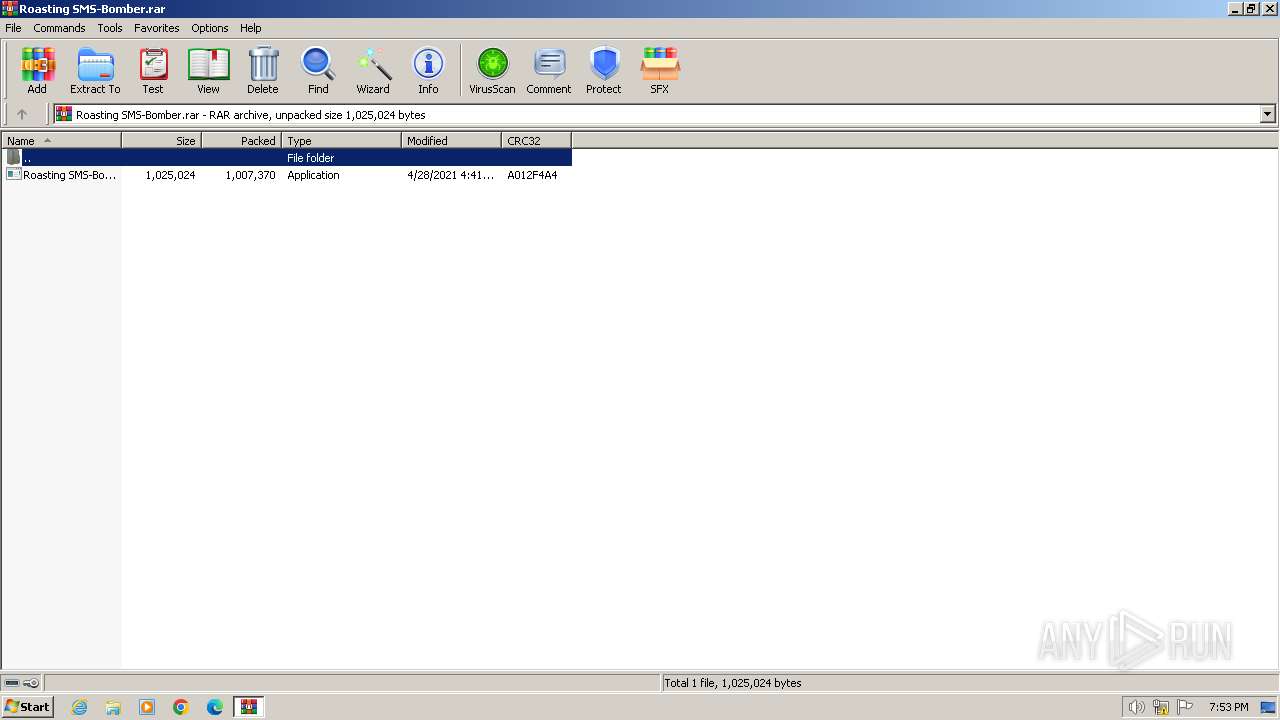
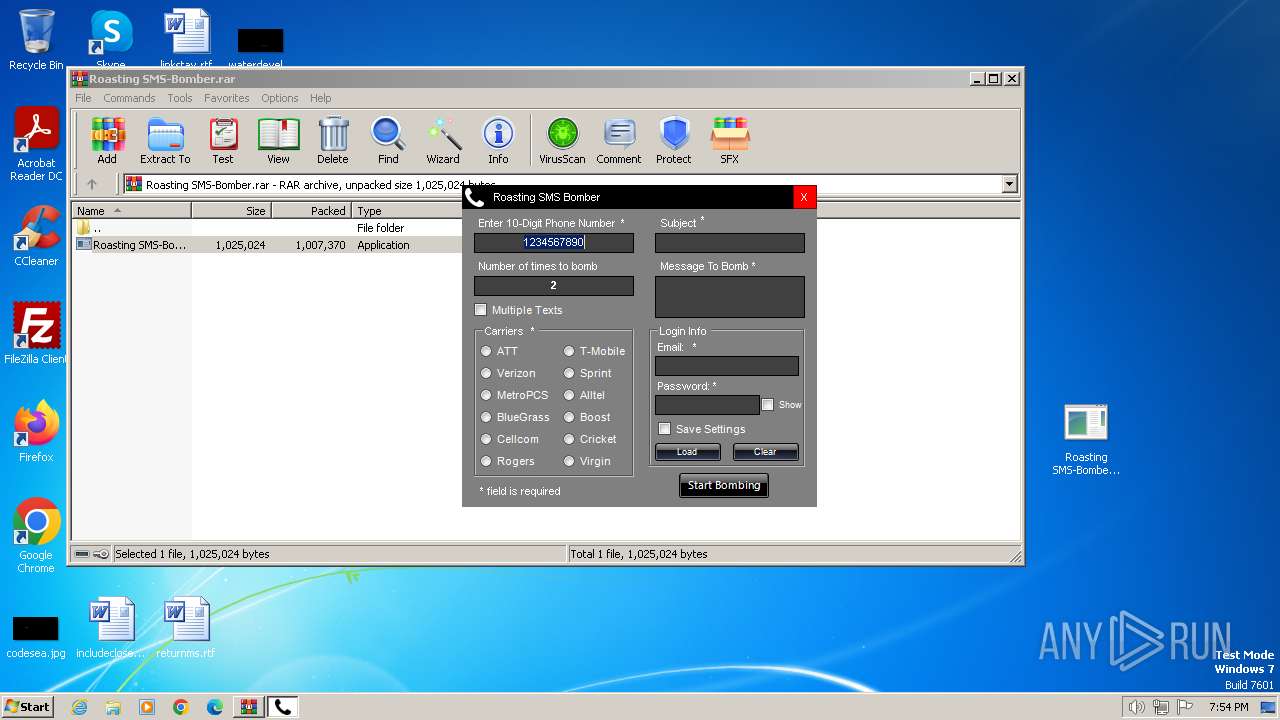
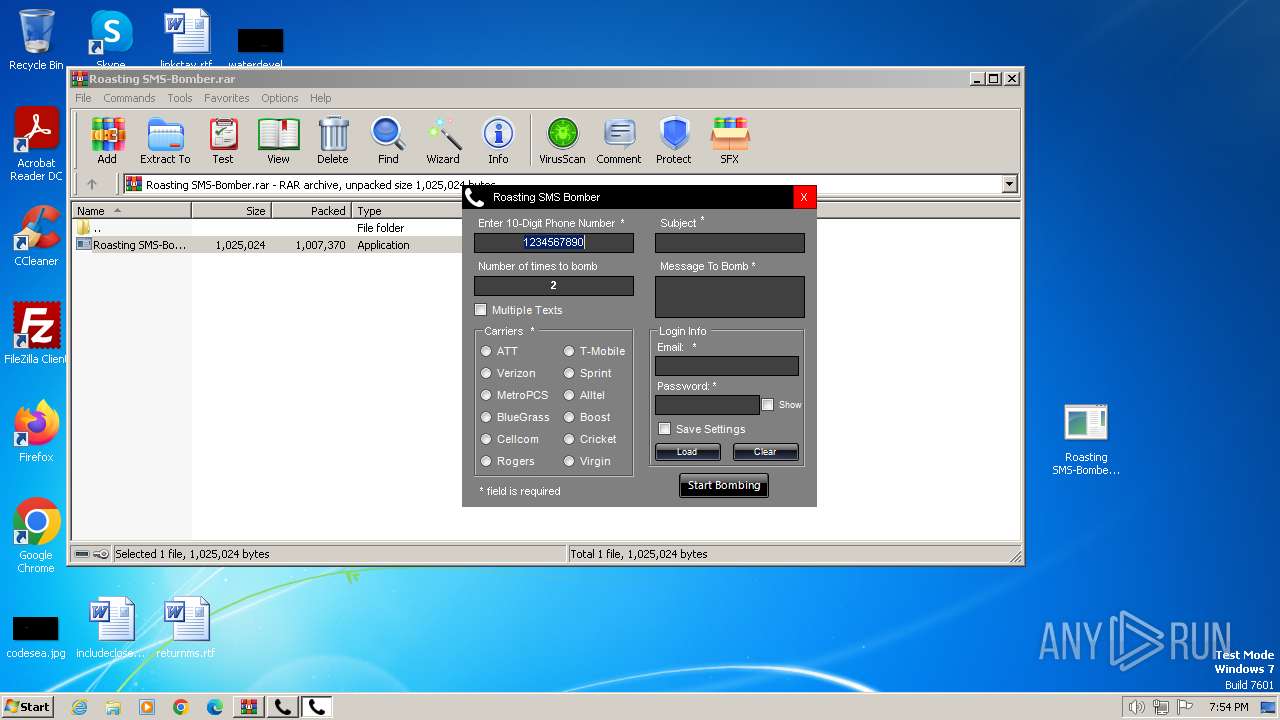
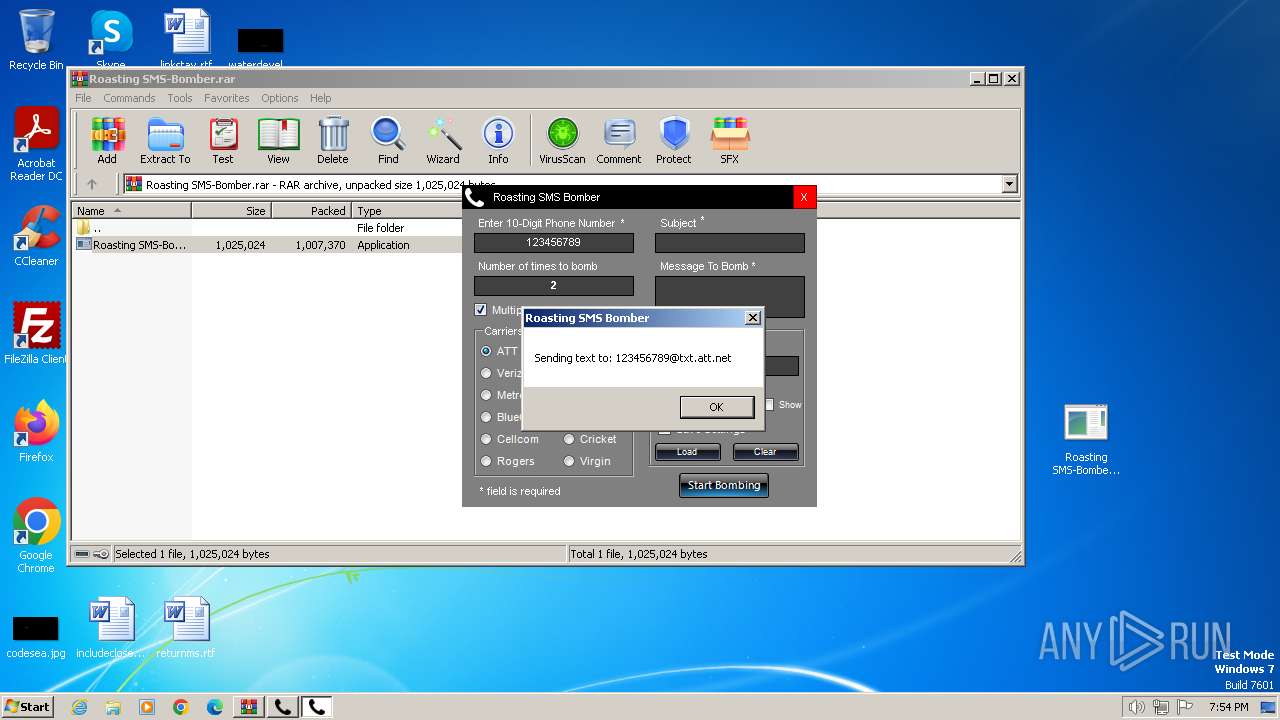
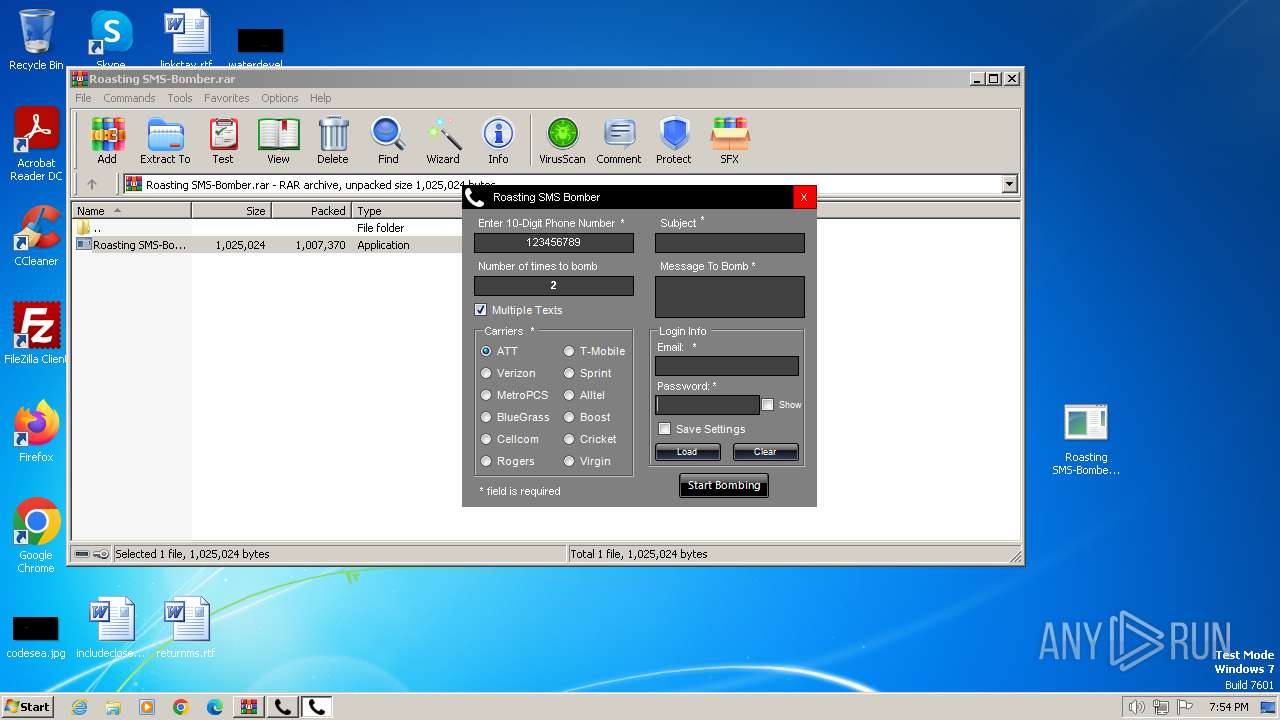
| File name: | Roasting SMS-Bomber.rar |
| Full analysis: | https://app.any.run/tasks/b7f2768b-6a2c-41b1-923e-2114c6dbb1c2 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | September 15, 2024, 18:53:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 5E8A54BF7EDED100232D20B008D76BFC |
| SHA1: | D1067AC8D59392A6C00D3867610DAEB8D01DDC4D |
| SHA256: | BEDA7F7DF375C7A6A5494615DDEB6548D1E11D280DC923B4CB5056D5725B13ED |
| SSDEEP: | 49152:HFRZYImHLVA4uOvT920QYtALSKwWP0tLEm7FuLMu3G3qMc4TkBwlqjpFcoAyetvM:nZYImHLuOvtQYkSKwWP0KeFuwu6DcskJ |
MALICIOUS
ASYNCRAT has been detected (MUTEX)
- WQ6bQ7VhNNErOoCKy913cOLHZWwNqxs35Sr.exe (PID: 3604)
- xsfCrhxFpoZ9p8VmQlUZCpmfBxPpJPLZcuK.exe (PID: 3284)
ASYNCRAT has been detected (YARA)
- WQ6bQ7VhNNErOoCKy913cOLHZWwNqxs35Sr.exe (PID: 3604)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 536)
Executable content was dropped or overwritten
- Roasting SMS-Bomber.exe (PID: 2204)
- Roasting SMS-Bomber.exe (PID: 3504)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 536)
Checks supported languages
- WQ6bQ7VhNNErOoCKy913cOLHZWwNqxs35Sr.exe (PID: 3604)
- Roasting SMS-Bomber.exe (PID: 2204)
- wmpnscfg.exe (PID: 3248)
- Roasting SMS-Bomber.exe (PID: 3504)
- uD85k1PnFCqSdeciQJQ0I7YcgWzJ4qUXvUZ.exe (PID: 3740)
- xsfCrhxFpoZ9p8VmQlUZCpmfBxPpJPLZcuK.exe (PID: 3284)
- Rcnh8ZvKgaNyF54HwowXml2461WofN0CS0D.exe (PID: 3500)
Reads the computer name
- WQ6bQ7VhNNErOoCKy913cOLHZWwNqxs35Sr.exe (PID: 3604)
- Roasting SMS-Bomber.exe (PID: 2204)
- wmpnscfg.exe (PID: 3248)
- Roasting SMS-Bomber.exe (PID: 3504)
- xsfCrhxFpoZ9p8VmQlUZCpmfBxPpJPLZcuK.exe (PID: 3284)
- Rcnh8ZvKgaNyF54HwowXml2461WofN0CS0D.exe (PID: 3500)
- uD85k1PnFCqSdeciQJQ0I7YcgWzJ4qUXvUZ.exe (PID: 3740)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 536)
Reads the machine GUID from the registry
- Roasting SMS-Bomber.exe (PID: 2204)
- WQ6bQ7VhNNErOoCKy913cOLHZWwNqxs35Sr.exe (PID: 3604)
- Roasting SMS-Bomber.exe (PID: 3504)
- Rcnh8ZvKgaNyF54HwowXml2461WofN0CS0D.exe (PID: 3500)
- xsfCrhxFpoZ9p8VmQlUZCpmfBxPpJPLZcuK.exe (PID: 3284)
- uD85k1PnFCqSdeciQJQ0I7YcgWzJ4qUXvUZ.exe (PID: 3740)
Create files in a temporary directory
- Roasting SMS-Bomber.exe (PID: 2204)
- Roasting SMS-Bomber.exe (PID: 3504)
Manual execution by a user
- Roasting SMS-Bomber.exe (PID: 3504)
- wmpnscfg.exe (PID: 3248)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(3604) WQ6bQ7VhNNErOoCKy913cOLHZWwNqxs35Sr.exe
C2 (2)127.0.0.1
tcp://2.tcp.ngrok.io
Ports (7)6606
7707
8808
1236
14283
13400
4578
Version0.5.7B
BotnetDefault
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQALRZ3OimsG8i6x0iz4vUlTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjEwNDI1MjE0MDA1WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAK6ll6G7d9VrxcBktvcc7VKToRIlffWtu7l7W7I3Zo2rLxt4kNgpPwpoCKeh+8epHR+xpcM1otjv...
Server_SignatureJWeWl3k5uE1SVD7TwFXQMVzSfvWH11rbCJUyLYlDgNl2EEFCSMuWMGLhdY3PuMH4bWzOT2MknBwqzvJxcfy9cEXHcLOUHOsFXDkGZjtukQDu7CZR+313SmfW/tVEMNNFSXX5EqoDWxrsxhvGWH7MyOQz3wDVtB8S4ya6W9JTGu7WgtpiFXO5uFqUb1on7ajIsVJqlX+905dbxYJ09vza+3YF1cWI70+Iot389QhfnGrEGJRQ2b6NC5CW5HxpA/uhBZxlYaOcfM0Cq2F26sVF2CHmrb9MAKtUrbL5MK7giSqL...
Keys
AES3f7104e74f590bff4b13587ff840c7366f086410f0281bd8a357ae9f590c6452
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
44
Monitored processes
8
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Roasting SMS-Bomber.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2204 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa536.24579\Roasting SMS-Bomber.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa536.24579\Roasting SMS-Bomber.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Stub Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3248 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3284 | C:\Users\admin\AppData\Local\Temp\xsfCrhxFpoZ9p8VmQlUZCpmfBxPpJPLZcuK.exe | C:\Users\admin\AppData\Local\Temp\xsfCrhxFpoZ9p8VmQlUZCpmfBxPpJPLZcuK.exe | Roasting SMS-Bomber.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3500 | C:\Users\admin\AppData\Local\Temp\Rcnh8ZvKgaNyF54HwowXml2461WofN0CS0D.exe | C:\Users\admin\AppData\Local\Temp\Rcnh8ZvKgaNyF54HwowXml2461WofN0CS0D.exe | — | Roasting SMS-Bomber.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Roasting SMS Bomber Version: 1.0.0.0 Modules
| |||||||||||||||
| 3504 | "C:\Users\admin\Desktop\Roasting SMS-Bomber.exe" | C:\Users\admin\Desktop\Roasting SMS-Bomber.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Stub Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3604 | C:\Users\admin\AppData\Local\Temp\WQ6bQ7VhNNErOoCKy913cOLHZWwNqxs35Sr.exe | C:\Users\admin\AppData\Local\Temp\WQ6bQ7VhNNErOoCKy913cOLHZWwNqxs35Sr.exe | Roasting SMS-Bomber.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
AsyncRat(PID) Process(3604) WQ6bQ7VhNNErOoCKy913cOLHZWwNqxs35Sr.exe C2 (2)127.0.0.1 tcp://2.tcp.ngrok.io Ports (7)6606 7707 8808 1236 14283 13400 4578 Version0.5.7B BotnetDefault Options AutoRunfalse MutexAsyncMutex_6SI8OkPnk InstallFolder%AppData% BSoDfalse AntiVMfalse Certificates Cert1MIIE8jCCAtqgAwIBAgIQALRZ3OimsG8i6x0iz4vUlTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjEwNDI1MjE0MDA1WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAK6ll6G7d9VrxcBktvcc7VKToRIlffWtu7l7W7I3Zo2rLxt4kNgpPwpoCKeh+8epHR+xpcM1otjv... Server_SignatureJWeWl3k5uE1SVD7TwFXQMVzSfvWH11rbCJUyLYlDgNl2EEFCSMuWMGLhdY3PuMH4bWzOT2MknBwqzvJxcfy9cEXHcLOUHOsFXDkGZjtukQDu7CZR+313SmfW/tVEMNNFSXX5EqoDWxrsxhvGWH7MyOQz3wDVtB8S4ya6W9JTGu7WgtpiFXO5uFqUb1on7ajIsVJqlX+905dbxYJ09vza+3YF1cWI70+Iot389QhfnGrEGJRQ2b6NC5CW5HxpA/uhBZxlYaOcfM0Cq2F26sVF2CHmrb9MAKtUrbL5MK7giSqL... Keys AES3f7104e74f590bff4b13587ff840c7366f086410f0281bd8a357ae9f590c6452 Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 3740 | C:\Users\admin\AppData\Local\Temp\uD85k1PnFCqSdeciQJQ0I7YcgWzJ4qUXvUZ.exe | C:\Users\admin\AppData\Local\Temp\uD85k1PnFCqSdeciQJQ0I7YcgWzJ4qUXvUZ.exe | — | Roasting SMS-Bomber.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Roasting SMS Bomber Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
2 134
Read events
2 087
Write events
47
Delete events
0
Modification events
| (PID) Process: | (536) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (536) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (536) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (536) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (536) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (536) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (536) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Roasting SMS-Bomber.rar | |||
| (PID) Process: | (536) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (536) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (536) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
6
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2204 | Roasting SMS-Bomber.exe | C:\Users\admin\AppData\Local\Temp\WQ6bQ7VhNNErOoCKy913cOLHZWwNqxs35Sr.exe | executable | |
MD5:BB82C303884B453D4FED9AED1FD1E898 | SHA256:AB14FEA139D44455BF9F09FE5846DA061FCCFAF1FC20BBBB9767FD8311CF97AC | |||
| 536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa536.25561\Roasting SMS-Bomber.exe | executable | |
MD5:64EA5F99953958A3F97F48AA814A5862 | SHA256:CE6A10E20D43A0876FB0BA72A62A46145C687442A0B2A07A6968CFF448364D8B | |||
| 536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa536.24579\Roasting SMS-Bomber.exe | executable | |
MD5:64EA5F99953958A3F97F48AA814A5862 | SHA256:CE6A10E20D43A0876FB0BA72A62A46145C687442A0B2A07A6968CFF448364D8B | |||
| 2204 | Roasting SMS-Bomber.exe | C:\Users\admin\AppData\Local\Temp\Rcnh8ZvKgaNyF54HwowXml2461WofN0CS0D.exe | executable | |
MD5:5E3F29A17E47E14C3373F8A6905320ED | SHA256:15206AD4075821EB73AFE5DAC6788BC16590434D623B8423120B7B925F94B4DA | |||
| 3504 | Roasting SMS-Bomber.exe | C:\Users\admin\AppData\Local\Temp\xsfCrhxFpoZ9p8VmQlUZCpmfBxPpJPLZcuK.exe | executable | |
MD5:BB82C303884B453D4FED9AED1FD1E898 | SHA256:AB14FEA139D44455BF9F09FE5846DA061FCCFAF1FC20BBBB9767FD8311CF97AC | |||
| 3504 | Roasting SMS-Bomber.exe | C:\Users\admin\AppData\Local\Temp\uD85k1PnFCqSdeciQJQ0I7YcgWzJ4qUXvUZ.exe | executable | |
MD5:5E3F29A17E47E14C3373F8A6905320ED | SHA256:15206AD4075821EB73AFE5DAC6788BC16590434D623B8423120B7B925F94B4DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
10
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?11acddbe1ebd82b3 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1372 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1372 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1060 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |