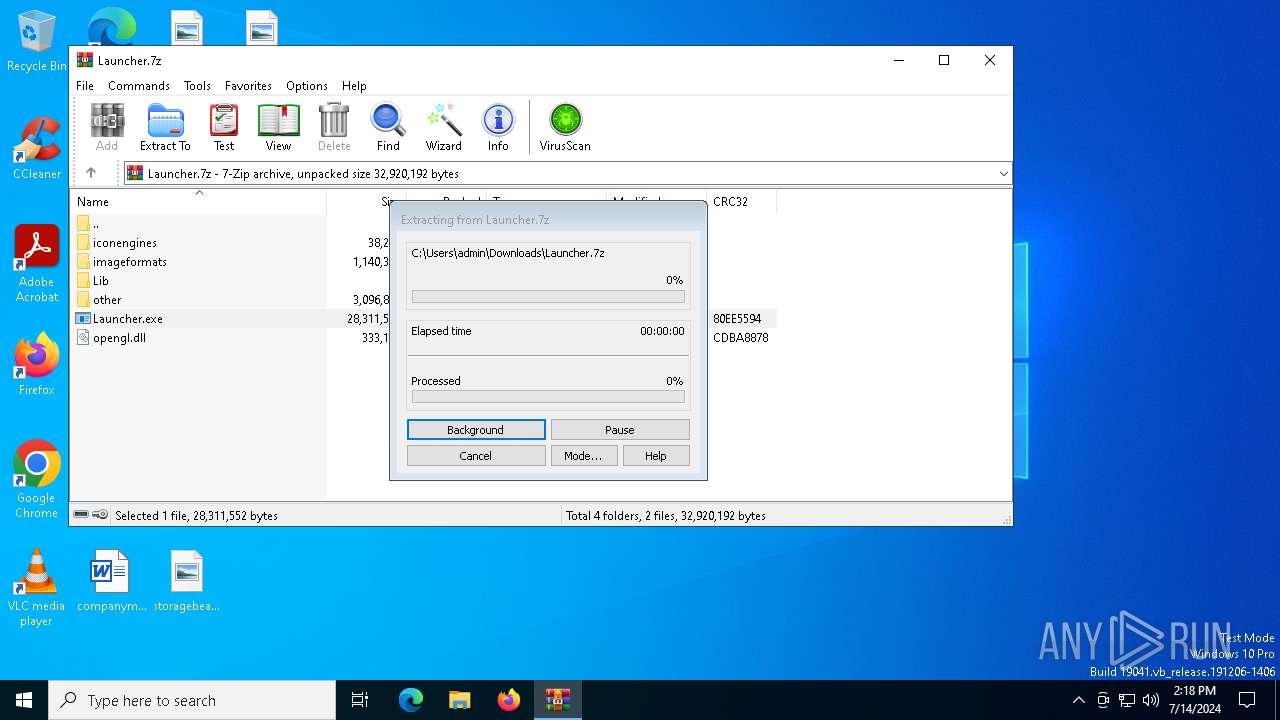
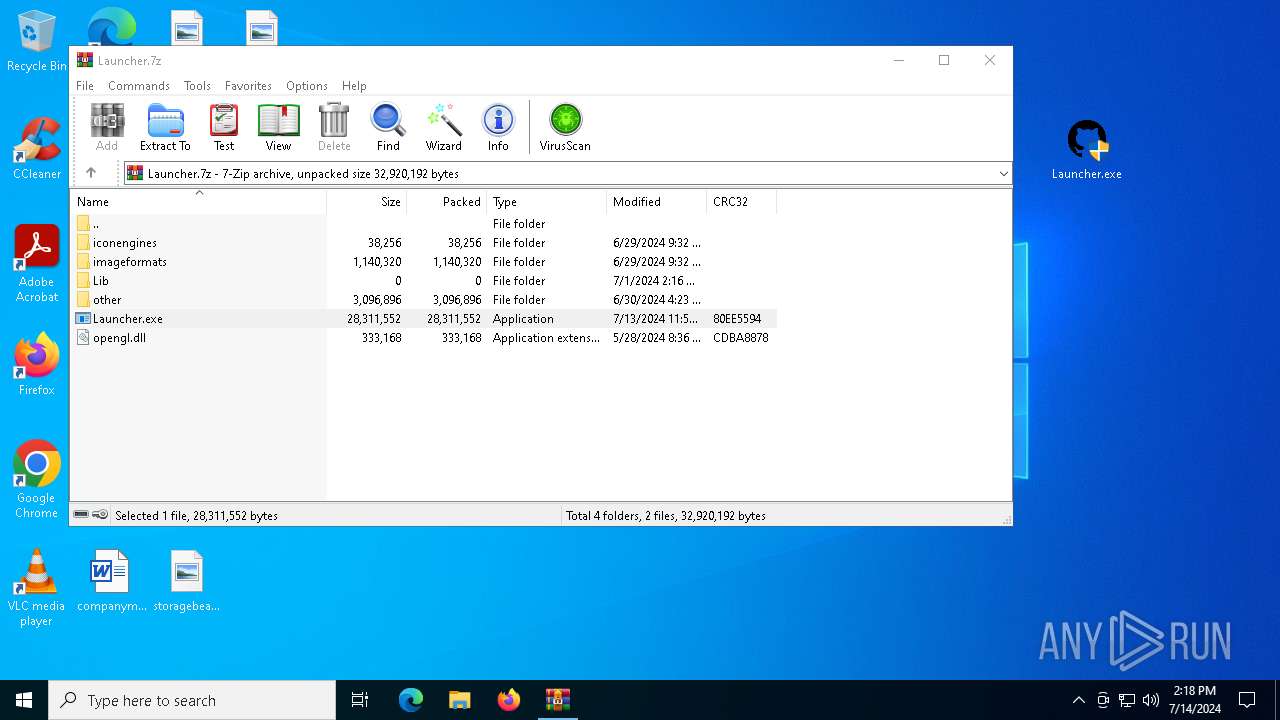
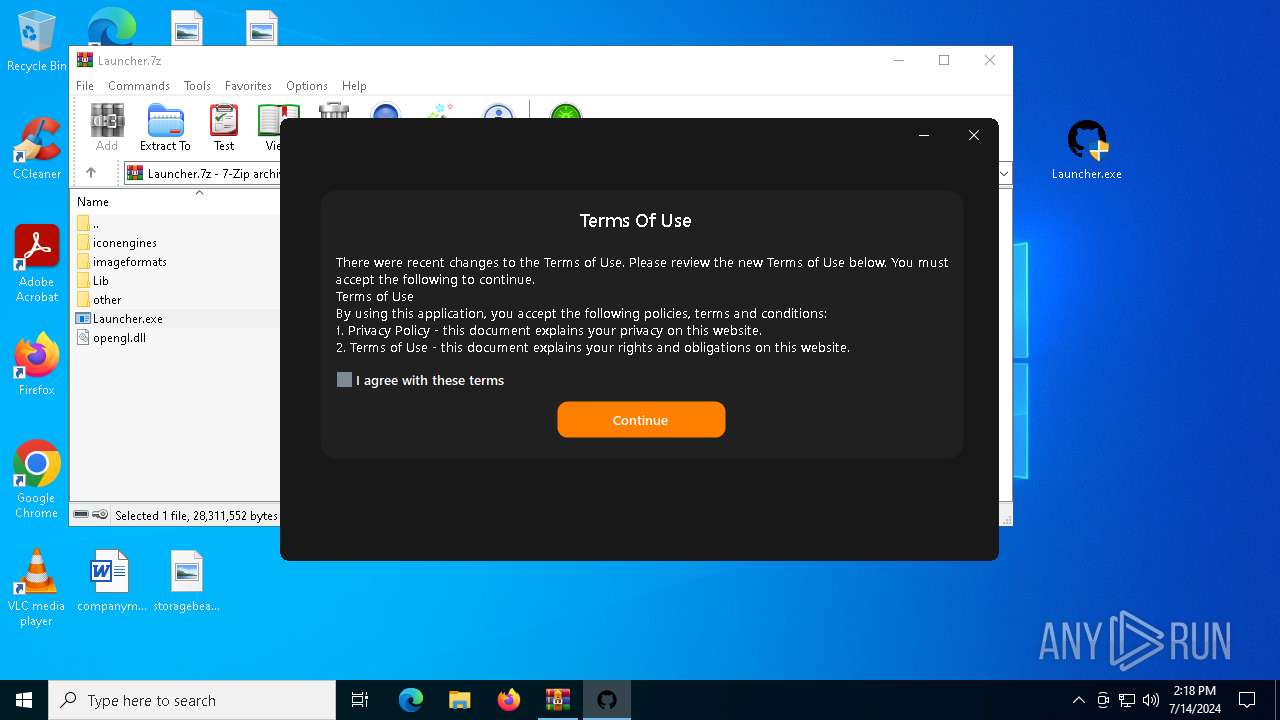
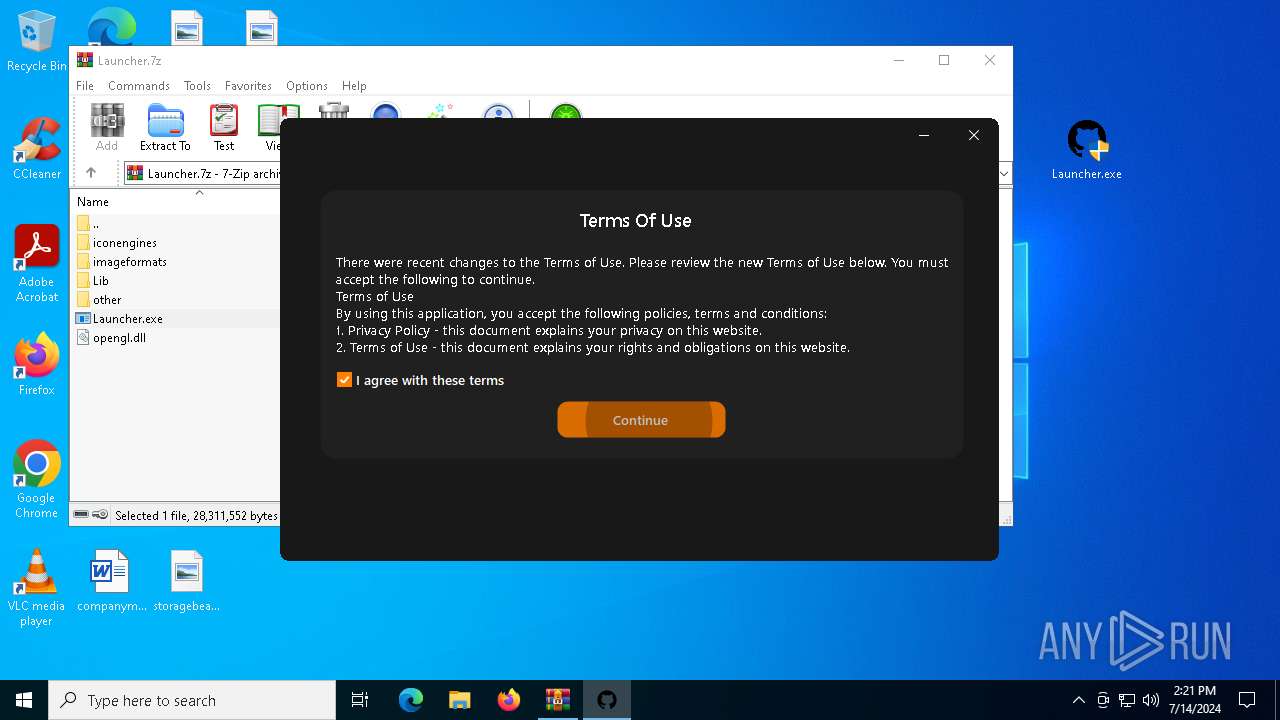
| URL: | https://github.com/Jkza1Klaus/Jkaz1/releases/download/Released/Launcher.7z |
| Full analysis: | https://app.any.run/tasks/cf7cc50f-dce8-4ac3-b8da-ba0b23cf6697 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | July 14, 2024, 14:17:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 067C62C02E6DD77E5057DFD0B335DA9C |
| SHA1: | D7F4AB6FA51C19A71EAEDD78AE7AC77E264F24A7 |
| SHA256: | BD8EB9E59EF1182CBD189315A7197BDD0D2428ED4A75B6494BAAA932E0F8951B |
| SSDEEP: | 3:N8tEdm1uBkMkC8AEhJNX:2uA+2Ai5 |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6592)
- powershell.exe (PID: 6884)
Adds path to the Windows Defender exclusion list
- Launcher.exe (PID: 5904)
Changes powershell execution policy (Bypass)
- Launcher.exe (PID: 5904)
Drops the executable file immediately after the start
- Launcher.exe (PID: 5904)
LUMMA has been detected (SURICATA)
- RegAsm.exe (PID: 5884)
- RegAsm.exe (PID: 752)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 5884)
- RegAsm.exe (PID: 752)
SUSPICIOUS
Reads security settings of Internet Explorer
- Launcher.exe (PID: 5904)
Script adds exclusion path to Windows Defender
- Launcher.exe (PID: 5904)
Starts POWERSHELL.EXE for commands execution
- Launcher.exe (PID: 5904)
Potential Corporate Privacy Violation
- Launcher.exe (PID: 5904)
Executable content was dropped or overwritten
- Launcher.exe (PID: 5904)
Reads the date of Windows installation
