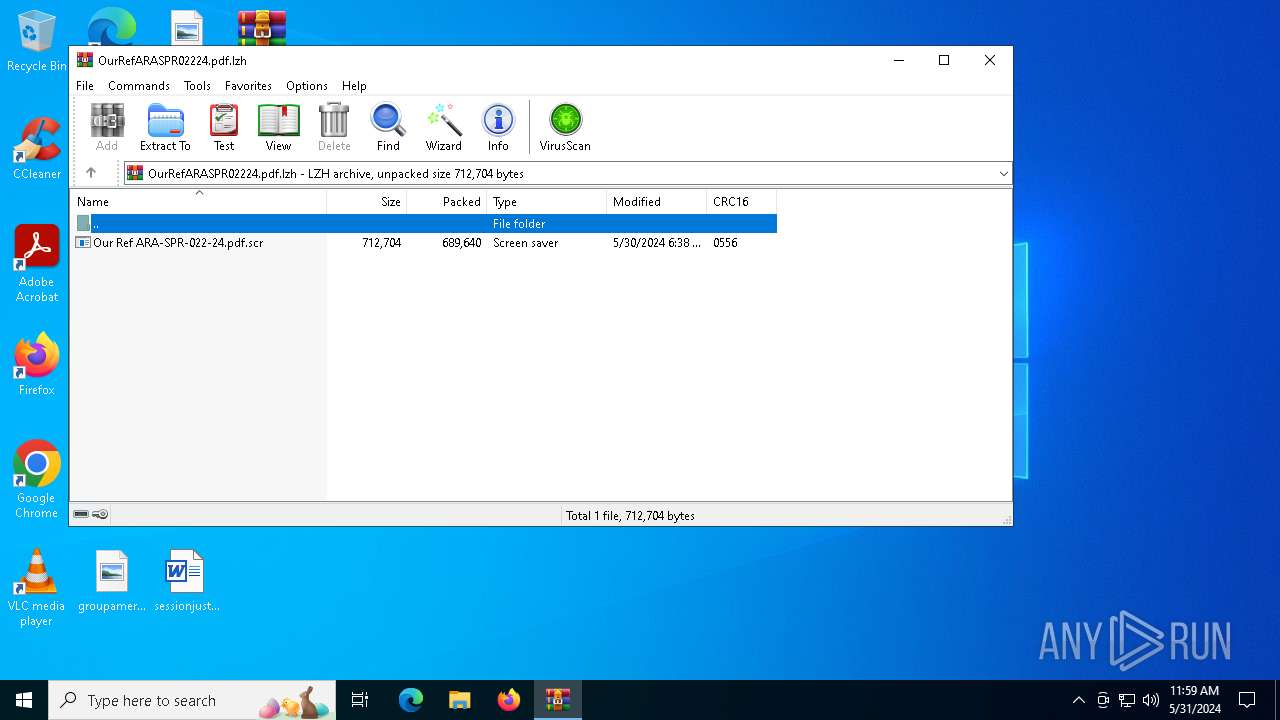
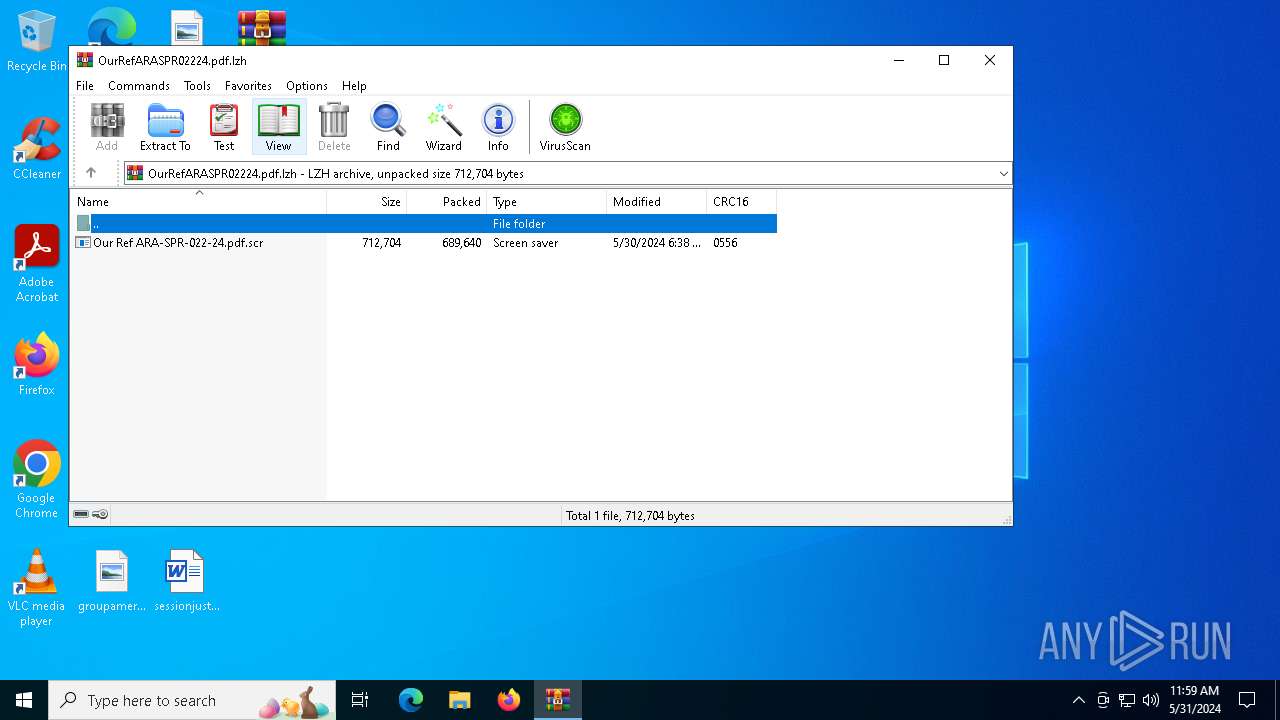
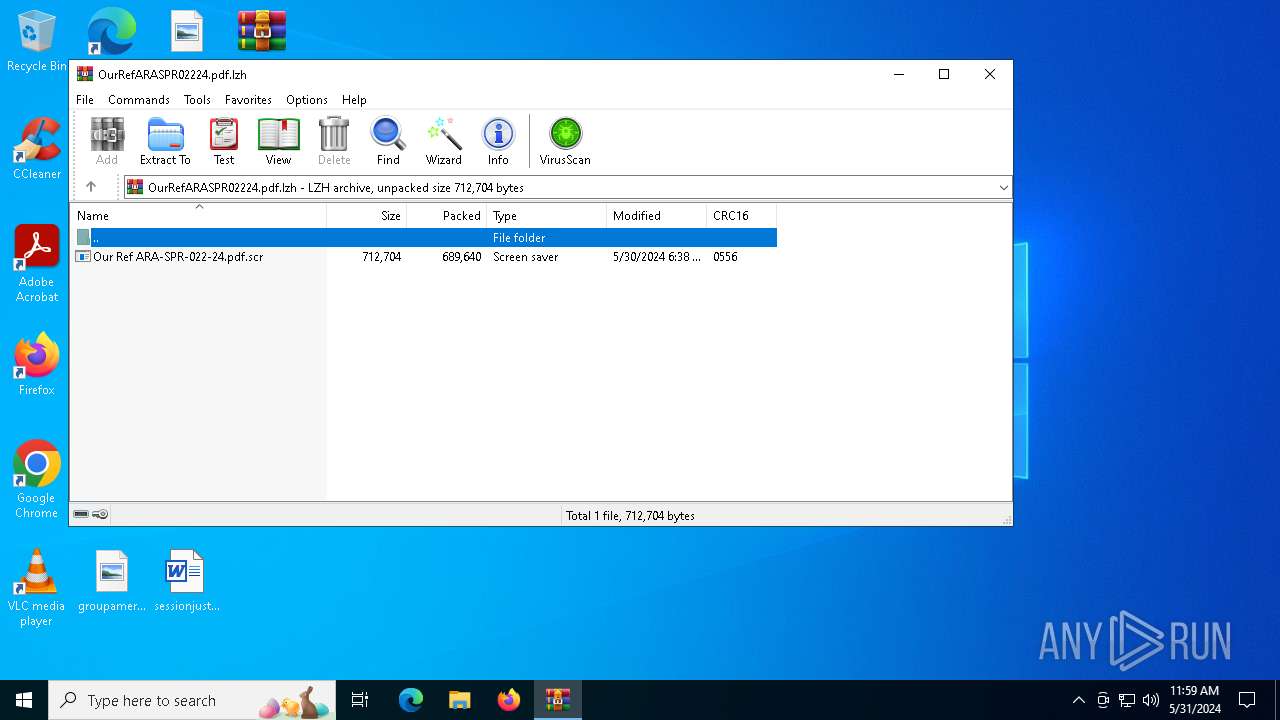
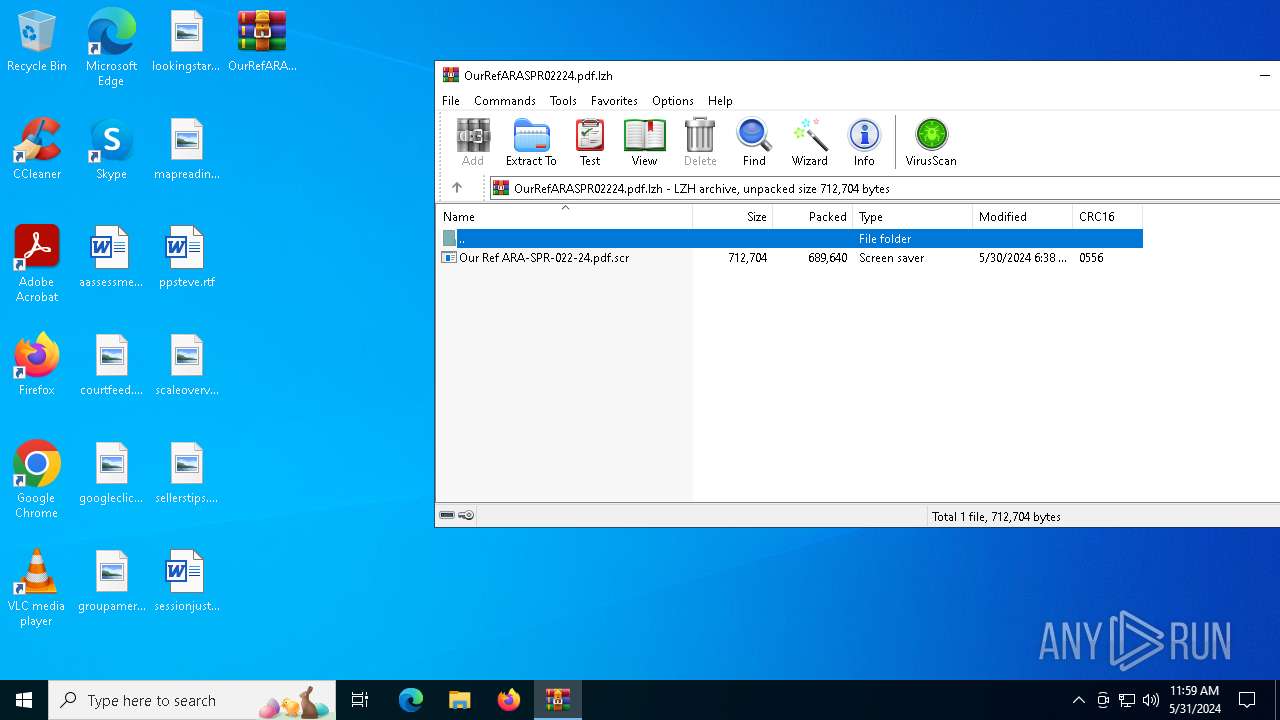
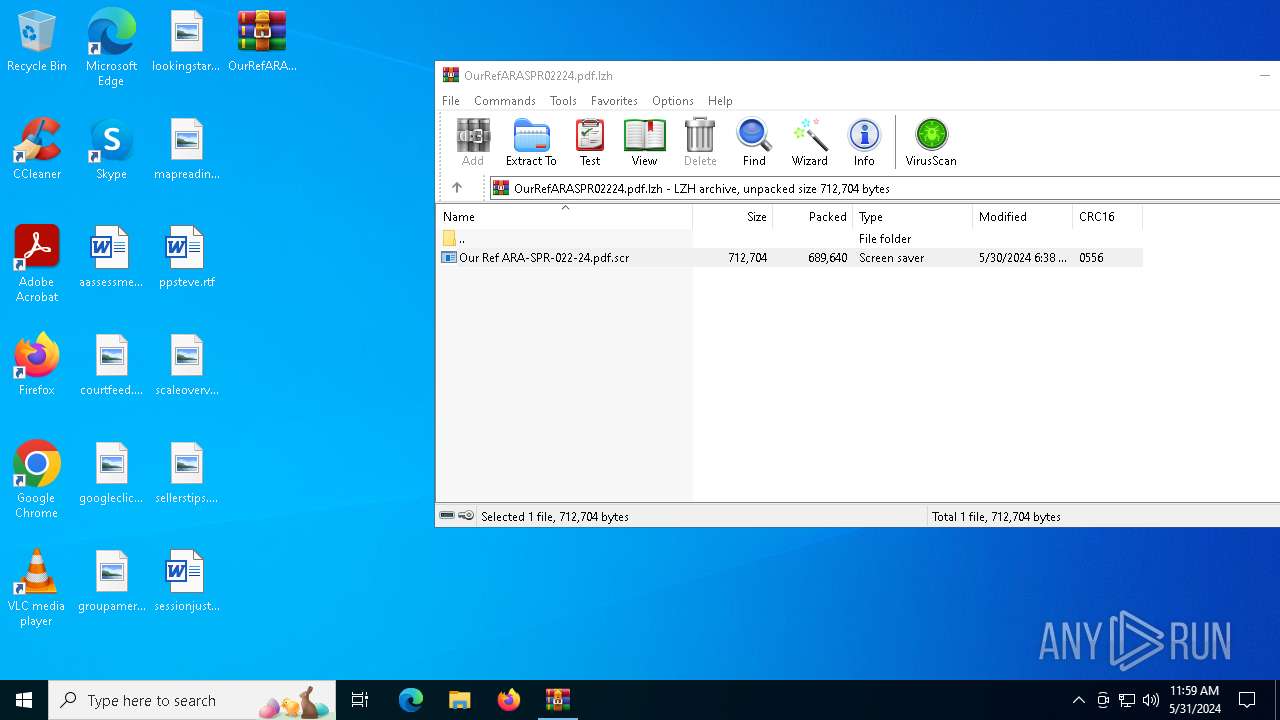
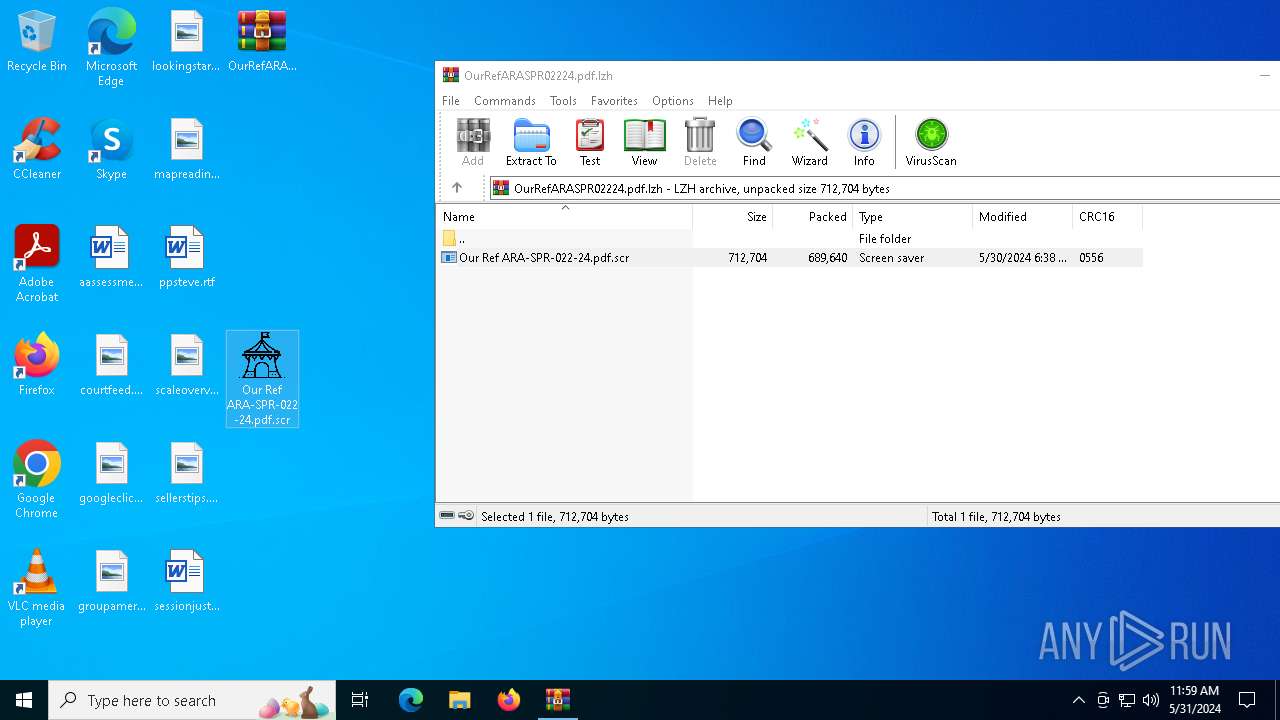
| File name: | OurRefARASPR02224.pdf.lzh |
| Full analysis: | https://app.any.run/tasks/b8593e70-1f5d-479c-a49a-3ab80717320d |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 31, 2024, 11:59:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-lzh-compressed |
| File info: | LHa (2.x) archive data [lh5], with "Our Ref ARA-SPR-022-24.pdf.scr" |
| MD5: | 85302F092DA9AD3EBA6E477111BEBF99 |
| SHA1: | C8507BDE9C09799A71607AC5055BD4F4F730695C |
| SHA256: | BECEB7569CC1B053B267CFB652D651179AF2D2F091087FEC9F34900818115EB5 |
| SSDEEP: | 24576:nsIX7YzM9PAia1SHtIT/lwgEkDjk24zZjt1x77BlySya0Dx/iUORjQ/k7/:nsILYzM9PAia1SHtITdwgEkDjk24zZjT |
MALICIOUS
AGENTTESLA has been detected (YARA)
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
Steals credentials from Web Browsers
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
Scans artifacts that could help determine the target
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
Actions looks like stealing of personal data
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
SUSPICIOUS
Application launched itself
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6816)
Starts application with an unusual extension
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6816)
Checks for external IP
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
Potential Corporate Privacy Violation
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
Connects to unusual port
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
Connects to FTP
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6484)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6484)
Manual execution by a user
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6816)
Reads the computer name
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6816)
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
Reads the machine GUID from the registry
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6816)
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
Reads the software policy settings
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
Checks supported languages
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6816)
Checks proxy server information
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
Reads Microsoft Office registry keys
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
Reads Environment values
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
Disables trace logs
- Our Ref ARA-SPR-022-24.pdf.scr (PID: 6976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lzh/lha | | | LHARC/LZARK compressed archive (generic) (100) |
|---|
Total processes
118
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6484 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\OurRefARASPR02224.pdf.lzh | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6816 | "C:\Users\admin\Desktop\Our Ref ARA-SPR-022-24.pdf.scr" /S | C:\Users\admin\Desktop\Our Ref ARA-SPR-022-24.pdf.scr | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 6976 | "C:\Users\admin\Desktop\Our Ref ARA-SPR-022-24.pdf.scr" | C:\Users\admin\Desktop\Our Ref ARA-SPR-022-24.pdf.scr | Our Ref ARA-SPR-022-24.pdf.scr | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
7 761
Read events
7 726
Write events
35
Delete events
0
Modification events
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\OurRefARASPR02224.pdf.lzh | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @shell32,-10162 |
Value: Screen saver | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFC700000040000000870400001B020000 | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6484 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6484.9010\Our Ref ARA-SPR-022-24.pdf.scr | executable | |
MD5:DB7EA196ED98857C564495D55C3CAD2E | SHA256:2F075B10CC83FFA8FBE331A31C26C169A63631E9DC870BF1E4656447471DF264 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
20
DNS requests
6
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 52.182.143.213:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | — | 9 b | unknown |
— | — | GET | 200 | 104.26.12.205:443 | https://api.ipify.org/ | unknown | text | 14 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4264 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5656 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5140 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5140 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5456 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6976 | Our Ref ARA-SPR-022-24.pdf.scr | 104.26.12.205:443 | api.ipify.org | CLOUDFLARENET | US | unknown |
6976 | Our Ref ARA-SPR-022-24.pdf.scr | 50.87.144.157:21 | beirutrest.com | UNIFIEDLAYER-AS-1 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
api.ipify.org |
| shared |
beirutrest.com |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2184 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
6976 | Our Ref ARA-SPR-022-24.pdf.scr | Potential Corporate Privacy Violation | ET POLICY Possible IP Check api.ipify.org |
6976 | Our Ref ARA-SPR-022-24.pdf.scr | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
— | — | Misc activity | INFO [ANY.RUN] FTP protocol command for uploading a file |
— | — | A Network Trojan was detected | ET MALWARE AgentTesla Exfil via FTP |
— | — | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
— | — | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
— | — | Misc activity | INFO [ANY.RUN] FTP server is ready for the new user |
2 ETPRO signatures available at the full report