| URL: | https://u45250775.ct.sendgrid.net/ls/click?upn=u001.tFoYEKu8c3QV4dCjnENfD8xt5kmuuDSrdqsY1RaUCNHUhTAxpCf-2FkQtKBbJ888oIbO8H_FnLC7kB6-2BHmARw1okfdNikp-2FzACuW8UETXmdqoYXSiKXoF1bfZy5CfNwzHmhJl6q6z-2B6A18KSPjAWLrWZiMLzxtCi-2FpHUjZMnVc9JZH2xfwPofZy5qfcHEimTxXX-2BlYvSZtaACLkmoON7t2HztkzOxry6Ur6NeGriREvJD-2FAoivXW64Cty-2BrMfW0htt0w8X3xYIPjtRjC102Wo9HpAM3Qg-3D-3D |
| Full analysis: | https://app.any.run/tasks/d4d0eccd-8bc7-4ce1-a51d-0327f4760a6c |
| Verdict: | Malicious activity |
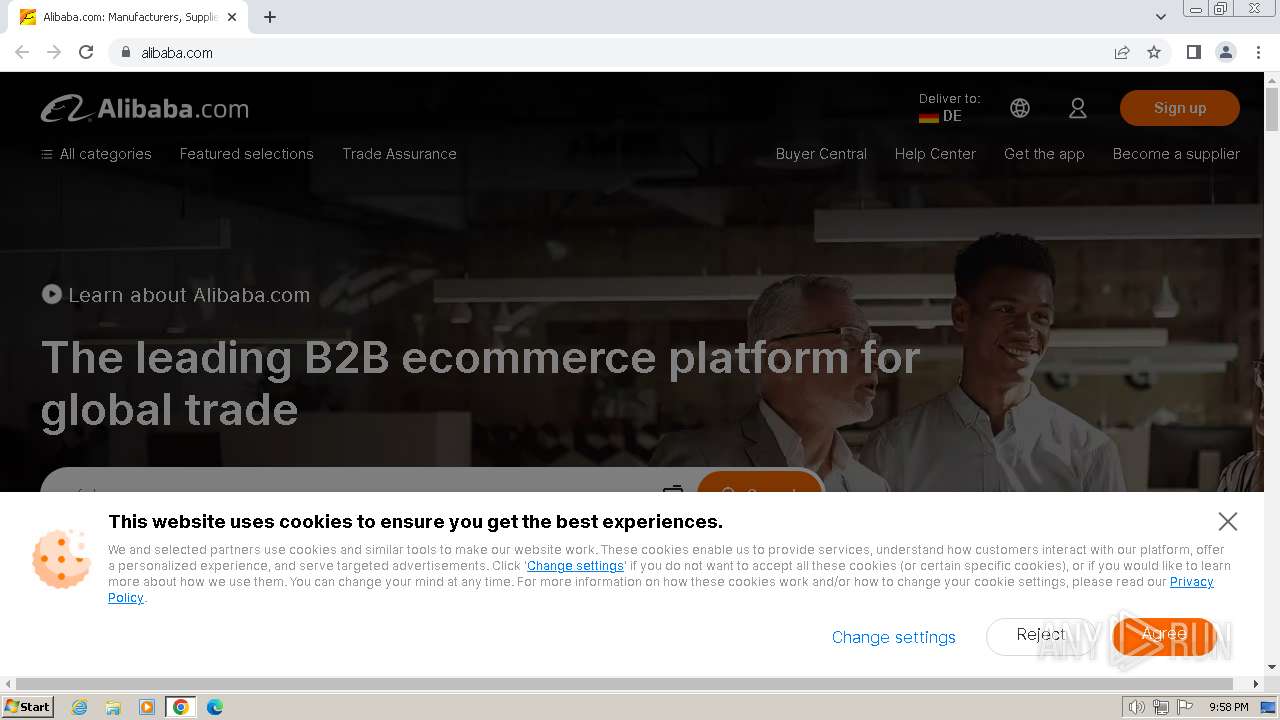
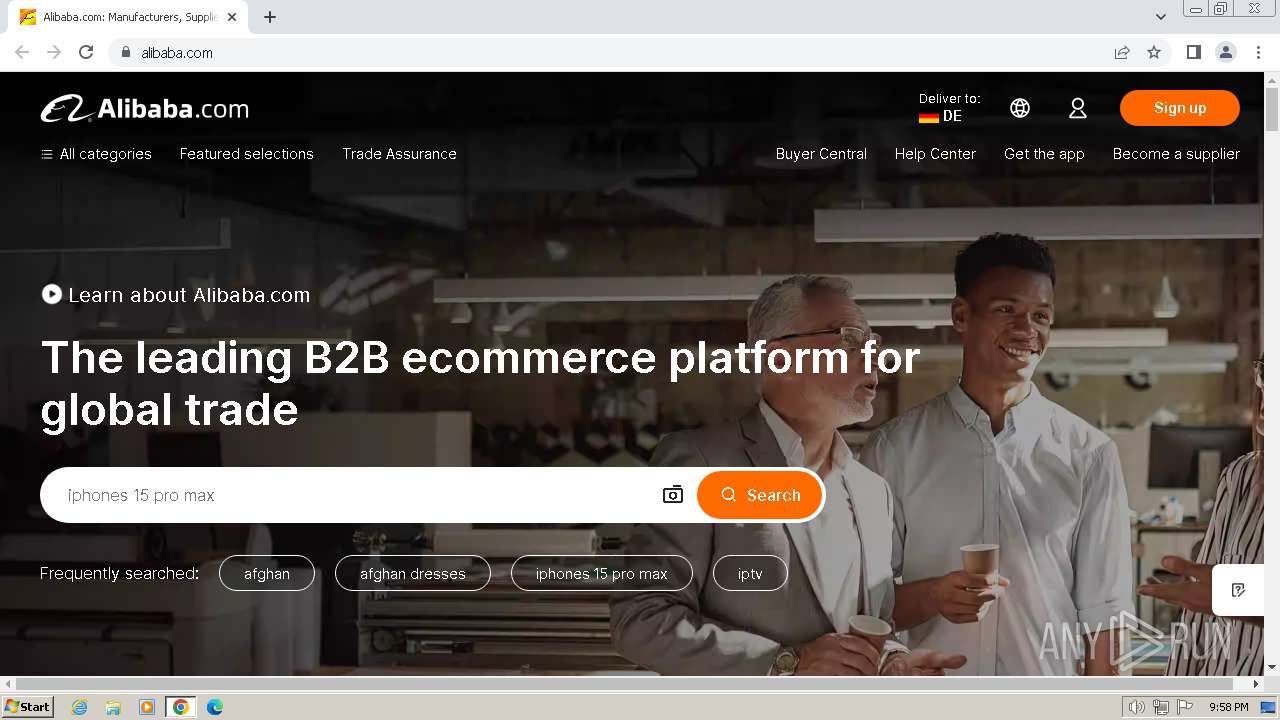
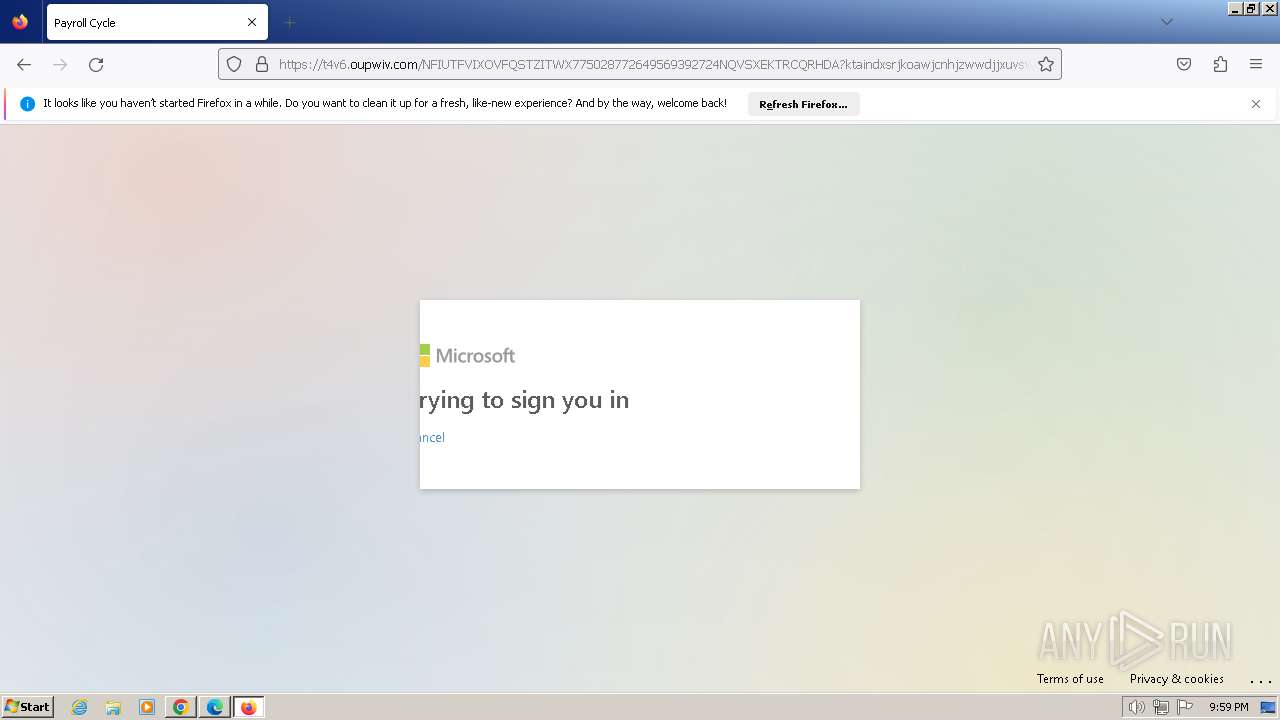
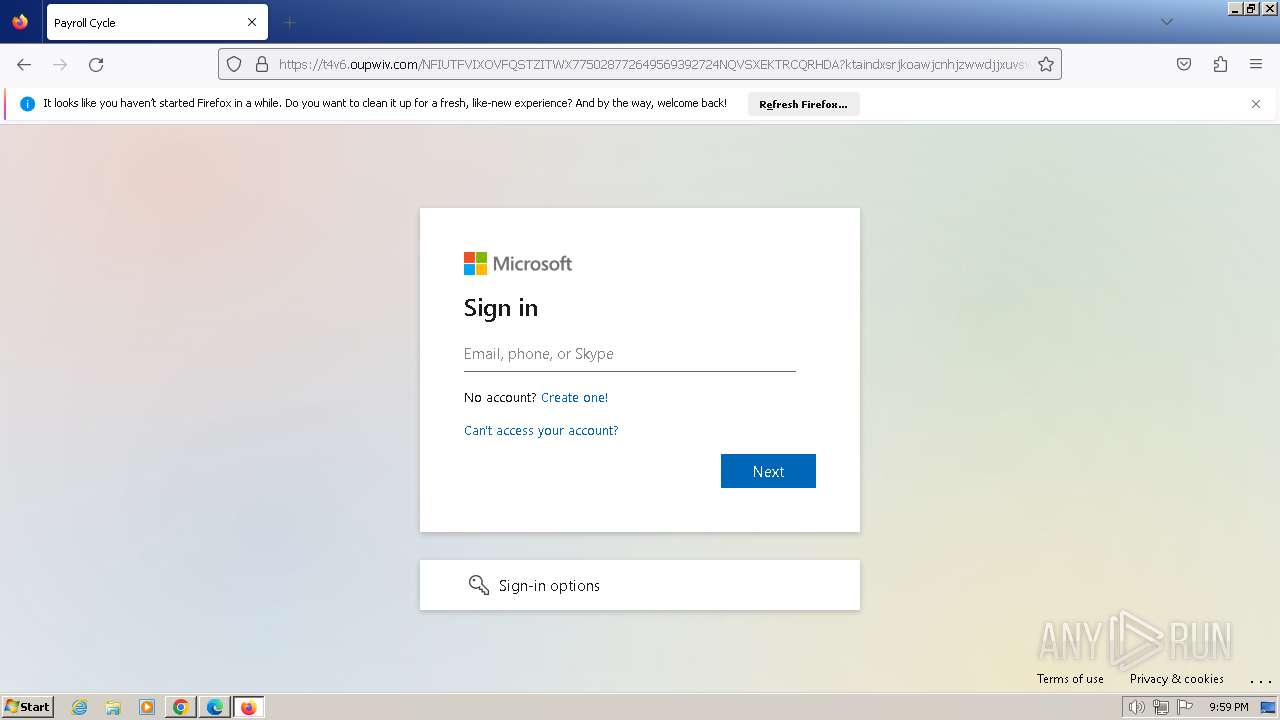
| Threats: | Tycoon 2FA is a phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) protections, particularly targeting Microsoft 365 and Gmail accounts. Its advanced evasion techniques and modular architecture make it a significant threat to organizations relying on MFA for security. |
| Analysis date: | June 21, 2024, 20:58:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B8FB35F0B92E66F02FF0A5BEF0AA5AE8 |
| SHA1: | D0F5AAA2C2D78F354A48E7F8FF774FAE2E910A08 |
| SHA256: | BCDCC5947DD297BDCE3D8C6BDFE3418E3A30EE34187CCDFFAC37EF44CF1DA7DC |
| SSDEEP: | 6:2f2LlY6xxIK8rQy7OkB5wV0zImxZpKk79yL695mHTht6Onkmm2O1i680dctP1p3N:2uuSx3oQSOkwmzhxZpZyW95m1tNO2Oo5 |
MALICIOUS
PHISHING has been detected (SURICATA)
- firefox.exe (PID: 2712)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- firefox.exe (PID: 1080)
- chrome.exe (PID: 3260)
- msedge.exe (PID: 2064)
- firefox.exe (PID: 2712)
Manual execution by a user
- msedge.exe (PID: 2064)
- firefox.exe (PID: 1080)
Executable content was dropped or overwritten
- firefox.exe (PID: 2712)
Drops the executable file immediately after the start
- firefox.exe (PID: 2712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
81
Monitored processes
44
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=3640 --field-trial-handle=1364,i,2860860906738639679,13343931104465535029,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 348 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1664 --field-trial-handle=1364,i,2860860906738639679,13343931104465535029,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 740 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2016 --field-trial-handle=1144,i,8048849257129729728,12703330543942780360,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 828 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2712.0.768611214\1535409474" -parentBuildID 20230710165010 -prefsHandle 1124 -prefMapHandle 1116 -prefsLen 28523 -prefMapSize 244195 -appDir "C:\Program Files\Mozilla Firefox\browser" - {8ecad513-f3ae-49d7-8130-25860dab5bf6} 2712 "\\.\pipe\gecko-crash-server-pipe.2712" 1228 d8aba20 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 115.0.2 Modules
| |||||||||||||||
| 936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=2964 --field-trial-handle=1144,i,8048849257129729728,12703330543942780360,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 980 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3768 --field-trial-handle=1364,i,2860860906738639679,13343931104465535029,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1000 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2260 --field-trial-handle=1364,i,2860860906738639679,13343931104465535029,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1080 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1420 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3416 --field-trial-handle=1364,i,2860860906738639679,13343931104465535029,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2140 --field-trial-handle=1364,i,2860860906738639679,13343931104465535029,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
33 406
Read events
33 253
Write events
141
Delete events
12
Modification events
| (PID) Process: | (3260) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3260) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3260) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3260) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3260) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3260) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3260) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3260) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3260) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3260) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
10
Suspicious files
643
Text files
149
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3260 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF4eb37.TMP | — | |
MD5:— | SHA256:— | |||
| 3260 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3260 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:825B582C78EC88D54C215EFDF1EAD639 | SHA256:367995D01A8F13E5C30C79499F86B034775BFD009D83DC97635DE438D47DFA37 | |||
| 3260 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\80a2ce9a-7711-43d3-bb77-fcc33949992e.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 3260 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF4ecdd.TMP | text | |
MD5:AD0DB8476493577A67FA94A162B646C4 | SHA256:304FB5B4FD83D4A9FF1EF4CF20232A1783169C148297BFE37ED24A1D22A74F2B | |||
| 3260 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF4eccd.TMP | text | |
MD5:ECD3386BCC950E73B86EB128A5F57622 | SHA256:C9A068EAFBC587EDFC89392F64DDD350EEB96C5CF195CDB030BAB8F6DD33833B | |||
| 3260 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF4f29a.TMP | — | |
MD5:— | SHA256:— | |||
| 3260 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3260 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:FA25AF7098FC1571F24F200A9D105D58 | SHA256:4F40C87070B7A151FB241CCF36E7027AA703C15CA0ACB0A1759DA07B2C318574 | |||
| 3260 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
186
DNS requests
438
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2064 | msedge.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?2abcb3c7da8e6dfe | unknown | — | — | unknown |
2712 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | unknown |
2712 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
2712 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | unknown |
2712 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
2712 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
2712 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2748 | chrome.exe | 74.125.128.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3260 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2748 | chrome.exe | 167.89.123.122:443 | u45250775.ct.sendgrid.net | SENDGRID | US | unknown |
2748 | chrome.exe | 172.67.184.246:443 | t4v6.oupwiv.com | CLOUDFLARENET | US | unknown |
2748 | chrome.exe | 104.21.36.2:443 | qznxs.p9j32.com | CLOUDFLARENET | — | unknown |
2748 | chrome.exe | 35.190.80.1:443 | a.nel.cloudflare.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
u45250775.ct.sendgrid.net |
| unknown |
t4v6.oupwiv.com |
| unknown |
qznxs.p9j32.com |
| unknown |
www.alibaba.com |
| whitelisted |
a.nel.cloudflare.com |
| whitelisted |
s.alicdn.com |
| whitelisted |
g.alicdn.com |
| whitelisted |
assets.alicdn.com |
| whitelisted |
insights.alibaba.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2748 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
1060 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
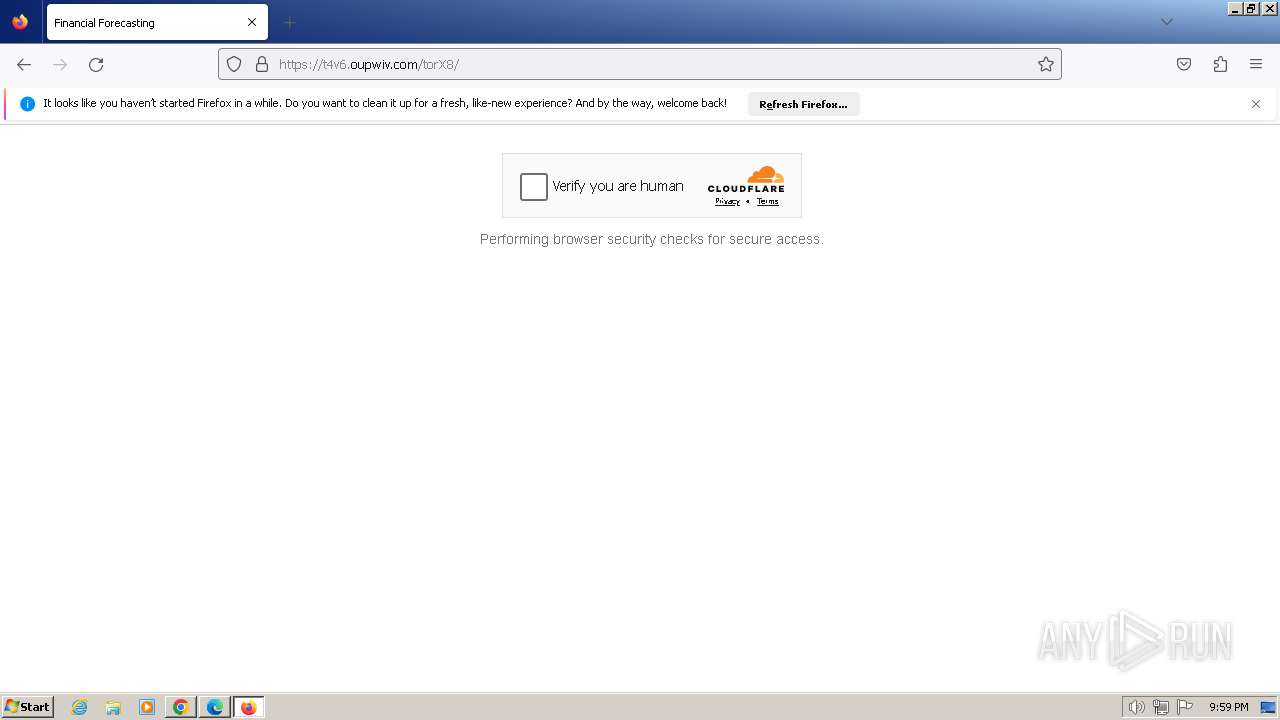
2712 | firefox.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
2712 | firefox.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain chain identified as Phishing (DadSec) |
2712 | firefox.exe | Not Suspicious Traffic | INFO [ANY.RUN] Client-Server Socket.IO CDN communication (cdn.socket .io) |
2712 | firefox.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain chain identified as Phishing (Tycoon 2FA) |