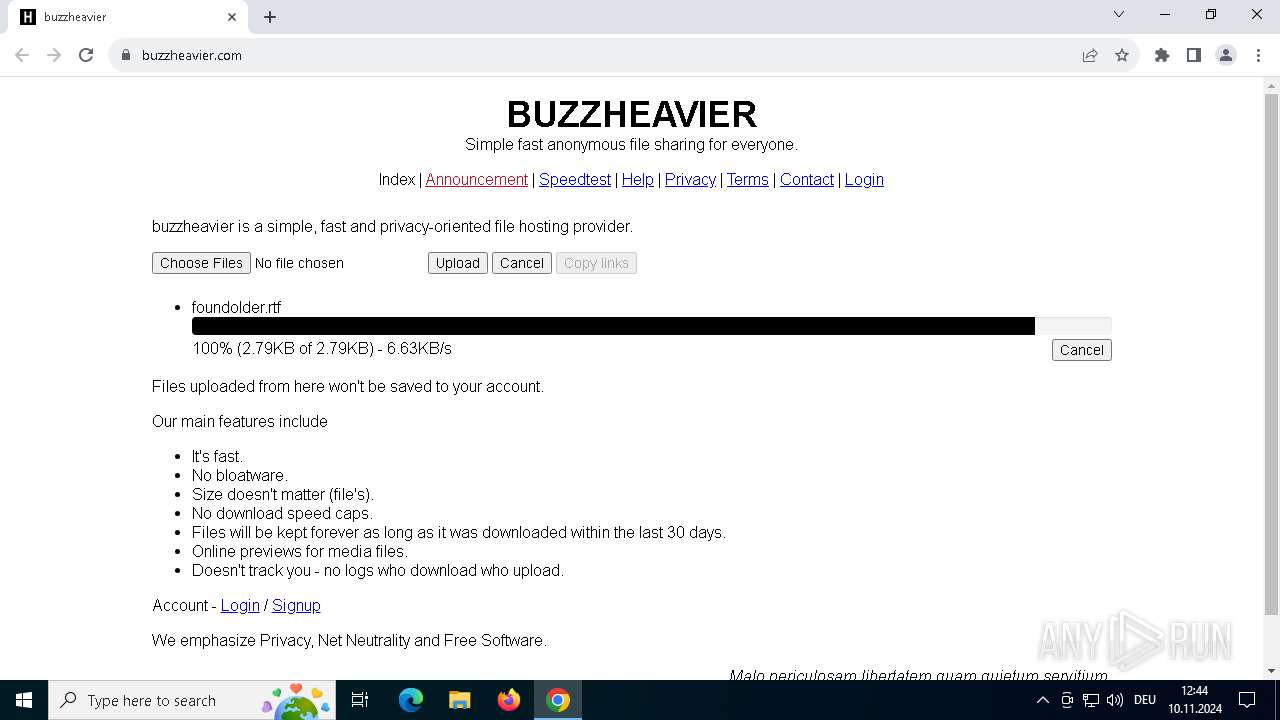
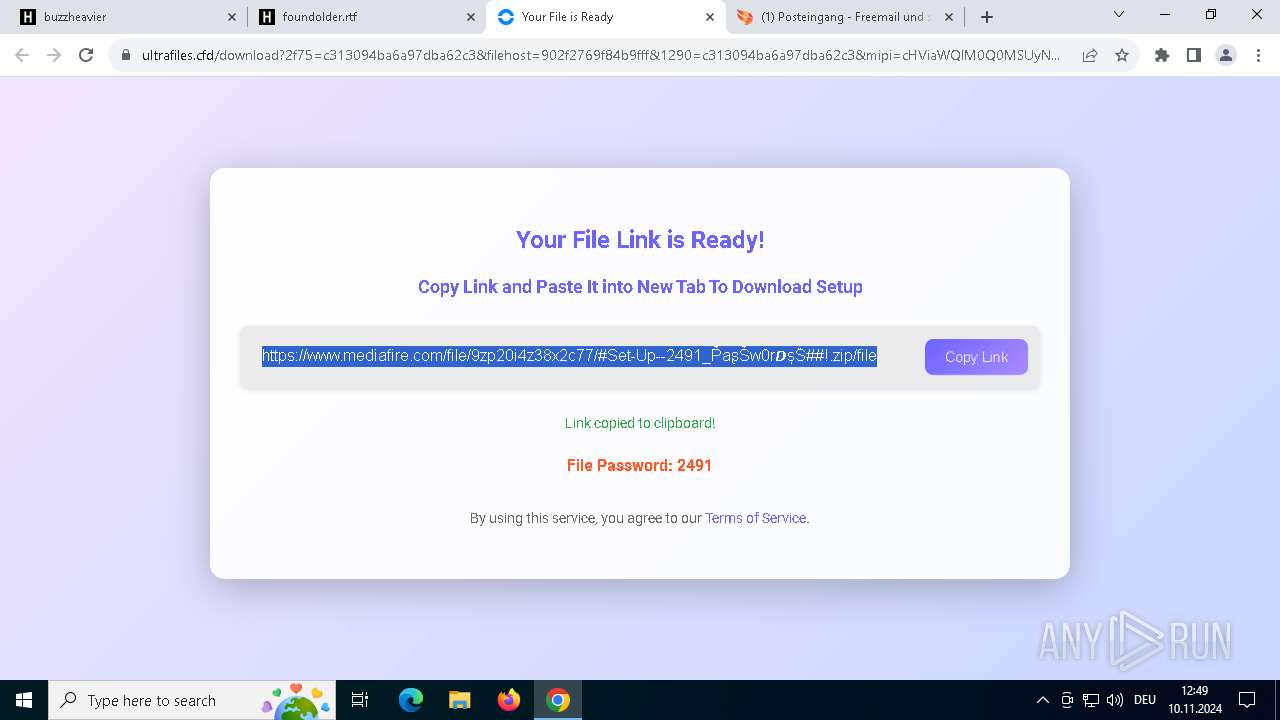
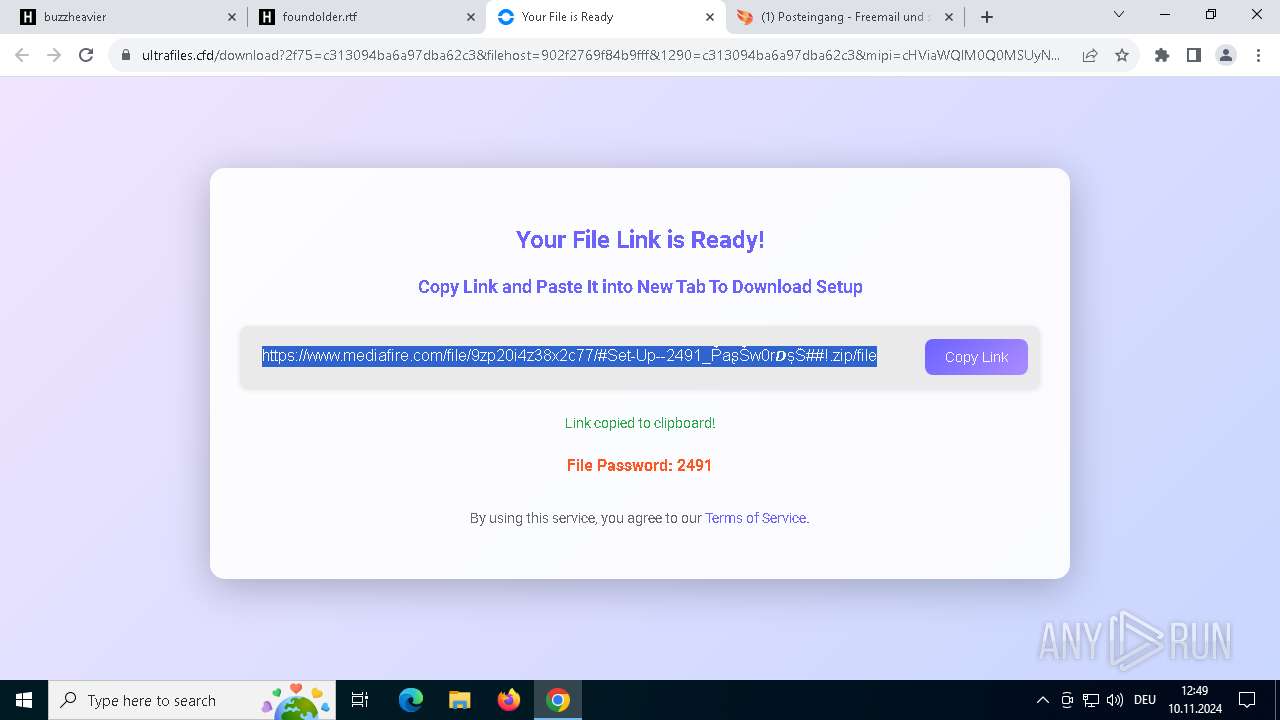
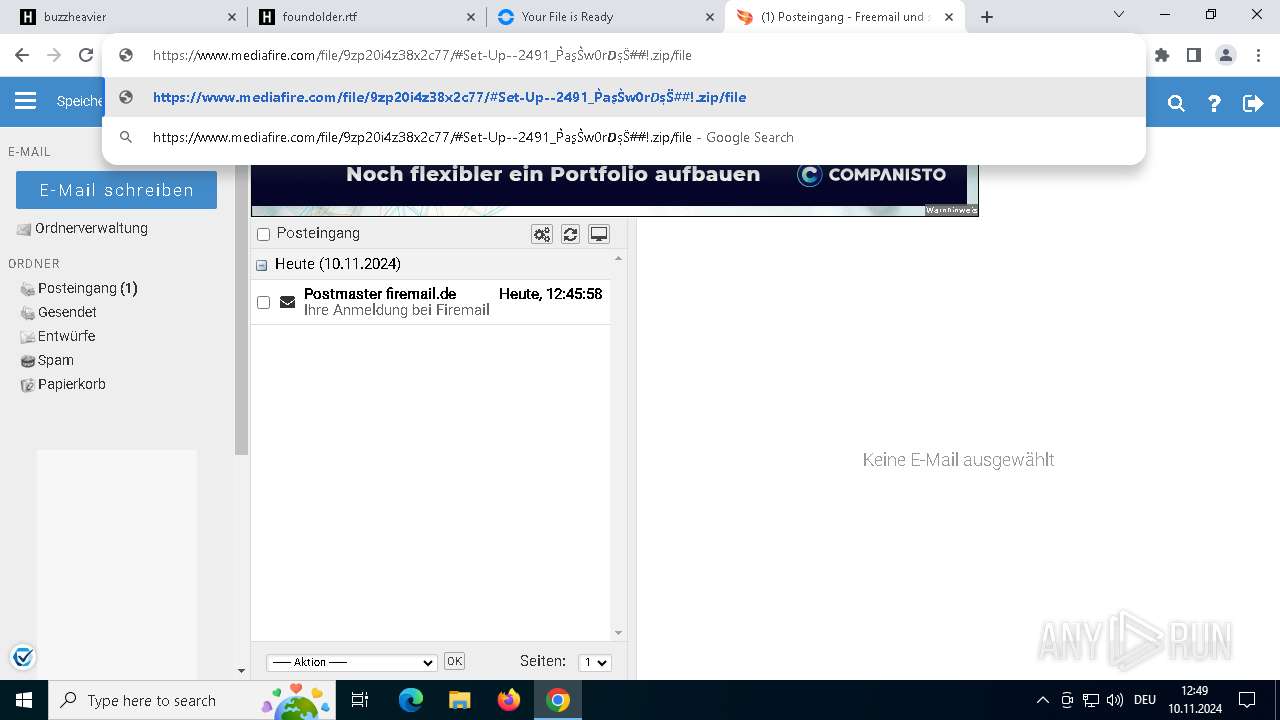
| URL: | https://buzzheavier.com/ |
| Full analysis: | https://app.any.run/tasks/f7ccf06c-8740-4eb5-b165-94e159bbfe53 |
| Verdict: | Malicious activity |
| Threats: | HijackLoader is a modular malware acting as a vehicle for distributing different types of malicious software on compromised systems. It gained prominence during the summer of 2023 and has since been used in multiple attacks against organizations from various sectors, including hospitality businesses. |
| Analysis date: | November 10, 2024, 11:43:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 2A66BE0E4A265615A07B0F8E4699E068 |
| SHA1: | 372EED597361DA7085ABA2B7C2C6EC5307A80364 |
| SHA256: | BE183DA1EEA5526F67F6D40A103A15306F88F6583AC7AA6479279FB02B57D261 |
| SSDEEP: | 3:N8XETz:2XETz |
MALICIOUS
Attempting to scan the network
- chrome.exe (PID: 6268)
HIJACKLOADER has been detected (YARA)
- Setup.exe (PID: 8648)
Changes the autorun value in the registry
- setup.exe (PID: 6312)
SUSPICIOUS
Potential Corporate Privacy Violation
- chrome.exe (PID: 6268)
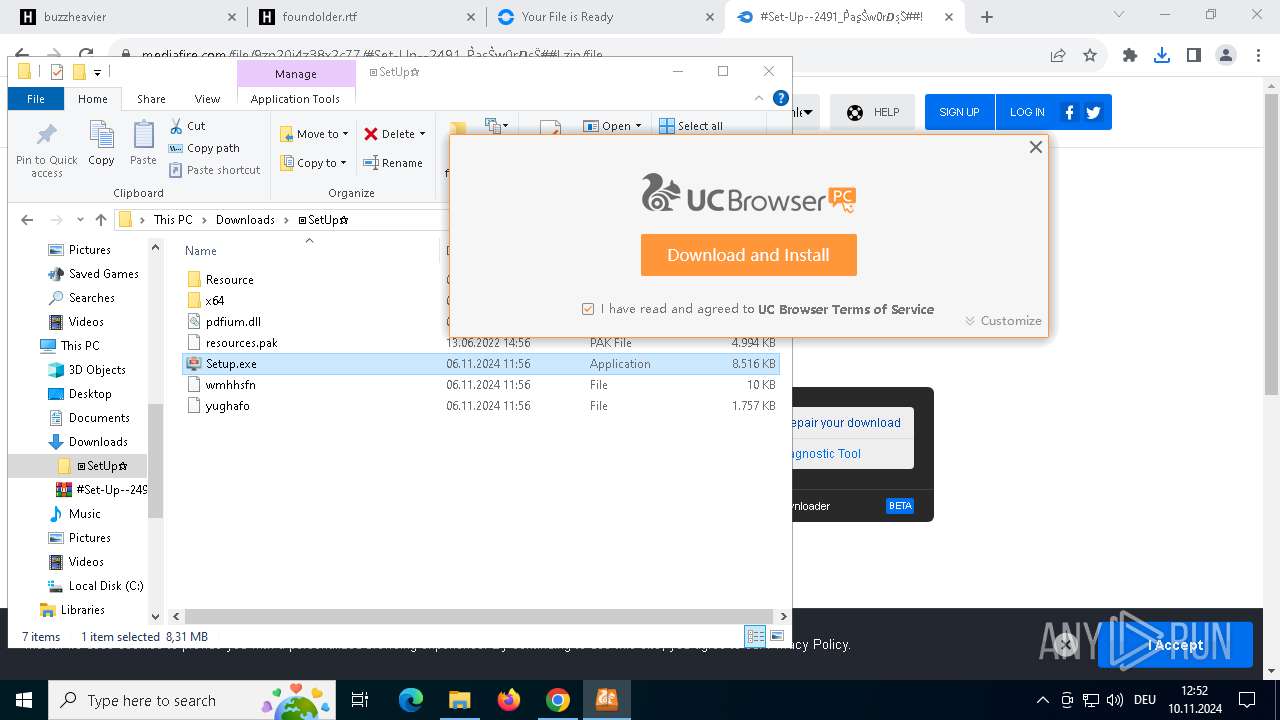
- uc-browser-6-12909-1603.exe (PID: 7848)
Process drops legitimate windows executable
- WinRAR.exe (PID: 8100)
- setup.exe (PID: 6312)
Executable content was dropped or overwritten
- Setup.exe (PID: 8648)
- uc-browser-6-12909-1603.exe (PID: 7848)
- installer.exe (PID: 6564)
- setup.exe (PID: 6312)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 8100)
Reads Internet Explorer settings
- uc-browser-6-12909-1603.exe (PID: 7848)
Reads security settings of Internet Explorer
- uc-browser-6-12909-1603.exe (PID: 9092)
- stats_uploader.exe (PID: 7280)
- stats_uploader.exe (PID: 8344)
- stats_uploader.exe (PID: 6284)
- stats_uploader.exe (PID: 4040)
- stats_uploader.exe (PID: 7576)
- stats_uploader.exe (PID: 8492)
- stats_uploader.exe (PID: 3524)
- stats_uploader.exe (PID: 4292)
- stats_uploader.exe (PID: 7640)
- stats_uploader.exe (PID: 2784)
- setup.exe (PID: 6312)
- stats_uploader.exe (PID: 7020)
- UCBrowser.exe (PID: 7840)
- installer.exe (PID: 6564)
Application launched itself
- uc-browser-6-12909-1603.exe (PID: 9092)
- UCBrowser.exe (PID: 3532)
- UCBrowser.exe (PID: 7840)
Process requests binary or script from the Internet
- uc-browser-6-12909-1603.exe (PID: 7848)
Drops 7-zip archiver for unpacking
- setup.exe (PID: 6312)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- setup.exe (PID: 6312)
Creates a software uninstall entry
- setup.exe (PID: 6312)
Searches for installed software
- setup.exe (PID: 6312)
Uses NETSH.EXE to add a firewall rule or allowed programs
- setup.exe (PID: 6312)
Executes as Windows Service
- UCService.exe (PID: 4076)
Checks Windows Trust Settings
- UCService.exe (PID: 4076)
Checks for external IP
- UCBrowser.exe (PID: 3532)
Connects to unusual port
- UCBrowser.exe (PID: 3532)
INFO
Executable content was dropped or overwritten
- chrome.exe (PID: 8800)
- chrome.exe (PID: 7312)
- WinRAR.exe (PID: 8100)
Manual execution by a user
- WinRAR.exe (PID: 8360)
- WinRAR.exe (PID: 8100)
- Setup.exe (PID: 8648)
The process uses the downloaded file
- WinRAR.exe (PID: 8360)
- WinRAR.exe (PID: 8100)
- chrome.exe (PID: 8176)
- uc-browser-6-12909-1603.exe (PID: 9092)
Checks supported languages
- Setup.exe (PID: 8648)
- uc-browser-6-12909-1603.exe (PID: 9092)
- uc-browser-6-12909-1603.exe (PID: 7848)
- stats_uploader.exe (PID: 8344)
- stats_uploader.exe (PID: 7280)
- stats_uploader.exe (PID: 6284)
- stats_uploader.exe (PID: 8492)
- stats_uploader.exe (PID: 7576)
- stats_uploader.exe (PID: 4040)
- stats_uploader.exe (PID: 7640)
- stats_uploader.exe (PID: 3524)
- installer.exe (PID: 6564)
- stats_uploader.exe (PID: 2784)
- stats_uploader.exe (PID: 4292)
- setup.exe (PID: 6312)
- UCService.exe (PID: 9208)
- UCService.exe (PID: 4076)
- stats_uploader.exe (PID: 7020)
- UCBrowser.exe (PID: 3532)
- UCBrowser.exe (PID: 7840)
- UCBrowser.exe (PID: 7124)
- UCBrowser.exe (PID: 1084)
- UCBrowser.exe (PID: 7340)
- UCService.exe (PID: 7460)
Creates files or folders in the user directory
- Setup.exe (PID: 8648)
- uc-browser-6-12909-1603.exe (PID: 7848)
- stats_uploader.exe (PID: 2784)
- setup.exe (PID: 6312)
- UCBrowser.exe (PID: 3532)
Reads the computer name
- Setup.exe (PID: 8648)
- uc-browser-6-12909-1603.exe (PID: 9092)
- uc-browser-6-12909-1603.exe (PID: 7848)
- stats_uploader.exe (PID: 7280)
- stats_uploader.exe (PID: 8344)
- stats_uploader.exe (PID: 6284)
- stats_uploader.exe (PID: 7576)
- stats_uploader.exe (PID: 4040)
- stats_uploader.exe (PID: 8492)
- stats_uploader.exe (PID: 3524)
- stats_uploader.exe (PID: 4292)
- stats_uploader.exe (PID: 2784)
- installer.exe (PID: 6564)
- setup.exe (PID: 6312)
- UCService.exe (PID: 9208)
- stats_uploader.exe (PID: 7640)
- stats_uploader.exe (PID: 7020)
- UCService.exe (PID: 7460)
- UCBrowser.exe (PID: 7840)
- UCBrowser.exe (PID: 3532)
- UCBrowser.exe (PID: 1084)
- UCBrowser.exe (PID: 7124)
- UCBrowser.exe (PID: 7340)
- UCService.exe (PID: 4076)
Checks proxy server information
- stats_uploader.exe (PID: 8344)
- stats_uploader.exe (PID: 7280)
- stats_uploader.exe (PID: 7576)
- stats_uploader.exe (PID: 4040)
- stats_uploader.exe (PID: 6284)
- stats_uploader.exe (PID: 8492)
- stats_uploader.exe (PID: 7640)
- stats_uploader.exe (PID: 3524)
- stats_uploader.exe (PID: 4292)
- installer.exe (PID: 6564)
- stats_uploader.exe (PID: 2784)
- UCBrowser.exe (PID: 7840)
- UCBrowser.exe (PID: 3532)
Application launched itself
- chrome.exe (PID: 4684)
Sends debugging messages
- uc-browser-6-12909-1603.exe (PID: 7848)
- installer.exe (PID: 6564)
- UCService.exe (PID: 9208)
- UCService.exe (PID: 4076)
- UCService.exe (PID: 7460)
Create files in a temporary directory
- Setup.exe (PID: 8648)
- installer.exe (PID: 6564)
- choice.exe (PID: 9164)
- UCBrowser.exe (PID: 3532)
Creates files in the program directory
- setup.exe (PID: 6312)
- UCService.exe (PID: 9208)
- UCService.exe (PID: 4076)
- UCBrowser.exe (PID: 7840)
- UCBrowser.exe (PID: 3532)
Process checks whether UAC notifications are on
- UCService.exe (PID: 9208)
- UCService.exe (PID: 7460)
Reads the software policy settings
- UCService.exe (PID: 4076)
- UCBrowser.exe (PID: 3532)
Reads the time zone
- UCBrowser.exe (PID: 1084)
- UCBrowser.exe (PID: 7340)
Process checks computer location settings
- UCBrowser.exe (PID: 1084)
- UCBrowser.exe (PID: 7340)
Reads the machine GUID from the registry
- UCBrowser.exe (PID: 3532)
- UCService.exe (PID: 4076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
346
Monitored processes
224
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=36 --mojo-platform-channel-handle=6896 --field-trial-handle=1852,i,14194652358142899474,2437265049934636735,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 764 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3064 --field-trial-handle=1852,i,14194652358142899474,2437265049934636735,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 784 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --mojo-platform-channel-handle=4380 --field-trial-handle=1852,i,14194652358142899474,2437265049934636735,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1048 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=152 --mojo-platform-channel-handle=11244 --field-trial-handle=1852,i,14194652358142899474,2437265049934636735,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1084 | "C:\Program Files (x86)\UCBrowser\Application\UCBrowser.exe" --type=renderer --disable-direct-write --enable-features=use-new-media-cache<use-new-media-cache --lang=en-US --force-fieldtrials=AutofillClassifier/Enabled/AutofillFieldMetadata/Enabled/AutofillProfileOrderByFrecency/EnabledLimitTo3/AutomaticTabDiscarding/Enabled_Once_5/BrowserBlacklist/Enabled/CaptivePortalInterstitial/Enabled/ChildAccountDetection/Disabled/ChromeDashboard/Enabled/ChromotingQUIC/Enabled/*DataReductionProxyConfigService/Enabled/EnableGoogleCachedCopyTextExperiment/Button/EnableSessionCrashedBubbleUI/Enabled/*ExtensionActionRedesign/Enabled/*ExtensionContentVerification/Enforce/ExtensionInstallVerification/Enforce/GoogleNow/Enable/*IconNTP/Default/InstanceID/Enabled/IntelligentSessionRestore/Enabled/LocalNTPSuggestionsService/Enabled/MaterialDesignDownloads/Enabled/*NetworkQualityEstimator/Enabled/*NewProfileManagement/Enabled/OfferUploadCreditCards/Enabled/*PageRevisitInstrumentation/Enabled/PasswordBranding/SmartLockBrandingSavePromptOnly/PasswordGeneration/Disabled/*QUIC/Enabled/RefreshTokenDeviceId/Enabled/RenderingPipelineThrottling/Enabled/ReportCertificateErrors/ShowAndPossiblySend/SRTPromptFieldTrial/On/SafeBrowsingReportPhishingErrorLink/Enabled/SafeBrowsingUnverifiedDownloads/DisableByParameterMostSbTypes2/SafeBrowsingUpdateFrequency/UpdateTime15m/SchedulerExpensiveTaskBlocking/Enabled/SdchPersistence/Enabled/*SettingsEnforcement/enforce_always_with_extensions_and_dse/SpdyEnableDependencies/Enable/StrictSecureCookies/Enabled/SyncHttpContentCompression/Enabled/TabSyncByRecency/Enabled/*TriggeredResetFieldTrial/On/VarationsServiceControl/Interval_30min/WebFontsIntervention/Enabled/WebRTC-LocalIPPermissionCheck/Enabled/WebRTC-PeerConnectionDTLS1.2/Enabled/use-new-media-cache/Enabled/ --wow-extension-center-url=https://chrome.google.com/webstore/category/extensions --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --content-image-texture-target=3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553 --video-image-texture-target=3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553,3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --wow-user-agent=UBrowser/6.0.1308.1016 --channel="3532.0.54186810\1242571258" /prefetch:1 | C:\Program Files (x86)\UCBrowser\Application\UCBrowser.exe | — | UCBrowser.exe | |||||||||||
User: admin Company: UCWeb Inc. Integrity Level: LOW Description: UC Browser Version: 6.0.1308.1016 Modules
| |||||||||||||||
| 1176 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --mojo-platform-channel-handle=5940 --field-trial-handle=1852,i,14194652358142899474,2437265049934636735,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1176 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=98 --mojo-platform-channel-handle=10676 --field-trial-handle=1852,i,14194652358142899474,2437265049934636735,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=10268 --field-trial-handle=1852,i,14194652358142899474,2437265049934636735,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5380 --field-trial-handle=1852,i,14194652358142899474,2437265049934636735,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2076 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=3456 --field-trial-handle=1852,i,14194652358142899474,2437265049934636735,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
43 552
Read events
43 195
Write events
322
Delete events
35
Modification events
| (PID) Process: | (4684) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4684) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4684) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4684) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4684) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6204) chrome.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6204) chrome.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0E000000000000000400000003000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (6204) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 96 | |||
| (PID) Process: | (6204) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: AB9C306700000000 | |||
| (PID) Process: | (4684) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
107
Suspicious files
648
Text files
544
Unknown types
152
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4684 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF8e874.TMP | — | |
MD5:— | SHA256:— | |||
| 4684 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF8e874.TMP | — | |
MD5:— | SHA256:— | |||
| 4684 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4684 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4684 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF8e884.TMP | — | |
MD5:— | SHA256:— | |||
| 4684 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4684 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF8e884.TMP | — | |
MD5:— | SHA256:— | |||
| 4684 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4684 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF8e894.TMP | — | |
MD5:— | SHA256:— | |||
| 4684 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
119
TCP/UDP connections
935
DNS requests
683
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4432 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4432 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
4432 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
4432 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
4432 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrga7eefaxjfdmmgfkiaxjg4yjq_2024.7.12.235938/eeigpngbgcognadeebkilcpcaedhellh_2024.07.12.235938_all_a6r64uyugl6fjh3lupjqo6w7ai.crx3 | unknown | — | — | whitelisted |
4432 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrga7eefaxjfdmmgfkiaxjg4yjq_2024.7.12.235938/eeigpngbgcognadeebkilcpcaedhellh_2024.07.12.235938_all_a6r64uyugl6fjh3lupjqo6w7ai.crx3 | unknown | — | — | whitelisted |
4432 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrga7eefaxjfdmmgfkiaxjg4yjq_2024.7.12.235938/eeigpngbgcognadeebkilcpcaedhellh_2024.07.12.235938_all_a6r64uyugl6fjh3lupjqo6w7ai.crx3 | unknown | — | — | whitelisted |
4432 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrga7eefaxjfdmmgfkiaxjg4yjq_2024.7.12.235938/eeigpngbgcognadeebkilcpcaedhellh_2024.07.12.235938_all_a6r64uyugl6fjh3lupjqo6w7ai.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4360 | SearchApp.exe | 23.15.178.179:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 2.16.164.43:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6944 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6268 | chrome.exe | 172.67.71.74:443 | buzzheavier.com | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
buzzheavier.com |
| unknown |
accounts.google.com |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
www.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6268 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
6268 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare R2 Storage (r2 .cloudflarestorage .com) |
6268 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare R2 Storage (r2 .cloudflarestorage .com) |
6268 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
6268 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
6268 | chrome.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempting to network scan inside a home network |
6268 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] PX-Cloud CDN (px-cloud .net) |
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2172 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
uc-browser-6-12909-1603.exe | [7848:7668:1110/125224:WARNING:wow_install_downloader_proxy.cc(190)] clear temp download data
|
uc-browser-6-12909-1603.exe | [7848:8416:1110/125224:ERROR:wow_wmi_utils.cc(148)] Failed to initialize security. result = -2147417831
|
uc-browser-6-12909-1603.exe | [7848:7668:1110/125225:INFO:wow_stats_helper.cc(326)] https://i18nmmstat.ucweb.com/lv=1.0&encrypt_data=bTkwAgwv4fLE+CXrisWLMdvdVZnzBZ/zH20dgeTAD6ZDgaw4fBcRaYYgill0n8R8mFLxb+8s+OYI++Kwx6VtoLpOlc8IIHM08ug47lOitDk7ijmUmy7s+n9+B0qMpnK78896NLc/MXiyMVFMf73wM3gBTJMjYgj1bvai/Ou2CbrAEpiXxzTQJ4/2s2oZF9bCHtbuchaZB9lTcdtBwkkMDdfTOK+QxMgKxDQo7LRCksccNl2YOI4y2Q7XLiknWipC5HEAU73Us18rKStuFA==
|
uc-browser-6-12909-1603.exe | [7848:7668:1110/125225:INFO:wow_stats_helper.cc(322)] bluesky.1.2.3.1.1?cache=1091227000&ka=&kb=2433f36584d9738cdbb9ee4d08b4f61a&kc=b7141b3680af7e1271d9562724bf707ev000000239b71be5&firstpid=4595&bid=35151&ver=6.1.3244.1000&installpid=4601&lang=en-US
|
uc-browser-6-12909-1603.exe | [7848:7668:1110/125225:INFO:wow_distribution_i18n.cc(487)] Got locale from UI language list.
|
uc-browser-6-12909-1603.exe | [7848:7668:1110/125225:INFO:wow_stats_helper.cc(326)] https://i18nmmstat.ucweb.com/lv=1.0&encrypt_data=bTkwAgov8ODG+CoZhMV4I9fdt72PBf2XGWeUyeDL/wBXgOH4dxdbJJwgx/5gwxCbhQ0g3eQsyw8D+HY+ofj6IkEVCnk4e7ek0bjrBCf0bQvA2tRtj3AZew9771PLo9n9SshnTgs8iEaNbB6lBbiyL8oFK5DIMDW/cPZDjo20KUa7R67k4GTTB6LtzZ8zDtipO9fQOjndHhAsfzgv4E12A/zEQwyg2yP//zJjfHVD7U0+eRstT4KVGHbf1QaXAxeg8Wm6sP2AUOW7C5yPKwNvSHi/cMkSj7W3PwdevNQ1zGsJ
|
uc-browser-6-12909-1603.exe | [7848:7668:1110/125225:INFO:wow_stats_helper.cc(322)] bluesky.1.2.3.1.15?cache=1091295000&ka=&kb=2433f36584d9738cdbb9ee4d08b4f61a&kc=b7141b3680af7e1271d9562724bf707ev000000239b71be5&firstpid=4595&bid=35151&ver=6.1.3244.1000&from=1&avproducts=Windows+Defender&lang=en-US
|
uc-browser-6-12909-1603.exe | [7848:7668:1110/125229:INFO:wow_stats_helper.cc(322)] bluesky.1.2.3.1.2?cache=1095607000&ka=&kb=2433f36584d9738cdbb9ee4d08b4f61a&kc=b7141b3680af7e1271d9562724bf707ev000000239b71be5&firstpid=4595&bid=35151&ver=6.1.3244.1000&installpid=4601&lang=en-US
|
uc-browser-6-12909-1603.exe | [7848:7668:1110/125229:INFO:wow_stats_helper.cc(326)] https://i18nmmstat.ucweb.com/lv=1.0&encrypt_data=bTkwAlMzKmmP9OxgM9lCuEnVy4t9HXHlMWE6JD/cID2/8YDQXAV9BSkUP+4Zi2kBxrpLEbUEMqwZ3+Hx8IFu54IuXQfAADtscdSpPdKOBQjhct/O3QYKRGpCaCf/ilWYh7+OgOsPRewVBSyz2olFJp75ThXBWgp3tzLp9TTyskVwUggHd3Sg1/S66nFQq+/bHB7AkAgh+X+OvWx0CfWzJluDhNNkdLS2+2Atq2n2r4py3hdWEibIg69zvfhA/pkVTBFYC+V0yzfYtcqciQ==
|
uc-browser-6-12909-1603.exe | [7848:4812:1110/125229:INFO:wow_install_downloader_proxy.cc(407)] Config url: http://www.uc123.com/pcbrowser_i18n/downloader.php?pid=4601&version=1.0.0.0&os=win&arch=x86_64
|