- Launcher.exe (PID: 5904)
Searches for installed software
- RegAsm.exe (PID: 5884)
- RegAsm.exe (PID: 752)
INFO
The process uses the downloaded file
- chrome.exe (PID: 4400)
- WinRAR.exe (PID: 1120)
- chrome.exe (PID: 3800)
Reads Microsoft Office registry keys
- chrome.exe (PID: 3800)
- firefox.exe (PID: 7128)
Application launched itself
- chrome.exe (PID: 3800)
- firefox.exe (PID: 7128)
- firefox.exe (PID: 1060)
Reads the computer name
- Launcher.exe (PID: 5904)
- RegAsm.exe (PID: 752)
- RegAsm.exe (PID: 5884)
Checks supported languages
- Launcher.exe (PID: 5904)
- build.exe (PID: 6168)
- RegAsm.exe (PID: 752)
- build.exe (PID: 2704)
- RegAsm.exe (PID: 5884)
Reads the machine GUID from the registry
- Launcher.exe (PID: 5904)
Manual execution by a user
- Launcher.exe (PID: 5904)
- Launcher.exe (PID: 7096)
- firefox.exe (PID: 1060)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1120)
Reads Environment values
- Launcher.exe (PID: 5904)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1120)
Create files in a temporary directory
- Launcher.exe (PID: 5904)
Disables trace logs
- Launcher.exe (PID: 5904)
Checks proxy server information
- Launcher.exe (PID: 5904)
Reads the software policy settings
- Launcher.exe (PID: 5904)
- RegAsm.exe (PID: 752)
- RegAsm.exe (PID: 5884)
Process checks computer location settings
- Launcher.exe (PID: 5904)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6884)
- powershell.exe (PID: 6592)
Connects to unusual port
- firefox.exe (PID: 7128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
180
Monitored processes
37
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffd94fddc40,0x7ffd94fddc4c,0x7ffd94fddc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 752 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | build.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 904 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2272 -parentBuildID 20240213221259 -prefsHandle 2264 -prefMapHandle 2252 -prefsLen 30537 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {2018950d-3515-4da2-b882-b5ad2c719819} 7128 "\\.\pipe\gecko-crash-server-pipe.7128" 1a377581d10 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1060 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1120 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Launcher.7z" | C:\Program Files\WinRAR\WinRAR.exe | chrome.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1436 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2652 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1916 -parentBuildID 20240213221259 -prefsHandle 1844 -prefMapHandle 1836 -prefsLen 30537 -prefMapSize 244343 -appDir "C:\Program Files\Mozilla Firefox\browser" - {17b9bb87-c0a0-4870-8e4c-ab7dd0c93422} 7128 "\\.\pipe\gecko-crash-server-pipe.7128" 1a37f7e3a10 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 2704 | "C:\Users\admin\AppData\Local\Temp\build.exe" | C:\Users\admin\AppData\Local\Temp\build.exe | — | Launcher.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3676 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.FileUtilService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5152 --field-trial-handle=2080,i,10588555593701934348,18163916590044266463,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3800 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://github.com/Jkza1Klaus/Jkaz1/releases/download/Released/Launcher.7z" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
46 216
Read events
46 105
Write events
109
Delete events
2
Modification events
| (PID) Process: | (3800) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3800) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3800) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3800) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3800) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3800) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3800) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3800) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3800) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3800) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
5
Suspicious files
242
Text files
62
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1cfb9d.TMP | — | |
MD5:— | SHA256:— | |||
| 3800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1cfbad.TMP | — | |
MD5:— | SHA256:— | |||
| 3800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF1cfb7e.TMP | text | |
MD5:8F45965291AB2DA10EEB049FB6E917C6 | SHA256:8A0DE526945B27CDBBD87357C85FDDD37B572370F894CB0A5AC533FD465D2166 | |||
| 3800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old~RF1cfd14.TMP | text | |
MD5:602C51DB8380F8CD0A961D9A46AF1186 | SHA256:84F716E38017F52138A76222524A3152DB8D3A7FBE30E94067458568B14DC36D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
172
DNS requests
164
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1792 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7128 | firefox.exe | POST | 200 | 184.24.77.71:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
7128 | firefox.exe | POST | 200 | 184.24.77.77:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
1792 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6428 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6336 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3508 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
7128 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | unknown |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4656 | SearchApp.exe | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1792 | MoUsoCoreWorker.exe | 2.16.164.34:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
1792 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1792 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6004 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
github.com |
| shared |
accounts.google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
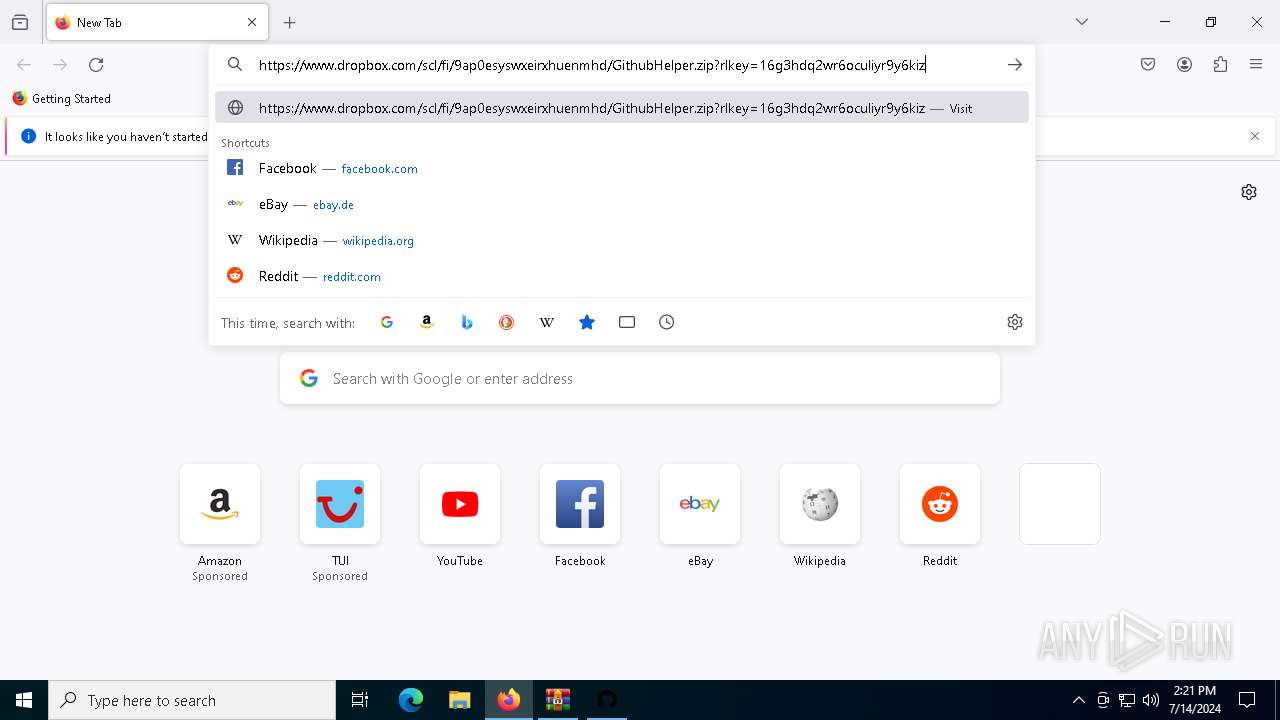
5904 | Launcher.exe | Potential Corporate Privacy Violation | ET POLICY Dropbox.com Offsite File Backup in Use |
752 | RegAsm.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |
5884 | RegAsm.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |