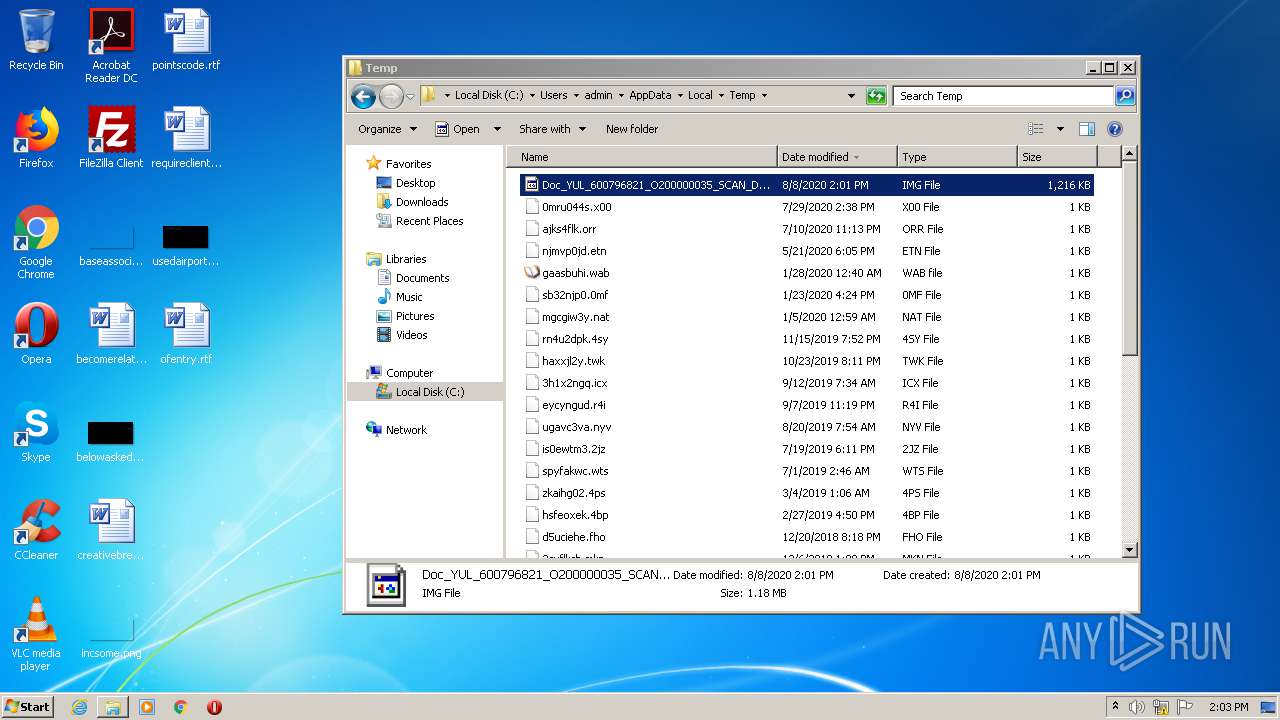
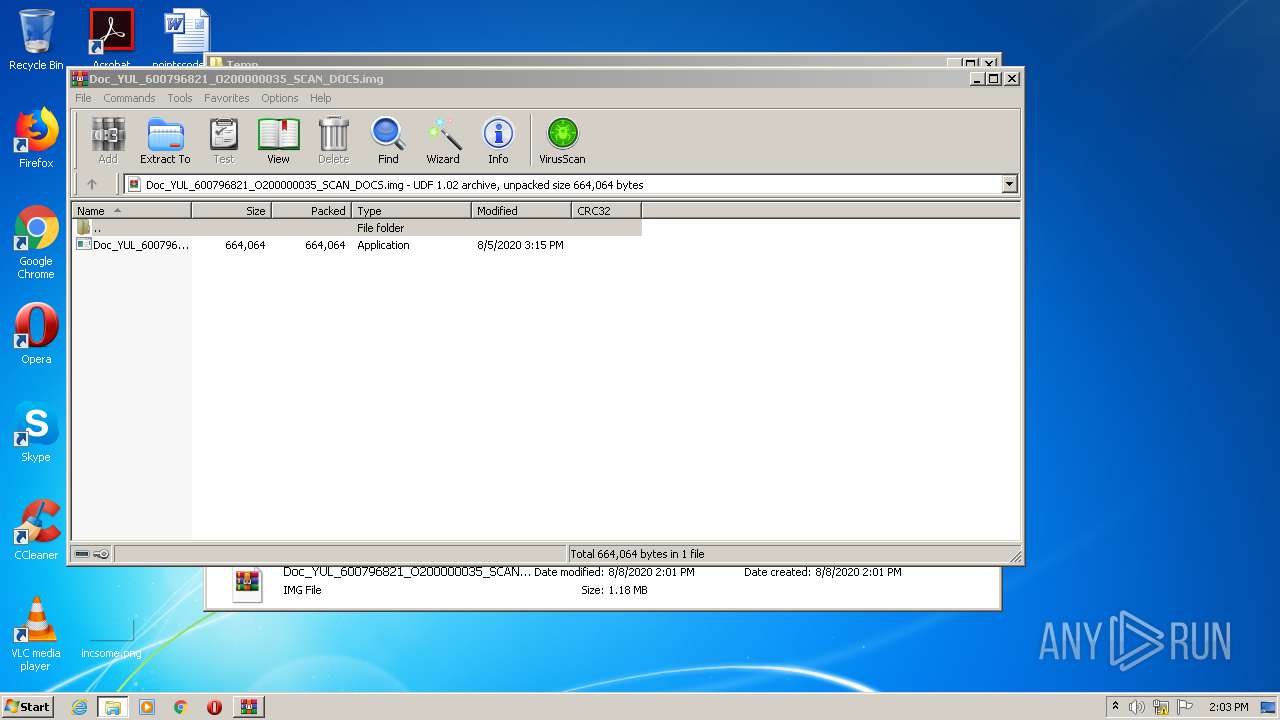
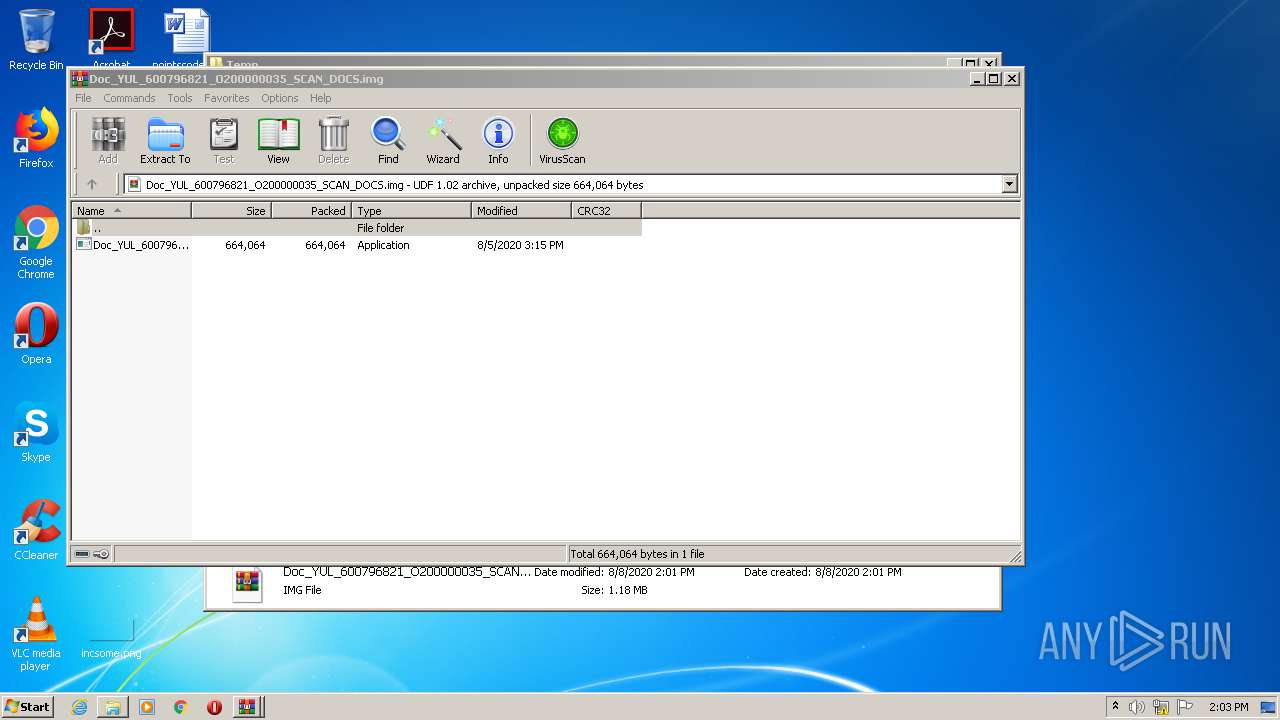
| download: | Doc_YUL_600796821_O200000035_SCAN_DOCS.img |
| Full analysis: | https://app.any.run/tasks/363b9a6c-9fd1-4764-984b-cb276db0eaa1 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | August 08, 2020, 13:01:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-iso9660-image |
| File info: | UDF filesystem data (version 1.5) 'DESKTOP' |
| MD5: | 47466161DA174888A942B85E450D8251 |
| SHA1: | 1731F1F1B83A9D3CCBE03AB417DC082187E89385 |
| SHA256: | BC8E5AB792B2768A08E9A0E605607AA2977EC614A7DD5891BD19A39A517CC984 |
| SSDEEP: | 6144:lkZWGYlDhZ//qtSMylCzLcYhRSSg478r61PPT2yEooUB1LR/XKITn5k:lkKjZASMyShG478o2yEor6I |
MALICIOUS
Application was dropped or rewritten from another process
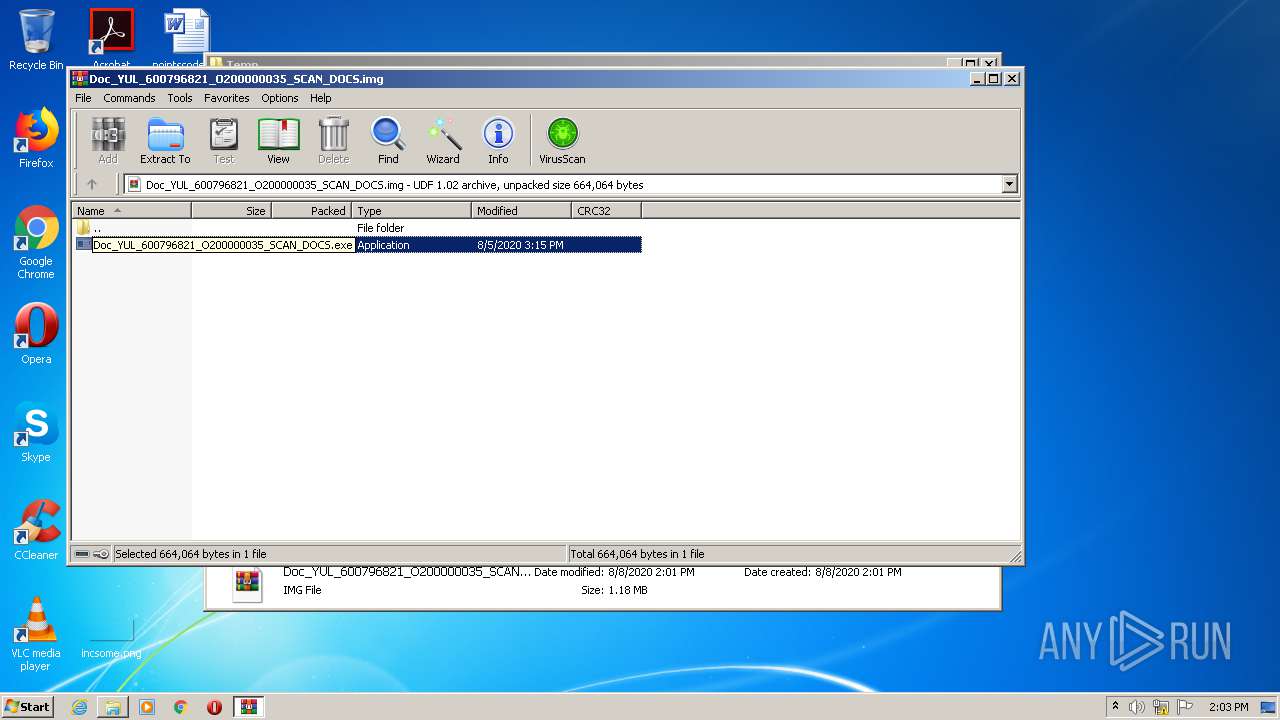
- Doc_YUL_600796821_O200000035_SCAN_DOCS.exe (PID: 3116)
- AddInProcess32.exe (PID: 2888)
AGENTTESLA was detected
- AddInProcess32.exe (PID: 2888)
Actions looks like stealing of personal data
- AddInProcess32.exe (PID: 2888)
SUSPICIOUS
Executable content was dropped or overwritten
- Doc_YUL_600796821_O200000035_SCAN_DOCS.exe (PID: 3116)
Creates files in the user directory
- AddInProcess32.exe (PID: 2888)
Reads Environment values
- AddInProcess32.exe (PID: 2888)
Reads the cookies of Mozilla Firefox
- AddInProcess32.exe (PID: 2888)
Reads the cookies of Google Chrome
- AddInProcess32.exe (PID: 2888)
INFO
Modifies the open verb of a shell class
- rundll32.exe (PID: 3624)
- rundll32.exe (PID: 2412)
Manual execution by user
- Rar.exe (PID: 2380)
- rundll32.exe (PID: 3624)
- Doc_YUL_600796821_O200000035_SCAN_DOCS.exe (PID: 3116)
- rundll32.exe (PID: 2412)
- WinRAR.exe (PID: 2116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .iso | | | ISO 9660 CD image (27.6) |
|---|---|---|
| .atn | | | Photoshop Action (27.1) |
| .gmc | | | Game Music Creator Music (6.1) |
EXIF
ISO
| VolumeName: | DESKTOP |
|---|---|
| VolumeBlockCount: | 599 |
| VolumeBlockSize: | 2048 |
| RootDirectoryCreateDate: | 2020:08:05 15:20:12-07:00 |
| VolumeSetName: | UNDEFINED |
| Software: | IMGBURN V2.5.8.0 - THE ULTIMATE IMAGE BURNER! |
| VolumeCreateDate: | 2020:08:05 15:20:12.00-07:00 |
| VolumeModifyDate: | 2020:08:05 15:20:12.00-07:00 |
Composite
| VolumeSize: | 1198 kB |
|---|
Total processes
57
Monitored processes
10
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1448 | "C:\Windows\System32\isoburn.exe" "C:\Users\admin\AppData\Local\Temp\Doc_YUL_600796821_O200000035_SCAN_DOCS.img" | C:\Windows\System32\isoburn.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Disc Image Burning Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2116 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Doc_YUL_600796821_O200000035_SCAN_DOCS.img" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2280 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Doc_YUL_600796821_O200000035_SCAN_DOCS.img | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2300 | "C:\Program Files\WinRAR\Rar.exe" "C:\Users\admin\AppData\Local\Temp\Doc_YUL_600796821_O200000035_SCAN_DOCS.img" | C:\Program Files\WinRAR\Rar.exe | — | rundll32.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: Command line RAR Exit code: 7 Version: 5.60.0 Modules
| |||||||||||||||
| 2380 | "C:\Program Files\WinRAR\Rar.exe" "C:\Users\admin\AppData\Local\Temp\Doc_YUL_600796821_O200000035_SCAN_DOCS.img" | C:\Program Files\WinRAR\Rar.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: Command line RAR Exit code: 7 Version: 5.60.0 Modules
| |||||||||||||||
| 2412 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Doc_YUL_600796821_O200000035_SCAN_DOCS.img | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2888 | "C:\Users\admin\AppData\Local\Temp\AddInProcess32.exe" | C:\Users\admin\AppData\Local\Temp\AddInProcess32.exe | Doc_YUL_600796821_O200000035_SCAN_DOCS.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 3116 | "C:\Users\admin\Desktop\Doc_YUL_600796821_O200000035_SCAN_DOCS.exe" | C:\Users\admin\Desktop\Doc_YUL_600796821_O200000035_SCAN_DOCS.exe | explorer.exe | ||||||||||||
User: admin Company: 5b!Rt(N9*Q4cf8~A6 Integrity Level: MEDIUM Description: Le8+@Fp5X2_s3!x Exit code: 0 Version: 5.7.10.12 Modules
| |||||||||||||||
| 3124 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Doc_YUL_600796821_O200000035_SCAN_DOCS.img" | C:\Program Files\WinRAR\WinRAR.exe | — | rundll32.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3624 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Doc_YUL_600796821_O200000035_SCAN_DOCS.img | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 772
Read events
3 240
Write events
524
Delete events
8
Modification events
| (PID) Process: | (2280) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\136\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2280) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\136\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\isoburn.exe,-350 |
Value: Disc Image File | |||
| (PID) Process: | (2280) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.img\OpenWithProgids |
| Operation: | write | Name: | Windows.IsoFile |
Value: | |||
| (PID) Process: | (2280) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\136\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\isoburn.exe,-352 |
Value: Windows Disc Image Burner | |||
| (PID) Process: | (2280) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\System32\isoburn.exe |
Value: Windows Disc Image Burner | |||
| (PID) Process: | (2280) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (2280) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (2280) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (2280) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (2280) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
Executable files
1
Suspicious files
1
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3124.12409\Doc_YUL_600796821_O200000035_SCAN_DOCS.exe | — | |
MD5:— | SHA256:— | |||
| 3624 | rundll32.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Explorer\thumbcache_idx.db | binary | |
MD5:— | SHA256:— | |||
| 2888 | AddInProcess32.exe | C:\Users\admin\AppData\Roaming\vnpe5b0e.p1n\Firefox\Profiles\qldyz51w.default\cookies.sqlite | sqlite | |
MD5:— | SHA256:— | |||
| 2888 | AddInProcess32.exe | C:\Users\admin\AppData\Roaming\vnpe5b0e.p1n\Chrome\Default\Cookies | sqlite | |
MD5:— | SHA256:— | |||
| 3116 | Doc_YUL_600796821_O200000035_SCAN_DOCS.exe | C:\Users\admin\AppData\Local\Temp\AddInProcess32.exe | executable | |
MD5:6A673BFC3B67AE9782CB31AF2F234C68 | SHA256:978A4093058AA2EBF05DC353897D90D950324389879B57741B64160825B5EC0E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
7
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2888 | AddInProcess32.exe | 208.91.198.143:587 | smtp.faithhopaendimages.com | PDR | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
smtp.faithhopaendimages.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2888 | AddInProcess32.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |
2888 | AddInProcess32.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |
2888 | AddInProcess32.exe | A Network Trojan was detected | ET TROJAN AgentTesla Exfil Via SMTP |
2888 | AddInProcess32.exe | A Network Trojan was detected | AV TROJAN Win.Keylogger.AgentTesla SMTP Activity |
2888 | AddInProcess32.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |
2 ETPRO signatures available at the full report