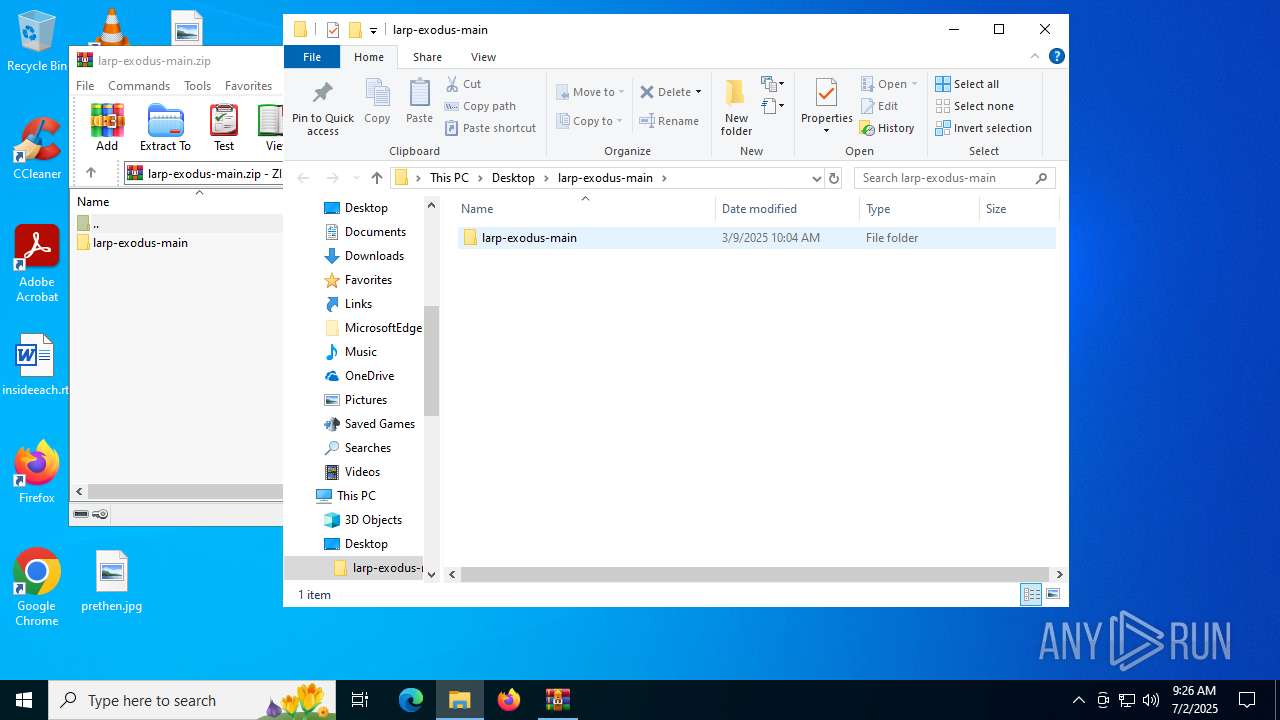
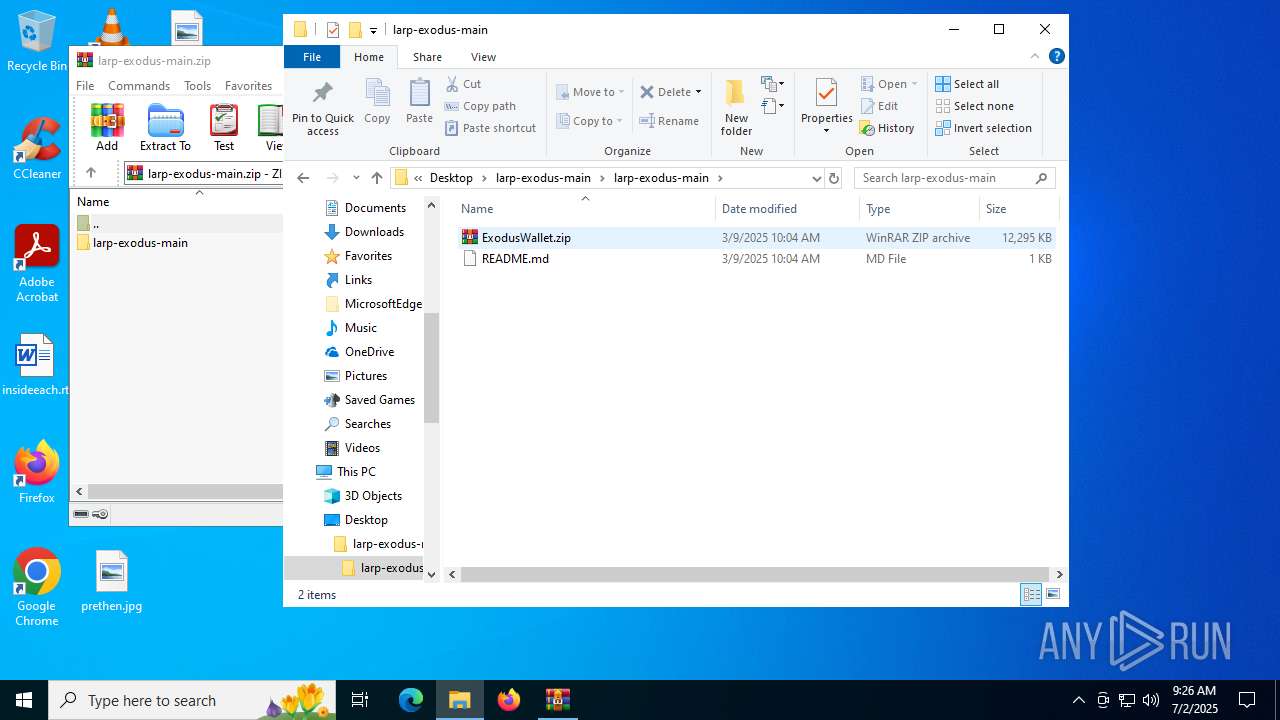
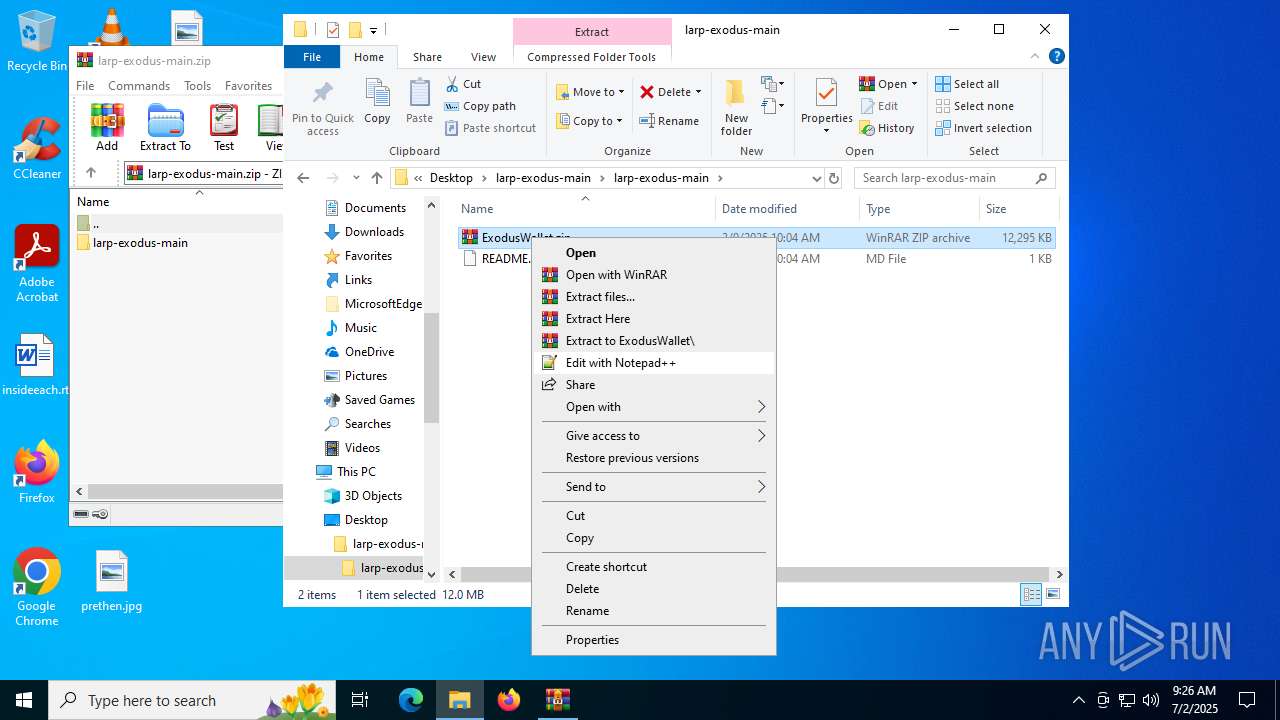
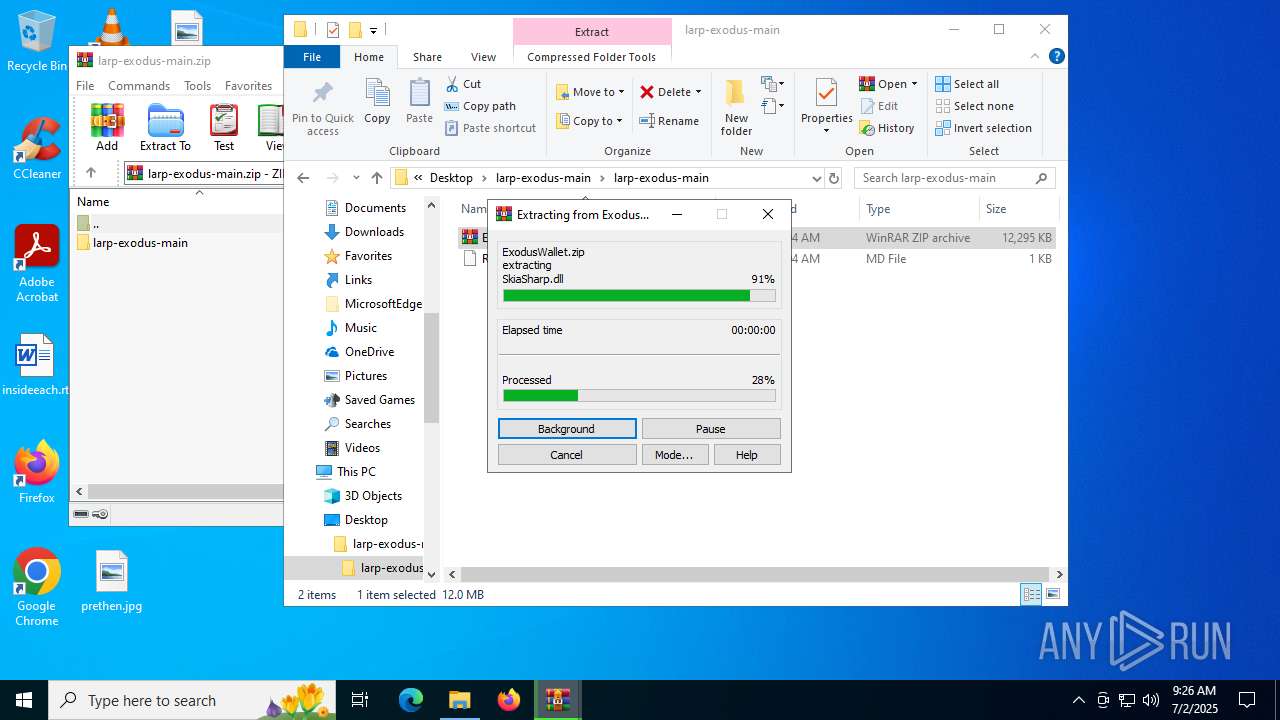
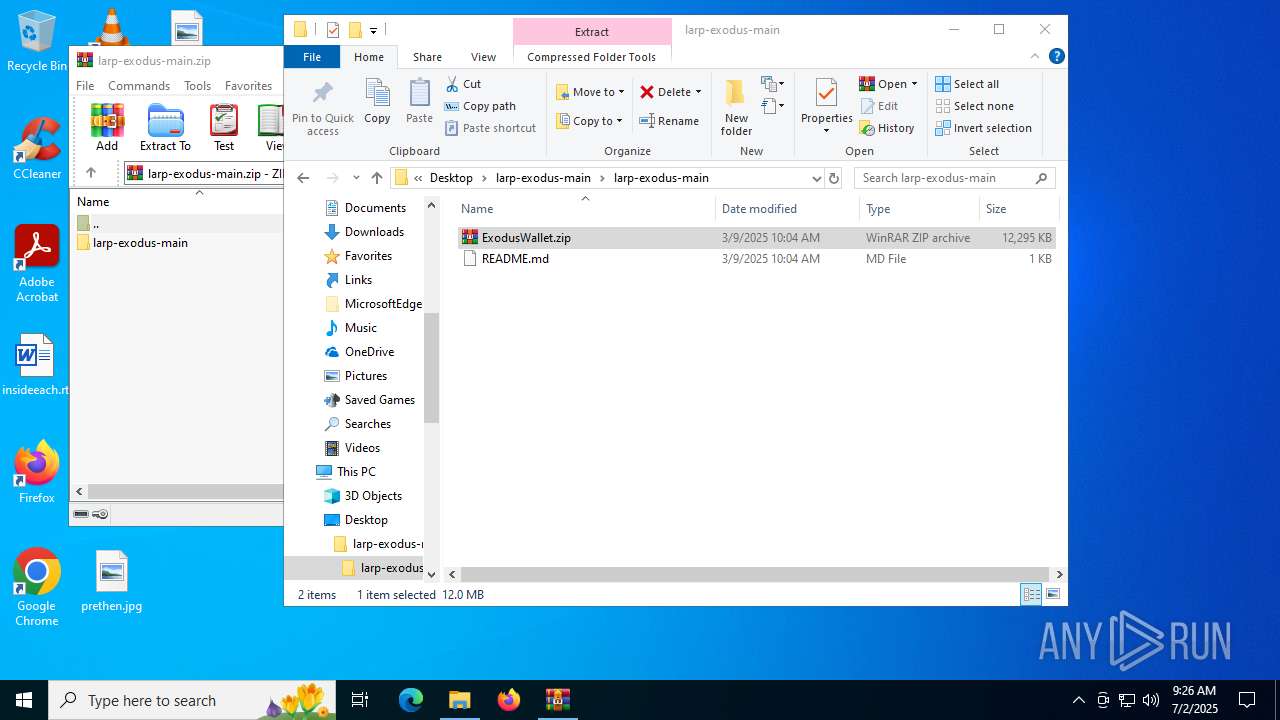
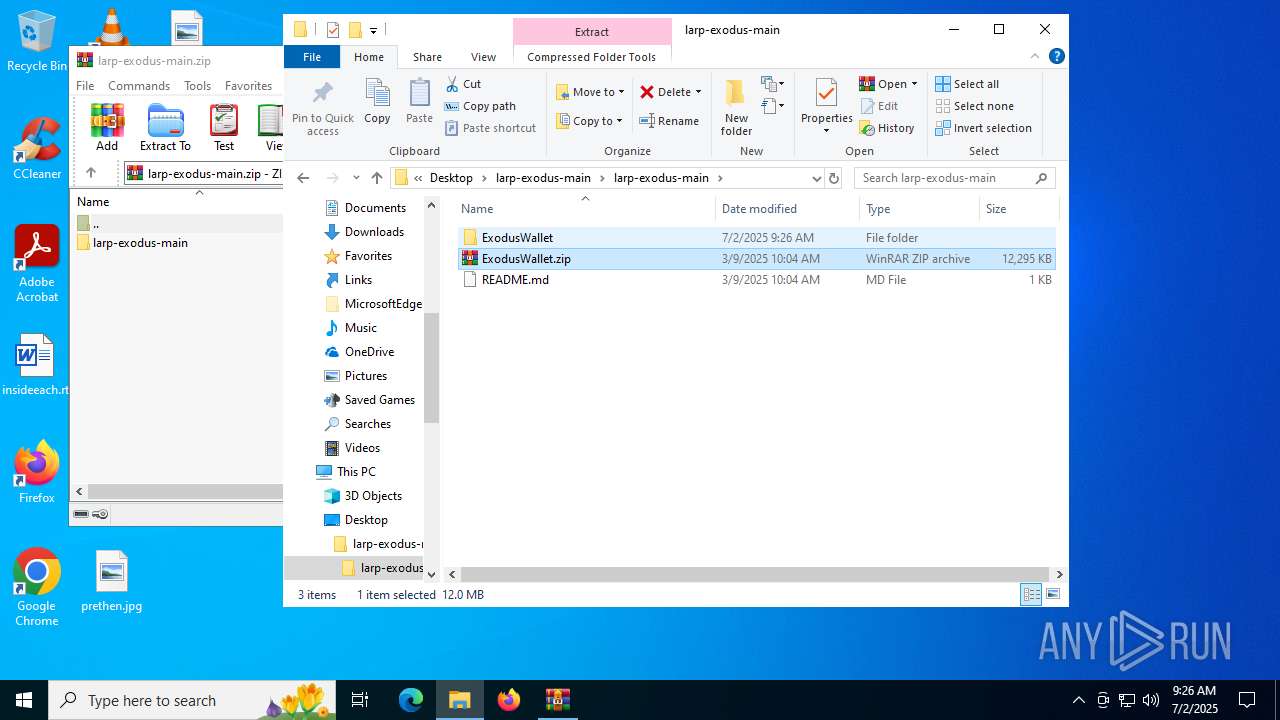
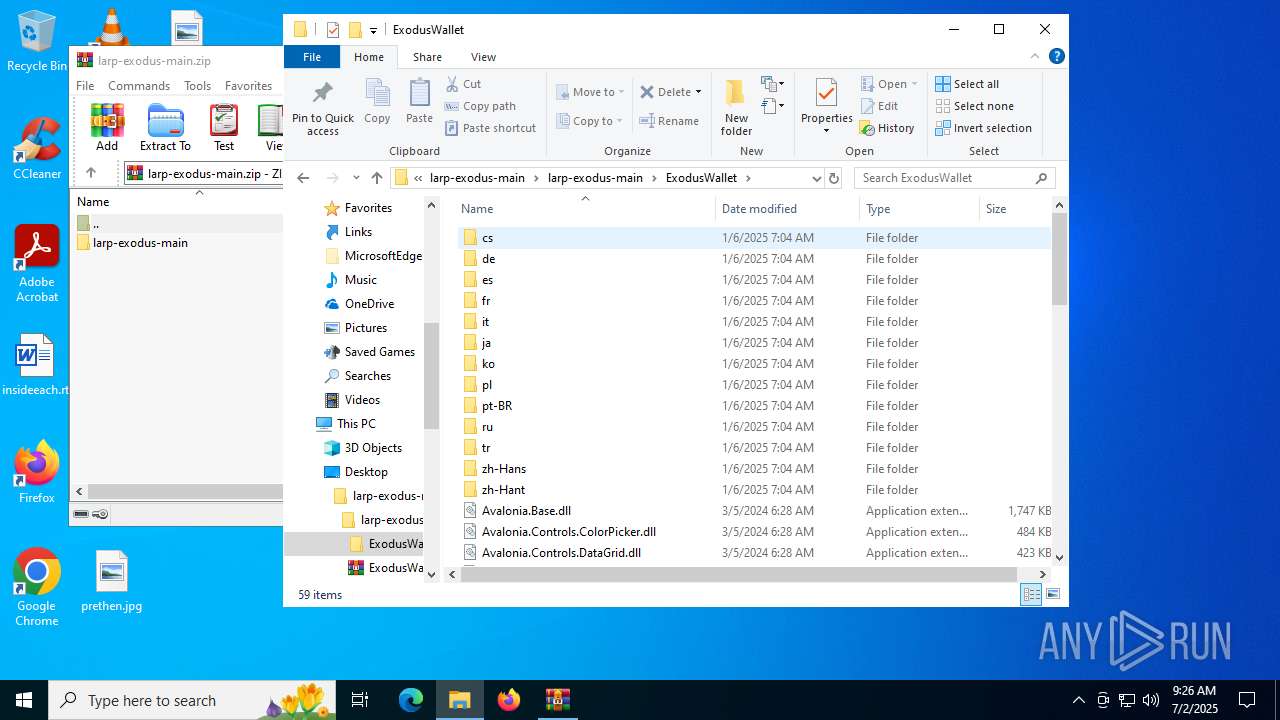
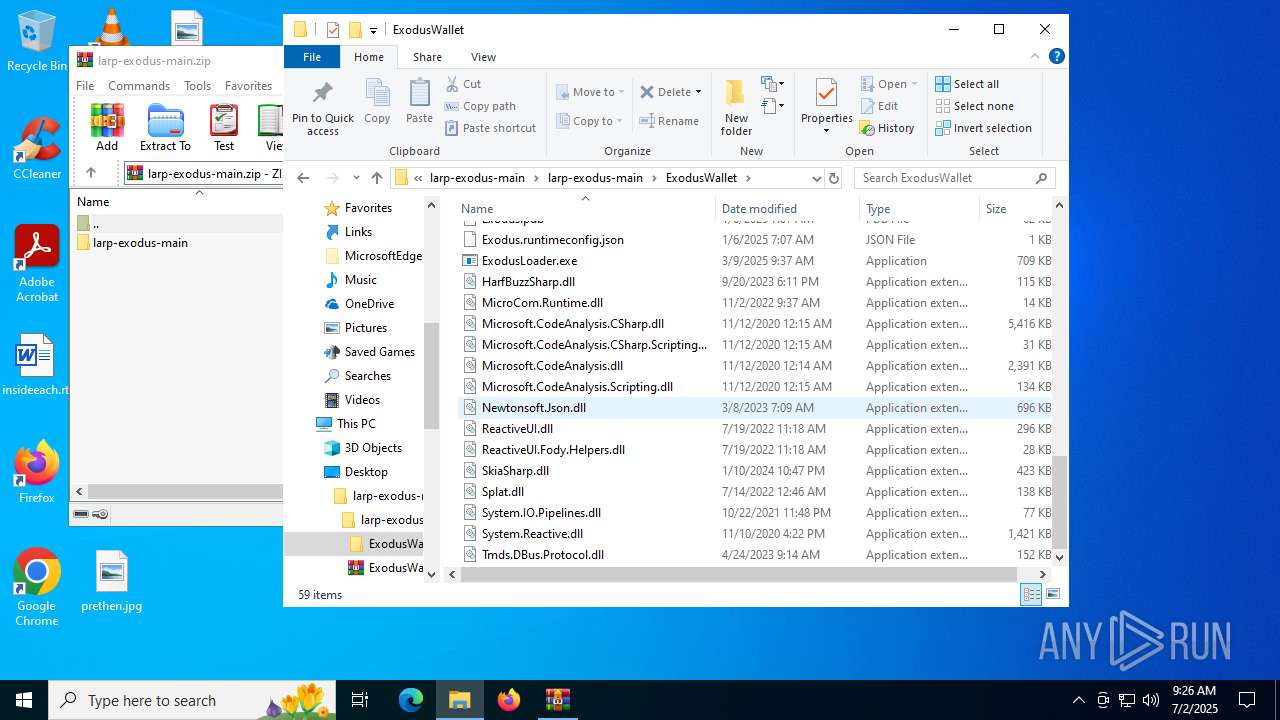
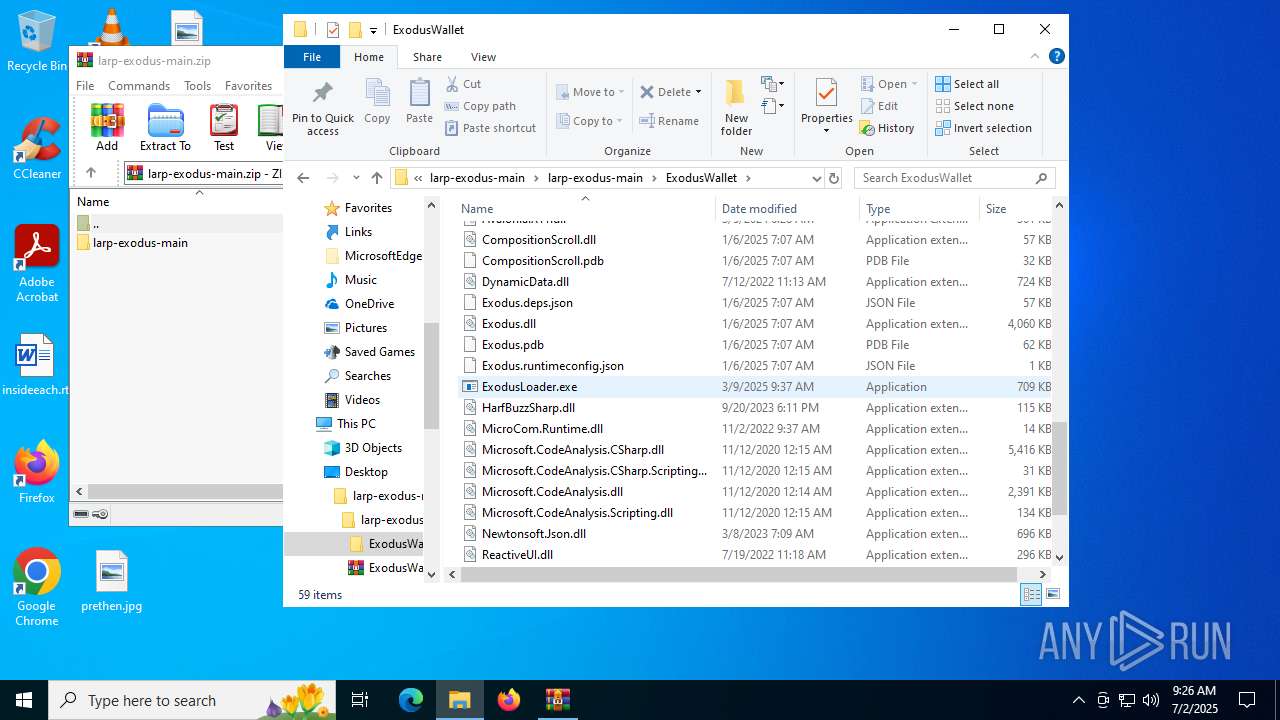
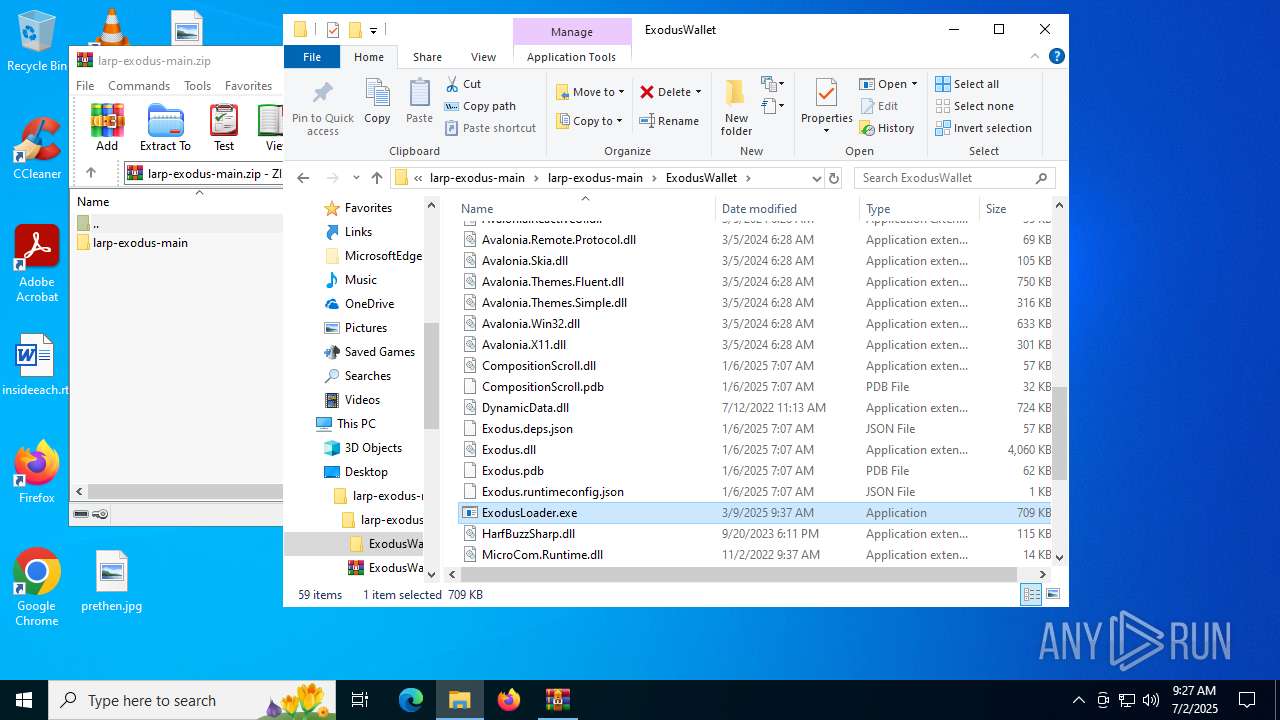
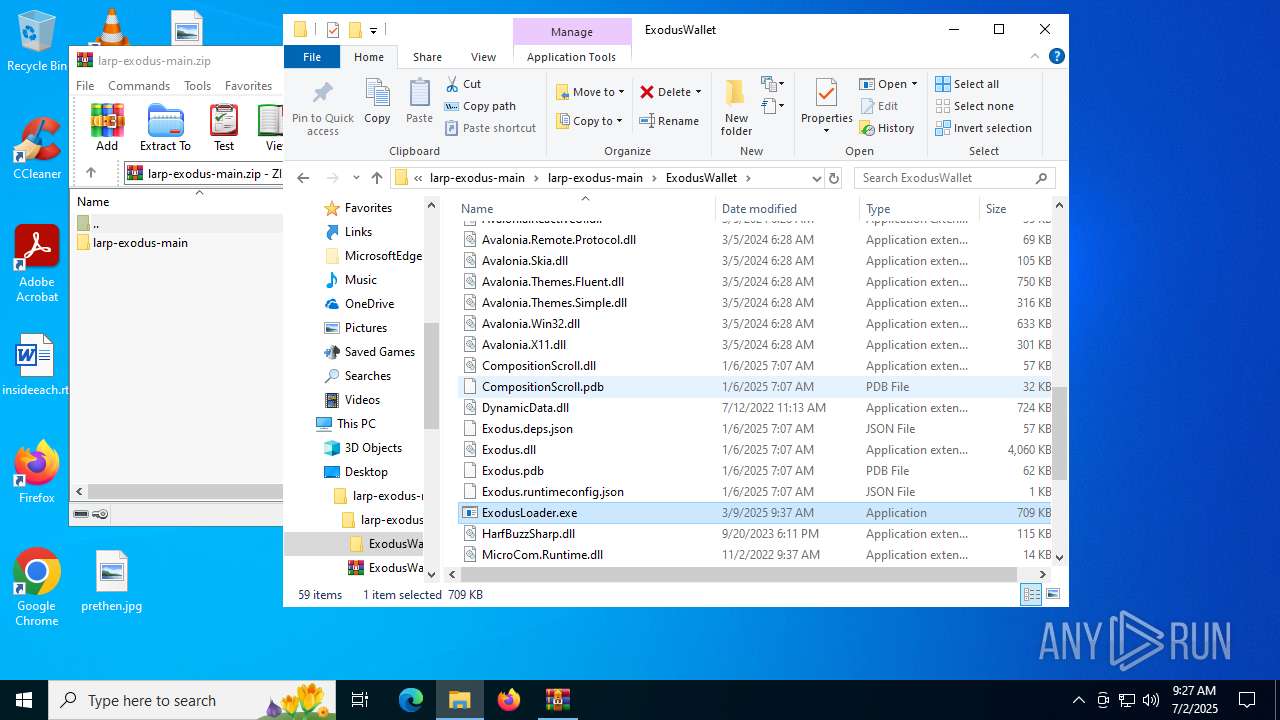
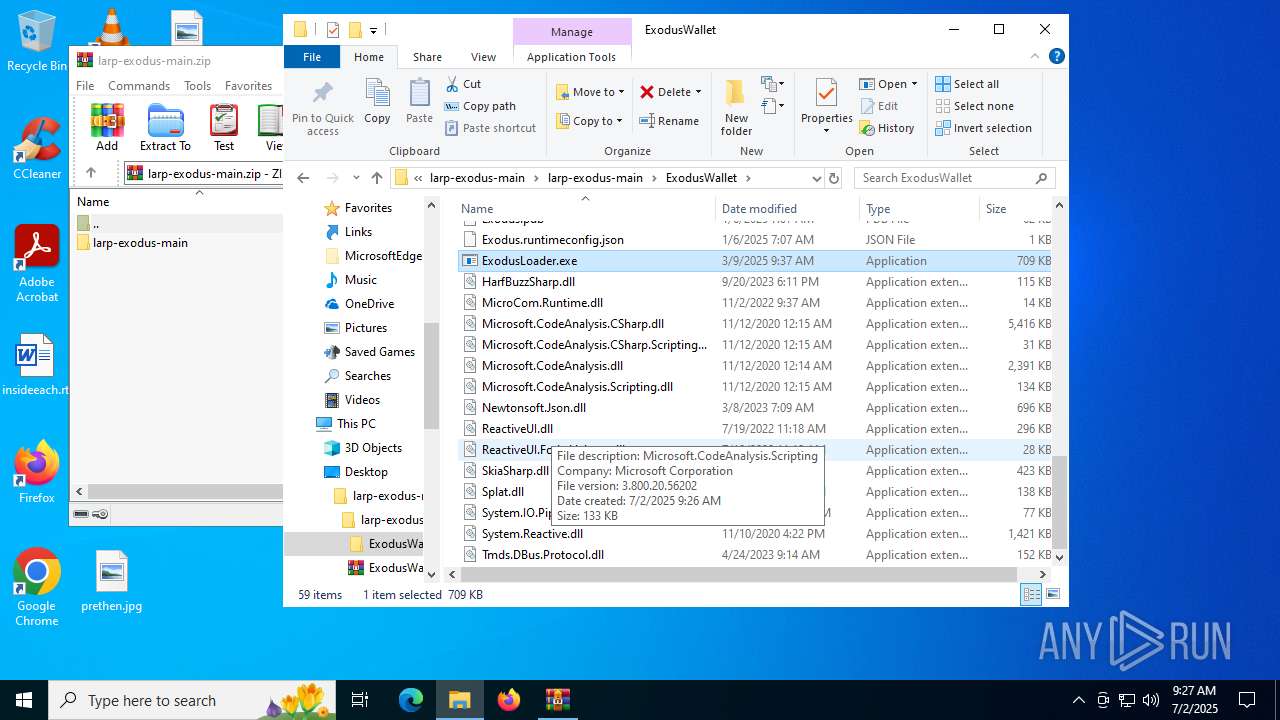
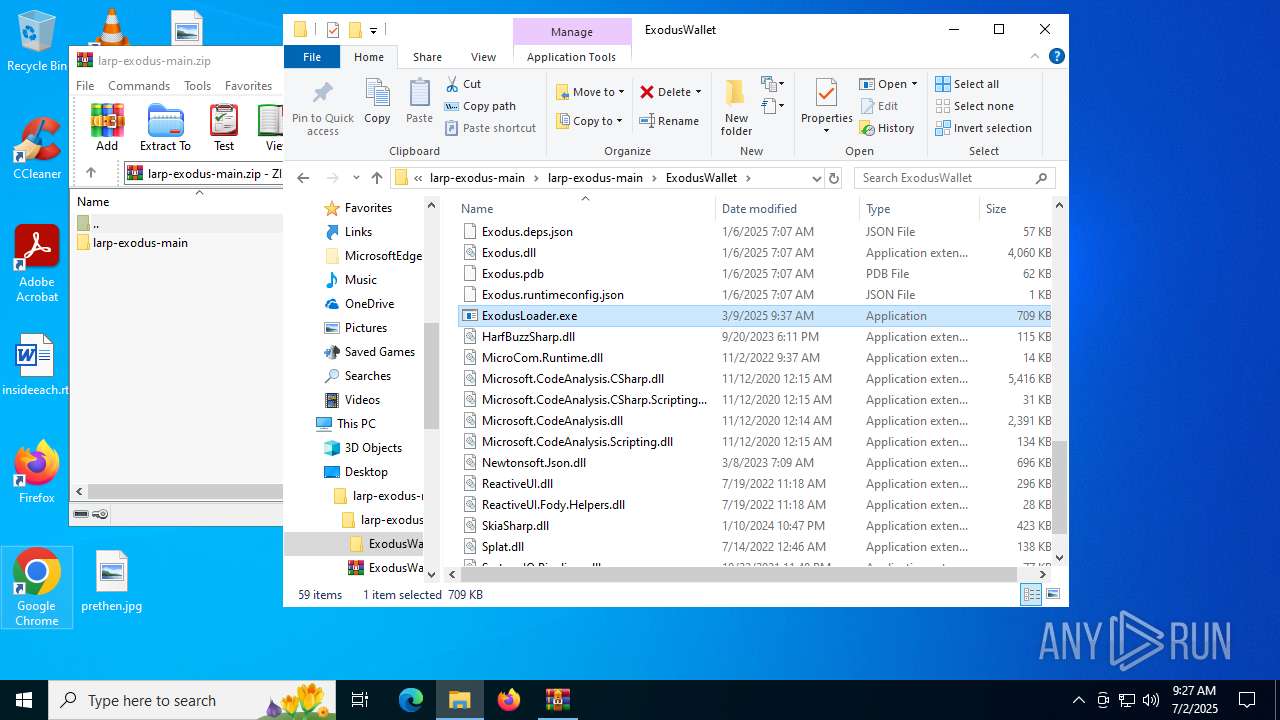
| File name: | larp-exodus-main.zip |
| Full analysis: | https://app.any.run/tasks/9c6c074e-3488-436f-9290-34e9b1384650 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | July 02, 2025, 09:26:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 8570C81C807180EC423404FB7908AE99 |
| SHA1: | 34287E0115DDE607C4A25AAEF771C762A591A6BD |
| SHA256: | BBA5F53C405C572979A2A250CE8883BA44C80ED31366D8E8A5447CC822A00C3B |
| SSDEEP: | 98304:S2HlCAskP4fWOW3xXpS7CrW2uM/Cfru+UYBByuX2teJoHHrlvl/bjTCjcFuXsd6F:3ehgI2kLZXKtK8AVZjOC6q |
MALICIOUS
QUASAR has been detected (YARA)
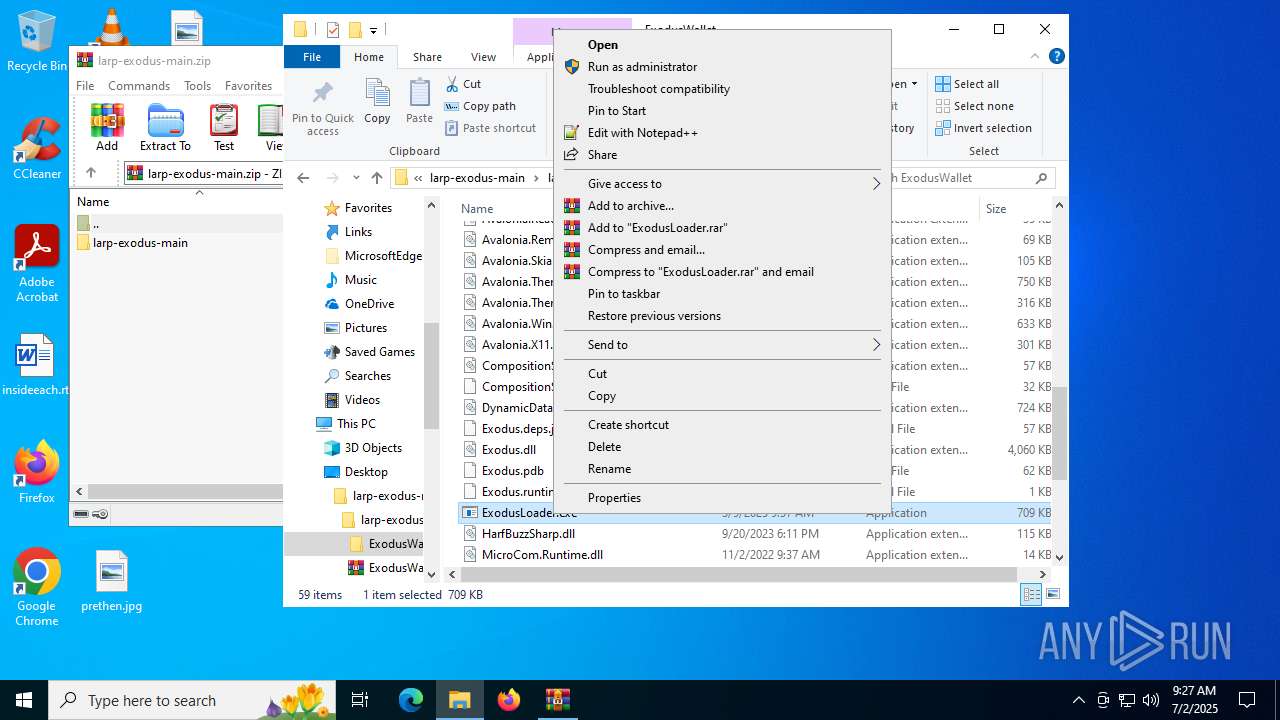
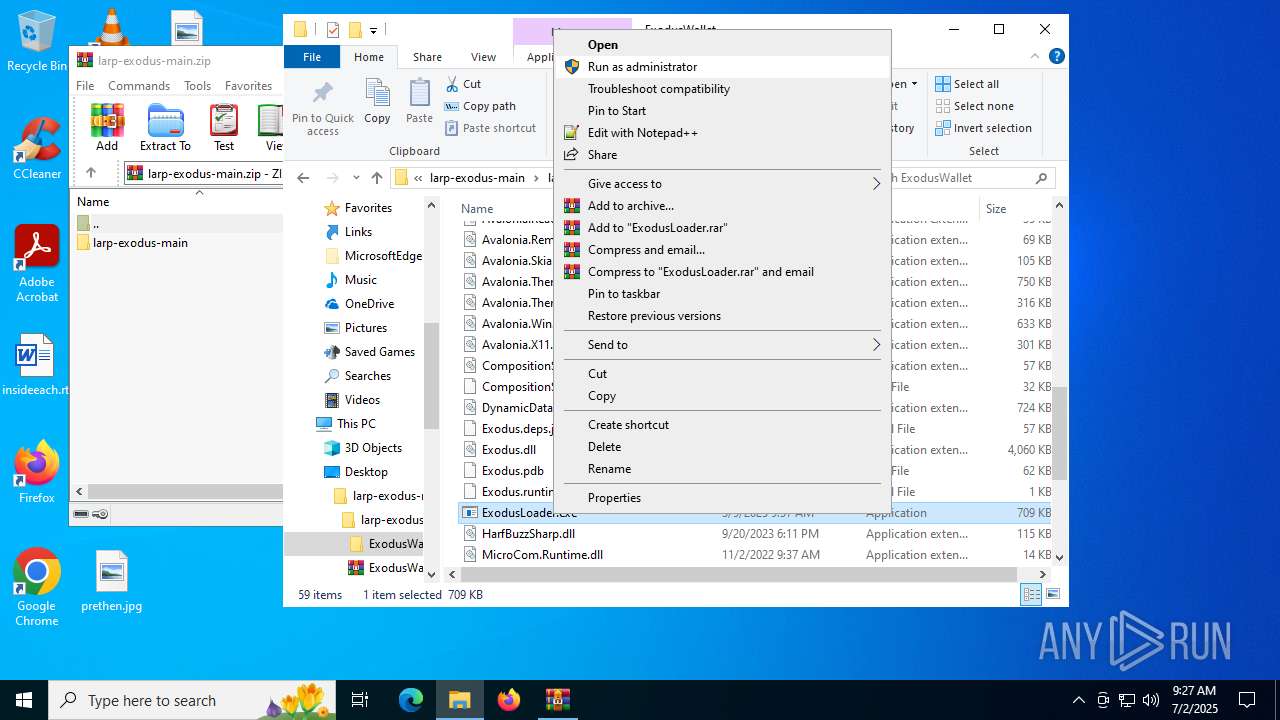
- ExodusLoader.exe (PID: 1068)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7032)
Process drops legitimate windows executable
- WinRAR.exe (PID: 5768)
- WinRAR.exe (PID: 7032)
Connects to unusual port
- ExodusLoader.exe (PID: 1068)
There is functionality for taking screenshot (YARA)
- ExodusLoader.exe (PID: 1068)
INFO
Reads the computer name
- ExodusLoader.exe (PID: 1068)
- ExodusLoader.exe (PID: 4808)
- ExodusLoader.exe (PID: 4788)
Reads the machine GUID from the registry
- ExodusLoader.exe (PID: 1068)
- ExodusLoader.exe (PID: 4808)
- ExodusLoader.exe (PID: 4788)
Manual execution by a user
- WinRAR.exe (PID: 5768)
- ExodusLoader.exe (PID: 4808)
- ExodusLoader.exe (PID: 1068)
- ExodusLoader.exe (PID: 4788)
- chrome.exe (PID: 1296)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5768)
Reads Environment values
- ExodusLoader.exe (PID: 1068)
- ExodusLoader.exe (PID: 4808)
- ExodusLoader.exe (PID: 4788)
Checks supported languages
- ExodusLoader.exe (PID: 1068)
- ExodusLoader.exe (PID: 4808)
- ExodusLoader.exe (PID: 4788)
Application launched itself
- chrome.exe (PID: 1296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(1068) ExodusLoader.exe
Version1.4.1
C2 (2)195.177.94.58:7000
Sub_DirSubDir
Install_NameClient.exe
Mutex7e03e3fb-22c0-4bc3-91c5-b78b68c8c267
StartupQuasar Modded Client Startup
Taglarpvault
LogDirLogs
Signatureeb6rcvggX2g2jJG+mT4TMCUgeiJ7yHmOXsTMFyHSFUGHWL9ArsaWLVobjwBoTirveRuv2Cud8ViZ+4sGgHiyMMzFL/MTsfWxOLYO2XZn6uJ3xQdHzW6bM4jGDwczxGvYEXJkAx1teye9B/BUHJcszcwxAF4x3GrYr7AmKKOpxL8nb4iL2CFXGxA+Eb7ya/3Ghb88IJydwXFhtkWqKBSnL9wnDyC0HoiA2bIF6+Dd3JBqHZuMvkVyJGzsHW2OljuIbiaKZHJJ/Sz3SN0woqihogftcKLg2z2GqYVIC8MXHz6B...
CertificateMIIFEzCCAvugAwIBAgIVANJOBlIqvxtJJZdAadGQZO16Mpq1MA0GCSqGSIb3DQEBDQUAMBUxEzARBgNVBAMMCk1vZCBTZXJ2ZXIwHhcNMjUwMzA3MTQwMDQ1WhcNMzUwMzA4MTQwMDQ1WjAVMRMwEQYDVQQDDApNb2QgU2VydmVyMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAjS2aLXlUspH5C7XyOfb8dvNAXvwZ/nxDz3xNkbzvwNYAMQaDJ1taksJWFXadFyvecotMLuqbD9JjsDEy6Kid...
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:03:09 03:04:06 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | larp-exodus-main/ |
Total processes
156
Monitored processes
18
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1068 | "C:\Users\admin\Desktop\larp-exodus-main\larp-exodus-main\ExodusWallet\ExodusLoader.exe" | C:\Users\admin\Desktop\larp-exodus-main\larp-exodus-main\ExodusWallet\ExodusLoader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.4.1 Modules
Quasar(PID) Process(1068) ExodusLoader.exe Version1.4.1 C2 (2)195.177.94.58:7000 Sub_DirSubDir Install_NameClient.exe Mutex7e03e3fb-22c0-4bc3-91c5-b78b68c8c267 StartupQuasar Modded Client Startup Taglarpvault LogDirLogs Signatureeb6rcvggX2g2jJG+mT4TMCUgeiJ7yHmOXsTMFyHSFUGHWL9ArsaWLVobjwBoTirveRuv2Cud8ViZ+4sGgHiyMMzFL/MTsfWxOLYO2XZn6uJ3xQdHzW6bM4jGDwczxGvYEXJkAx1teye9B/BUHJcszcwxAF4x3GrYr7AmKKOpxL8nb4iL2CFXGxA+Eb7ya/3Ghb88IJydwXFhtkWqKBSnL9wnDyC0HoiA2bIF6+Dd3JBqHZuMvkVyJGzsHW2OljuIbiaKZHJJ/Sz3SN0woqihogftcKLg2z2GqYVIC8MXHz6B... CertificateMIIFEzCCAvugAwIBAgIVANJOBlIqvxtJJZdAadGQZO16Mpq1MA0GCSqGSIb3DQEBDQUAMBUxEzARBgNVBAMMCk1vZCBTZXJ2ZXIwHhcNMjUwMzA3MTQwMDQ1WhcNMzUwMzA4MTQwMDQ1WjAVMRMwEQYDVQQDDApNb2QgU2VydmVyMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAjS2aLXlUspH5C7XyOfb8dvNAXvwZ/nxDz3xNkbzvwNYAMQaDJ1taksJWFXadFyvecotMLuqbD9JjsDEy6Kid... | |||||||||||||||
| 1296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --extension-process --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=3788,i,8925783843014469119,3683635749611460030,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3776 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=3148,i,8925783843014469119,3683635749611460030,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3188 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2356 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=1988,i,8925783843014469119,3683635749611460030,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=1952 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 3392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --field-trial-handle=3140,i,8925783843014469119,3683635749611460030,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3136 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 3648 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=4836,i,8925783843014469119,3683635749611460030,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=4944 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 3704 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3880 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4528 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=133.0.6943.127 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffc3ff7fff8,0x7ffc3ff80004,0x7ffc3ff80010 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
Total events
5 647
Read events
5 614
Write events
20
Delete events
13
Modification events
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\larp-exodus-main.zip | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
93
Suspicious files
12
Text files
20
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5768 | WinRAR.exe | C:\Users\admin\Desktop\larp-exodus-main\larp-exodus-main\ExodusWallet\ReactiveUI.Fody.Helpers.dll | executable | |
MD5:2276DC006B3C86F136CAC75E73EA0756 | SHA256:184BB1A17A1F30C38BD039FF776C3C6FE7A3F680A2B30D8785D3FF90E5FBD14E | |||
| 5768 | WinRAR.exe | C:\Users\admin\Desktop\larp-exodus-main\larp-exodus-main\ExodusWallet\MicroCom.Runtime.dll | executable | |
MD5:C27B01D179AB856B42E910496FE749F9 | SHA256:59839E18E46B06AB23B633944AE3C3B552A300C5DA389DA870DFA980BCEF93C1 | |||
| 5768 | WinRAR.exe | C:\Users\admin\Desktop\larp-exodus-main\larp-exodus-main\ExodusWallet\ReactiveUI.dll | executable | |
MD5:CB35EE743A0D1CB032849A15824F3EB1 | SHA256:620B8AEB14CDD6143D3FCB5273AF510CD898E50B08B6DD717BA124EB64E77BB5 | |||
| 5768 | WinRAR.exe | C:\Users\admin\Desktop\larp-exodus-main\larp-exodus-main\ExodusWallet\Microsoft.CodeAnalysis.CSharp.Scripting.dll | executable | |
MD5:B134242E74090BE398630D825939429F | SHA256:EB5185D1B4424BC2538C8DBB3311B787F8EFA153D68885E82EC199AA5A6B90DE | |||
| 5768 | WinRAR.exe | C:\Users\admin\Desktop\larp-exodus-main\larp-exodus-main\ExodusWallet\System.IO.Pipelines.dll | executable | |
MD5:90EB4D273FD68509702F2E68BD681177 | SHA256:F36033873E9BC148ABD9B1858312201547B479CAFA25312EC659F1B56A5DB3E2 | |||
| 5768 | WinRAR.exe | C:\Users\admin\Desktop\larp-exodus-main\larp-exodus-main\ExodusWallet\cs\Microsoft.CodeAnalysis.CSharp.Scripting.resources.dll | executable | |
MD5:08A3C9D07299343B8A7E18DB0E5EA672 | SHA256:252742341B4CD14AC19604D4274D4DB2657F052B366A24C0EB41470E7CCD4814 | |||
| 5768 | WinRAR.exe | C:\Users\admin\Desktop\larp-exodus-main\larp-exodus-main\ExodusWallet\Splat.dll | executable | |
MD5:5378F7B03620F7ED4275AC5D73FB86C0 | SHA256:626E82D8797EAE368DC11347DF2425D3F9860FCA8BA52DF741139895DFFA92A5 | |||
| 5768 | WinRAR.exe | C:\Users\admin\Desktop\larp-exodus-main\larp-exodus-main\ExodusWallet\cs\Microsoft.CodeAnalysis.CSharp.resources.dll | executable | |
MD5:98F732A2A542AC4D97392B7E42709131 | SHA256:3600CC8A8D83522BAA10F07FC7027D3CF64EF03B644A35DB920D248BBACCD30E | |||
| 5768 | WinRAR.exe | C:\Users\admin\Desktop\larp-exodus-main\larp-exodus-main\ExodusWallet\System.Reactive.dll | executable | |
MD5:EF5A00287AD15393D41B12AA4B726FF7 | SHA256:2B6C31DFB1FC6019A42A007ED0E5E00574DE6EA0C47FED0CA282BF3BB2771B0C | |||
| 5768 | WinRAR.exe | C:\Users\admin\Desktop\larp-exodus-main\larp-exodus-main\ExodusWallet\Tmds.DBus.Protocol.dll | executable | |
MD5:492783813953BF82E43C2083BF262A7C | SHA256:6A38C93A728FA33DD1EE35EA5E12EBEF9E9365C2A550D2A1C3D54E46DF8594BA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
47
DNS requests
38
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2072 | SIHClient.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2072 | SIHClient.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3944 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7064 | chrome.exe | GET | 200 | 142.250.184.206:80 | http://clients2.google.com/time/1/current?cup2key=8:-XFL2ZDs1bdyp0L8QrQ59KdDlf_LR5MUlOyBXzQh5NQ&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.18.121.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
7136 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1268 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.18.121.147:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
1268 | svchost.exe | 104.85.1.163:80 | www.microsoft.com | AKAMAI-AS | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3944 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |