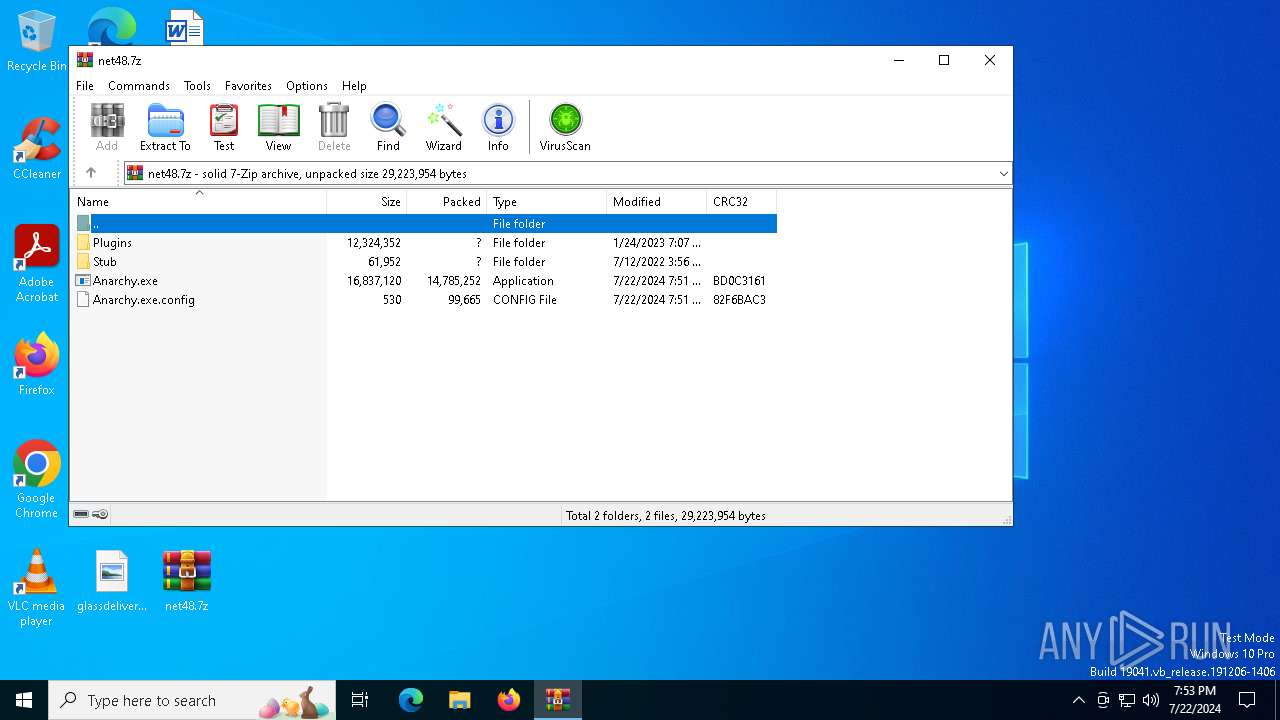
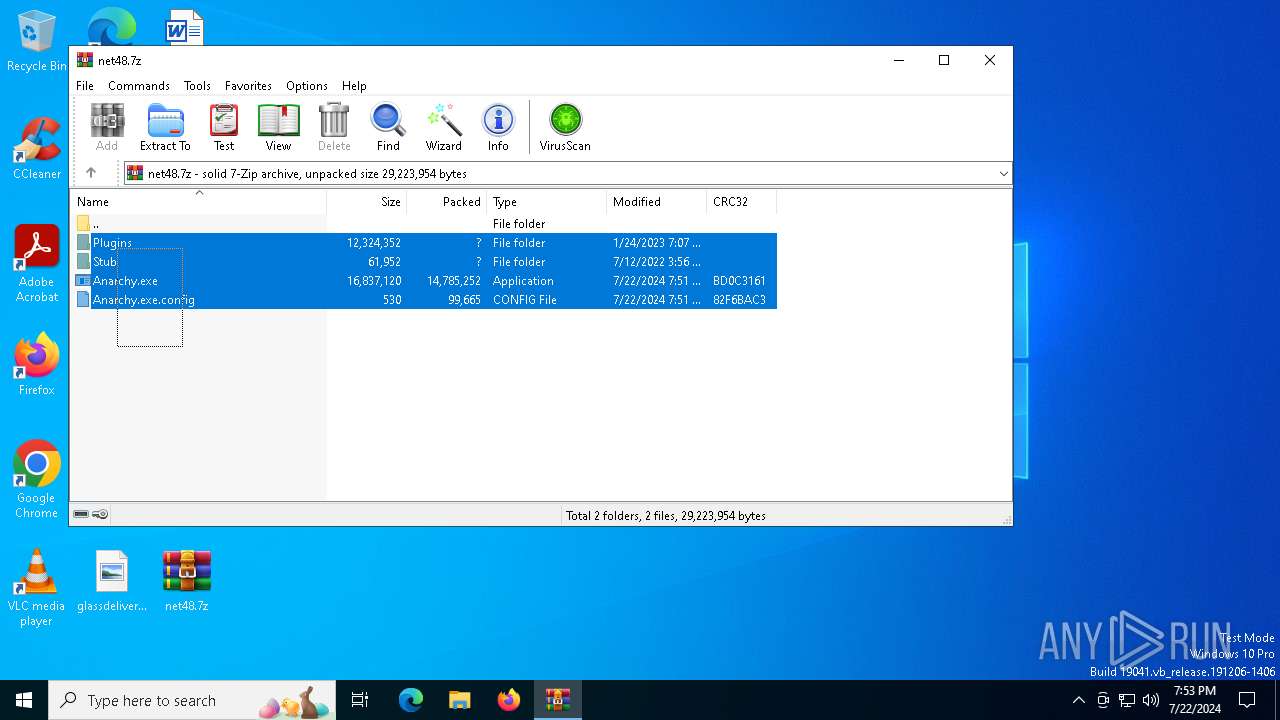
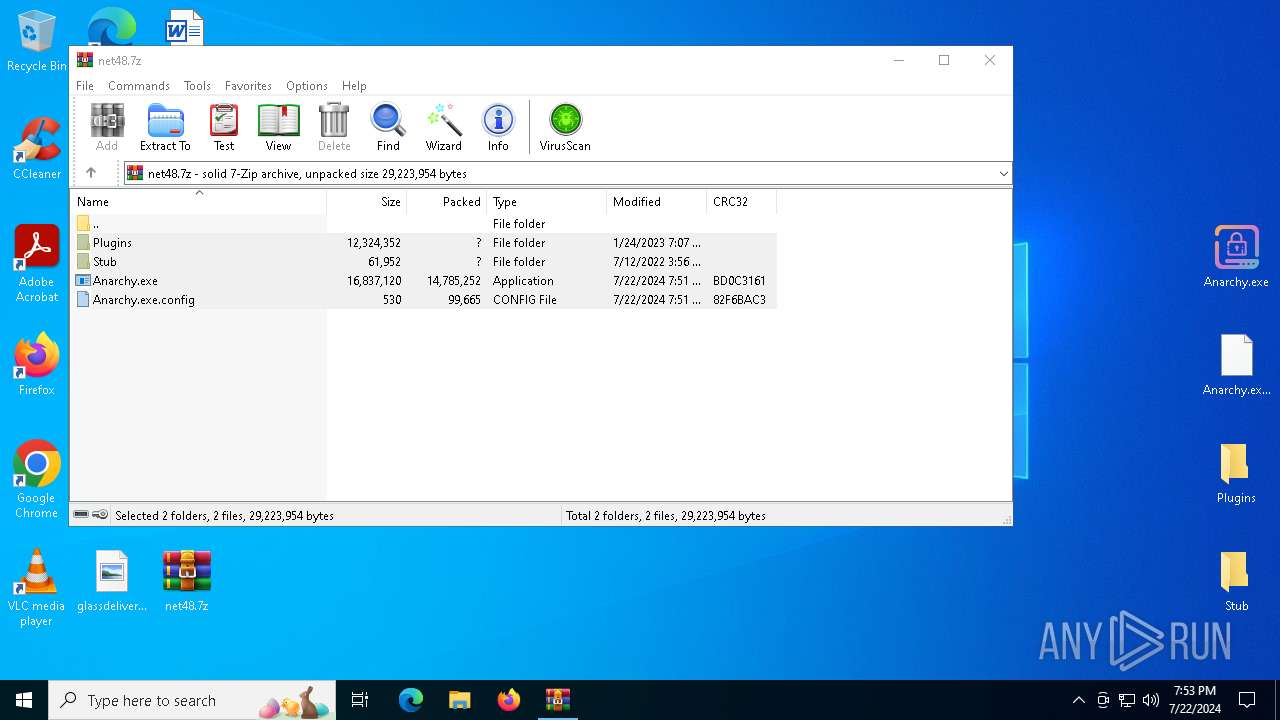
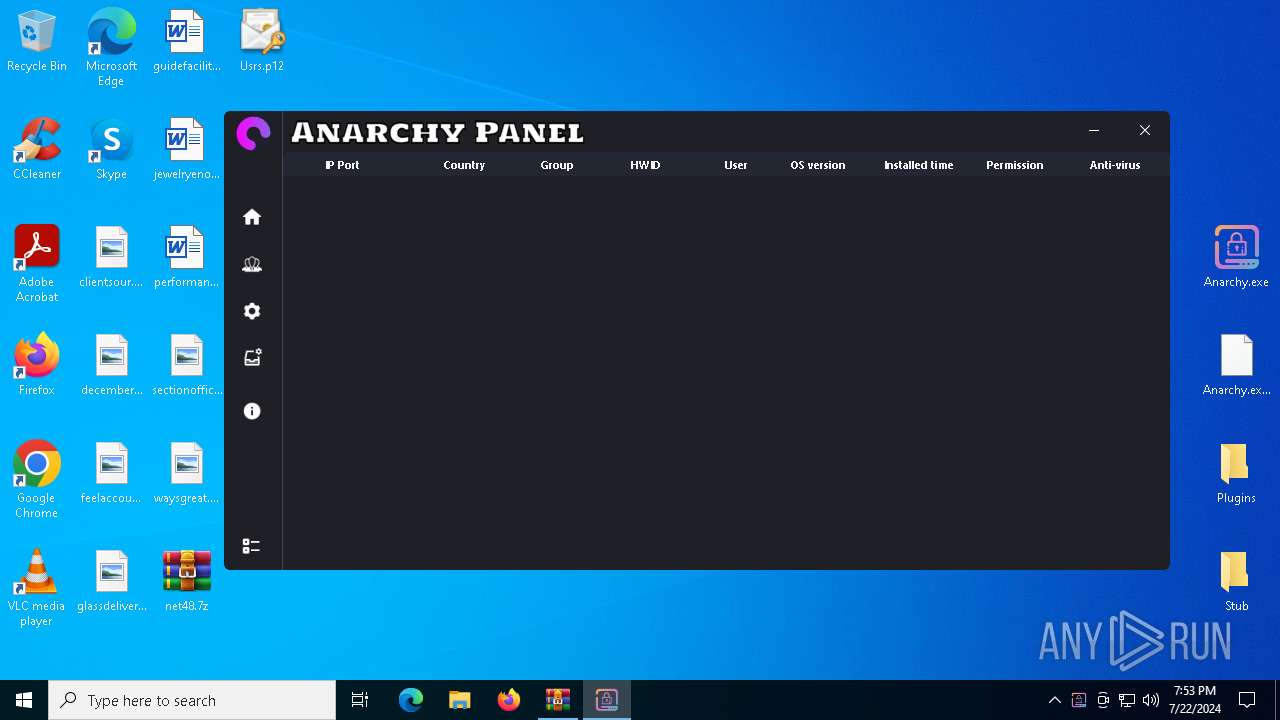
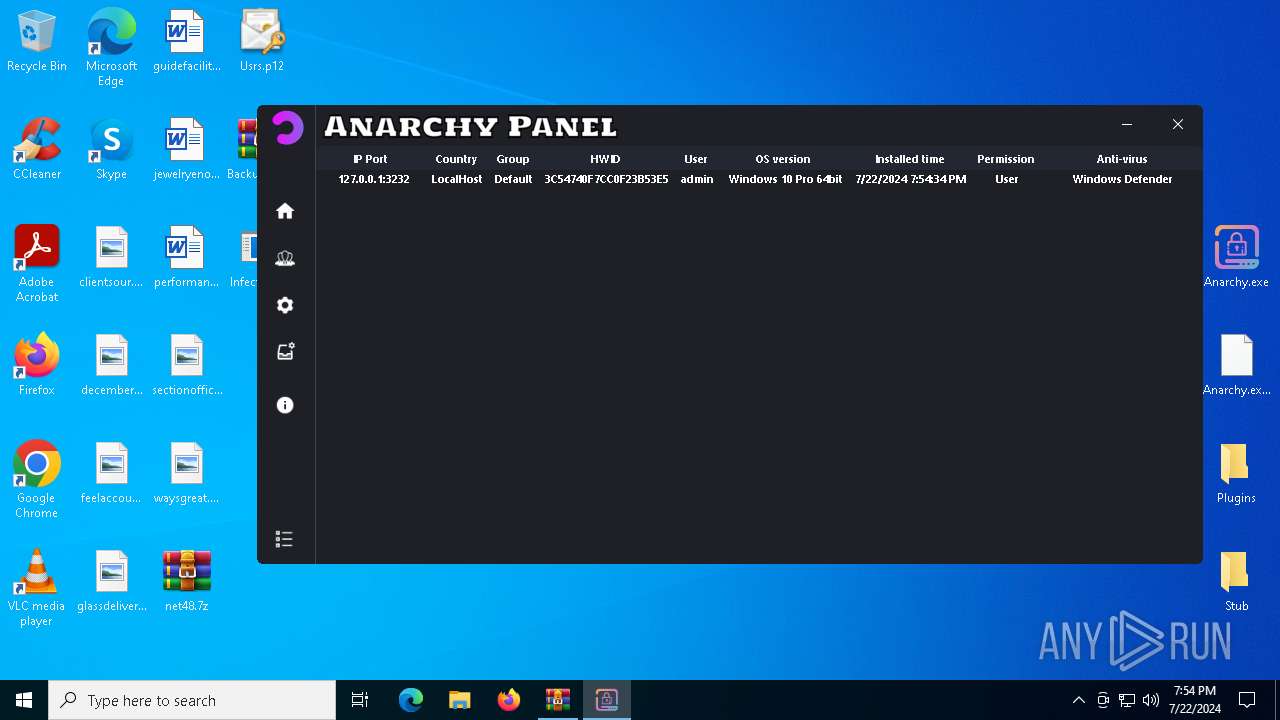
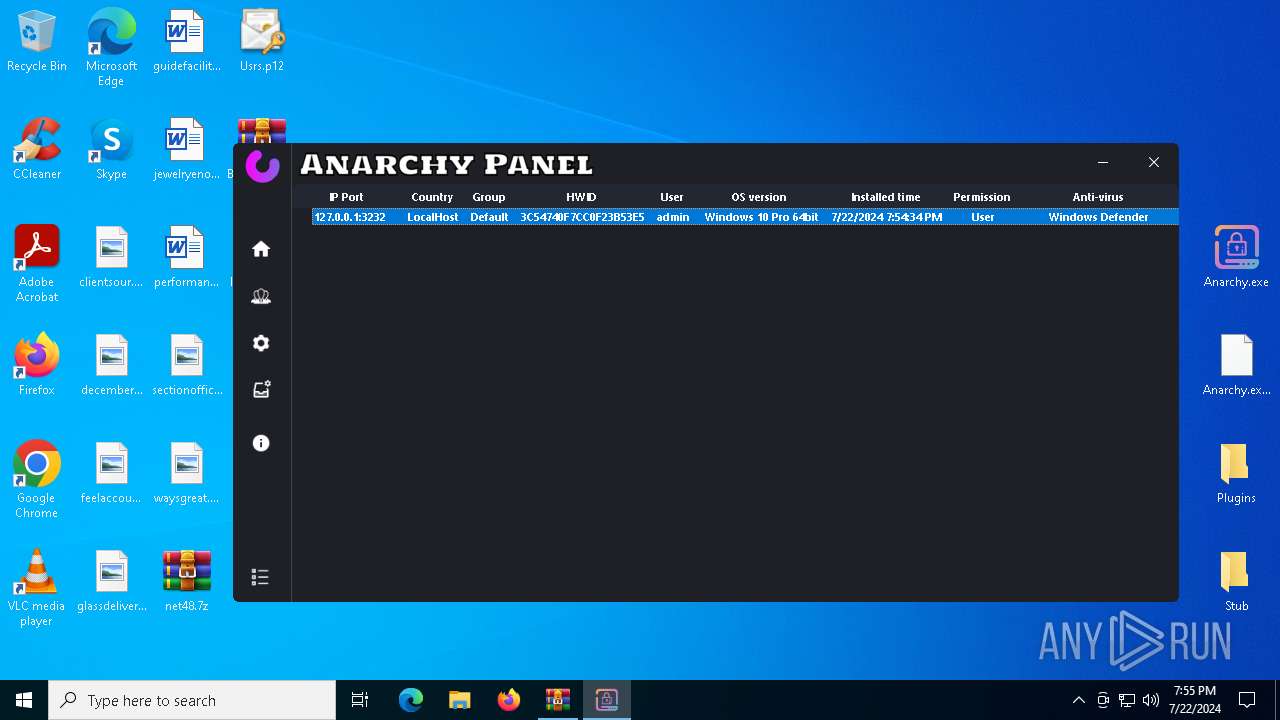
| File name: | net48.7z |
| Full analysis: | https://app.any.run/tasks/3a2171d5-017a-4c66-b8a4-accbe8155b23 |
| Verdict: | Malicious activity |
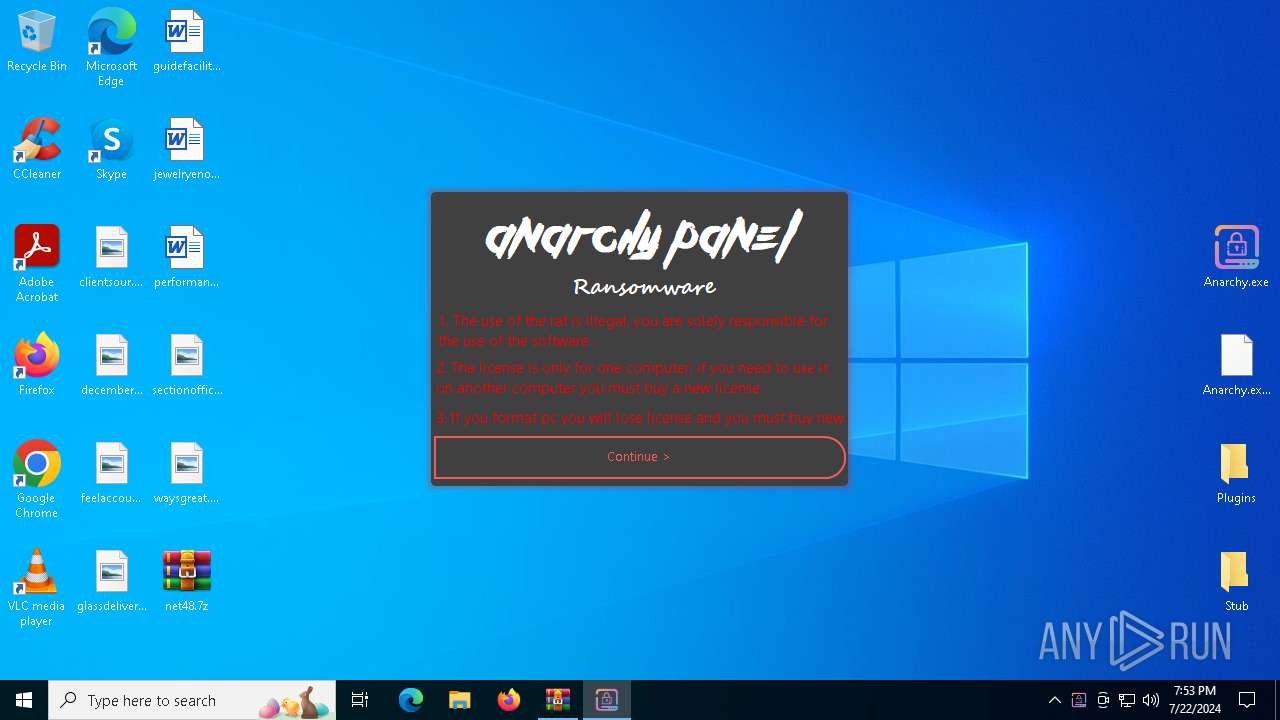
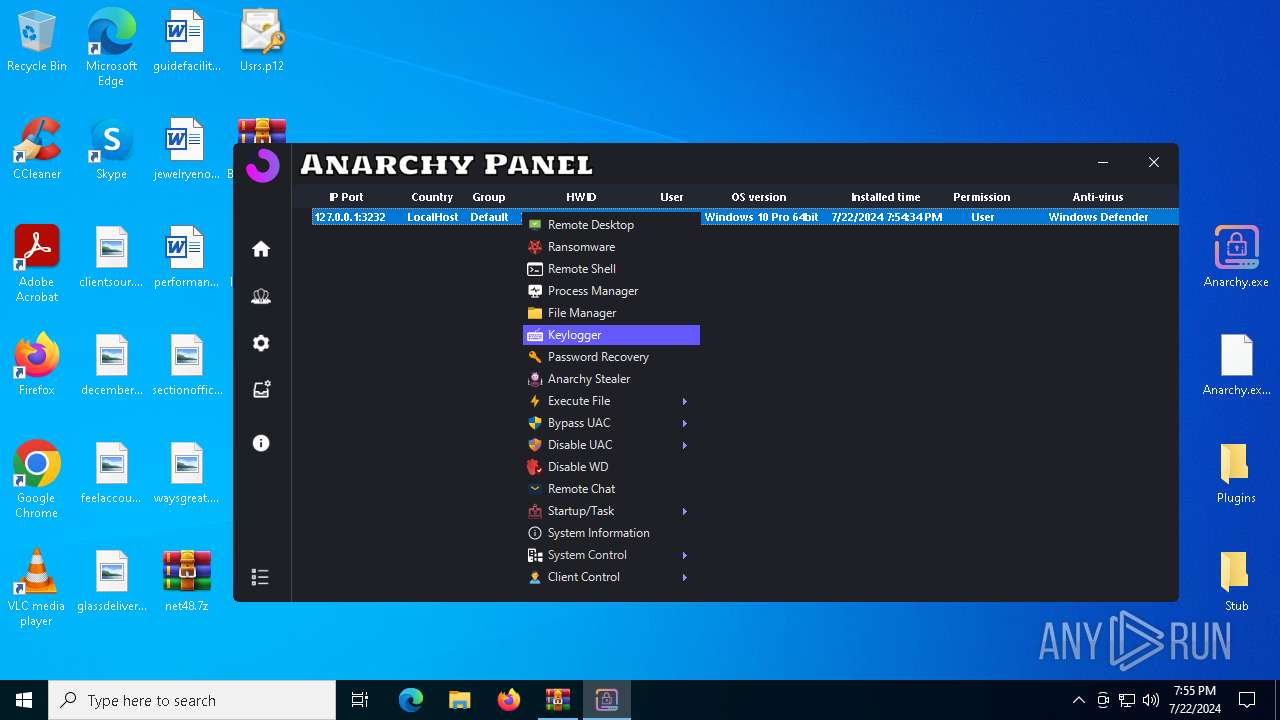
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | July 22, 2024, 19:53:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 321233ED8F1D9280CF4235A71D7CF634 |
| SHA1: | 3C85ED4D7258ED9F35B5F82F1533B966D57D39D0 |
| SHA256: | BC57A717D4497BB7793D8CA57D7CCE9E2E08A35F5CEF8B590B088ECD2D783449 |
| SSDEEP: | 98304:RIcLdlfZUuZxDArBZFXsyJKgah5mEpBa7I22guYPzOXwOPDN6kICR4vudsaaqiTC:LifrC5F9n0YXq03w0HvcGYw4o5XFqhS |
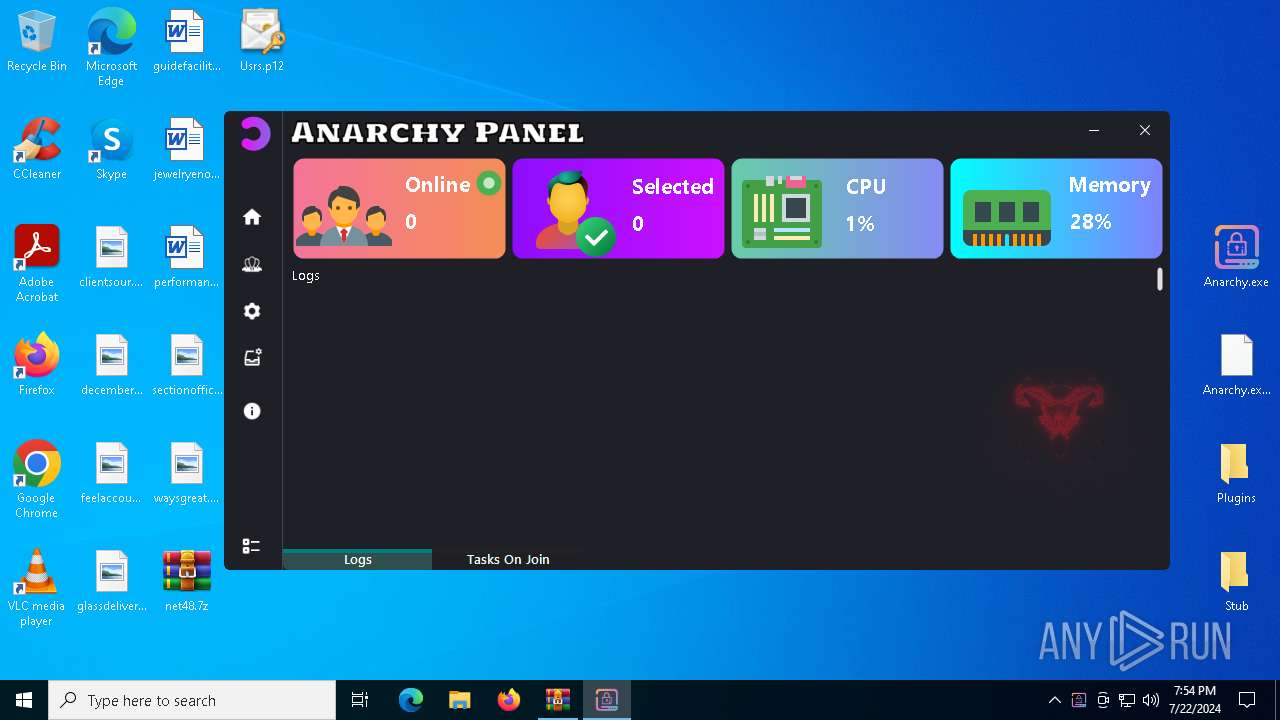
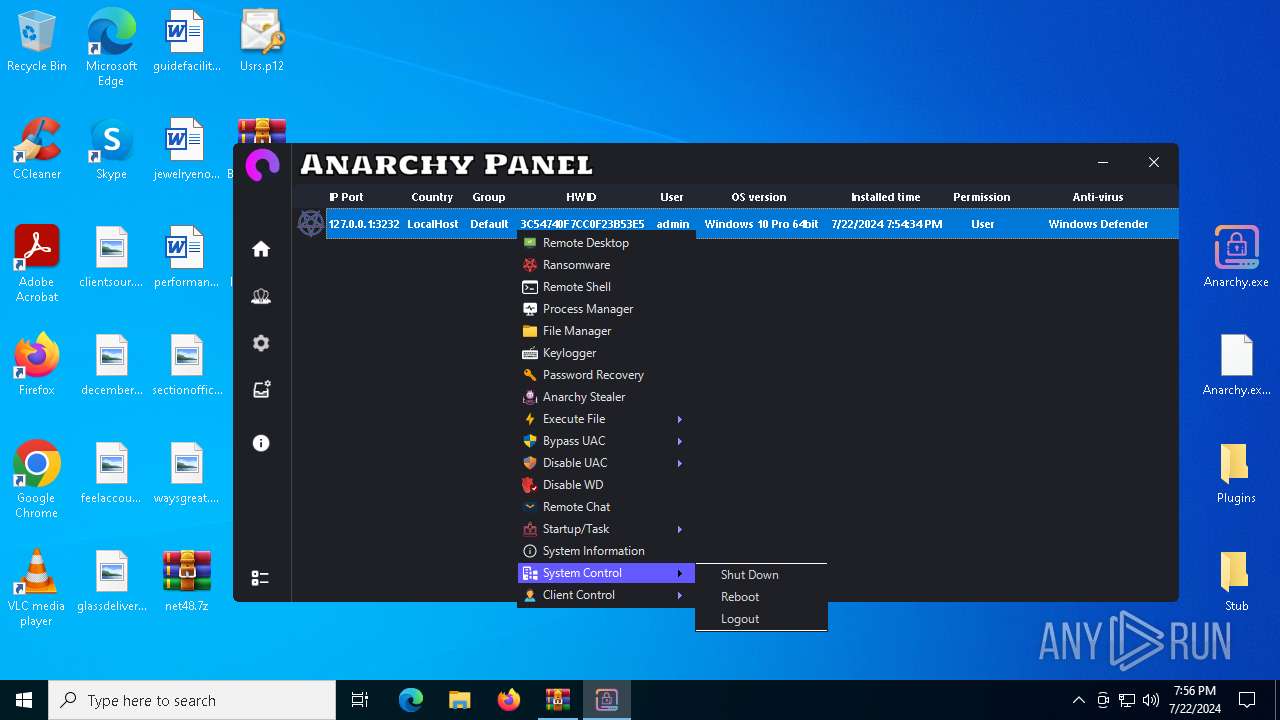
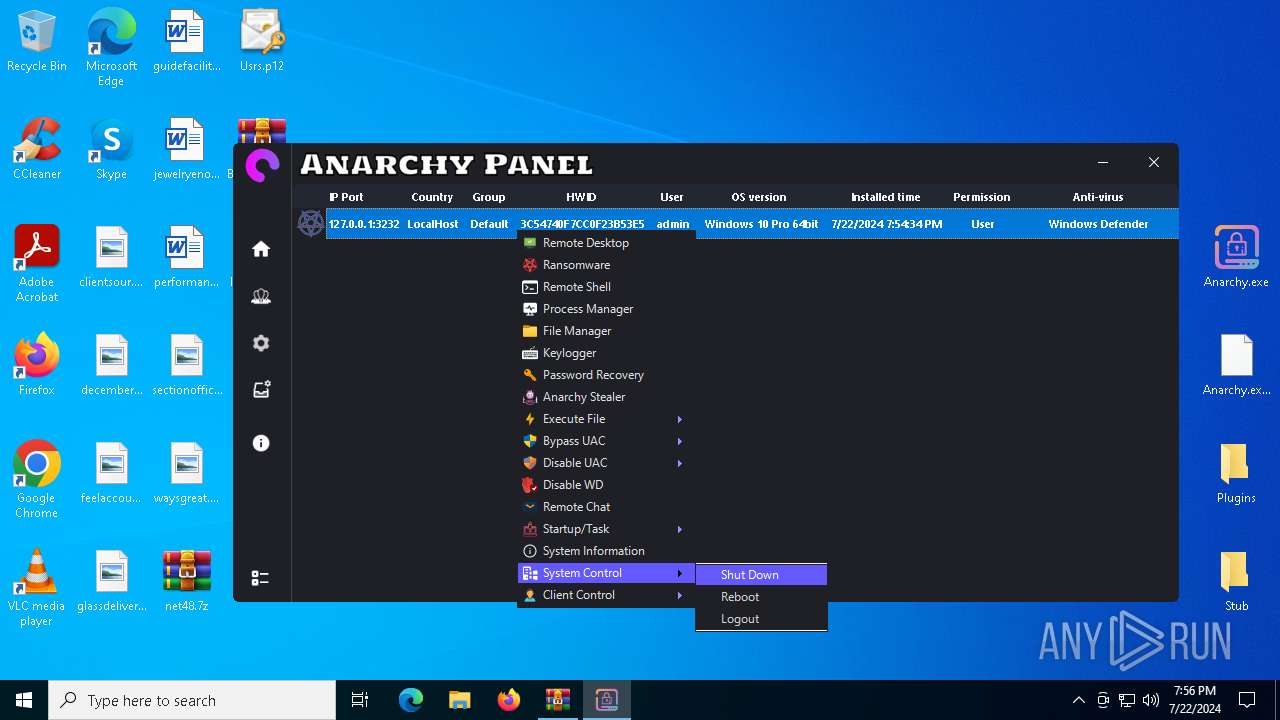
MALICIOUS
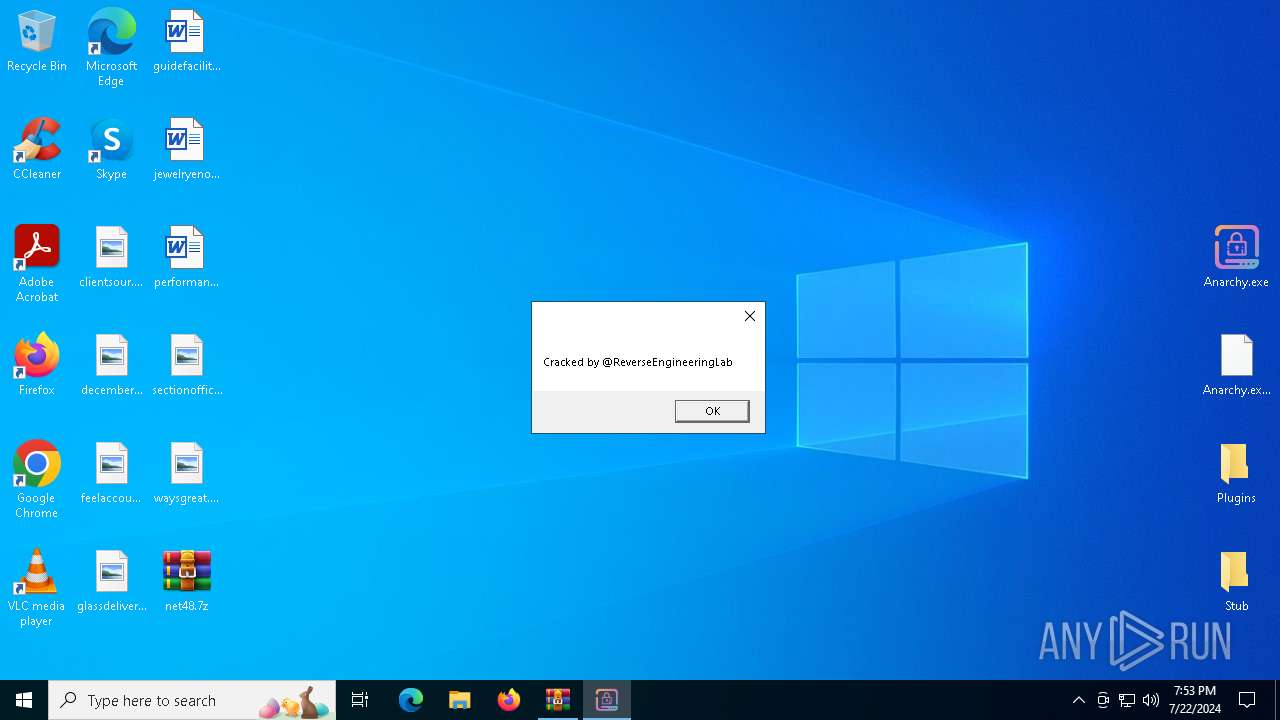
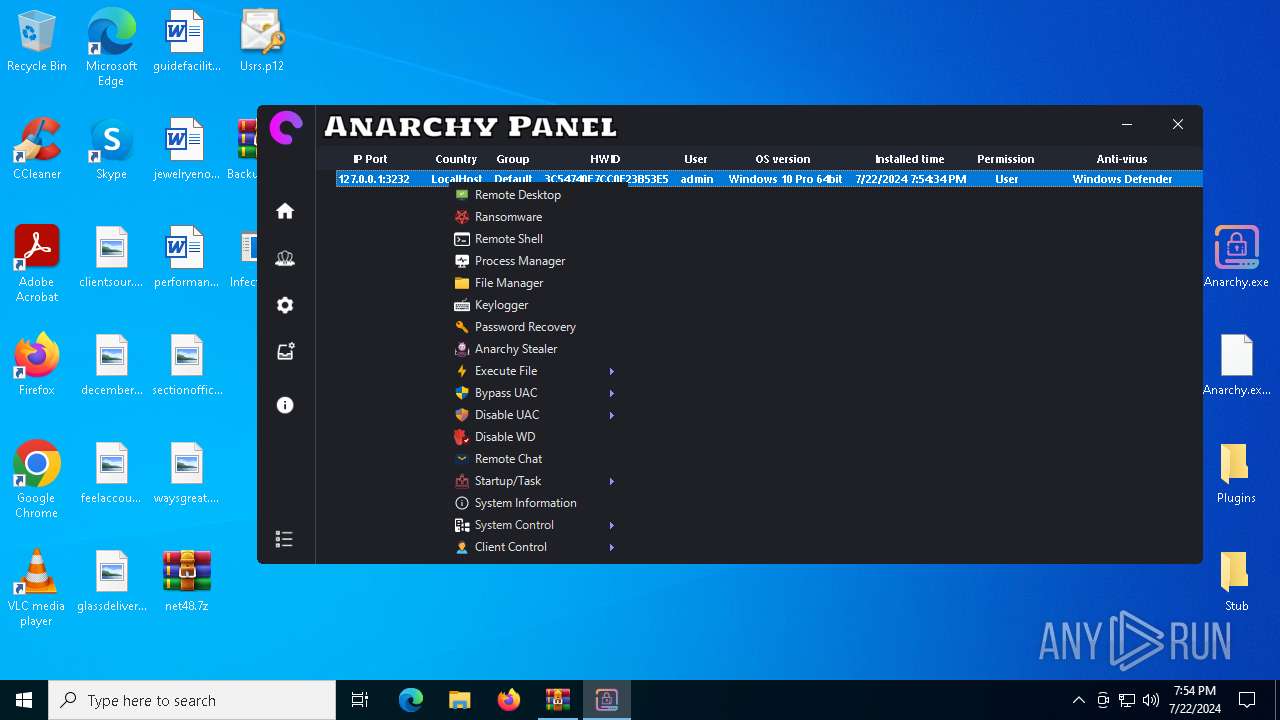
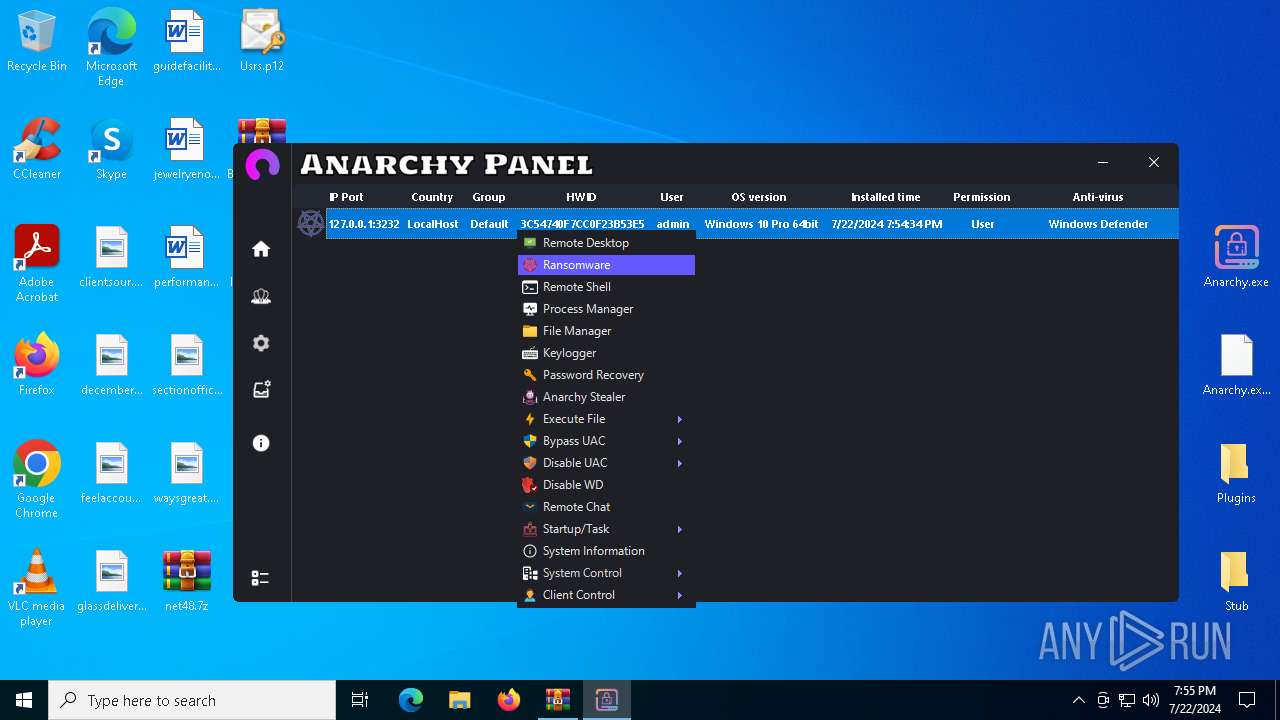
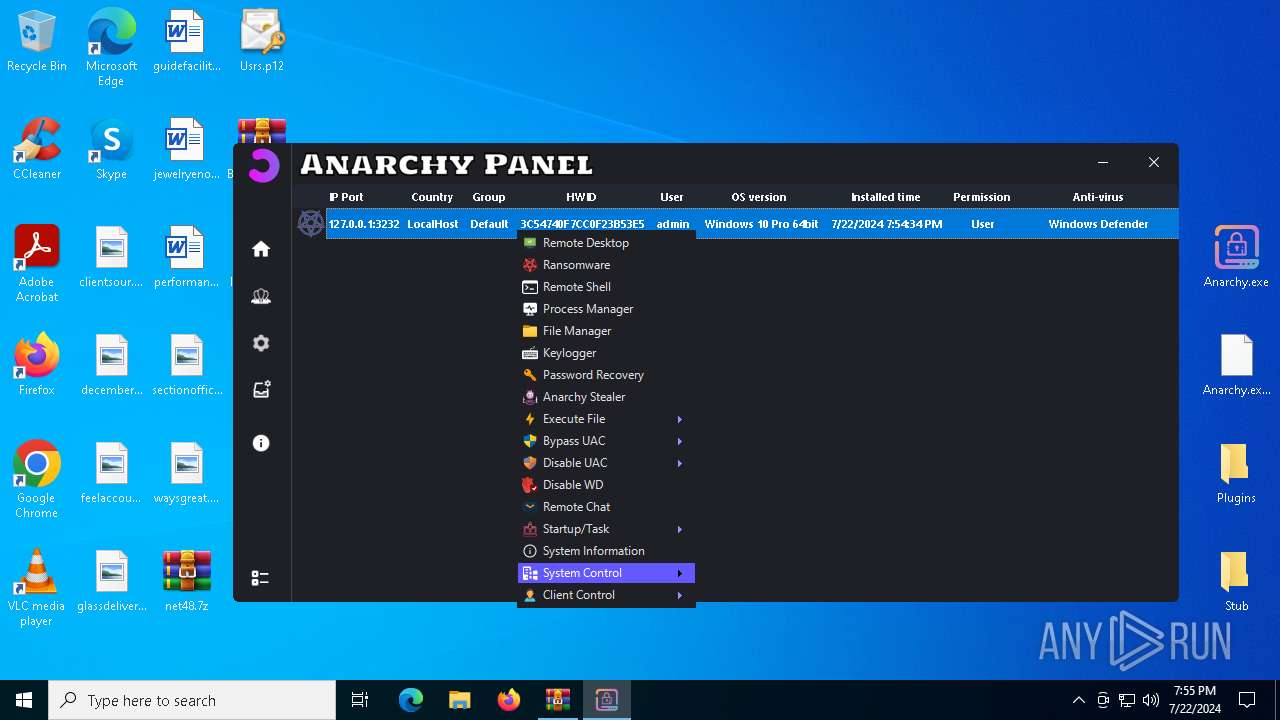
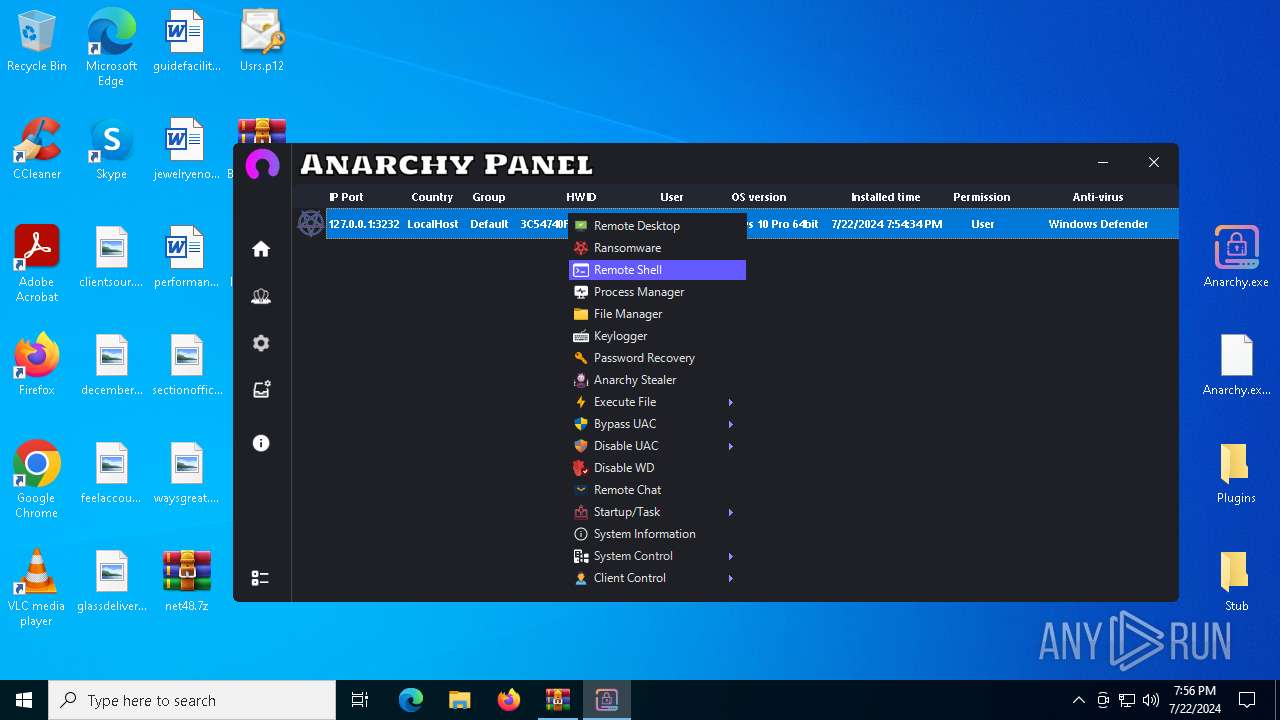
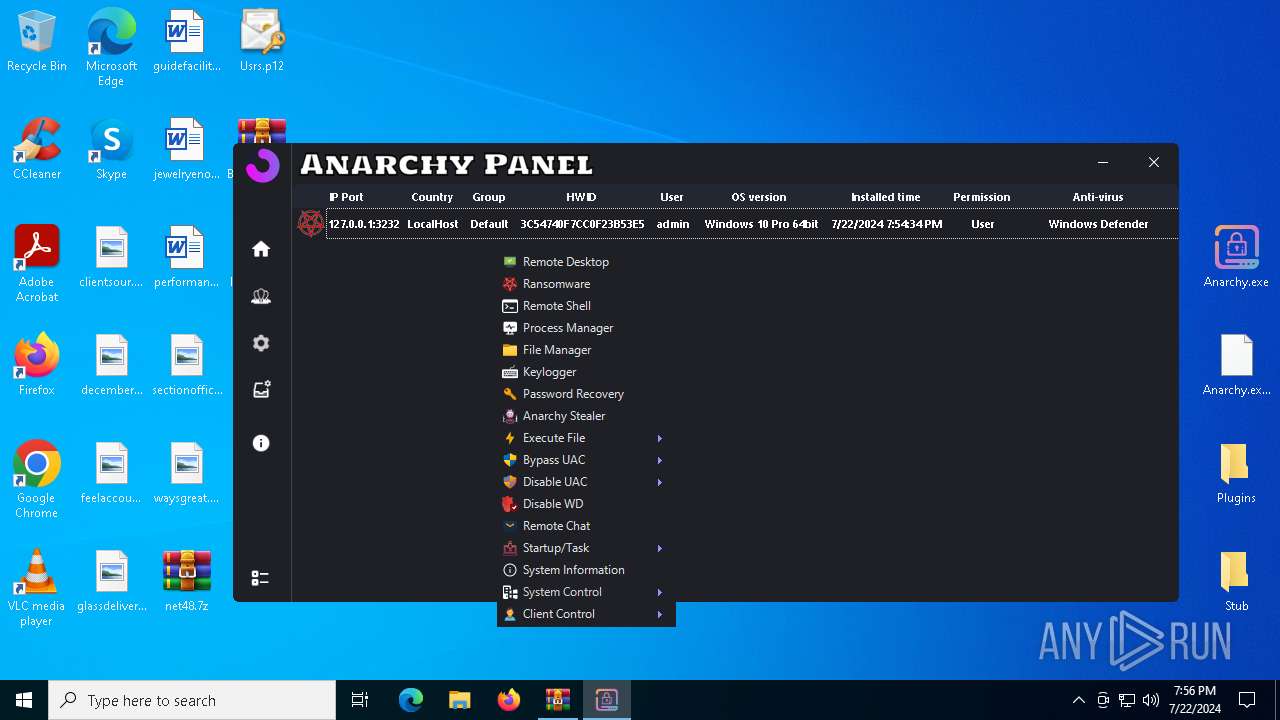
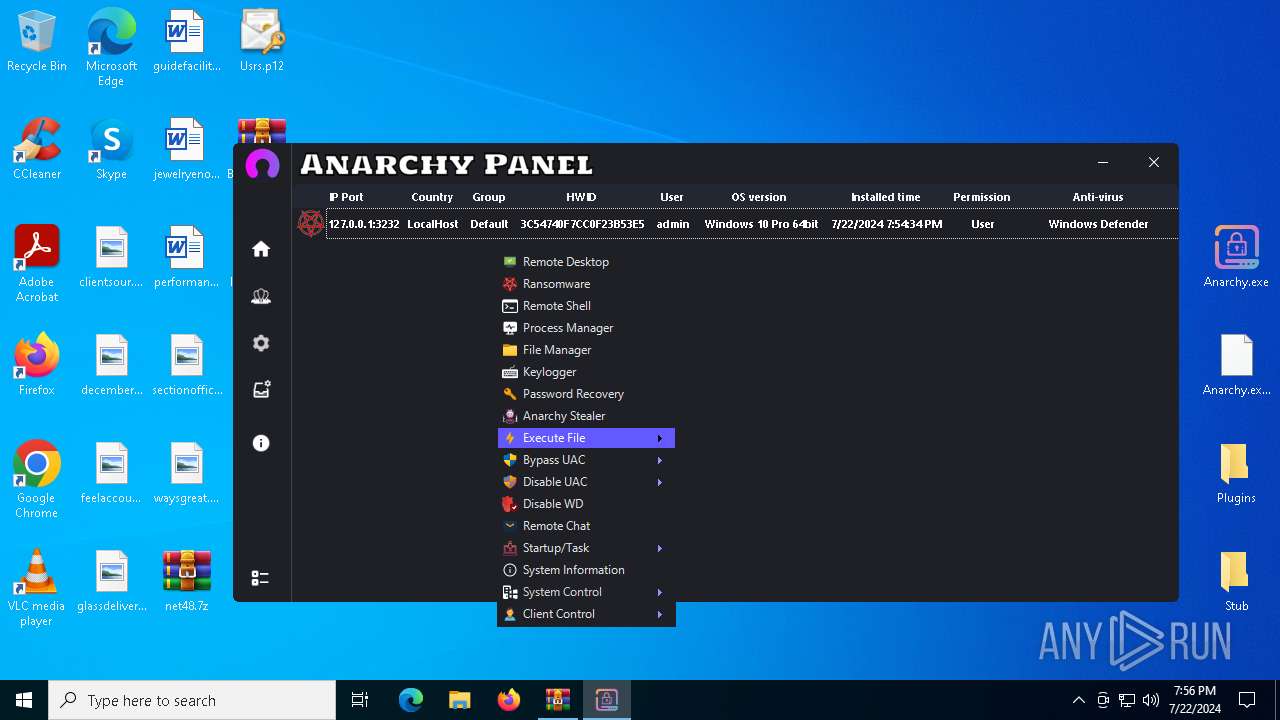
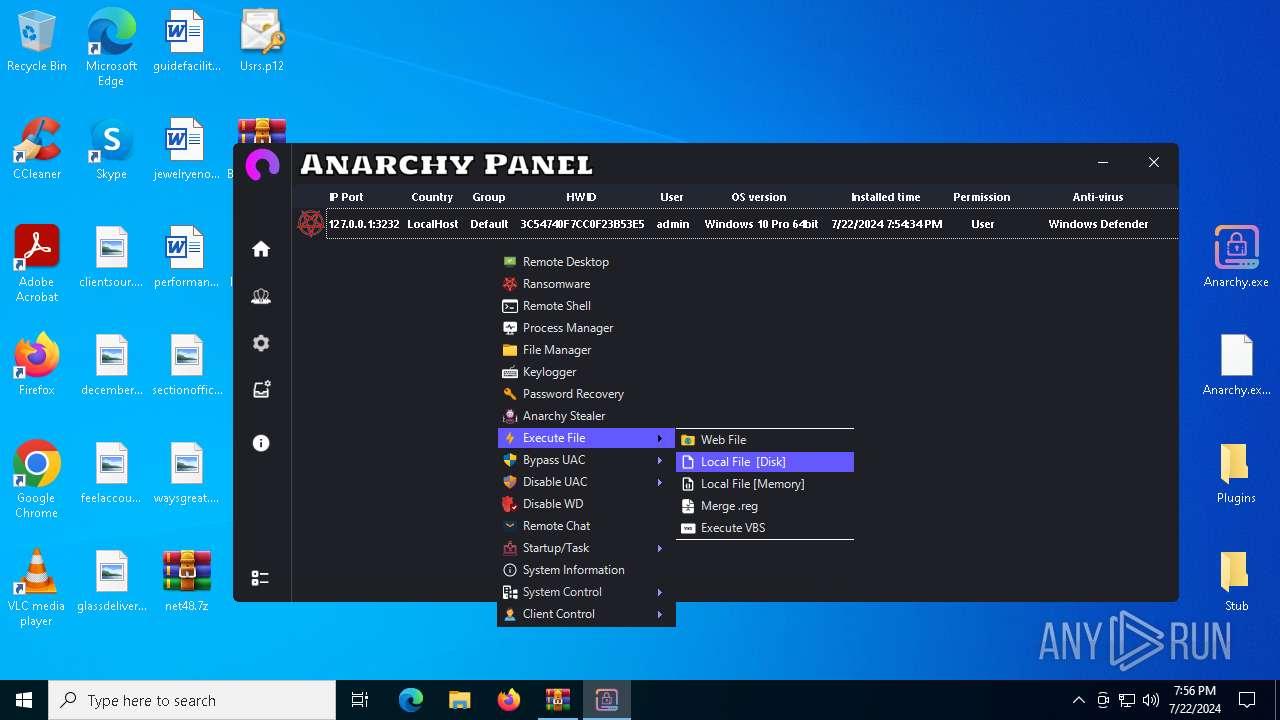
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4052)
- Infected.exe (PID: 5532)
ASYNCRAT has been detected (YARA)
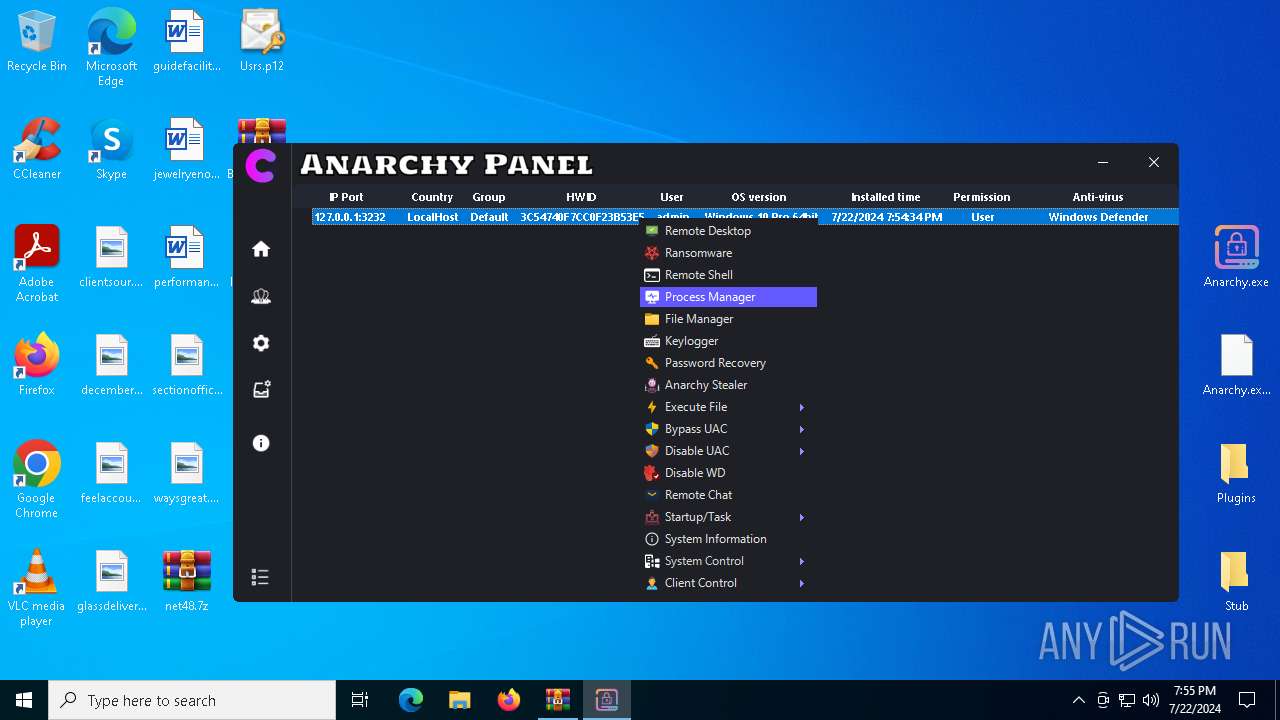
- Anarchy.exe (PID: 4020)
- Infected.exe (PID: 5532)
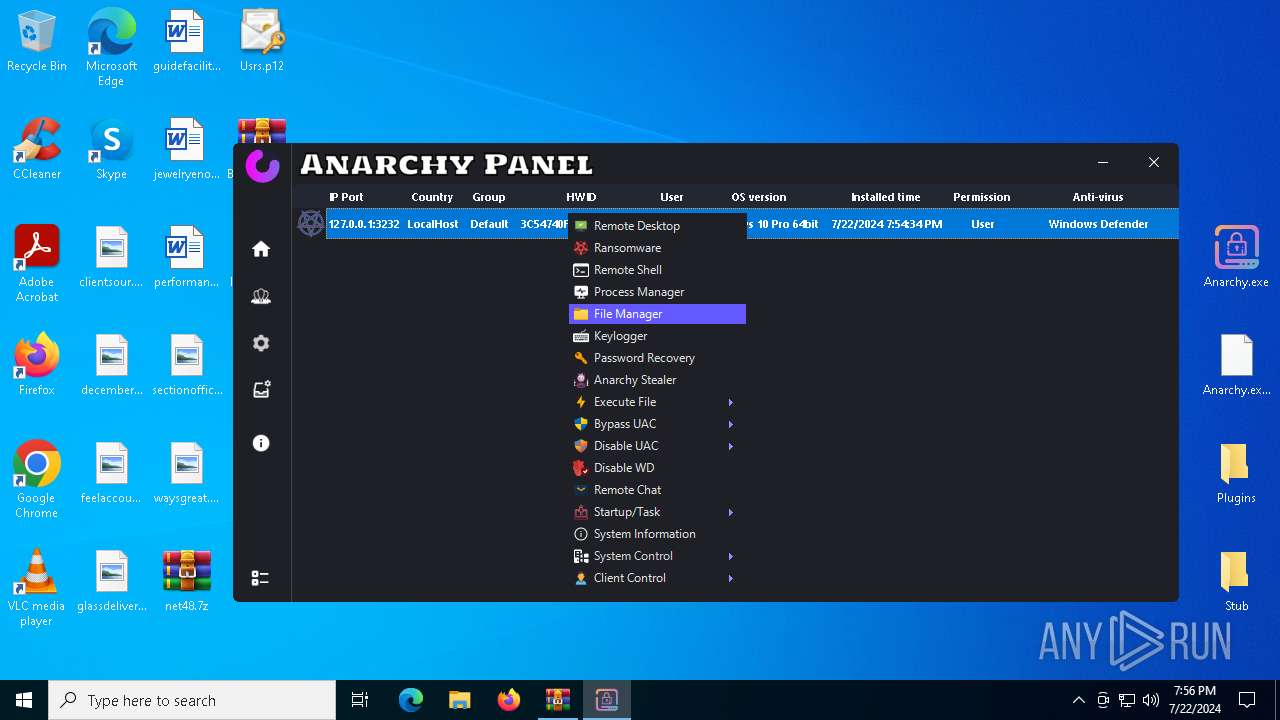
Steals credentials from Web Browsers
- Infected.exe (PID: 5532)
Actions looks like stealing of personal data
- Infected.exe (PID: 5532)
SUSPICIOUS
Reads security settings of Internet Explorer
- Anarchy.exe (PID: 4020)
There is functionality for VM detection (antiVM strings)
- Anarchy.exe (PID: 4020)
The process checks if it is being run in the virtual environment
- Anarchy.exe (PID: 4020)
Creates file in the systems drive root
- Anarchy.exe (PID: 4020)
There is functionality for capture public ip (YARA)
- Anarchy.exe (PID: 4020)
There is functionality for taking screenshot (YARA)
- Anarchy.exe (PID: 4020)
Reads Microsoft Outlook installation path
- Anarchy.exe (PID: 4020)
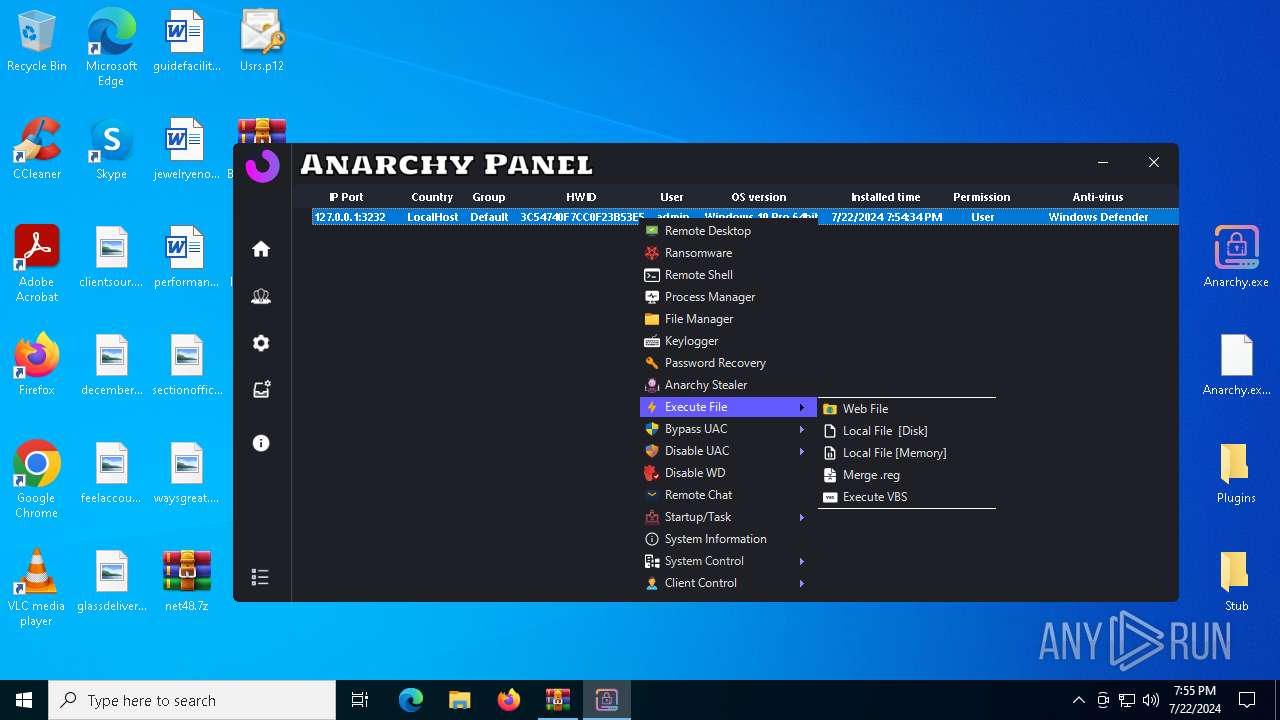
Executable content was dropped or overwritten
- Infected.exe (PID: 5532)
INFO
Checks supported languages
- Anarchy.exe (PID: 4020)
- Infected.exe (PID: 5532)
Creates files or folders in the user directory
- Anarchy.exe (PID: 4020)
- Infected.exe (PID: 5532)
Reads the computer name
- Anarchy.exe (PID: 4020)
- Infected.exe (PID: 5532)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4052)
Manual execution by a user
- Anarchy.exe (PID: 4020)
- Infected.exe (PID: 5532)
Reads the machine GUID from the registry
- Infected.exe (PID: 5532)
- Anarchy.exe (PID: 4020)
Reads Environment values
- Anarchy.exe (PID: 4020)
- Infected.exe (PID: 5532)
Reads the software policy settings
- Infected.exe (PID: 5532)
- slui.exe (PID: 4328)
Checks proxy server information
- slui.exe (PID: 4328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
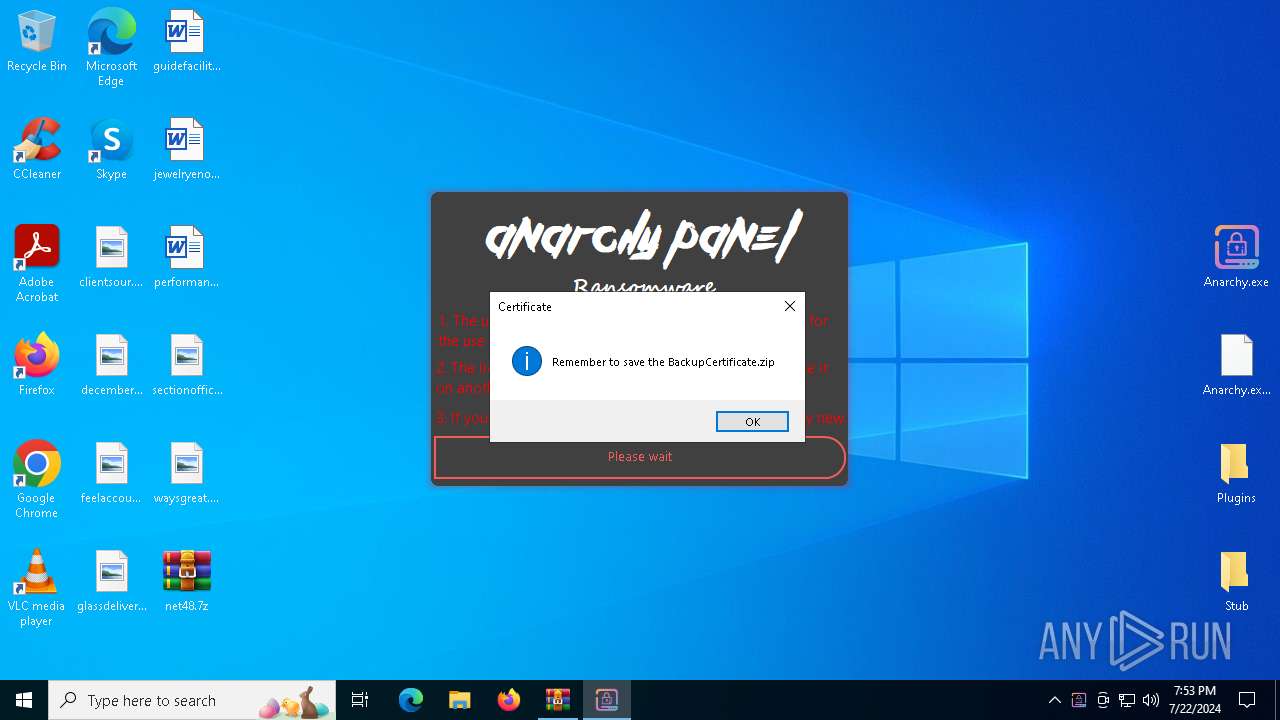
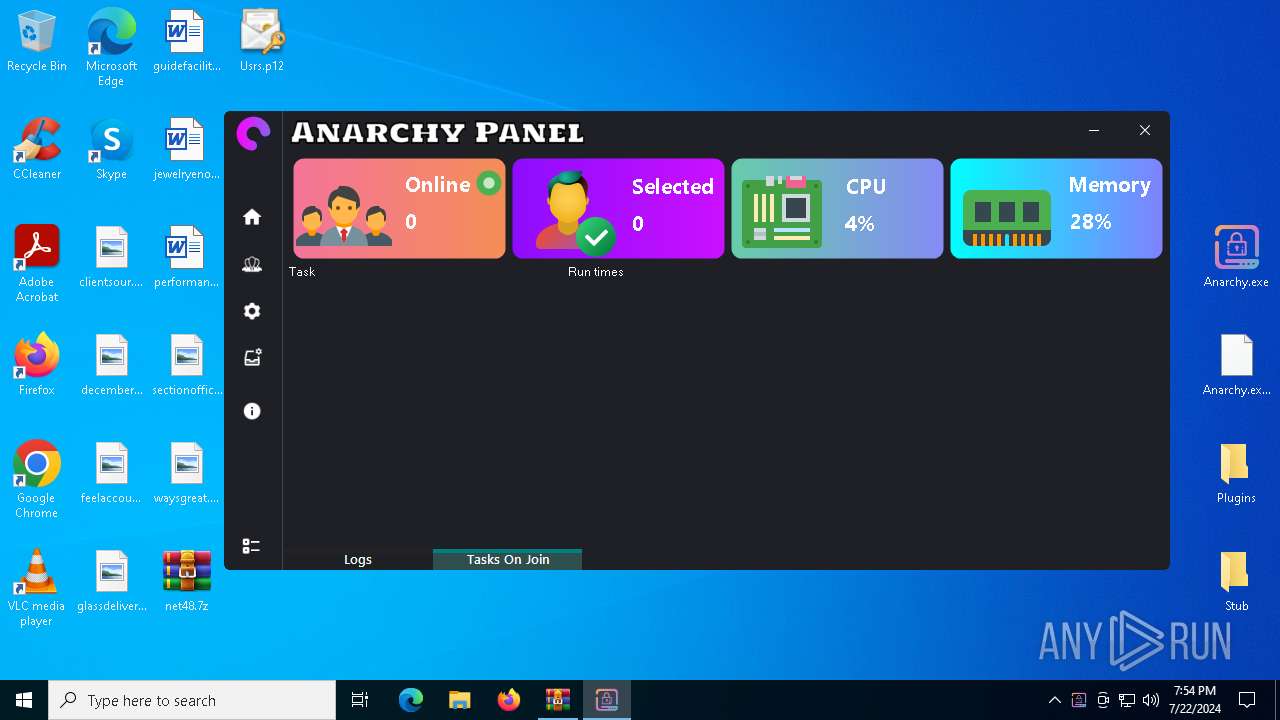
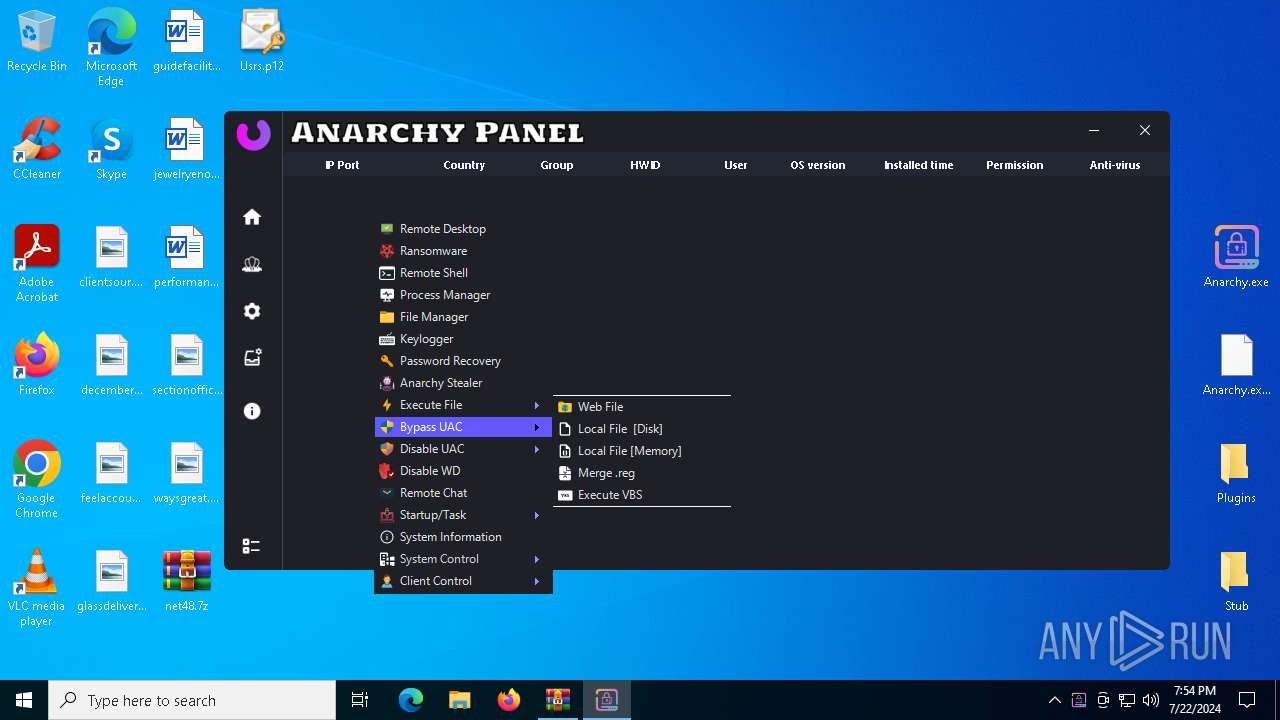
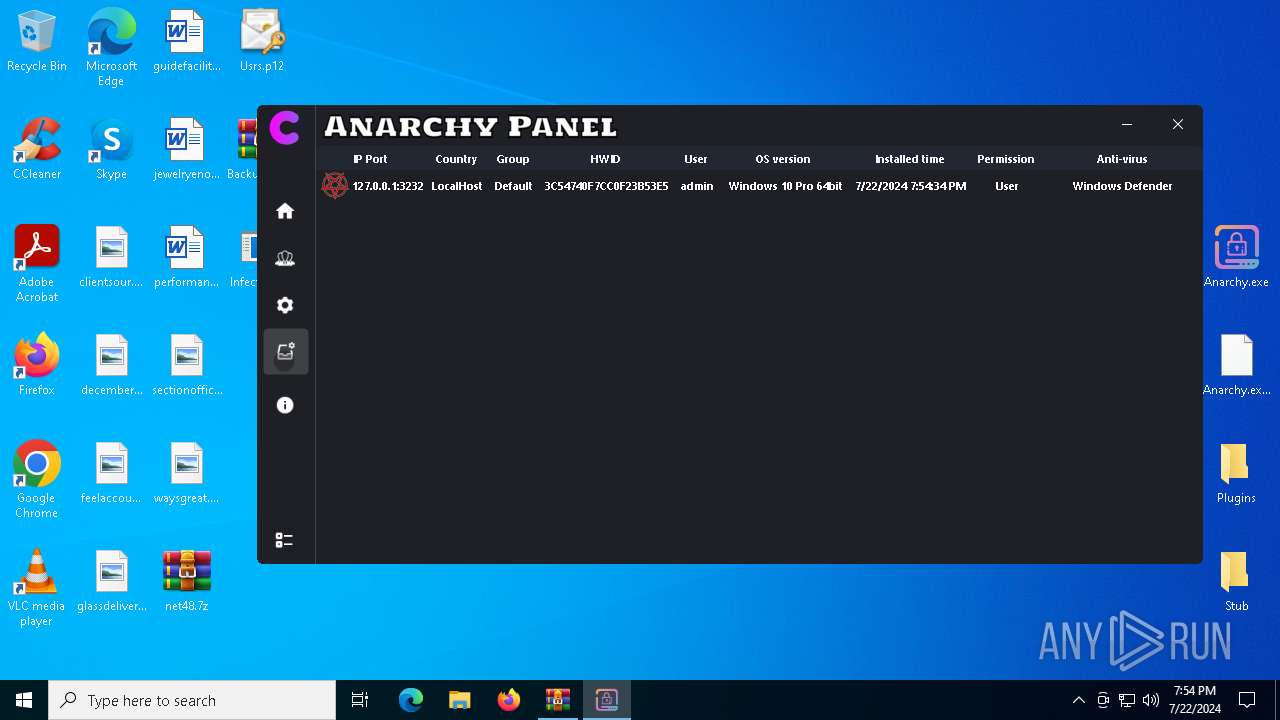
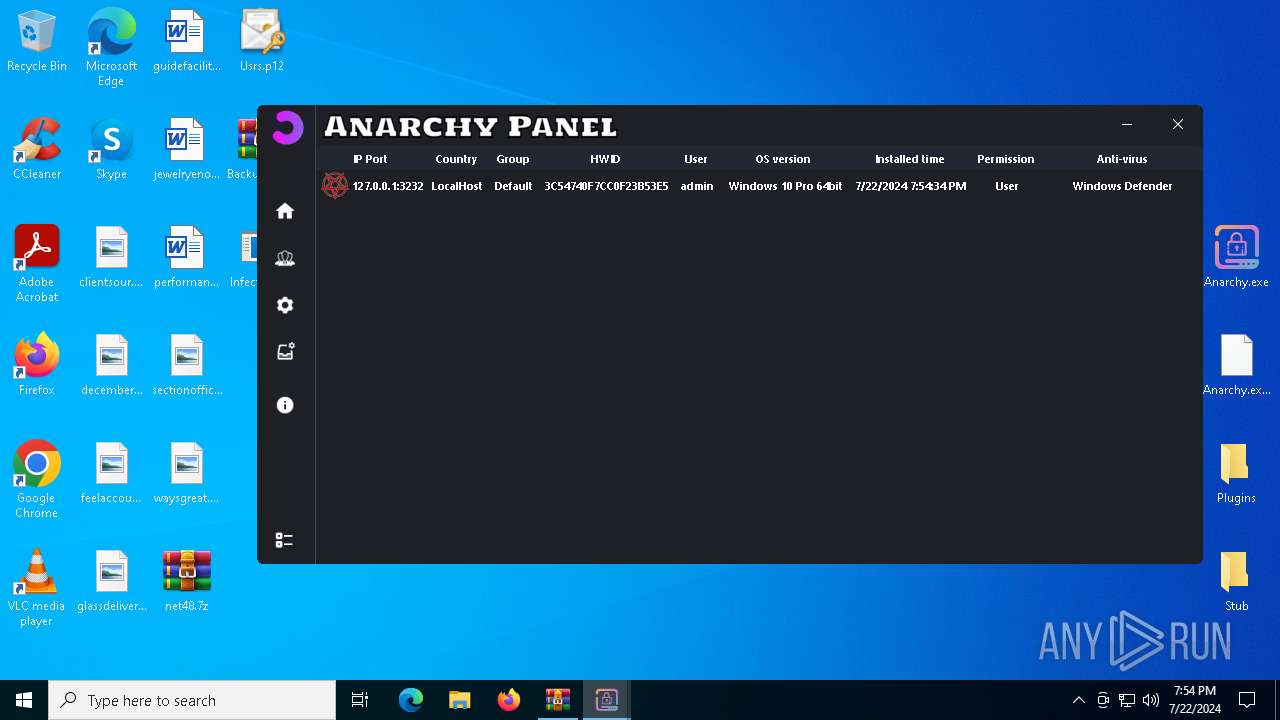
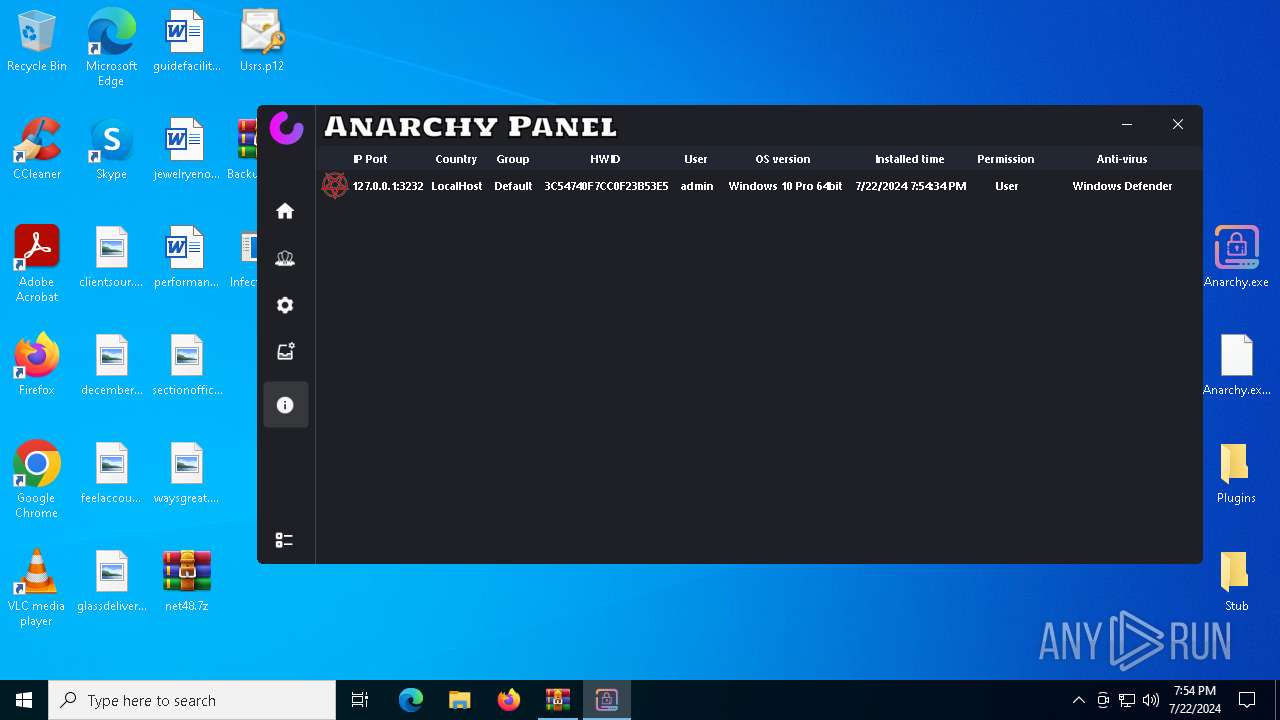
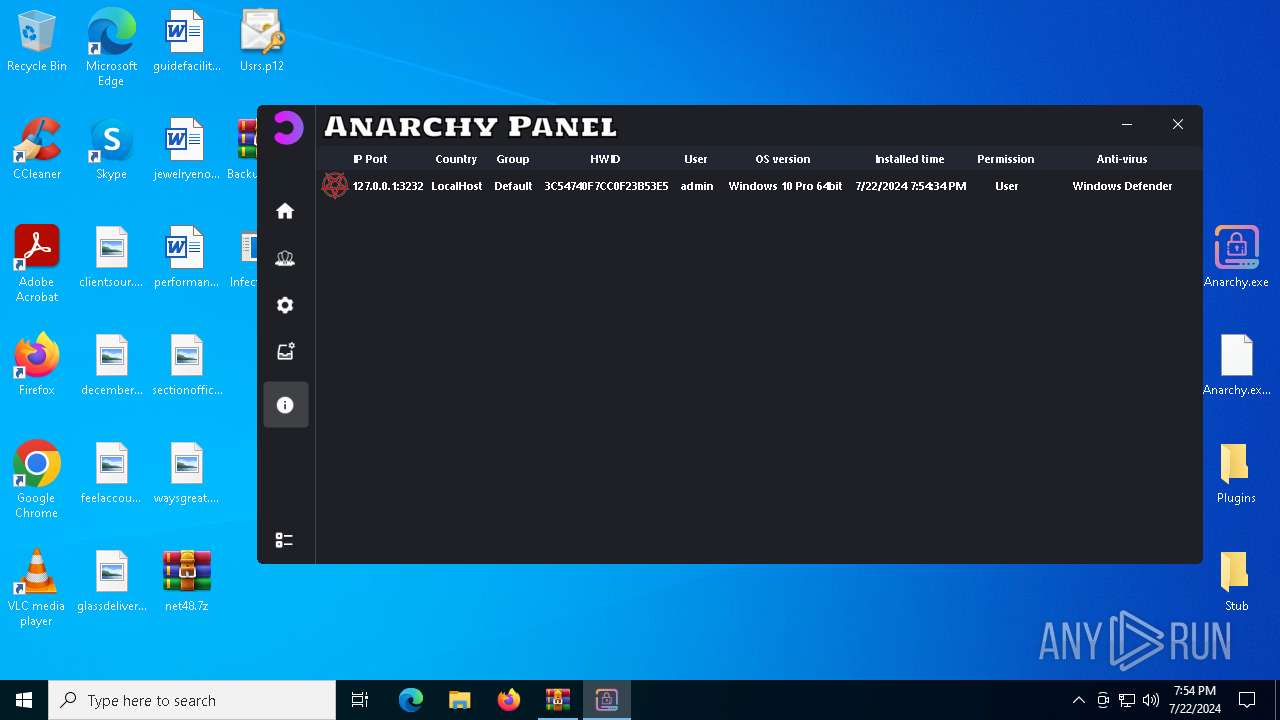
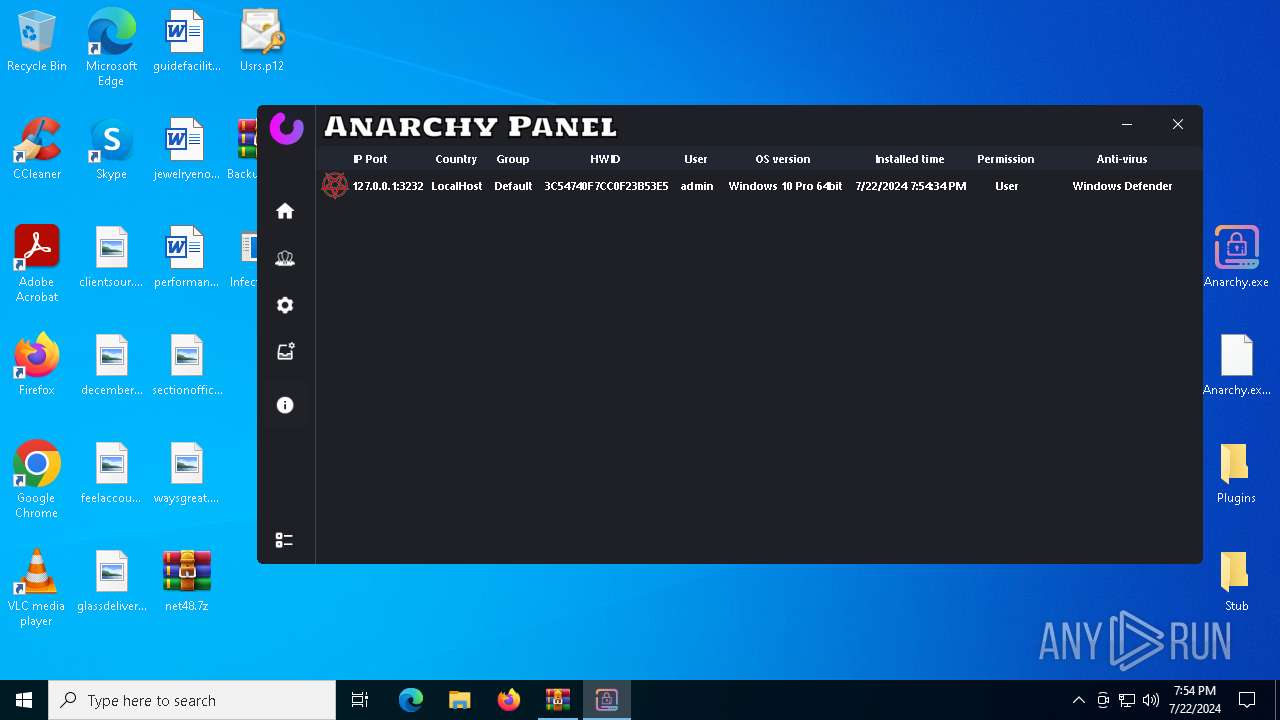
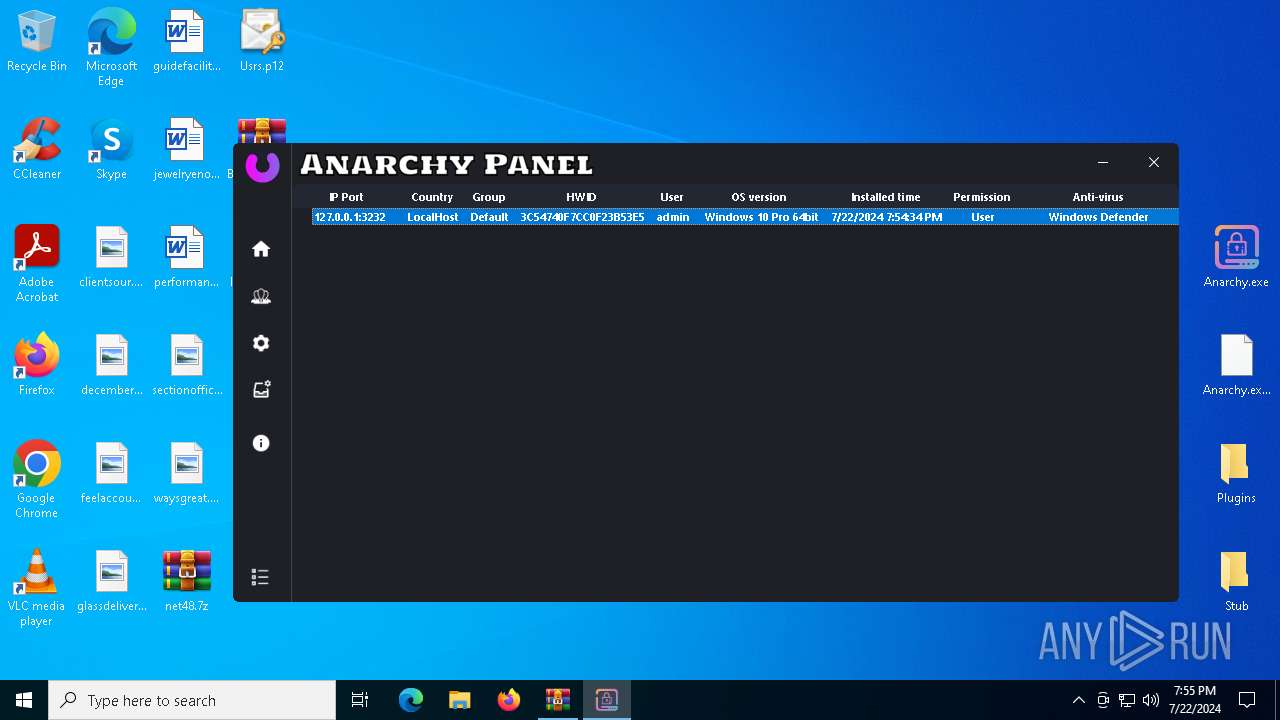
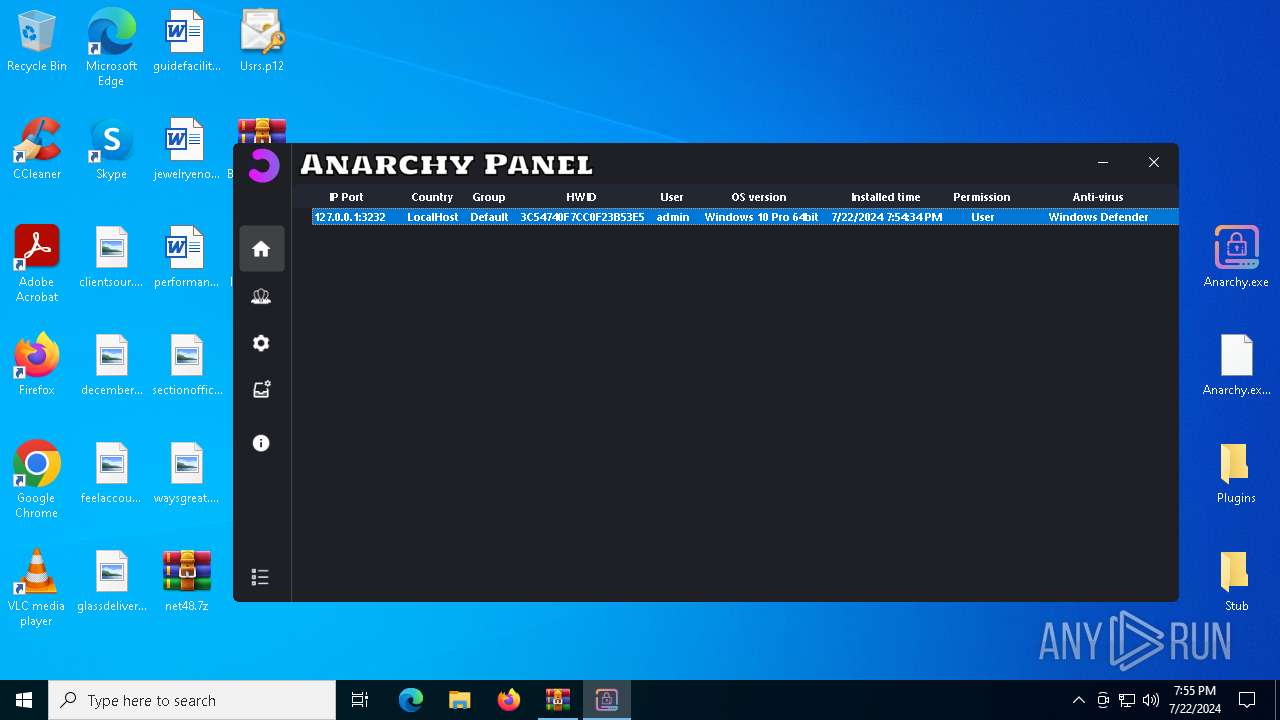
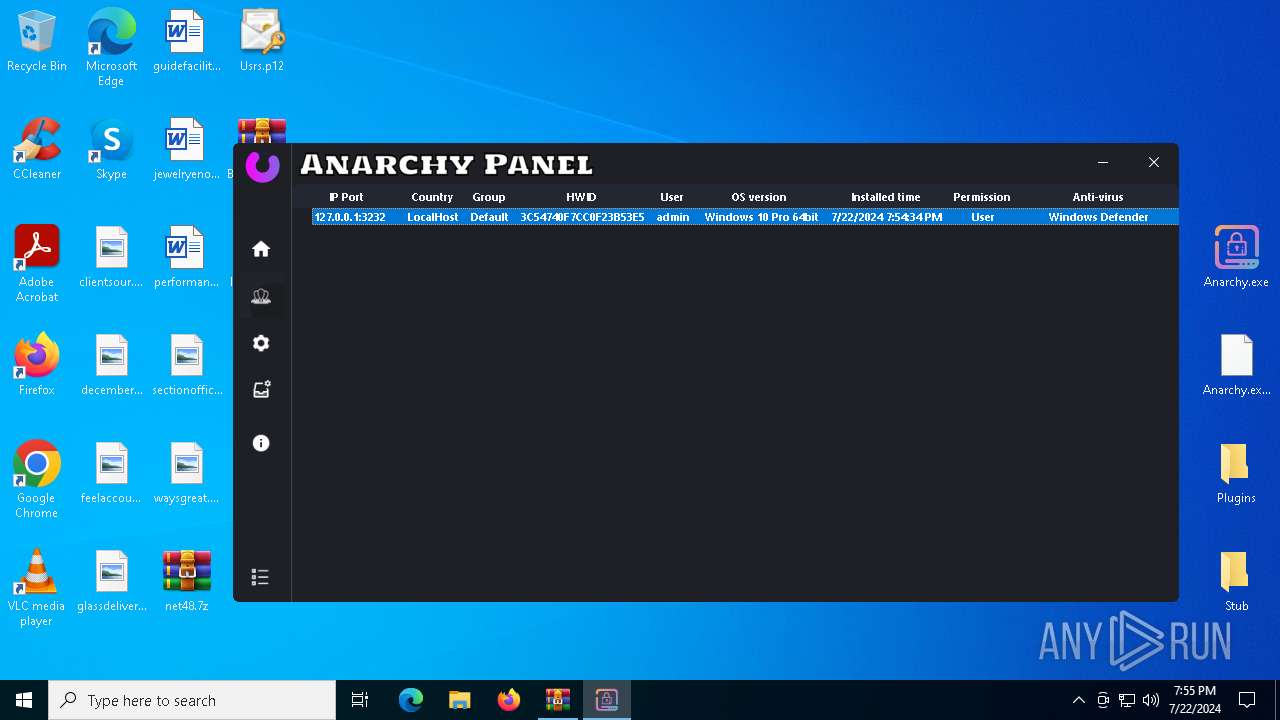
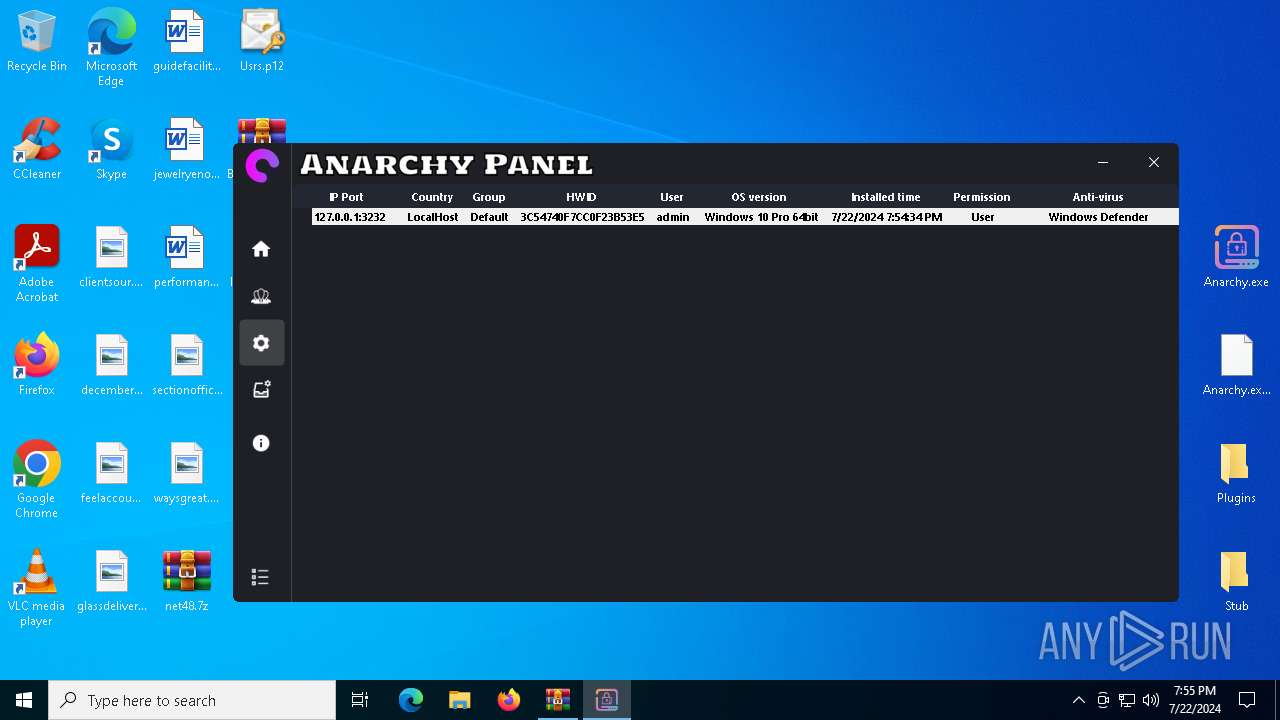
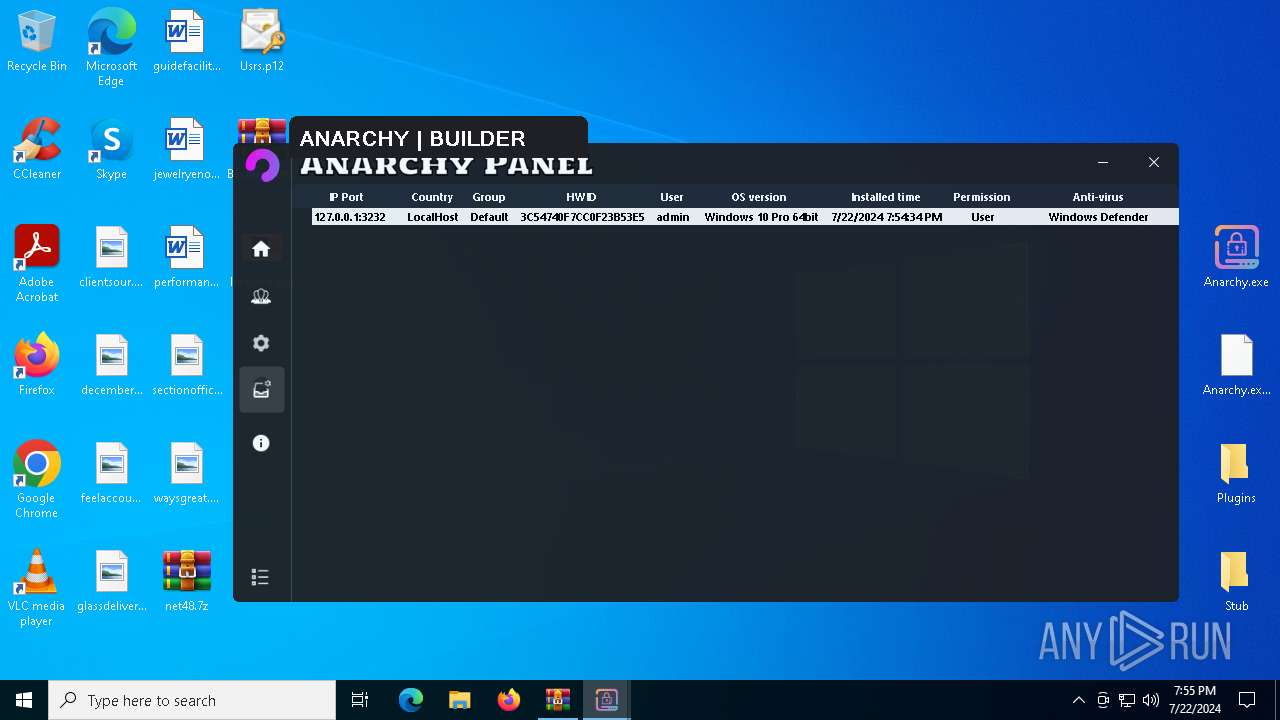
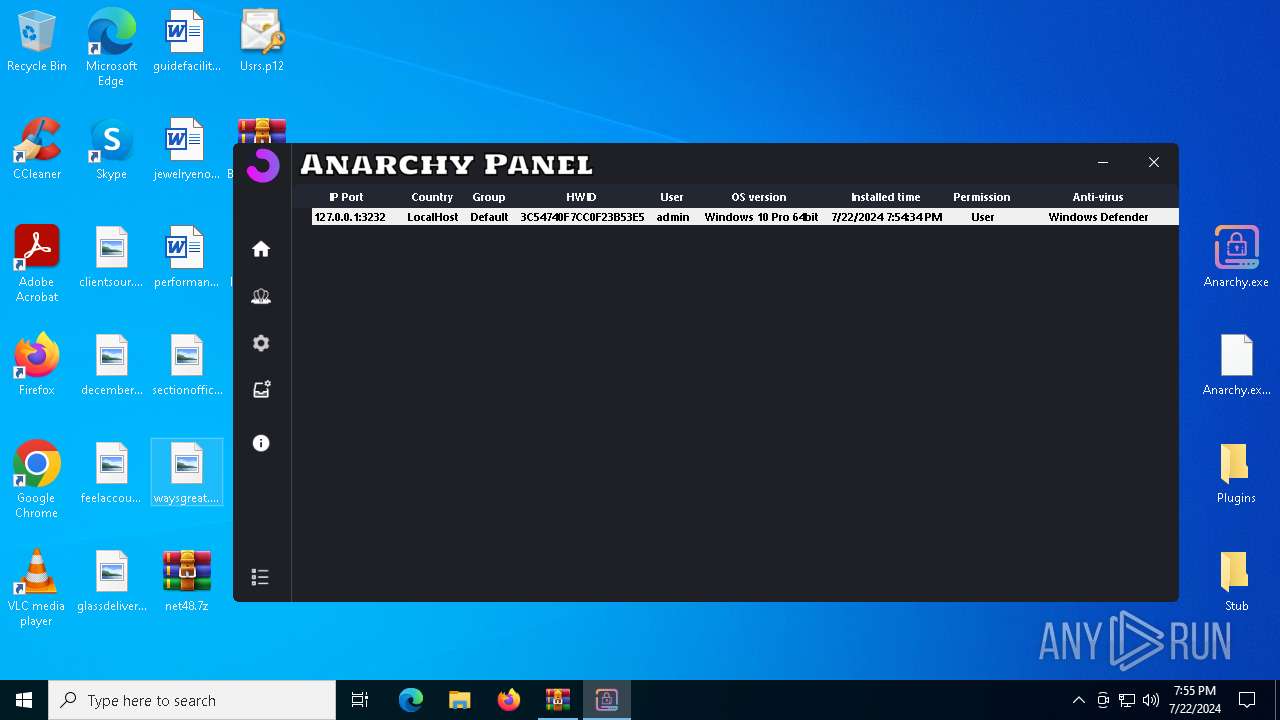
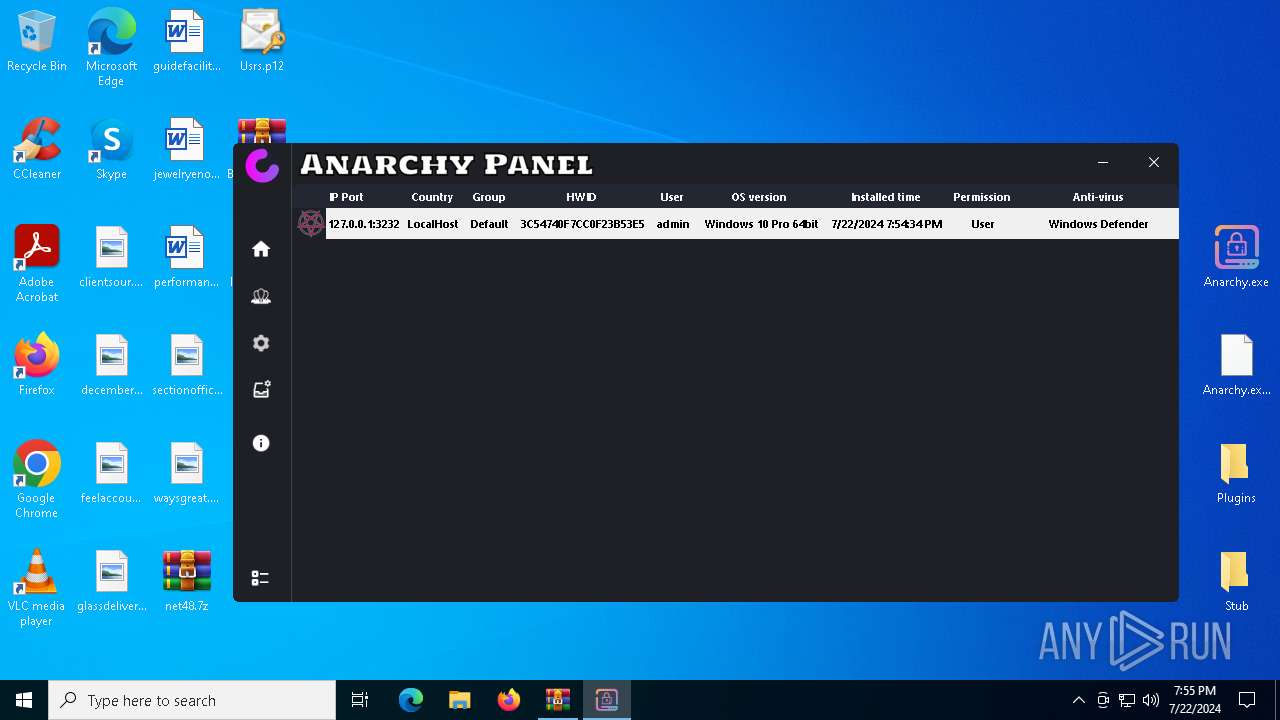
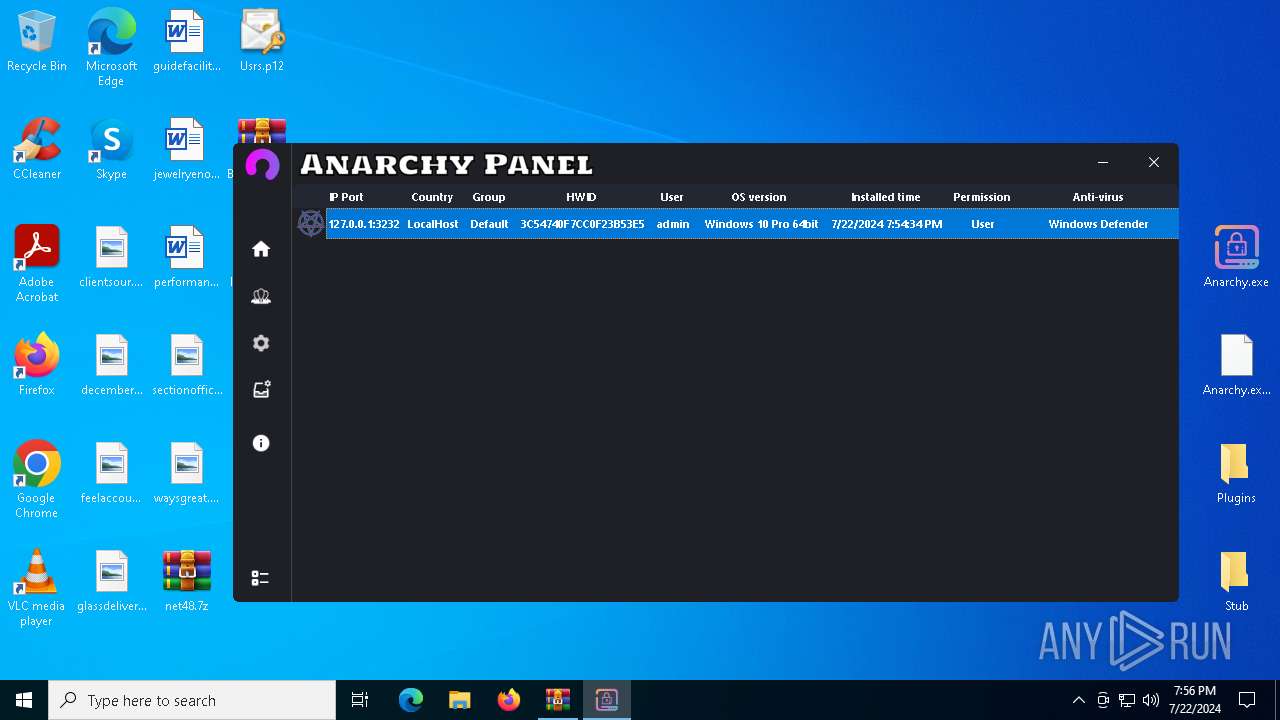
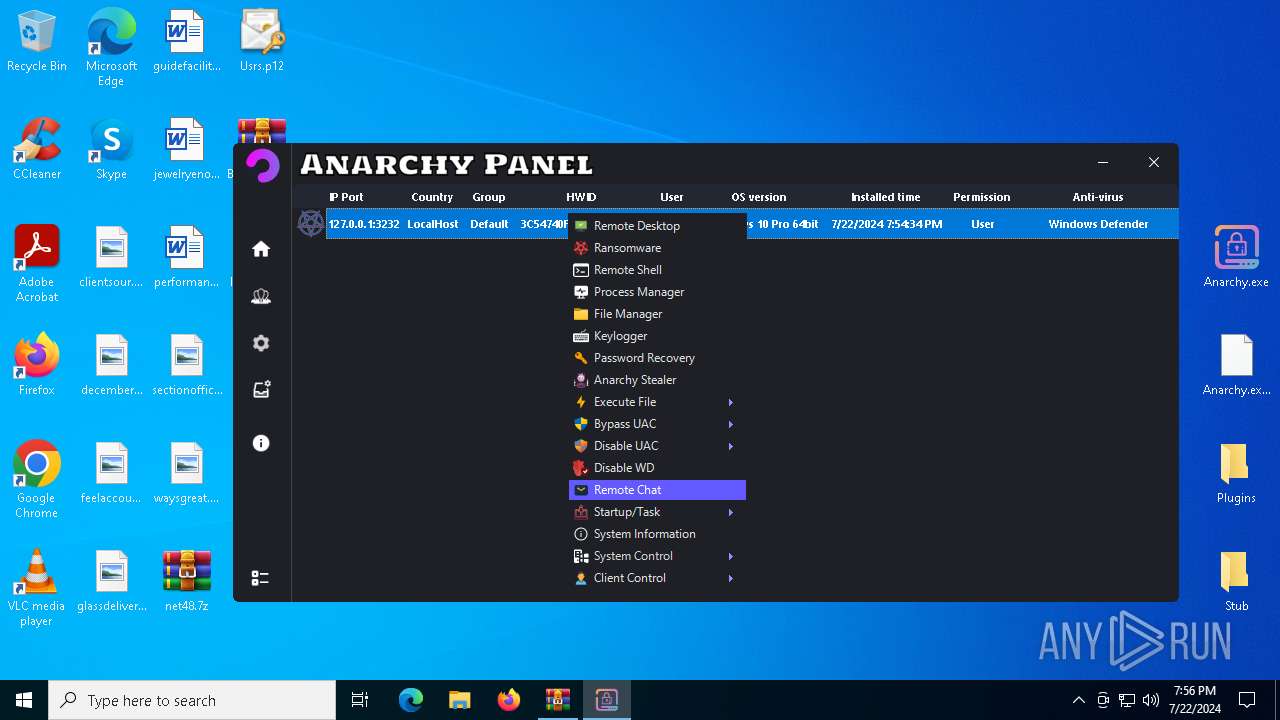
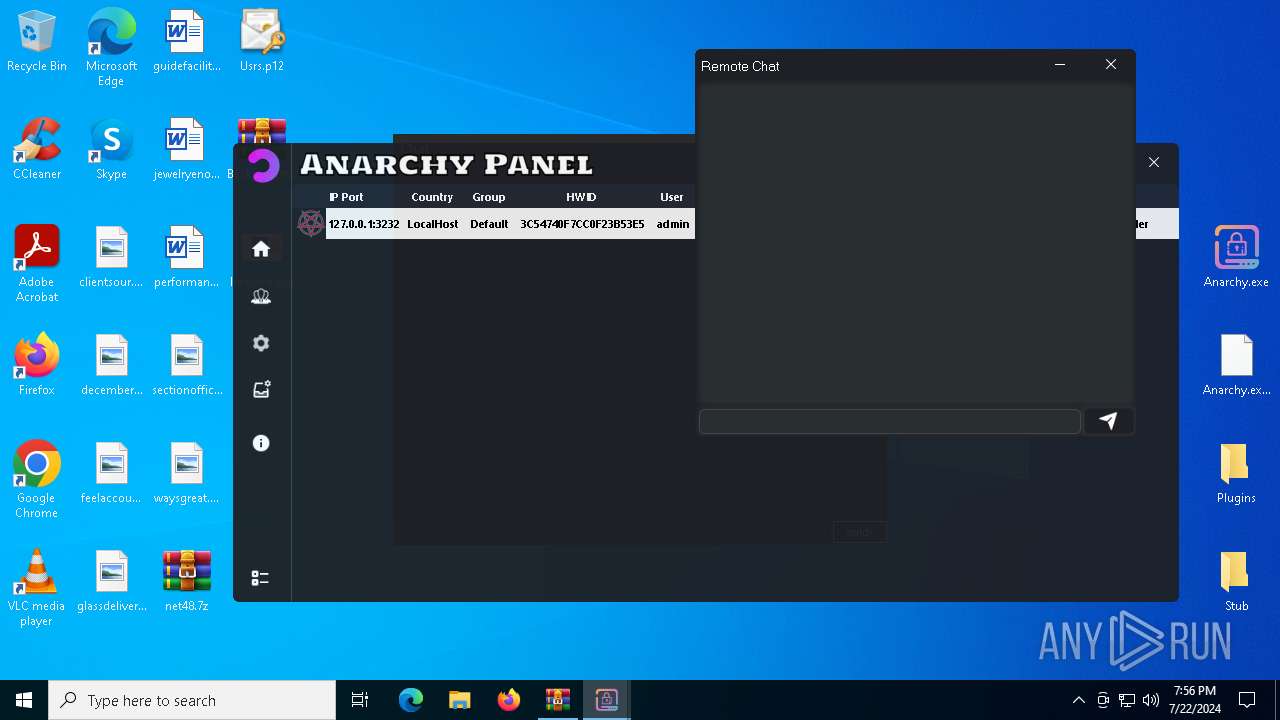
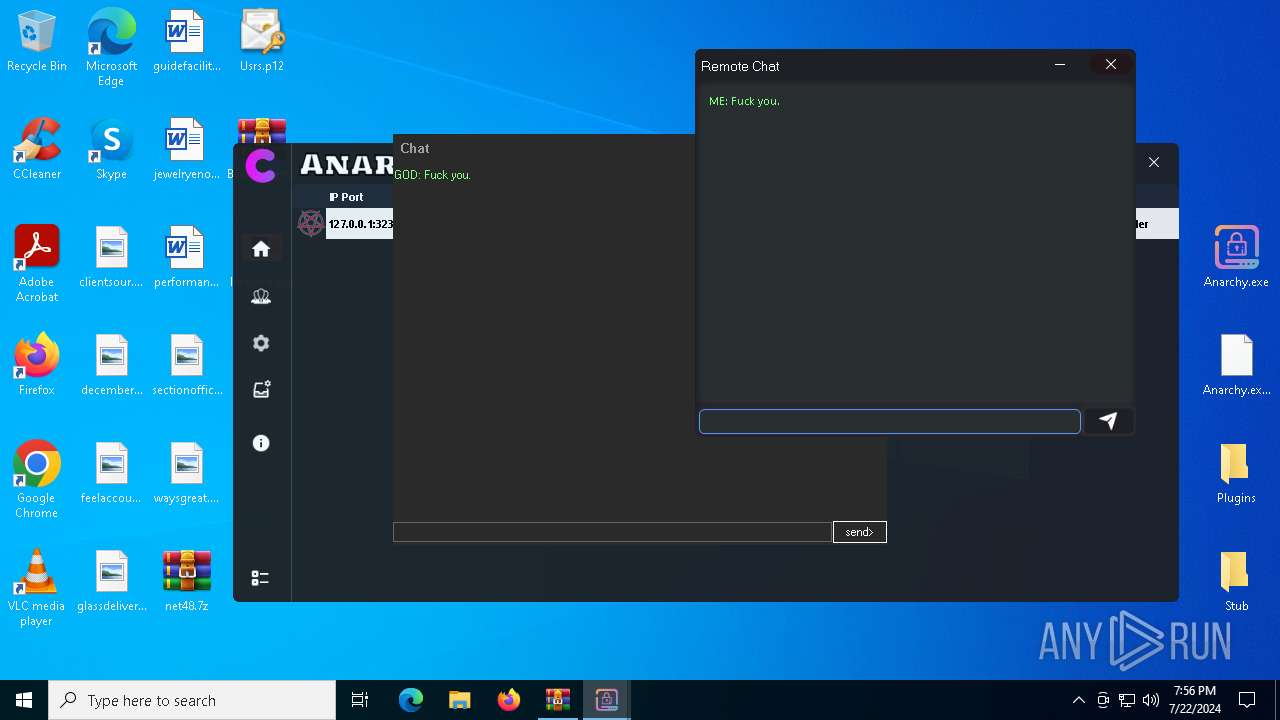
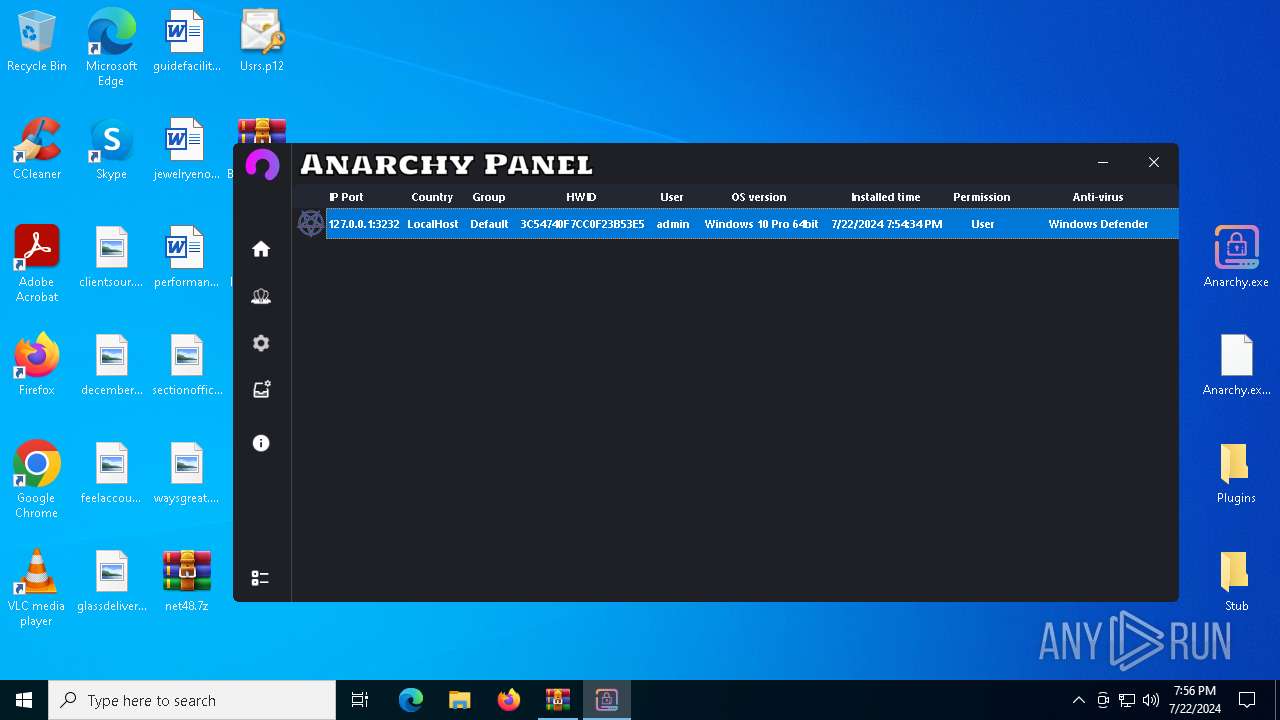
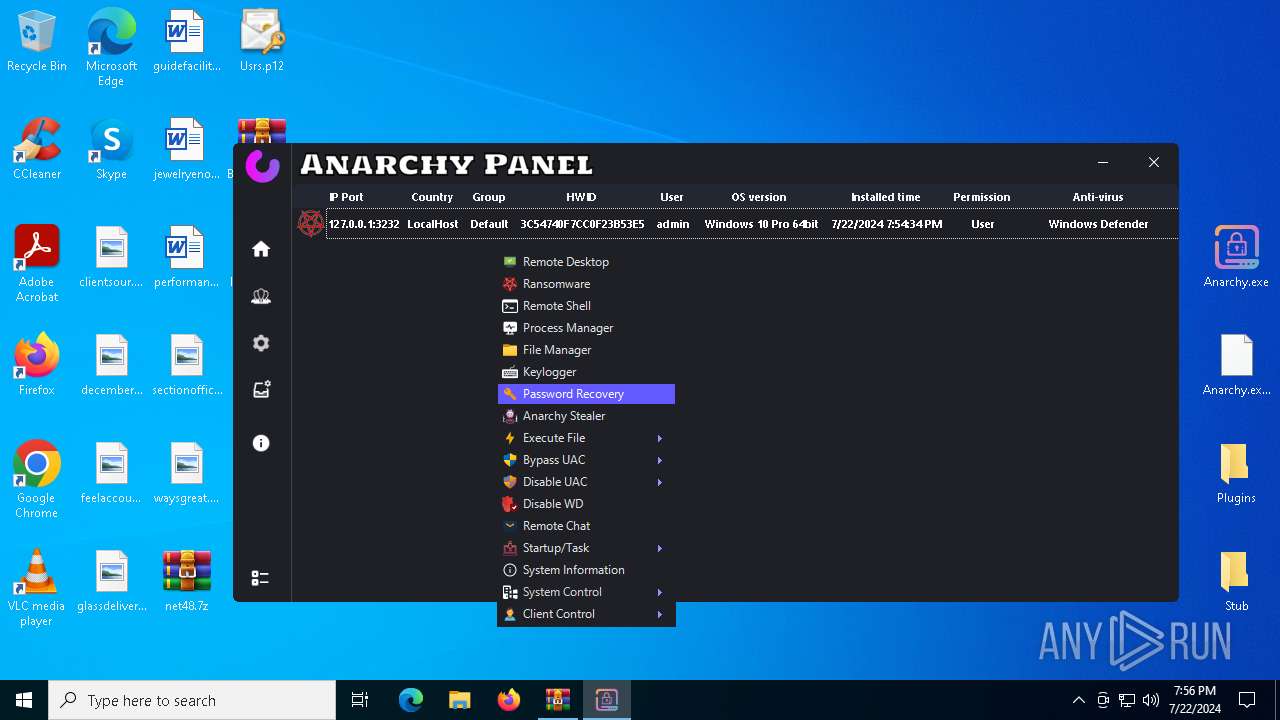
AsyncRat
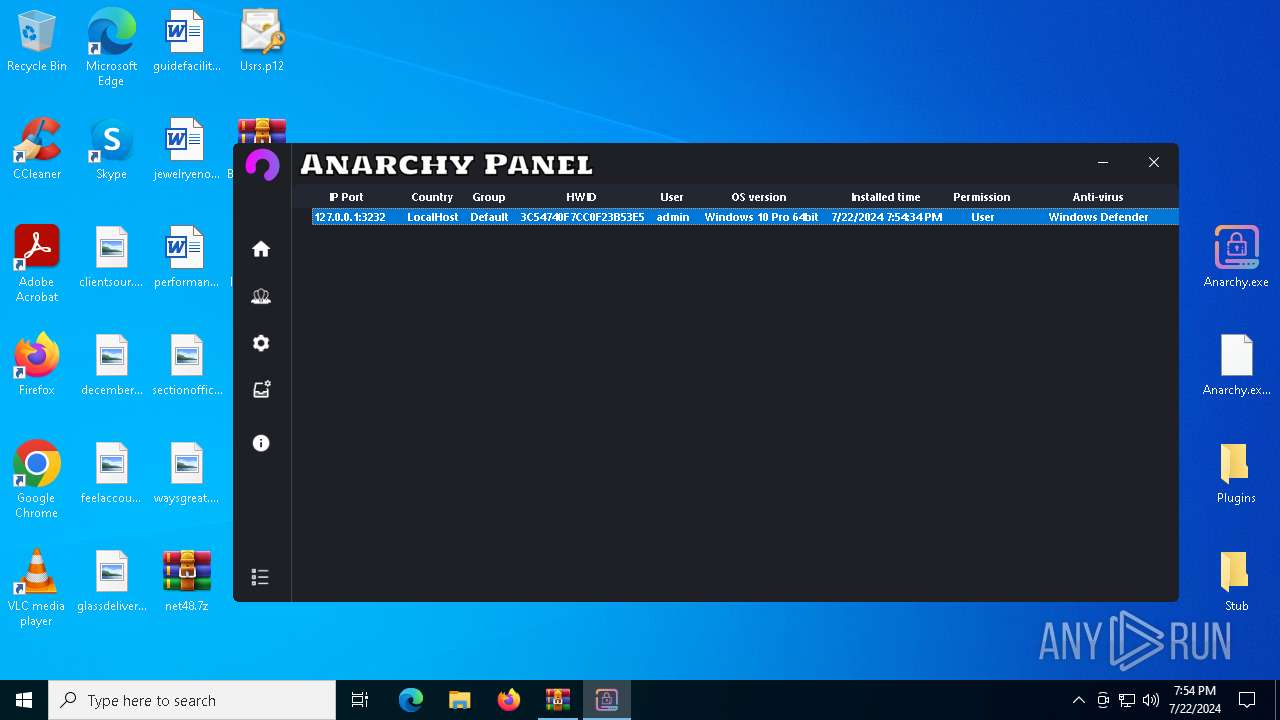
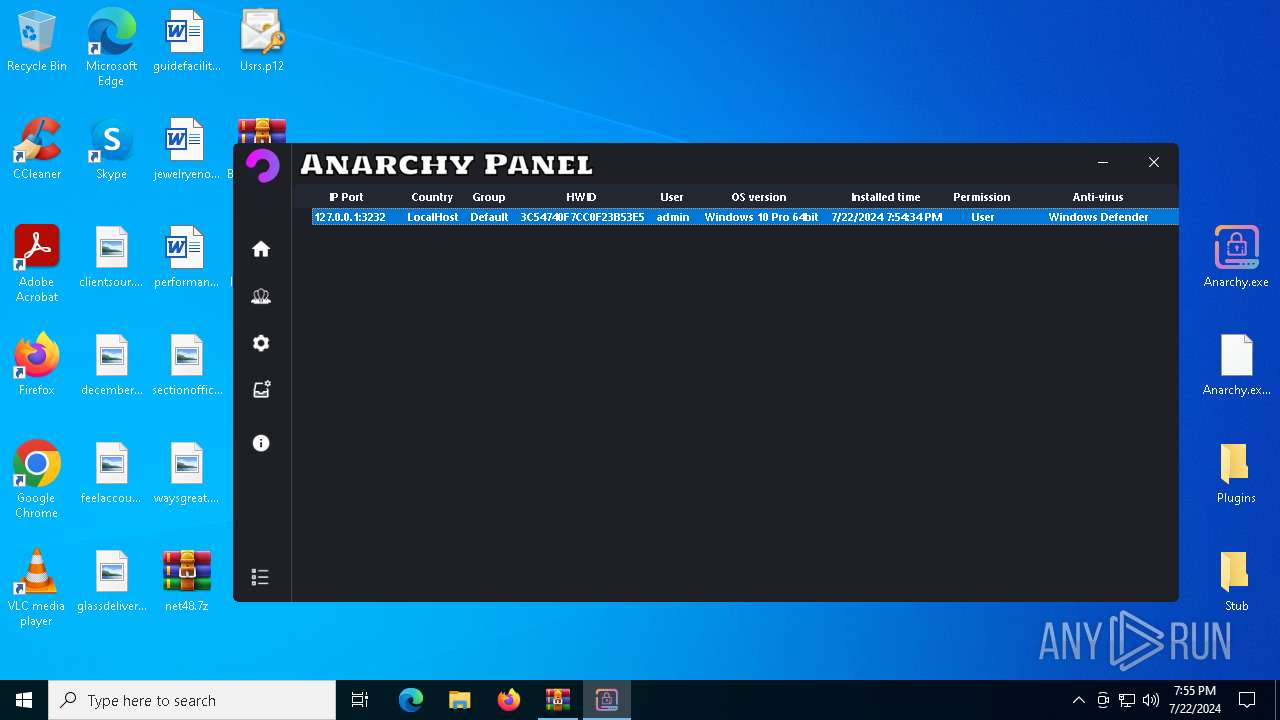
(PID) Process(5532) Infected.exe
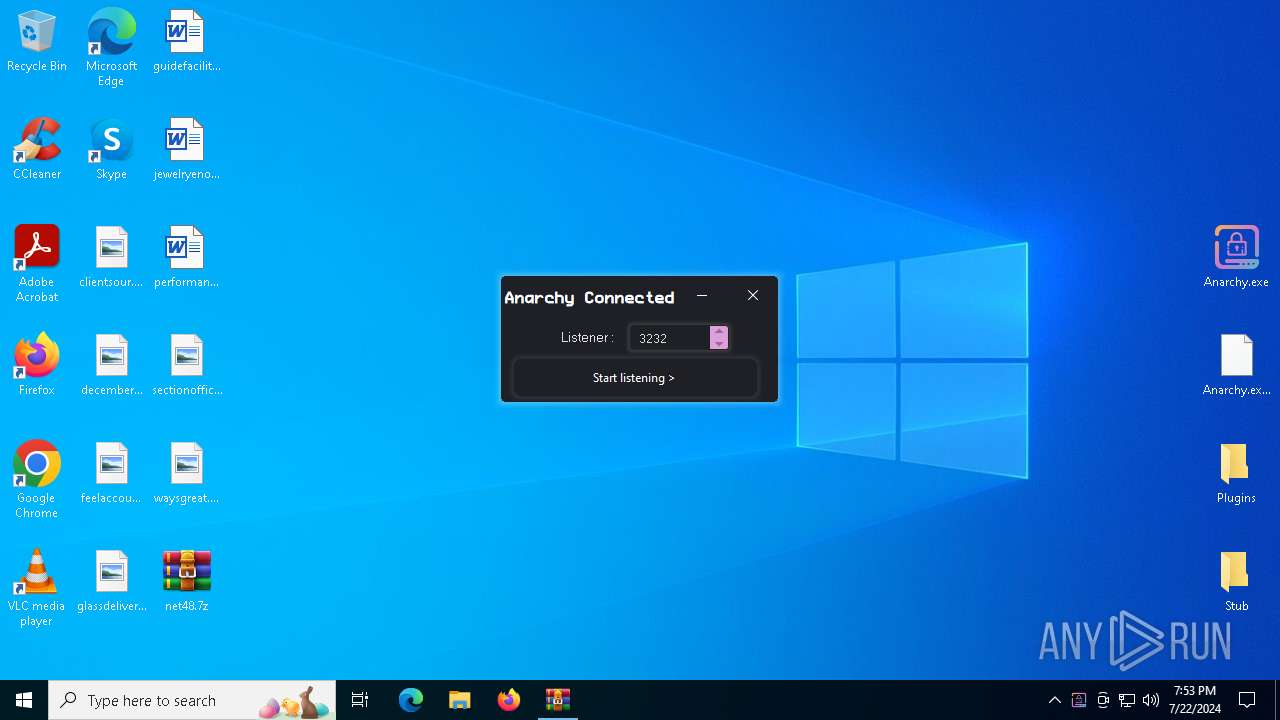
C2 (1)127.0.0.1
Ports (1)3232
Version
Options
AutoRunfalse
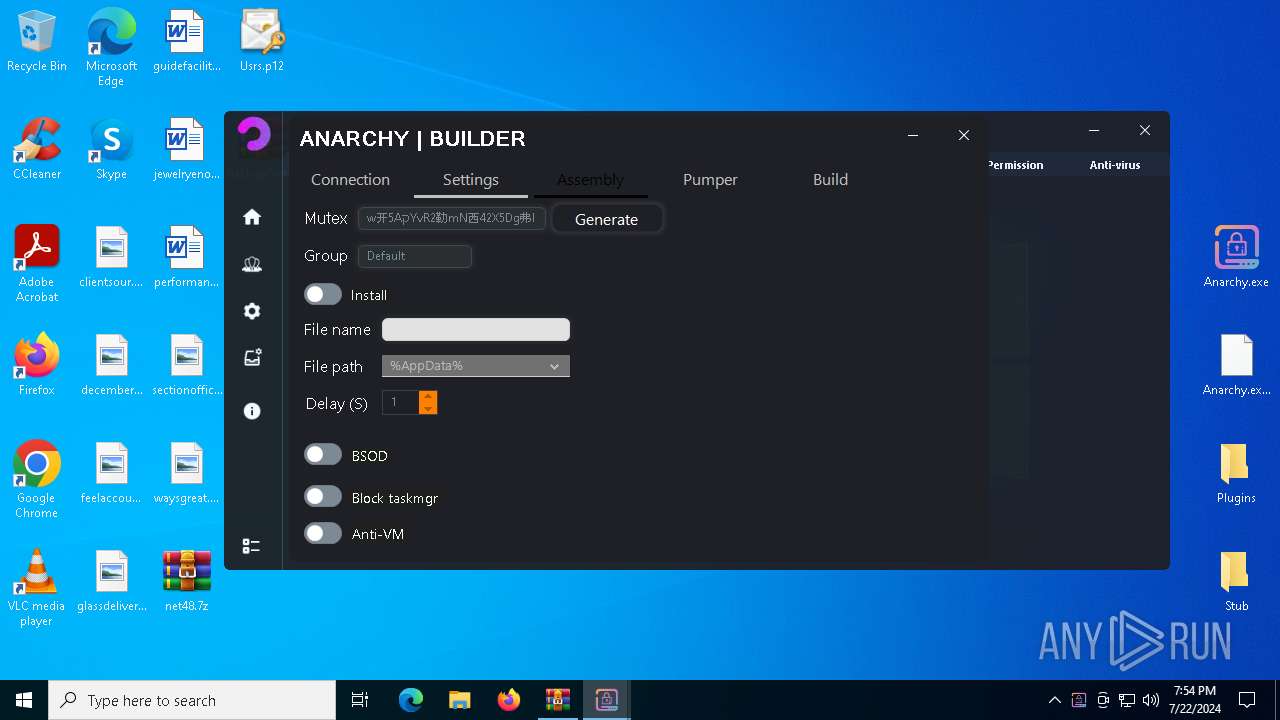
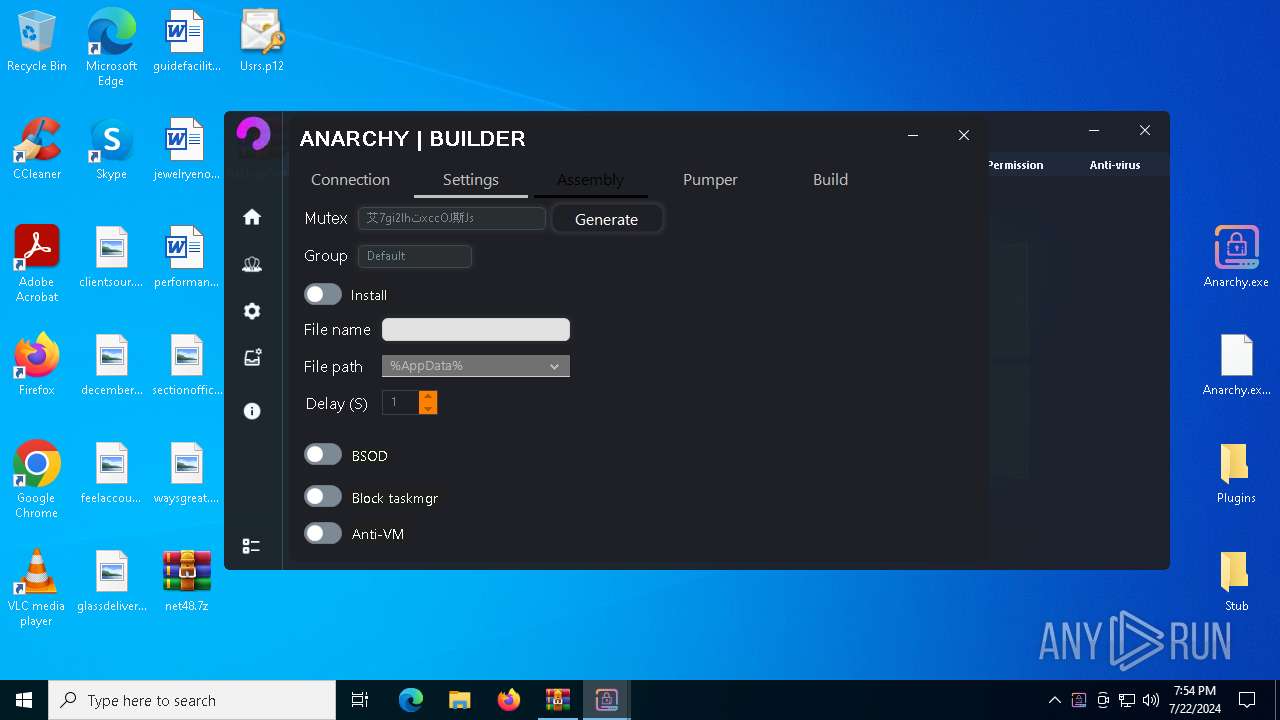
Mutex艾7gi2lhتxccOJ斯Js
InstallFolder%AppData%
Certificates
Cert1MIICKTCCAZKgAwIBAgIVAK0+PQKaks/5bYDWBIAP3wW9y83PMA0GCSqGSIb3DQEBDQUAMF0xDjAMBgNVBAMMBUVCT0xBMRMwEQYDVQQLDApxd3FkYW5jaHVuMRwwGgYDVQQKDBNEY1JhdCBCeSBxd3FkYW5jaHVuMQswCQYDVQQHDAJTSDELMAkGA1UEBhMCQ04wHhcNMjMxMDExMTk1MzQ5WhcNMzQwNzIwMTk1MzQ5WjAQMQ4wDAYDVQQDDAVEY1JhdDCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA...
Server_SignatureWHCEF6UrumQOw/j13BuCiZ6LLY176M927Q7JzYsOR0wcqv2gGV4uVkH0KSa2Q3Wuv/3ExaoJtheoTVtcfygFv0UdHDcH1yixyFkd3lyTjOuOBffuQrlq7y4Bcw9hYmHHUZWVQ26rMRLjjls08ZaLw0J6JaMhpeSCLBNYDFuMchg=
Keys
AES93a9a75905f548ec27934a645a3b2efeebcacb61427384819f252f9aa5b3ac0b
SaltDcRatByqwqdanchun
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
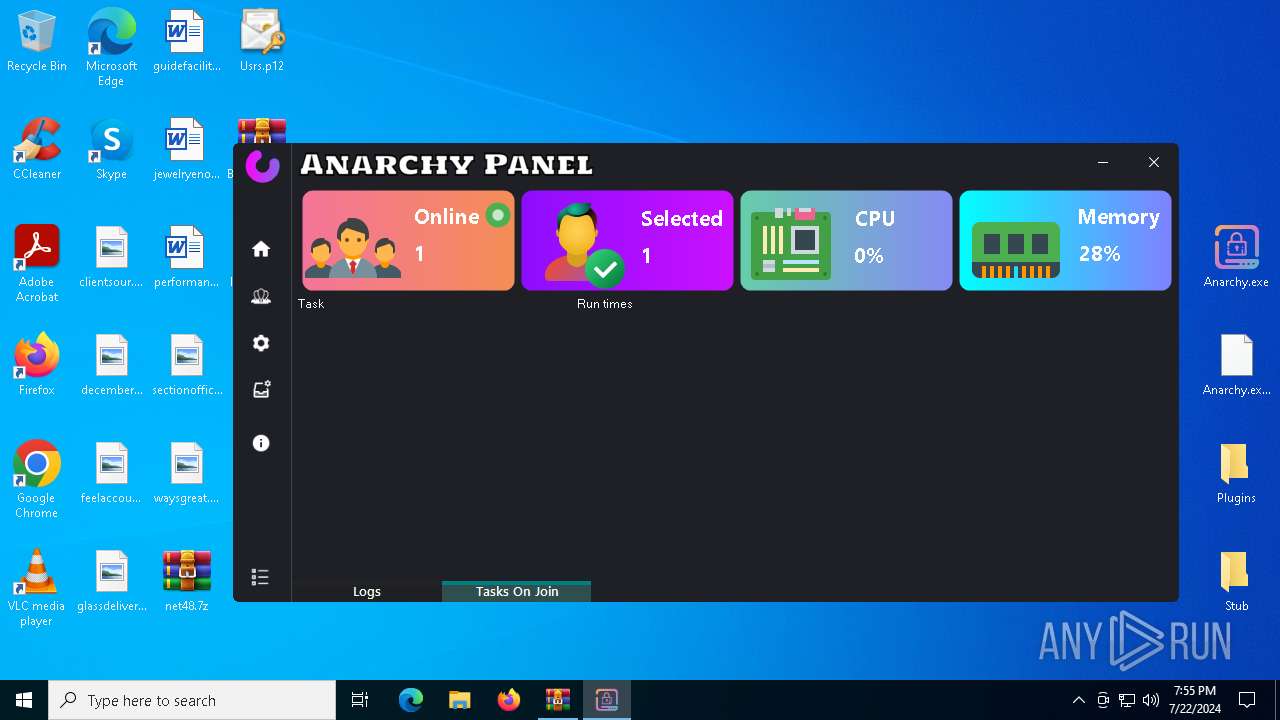
Total processes
137
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4020 | "C:\Users\admin\Desktop\Anarchy.exe" | C:\Users\admin\Desktop\Anarchy.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Anarchy Exit code: 0 Version: 4.1.0.0 Modules
| |||||||||||||||
| 4052 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\net48.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4328 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5532 | "C:\Users\admin\Desktop\Infected.exe" | C:\Users\admin\Desktop\Infected.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 3.6.0.0 Modules
AsyncRat(PID) Process(5532) Infected.exe C2 (1)127.0.0.1 Ports (1)3232 Version Options AutoRunfalse Mutex艾7gi2lhتxccOJ斯Js InstallFolder%AppData% Certificates Cert1MIICKTCCAZKgAwIBAgIVAK0+PQKaks/5bYDWBIAP3wW9y83PMA0GCSqGSIb3DQEBDQUAMF0xDjAMBgNVBAMMBUVCT0xBMRMwEQYDVQQLDApxd3FkYW5jaHVuMRwwGgYDVQQKDBNEY1JhdCBCeSBxd3FkYW5jaHVuMQswCQYDVQQHDAJTSDELMAkGA1UEBhMCQ04wHhcNMjMxMDExMTk1MzQ5WhcNMzQwNzIwMTk1MzQ5WjAQMQ4wDAYDVQQDDAVEY1JhdDCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA... Server_SignatureWHCEF6UrumQOw/j13BuCiZ6LLY176M927Q7JzYsOR0wcqv2gGV4uVkH0KSa2Q3Wuv/3ExaoJtheoTVtcfygFv0UdHDcH1yixyFkd3lyTjOuOBffuQrlq7y4Bcw9hYmHHUZWVQ26rMRLjjls08ZaLw0J6JaMhpeSCLBNYDFuMchg= Keys AES93a9a75905f548ec27934a645a3b2efeebcacb61427384819f252f9aa5b3ac0b SaltDcRatByqwqdanchun | |||||||||||||||
Total events
19 823
Read events
19 750
Write events
68
Delete events
5
Modification events
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\net48.7z | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4020) Anarchy.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4020) Anarchy.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
22
Suspicious files
3
Text files
6
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.32886\Plugins\EVa7gBMKoaHmLC.dll | executable | |
MD5:64A3D908B8A5FEFF2BCCFC67F3A67DBD | SHA256:6EA1AE7AB496666C0117FC20E704BFB6104B13CFB0408073A09689F863FA64B1 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.32886\Plugins\9Ood5SWkbwPn.AnarHs | executable | |
MD5:2CF2EFCC0E1D910D2D9C933CA73055D0 | SHA256:2475C46EBA856424C41CF41DB71FD5D6089E8BE9031B35279F051DA760AA216F | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.32886\Plugins\fzAgyDYa.AnarHs | executable | |
MD5:21AAF842F7518FDC7038C09A78292C7E | SHA256:F0A82D67F8B53DE0915C2C8853E47B191AA24BE180C398F61C5332E558094E4A | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.32886\Plugins\KNTmoSnG.AnarHs.dll | executable | |
MD5:1681E0F3311751361030FF30A957A1ED | SHA256:234724F14DBB999853AEB872D7E6C3ED0B3DE5B105009B5C66131A2AF8D0DBB4 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.32886\Plugins\FBSyChwp.dll | executable | |
MD5:0D41CCFAA8E7EF96248B8270D1A44D08 | SHA256:0EA38D0D964815E2B84748A78BD5A829AE01586478E5F17B976F1AE763C8DEC3 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.32886\Plugins\oYsKwDG.dll | executable | |
MD5:19F8D8099CC9B7B6A68E7EFEBC44AC18 | SHA256:9157A6021901939611C80C4246DBEC6007200B2F2457D348CE8834BEF9872535 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.32886\Plugins\59Zp7paEHDF7luJ.dll | executable | |
MD5:15E3D44D37439F3AC8574AC1C9789EC2 | SHA256:5DB4C26057A05BB75FF7892FB60FD76620FC2228811D913D152A0AA4EC9DB7A5 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.32886\Plugins\K8oCBS3ThnW0WP.dll | executable | |
MD5:1681E0F3311751361030FF30A957A1ED | SHA256:234724F14DBB999853AEB872D7E6C3ED0B3DE5B105009B5C66131A2AF8D0DBB4 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.32886\Plugins\maSN8TBMgUEC.dll | executable | |
MD5:D5A278ACDAFA0C8B4380EFB7D83E053E | SHA256:D93D72C6E929BD9CEA468458E6C0558908A92F0ECD11F4F4DB0F49ACFE9D4FC5 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.32886\Plugins\mML6WKMqdxjDGA.dll | executable | |
MD5:E03B206EEC8A7EFBD1A47909071226E5 | SHA256:778877431354A9584325DADB663BE077F757227EAAE8BCAD33E4BF26EFD6B965 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
44
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3148 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1560 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3204 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4204 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
7124 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5368 | SearchApp.exe | 2.20.142.155:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5272 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |