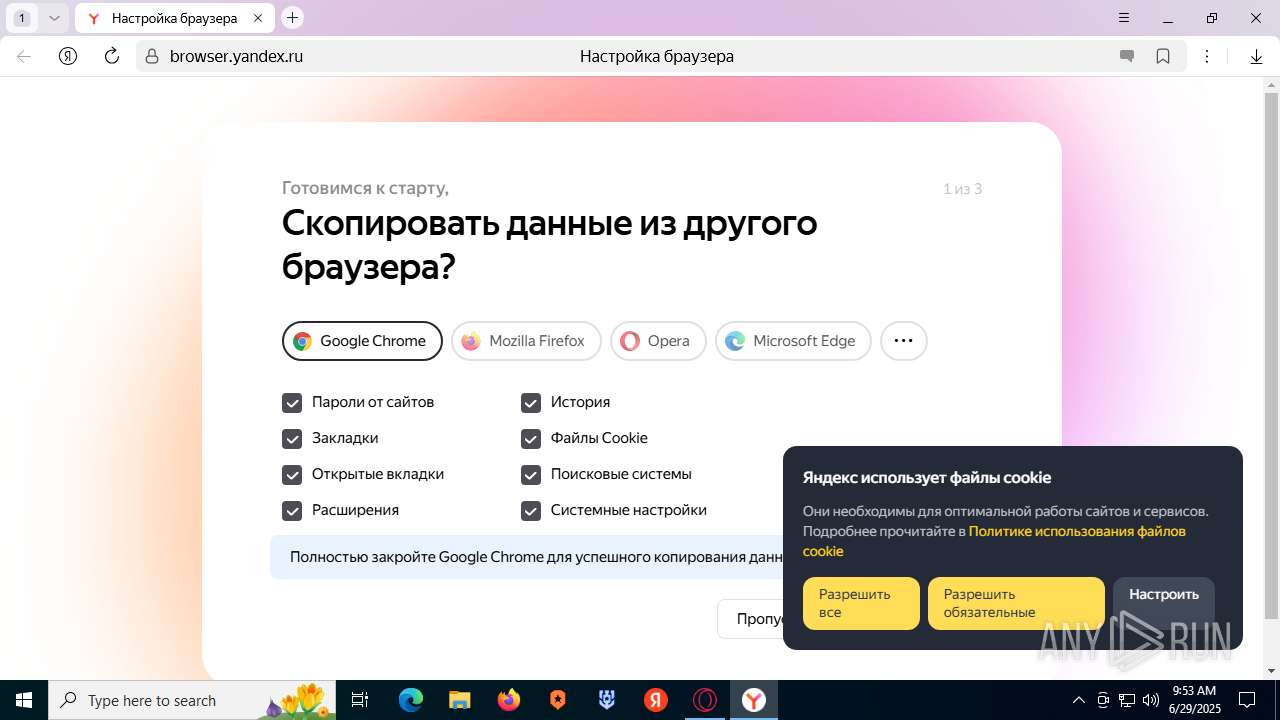
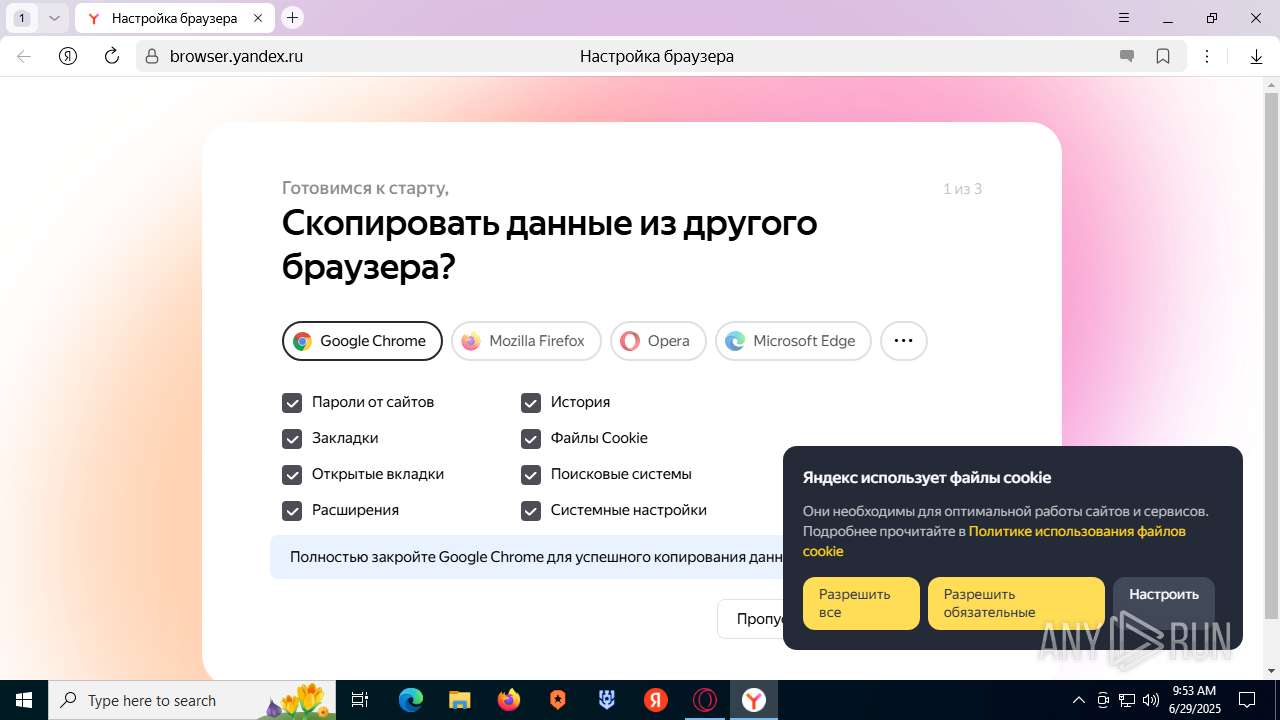
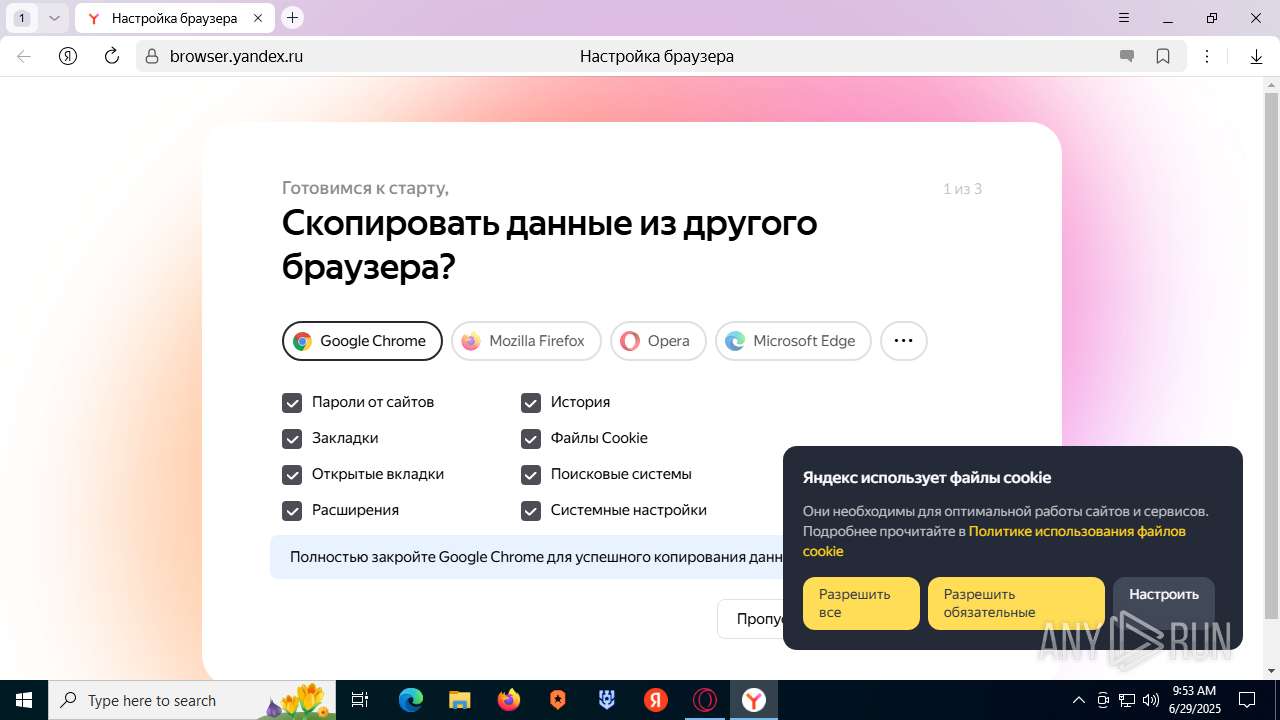
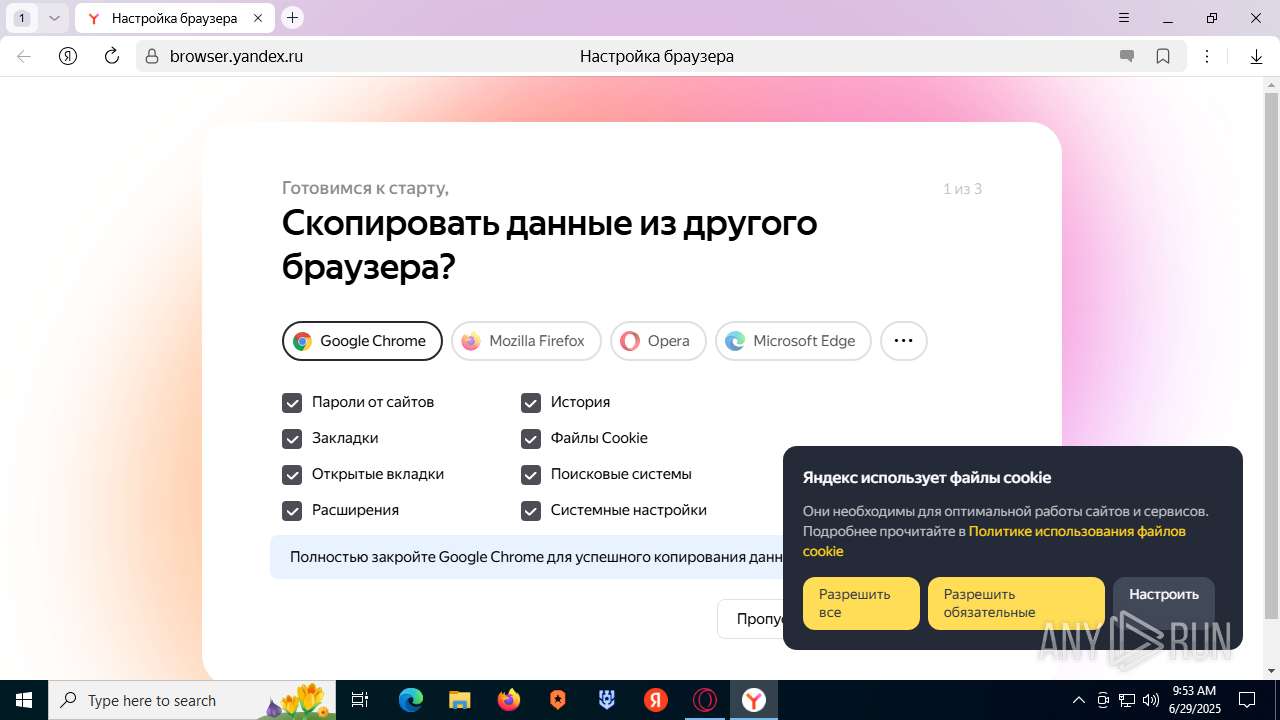
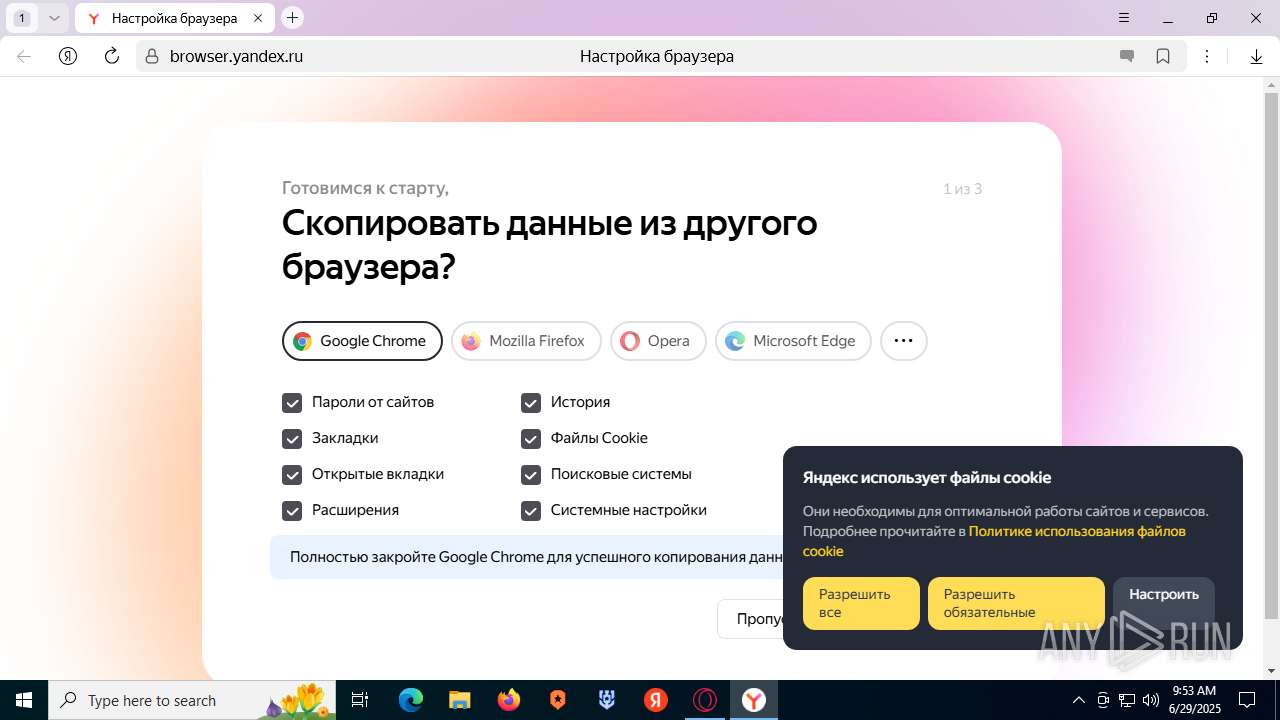
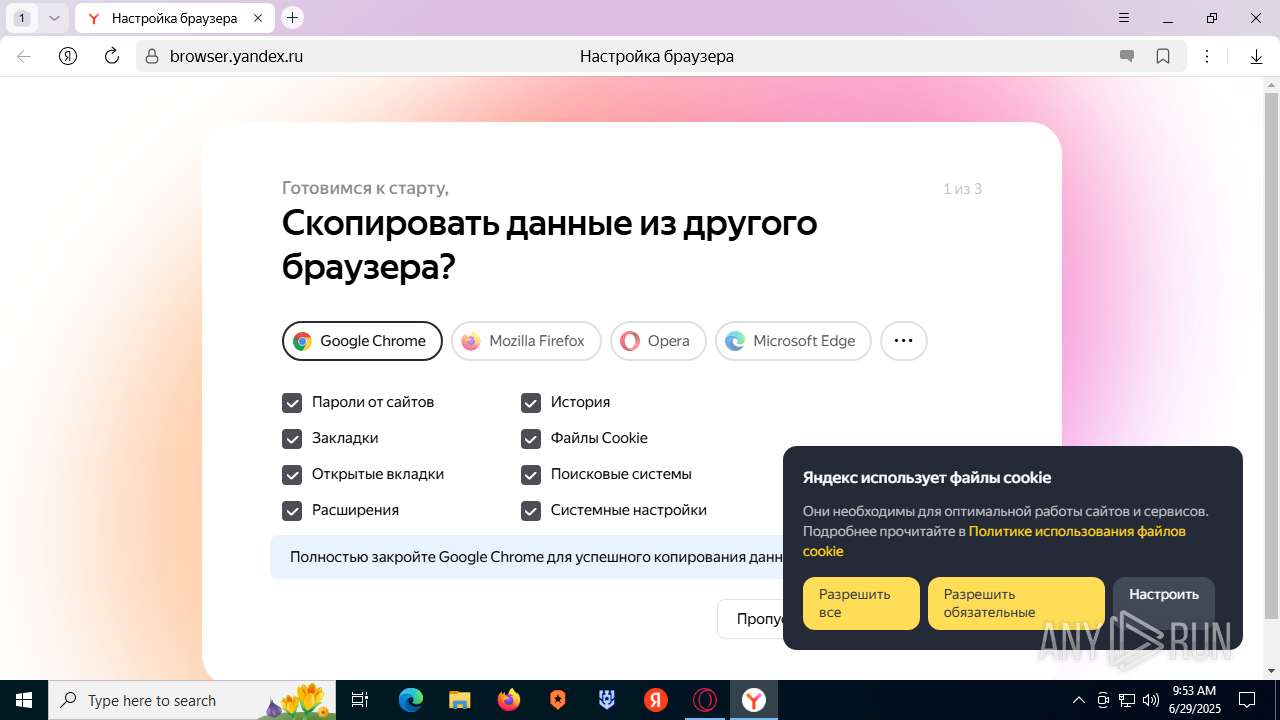
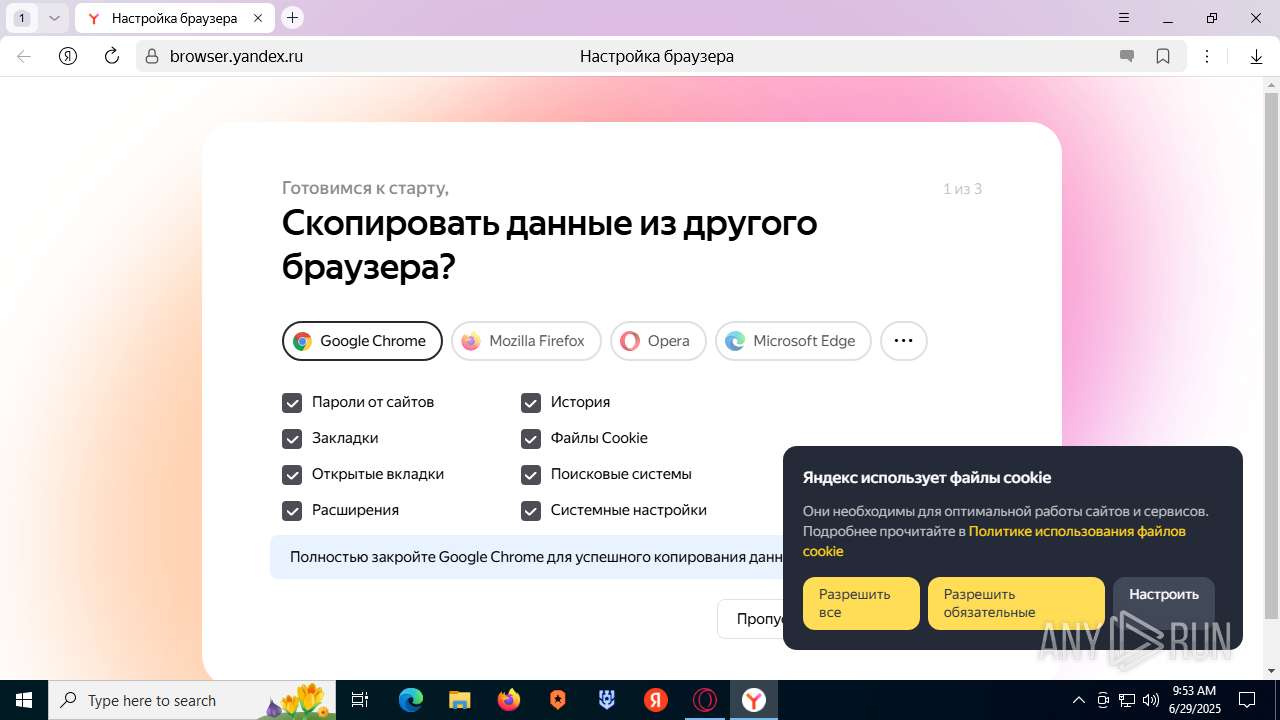
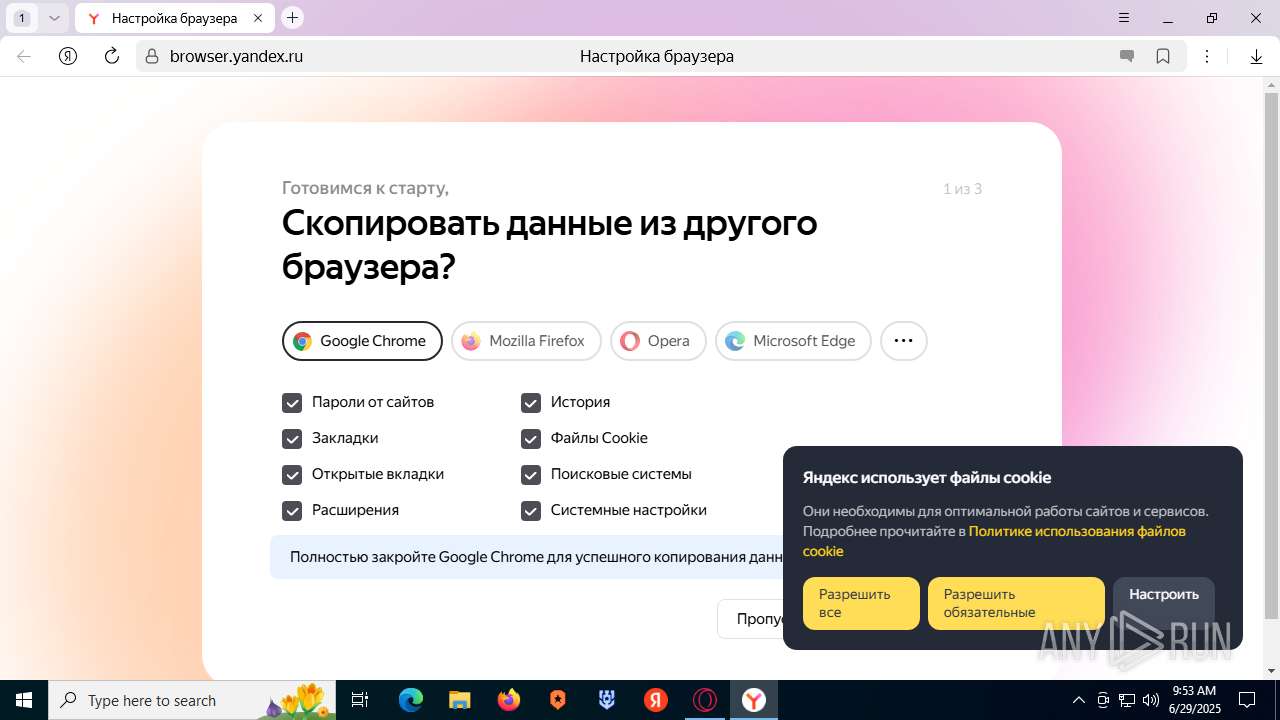
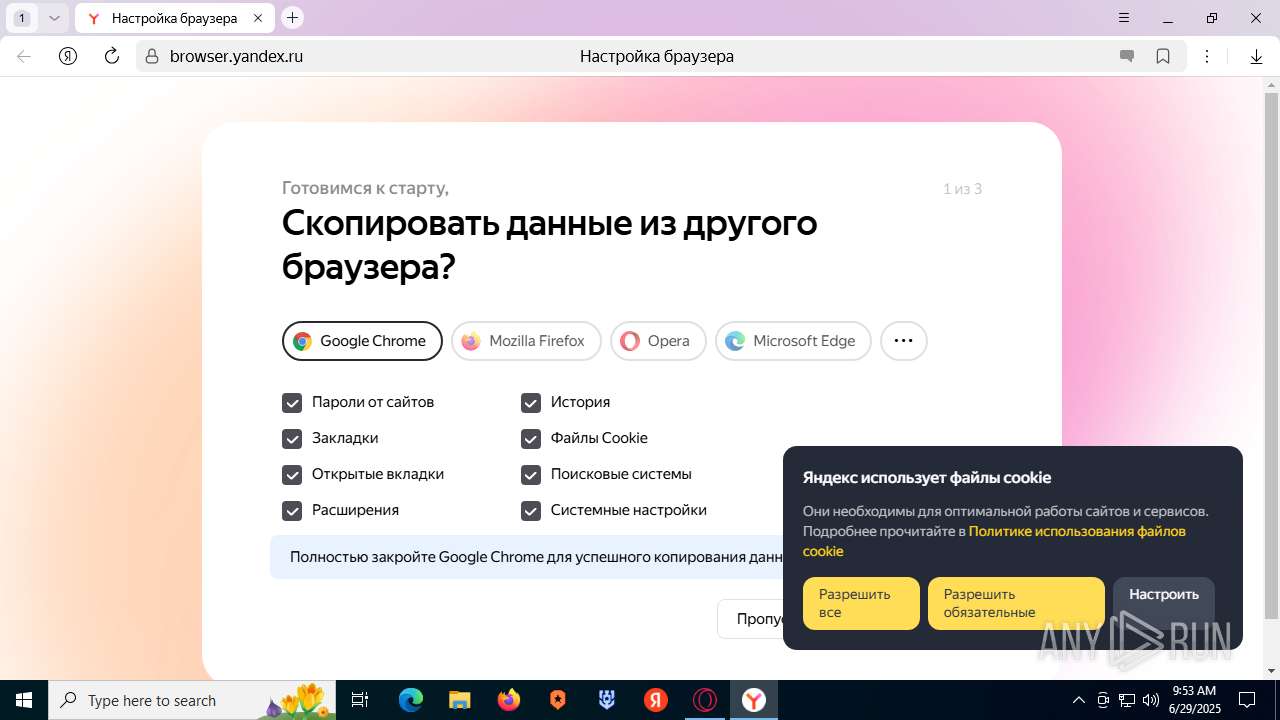
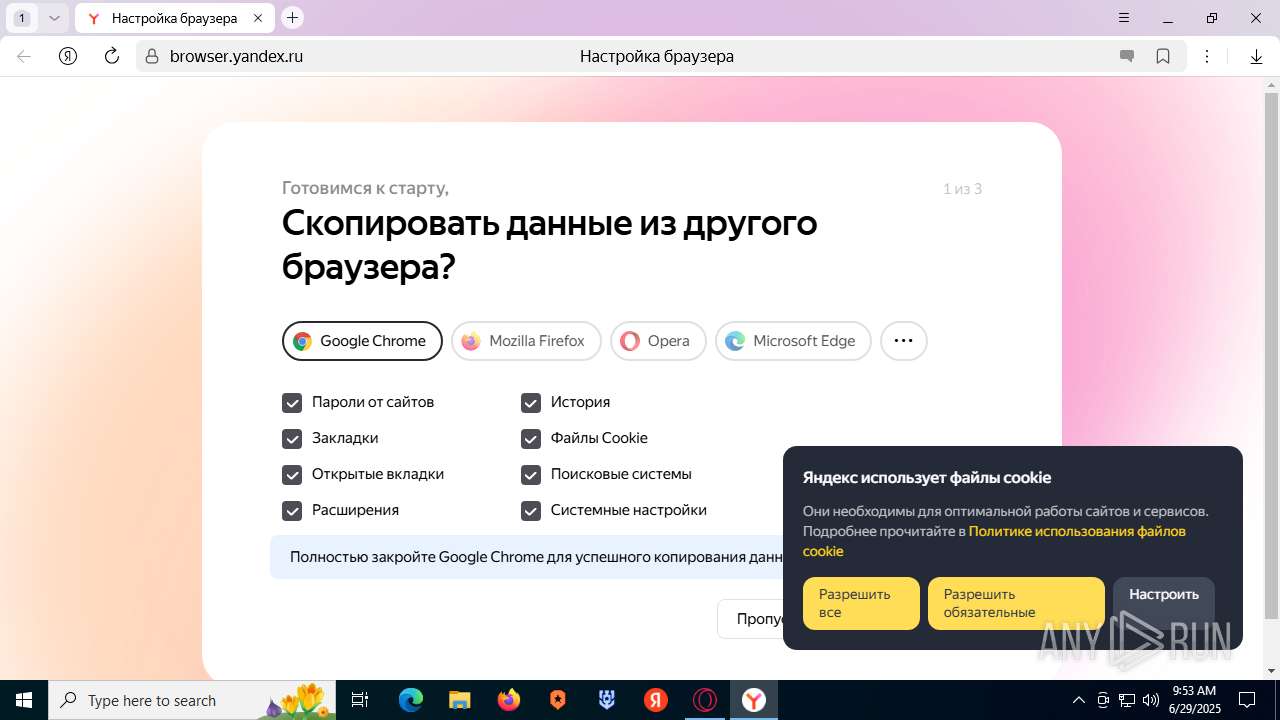
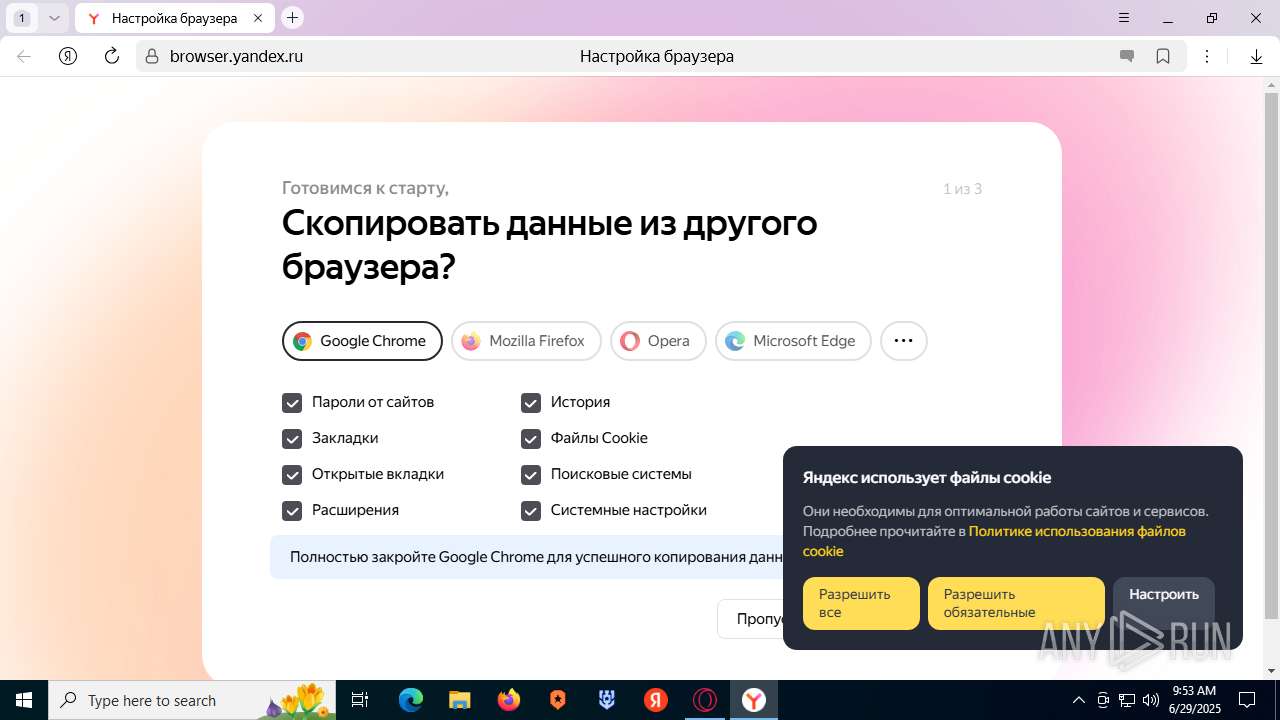
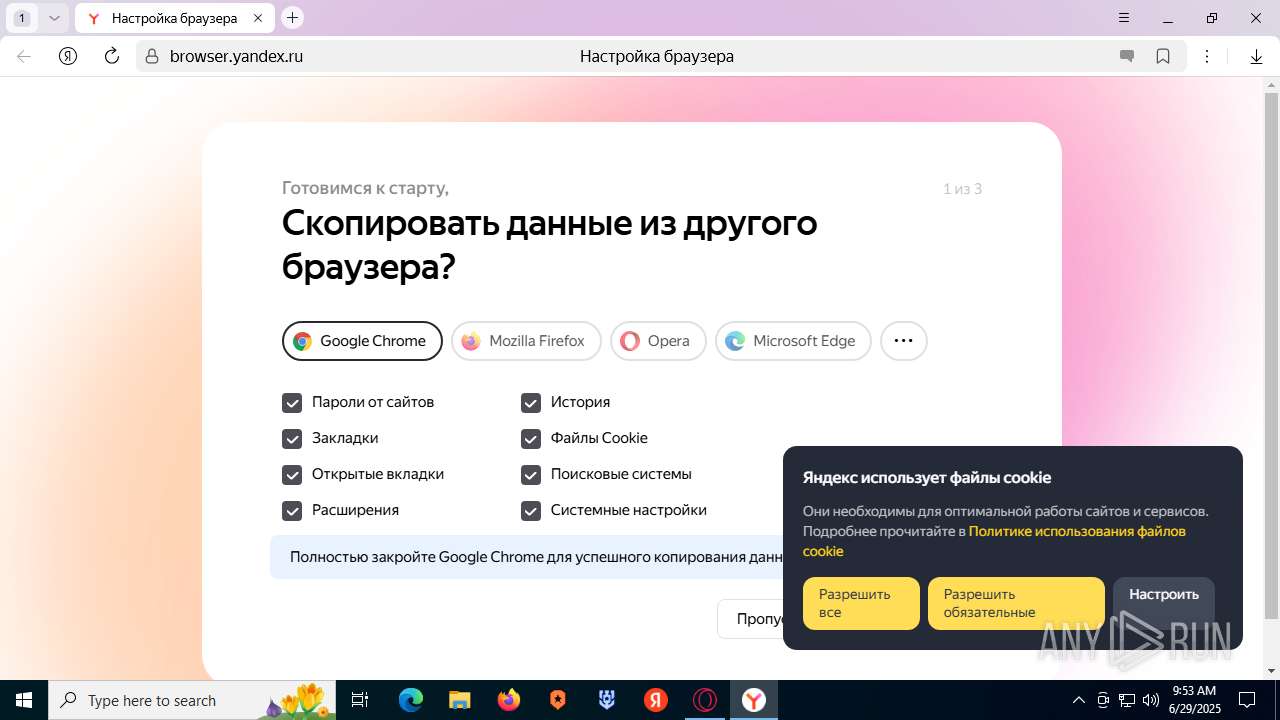
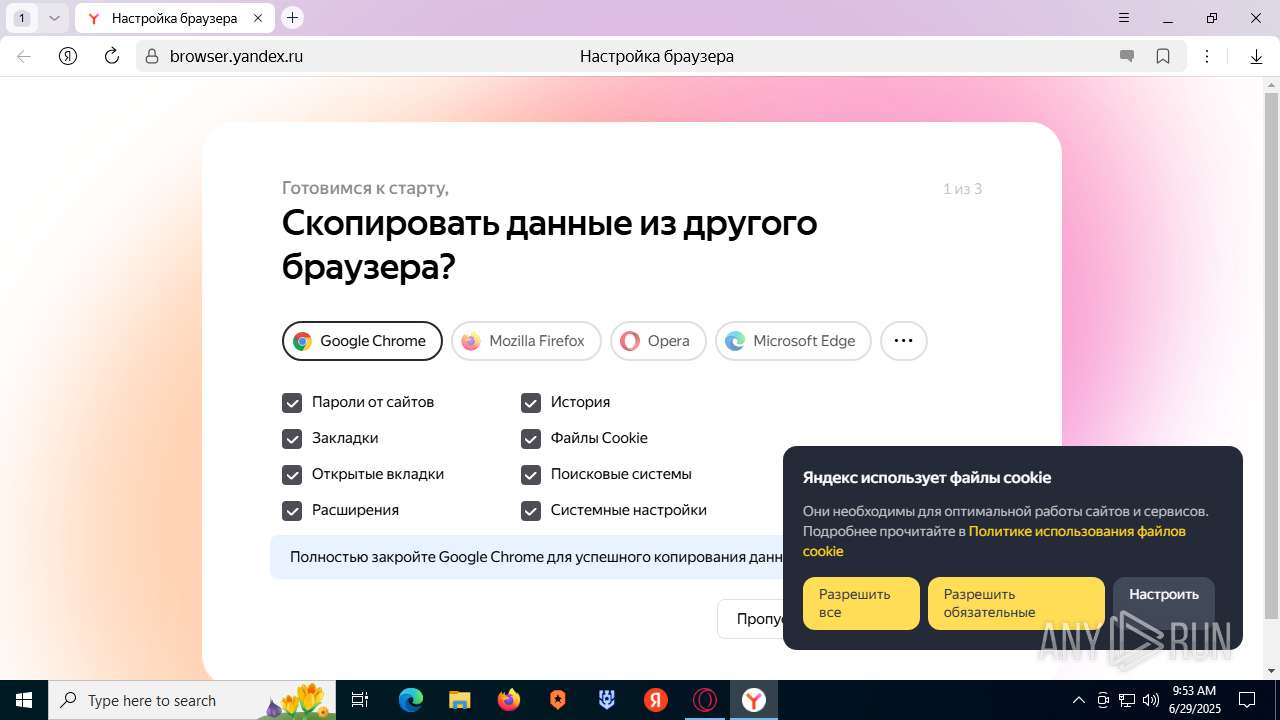
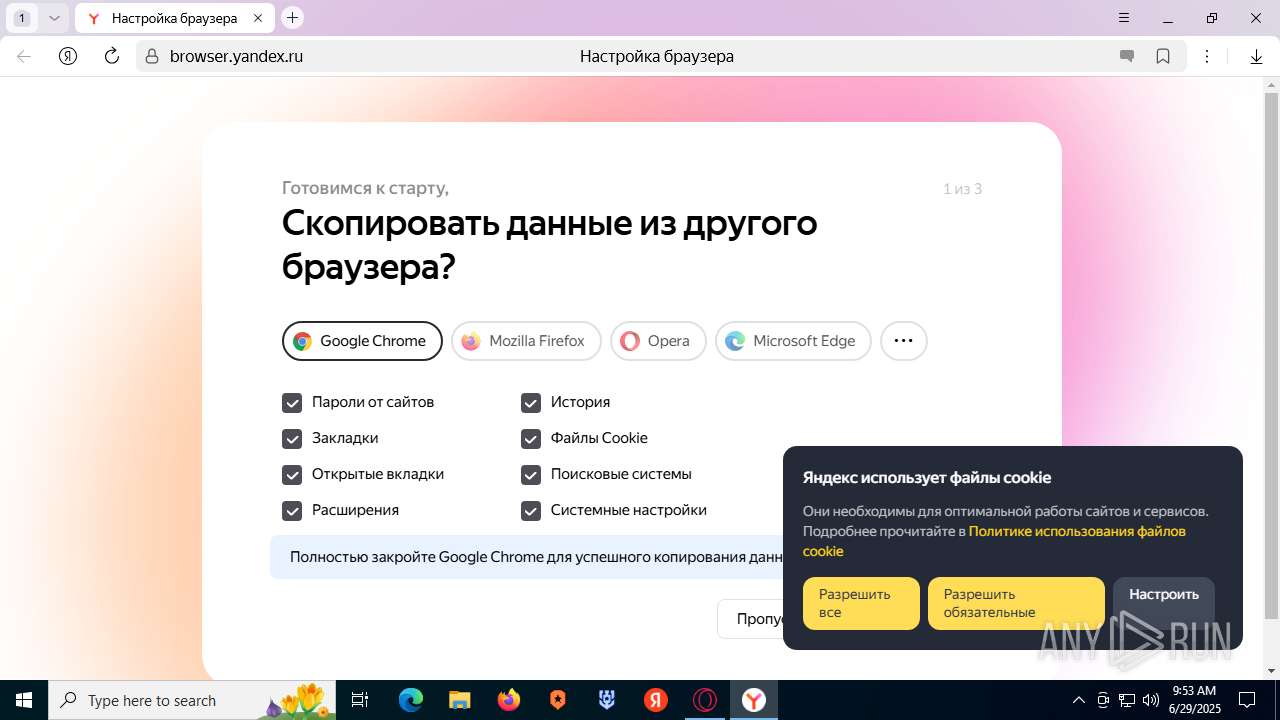
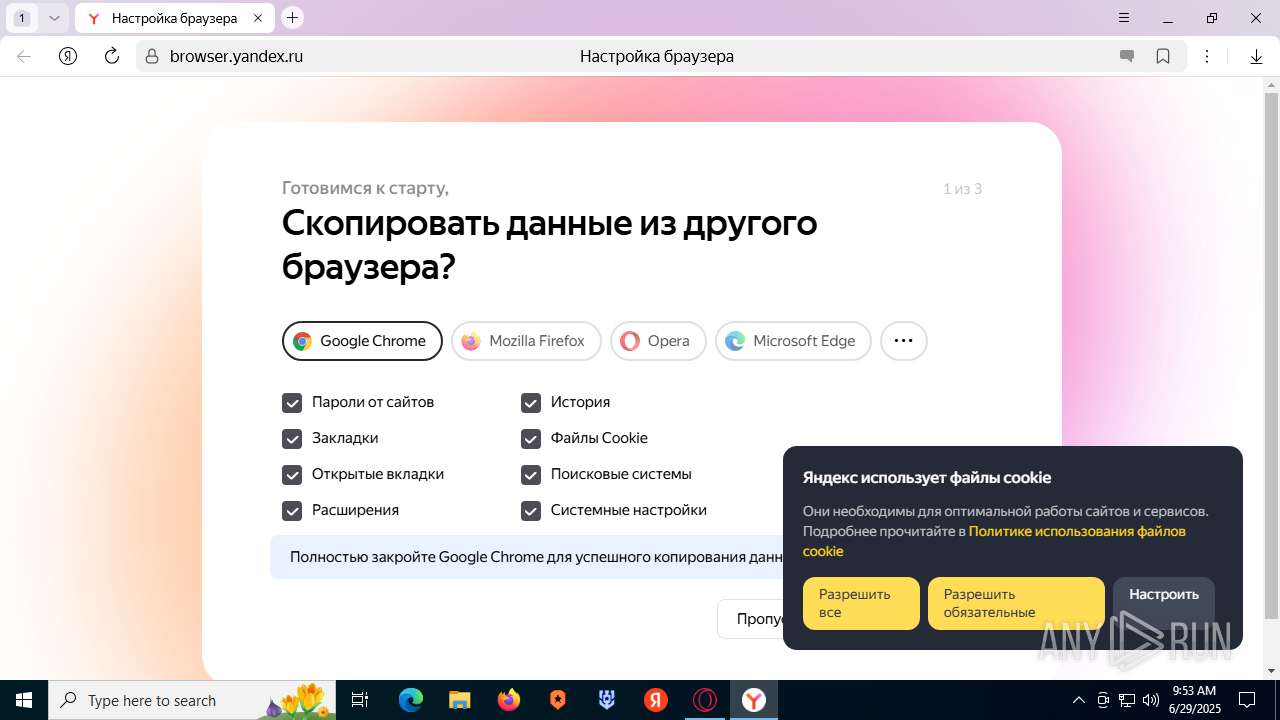
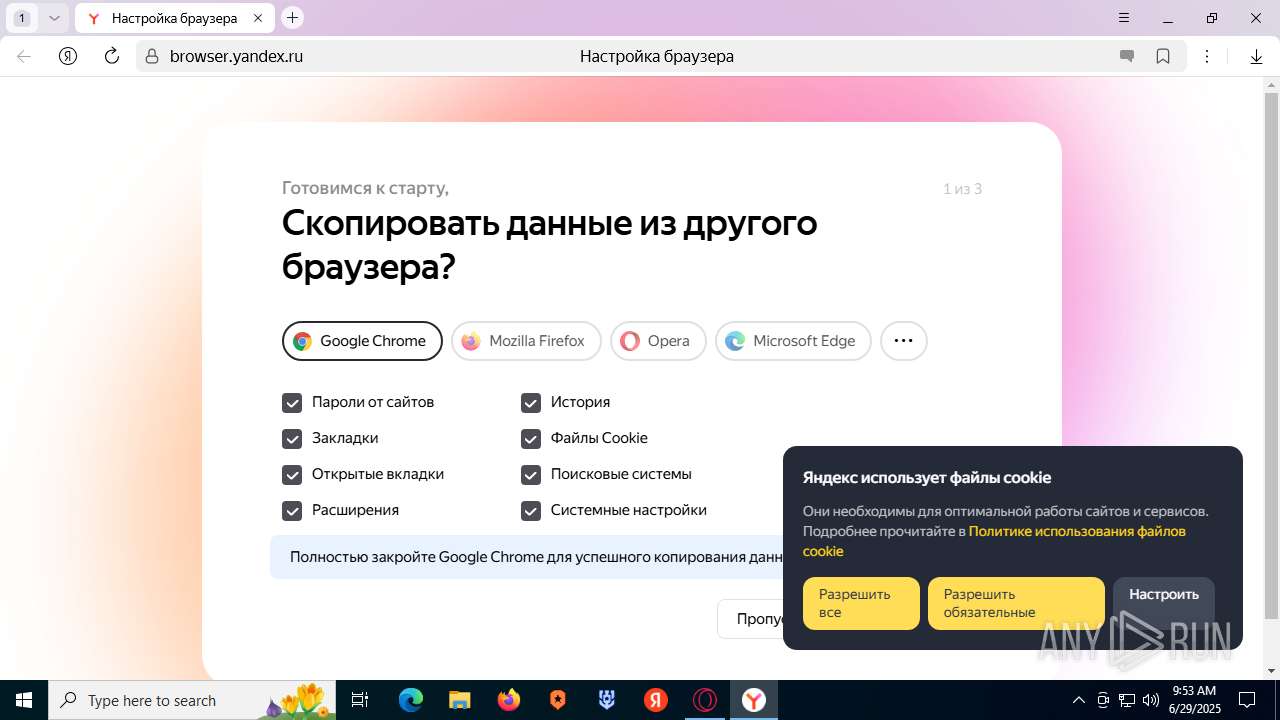
| URL: | https://discord.softbeachcamp.com/ |
| Full analysis: | https://app.any.run/tasks/6982d88b-d745-47c7-93a9-4dc69e9f3117 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | June 29, 2025, 09:48:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 48513C788BC2405CC75F906715764595 |
| SHA1: | BBDDEE87171917E6408B20FF0046F3257A44A8FE |
| SHA256: | BEFA33D04008256E7A51692D5FE058B6C32C8912D92CA13EA0EF48C8FEE52DE6 |
| SSDEEP: | 3:N8U8X01Ghf3:2Uif3 |
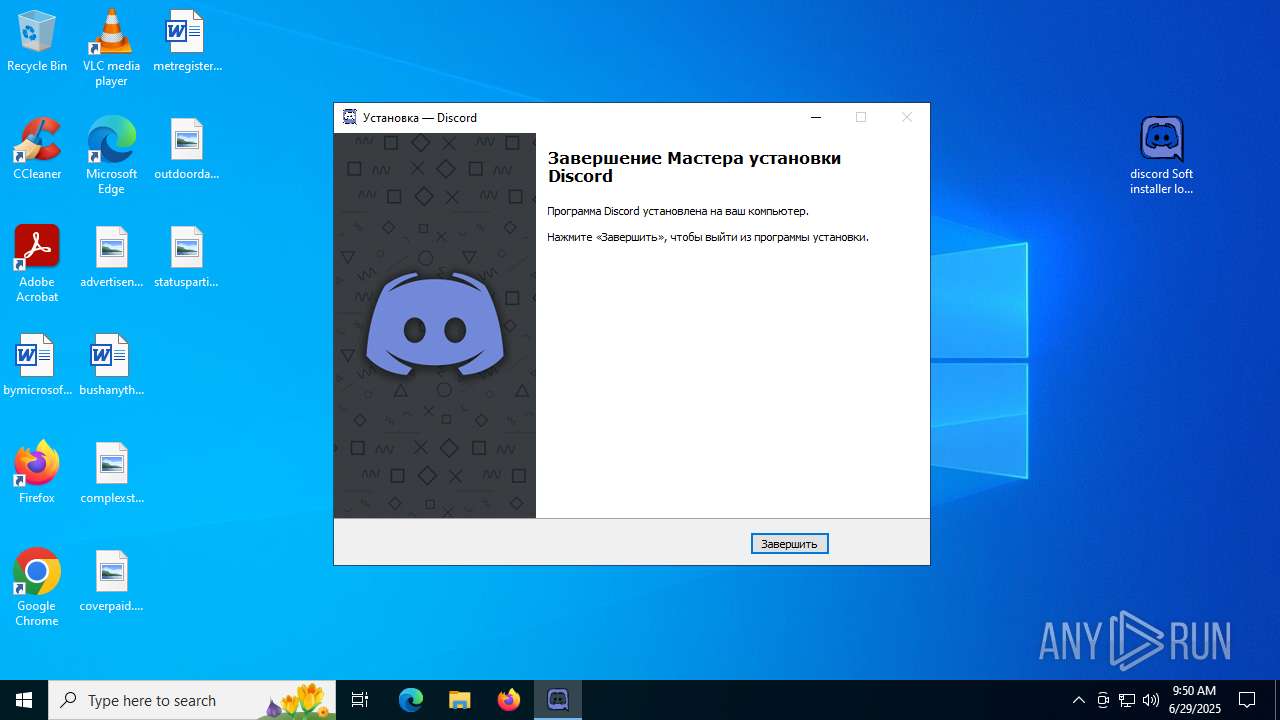
MALICIOUS
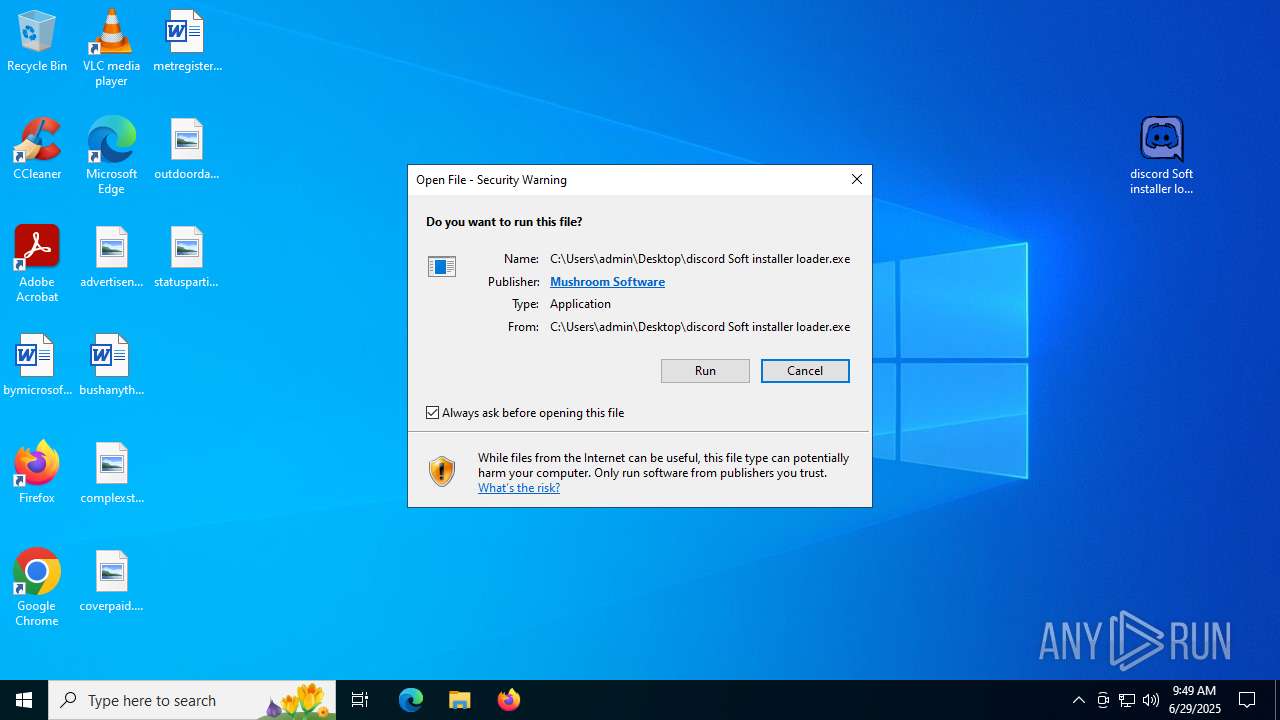
Signed with known abused certificate
- explorer.exe (PID: 4772)
Actions looks like stealing of personal data
- discord Soft installer loader.tmp (PID: 7636)
- Discord.exe (PID: 7432)
- seederexe.exe (PID: 4804)
- lite_installer.exe (PID: 7276)
- setup.exe (PID: 3900)
- csrss.exe (PID: 608)
- explorer.exe (PID: 9356)
- opera.exe (PID: 7812)
- clidmgr.exe (PID: 9260)
- csrss.exe (PID: 524)
- browser.exe (PID: 9264)
- browser.exe (PID: 9280)
- clidmgr.exe (PID: 7228)
- browser.exe (PID: 9408)
- browser.exe (PID: 3908)
- browser.exe (PID: 9860)
- browser.exe (PID: 10236)
- browser.exe (PID: 8200)
- browser.exe (PID: 8880)
- browser.exe (PID: 9224)
- browser.exe (PID: 10132)
- browser.exe (PID: 6516)
- browser.exe (PID: 7972)
- browser.exe (PID: 8868)
- browser.exe (PID: 1704)
- browser.exe (PID: 5900)
- browser.exe (PID: 8436)
- browser.exe (PID: 10028)
- browser.exe (PID: 3880)
- browser.exe (PID: 1828)
- browser.exe (PID: 9428)
- browser.exe (PID: 7592)
- browser.exe (PID: 5168)
- browser.exe (PID: 7152)
- browser.exe (PID: 3676)
- browser.exe (PID: 8340)
- browser.exe (PID: 9928)
- browser.exe (PID: 8356)
- browser.exe (PID: 9912)
- browser.exe (PID: 9240)
- browser.exe (PID: 8892)
- browser.exe (PID: 8348)
- browser.exe (PID: 9924)
- browser.exe (PID: 7628)
- browser.exe (PID: 10500)
- browser.exe (PID: 10832)
- browser.exe (PID: 10812)
- 360TS_Setup.exe (PID: 7368)
- browser.exe (PID: 8464)
- browser.exe (PID: 10132)
- browser.exe (PID: 11236)
- browser.exe (PID: 6368)
- browser.exe (PID: 8120)
- browser.exe (PID: 7940)
- browser.exe (PID: 10116)
- browser.exe (PID: 6408)
- browser.exe (PID: 10016)
- browser.exe (PID: 10556)
- browser.exe (PID: 7296)
- browser.exe (PID: 10608)
- browser.exe (PID: 10184)
- browser.exe (PID: 10472)
- browser.exe (PID: 10048)
- browser.exe (PID: 6068)
- browser.exe (PID: 10260)
- browser.exe (PID: 10216)
- regsvr32.exe (PID: 11128)
- PowerSaver.exe (PID: 10412)
- WscReg.exe (PID: 10940)
- EaInstHelper64.exe (PID: 10816)
- WscReg.exe (PID: 10552)
- QHActiveDefense.exe (PID: 10924)
- QHActiveDefense.exe (PID: 7640)
- QHSafeTray.exe (PID: 1044)
- PopWndLog.exe (PID: 10548)
- QHSafeTray.exe (PID: 2520)
- regsvr32.exe (PID: 10440)
- QHSafeTray.exe (PID: 2124)
- PopWndLog.exe (PID: 8096)
- KB931125-rootsupd.exe (PID: 5480)
- regsvr32.exe (PID: 2228)
- regsvr32.exe (PID: 592)
- WscReg.exe (PID: 2312)
- WscReg.exe (PID: 2800)
Changes the autorun value in the registry
- reg.exe (PID: 2716)
- opera.exe (PID: 7812)
- browser.exe (PID: 9264)
- 360TS_Setup.exe (PID: 7368)
- QHActiveDefense.exe (PID: 7640)
- KB931125-rootsupd.exe (PID: 5480)
Steals credentials from Web Browsers
- seederexe.exe (PID: 4804)
- opera.exe (PID: 7812)
- browser.exe (PID: 9264)
- QHSafeTray.exe (PID: 1044)
Registers / Runs the DLL via REGSVR32.EXE
- 360TS_Setup.exe (PID: 7368)
- QHSafeTray.exe (PID: 1044)
- QHActiveDefense.exe (PID: 7640)
Executing a file with an untrusted certificate
- PowerSaver.exe (PID: 10412)
- EaInstHelper64.exe (PID: 10816)
- QHWatchdog.exe (PID: 8964)
- QHWatchdog.exe (PID: 4808)
- KB931125-rootsupd.exe (PID: 5480)
SUSPICIOUS
Creates file in the systems drive root
- explorer.exe (PID: 4772)
- 360TS_Setup.exe (PID: 7368)
Executable content was dropped or overwritten
- discord Soft installer loader.exe (PID: 7628)
- discord Soft installer loader.tmp (PID: 7636)
- DiscordSetup.exe (PID: 7184)
- Update.exe (PID: 2792)
- 53a5c74467f51164e58d1ffcc590ecae.exe (PID: 4676)
- 7ad0ee4323e7d6b7a02706659c036335.exe (PID: 6408)
- setup.exe (PID: 8144)
- setup.exe (PID: 4764)
- setup.exe (PID: 2388)
- setup.exe (PID: 4808)
- setup.exe (PID: 5900)
- Yandex.exe (PID: 620)
- lite_installer.exe (PID: 7276)
- yb9BDD.tmp (PID: 7360)
- Opera_GX_assistant_73.0.3856.382_Setup.exe_sfx.exe (PID: 4560)
- installer.exe (PID: 7200)
- installer.exe (PID: 3632)
- setup.exe (PID: 3900)
- installer.exe (PID: 8888)
- installer.exe (PID: 9376)
- 360TS_Setup.exe (PID: 8420)
- installer.exe (PID: 9436)
- opera_autoupdate.exe (PID: 3936)
- 360TS_Setup.exe (PID: 7368)
- browser.exe (PID: 10500)
- browser.exe (PID: 10260)
- opera.exe (PID: 8516)
- EaInstHelper64.exe (PID: 10816)
- QHActiveDefense.exe (PID: 10924)
- KB931125-rootsupd.exe (PID: 5480)
- QHActiveDefense.exe (PID: 7640)
- opera.exe (PID: 892)
Reads the Windows owner or organization settings
- discord Soft installer loader.tmp (PID: 7636)
- msiexec.exe (PID: 5992)
Reads security settings of Internet Explorer
- discord Soft installer loader.tmp (PID: 7636)
- 7ad0ee4323e7d6b7a02706659c036335.exe (PID: 6408)
- setup.exe (PID: 8144)
- {9F4D9FA3-9C18-478F-9AEE-EAA9FFFA9101}.exe (PID: 7172)
- lite_installer.exe (PID: 7276)
- Yandex.exe (PID: 620)
- explorer.exe (PID: 7460)
- setup.exe (PID: 3900)
- installer.exe (PID: 7200)
- explorer.exe (PID: 9356)
- 360TS_Setup.exe (PID: 7368)
- QHSafeTray.exe (PID: 1044)
- PopWndLog.exe (PID: 10548)
- PopWndLog.exe (PID: 8096)
- QHActiveDefense.exe (PID: 7640)
Process drops legitimate windows executable
- Update.exe (PID: 2792)
- discord Soft installer loader.tmp (PID: 7636)
- 360TS_Setup.exe (PID: 7368)
- KB931125-rootsupd.exe (PID: 5480)
Application launched itself
- Discord.exe (PID: 7432)
- setup.exe (PID: 8144)
- setup.exe (PID: 4808)
- explorer.exe (PID: 4772)
- assistant_installer.exe (PID: 7500)
- setup.exe (PID: 3900)
- installer.exe (PID: 7200)
- opera.exe (PID: 7812)
- installer.exe (PID: 8888)
- explorer.exe (PID: 9356)
- opera_autoupdate.exe (PID: 9388)
- opera_autoupdate.exe (PID: 3936)
- browser.exe (PID: 9264)
- browser.exe (PID: 10812)
- browser.exe (PID: 8120)
- browser.exe (PID: 10016)
- QHSafeTray.exe (PID: 1044)
- PopWndLog.exe (PID: 10548)
Uses REG/REGEDIT.EXE to modify registry
- Discord.exe (PID: 7432)
Starts a Microsoft application from unusual location
- 0add47bac3d7721ac14e80627c09b41c.exe (PID: 8152)
- updroots.exe (PID: 4104)
- updroots.exe (PID: 6004)
- updroots.exe (PID: 1712)
- updroots.exe (PID: 7172)
Creates a software uninstall entry
- Update.exe (PID: 2792)
- Yandex.exe (PID: 620)
- installer.exe (PID: 7200)
- setup.exe (PID: 3900)
- 360TS_Setup.exe (PID: 7368)
Searches for installed software
- Update.exe (PID: 2792)
- installer.exe (PID: 7200)
- setup.exe (PID: 3900)
- 360TS_Setup.exe (PID: 7368)
- QHSafeTray.exe (PID: 1044)
Starts itself from another location
- setup.exe (PID: 8144)
- Yandex.exe (PID: 620)
- setup.exe (PID: 3900)
- 360TS_Setup.exe (PID: 8420)
Process requests binary or script from the Internet
- 7ad0ee4323e7d6b7a02706659c036335.exe (PID: 6408)
- lite_installer.exe (PID: 7276)
- 360TS_Setup.exe (PID: 7368)
Potential Corporate Privacy Violation
- 7ad0ee4323e7d6b7a02706659c036335.exe (PID: 6408)
- lite_installer.exe (PID: 7276)
Reads Mozilla Firefox installation path
- seederexe.exe (PID: 4804)
- opera.exe (PID: 7812)
- browser.exe (PID: 9264)
Changes the Home page of Internet Explorer
- seederexe.exe (PID: 4804)
Changes the title of the Internet Explorer window
- seederexe.exe (PID: 4804)
The process creates files with name similar to system file names
- Yandex.exe (PID: 620)
- setup.exe (PID: 3900)
Starts application with an unusual extension
- {9F4D9FA3-9C18-478F-9AEE-EAA9FFFA9101}.exe (PID: 7172)
There is functionality for taking screenshot (YARA)
- setup.exe (PID: 8144)
- setup.exe (PID: 4764)
Reads the date of Windows installation
- installer.exe (PID: 7200)
- opera.exe (PID: 7812)
- explorer.exe (PID: 9356)
The process executes via Task Scheduler
- opera_autoupdate.exe (PID: 3936)
The process checks if it is being run in the virtual environment
- opera.exe (PID: 7812)
- browser.exe (PID: 9264)
- browser.exe (PID: 10016)
- browser.exe (PID: 8120)
The process verifies whether the antivirus software is installed
- 360TS_Setup.exe (PID: 7368)
- regsvr32.exe (PID: 11128)
- PowerSaver.exe (PID: 10412)
- csrss.exe (PID: 608)
- EaInstHelper64.exe (PID: 10816)
- WscReg.exe (PID: 10552)
- WscReg.exe (PID: 10940)
- QHActiveDefense.exe (PID: 7640)
- QHActiveDefense.exe (PID: 10924)
- csrss.exe (PID: 524)
- QHSafeTray.exe (PID: 1044)
- QHWatchdog.exe (PID: 8964)
- explorer.exe (PID: 4772)
- QHSafeTray.exe (PID: 2520)
- PopWndLog.exe (PID: 10548)
- regsvr32.exe (PID: 10440)
- QHSafeTray.exe (PID: 2124)
- PopWndLog.exe (PID: 8096)
- KB931125-rootsupd.exe (PID: 5480)
- regsvr32.exe (PID: 2228)
- regsvr32.exe (PID: 592)
- WscReg.exe (PID: 2800)
- WscReg.exe (PID: 2312)
Drops 7-zip archiver for unpacking
- 360TS_Setup.exe (PID: 7368)
Drops a system driver (possible attempt to evade defenses)
- 360TS_Setup.exe (PID: 7368)
- EaInstHelper64.exe (PID: 10816)
- QHActiveDefense.exe (PID: 10924)
- QHActiveDefense.exe (PID: 7640)
Creates files in the driver directory
- 360TS_Setup.exe (PID: 7368)
- EaInstHelper64.exe (PID: 10816)
- QHActiveDefense.exe (PID: 10924)
- QHActiveDefense.exe (PID: 7640)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 11128)
Adds/modifies Windows certificates
- PowerSaver.exe (PID: 10412)
- WscReg.exe (PID: 10940)
- updroots.exe (PID: 4104)
- updroots.exe (PID: 7172)
- updroots.exe (PID: 6004)
Creates or modifies Windows services
- 360TS_Setup.exe (PID: 7368)
- QHActiveDefense.exe (PID: 10924)
- EaInstHelper64.exe (PID: 10816)
- QHActiveDefense.exe (PID: 7640)
Executes as Windows Service
- WscReg.exe (PID: 10940)
- QHActiveDefense.exe (PID: 7640)
- WscReg.exe (PID: 2312)
Zapya greyware has been detected
- QHActiveDefense.exe (PID: 7640)
Connects to the server without a host name
- QHSafeTray.exe (PID: 1044)
INFO
Executable content was dropped or overwritten
- msedge.exe (PID: 2780)
- msiexec.exe (PID: 5992)
- msiexec.exe (PID: 5188)
Reads Environment values
- identity_helper.exe (PID: 7524)
- identity_helper.exe (PID: 8140)
- Discord.exe (PID: 7432)
- identity_helper.exe (PID: 6764)
- QHSafeTray.exe (PID: 1044)
- QHActiveDefense.exe (PID: 7640)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4772)
- explorer.exe (PID: 7280)
- explorer.exe (PID: 7256)
Reads the computer name
- identity_helper.exe (PID: 7524)
- identity_helper.exe (PID: 8140)
- discord Soft installer loader.tmp (PID: 7636)
- Discord.exe (PID: 7432)
- Update.exe (PID: 2792)
- Discord.exe (PID: 6732)
- Discord.exe (PID: 7420)
- Update.exe (PID: 7276)
- 0add47bac3d7721ac14e80627c09b41c.exe (PID: 8152)
- 7ad0ee4323e7d6b7a02706659c036335.exe (PID: 6408)
- setup.exe (PID: 8144)
- msiexec.exe (PID: 5992)
- setup.exe (PID: 4808)
- msiexec.exe (PID: 5188)
- lite_installer.exe (PID: 7276)
- seederexe.exe (PID: 4804)
- {9F4D9FA3-9C18-478F-9AEE-EAA9FFFA9101}.exe (PID: 7172)
- Yandex.exe (PID: 620)
- sender.exe (PID: 7252)
- explorer.exe (PID: 7460)
- assistant_installer.exe (PID: 7500)
- identity_helper.exe (PID: 6764)
- yb9BDD.tmp (PID: 7360)
- setup.exe (PID: 3900)
- installer.exe (PID: 7200)
- opera.exe (PID: 7812)
- opera.exe (PID: 7792)
- opera.exe (PID: 3940)
- opera_gx_splash.exe (PID: 7940)
- opera.exe (PID: 8528)
- installer.exe (PID: 8888)
- opera_autoupdate.exe (PID: 9388)
- explorer.exe (PID: 9356)
- opera_autoupdate.exe (PID: 3936)
- clidmgr.exe (PID: 7228)
- clidmgr.exe (PID: 9260)
- browser.exe (PID: 9264)
- browser.exe (PID: 3908)
- browser.exe (PID: 6516)
- browser.exe (PID: 9224)
- browser.exe (PID: 8200)
- browser.exe (PID: 10236)
- 360TS_Setup.exe (PID: 8420)
- 360TS_Setup.exe (PID: 7368)
- browser.exe (PID: 9428)
- browser.exe (PID: 10812)
- browser.exe (PID: 8120)
- browser.exe (PID: 10116)
- browser.exe (PID: 7940)
- browser.exe (PID: 6408)
- browser.exe (PID: 8464)
- browser.exe (PID: 7296)
- browser.exe (PID: 10016)
- browser.exe (PID: 10608)
- opera.exe (PID: 9344)
- browser.exe (PID: 10556)
- browser.exe (PID: 10216)
- EaInstHelper64.exe (PID: 10816)
- WscReg.exe (PID: 10940)
- WscReg.exe (PID: 10552)
- QHActiveDefense.exe (PID: 10924)
- QHActiveDefense.exe (PID: 7640)
- QHSafeTray.exe (PID: 1044)
- QHSafeTray.exe (PID: 2520)
- PopWndLog.exe (PID: 10548)
- QHSafeTray.exe (PID: 2124)
- PopWndLog.exe (PID: 8096)
- WscReg.exe (PID: 2312)
- WscReg.exe (PID: 2800)
Checks supported languages
- identity_helper.exe (PID: 7524)
- identity_helper.exe (PID: 8140)
- discord Soft installer loader.exe (PID: 7628)
- discord Soft installer loader.tmp (PID: 7636)
- DiscordSetup.exe (PID: 7184)
- Discord.exe (PID: 7432)
- Update.exe (PID: 2792)
- Discord.exe (PID: 7232)
- Update.exe (PID: 7276)
- Discord.exe (PID: 6732)
- Discord.exe (PID: 7420)
- 7ad0ee4323e7d6b7a02706659c036335.exe (PID: 6408)
- 0add47bac3d7721ac14e80627c09b41c.exe (PID: 8152)
- setup.exe (PID: 8144)
- 53a5c74467f51164e58d1ffcc590ecae.exe (PID: 4676)
- setup.exe (PID: 4764)
- 4342ac23942469b1de84b111f8b2a58f.exe (PID: 7516)
- msiexec.exe (PID: 5992)
- setup.exe (PID: 2388)
- 4342ac23942469b1de84b111f8b2a58f.exe (PID: 1652)
- setup.exe (PID: 5900)
- setup.exe (PID: 4808)
- msiexec.exe (PID: 5188)
- seederexe.exe (PID: 4804)
- lite_installer.exe (PID: 7276)
- {9F4D9FA3-9C18-478F-9AEE-EAA9FFFA9101}.exe (PID: 7172)
- Yandex.exe (PID: 620)
- explorer.exe (PID: 7460)
- sender.exe (PID: 7252)
- Opera_GX_assistant_73.0.3856.382_Setup.exe_sfx.exe (PID: 4560)
- assistant_installer.exe (PID: 7500)
- assistant_installer.exe (PID: 2356)
- identity_helper.exe (PID: 6764)
- yb9BDD.tmp (PID: 7360)
- setup.exe (PID: 3900)
- setup.exe (PID: 1932)
- installer.exe (PID: 7200)
- opera.exe (PID: 7812)
- opera_crashreporter.exe (PID: 7712)
- opera.exe (PID: 3940)
- installer.exe (PID: 3632)
- opera.exe (PID: 7792)
- opera.exe (PID: 2716)
- opera.exe (PID: 7916)
- opera.exe (PID: 6836)
- opera.exe (PID: 6668)
- opera.exe (PID: 2388)
- opera_gx_splash.exe (PID: 7940)
- opera.exe (PID: 480)
- opera.exe (PID: 3580)
- opera.exe (PID: 4264)
- opera.exe (PID: 3620)
- opera.exe (PID: 7660)
- opera.exe (PID: 5500)
- opera.exe (PID: 7768)
- opera.exe (PID: 6360)
- opera.exe (PID: 536)
- opera.exe (PID: 436)
- opera.exe (PID: 8156)
- opera.exe (PID: 8372)
- opera.exe (PID: 1068)
- opera.exe (PID: 8388)
- opera.exe (PID: 8396)
- opera.exe (PID: 3624)
- opera.exe (PID: 4864)
- opera.exe (PID: 6548)
- opera.exe (PID: 8412)
- opera.exe (PID: 8380)
- opera.exe (PID: 8528)
- opera.exe (PID: 8428)
- opera.exe (PID: 8452)
- opera.exe (PID: 8472)
- opera.exe (PID: 8480)
- opera.exe (PID: 9204)
- opera.exe (PID: 8444)
- opera.exe (PID: 8420)
- opera.exe (PID: 8436)
- opera.exe (PID: 8464)
- opera.exe (PID: 8404)
- opera.exe (PID: 8648)
- installer.exe (PID: 8888)
- opera.exe (PID: 8564)
- opera.exe (PID: 1660)
- opera.exe (PID: 8360)
- opera.exe (PID: 7760)
- explorer.exe (PID: 9408)
- opera_autoupdate.exe (PID: 9424)
- installer.exe (PID: 9376)
- explorer.exe (PID: 9356)
- opera_autoupdate.exe (PID: 9388)
- opera_autoupdate.exe (PID: 9884)
- opera.exe (PID: 9972)
- opera.exe (PID: 8316)
- opera_autoupdate.exe (PID: 3936)
- clidmgr.exe (PID: 9260)
- clidmgr.exe (PID: 7228)
- browser.exe (PID: 9264)
- browser.exe (PID: 9280)
- opera.exe (PID: 8968)
- browser.exe (PID: 6516)
- browser.exe (PID: 3908)
- browser.exe (PID: 10236)
- browser.exe (PID: 9860)
- browser.exe (PID: 8200)
- browser.exe (PID: 9408)
- browser.exe (PID: 8880)
- browser.exe (PID: 9224)
- browser.exe (PID: 10132)
- browser.exe (PID: 7972)
- browser.exe (PID: 8868)
- browser.exe (PID: 1704)
- browser.exe (PID: 5900)
- browser.exe (PID: 3880)
- browser.exe (PID: 8436)
- browser.exe (PID: 10028)
- browser.exe (PID: 1828)
- installer.exe (PID: 9436)
- 360TS_Setup.exe (PID: 8420)
- opera.exe (PID: 8296)
- 360TS_Setup.exe (PID: 7368)
- opera.exe (PID: 1268)
- opera.exe (PID: 9224)
- opera.exe (PID: 9232)
- browser.exe (PID: 7592)
- browser.exe (PID: 5168)
- browser.exe (PID: 8340)
- browser.exe (PID: 7152)
- browser.exe (PID: 3676)
- browser.exe (PID: 9928)
- browser.exe (PID: 8348)
- browser.exe (PID: 9428)
- browser.exe (PID: 8892)
- browser.exe (PID: 9924)
- browser.exe (PID: 8356)
- browser.exe (PID: 9240)
- opera.exe (PID: 8800)
- opera.exe (PID: 8492)
- opera.exe (PID: 9916)
- opera.exe (PID: 9896)
- browser.exe (PID: 7628)
- browser.exe (PID: 9912)
- opera.exe (PID: 6936)
- opera.exe (PID: 9224)
- opera.exe (PID: 10272)
- opera.exe (PID: 10264)
- browser.exe (PID: 10500)
- opera.exe (PID: 10456)
- opera.exe (PID: 10544)
- opera.exe (PID: 8724)
- opera.exe (PID: 3568)
- opera.exe (PID: 6352)
- opera.exe (PID: 10340)
- opera.exe (PID: 10420)
- browser.exe (PID: 10832)
- opera.exe (PID: 10552)
- opera.exe (PID: 10732)
- opera.exe (PID: 10636)
- browser.exe (PID: 10812)
- opera.exe (PID: 10972)
- opera.exe (PID: 11176)
- opera.exe (PID: 11044)
- browser.exe (PID: 6408)
- browser.exe (PID: 11236)
- browser.exe (PID: 8120)
- browser.exe (PID: 6368)
- browser.exe (PID: 8464)
- browser.exe (PID: 10132)
- browser.exe (PID: 10116)
- browser.exe (PID: 7940)
- browser.exe (PID: 7296)
- browser.exe (PID: 10556)
- browser.exe (PID: 10016)
- browser.exe (PID: 10608)
- opera.exe (PID: 3704)
- opera.exe (PID: 9344)
- browser.exe (PID: 10184)
- opera.exe (PID: 9320)
- browser.exe (PID: 10048)
- browser.exe (PID: 10472)
- browser.exe (PID: 10216)
- browser.exe (PID: 10260)
- opera.exe (PID: 8516)
- browser.exe (PID: 6068)
- PowerSaver.exe (PID: 10412)
- WscReg.exe (PID: 10940)
- EaInstHelper64.exe (PID: 10816)
- WscReg.exe (PID: 10552)
- QHActiveDefense.exe (PID: 10924)
- QHActiveDefense.exe (PID: 7640)
- QHWatchdog.exe (PID: 8964)
- QHSafeTray.exe (PID: 1044)
- PopWndLog.exe (PID: 10548)
- QHSafeTray.exe (PID: 2520)
- QHWatchdog.exe (PID: 4808)
- QHSafeTray.exe (PID: 2124)
- PopWndLog.exe (PID: 8096)
- KB931125-rootsupd.exe (PID: 5480)
- updroots.exe (PID: 4104)
- updroots.exe (PID: 6004)
- updroots.exe (PID: 1712)
- updroots.exe (PID: 7172)
- WscReg.exe (PID: 2800)
- opera.exe (PID: 892)
- WscReg.exe (PID: 2312)
Application launched itself
- msedge.exe (PID: 2780)
- msedge.exe (PID: 7176)
- msedge.exe (PID: 7656)
Checks proxy server information
- explorer.exe (PID: 4772)
- discord Soft installer loader.tmp (PID: 7636)
- Discord.exe (PID: 7432)
- 7ad0ee4323e7d6b7a02706659c036335.exe (PID: 6408)
- setup.exe (PID: 8144)
- lite_installer.exe (PID: 7276)
- {9F4D9FA3-9C18-478F-9AEE-EAA9FFFA9101}.exe (PID: 7172)
- setup.exe (PID: 3900)
- slui.exe (PID: 7028)
- opera.exe (PID: 7812)
- opera_autoupdate.exe (PID: 9388)
- browser.exe (PID: 9264)
- opera_autoupdate.exe (PID: 3936)
- 360TS_Setup.exe (PID: 7368)
- browser.exe (PID: 10812)
- browser.exe (PID: 8120)
- browser.exe (PID: 10016)
- QHSafeTray.exe (PID: 1044)
Reads the software policy settings
- explorer.exe (PID: 4772)
- discord Soft installer loader.tmp (PID: 7636)
- setup.exe (PID: 8144)
- msiexec.exe (PID: 5992)
- lite_installer.exe (PID: 7276)
- {9F4D9FA3-9C18-478F-9AEE-EAA9FFFA9101}.exe (PID: 7172)
- setup.exe (PID: 3900)
- slui.exe (PID: 7028)
- explorer.exe (PID: 9356)
- browser.exe (PID: 9264)
- 360TS_Setup.exe (PID: 7368)
- browser.exe (PID: 10812)
- browser.exe (PID: 8120)
- browser.exe (PID: 10016)
Create files in a temporary directory
- discord Soft installer loader.exe (PID: 7628)
- discord Soft installer loader.tmp (PID: 7636)
- DiscordSetup.exe (PID: 7184)
- Update.exe (PID: 2792)
- 7ad0ee4323e7d6b7a02706659c036335.exe (PID: 6408)
- setup.exe (PID: 8144)
- 0add47bac3d7721ac14e80627c09b41c.exe (PID: 8152)
- 53a5c74467f51164e58d1ffcc590ecae.exe (PID: 4676)
- setup.exe (PID: 4764)
- setup.exe (PID: 2388)
- setup.exe (PID: 4808)
- setup.exe (PID: 5900)
- msiexec.exe (PID: 5188)
- lite_installer.exe (PID: 7276)
- seederexe.exe (PID: 4804)
- {9F4D9FA3-9C18-478F-9AEE-EAA9FFFA9101}.exe (PID: 7172)
- sender.exe (PID: 7252)
- Yandex.exe (PID: 620)
- Opera_GX_assistant_73.0.3856.382_Setup.exe_sfx.exe (PID: 4560)
- yb9BDD.tmp (PID: 7360)
- setup.exe (PID: 3900)
- installer.exe (PID: 7200)
- installer.exe (PID: 3632)
- opera.exe (PID: 7812)
- installer.exe (PID: 8888)
- installer.exe (PID: 9376)
- browser.exe (PID: 9224)
- browser.exe (PID: 9264)
- opera_autoupdate.exe (PID: 3936)
- installer.exe (PID: 9436)
- 360TS_Setup.exe (PID: 8420)
- 360TS_Setup.exe (PID: 7368)
- browser.exe (PID: 10812)
- KB931125-rootsupd.exe (PID: 5480)
Creates files or folders in the user directory
- explorer.exe (PID: 4772)
- Discord.exe (PID: 7432)
- Discord.exe (PID: 7232)
- discord Soft installer loader.tmp (PID: 7636)
- DiscordSetup.exe (PID: 7184)
- Update.exe (PID: 2792)
- Discord.exe (PID: 7420)
- Update.exe (PID: 7276)
- setup.exe (PID: 4764)
- 7ad0ee4323e7d6b7a02706659c036335.exe (PID: 6408)
- msiexec.exe (PID: 5992)
- setup.exe (PID: 8144)
- seederexe.exe (PID: 4804)
- msiexec.exe (PID: 5188)
- lite_installer.exe (PID: 7276)
- explorer.exe (PID: 7460)
- {9F4D9FA3-9C18-478F-9AEE-EAA9FFFA9101}.exe (PID: 7172)
- Yandex.exe (PID: 620)
- setup.exe (PID: 4808)
- setup.exe (PID: 3900)
- setup.exe (PID: 1932)
- installer.exe (PID: 7200)
- opera.exe (PID: 7812)
- opera.exe (PID: 7792)
- explorer.exe (PID: 9356)
- browser.exe (PID: 9264)
- browser.exe (PID: 6516)
- opera_autoupdate.exe (PID: 3936)
- 360TS_Setup.exe (PID: 7368)
- browser.exe (PID: 10812)
- browser.exe (PID: 10832)
- browser.exe (PID: 8120)
- browser.exe (PID: 6368)
- browser.exe (PID: 7296)
- browser.exe (PID: 10016)
- opera.exe (PID: 9344)
- browser.exe (PID: 10216)
- QHSafeTray.exe (PID: 1044)
Compiled with Borland Delphi (YARA)
- discord Soft installer loader.exe (PID: 7628)
- discord Soft installer loader.tmp (PID: 7636)
Detects InnoSetup installer (YARA)
- discord Soft installer loader.tmp (PID: 7636)
- discord Soft installer loader.exe (PID: 7628)
Process checks computer location settings
- discord Soft installer loader.tmp (PID: 7636)
- Discord.exe (PID: 7432)
- msiexec.exe (PID: 5188)
- Yandex.exe (PID: 620)
- explorer.exe (PID: 7460)
- opera.exe (PID: 7812)
- opera.exe (PID: 480)
- opera.exe (PID: 4264)
- opera.exe (PID: 436)
- opera.exe (PID: 3620)
- opera.exe (PID: 7660)
- opera.exe (PID: 6548)
- opera.exe (PID: 4864)
- opera.exe (PID: 5500)
- opera.exe (PID: 8156)
- opera.exe (PID: 1068)
- opera.exe (PID: 8480)
- opera.exe (PID: 9204)
- opera.exe (PID: 8360)
- explorer.exe (PID: 9356)
- opera.exe (PID: 9972)
- opera.exe (PID: 8316)
- opera.exe (PID: 8968)
- browser.exe (PID: 9264)
- browser.exe (PID: 10132)
- browser.exe (PID: 5900)
- browser.exe (PID: 3880)
- 7ad0ee4323e7d6b7a02706659c036335.exe (PID: 6408)
- browser.exe (PID: 7972)
- browser.exe (PID: 8436)
- browser.exe (PID: 1828)
- 360TS_Setup.exe (PID: 7368)
- opera.exe (PID: 10636)
- opera.exe (PID: 10732)
- opera.exe (PID: 10972)
- opera.exe (PID: 11176)
- opera.exe (PID: 11044)
- browser.exe (PID: 11236)
- QHSafeTray.exe (PID: 1044)
The sample compiled with english language support
- discord Soft installer loader.tmp (PID: 7636)
- Update.exe (PID: 2792)
- 53a5c74467f51164e58d1ffcc590ecae.exe (PID: 4676)
- 7ad0ee4323e7d6b7a02706659c036335.exe (PID: 6408)
- setup.exe (PID: 8144)
- setup.exe (PID: 2388)
- setup.exe (PID: 4808)
- setup.exe (PID: 5900)
- lite_installer.exe (PID: 7276)
- Opera_GX_assistant_73.0.3856.382_Setup.exe_sfx.exe (PID: 4560)
- yb9BDD.tmp (PID: 7360)
- installer.exe (PID: 7200)
- installer.exe (PID: 3632)
- setup.exe (PID: 3900)
- installer.exe (PID: 8888)
- installer.exe (PID: 9376)
- opera_autoupdate.exe (PID: 3936)
- installer.exe (PID: 9436)
- browser.exe (PID: 10500)
- 360TS_Setup.exe (PID: 7368)
- opera.exe (PID: 8516)
- QHActiveDefense.exe (PID: 10924)
- KB931125-rootsupd.exe (PID: 5480)
- opera.exe (PID: 892)
Reads the machine GUID from the registry
- Update.exe (PID: 2792)
- Discord.exe (PID: 7432)
- Update.exe (PID: 7276)
- 7ad0ee4323e7d6b7a02706659c036335.exe (PID: 6408)
- msiexec.exe (PID: 5992)
- setup.exe (PID: 8144)
- seederexe.exe (PID: 4804)
- lite_installer.exe (PID: 7276)
- {9F4D9FA3-9C18-478F-9AEE-EAA9FFFA9101}.exe (PID: 7172)
- setup.exe (PID: 3900)
- opera.exe (PID: 7812)
- opera_autoupdate.exe (PID: 9388)
- opera_autoupdate.exe (PID: 9424)
- explorer.exe (PID: 9356)
- opera_autoupdate.exe (PID: 9884)
- opera_autoupdate.exe (PID: 3936)
- browser.exe (PID: 9264)
- 360TS_Setup.exe (PID: 7368)
- opera.exe (PID: 9344)
- browser.exe (PID: 10216)
- QHActiveDefense.exe (PID: 7640)
- QHSafeTray.exe (PID: 1044)
Reads product name
- Discord.exe (PID: 7432)
Creates a software uninstall entry
- discord Soft installer loader.tmp (PID: 7636)
Launching a file from a Registry key
- reg.exe (PID: 2716)
- opera.exe (PID: 7812)
- browser.exe (PID: 9264)
- 360TS_Setup.exe (PID: 7368)
- QHActiveDefense.exe (PID: 7640)
- KB931125-rootsupd.exe (PID: 5480)
Disables trace logs
- 7ad0ee4323e7d6b7a02706659c036335.exe (PID: 6408)
- 360TS_Setup.exe (PID: 7368)
- QHSafeTray.exe (PID: 1044)
- QHActiveDefense.exe (PID: 7640)
- QHSafeTray.exe (PID: 2520)
- QHSafeTray.exe (PID: 2124)
The sample compiled with russian language support
- msiexec.exe (PID: 5188)
- setup.exe (PID: 3900)
- 360TS_Setup.exe (PID: 7368)
Yandex updater related mutex has been found
- {9F4D9FA3-9C18-478F-9AEE-EAA9FFFA9101}.exe (PID: 7172)
- browser.exe (PID: 9224)
- browser.exe (PID: 9264)
- browser.exe (PID: 10812)
- browser.exe (PID: 8120)
- browser.exe (PID: 10016)
OPERA mutex has been found
- opera.exe (PID: 7812)
- opera_autoupdate.exe (PID: 9388)
- opera_autoupdate.exe (PID: 3936)
Creates files in the program directory
- 360TS_Setup.exe (PID: 8420)
- 360TS_Setup.exe (PID: 7368)
- QHSafeTray.exe (PID: 1044)
- QHActiveDefense.exe (PID: 7640)
- PopWndLog.exe (PID: 10548)
- PopWndLog.exe (PID: 8096)
- WscReg.exe (PID: 2800)
The sample compiled with chinese language support
- 360TS_Setup.exe (PID: 8420)
- 360TS_Setup.exe (PID: 7368)
- EaInstHelper64.exe (PID: 10816)
- QHActiveDefense.exe (PID: 7640)
Reads CPU info
- browser.exe (PID: 9264)
- opera.exe (PID: 7812)
- 360TS_Setup.exe (PID: 7368)
- QHActiveDefense.exe (PID: 7640)
The sample compiled with turkish language support
- 360TS_Setup.exe (PID: 7368)
Process checks whether UAC notifications are on
- 360TS_Setup.exe (PID: 7368)
- QHActiveDefense.exe (PID: 7640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
437
Monitored processes
291
Malicious processes
99
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 436 | "C:\Users\admin\AppData\Local\Programs\Opera GX\opera.exe" --type=renderer --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36 OPR/119.0.0.0 (Edition std-2)" --no-pre-read-main-dll --start-stack-profiler --with-feature:cashback-assistant=on --with-feature:address-bar-dropdown-autocompleted-domains=on --with-feature:address-bar-dropdown-cities=off --with-feature:address-bar-dropdown-keyword-ads=on --with-feature:address-bar-dropdown-unfiltered-full=off --with-feature:ai-writing-mode-in-context-menu=on --with-feature:aria-in-tab-view=on --with-feature:cashback-assistant=on --with-feature:certificate-transparency-enforcement=on --with-feature:continue-on-booking=on --with-feature:continue-on-shopping-via-amp=off --with-feature:continue-shopping=on --with-feature:continue-shopping-2=on --with-feature:continue-shopping-amazon-us-associates=off --with-feature:continue-shopping-explore=off --with-feature:continue-shopping-structured-partners=on --with-feature:feature-remote-disable-updates-testing-flag=off --with-feature:feature-remote-updates-testing-flag=on --with-feature:game-servers=off --with-feature:gx-april1st=off --with-feature:gx-post-mortem=on --with-feature:gx-reactinator=on --with-feature:gx-spotlight=on --with-feature:gx-video-to-phone=on --with-feature:hide-navigations-from-extensions=on --with-feature:panic-button=on --with-feature:play-again=on --with-feature:realtime-impressions-reporting=on --with-feature:run-at-startup-default=on --with-feature:sd-suggestions-external=on --with-feature:side-profiles=on --with-feature:sitecheck-age=on --with-feature:suggestion-redirect-handler=on --with-feature:tiktok-panel=on --with-feature:ui-compositor-multithreaded=on --with-feature:vpn-pro-v4-support=on --with-feature:installer-experiment-test=off --ab_tests=GXCTest50-test:DNA-99214_GXCTest50 --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --field-trial-handle=1972,i,2261254874343359812,1028667121888538661,262144 --enable-features=CertificateTransparencyAskBeforeEnabling --disable-features=PlatformSoftwareH264EncoderInGpu,UpdatableKeyPins --variations-seed-version --mojo-platform-channel-handle=4592 /prefetch:1 | C:\Users\admin\AppData\Local\Programs\Opera GX\opera.exe | — | opera.exe | |||||||||||
User: admin Company: Opera Software Integrity Level: LOW Description: Opera GX Internet Browser Version: 119.0.5497.144 Modules
| |||||||||||||||
| 480 | "C:\Users\admin\AppData\Local\Programs\Opera GX\opera.exe" --type=renderer --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36 OPR/119.0.0.0 (Edition std-2)" --no-pre-read-main-dll --with-feature:cashback-assistant=on --with-feature:address-bar-dropdown-autocompleted-domains=on --with-feature:address-bar-dropdown-cities=off --with-feature:address-bar-dropdown-keyword-ads=on --with-feature:address-bar-dropdown-unfiltered-full=off --with-feature:ai-writing-mode-in-context-menu=on --with-feature:aria-in-tab-view=on --with-feature:cashback-assistant=on --with-feature:certificate-transparency-enforcement=on --with-feature:continue-on-booking=on --with-feature:continue-on-shopping-via-amp=off --with-feature:continue-shopping=on --with-feature:continue-shopping-2=on --with-feature:continue-shopping-amazon-us-associates=off --with-feature:continue-shopping-explore=off --with-feature:continue-shopping-structured-partners=on --with-feature:feature-remote-disable-updates-testing-flag=off --with-feature:feature-remote-updates-testing-flag=on --with-feature:game-servers=off --with-feature:gx-april1st=off --with-feature:gx-post-mortem=on --with-feature:gx-reactinator=on --with-feature:gx-spotlight=on --with-feature:gx-video-to-phone=on --with-feature:hide-navigations-from-extensions=on --with-feature:panic-button=on --with-feature:play-again=on --with-feature:realtime-impressions-reporting=on --with-feature:run-at-startup-default=on --with-feature:sd-suggestions-external=on --with-feature:side-profiles=on --with-feature:sitecheck-age=on --with-feature:suggestion-redirect-handler=on --with-feature:tiktok-panel=on --with-feature:ui-compositor-multithreaded=on --with-feature:vpn-pro-v4-support=on --with-feature:installer-experiment-test=off --ab_tests=GXCTest50-test:DNA-99214_GXCTest50 --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --field-trial-handle=1972,i,2261254874343359812,1028667121888538661,262144 --enable-features=CertificateTransparencyAskBeforeEnabling --disable-features=PlatformSoftwareH264EncoderInGpu,UpdatableKeyPins --variations-seed-version --mojo-platform-channel-handle=3852 /prefetch:1 | C:\Users\admin\AppData\Local\Programs\Opera GX\opera.exe | — | opera.exe | |||||||||||
User: admin Company: Opera Software Integrity Level: LOW Description: Opera GX Internet Browser Exit code: 0 Version: 119.0.5497.144 Modules
| |||||||||||||||
| 524 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 536 | "C:\Users\admin\AppData\Local\Programs\Opera GX\opera.exe" --type=utility --utility-sub-type=opera.lights.mojom.LightsProvider --lang=en-US --service-sandbox-type=none --enable-quic --logitech-lights-process --no-pre-read-main-dll --with-feature:cashback-assistant=on --with-feature:address-bar-dropdown-autocompleted-domains=on --with-feature:address-bar-dropdown-cities=off --with-feature:address-bar-dropdown-keyword-ads=on --with-feature:address-bar-dropdown-unfiltered-full=off --with-feature:ai-writing-mode-in-context-menu=on --with-feature:aria-in-tab-view=on --with-feature:cashback-assistant=on --with-feature:certificate-transparency-enforcement=on --with-feature:continue-on-booking=on --with-feature:continue-on-shopping-via-amp=off --with-feature:continue-shopping=on --with-feature:continue-shopping-2=on --with-feature:continue-shopping-amazon-us-associates=off --with-feature:continue-shopping-explore=off --with-feature:continue-shopping-structured-partners=on --with-feature:feature-remote-disable-updates-testing-flag=off --with-feature:feature-remote-updates-testing-flag=on --with-feature:game-servers=off --with-feature:gx-april1st=off --with-feature:gx-post-mortem=on --with-feature:gx-reactinator=on --with-feature:gx-spotlight=on --with-feature:gx-video-to-phone=on --with-feature:hide-navigations-from-extensions=on --with-feature:panic-button=on --with-feature:play-again=on --with-feature:realtime-impressions-reporting=on --with-feature:run-at-startup-default=on --with-feature:sd-suggestions-external=on --with-feature:side-profiles=on --with-feature:sitecheck-age=on --with-feature:suggestion-redirect-handler=on --with-feature:tiktok-panel=on --with-feature:ui-compositor-multithreaded=on --with-feature:vpn-pro-v4-support=on --with-feature:installer-experiment-test=off --ab_tests=GXCTest50-test:DNA-99214_GXCTest50 --field-trial-handle=1972,i,2261254874343359812,1028667121888538661,262144 --enable-features=CertificateTransparencyAskBeforeEnabling --disable-features=PlatformSoftwareH264EncoderInGpu,UpdatableKeyPins --variations-seed-version --mojo-platform-channel-handle=5404 /prefetch:8 | C:\Users\admin\AppData\Local\Programs\Opera GX\opera.exe | — | opera.exe | |||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera GX Internet Browser Exit code: 0 Version: 119.0.5497.144 Modules
| |||||||||||||||
| 592 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files (x86)\360\Total Security\safemon\bdfltlib.dll" | C:\Windows\SysWOW64\regsvr32.exe | QHActiveDefense.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 608 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 620 | C:\Users\admin\AppData\Local\Yandex\YaPin\Yandex.exe --silent --pin-taskbar=y --pin-desktop=n | C:\Users\admin\AppData\Local\Yandex\YaPin\Yandex.exe | seederexe.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: YandexPin Exit code: 0 Version: 3.7.9.0 Modules
| |||||||||||||||
| 892 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --pdf-upsell-enabled --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3256,i,18366704426409401434,15799497848186704033,262144 --variations-seed-version --mojo-platform-channel-handle=3808 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 892 | "C:\Users\admin\AppData\Local\Programs\Opera GX\opera.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --enable-quic --no-pre-read-main-dll --with-feature:cashback-assistant=on --with-feature:address-bar-dropdown-autocompleted-domains=on --with-feature:address-bar-dropdown-cities=off --with-feature:address-bar-dropdown-keyword-ads=on --with-feature:address-bar-dropdown-unfiltered-full=off --with-feature:ai-writing-mode-in-context-menu=on --with-feature:aria-in-tab-view=on --with-feature:cashback-assistant=on --with-feature:certificate-transparency-enforcement=on --with-feature:continue-on-booking=on --with-feature:continue-on-shopping-via-amp=off --with-feature:continue-shopping=on --with-feature:continue-shopping-2=on --with-feature:continue-shopping-amazon-us-associates=off --with-feature:continue-shopping-explore=off --with-feature:continue-shopping-structured-partners=on --with-feature:feature-remote-disable-updates-testing-flag=off --with-feature:feature-remote-updates-testing-flag=on --with-feature:game-servers=off --with-feature:gx-april1st=off --with-feature:gx-post-mortem=on --with-feature:gx-reactinator=on --with-feature:gx-spotlight=on --with-feature:gx-video-to-phone=on --with-feature:hide-navigations-from-extensions=on --with-feature:panic-button=on --with-feature:play-again=on --with-feature:realtime-impressions-reporting=on --with-feature:run-at-startup-default=on --with-feature:sd-suggestions-external=on --with-feature:side-profiles=on --with-feature:sitecheck-age=on --with-feature:suggestion-redirect-handler=on --with-feature:tiktok-panel=on --with-feature:ui-compositor-multithreaded=on --with-feature:vpn-pro-v4-support=on --with-feature:installer-experiment-test=off --ab_tests=GXCTest50-test:DNA-99214_GXCTest50 --field-trial-handle=1972,i,2261254874343359812,1028667121888538661,262144 --enable-features=CertificateTransparencyAskBeforeEnabling --disable-features=PlatformSoftwareH264EncoderInGpu,UpdatableKeyPins --variations-seed-version --mojo-platform-channel-handle=10056 /prefetch:8 | C:\Users\admin\AppData\Local\Programs\Opera GX\opera.exe | opera.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: LOW Description: Opera GX Internet Browser Exit code: 0 Version: 119.0.5497.144 Modules
| |||||||||||||||
| 1044 | /showtrayicon | C:\Program Files (x86)\360\Total Security\safemon\QHSafeTray.exe | QHActiveDefense.exe | ||||||||||||
User: admin Company: Qihoo 360 Technology Co. Ltd. Integrity Level: HIGH Description: 360 Total Security Version: 10,0,0,1860 Modules
| |||||||||||||||
Total events
134 477
Read events
130 955
Write events
2 705
Delete events
817
Modification events
| (PID) Process: | (2780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2780) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: D25C7E1A49972F00 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000080272 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (2780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\524914 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {D688CCE7-C24C-4463-8334-3998D5980FFC} | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000050312 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (2780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\524914 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {08E2B6BC-E374-4F48-A100-97BAC5C04790} | |||
| (PID) Process: | (2780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\524914 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {6B356E0B-FED8-4E44-A2D2-422CE250A643} | |||
Executable files
1 390
Suspicious files
2 799
Text files
1 369
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF175aa3.TMP | — | |
MD5:— | SHA256:— | |||
| 2780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF175af1.TMP | — | |
MD5:— | SHA256:— | |||
| 2780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF175af1.TMP | — | |
MD5:— | SHA256:— | |||
| 2780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF175b01.TMP | — | |
MD5:— | SHA256:— | |||
| 2780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF175b01.TMP | — | |
MD5:— | SHA256:— | |||
| 2780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
140
TCP/UDP connections
413
DNS requests
358
Threats
39
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3392 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:rdVQ-XUZIuFFn13cl54Cfe79ljucKhbnPztSr58rsT8&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2552 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5060 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5060 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4772 | explorer.exe | GET | 200 | 18.173.205.43:80 | http://ocsps.ssl.com/MEkwRzBFMEMwQTAJBgUrDgMCGgUABBQMDtATfnJO6JAXDQoHl8pAaJdhTQQU3QQJB6L1en1SUxKSle44gCUNplkCCGQzUdPHOJ8I | unknown | — | — | whitelisted |
4772 | explorer.exe | GET | 200 | 18.173.205.43:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSOf8DjMnuwFThpZh9bv9IoPvmNMAQUVML%2BEJUAk81q9efA19myS7iPDOMCECqUZOyGzVdH%2B97SMTMe6dk%3D | unknown | — | — | whitelisted |
6408 | 7ad0ee4323e7d6b7a02706659c036335.exe | GET | 200 | 54.255.136.181:80 | http://s.360safe.com/safei18n/query_env.htm?v611=DgY0MAEI90Wu5wABAAB4Jw3oOs%2BcuxG0BFeCtOk7Ajjg3WZjlMJSbpbAdoZnadNJJkR6RIDtUqukzW7xLRU6bkz7e7jNQ2Tg2cYQdWMVS65lgmVpM8ZJdEjXXHoscoZLY3OCYvCzRVX6BVkhWZP47U3Ihazn9jYiHYx0HgSYOQLWAQH9FfVfmM%2BmtIRN8FkWi0qCgbmusHXA0EZ2gcx7hUwUo8Qq%2For2ukVsvX%2FGC0dNl7fvLWF0%2F7CThV3RRABp6dhRo5SH8ul7N%2BNBsAL3VkurTuYUjonnDPR3XjVniNe32WD5if%2FiFMUFKdoiLpzGcciyQ%2FcPNsAhAQKsT3RjqX%2FUTyQqT99B1bzgISGcntqZmVNNHn3pAF64Ph6%2BRzkEQpkVa2XB12yi15a3nKcGm6lxDz%2Fo7yRMP7SxU5R7gqCprBnuBXlLI36RZYiVczSt%2BXtPoYUnOA3tzXRmkeBPutujSRqYVuzQaeeRM5x7ayE7jcWhzaMdOICozPQeVl2%2FyOTLMws3gG8f7okPQFs%3D | unknown | — | — | whitelisted |
6408 | 7ad0ee4323e7d6b7a02706659c036335.exe | GET | 200 | 54.255.136.181:80 | http://s.360safe.com/360ts/mini_inst.htm?ver=6.6.0.1054&pid=RU.Omgm.CPI202204&os=10.0&mid=80342cb959da2233832ae840f019ccba&state=153 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6936 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3392 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3392 | msedge.exe | 150.171.28.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3392 | msedge.exe | 85.209.70.13:443 | discord.softbeachcamp.com | Docker LTD | RU | unknown |
3392 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3392 | msedge.exe | 92.123.104.45:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
discord.softbeachcamp.com |
| unknown |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
mc.yandex.ru |
| whitelisted |
xpaywalletcdn.azureedge.net |
| whitelisted |
mc.yandex.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
— | — | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
6408 | 7ad0ee4323e7d6b7a02706659c036335.exe | Misc activity | ET INFO Packed Executable Download |
6408 | 7ad0ee4323e7d6b7a02706659c036335.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7276 | lite_installer.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
7276 | lite_installer.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
7580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
7580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
7580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
Process | Message |
|---|---|
DiscordSetup.exe | Elevated process: ?
|
DiscordSetup.exe | Want standard install |
DiscordSetup.exe | Start up installer: -s |
0add47bac3d7721ac14e80627c09b41c.exe | IsMSISrvFree() In |
0add47bac3d7721ac14e80627c09b41c.exe | IsMSISrvFree() : OpenMutex() err ret = 2
|
0add47bac3d7721ac14e80627c09b41c.exe | IsAlreadyRun() Out : ret (BOOL) = 0
|
0add47bac3d7721ac14e80627c09b41c.exe | IsMSISrvFree() Out ret = 1
|
0add47bac3d7721ac14e80627c09b41c.exe | IsAlreadyRun() In
|
0add47bac3d7721ac14e80627c09b41c.exe | GetLoggedCreds_WTSSessionInfo(): szUserName = admin, szDomain = DESKTOP-JGLLJLD, dwSessionId = 1
|
0add47bac3d7721ac14e80627c09b41c.exe | GetSidFromEnumSess(): LsaEnumerateLogonSessions() lpszSid = S-1-5-21-1693682860-607145093-2874071422-1001
|