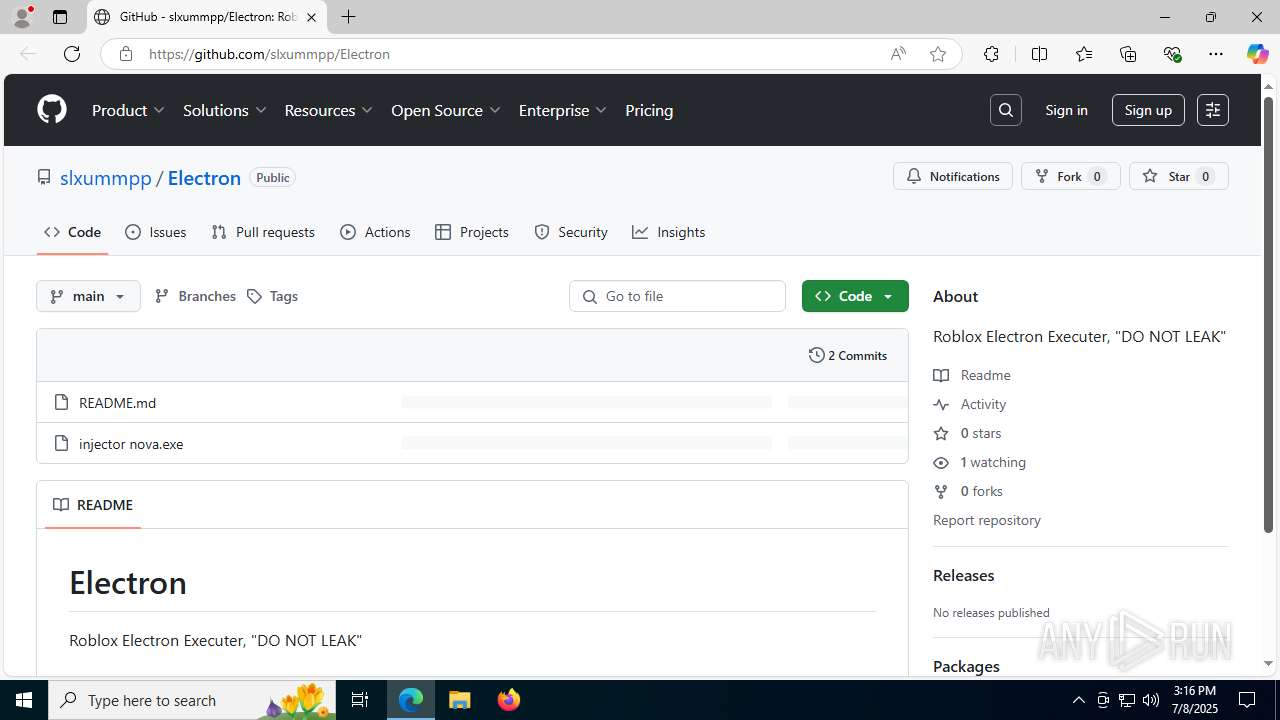
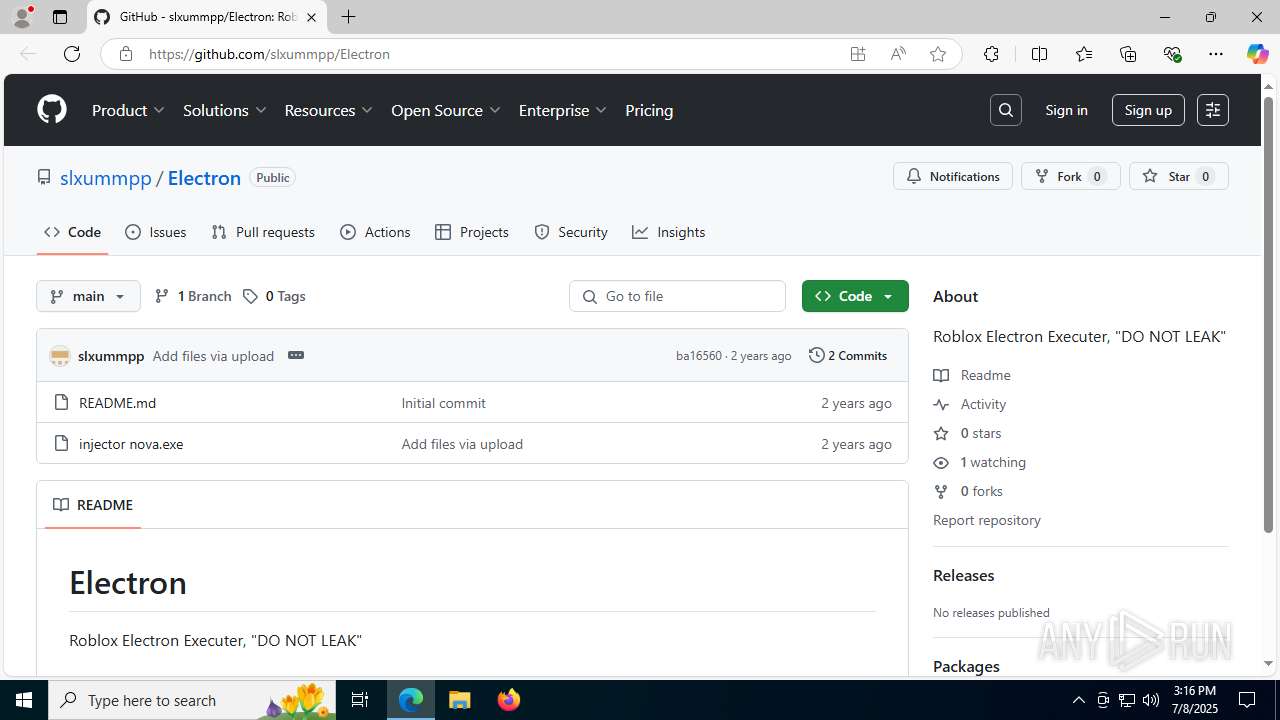
| URL: | https://github.com/slxummpp/Electron |
| Full analysis: | https://app.any.run/tasks/4209fccb-7681-4f56-9826-10fba4567e7a |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | July 08, 2025, 15:15:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| MD5: | 42DD1FD4864F3D29A33EF49CD6E67D08 |
| SHA1: | 3F175AB2C64F58736C9AB27CE7CB31C5C38EDFDD |
| SHA256: | BB7A698BB1D656B55D4673C54C534C41694D4B1D1DEC9B0CD28CF3FAD5F5FA82 |
| SSDEEP: | 3:N8tEdmJUTjRA:2uwJsK |
MALICIOUS
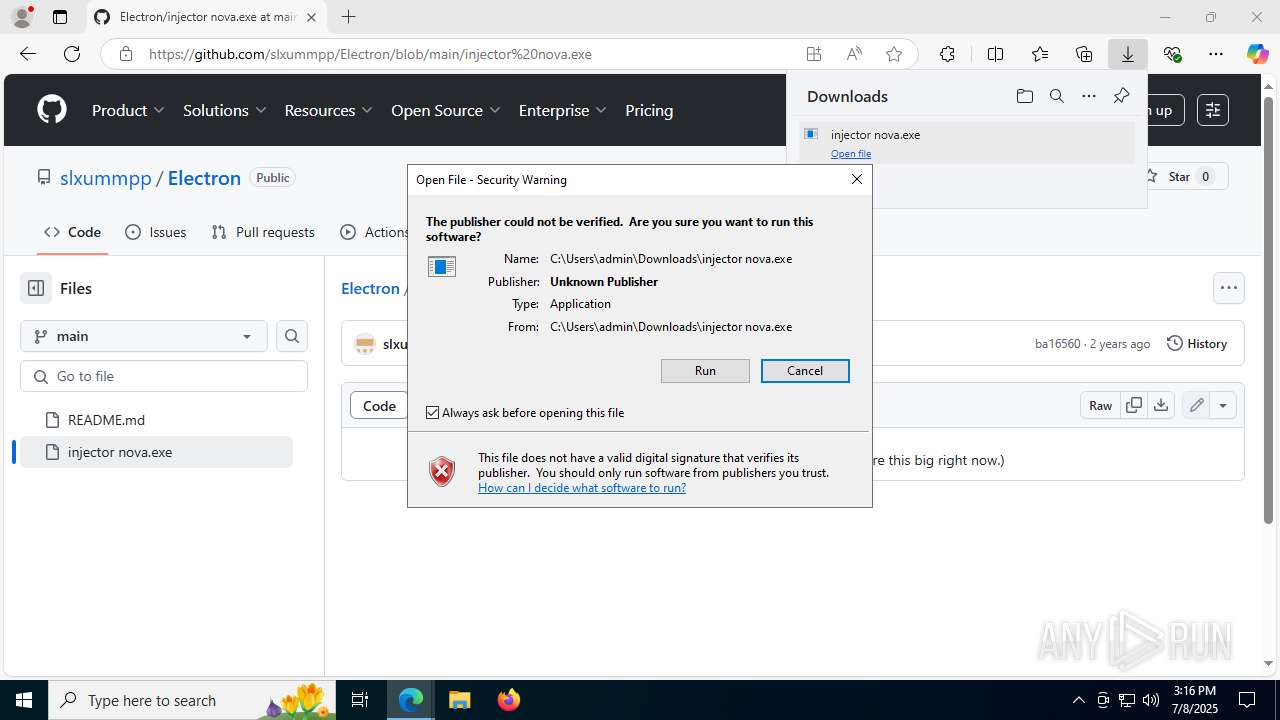
Executing a file with an untrusted certificate
- injector nova.exe (PID: 7820)
- injector nova.exe (PID: 7860)
- injector nova.exe (PID: 6788)
- injector nova.exe (PID: 4860)
BlankGrabber has been detected
- injector nova.exe (PID: 7820)
- injector nova.exe (PID: 6788)
Adds path to the Windows Defender exclusion list
- injector nova.exe (PID: 4860)
- cmd.exe (PID: 7956)
- cmd.exe (PID: 7932)
- cmd.exe (PID: 8028)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 7952)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 7768)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 7768)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 7768)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 7768)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 7768)
Changes settings for real-time protection
- powershell.exe (PID: 7768)
Changes Windows Defender settings
- cmd.exe (PID: 7952)
- cmd.exe (PID: 7932)
- cmd.exe (PID: 8028)
- cmd.exe (PID: 7956)
Changes Controlled Folder Access settings
- powershell.exe (PID: 7768)
Create files in the Startup directory
- injector nova.exe (PID: 4860)
Actions looks like stealing of personal data
- injector nova.exe (PID: 4860)
Steals credentials from Web Browsers
- injector nova.exe (PID: 4860)
Bypass execution policy to execute commands
- powershell.exe (PID: 8556)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 7732)
Resets Windows Defender malware definitions to the base version
- MpCmdRun.exe (PID: 8380)
Steals Growtopia credentials and data (YARA)
- injector nova.exe (PID: 4860)
DISCORDGRABBER has been detected (YARA)
- injector nova.exe (PID: 4860)
BLANKGRABBER has been detected (SURICATA)
- injector nova.exe (PID: 4860)
Starts CMD.EXE for self-deleting
- injector nova.exe (PID: 4860)
SUSPICIOUS
Process drops legitimate windows executable
- msedge.exe (PID: 6528)
- msedge.exe (PID: 1976)
- injector nova.exe (PID: 7820)
- injector nova.exe (PID: 6788)
- injector nova.exe (PID: 4860)
Application launched itself
- injector nova.exe (PID: 7820)
- injector nova.exe (PID: 7860)
- injector nova.exe (PID: 6788)
Reads the date of Windows installation
- injector nova.exe (PID: 7860)
The process drops C-runtime libraries
- injector nova.exe (PID: 7820)
- injector nova.exe (PID: 6788)
Executable content was dropped or overwritten
- injector nova.exe (PID: 7820)
- injector nova.exe (PID: 6788)
- injector nova.exe (PID: 4860)
- bound.exe (PID: 8096)
- csc.exe (PID: 3788)
Reads security settings of Internet Explorer
- injector nova.exe (PID: 7860)
Process drops python dynamic module
- injector nova.exe (PID: 7820)
- injector nova.exe (PID: 6788)
Starts CMD.EXE for commands execution
- injector nova.exe (PID: 4860)
Get information on the list of running processes
- injector nova.exe (PID: 4860)
- cmd.exe (PID: 864)
- cmd.exe (PID: 7312)
- cmd.exe (PID: 2116)
- cmd.exe (PID: 6756)
Found strings related to reading or modifying Windows Defender settings
- injector nova.exe (PID: 4860)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7956)
- cmd.exe (PID: 7952)
- cmd.exe (PID: 7932)
- cmd.exe (PID: 8028)
- cmd.exe (PID: 3724)
- cmd.exe (PID: 7732)
- cmd.exe (PID: 8352)
- cmd.exe (PID: 7816)
- cmd.exe (PID: 7244)
- cmd.exe (PID: 7300)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 7952)
Script disables Windows Defender's IPS
- cmd.exe (PID: 7952)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 7932)
- cmd.exe (PID: 8028)
- cmd.exe (PID: 7956)
The executable file from the user directory is run by the CMD process
- bound.exe (PID: 8096)
- rar.exe (PID: 8716)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 7404)
- cmd.exe (PID: 3788)
- cmd.exe (PID: 1480)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 7400)
- WMIC.exe (PID: 1352)
Checks for external IP
- svchost.exe (PID: 2200)
- injector nova.exe (PID: 4860)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 7772)
- cmd.exe (PID: 5104)
- cmd.exe (PID: 8892)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 7796)
- WMIC.exe (PID: 6680)
- WMIC.exe (PID: 7216)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 8012)
Base64-obfuscated command line is found
- cmd.exe (PID: 7732)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7732)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 7732)
Starts application with an unusual extension
- cmd.exe (PID: 8620)
- cmd.exe (PID: 3940)
- cmd.exe (PID: 8984)
- cmd.exe (PID: 8868)
- cmd.exe (PID: 9080)
- cmd.exe (PID: 9164)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 8292)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 8104)
CSC.EXE is used to compile C# code
- csc.exe (PID: 3788)
Captures screenshot (POWERSHELL)
- powershell.exe (PID: 8556)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 8760)
- cmd.exe (PID: 8912)
- cmd.exe (PID: 9012)
- cmd.exe (PID: 7676)
- cmd.exe (PID: 8704)
- cmd.exe (PID: 8144)
- cmd.exe (PID: 7976)
- cmd.exe (PID: 9040)
- cmd.exe (PID: 3656)
- cmd.exe (PID: 8284)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 8844)
- cmd.exe (PID: 8316)
Possible usage of Discord/Telegram API has been detected (YARA)
- injector nova.exe (PID: 4860)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 8204)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 2648)
Hides command output
- cmd.exe (PID: 1324)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 504)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 7052)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1324)
INFO
Checks supported languages
- identity_helper.exe (PID: 7640)
- injector nova.exe (PID: 7820)
- injector nova.exe (PID: 7860)
- injector nova.exe (PID: 6788)
- injector nova.exe (PID: 4860)
- bound.exe (PID: 8096)
- tree.com (PID: 8484)
- tree.com (PID: 8760)
- tree.com (PID: 9060)
- tree.com (PID: 8948)
- tree.com (PID: 9140)
- MpCmdRun.exe (PID: 8380)
- csc.exe (PID: 3788)
- cvtres.exe (PID: 6124)
- tree.com (PID: 3656)
- rar.exe (PID: 8716)
The sample compiled with english language support
- msedge.exe (PID: 1976)
- msedge.exe (PID: 6528)
- injector nova.exe (PID: 7820)
- injector nova.exe (PID: 6788)
- injector nova.exe (PID: 4860)
Reads the computer name
- injector nova.exe (PID: 7820)
- injector nova.exe (PID: 7860)
- identity_helper.exe (PID: 7640)
- injector nova.exe (PID: 6788)
- injector nova.exe (PID: 4860)
- MpCmdRun.exe (PID: 8380)
Executable content was dropped or overwritten
- msedge.exe (PID: 6528)
- msedge.exe (PID: 1976)
Create files in a temporary directory
- injector nova.exe (PID: 7820)
- injector nova.exe (PID: 6788)
- injector nova.exe (PID: 4860)
- injector nova.exe (PID: 7860)
- csc.exe (PID: 3788)
- MpCmdRun.exe (PID: 8380)
- cvtres.exe (PID: 6124)
- rar.exe (PID: 8716)
Application launched itself
- msedge.exe (PID: 6528)
Reads Environment values
- identity_helper.exe (PID: 7640)
Process checks computer location settings
- injector nova.exe (PID: 7860)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7400)
- WMIC.exe (PID: 7796)
- WMIC.exe (PID: 6680)
- WMIC.exe (PID: 8292)
- WMIC.exe (PID: 7052)
- WMIC.exe (PID: 6228)
- WMIC.exe (PID: 1352)
- WMIC.exe (PID: 7216)
Launching a file from the Startup directory
- injector nova.exe (PID: 4860)
Creates files in the program directory
- injector nova.exe (PID: 4860)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7660)
- powershell.exe (PID: 7768)
- powershell.exe (PID: 8076)
- powershell.exe (PID: 7444)
The Powershell gets current clipboard
- powershell.exe (PID: 8320)
Checks the directory tree
- tree.com (PID: 8760)
- tree.com (PID: 8948)
- tree.com (PID: 9060)
- tree.com (PID: 9140)
- tree.com (PID: 8484)
- tree.com (PID: 3656)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8076)
- powershell.exe (PID: 7768)
- powershell.exe (PID: 7660)
- powershell.exe (PID: 7444)
- powershell.exe (PID: 5612)
- powershell.exe (PID: 8688)
Reads the machine GUID from the registry
- csc.exe (PID: 3788)
- rar.exe (PID: 8716)
PyInstaller has been detected (YARA)
- injector nova.exe (PID: 6788)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 8460)
Found Base64 encoded reflection usage via PowerShell (YARA)
- injector nova.exe (PID: 4860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(4860) injector nova.exe
Discord-Webhook-Tokens (1)1163028176633606227/It3so33FmI2_r4N6_YF1v3GCJVE5S9-C4R0y1AEvFhK2UMYq_ORqnBtu2IHIkaCTva47
Discord-Info-Links
1163028176633606227/It3so33FmI2_r4N6_YF1v3GCJVE5S9-C4R0y1AEvFhK2UMYq_ORqnBtu2IHIkaCTva47
Get Webhook Infohttps://discord.com/api/webhooks/1163028176633606227/It3so33FmI2_r4N6_YF1v3GCJVE5S9-C4R0y1AEvFhK2UMYq_ORqnBtu2IHIkaCTva47
Total processes
326
Monitored processes
187
Malicious processes
10
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | taskkill /F /PID 6240 | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 504 | C:\WINDOWS\system32\cmd.exe /c "netsh wlan show profile" | C:\Windows\System32\cmd.exe | — | injector nova.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4236,i,1611958611366860973,8676336621021482638,262144 --variations-seed-version --mojo-platform-channel-handle=4312 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 864 | C:\WINDOWS\system32\cmd.exe /c "tasklist /FO LIST" | C:\Windows\System32\cmd.exe | — | injector nova.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | C:\WINDOWS\system32\cmd.exe /c "ping localhost -n 3 > NUL && del /A H /F "C:\Users\admin\Downloads\injector nova.exe"" | C:\Windows\System32\cmd.exe | — | injector nova.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1332 | REG QUERY HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4D36E968-E325-11CE-BFC1-08002BE10318}\0000\ProviderName 2 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1352 | wmic csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
74 859
Read events
74 837
Write events
22
Delete events
0
Modification events
| (PID) Process: | (6528) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6528) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6528) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6528) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6528) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6528) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6528) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 509193B802982F00 | |||
| (PID) Process: | (6528) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459378 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {DBE1D1A0-D7EF-441A-846B-BADE19C57C97} | |||
| (PID) Process: | (6528) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459378 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {14864F53-4652-4D10-9968-003132551FE3} | |||
| (PID) Process: | (6528) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459378 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5614A625-4EB1-43C2-A63F-E8F9C6619216} | |||
Executable files
44
Suspicious files
337
Text files
116
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6528 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF17593b.TMP | — | |
MD5:— | SHA256:— | |||
| 6528 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6528 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF17593b.TMP | — | |
MD5:— | SHA256:— | |||
| 6528 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6528 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF17594b.TMP | — | |
MD5:— | SHA256:— | |||
| 6528 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6528 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF17594b.TMP | — | |
MD5:— | SHA256:— | |||
| 6528 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6528 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF17595b.TMP | — | |
MD5:— | SHA256:— | |||
| 6528 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
73
DNS requests
68
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1688 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1976 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:heUjSLDu7VS9RxvTCgkV6CBCjq1n1NoQqp7UOihDHsw&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4860 | injector nova.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.30:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6528 | msedge.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEEj8k7RgVZSNNqfJionWlBY%3D | unknown | — | — | whitelisted |
8180 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6528 | msedge.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRd0JozUYXMqqW4y4zJTrLcMCRSkAQUgTKSQSsozUbIxKLGKjkS7EipPxQCEQC%2FsVABu%2FWS1JYqd5fqc2%2Bj | unknown | — | — | whitelisted |
8180 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6528 | msedge.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEDPXCKiRQFMZ4qW70zm5rW4%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4860 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1976 | msedge.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
1976 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1976 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1976 | msedge.exe | 104.126.37.136:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
1976 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
github.com |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| whitelisted |
user-images.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Possible Chrome Plugin install |
1976 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
1976 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
— | — | Misc activity | ET HUNTING EXE Downloaded from Github |
— | — | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
2200 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
4860 | injector nova.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2200 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2200 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |