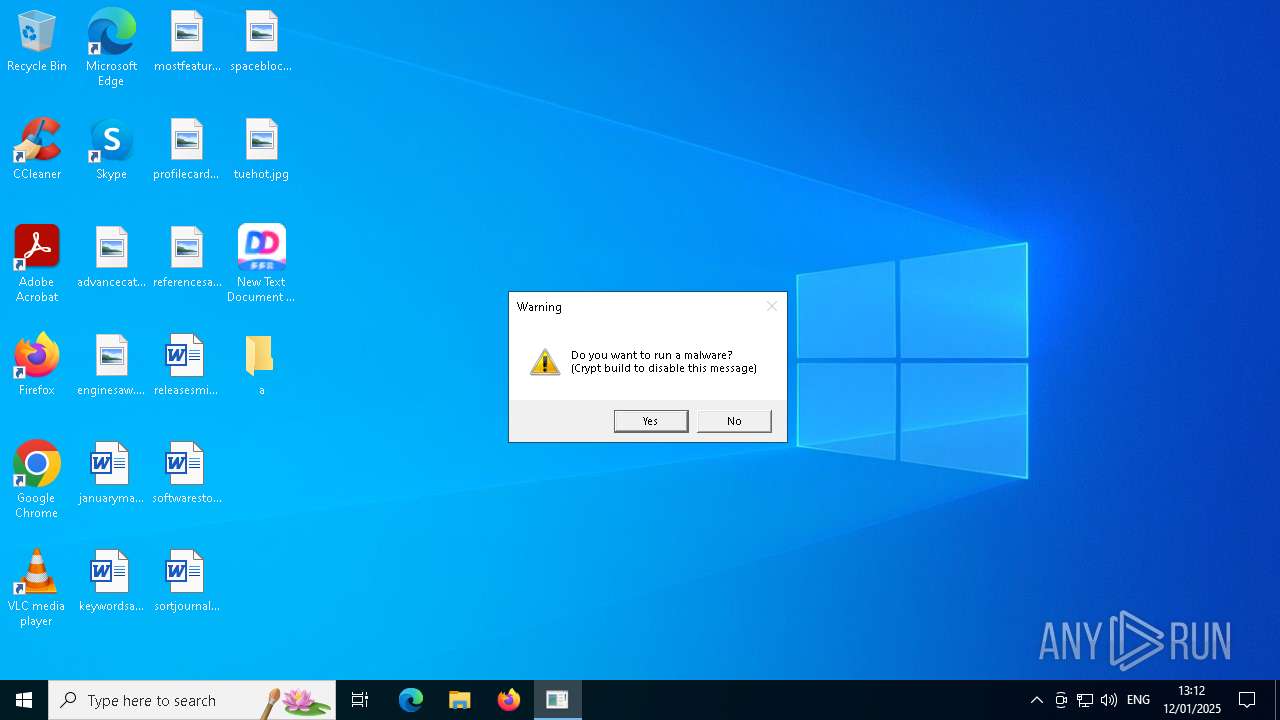
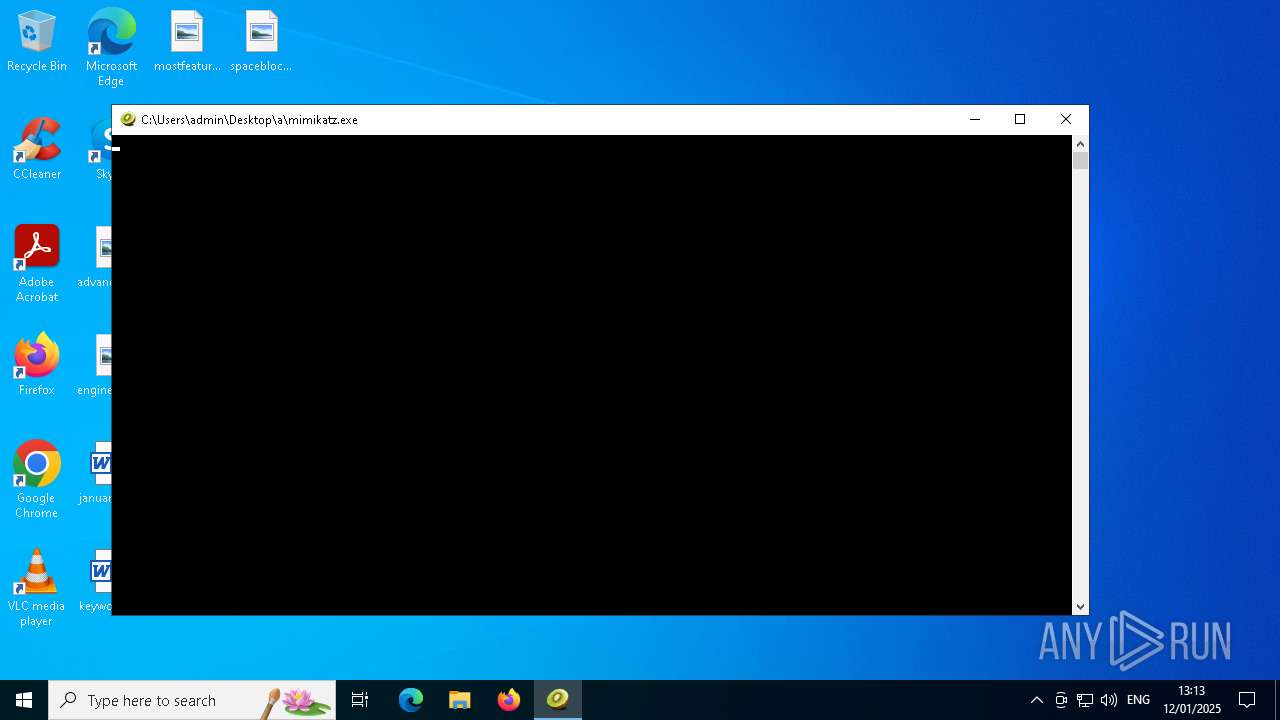
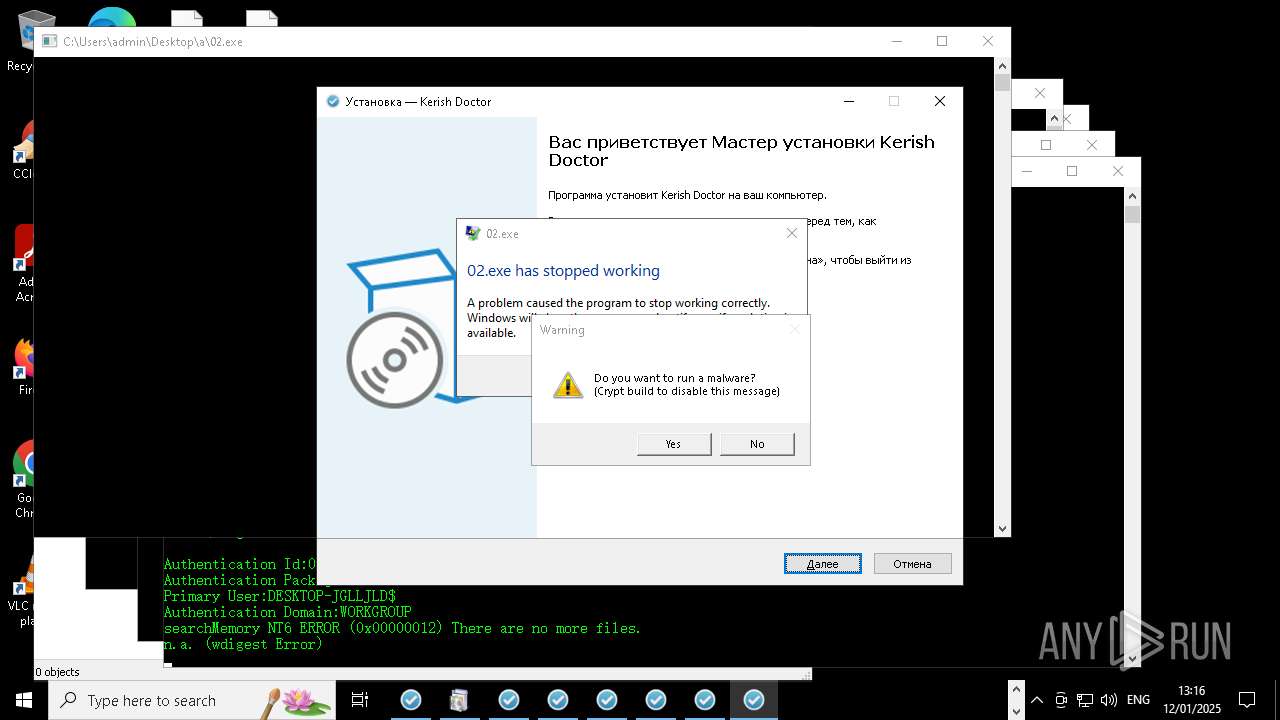
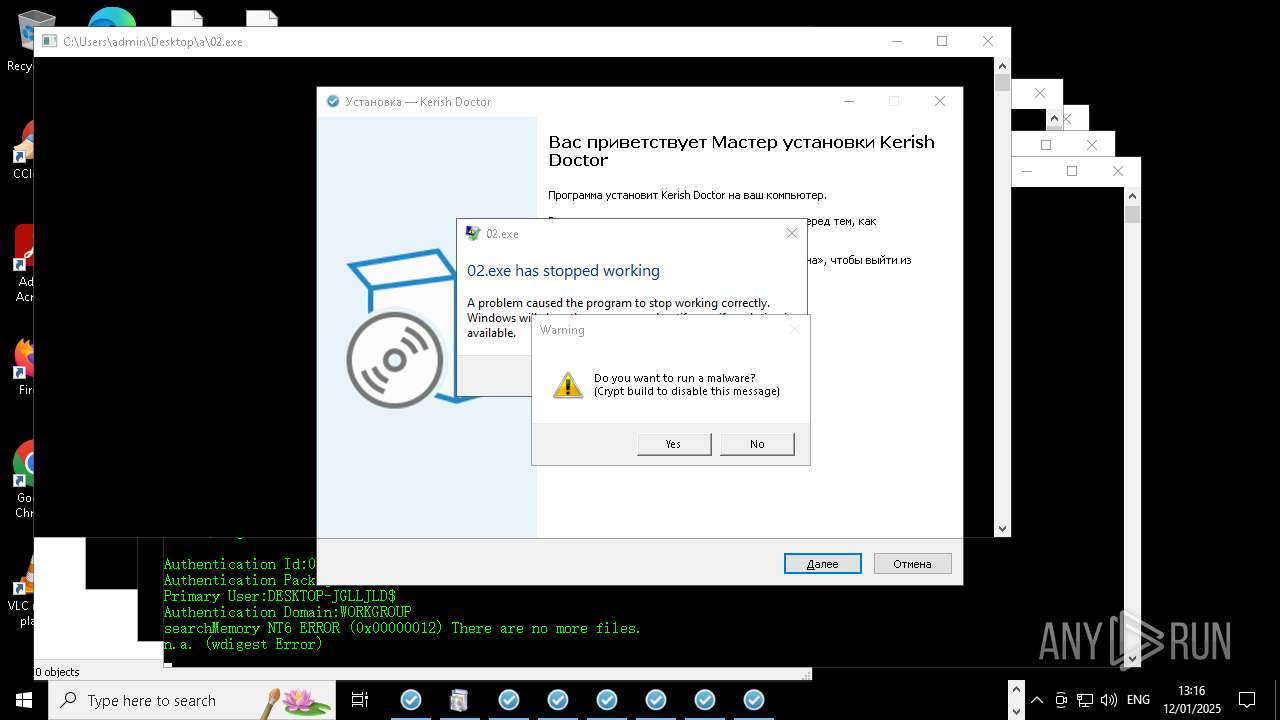
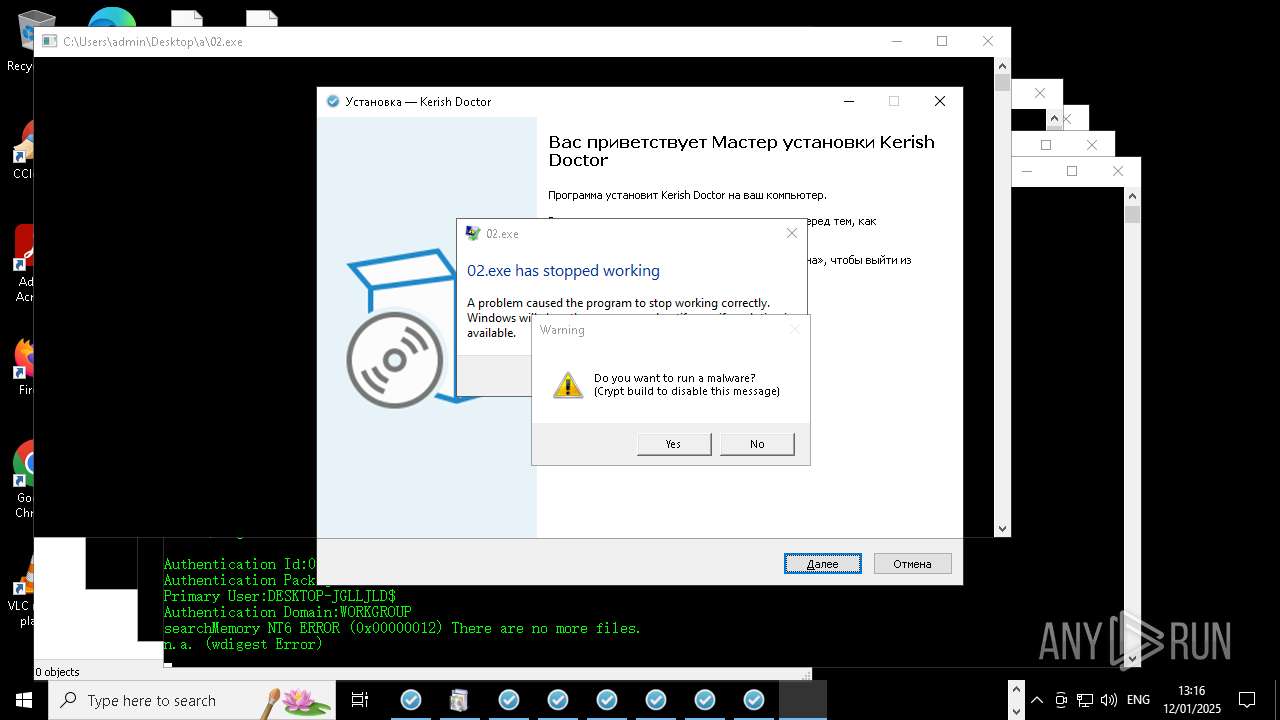
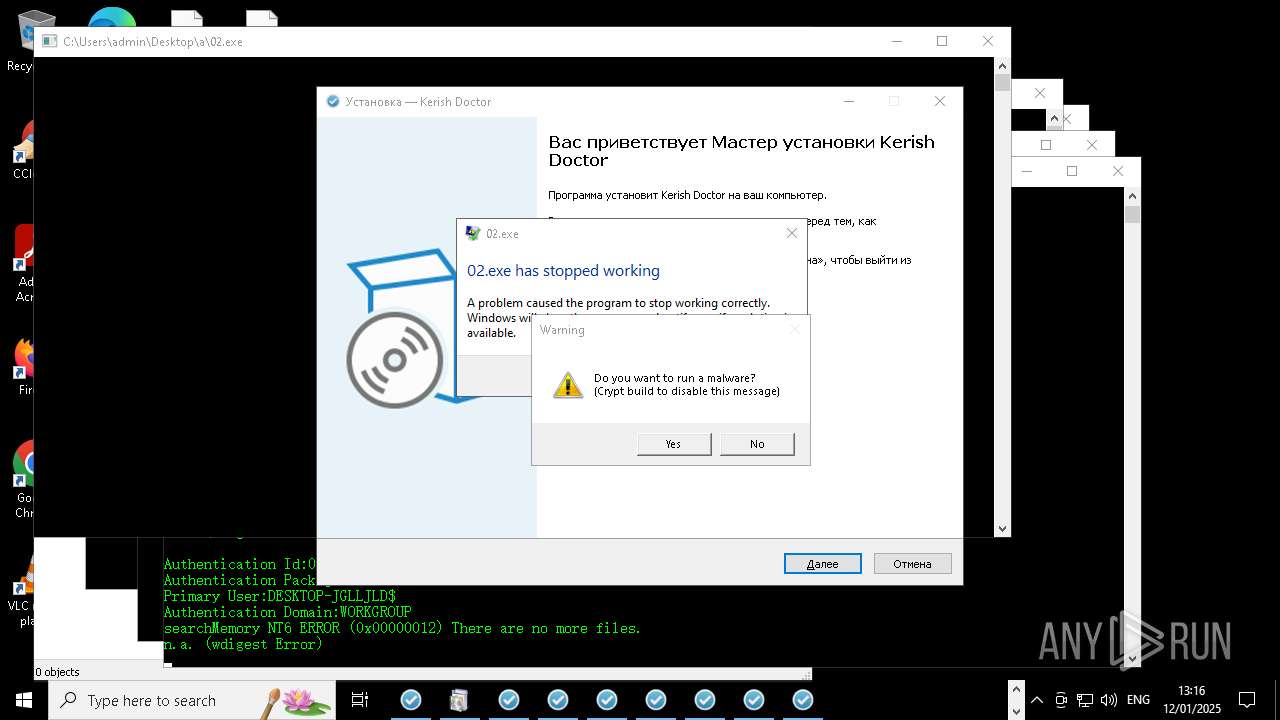
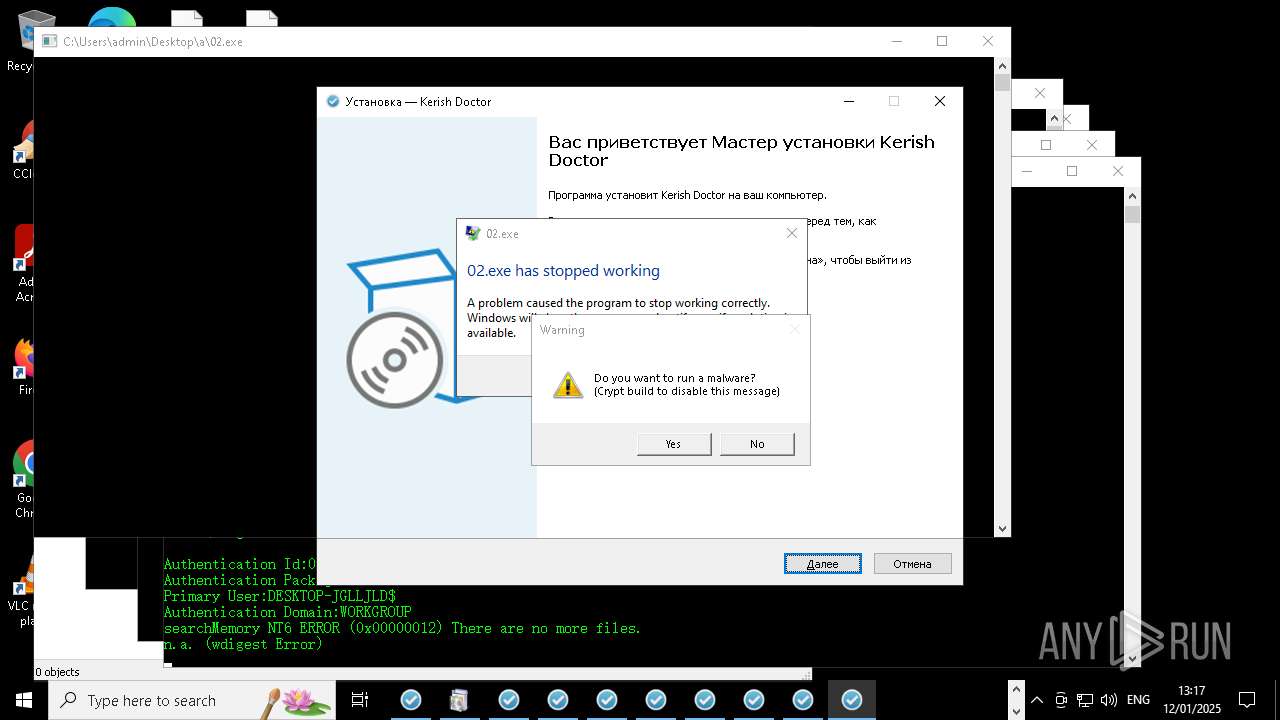
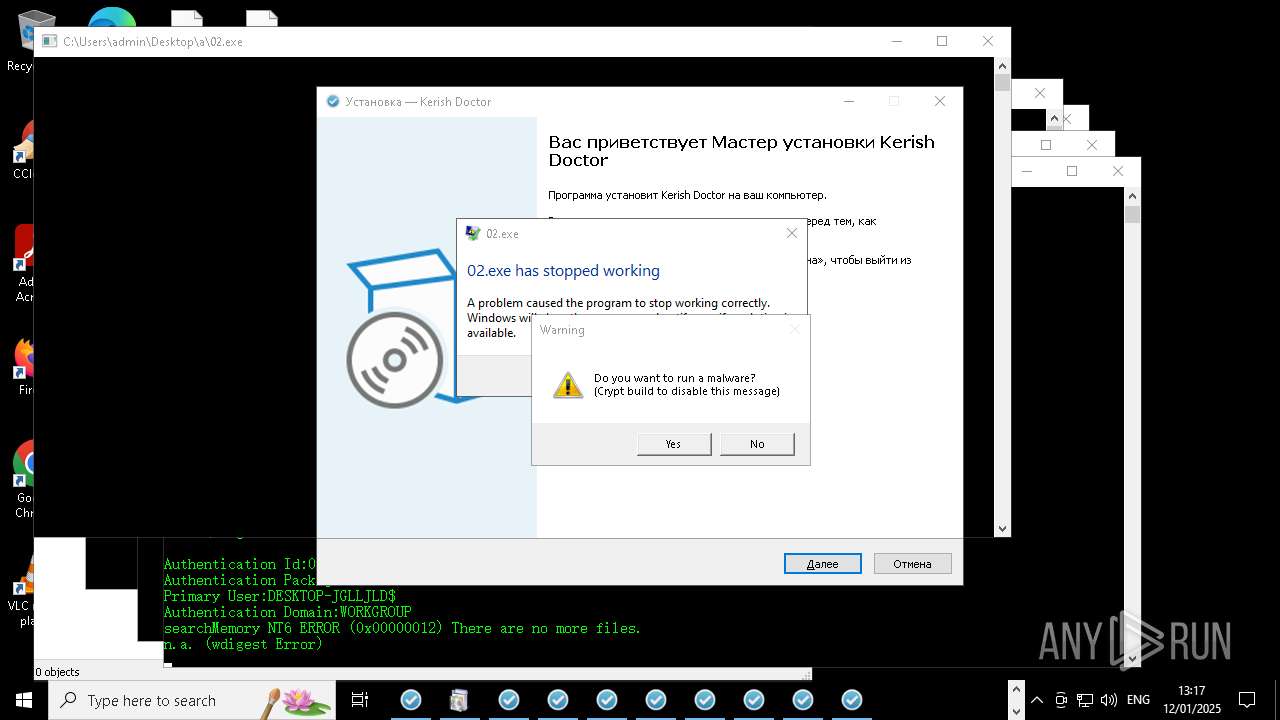
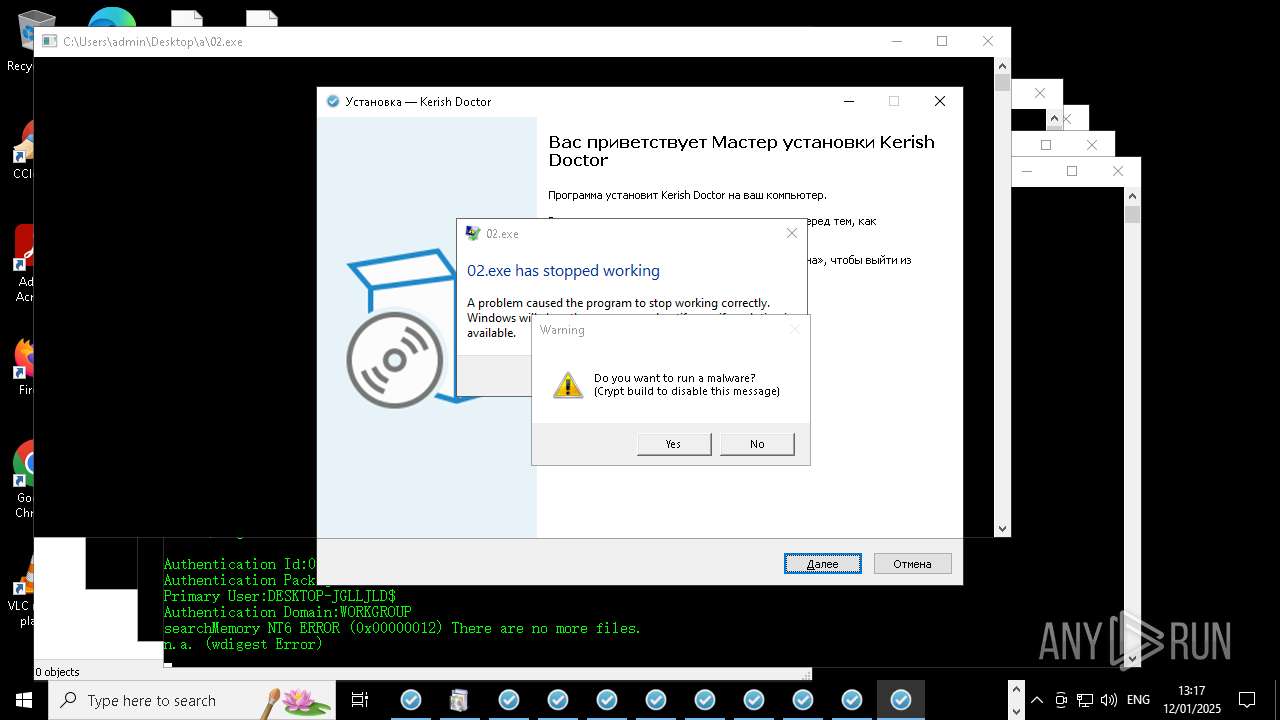
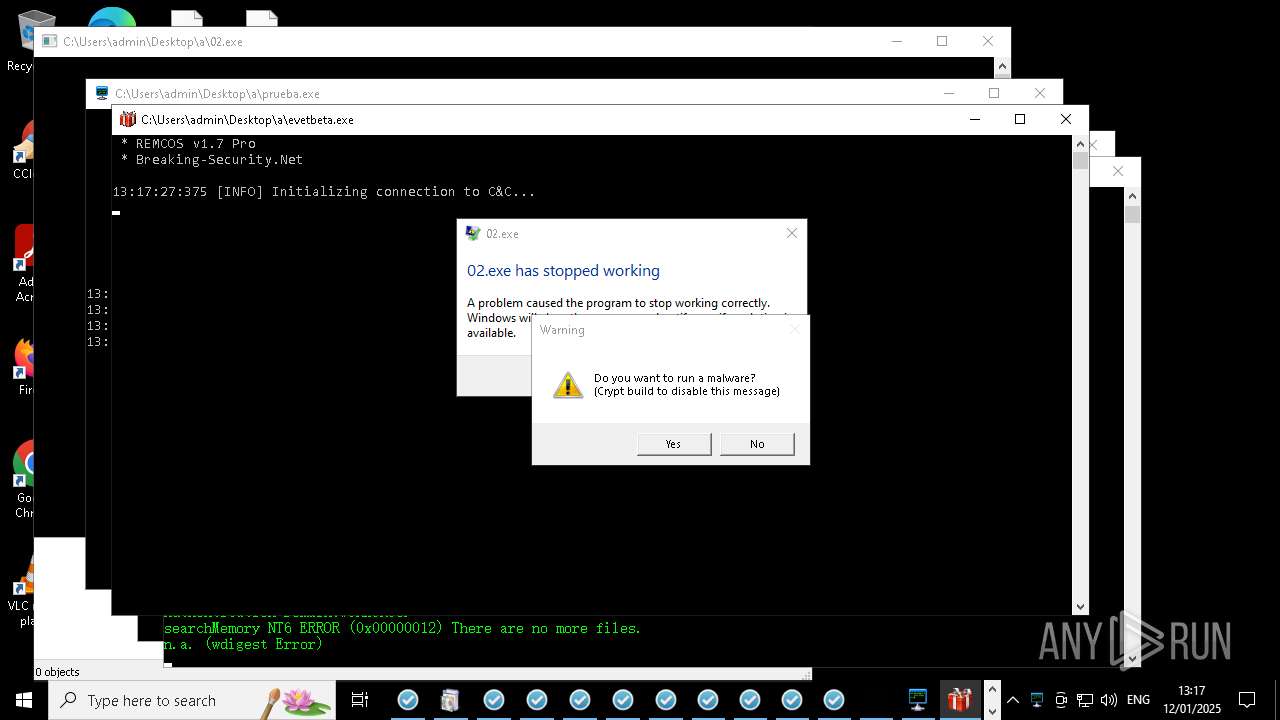
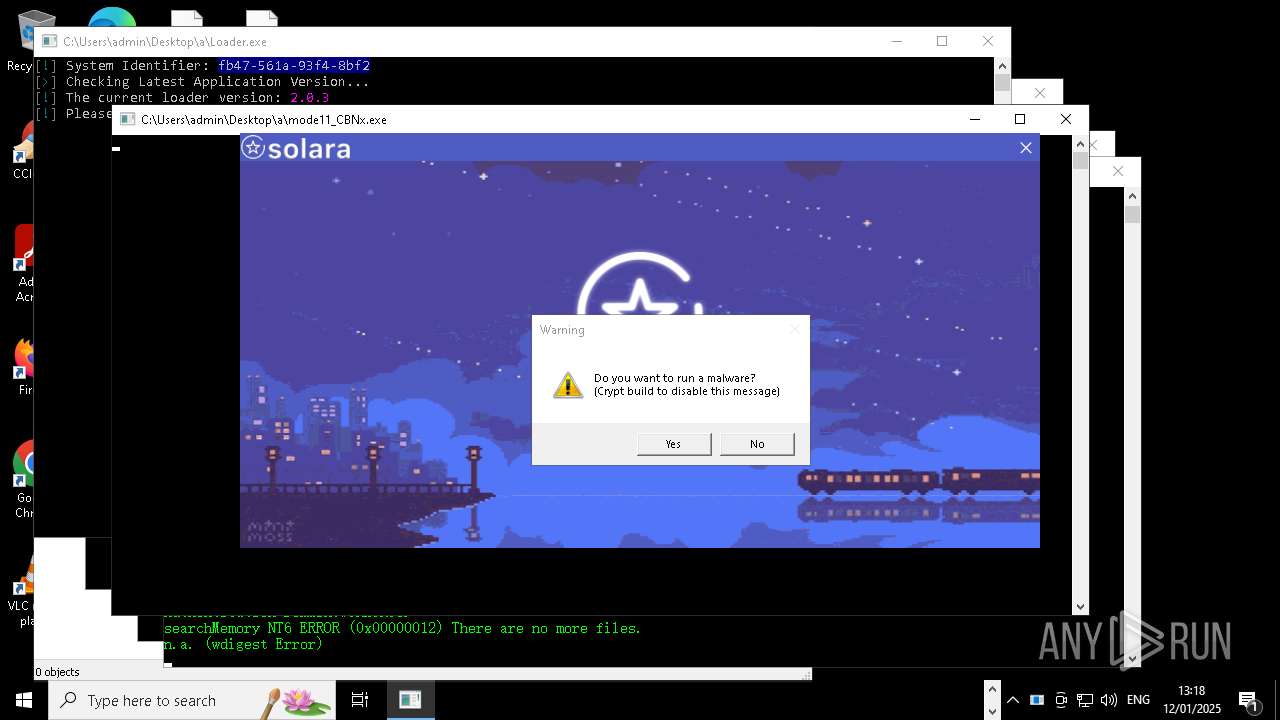
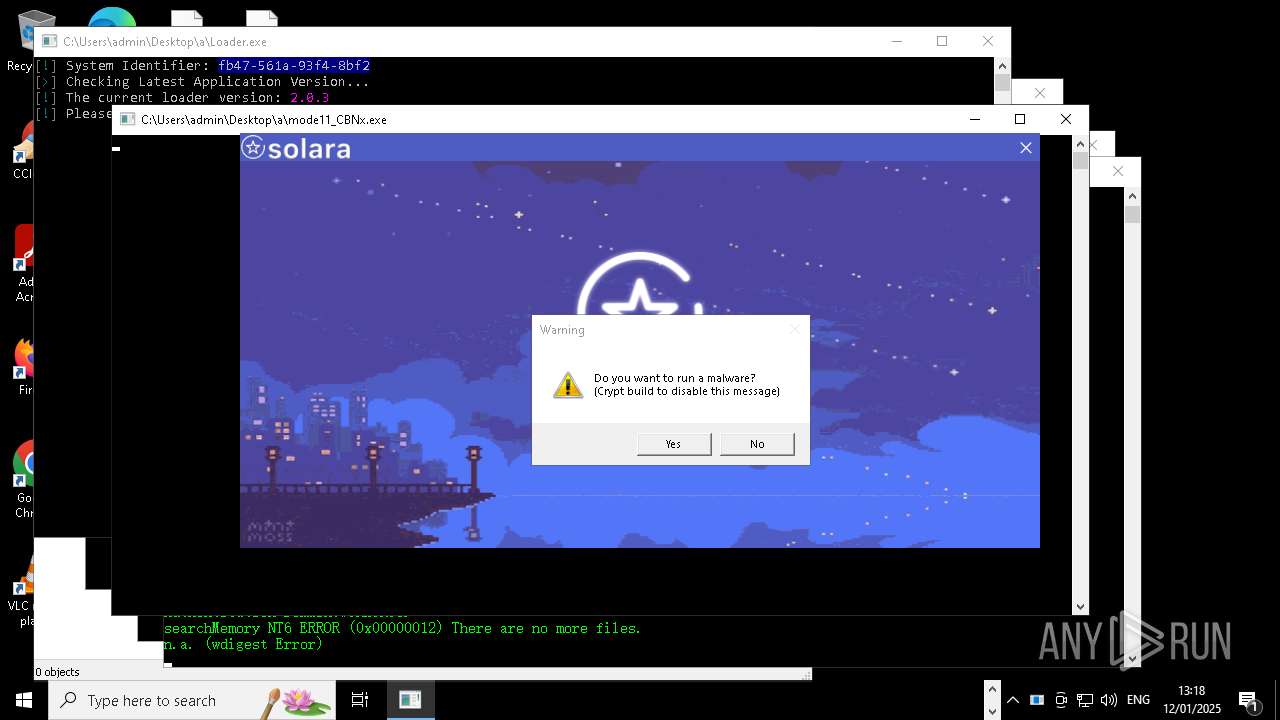
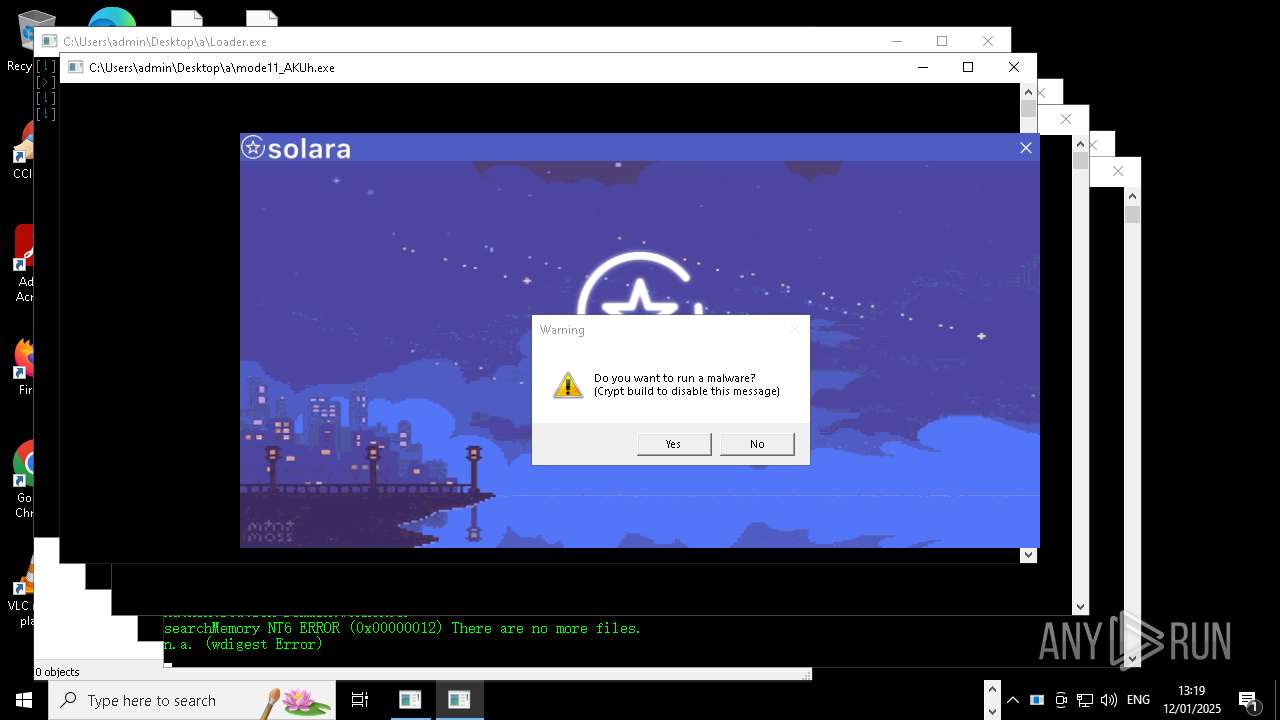
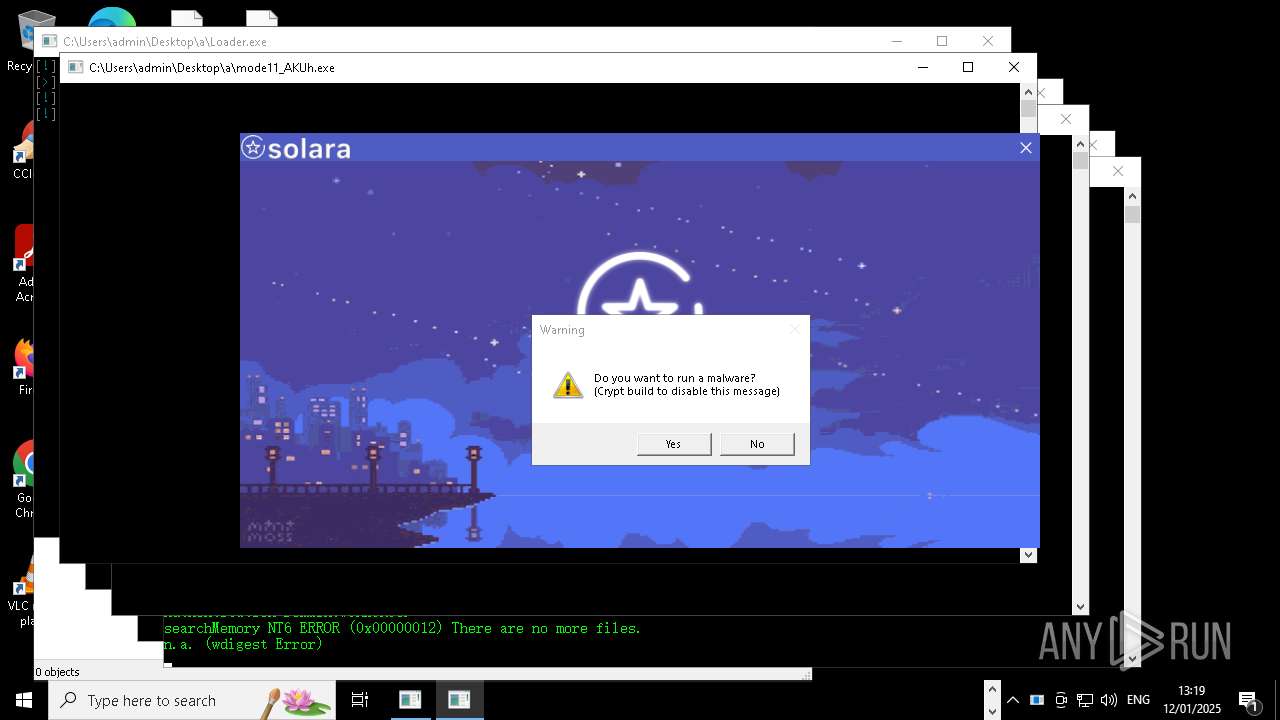
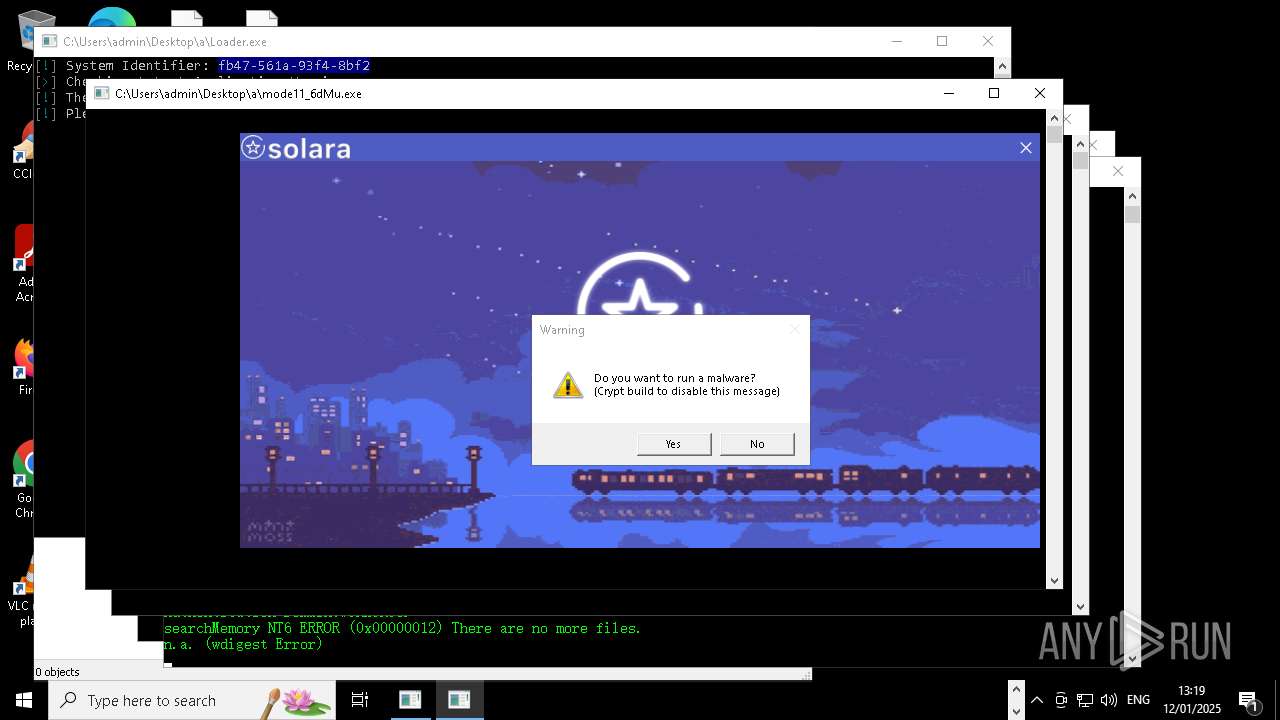
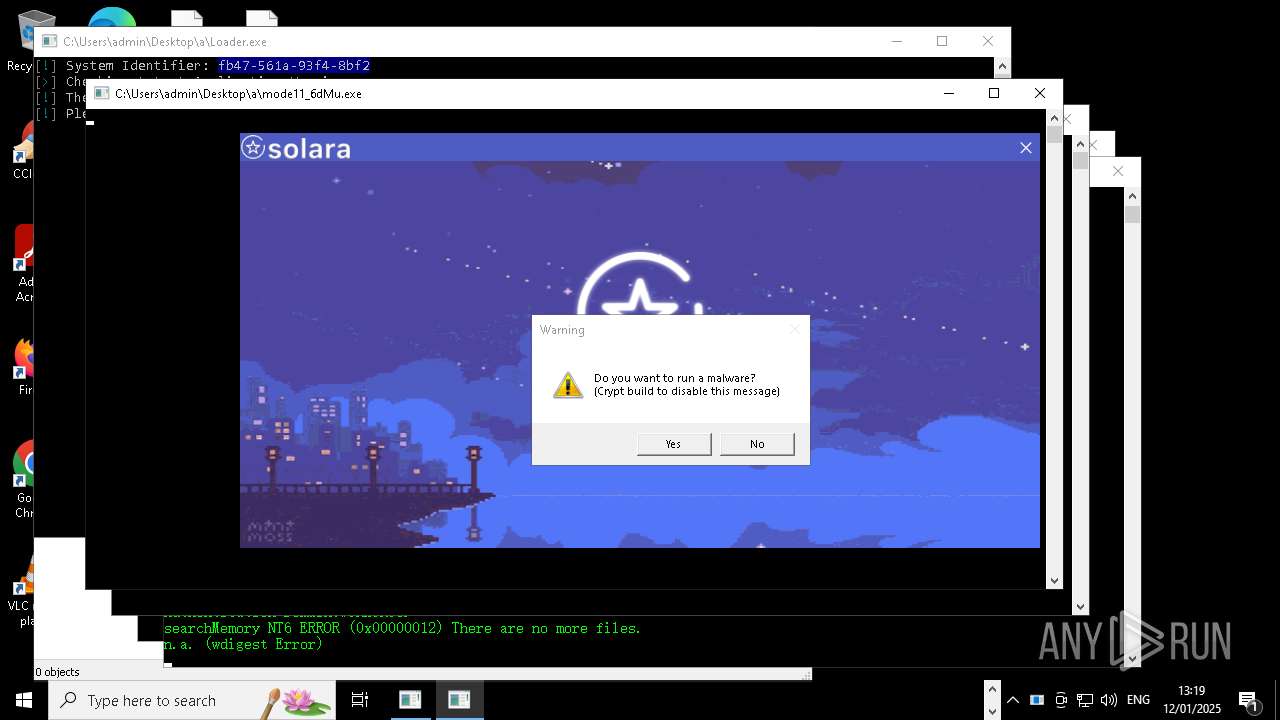
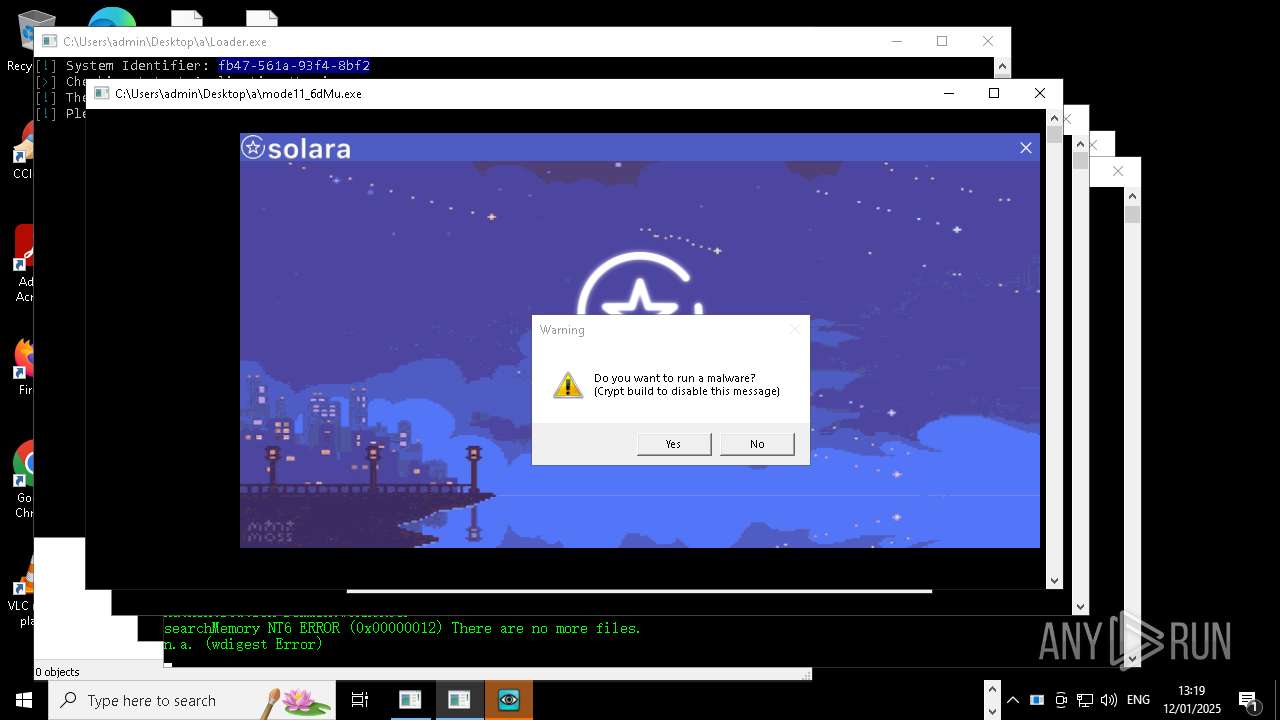
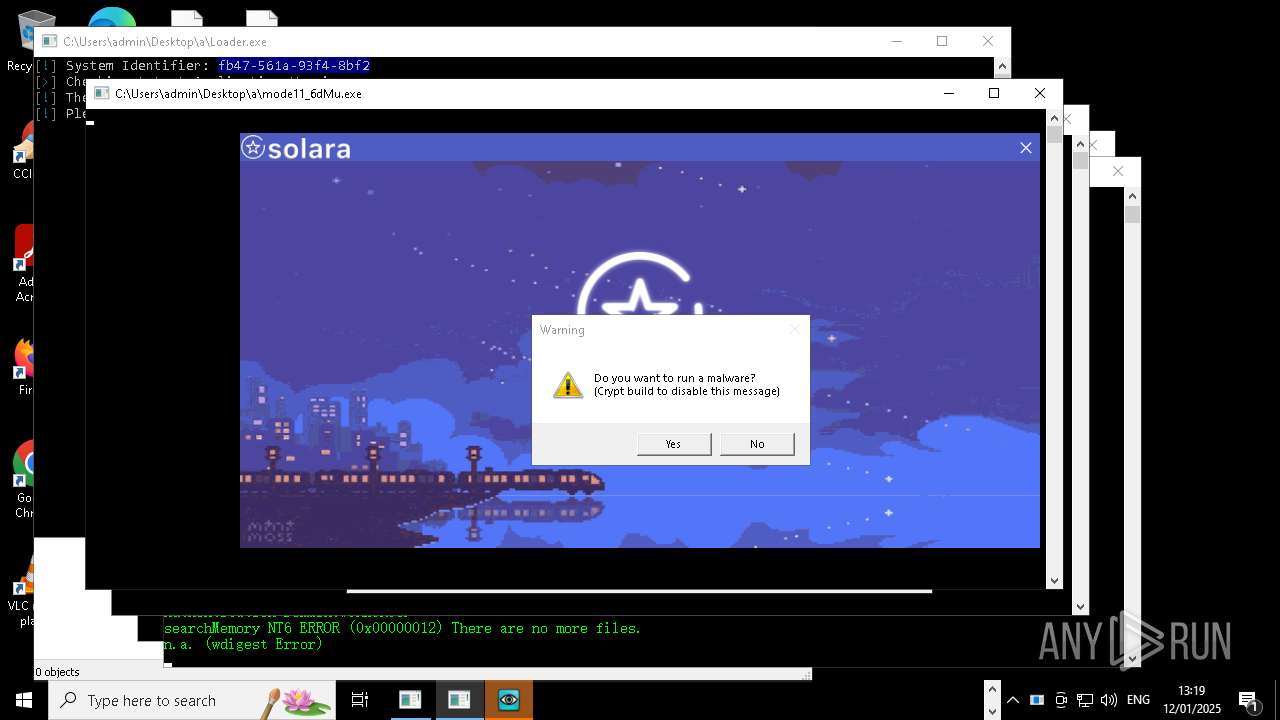
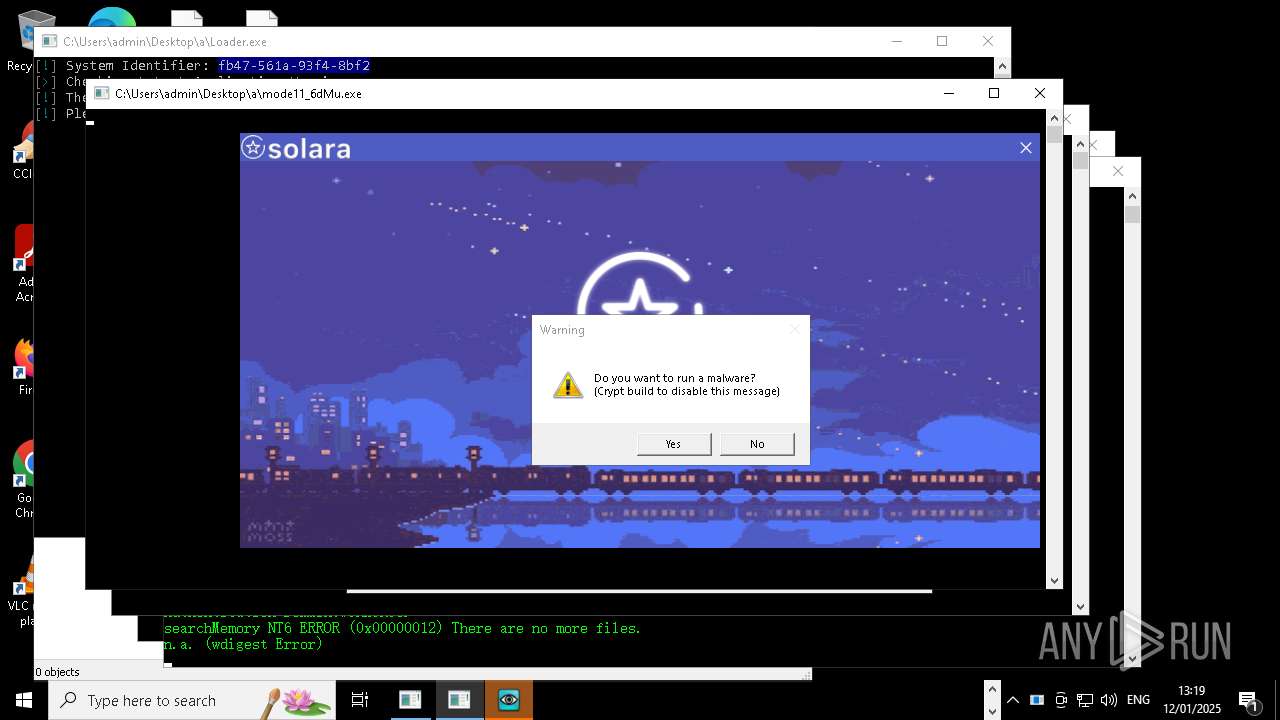
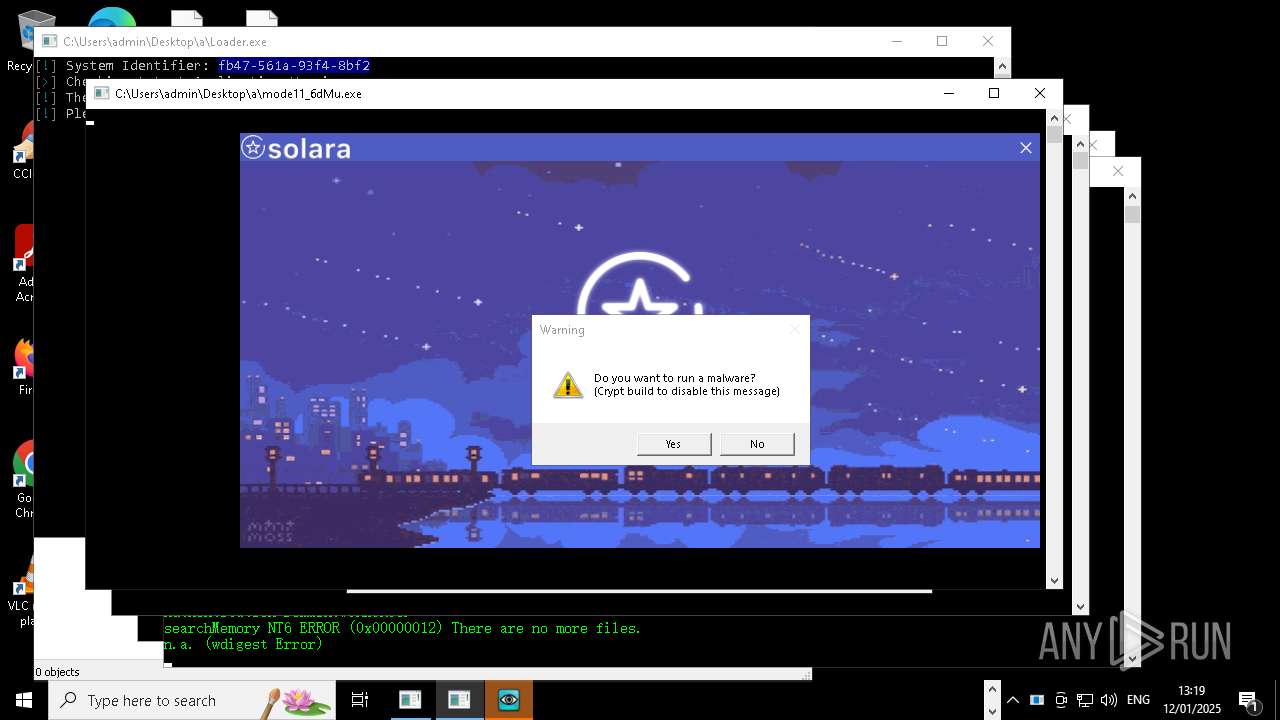
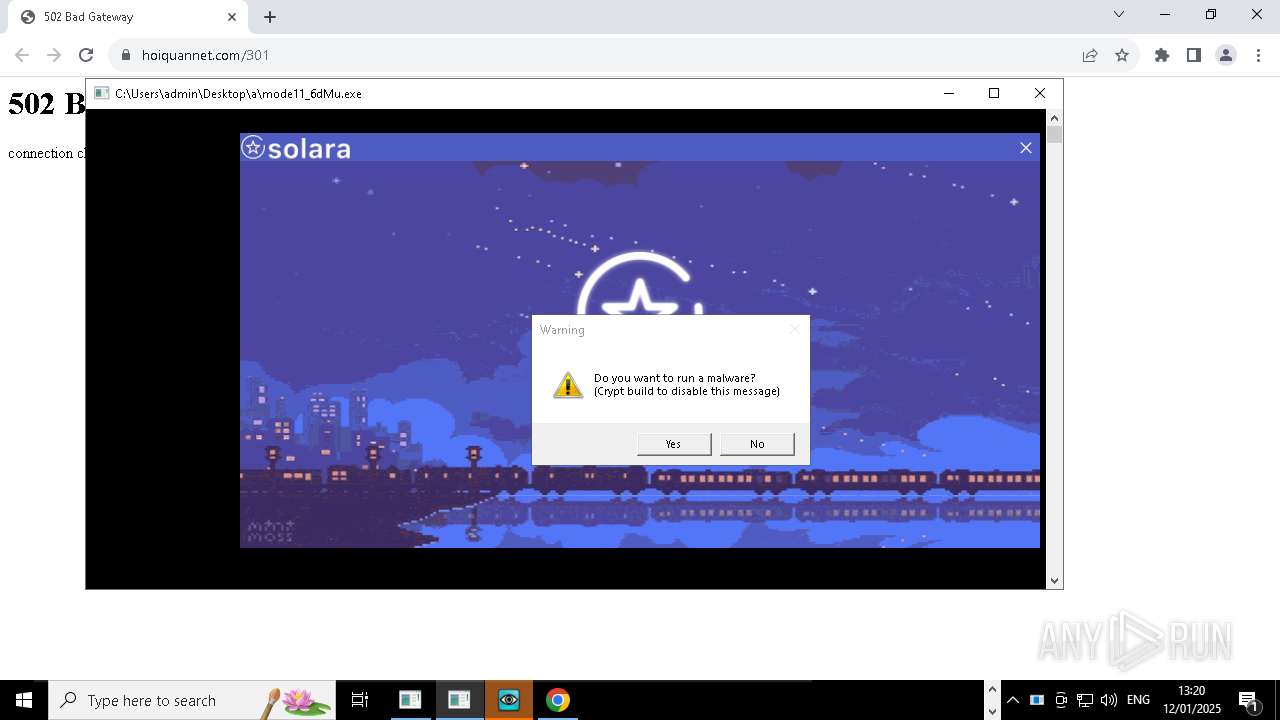
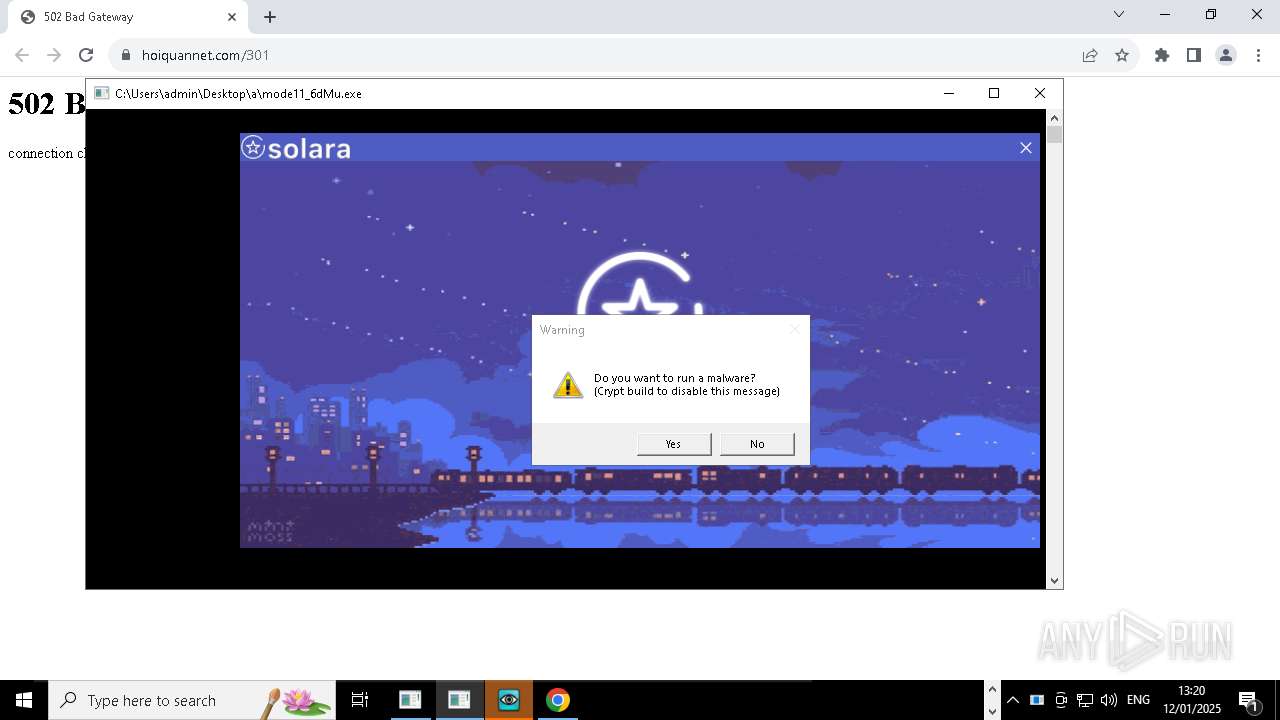
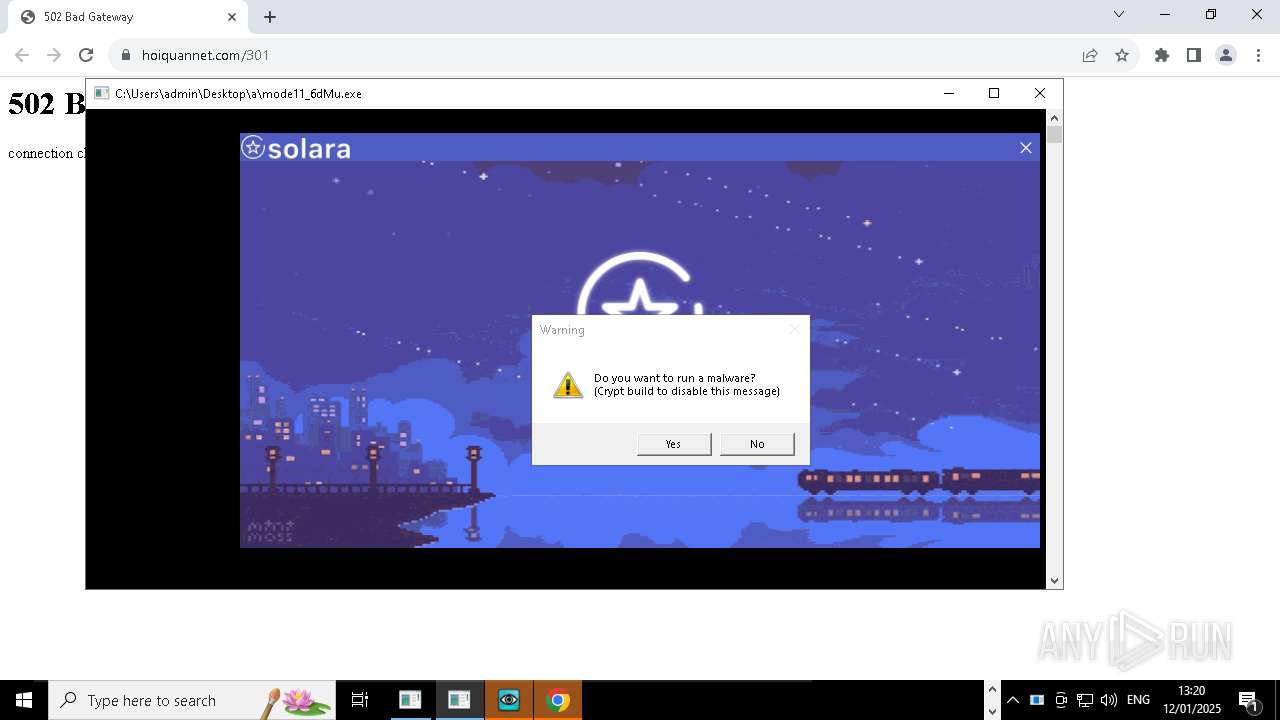
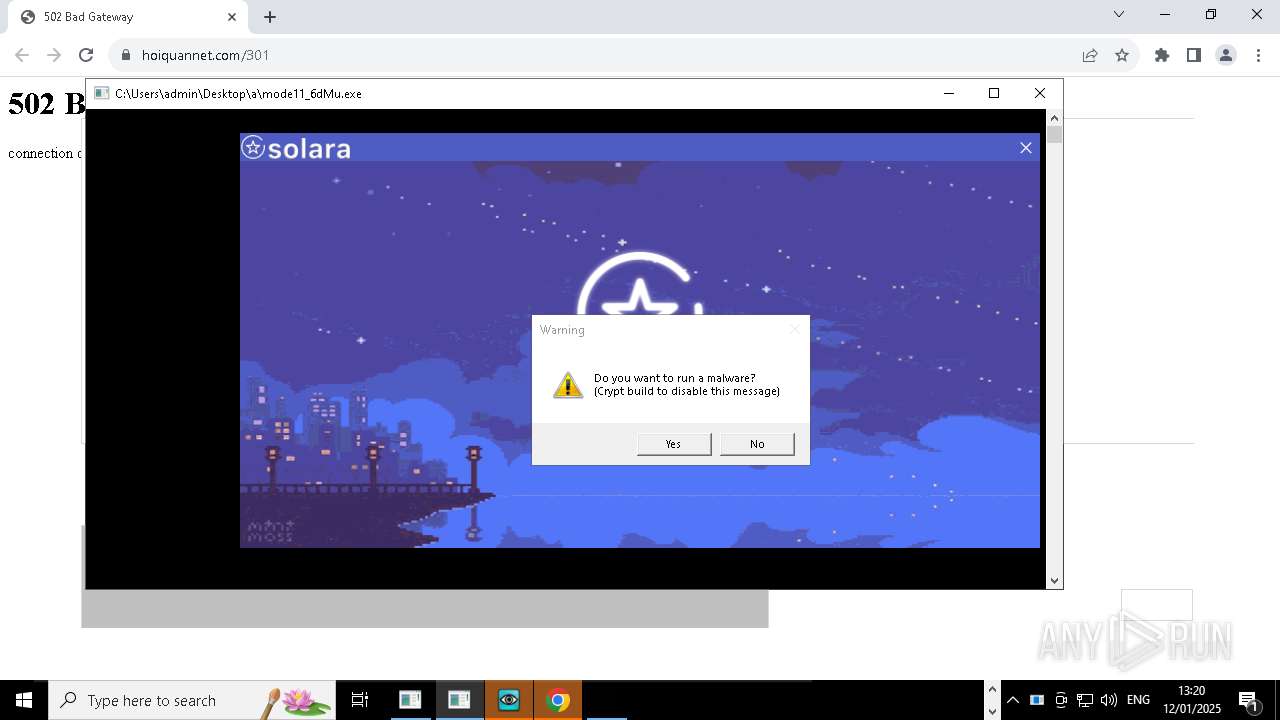
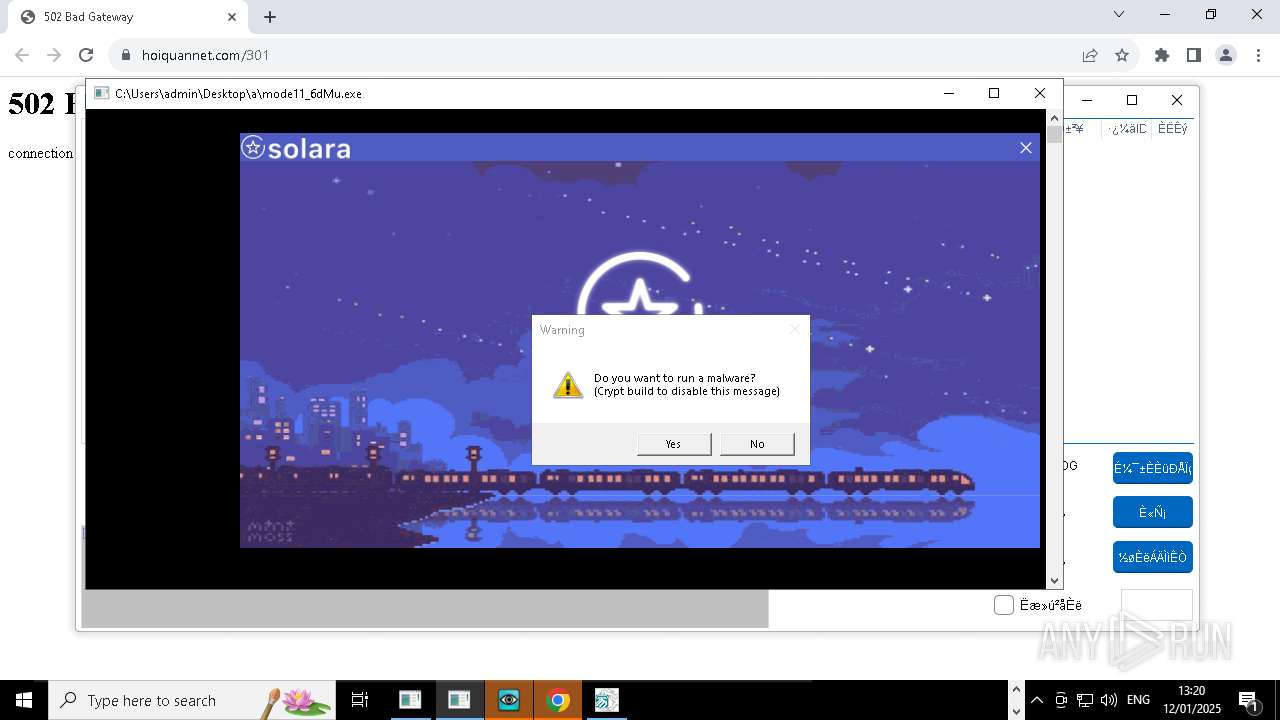
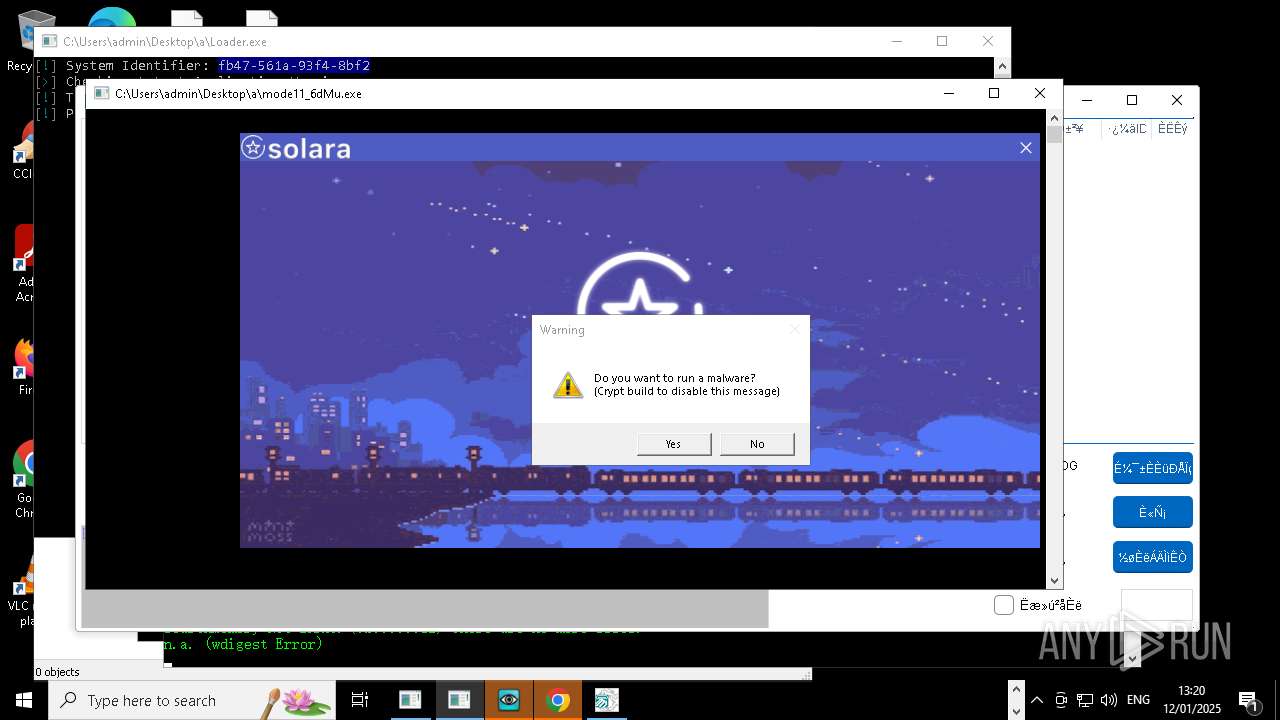
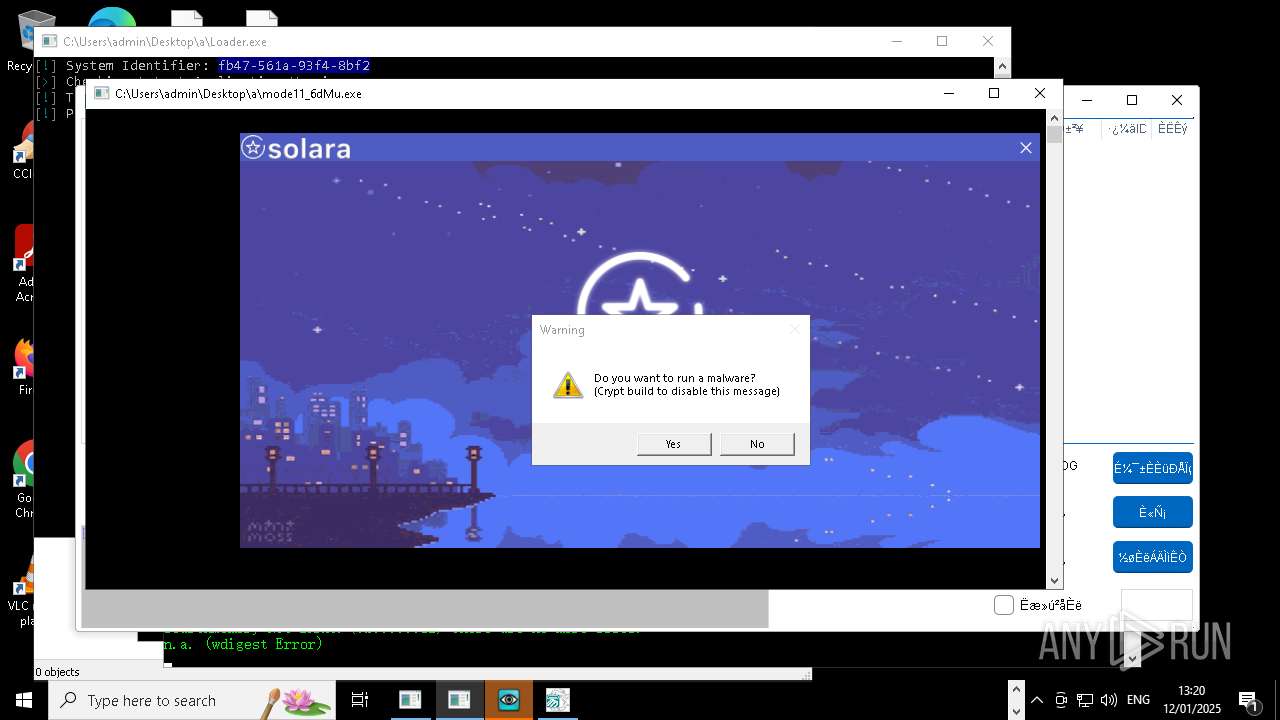
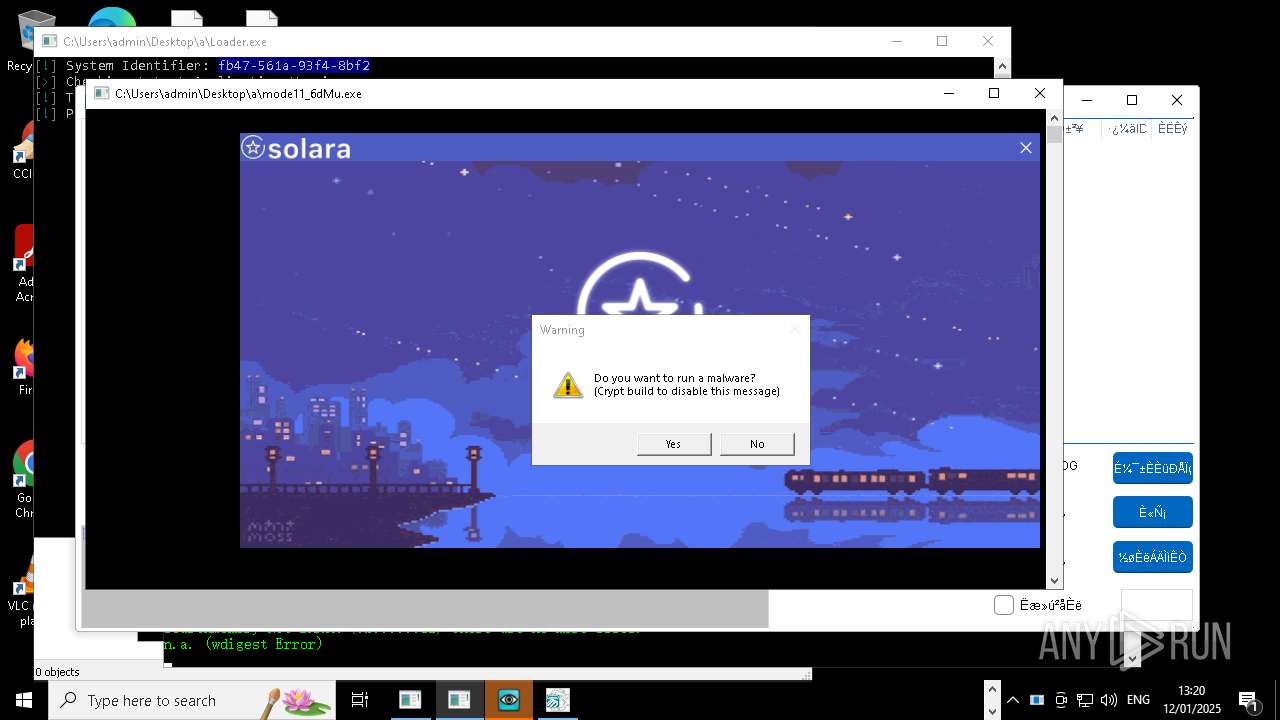
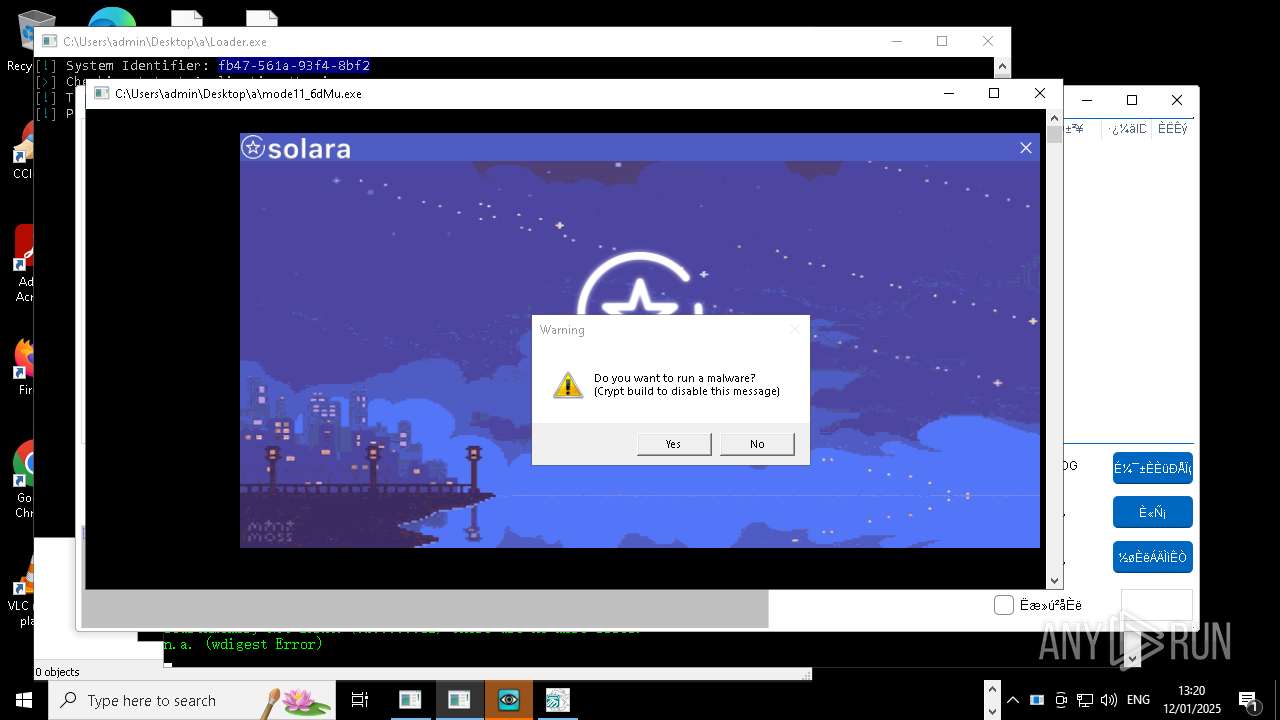
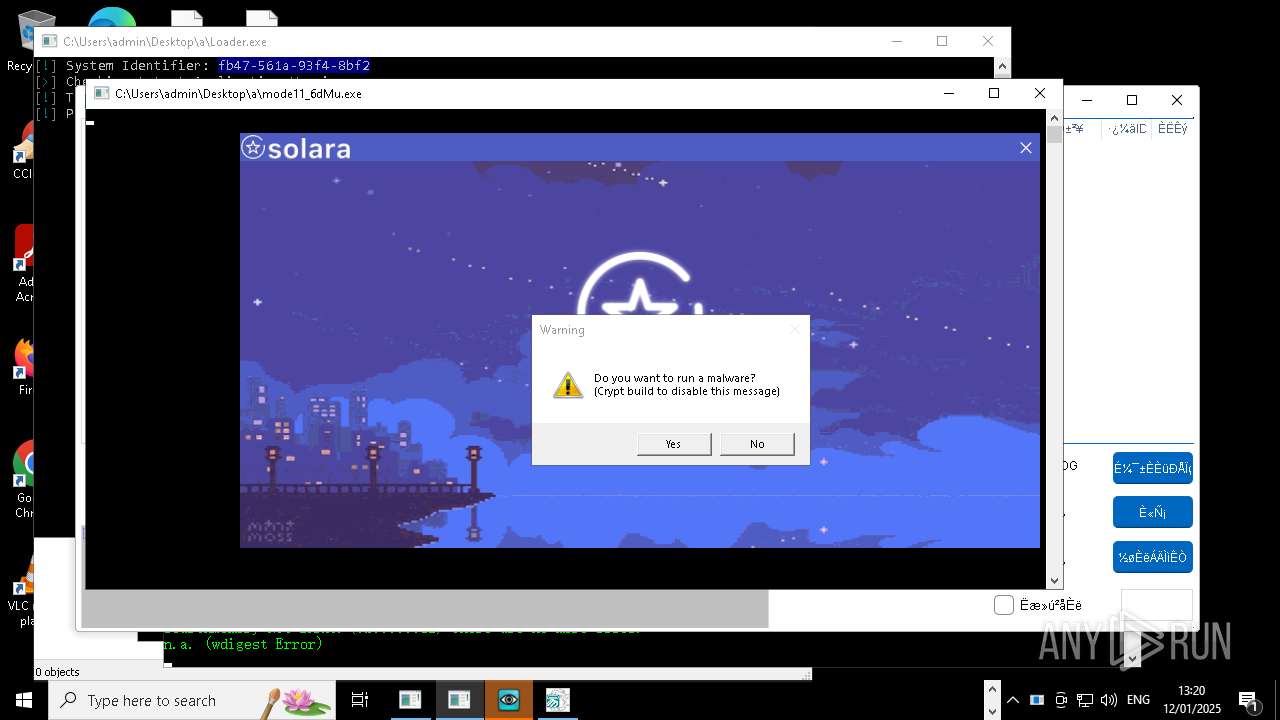
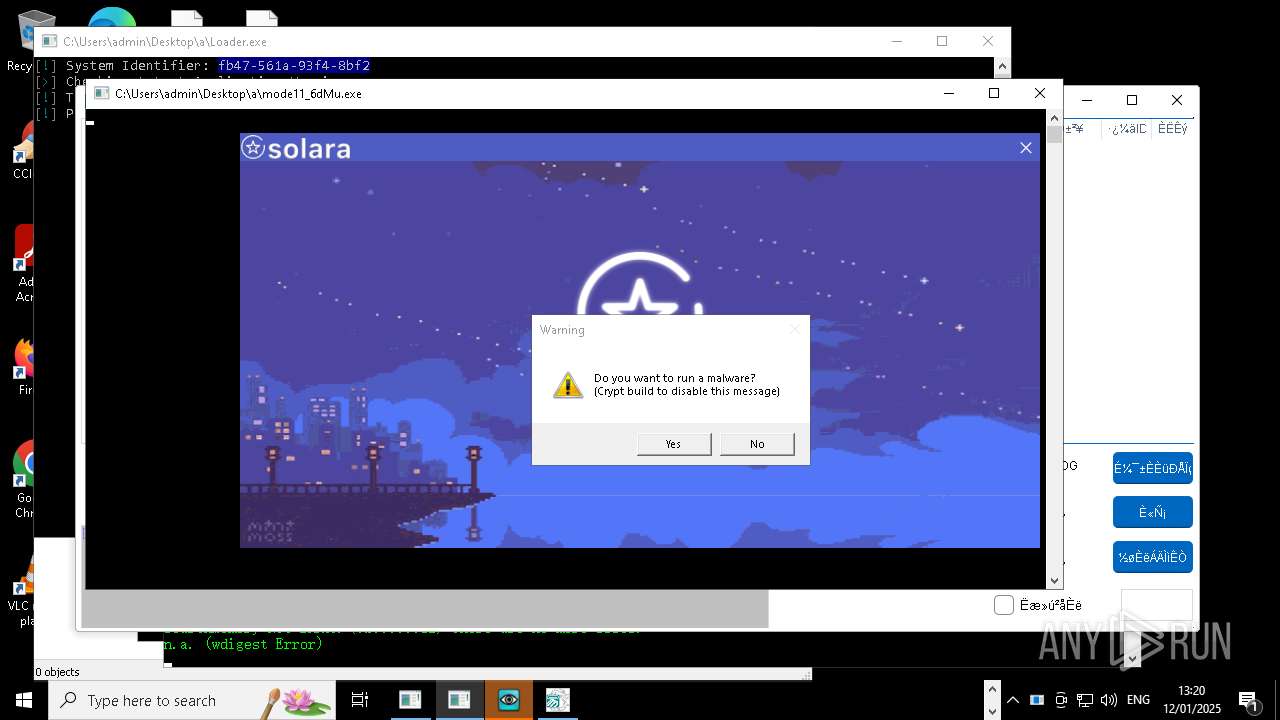
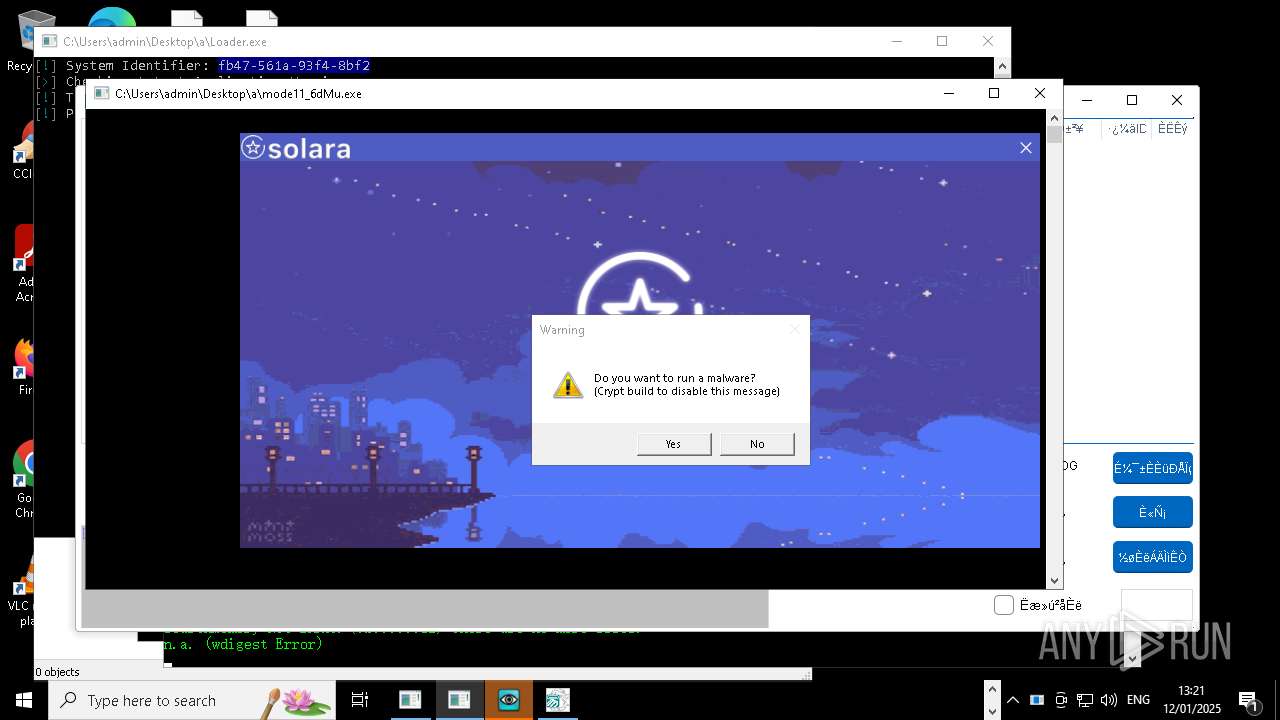
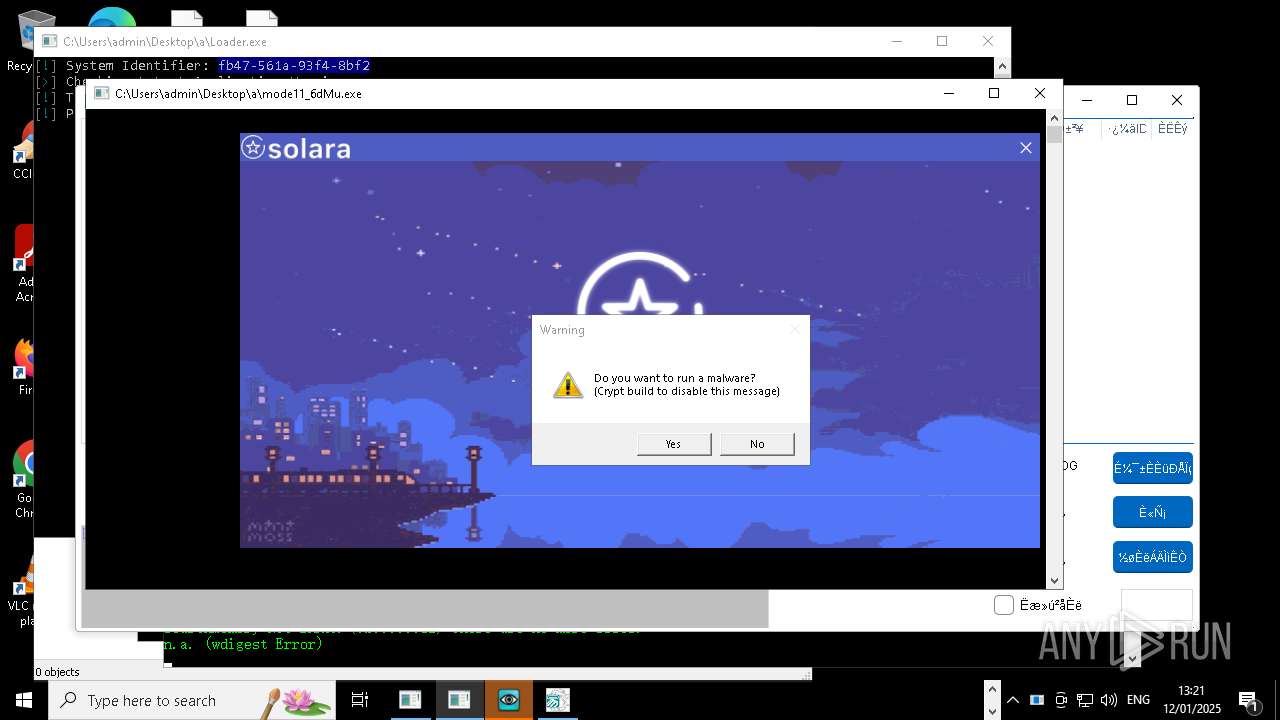
| File name: | New Text Document mod.exe.bin |
| Full analysis: | https://app.any.run/tasks/bed40f9f-dd41-40b1-abc7-841bf2b19b72 |
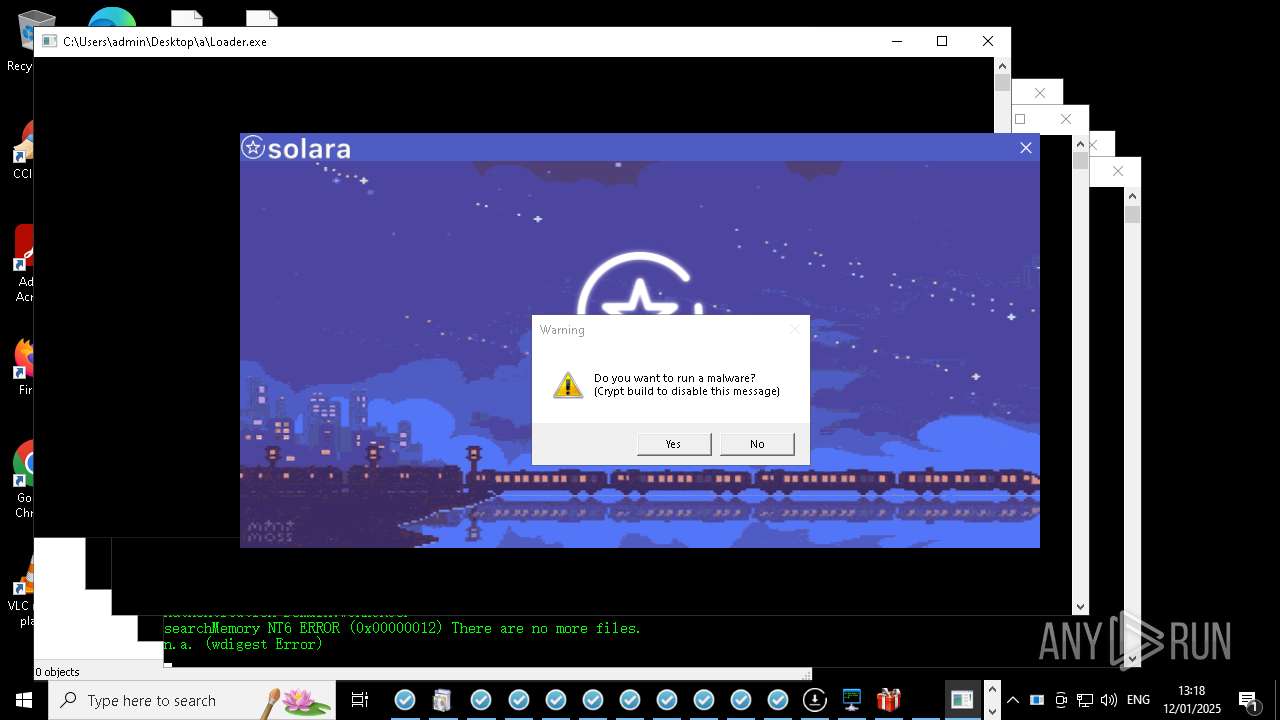
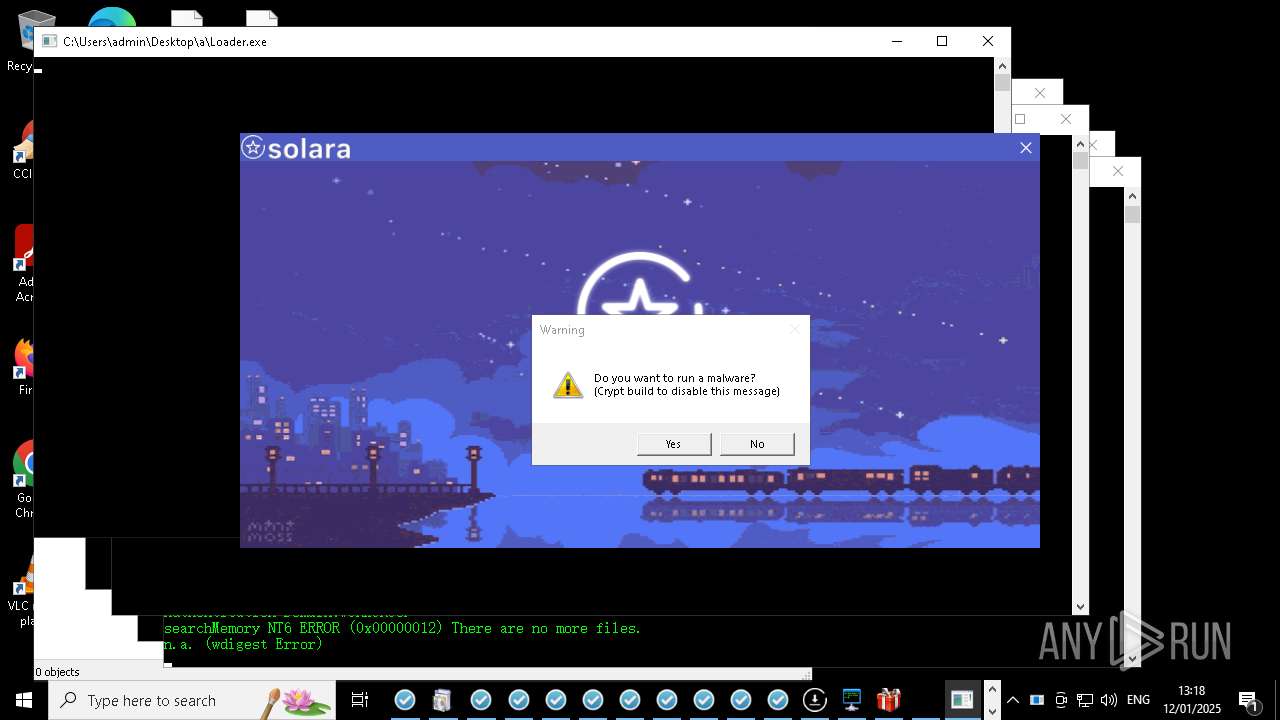
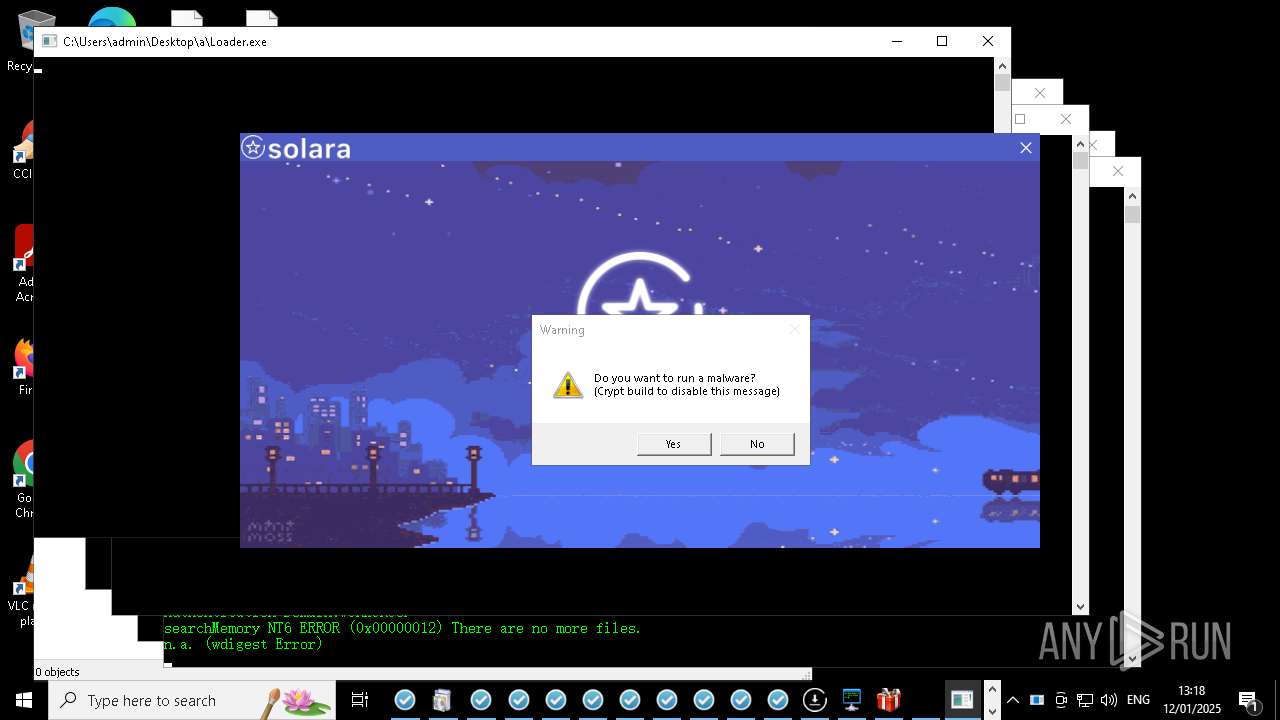
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | January 12, 2025, 13:10:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | C6040234EE8EAEDBE618632818C3B1B3 |
| SHA1: | 68115F8C3394C782AA6BA663AC78695D2B80BF75 |
| SHA256: | BB459869E5EF6D6DD6F0329080D7CB12542C4B37163AE2CD782620ADCD7D55A0 |
| SSDEEP: | 12288:f3H6yScLnqOl0r5Zu0LMFbtizFJ6rAPvOxrcg0i7u48S+isSl:f3HzLnqOaNMCFJ6kPvOxrcg0i7uFSsE |
MALICIOUS
Changes the autorun value in the registry
- New Text Document mod.exe.bin.exe (PID: 624)
- WinDrive-f4855f59e0.exe (PID: 6860)
- 2018910798.exe (PID: 6416)
- Crawl.exe (PID: 6448)
- windows 3543.exe (PID: 9860)
- reg.exe (PID: 10076)
- .exe (PID: 13588)
- seksiak.exe (PID: 8992)
- server.exe (PID: 9196)
- diskutil.exe (PID: 16244)
- seksiak.exe (PID: 12372)
- Onedrive.exe (PID: 16608)
- seksiak.exe (PID: 18232)
- windows 3543.exe (PID: 17012)
- seksiak.exe (PID: 9200)
- seksiak.exe (PID: 16964)
- XClient.exe (PID: 19052)
- seksiak.exe (PID: 19252)
- Bootxr.exe (PID: 19728)
- dropper64.exe (PID: 20180)
- audiodg.exe (PID: 20280)
- svchost.exe (PID: 20272)
- msiexec.exe (PID: 20288)
- seksiak.exe (PID: 18164)
- seksiak.exe (PID: 22292)
- seksiak.exe (PID: 21740)
- explorer.exe (PID: 4488)
- seksiak.exe (PID: 19004)
- seksiak.exe (PID: 18624)
Connects to the CnC server
- Synaptics.exe (PID: 4952)
- whiteshadow123.exe (PID: 5864)
- svchost.exe (PID: 2192)
- tmx.exe (PID: 6456)
- sysnldcvmr.exe (PID: 2792)
- Steanings.exe (PID: 7748)
- skotes.exe (PID: 6372)
- Server1.exe (PID: 8340)
- sela.exe (PID: 9336)
- 4e452a47dd.exe (PID: 9076)
- 3t57j.exe (PID: 10248)
- SCLKFNF21ARIHQ5RV63UYR.exe (PID: 10568)
- evetbeta.exe (PID: 14488)
- server.exe (PID: 14200)
- server.exe (PID: 9196)
- cici.exe (PID: 18496)
- XClient.exe (PID: 19052)
- Java32.exe (PID: 18964)
- ioc.exe (PID: 20100)
XRED has been detected
- New Text Document mod.exe.bin.exe (PID: 624)
CRYPTBOT mutex has been found
- whiteshadow123.exe (PID: 5864)
- Set-up.exe (PID: 3812)
- 4e452a47dd.exe (PID: 9076)
HAUSBOMBER has been detected (YARA)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
DCRAT has been detected (YARA)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
Executing a file with an untrusted certificate
- whiteshadow123.exe (PID: 5864)
- Set-up.exe (PID: 3812)
- TPB-1.exe (PID: 7216)
- TPB-1.exe (PID: 4428)
- TPB-1.exe (PID: 11640)
- mcgen.exe (PID: 14080)
- mcgen.exe (PID: 14340)
- mcgen.exe (PID: 16096)
- mcgen.exe (PID: 16196)
- hr.exe (PID: 18108)
- Built.exe (PID: 20996)
- Built.exe (PID: 21368)
Create files in the Startup directory
- minimal.exe (PID: 4320)
- cbot.exe (PID: 236)
- Server1.exe (PID: 8340)
- Crawl.exe (PID: 6448)
- server.exe (PID: 14200)
- mcgen.exe (PID: 16196)
- Java32.exe (PID: 18964)
- Built.exe (PID: 21368)
LUMMA has been detected (YARA)
- conhost.exe (PID: 4512)
- Synaptics.exe (PID: 4952)
- whiteshadow123.exe (PID: 5864)
- LummaC2.exe (PID: 4592)
- conhost.exe (PID: 4668)
- minimal.exe (PID: 4320)
- johnmartin.exe (PID: 4472)
- sk.exe (PID: 6684)
- service123.exe (PID: 6900)
- WinDrive-f4855f59e0.exe (PID: 6860)
- gem1.exe (PID: 6432)
- svchost.exe (PID: 7024)
XRED has been detected (YARA)
- Synaptics.exe (PID: 4952)
CRYPTBOT has been detected (SURICATA)
- whiteshadow123.exe (PID: 5864)
- 4e452a47dd.exe (PID: 9076)
Actions looks like stealing of personal data
- whiteshadow123.exe (PID: 5864)
- johnmartin.exe (PID: 4472)
- gem1.exe (PID: 6432)
- LummaC2.exe (PID: 4592)
- tmx.exe (PID: 6456)
- BitLockerToGo.exe (PID: 6752)
- 3061413023.exe (PID: 7496)
- Steanings.exe (PID: 7748)
- build1.exe (PID: 7792)
- 293637911.exe (PID: 7392)
- 2D8630.exe (PID: 4912)
- Crawl.exe (PID: 6448)
- 4e452a47dd.exe (PID: 9076)
- TPB-1.exe (PID: 11640)
- mcgen.exe (PID: 16196)
- cici.exe (PID: 18496)
- cmd.exe (PID: 7236)
- ioc.exe (PID: 20100)
- Built.exe (PID: 21368)
Steals credentials from Web Browsers
- johnmartin.exe (PID: 4472)
- gem1.exe (PID: 6432)
- LummaC2.exe (PID: 4592)
- tmx.exe (PID: 6456)
- BitLockerToGo.exe (PID: 6752)
- build1.exe (PID: 7792)
- Steanings.exe (PID: 7748)
- 2D8630.exe (PID: 4912)
- TPB-1.exe (PID: 11640)
- mcgen.exe (PID: 16196)
- cici.exe (PID: 18496)
- Built.exe (PID: 21368)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2192)
LUMMA mutex has been found
- johnmartin.exe (PID: 4472)
- LummaC2.exe (PID: 4592)
- BitLockerToGo.exe (PID: 6752)
- 2D8630.exe (PID: 4912)
- TPB-1.exe (PID: 11640)
Known privilege escalation attack
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 15124)
Adds process to the Windows Defender exclusion list
- WinDrive-f4855f59e0.exe (PID: 6860)
Uses Task Scheduler to run other applications
- whiteshadow123.exe (PID: 5864)
- 4e452a47dd.exe (PID: 9076)
- XClient.exe (PID: 19052)
Bypass execution policy to execute commands
- powershell.exe (PID: 1944)
- powershell.exe (PID: 7240)
- powershell.exe (PID: 17324)
- powershell.exe (PID: 22324)
MEDUZASTEALER has been detected (SURICATA)
- gem1.exe (PID: 6432)
Changes powershell execution policy (Bypass)
- johnmartin.exe (PID: 4472)
- LummaC2.exe (PID: 4592)
- cmd.exe (PID: 14816)
- cmd.exe (PID: 21892)
Uses Task Scheduler to autorun other applications
- WinDrive-f4855f59e0.exe (PID: 6860)
- cmd.exe (PID: 10876)
- cmd.exe (PID: 11080)
STEALER has been found (auto)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
Starts REAGENTC.EXE to disable the Windows Recovery Environment
- ReAgentc.exe (PID: 7164)
MEDUZASTEALER has been found (auto)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
PHORPIEX mutex has been found
- 2018910798.exe (PID: 6416)
- sysnldcvmr.exe (PID: 2792)
- 2621933628.exe (PID: 8764)
REDLINE has been detected (SURICATA)
- tmx.exe (PID: 6456)
- Steanings.exe (PID: 7748)
- build1.exe (PID: 7792)
- cici.exe (PID: 18496)
- ioc.exe (PID: 20100)
METASTEALER has been detected (SURICATA)
- tmx.exe (PID: 6456)
- Steanings.exe (PID: 7748)
- cici.exe (PID: 18496)
- ioc.exe (PID: 20100)
XMRig has been detected
- win.exe (PID: 2280)
- xmrig.exe (PID: 6316)
- xmrig.exe (PID: 7620)
BOTNET has been found (auto)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
MINER has been detected (SURICATA)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- svchost.exe (PID: 2192)
- 1724930485.exe (PID: 6180)
- powershell.exe (PID: 19952)
PHORPIEX has been detected (SURICATA)
- sysnldcvmr.exe (PID: 2792)
- svchost.exe (PID: 2192)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
QUASARRAT has been found (auto)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
QUASAR mutex has been found
- Client-built.exe (PID: 6976)
- uu.exe (PID: 8280)
PHORPIEX has been found (auto)
- 1724930485.exe (PID: 6180)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
Stealers network behavior
- Steanings.exe (PID: 7748)
LEFTHOOK has been detected (SURICATA)
- build1.exe (PID: 7792)
AMADEY mutex has been found
- 1X48r0.exe (PID: 8156)
- skotes.exe (PID: 6372)
- skotes.exe (PID: 3556)
- KQ2ZHT79N1C50FF5FGMYRJFW3BR4.exe (PID: 9412)
- skotes.exe (PID: 7656)
- skotes.exe (PID: 12508)
- skotes.exe (PID: 13244)
- skotes.exe (PID: 16724)
- skotes.exe (PID: 15448)
- skotes.exe (PID: 20688)
- skotes.exe (PID: 22060)
- skotes.exe (PID: 21316)
AMADEY has been detected (SURICATA)
- skotes.exe (PID: 6372)
RAT has been found (auto)
- svchost.exe (PID: 7024)
- XClient.exe (PID: 19052)
NJRAT has been detected (SURICATA)
- Server1.exe (PID: 8340)
- sela.exe (PID: 9336)
- server.exe (PID: 9196)
- server.exe (PID: 14200)
Deletes shadow copies
- Crawl.exe (PID: 6448)
Renames files like ransomware
- Crawl.exe (PID: 6448)
NJRAT mutex has been found
- sela.exe (PID: 9336)
StealC has been detected
- 696969.exe (PID: 9580)
- SCLKFNF21ARIHQ5RV63UYR.exe (PID: 10568)
- 3t57j.exe (PID: 10248)
- daytjhasdawd.exe (PID: 18708)
RANSOMWARE has been detected
- Crawl.exe (PID: 6448)
Writes a file to the Word startup folder
- Crawl.exe (PID: 6448)
ASYNCRAT has been detected (MUTEX)
- sdggwsdgdrwgrwgrwgrwgrw.exe (PID: 9812)
- image%20logger.exe (PID: 17592)
Starts CMD.EXE for self-deleting
- Crawl.exe (PID: 6448)
- IMG001.exe (PID: 11028)
- mcgen.exe (PID: 16196)
STEALC has been detected (SURICATA)
- 3t57j.exe (PID: 10248)
- SCLKFNF21ARIHQ5RV63UYR.exe (PID: 10568)
GENERIC has been found (auto)
- 1724930485.exe (PID: 6180)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
LUMMA has been found (auto)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
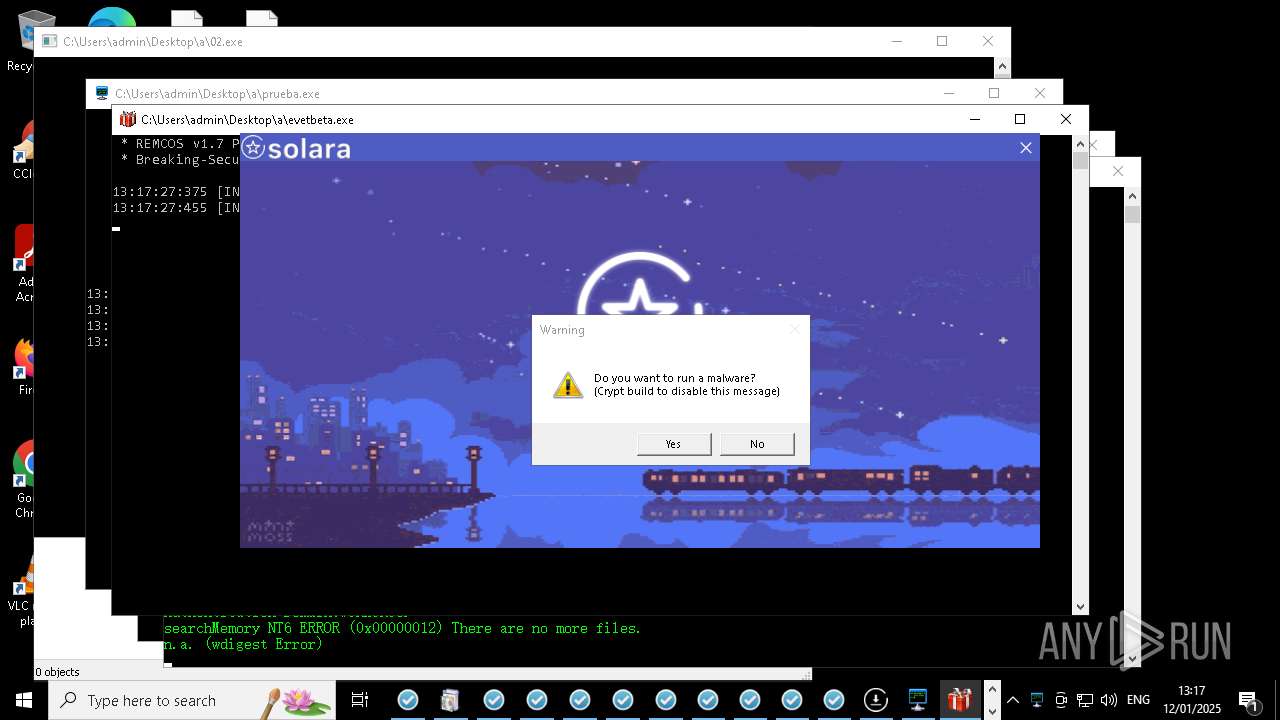
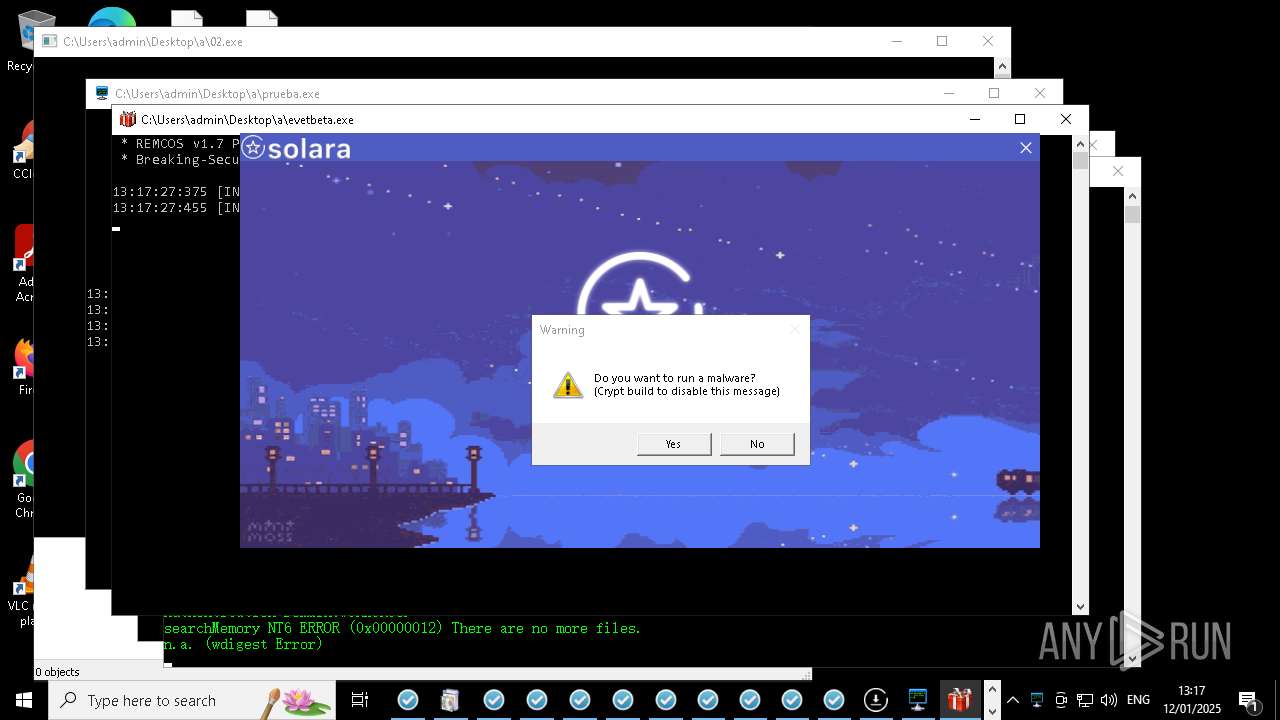
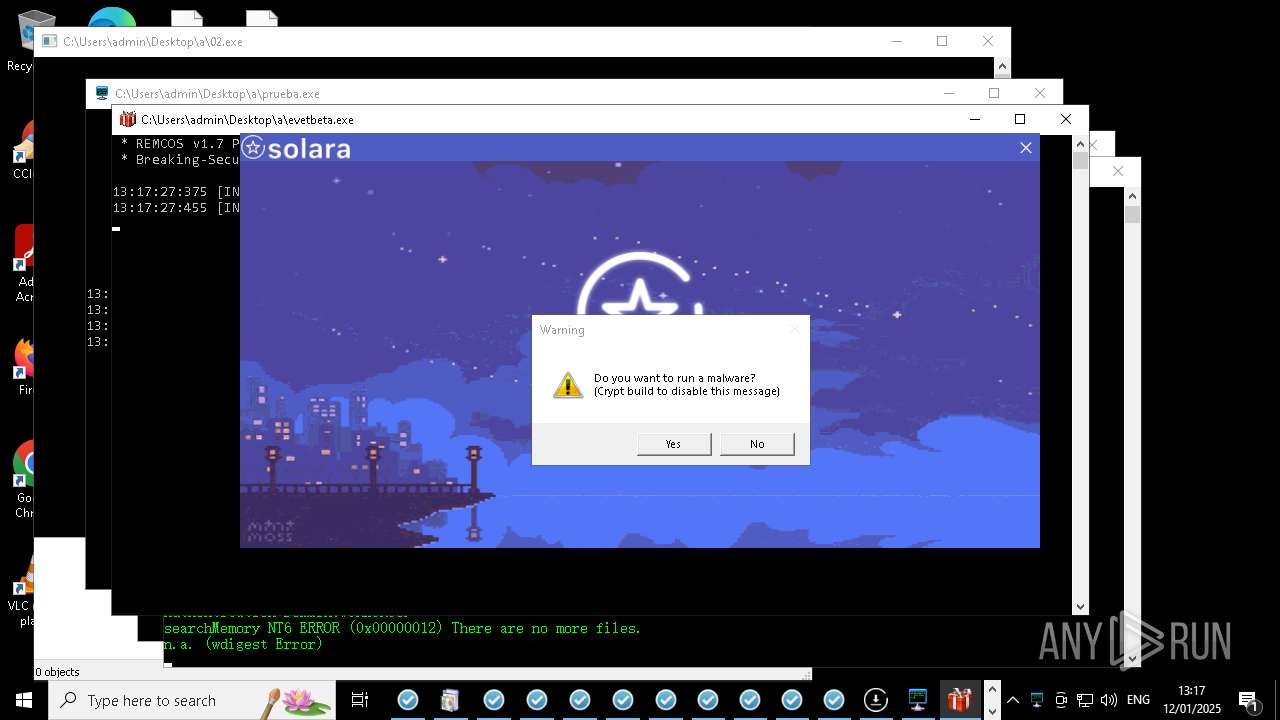
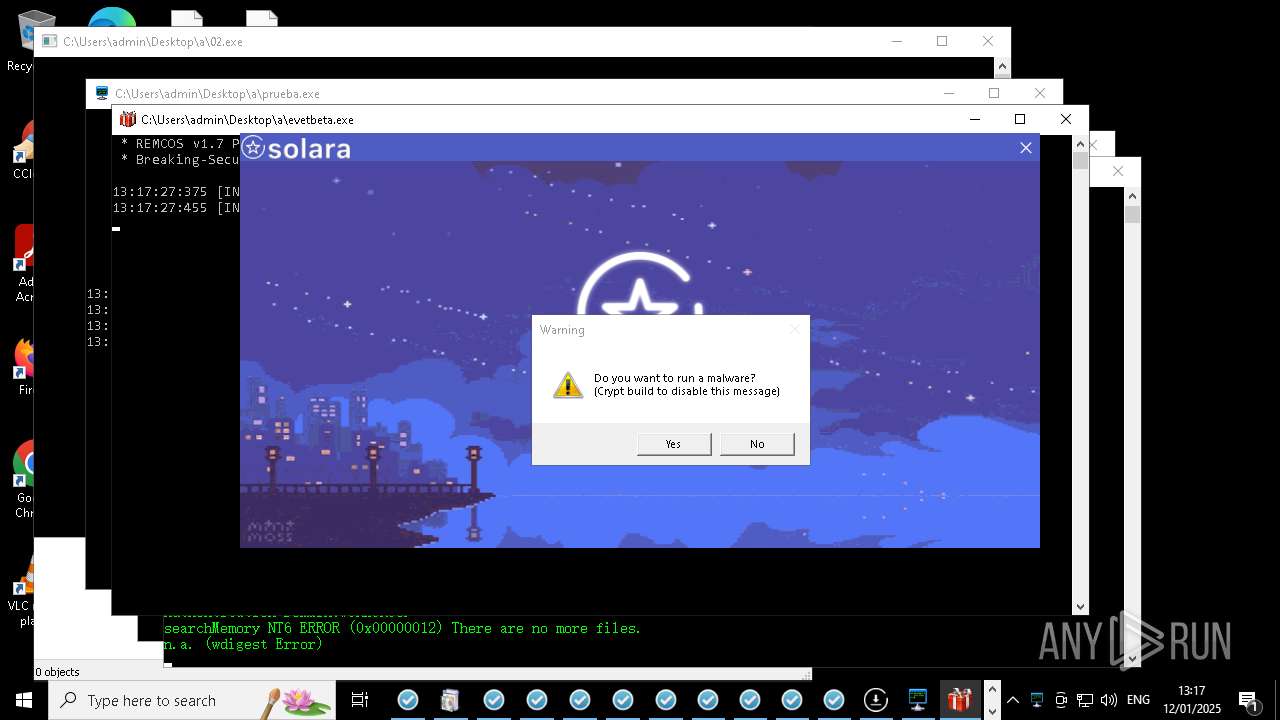
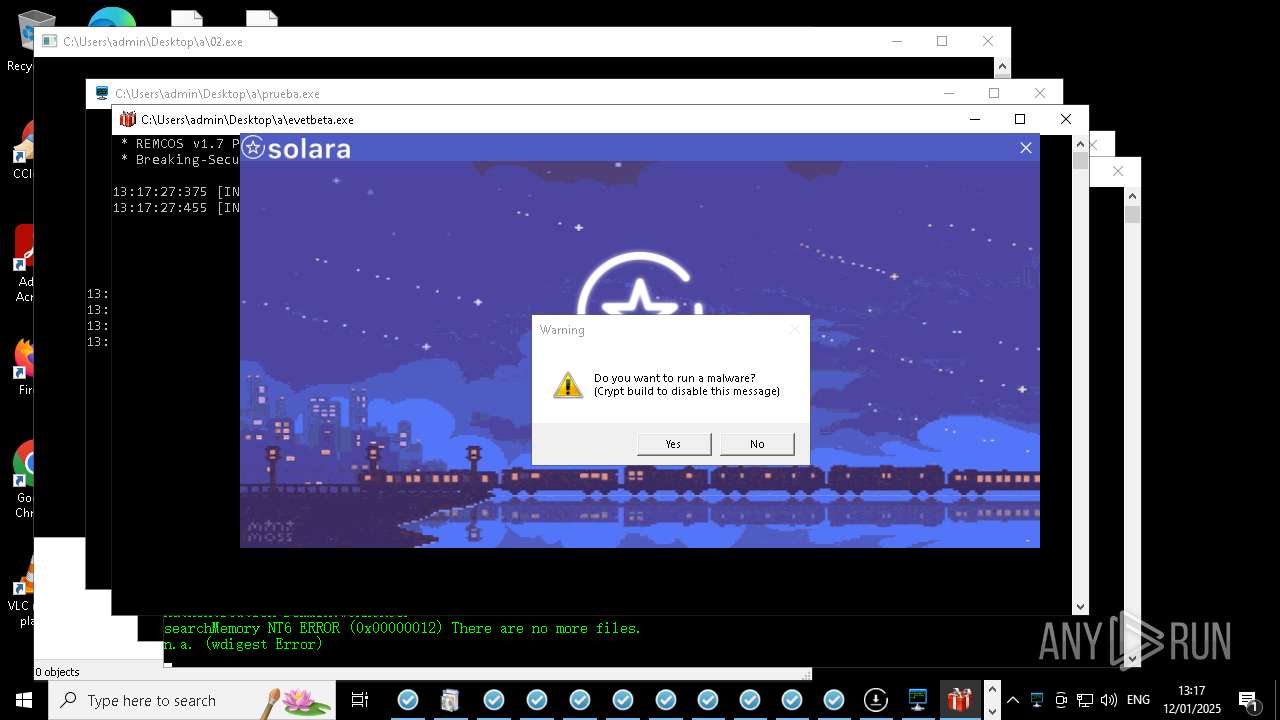
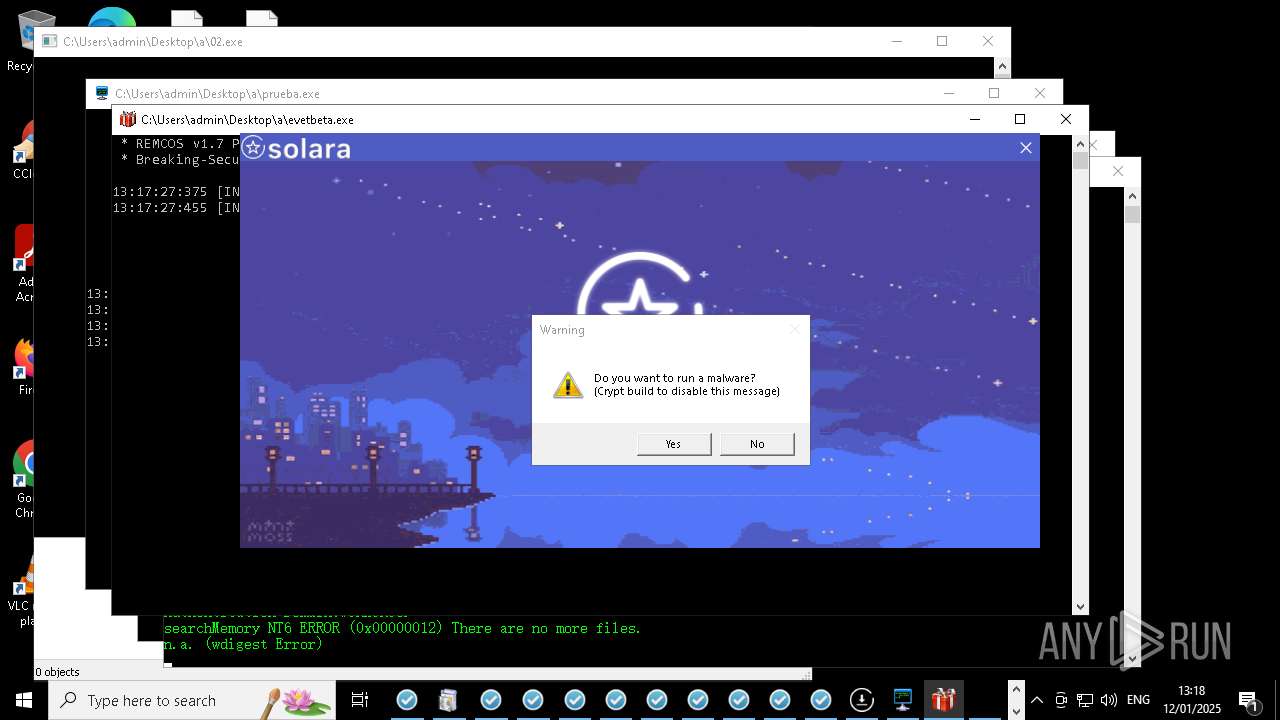
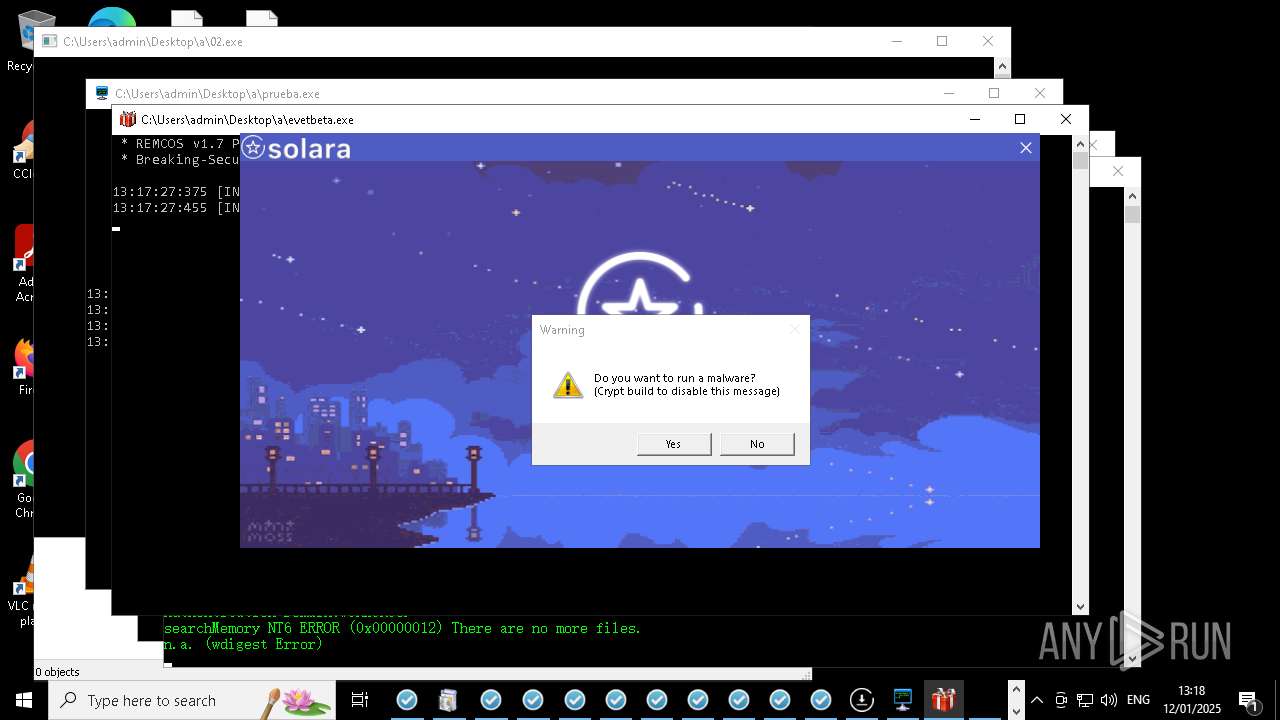
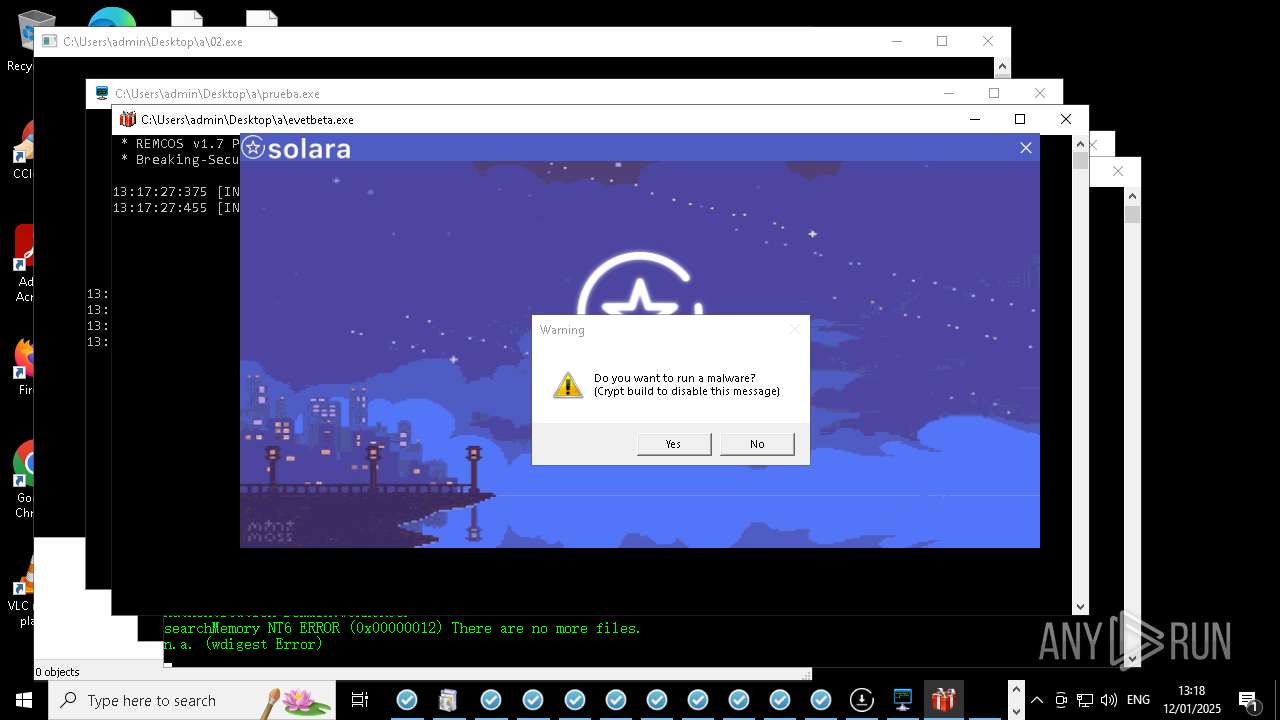
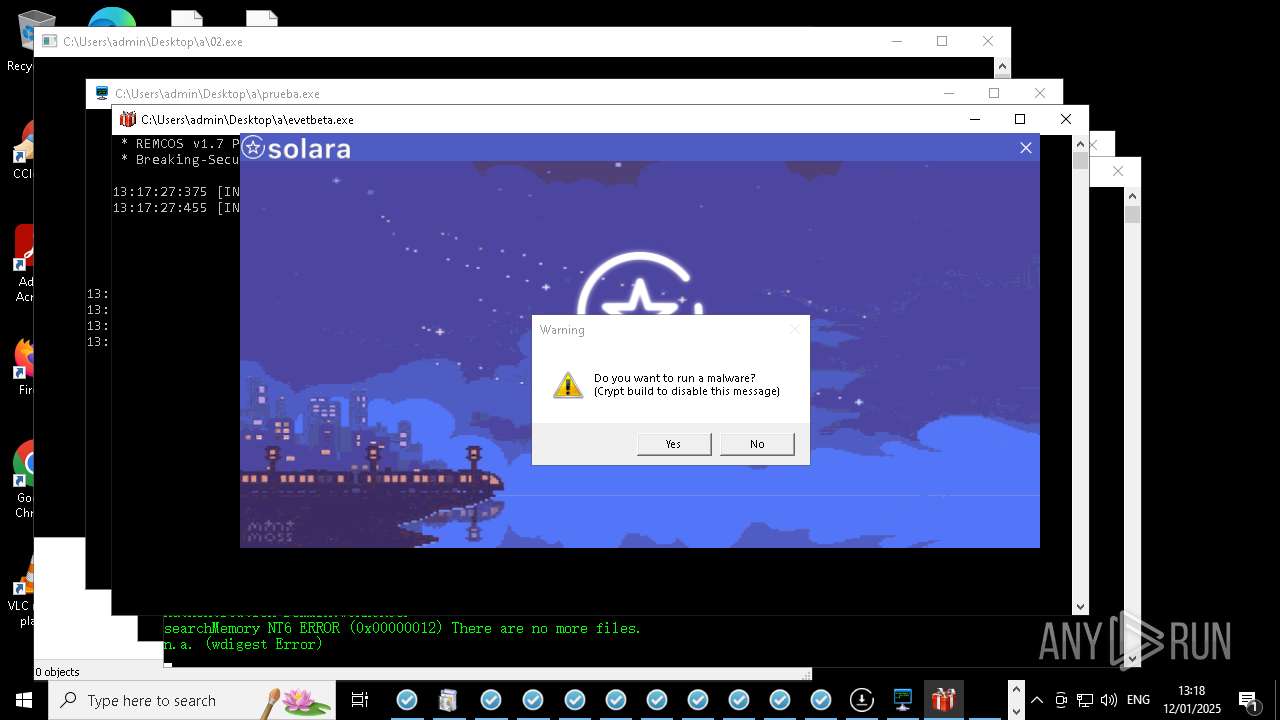
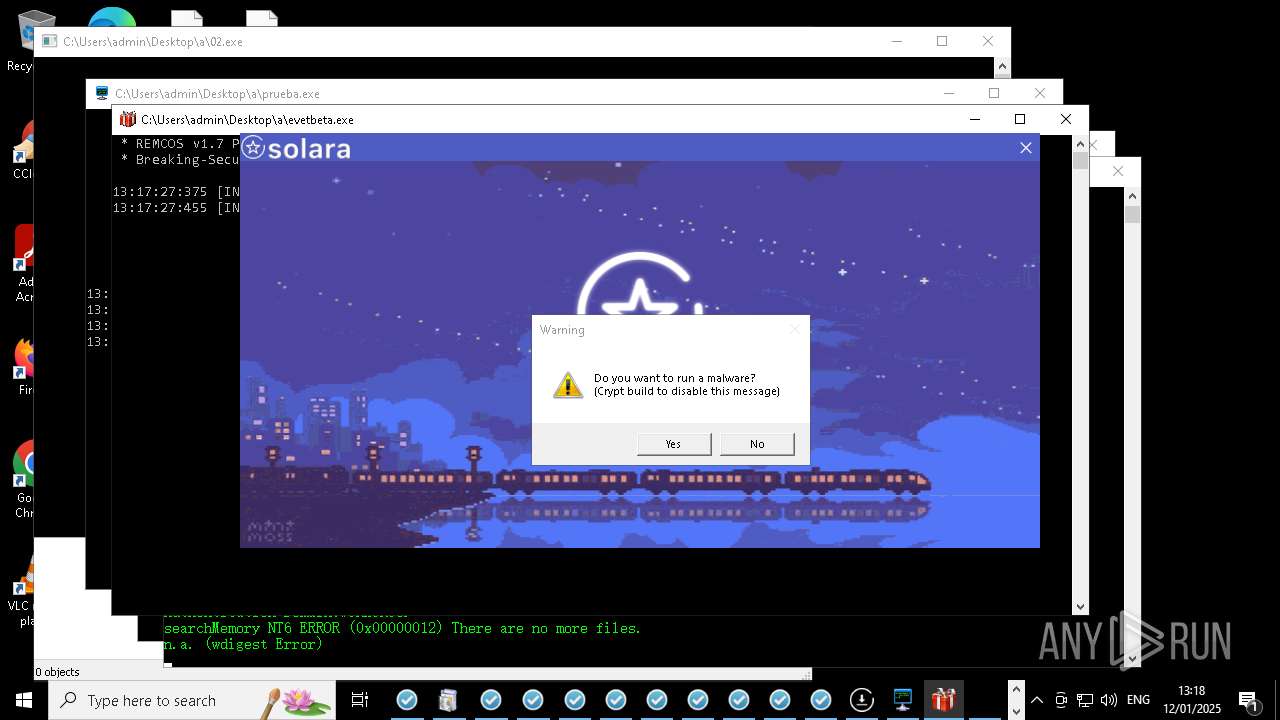
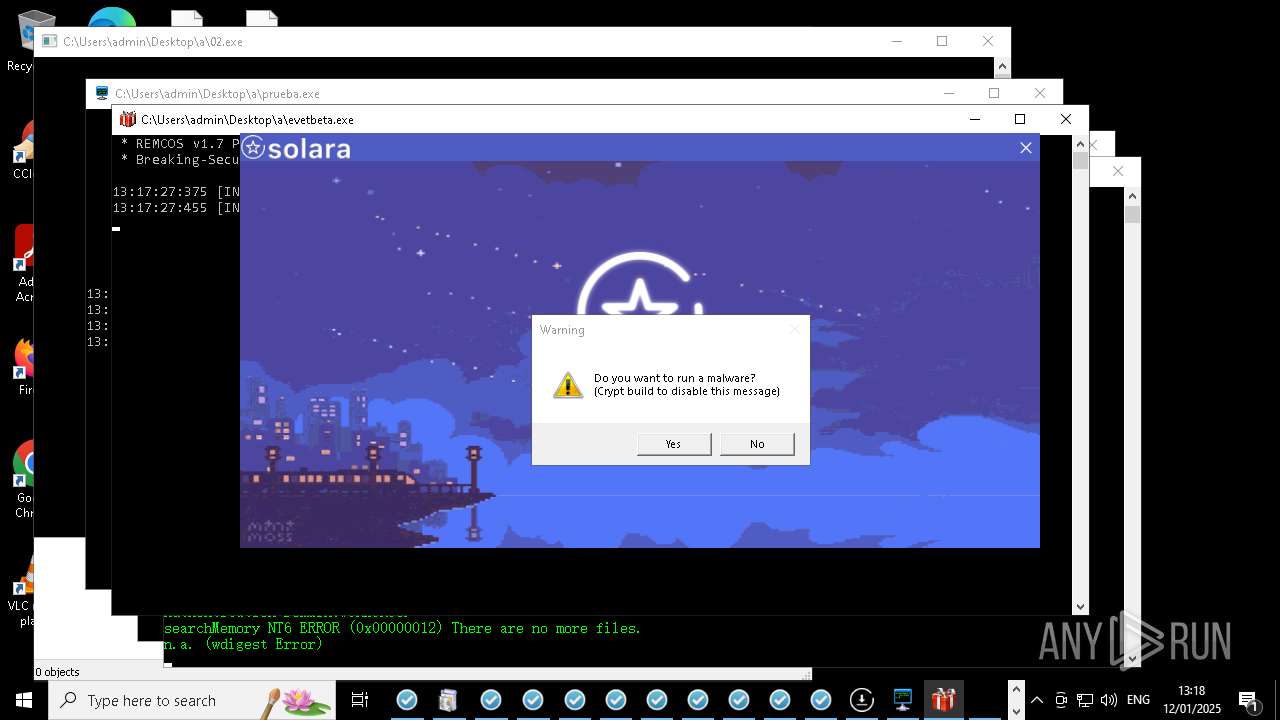
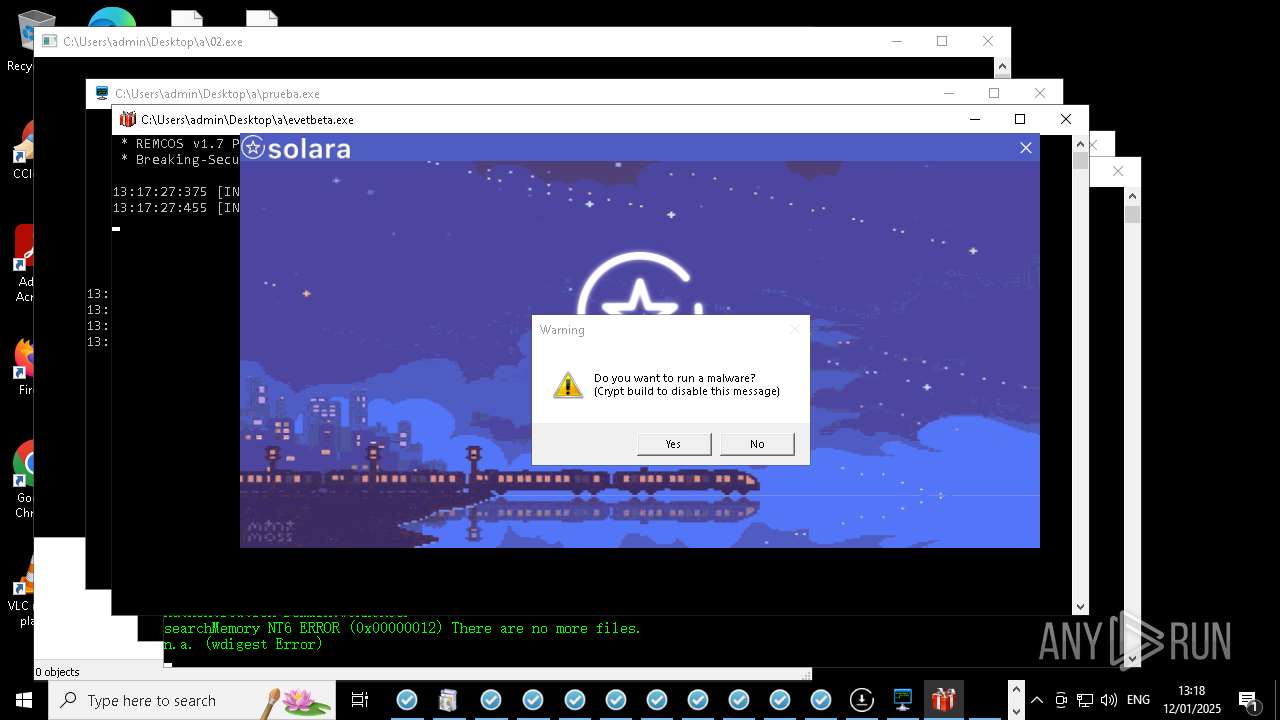
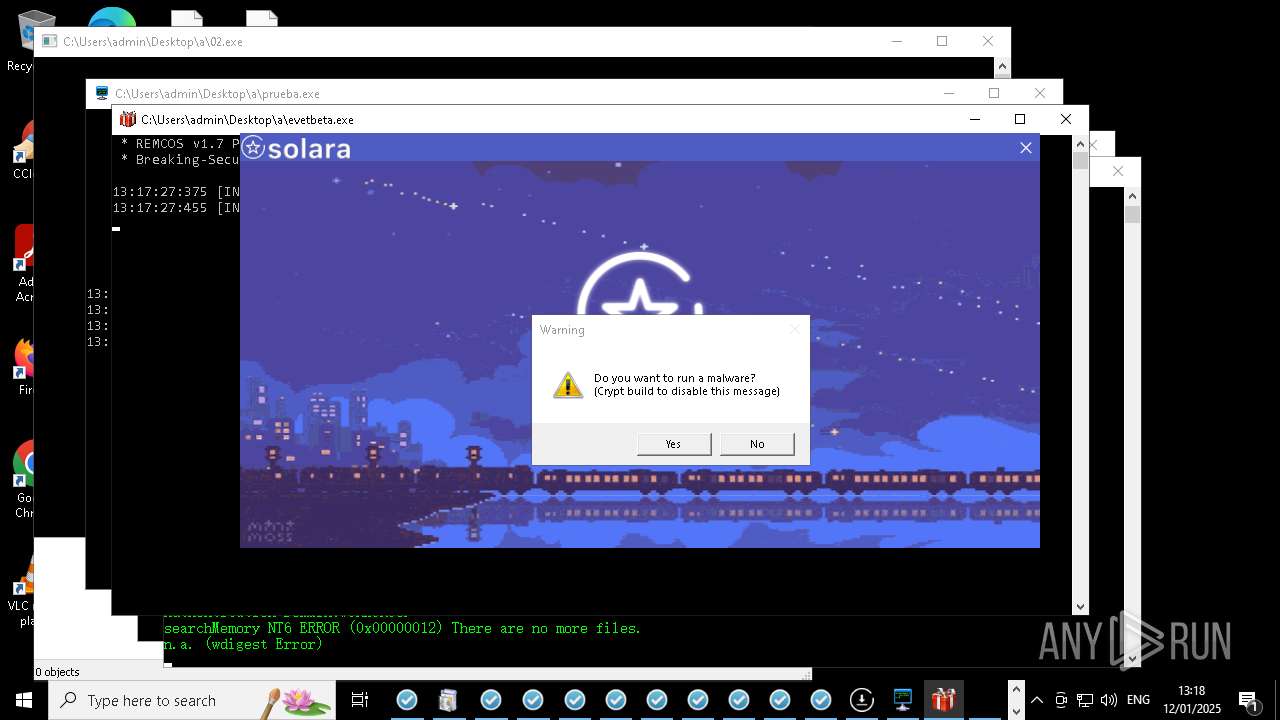
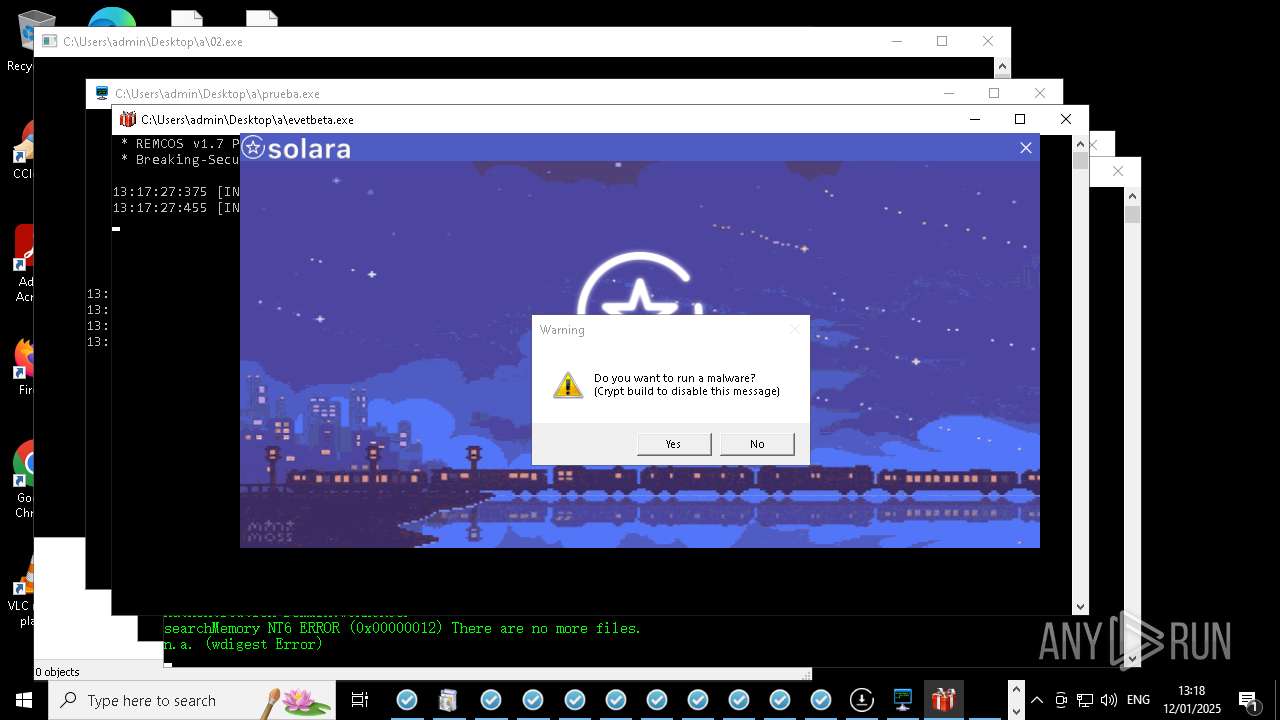
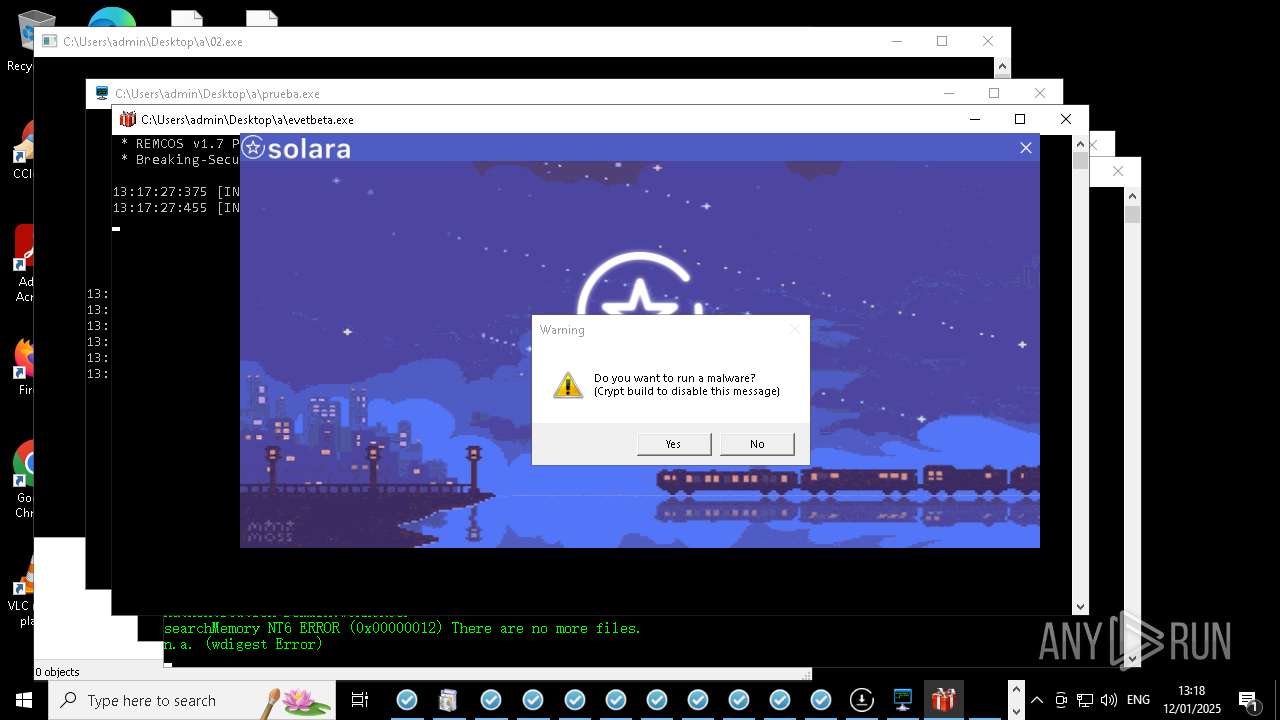
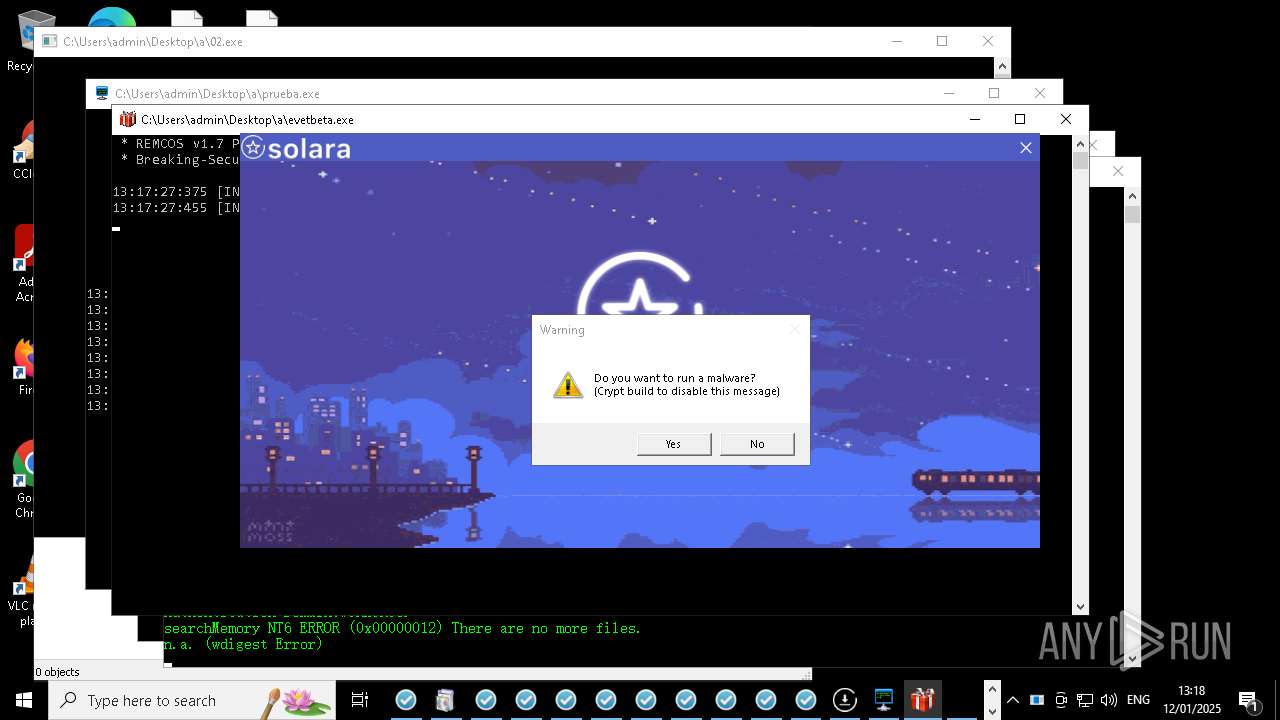
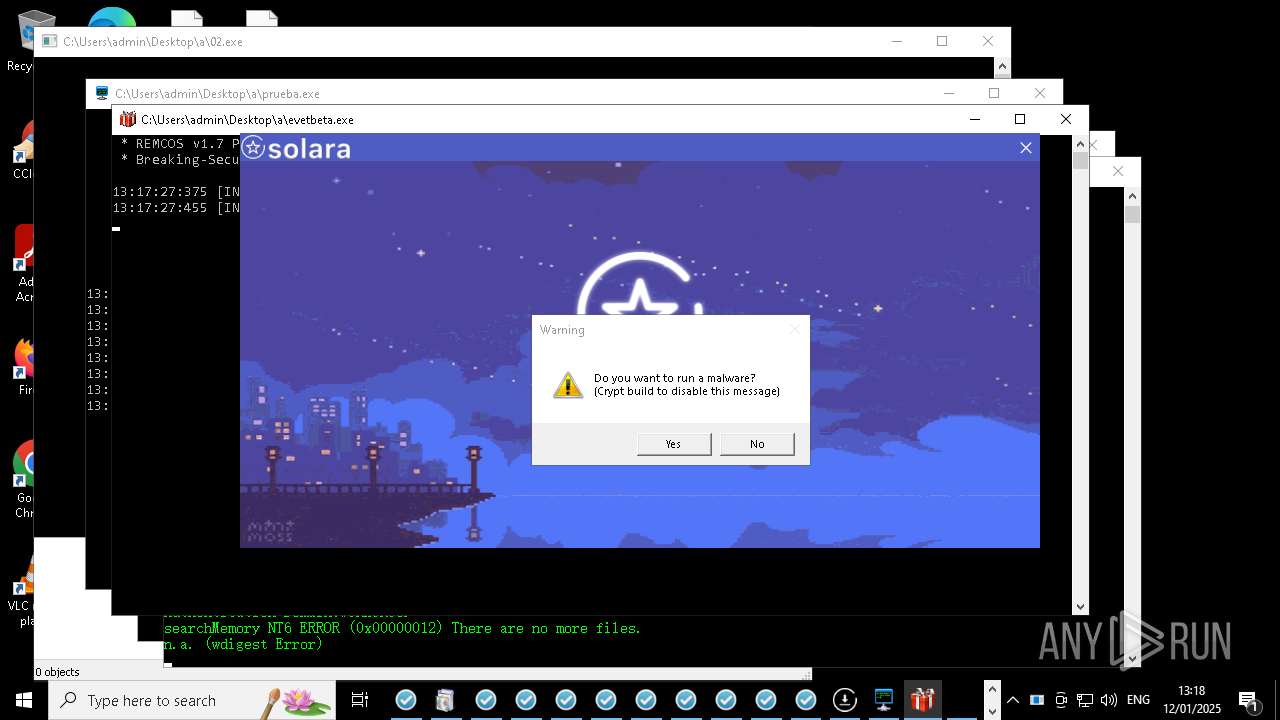
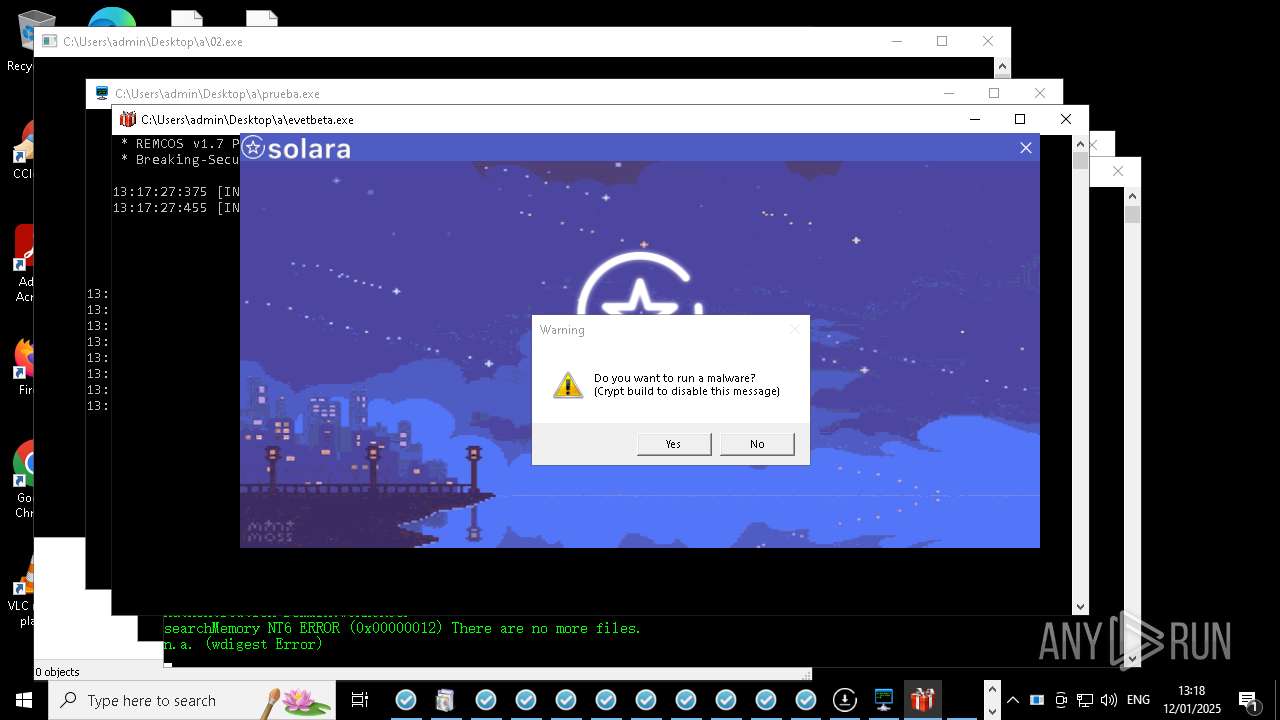
REMCOS has been detected
- evetbeta.exe (PID: 14488)
REMCOS mutex has been found
- prueba.exe (PID: 14396)
- evetbeta.exe (PID: 14488)
- benpolatalemdar.exe (PID: 14568)
REMCOS has been found (auto)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
REMCOS has been detected (SURICATA)
- evetbeta.exe (PID: 14488)
- prueba.exe (PID: 14396)
- iexplore.exe (PID: 13116)
NJRAT has been found (auto)
- testingg.exe (PID: 15096)
- Server.exe (PID: 15292)
- server.exe (PID: 14200)
Starts CMD.EXE for commands execution
- iexplore.exe (PID: 13116)
UAC/LUA settings modification
- reg.exe (PID: 9080)
BlankGrabber has been detected
- mcgen.exe (PID: 14080)
- mcgen.exe (PID: 16096)
Bypass User Account Control (Modify registry)
- reg.exe (PID: 13216)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 15712)
QUASAR has been found (auto)
- 2klz.exe (PID: 15808)
- diskutil.exe (PID: 15508)
- Test2.exe (PID: 16128)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- OneDrive.exe (PID: 15196)
Adds path to the Windows Defender exclusion list
- mcgen.exe (PID: 16196)
- cmd.exe (PID: 16372)
- cmd.exe (PID: 16952)
- Bootxr.exe (PID: 19728)
- cmd.exe (PID: 19844)
- Built.exe (PID: 21368)
- cmd.exe (PID: 19784)
- cmd.exe (PID: 18544)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 16380)
- cmd.exe (PID: 15948)
NjRAT is detected
- server.exe (PID: 9196)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 16144)
- powershell.exe (PID: 20628)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 16144)
- powershell.exe (PID: 20628)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 16144)
- powershell.exe (PID: 20628)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 16144)
- powershell.exe (PID: 20628)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 16144)
- powershell.exe (PID: 20628)
Changes Controlled Folder Access settings
- powershell.exe (PID: 16144)
- powershell.exe (PID: 20628)
Changes settings for real-time protection
- powershell.exe (PID: 16144)
- powershell.exe (PID: 20628)
BLANKGRABBER has been found (auto)
- mcgen.exe (PID: 16196)
REDLINE has been found (auto)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
Resets Windows Defender malware definitions to the base version
- MpCmdRun.exe (PID: 18040)
- MpCmdRun.exe (PID: 15880)
Scans artifacts that could help determine the target
- dw20.exe (PID: 18872)
XWORM has been detected (SURICATA)
- Java32.exe (PID: 18964)
- XClient.exe (PID: 19052)
VIDAR mutex has been found
- ghjaedjgaw.exe (PID: 19912)
Application was injected by another process
- explorer.exe (PID: 4488)
Runs injected code in another process
- svchost.exe (PID: 20272)
Loads dropped or rewritten executable
- conhost.exe (PID: 4428)
- conhost.exe (PID: 8440)
- cmd.exe (PID: 15464)
- SIHClient.exe (PID: 12784)
- consent.exe (PID: 10092)
- consent.exe (PID: 13920)
- 2klz.exe (PID: 14792)
- cmd.exe (PID: 14592)
- powershell.exe (PID: 15004)
- mimikatz.exe (PID: 6348)
- powershell.exe (PID: 15916)
- cmd.exe (PID: 16424)
- systeminfo.exe (PID: 15168)
- cmd.exe (PID: 18336)
- WinDrive-f4855f59e0.exe (PID: 6860)
- cmd.exe (PID: 15712)
- consent.exe (PID: 4932)
- conhost.exe (PID: 14980)
- cmd.exe (PID: 16952)
- conhost.exe (PID: 20324)
- consent.exe (PID: 2084)
- cmd.exe (PID: 16496)
- conhost.exe (PID: 15540)
- mode11_AKUh.exe (PID: 15388)
- conhost.exe (PID: 8700)
- conhost.exe (PID: 16484)
- conhost.exe (PID: 8924)
- cmd.exe (PID: 15316)
- conhost.exe (PID: 7012)
- cmd.exe (PID: 15980)
- seksiak.exe (PID: 19252)
- conhost.exe (PID: 14420)
- 2klz.exe (PID: 15808)
- conhost.exe (PID: 12372)
- cmd.exe (PID: 17700)
- svchost.exe (PID: 7024)
- conhost.exe (PID: 14728)
- cmd.exe (PID: 6180)
- Onedrive.exe (PID: 16608)
- diskutil.exe (PID: 15508)
- consent.exe (PID: 10216)
- seksiak.exe (PID: 18232)
- conhost.exe (PID: 19536)
- cmd.exe (PID: 9344)
- elm.exe (PID: 6372)
- cmd.exe (PID: 19016)
- cmd.exe (PID: 15136)
- win.exe (PID: 2280)
- WMIC.exe (PID: 16456)
- conhost.exe (PID: 14748)
- cmd.exe (PID: 14788)
- conhost.exe (PID: 11760)
- cmd.exe (PID: 16124)
- conhost.exe (PID: 21040)
- conhost.exe (PID: 15876)
- cmd.exe (PID: 15500)
- conhost.exe (PID: 18924)
- conhost.exe (PID: 10920)
- cmd.exe (PID: 16380)
- seksiak.exe (PID: 16664)
- xmrig.exe (PID: 6316)
- cmd.exe (PID: 16620)
- cmd.exe (PID: 6492)
- conhost.exe (PID: 16628)
- hdont.exe (PID: 4708)
- conhost.exe (PID: 19936)
- cmd.exe (PID: 13760)
- cmd.exe (PID: 13676)
- consent.exe (PID: 12084)
- backgroundTaskHost.exe (PID: 19616)
- conhost.exe (PID: 3724)
- conhost.exe (PID: 4144)
- conhost.exe (PID: 11000)
- conhost.exe (PID: 16880)
- conhost.exe (PID: 11884)
- powershell.exe (PID: 4460)
- conhost.exe (PID: 7800)
- utkin.exe (PID: 68)
- conhost.exe (PID: 18156)
- consent.exe (PID: 6444)
- consent.exe (PID: 15484)
- netsh.exe (PID: 15212)
- 2klz.exe (PID: 15368)
- powershell.exe (PID: 17324)
- conhost.exe (PID: 6936)
- Google%20Chrome.exe (PID: 15892)
- dllhost.exe (PID: 6176)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- windows 3543.exe (PID: 9860)
- BootstrapperNew.exe (PID: 8104)
- cmd.exe (PID: 6540)
- conhost.exe (PID: 8384)
- cmd.exe (PID: 15248)
- consent.exe (PID: 13200)
- conhost.exe (PID: 13244)
- dllhost.exe (PID: 6960)
- seksiak.exe (PID: 9200)
- conhost.exe (PID: 11068)
- mode11_buqd.exe (PID: 18612)
- diskutil.exe (PID: 16244)
- conhost.exe (PID: 9824)
- svchost.exe (PID: 3532)
- conhost.exe (PID: 9380)
- hr.exe (PID: 18108)
- schtasks.exe (PID: 2040)
- conhost.exe (PID: 3620)
- cmd.exe (PID: 14936)
- consent.exe (PID: 4968)
- powercfg.exe (PID: 2928)
- hdont.exe (PID: 5572)
- cmd.exe (PID: 14956)
- RuntimeBroker.exe (PID: 7216)
- cmd.exe (PID: 18808)
- conhost.exe (PID: 12564)
- cmd.exe (PID: 15868)
- conhost.exe (PID: 15972)
- cmd.exe (PID: 18956)
- consent.exe (PID: 5980)
- cbot.exe (PID: 236)
- TrustedInstaller.exe (PID: 18096)
- Client.exe (PID: 16956)
- RuntimeBroker.exe (PID: 12056)
- icacls.exe (PID: 6468)
- conhost.exe (PID: 12164)
- svchost.exe (PID: 14976)
- consent.exe (PID: 2280)
- consent.exe (PID: 4688)
- conhost.exe (PID: 15308)
- cmd.exe (PID: 5448)
- cmd.exe (PID: 19100)
- conhost.exe (PID: 15296)
- RuntimeBroker.exe (PID: 11068)
- cmd.exe (PID: 14816)
- conhost.exe (PID: 14820)
- dllhost.exe (PID: 4036)
- conhost.exe (PID: 18144)
- cmd.exe (PID: 6952)
- mcgen.exe (PID: 16196)
- 2klz.exe (PID: 18148)
- cmd.exe (PID: 17268)
- Built.exe (PID: 21368)
- wevtutil.exe (PID: 13688)
- conhost.exe (PID: 19028)
- conhost.exe (PID: 13612)
- conhost.exe (PID: 14404)
- cmd.exe (PID: 17612)
- cmd.exe (PID: 15416)
- conhost.exe (PID: 19776)
- cmd.exe (PID: 15128)
- tasklist.exe (PID: 17284)
- WMIC.exe (PID: 6692)
- JJSPLOIT.V2.exe (PID: 9724)
- consent.exe (PID: 8232)
- conhost.exe (PID: 16172)
- conhost.exe (PID: 16876)
- conhost.exe (PID: 8352)
- Client.exe (PID: 16696)
- Gorebox%20ModMenu%201.2.0.exe (PID: 15864)
- conhost.exe (PID: 15512)
- powershell.exe (PID: 17200)
- conhost.exe (PID: 9060)
- chrome.exe (PID: 11200)
- Client.exe (PID: 13236)
- conhost.exe (PID: 6296)
- consent.exe (PID: 10108)
- cmd.exe (PID: 14708)
- conhost.exe (PID: 7148)
- conhost.exe (PID: 15868)
- conhost.exe (PID: 18620)
- consent.exe (PID: 10588)
- conhost.exe (PID: 16084)
- conhost.exe (PID: 16524)
- consent.exe (PID: 4336)
- OneDrive.exe (PID: 15196)
- conhost.exe (PID: 10080)
- TiWorker.exe (PID: 15220)
- conhost.exe (PID: 6328)
- cmd.exe (PID: 14748)
- cmd.exe (PID: 17388)
- dropper64.exe (PID: 20180)
- consent.exe (PID: 13396)
- powercfg.exe (PID: 3032)
- audiodg.exe (PID: 20280)
- cmd.exe (PID: 9816)
- 3148931435.exe (PID: 12056)
- conhost.exe (PID: 13528)
- 2klz.exe (PID: 14744)
- conhost.exe (PID: 14204)
- cmd.exe (PID: 19396)
- seksiak.exe (PID: 12372)
- conhost.exe (PID: 4336)
- cmd.exe (PID: 16936)
- conhost.exe (PID: 4668)
- conhost.exe (PID: 16020)
- takeown.exe (PID: 4944)
- conhost.exe (PID: 13184)
- tasklist.exe (PID: 15816)
- consent.exe (PID: 12896)
- cmd.exe (PID: 15400)
- TEST.exe (PID: 8624)
- cmd.exe (PID: 17396)
- cmd.exe (PID: 17308)
- conhost.exe (PID: 1472)
- Client.exe (PID: 21012)
- @bebanrti%20(1).exe (PID: 6896)
- cmd.exe (PID: 2512)
- consent.exe (PID: 6296)
- conhost.exe (PID: 14332)
- seksiak.exe (PID: 18736)
- conhost.exe (PID: 2728)
- WMIC.exe (PID: 16056)
- conhost.exe (PID: 20944)
- powercfg.exe (PID: 6244)
- consent.exe (PID: 14972)
- msiexec.exe (PID: 20288)
- cmd.exe (PID: 12148)
- conhost.exe (PID: 6968)
- csc.exe (PID: 17860)
- conhost.exe (PID: 19108)
- cmd.exe (PID: 16716)
- markiz.exe (PID: 6656)
- conhost.exe (PID: 3792)
- icacls.exe (PID: 6584)
- Client.exe (PID: 18900)
- utkin.exe (PID: 6164)
- conhost.exe (PID: 17792)
- mode11_N1Fz.exe (PID: 16932)
- conhost.exe (PID: 6712)
- conhost.exe (PID: 5448)
- conhost.exe (PID: 9556)
- conhost.exe (PID: 15420)
- WmiPrvSE.exe (PID: 17024)
- chrome.exe (PID: 19868)
- cmd.exe (PID: 16900)
- svchost.exe (PID: 7000)
- conhost.exe (PID: 6548)
- conhost.exe (PID: 6868)
- kanew.exe (PID: 7008)
- conhost.exe (PID: 15384)
- consent.exe (PID: 1544)
- cmd.exe (PID: 7236)
- WmiPrvSE.exe (PID: 6568)
- conhost.exe (PID: 7628)
- conhost.exe (PID: 6272)
- conhost.exe (PID: 6892)
- Coc%20Coc.exe (PID: 18552)
- conhost.exe (PID: 16316)
- cmd.exe (PID: 17208)
- WMIC.exe (PID: 7032)
- Java32.exe (PID: 18964)
- conhost.exe (PID: 15716)
- consent.exe (PID: 6492)
- consent.exe (PID: 6744)
- conhost.exe (PID: 15488)
- mode11_UVo6.exe (PID: 15944)
- conhost.exe (PID: 4512)
- conhost.exe (PID: 16744)
- MpCmdRun.exe (PID: 18040)
- conhost.exe (PID: 17596)
- conhost.exe (PID: 19180)
- cmd.exe (PID: 14016)
- WMIC.exe (PID: 9760)
- 1346722953.exe (PID: 8832)
- cmd.exe (PID: 9092)
- conhost.exe (PID: 19388)
- conhost.exe (PID: 2040)
- consent.exe (PID: 18360)
- conhost.exe (PID: 2392)
- conhost.exe (PID: 11008)
- consent.exe (PID: 4548)
- kanew.exe (PID: 6184)
- cmd.exe (PID: 14584)
- seksiak.exe (PID: 16964)
- cmd.exe (PID: 6404)
- Client.exe (PID: 17124)
- cmd.exe (PID: 9304)
- chrtrome22.exe (PID: 6700)
- 64.exe (PID: 9820)
- conhost.exe (PID: 13940)
- sk.exe (PID: 6684)
- conhost.exe (PID: 12864)
- svhost.exe (PID: 6892)
- conhost.exe (PID: 6224)
- 2klz.exe (PID: 17152)
- conhost.exe (PID: 4036)
- windows 3543.exe (PID: 17012)
- elm.exe (PID: 6324)
- conhost.exe (PID: 19356)
- gem2.exe (PID: 6704)
- mcgen.exe (PID: 14080)
- cmd.exe (PID: 16344)
- conhost.exe (PID: 14300)
- XClient.exe (PID: 19052)
- conhost.exe (PID: 16996)
- Client.exe (PID: 18760)
- 2klz.exe (PID: 18872)
- wevtutil.exe (PID: 16320)
- cmd.exe (PID: 2216)
- conhost.exe (PID: 14916)
- conhost.exe (PID: 13688)
- mcgen.exe (PID: 14340)
- consent.exe (PID: 6388)
- cmd.exe (PID: 15452)
- conhost.exe (PID: 8180)
- conhost.exe (PID: 16916)
- conhost.exe (PID: 19760)
- svchost.exe (PID: 11680)
- powercfg.exe (PID: 6300)
- RuntimeBroker.exe (PID: 14252)
- conhost.exe (PID: 9772)
- Built.exe (PID: 20996)
- conhost.exe (PID: 15192)
- WmiPrvSE.exe (PID: 14596)
- mcgen.exe (PID: 16096)
- dllhost.exe (PID: 6784)
- xmrig.exe (PID: 7620)
- Loader.exe (PID: 15480)
- conhost.exe (PID: 6924)
- conhost.exe (PID: 15628)
- conhost.exe (PID: 14504)
- cmd.exe (PID: 19748)
- WMIC.exe (PID: 10976)
- C996.tmp.zx.exe (PID: 21092)
- 2klz.exe (PID: 16300)
- 2klz.exe (PID: 13192)
- conhost.exe (PID: 13244)
- Client.exe (PID: 18068)
- conhost.exe (PID: 16736)
- consent.exe (PID: 6752)
- conhost.exe (PID: 6504)
- conhost.exe (PID: 17360)
- conhost.exe (PID: 2776)
- conhost.exe (PID: 18724)
- WmiPrvSE.exe (PID: 17708)
- consent.exe (PID: 9332)
- powershell.exe (PID: 6884)
- Test2.exe (PID: 16128)
- cmd.exe (PID: 2576)
- conhost.exe (PID: 15296)
- minimal.exe (PID: 4320)
- consent.exe (PID: 13120)
- conhost.exe (PID: 13508)
- conhost.exe (PID: 11072)
- markiz.exe (PID: 6564)
- drop2.exe (PID: 9952)
- conhost.exe (PID: 7252)
- cmd.exe (PID: 19736)
- @bebanrti%20(1).exe (PID: 6460)
- seksiak.exe (PID: 8992)
- conhost.exe (PID: 16572)
- cmd.exe (PID: 12516)
- getmac.exe (PID: 14852)
- WmiPrvSE.exe (PID: 1416)
- consent.exe (PID: 20508)
- conhost.exe (PID: 13920)
- conhost.exe (PID: 16352)
- tasklist.exe (PID: 16848)
- conhost.exe (PID: 14808)
- chrome.exe (PID: 4204)
- WMIC.exe (PID: 3732)
- cmd.exe (PID: 16088)
- conhost.exe (PID: 10288)
- cmd.exe (PID: 16372)
- consent.exe (PID: 11280)
- cmd.exe (PID: 15468)
- conhost.exe (PID: 16700)
- cmd.exe (PID: 21024)
- conhost.exe (PID: 11064)
- tasklist.exe (PID: 15160)
- conhost.exe (PID: 15460)
- consent.exe (PID: 2928)
- Client.exe (PID: 12836)
- svchost.exe (PID: 16544)
- cmd.exe (PID: 9532)
- curl.exe (PID: 6612)
- audiodg.exe (PID: 7216)
- svchost.exe (PID: 20272)
- ReAgentc.exe (PID: 7164)
- dllhost.exe (PID: 7108)
- conhost.exe (PID: 6700)
- consent.exe (PID: 9244)
- seksiak.exe (PID: 17988)
- conhost.exe (PID: 14332)
- conhost.exe (PID: 6328)
- conhost.exe (PID: 3428)
- conhost.exe (PID: 8916)
- conhost.exe (PID: 13696)
- cmd.exe (PID: 19412)
- conhost.exe (PID: 3692)
- seksiak.exe (PID: 20952)
- consent.exe (PID: 7020)
- sk.exe (PID: 6584)
- cmd.exe (PID: 15612)
- conhost.exe (PID: 9780)
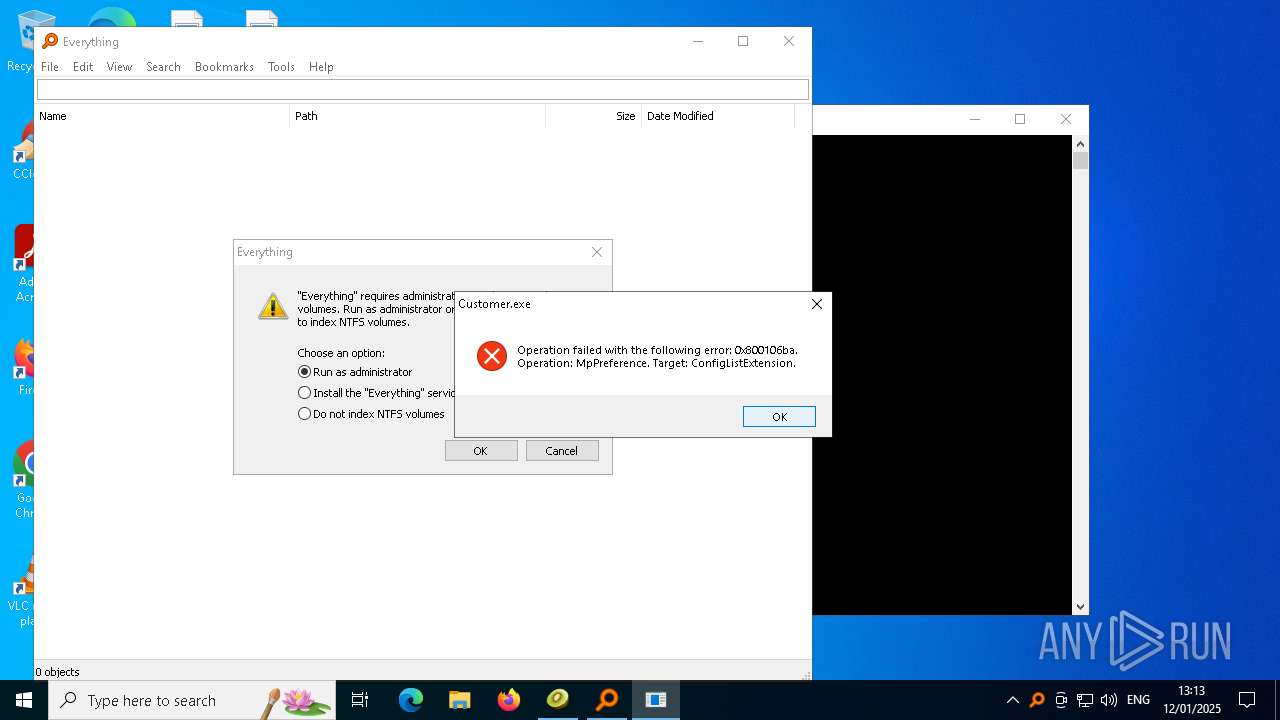
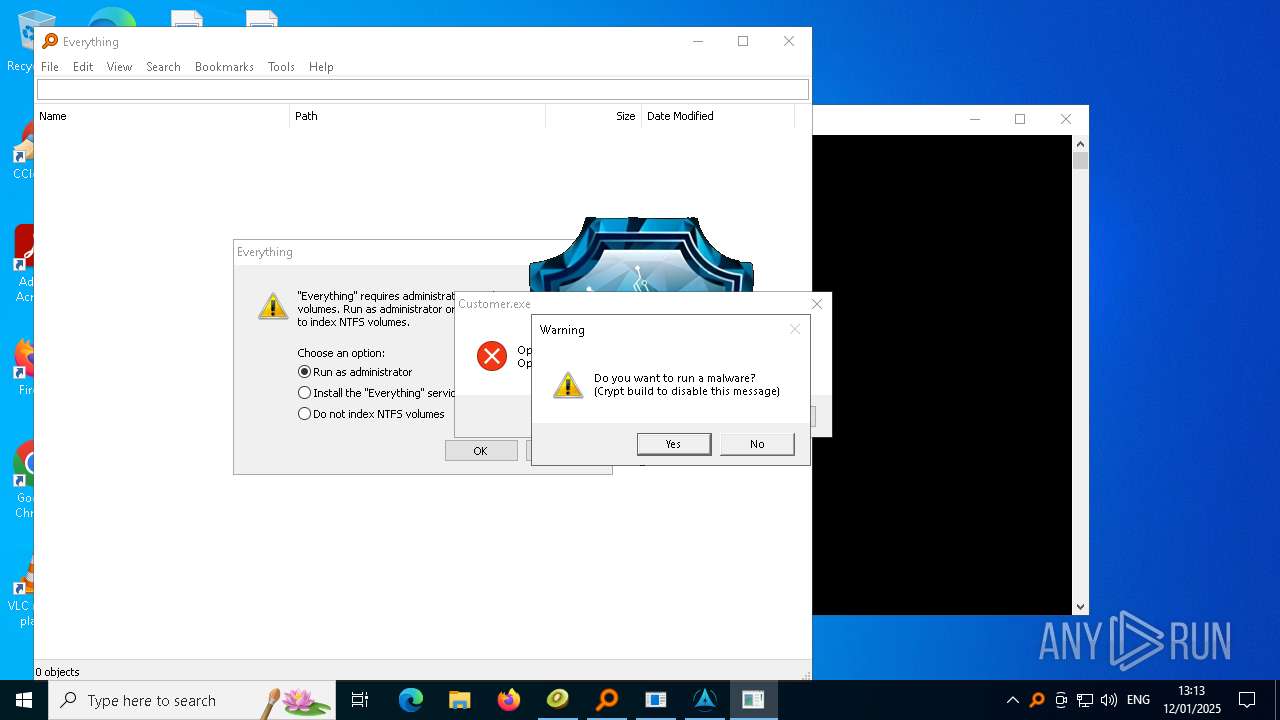
- Customer.exe (PID: 7968)
- ComputerDefaults.exe (PID: 15712)
- consent.exe (PID: 8508)
- conhost.exe (PID: 9696)
- WMIC.exe (PID: 6032)
- cmd.exe (PID: 19528)
- conhost.exe (PID: 12488)
- conhost.exe (PID: 16808)
- AdobePDFReader.exe (PID: 19308)
- ShellExperienceHost.exe (PID: 13568)
- consent.exe (PID: 12788)
- consent.exe (PID: 7916)
- conhost.exe (PID: 9772)
- powershell.exe (PID: 16144)
- curl.exe (PID: 5992)
- conhost.exe (PID: 14876)
- Launcher_Start.exe (PID: 9404)
- mode11_0HVJ.exe (PID: 16756)
- schtasks.exe (PID: 18792)
- WMIC.exe (PID: 15048)
- conhost.exe (PID: 12248)
- consent.exe (PID: 9752)
- csc.exe (PID: 8160)
- 2klz.exe (PID: 16248)
- cmd.exe (PID: 19636)
- cmd.exe (PID: 20464)
- cmd.exe (PID: 18568)
- powershell.exe (PID: 15712)
- C996.tmp.zx.exe (PID: 18152)
- WmiPrvSE.exe (PID: 18240)
- consent.exe (PID: 20756)
- conhost.exe (PID: 18776)
- cmd.exe (PID: 19008)
- conhost.exe (PID: 18732)
- conhost.exe (PID: 19168)
- conhost.exe (PID: 21260)
- cmd.exe (PID: 19784)
- WMIC.exe (PID: 19560)
- tasklist.exe (PID: 20248)
- cmd.exe (PID: 15948)
- cmd.exe (PID: 20496)
- conhost.exe (PID: 20224)
- powershell.exe (PID: 20628)
- conhost.exe (PID: 20932)
- cmd.exe (PID: 20088)
- powershell.exe (PID: 21424)
- WMIC.exe (PID: 12384)
- 2klz.exe (PID: 9012)
- conhost.exe (PID: 17828)
- cmd.exe (PID: 17812)
- WMIC.exe (PID: 21464)
- conhost.exe (PID: 20800)
- cmd.exe (PID: 20200)
- conhost.exe (PID: 16404)
- cmd.exe (PID: 16400)
- conhost.exe (PID: 15380)
- powershell.exe (PID: 17656)
- conhost.exe (PID: 13752)
- conhost.exe (PID: 21084)
- cmd.exe (PID: 18788)
- cmd.exe (PID: 11892)
- conhost.exe (PID: 14752)
- cmd.exe (PID: 18544)
- cmd.exe (PID: 19864)
- rar.exe (PID: 15624)
- seksiak.exe (PID: 18164)
- conhost.exe (PID: 13180)
- Client.exe (PID: 21464)
- cmd.exe (PID: 17828)
- conhost.exe (PID: 21612)
- cmd.exe (PID: 21468)
- conhost.exe (PID: 21656)
- conhost.exe (PID: 21488)
- conhost.exe (PID: 19684)
- conhost.exe (PID: 21852)
- conhost.exe (PID: 21952)
- cmd.exe (PID: 21576)
- cmd.exe (PID: 21644)
- conhost.exe (PID: 22088)
- cmd.exe (PID: 21604)
- powershell.exe (PID: 21816)
- cmd.exe (PID: 21732)
- conhost.exe (PID: 21748)
- conhost.exe (PID: 21700)
- conhost.exe (PID: 21792)
- conhost.exe (PID: 21900)
- cmd.exe (PID: 21836)
- cmd.exe (PID: 21684)
- cmd.exe (PID: 21892)
- tasklist.exe (PID: 22140)
- cmd.exe (PID: 22028)
- tasklist.exe (PID: 22180)
- cmd.exe (PID: 21780)
- tasklist.exe (PID: 22300)
- powershell.exe (PID: 22312)
- WMIC.exe (PID: 22448)
- powershell.exe (PID: 22324)
- systeminfo.exe (PID: 22424)
- WMIC.exe (PID: 22172)
- netsh.exe (PID: 22372)
- conhost.exe (PID: 21476)
- MpCmdRun.exe (PID: 15880)
- cmd.exe (PID: 17288)
- conhost.exe (PID: 20240)
- conhost.exe (PID: 20484)
- cmd.exe (PID: 20264)
- conhost.exe (PID: 16768)
- conhost.exe (PID: 19516)
- cmd.exe (PID: 17256)
- cmd.exe (PID: 18988)
- cmd.exe (PID: 11736)
- WMIC.exe (PID: 20136)
- cmd.exe (PID: 21668)
- conhost.exe (PID: 20684)
- conhost.exe (PID: 22032)
- TrustedInstaller.exe (PID: 22036)
- cmd.exe (PID: 22436)
- cmd.exe (PID: 20124)
- conhost.exe (PID: 20220)
- conhost.exe (PID: 22016)
- WMIC.exe (PID: 18756)
- csc.exe (PID: 15868)
- conhost.exe (PID: 4240)
- TiWorker.exe (PID: 11700)
- cmd.exe (PID: 21476)
- powershell.exe (PID: 9128)
- conhost.exe (PID: 22420)
- cmd.exe (PID: 22200)
- conhost.exe (PID: 8044)
- conhost.exe (PID: 21656)
- cmd.exe (PID: 19672)
- conhost.exe (PID: 22356)
- conhost.exe (PID: 22016)
- conhost.exe (PID: 21948)
- powershell.exe (PID: 15868)
- wusa.exe (PID: 19216)
- 2klz.exe (PID: 17348)
- WMIC.exe (PID: 19880)
- cmd.exe (PID: 18024)
- conhost.exe (PID: 22444)
- conhost.exe (PID: 22436)
- cmd.exe (PID: 21792)
- powershell.exe (PID: 21964)
- conhost.exe (PID: 20204)
- cmd.exe (PID: 17584)
- seksiak.exe (PID: 22292)
- Client.exe (PID: 22048)
- conhost.exe (PID: 20160)
- cmd.exe (PID: 19672)
- conhost.exe (PID: 18284)
- cmd.exe (PID: 6448)
- conhost.exe (PID: 20988)
- cmd.exe (PID: 20888)
- conhost.exe (PID: 19872)
- conhost.exe (PID: 20316)
- wusa.exe (PID: 15860)
- cmd.exe (PID: 15412)
- getmac.exe (PID: 21936)
- 2klz.exe (PID: 15024)
- cmd.exe (PID: 6680)
- conhost.exe (PID: 15524)
- cmd.exe (PID: 20960)
- conhost.exe (PID: 17732)
- seksiak.exe (PID: 21740)
- Client.exe (PID: 21220)
- conhost.exe (PID: 17328)
- cmd.exe (PID: 15860)
- cmd.exe (PID: 20348)
- conhost.exe (PID: 18448)
- 2klz.exe (PID: 22340)
- conhost.exe (PID: 19712)
- cmd.exe (PID: 12764)
- seksiak.exe (PID: 21896)
- Client.exe (PID: 17816)
- conhost.exe (PID: 19924)
- conhost.exe (PID: 21676)
- cmd.exe (PID: 5724)
- cmd.exe (PID: 21088)
- 2klz.exe (PID: 19744)
- Client.exe (PID: 19488)
- conhost.exe (PID: 19896)
- cmd.exe (PID: 22076)
- seksiak.exe (PID: 19004)
- cmd.exe (PID: 15880)
- conhost.exe (PID: 17280)
- cmd.exe (PID: 19120)
- conhost.exe (PID: 10248)
- 2klz.exe (PID: 21596)
- cmd.exe (PID: 20664)
- conhost.exe (PID: 20676)
- Client.exe (PID: 22364)
- seksiak.exe (PID: 18624)
- conhost.exe (PID: 4800)
- conhost.exe (PID: 21744)
- cmd.exe (PID: 14452)
- cmd.exe (PID: 19700)
- 2klz.exe (PID: 20568)
- conhost.exe (PID: 7084)
- cmd.exe (PID: 8708)
- Client.exe (PID: 17332)
- seksiak.exe (PID: 8992)
- conhost.exe (PID: 22460)
- conhost.exe (PID: 2628)
- cmd.exe (PID: 18756)
- cmd.exe (PID: 19164)
- 2klz.exe (PID: 17576)
- cmd.exe (PID: 19516)
- Client.exe (PID: 13960)
- seksiak.exe (PID: 4304)
- conhost.exe (PID: 2452)
- conhost.exe (PID: 20056)
- conhost.exe (PID: 17380)
- cmd.exe (PID: 19740)
- cmd.exe (PID: 15412)
Adds extension to the Windows Defender exclusion list
- onedrive.exe (PID: 21100)
- vsrumanlxdbr.exe (PID: 18396)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 19952)
Uninstalls Malicious Software Removal Tool (MRT)
- cmd.exe (PID: 22200)
- cmd.exe (PID: 20888)
BLANKGRABBER has been detected (SURICATA)
- mcgen.exe (PID: 16196)
SUSPICIOUS
Reads security settings of Internet Explorer
- New Text Document mod.exe.bin.exe (PID: 624)
- Synaptics.exe (PID: 4952)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- whiteshadow.exe (PID: 2992)
- whiteshadow123.exe (PID: 5864)
- gem1.exe (PID: 6432)
- WinDrive-f4855f59e0.exe (PID: 6860)
- 32.exe (PID: 4912)
- sysnldcvmr.exe (PID: 2792)
- chrtrome22.exe (PID: 6700)
- 1724930485.exe (PID: 6180)
- Customer.exe (PID: 7968)
- 1X48r0.exe (PID: 8156)
- skotes.exe (PID: 6372)
- 696969.exe (PID: 9580)
- IMG001.exe (PID: 10860)
- IMG001.exe (PID: 11028)
- 3t57j.exe (PID: 10248)
- SCLKFNF21ARIHQ5RV63UYR.exe (PID: 10568)
- 4e452a47dd.exe (PID: 9076)
- 1346722953.exe (PID: 8832)
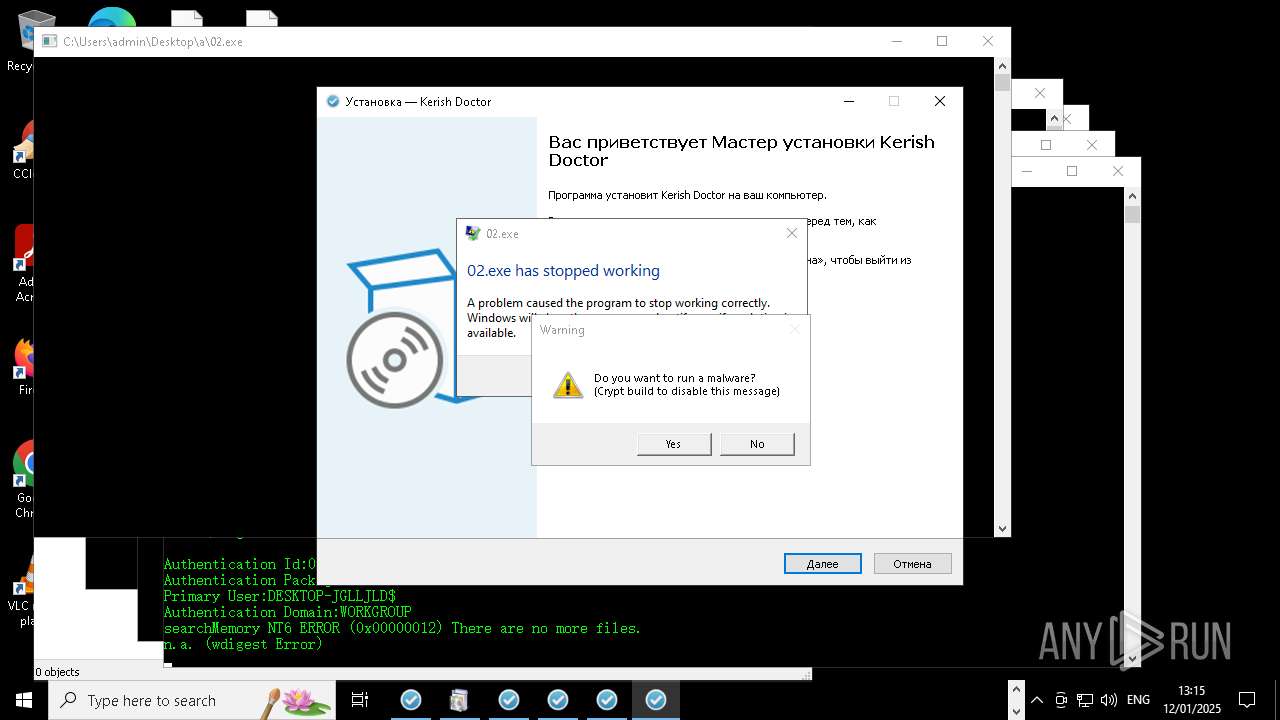
- Kerish_Doctor_Windows_XP.tmp (PID: 12992)
- Kerish_Doctor_Windows_8.tmp (PID: 12776)
- Kerish_Doctor_Windows.tmp (PID: 11568)
- Kerish_Doctor_Windows_Vista.tmp (PID: 13452)
- BootstrapperNew.exe (PID: 8104)
- testingg.exe (PID: 15096)
- ShellExperienceHost.exe (PID: 13568)
- Server.exe (PID: 15292)
- seksiak.exe (PID: 8992)
- 2klz.exe (PID: 16248)
- Client.exe (PID: 12836)
- seksiak.exe (PID: 12372)
- 2klz.exe (PID: 16300)
- Client.exe (PID: 13236)
- windows 3543.exe (PID: 9860)
- 2klz.exe (PID: 14792)
- Client.exe (PID: 16956)
- seksiak.exe (PID: 9200)
- 2klz.exe (PID: 13192)
- mode11_UVo6.exe (PID: 15944)
- Client.exe (PID: 18068)
- mode11_0HVJ.exe (PID: 16756)
- mode11_AKUh.exe (PID: 15388)
- 2klz.exe (PID: 18148)
- seksiak.exe (PID: 16964)
- Client.exe (PID: 16696)
- mode11_N1Fz.exe (PID: 16932)
- 2klz.exe (PID: 14744)
- seksiak.exe (PID: 18736)
- Client.exe (PID: 18760)
- 2klz.exe (PID: 15368)
- mode11_buqd.exe (PID: 18612)
- seksiak.exe (PID: 17988)
- Coc%20Coc.exe (PID: 18552)
- 2klz.exe (PID: 18872)
- Google%20Chrome.exe (PID: 15892)
- Client.exe (PID: 17124)
- seksiak.exe (PID: 19252)
- ghjaedjgaw.exe (PID: 19912)
- microsoft-onedrive.exe (PID: 20660)
- Client.exe (PID: 21012)
- seksiak.exe (PID: 20952)
- seksiak.exe (PID: 18164)
- seksiak.exe (PID: 22292)
- Client.exe (PID: 22048)
- 2klz.exe (PID: 15024)
- Client.exe (PID: 21220)
- 2klz.exe (PID: 22340)
- seksiak.exe (PID: 21896)
- Client.exe (PID: 17816)
- 2klz.exe (PID: 19744)
- seksiak.exe (PID: 19004)
- Client.exe (PID: 19488)
- 2klz.exe (PID: 21596)
- 2klz.exe (PID: 20568)
- seksiak.exe (PID: 8992)
- Client.exe (PID: 17332)
- 2klz.exe (PID: 17576)
- Client.exe (PID: 13960)
- seksiak.exe (PID: 4304)
Executable content was dropped or overwritten
- New Text Document mod.exe.bin.exe (PID: 624)
- Synaptics.exe (PID: 4952)
- whiteshadow.exe (PID: 2992)
- minimal.exe (PID: 4320)
- sk.exe (PID: 6684)
- gem2.exe (PID: 6704)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- WinDrive-f4855f59e0.exe (PID: 6860)
- cbot.exe (PID: 236)
- 32.exe (PID: 4912)
- 2018910798.exe (PID: 6416)
- 1724930485.exe (PID: 6180)
- chrtrome22.exe (PID: 6700)
- csc.exe (PID: 8160)
- none.exe (PID: 7900)
- b2l20.exe (PID: 6224)
- 1X48r0.exe (PID: 8156)
- r3P25.exe (PID: 7944)
- 293637911.exe (PID: 7392)
- skotes.exe (PID: 6372)
- Server1.exe (PID: 8340)
- TEST.exe (PID: 8624)
- JJSPLOIT.V2.exe (PID: 9724)
- Launcher_Start.exe (PID: 9404)
- wudi.exe (PID: 4676)
- 2D8630.exe (PID: 4912)
- Crawl.exe (PID: 6448)
- IMG001.exe (PID: 10860)
- Kerish_Doctor_2022.exe (PID: 6636)
- Kerish_Doctor_2022.exe (PID: 10268)
- Kerish_Doctor_2022.tmp (PID: 10296)
- IMG001.exe (PID: 11028)
- Kerish_Doctor_2023.exe (PID: 10636)
- Kerish_Doctor_2023.tmp (PID: 10664)
- Kerish_Doctor.exe (PID: 7656)
- Kerish_Doctor.exe (PID: 11356)
- Kerish_Doctor.tmp (PID: 11388)
- Kerish_Doctor_2021.exe (PID: 12068)
- Kerish_Doctor_2021.exe (PID: 9616)
- Kerish_Doctor_2021.tmp (PID: 10748)
- 3070213606.exe (PID: 6700)
- Kerish_Doctor_Windows_8.2.exe (PID: 13052)
- Kerish_Doctor_2023.exe (PID: 7920)
- Kerish_Doctor_Windows_8.2.tmp (PID: 13228)
- Kerish_Doctor_Windows_XP.exe (PID: 11716)
- Kerish_Doctor_Windows_8.2.exe (PID: 13204)
- Kerish_Doctor_Windows_XP.exe (PID: 12244)
- Kerish_Doctor_Windows_XP.tmp (PID: 6096)
- Kerish_Doctor_Windows_8.exe (PID: 12644)
- Kerish_Doctor_Windows_8.exe (PID: 12952)
- Kerish_Doctor_Windows_8.tmp (PID: 12572)
- Kerish_Doctor_Windows.exe (PID: 11544)
- Kerish_Doctor_Windows.exe (PID: 9232)
- Kerish_Doctor_Windows.tmp (PID: 12092)
- Kerish_Doctor_2017.exe (PID: 13880)
- Kerish_Doctor_2017.tmp (PID: 12820)
- Kerish_Doctor_2017.exe (PID: 9008)
- Kerish_Doctor_Windows_Vista.exe (PID: 13372)
- Kerish_Doctor_Windows_Vista.tmp (PID: 13616)
- Kerish_Doctor_Windows_Vista.exe (PID: 13480)
- NOTallowedtocrypt.exe (PID: 15344)
- testingg.exe (PID: 15096)
- Server.exe (PID: 15292)
- mcgen.exe (PID: 14080)
- server.exe (PID: 14200)
- mcgen.exe (PID: 16096)
- 2klz.exe (PID: 15808)
- diskutil.exe (PID: 15508)
- Test2.exe (PID: 16128)
- OneDrive.exe (PID: 15196)
- mcgen.exe (PID: 16196)
- csc.exe (PID: 17860)
- XClient.exe (PID: 19052)
- Coc%20Coc.exe (PID: 18552)
- dropper64.exe (PID: 20180)
- explorer.exe (PID: 4488)
- microsoft-onedrive.exe (PID: 20660)
- C996.tmp.zx.exe (PID: 21092)
- Built.exe (PID: 20996)
- 33.exe (PID: 20532)
- Built.exe (PID: 21368)
- csc.exe (PID: 15868)
- onedrive.exe (PID: 21100)
- vsrumanlxdbr.exe (PID: 18396)
Contacting a server suspected of hosting an CnC
- Synaptics.exe (PID: 4952)
- svchost.exe (PID: 2192)
- build1.exe (PID: 7792)
- skotes.exe (PID: 6372)
- Server1.exe (PID: 8340)
- sela.exe (PID: 9336)
- 3t57j.exe (PID: 10248)
- SCLKFNF21ARIHQ5RV63UYR.exe (PID: 10568)
- evetbeta.exe (PID: 14488)
- server.exe (PID: 14200)
- server.exe (PID: 9196)
- prueba.exe (PID: 14396)
- iexplore.exe (PID: 13116)
- XClient.exe (PID: 19052)
- Java32.exe (PID: 18964)
Process requests binary or script from the Internet
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- 32.exe (PID: 4912)
- 1724930485.exe (PID: 6180)
- skotes.exe (PID: 6372)
- svchost.exe (PID: 7024)
- 2D8630.exe (PID: 4912)
- powershell.exe (PID: 19952)
Reads the date of Windows installation
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- chrtrome22.exe (PID: 6700)
- 3148931435.exe (PID: 12056)
- seksiak.exe (PID: 8992)
- 2klz.exe (PID: 16300)
- Client.exe (PID: 13236)
- seksiak.exe (PID: 9200)
- seksiak.exe (PID: 16964)
- 2klz.exe (PID: 14744)
- Client.exe (PID: 18760)
- dw20.exe (PID: 18872)
- 2klz.exe (PID: 15368)
- seksiak.exe (PID: 17988)
- Client.exe (PID: 18900)
- Client.exe (PID: 17124)
- seksiak.exe (PID: 19252)
- Client.exe (PID: 21012)
- 2klz.exe (PID: 9012)
- Client.exe (PID: 21464)
- 2klz.exe (PID: 17348)
- Client.exe (PID: 22048)
- seksiak.exe (PID: 21740)
- 2klz.exe (PID: 22340)
- Client.exe (PID: 17816)
- seksiak.exe (PID: 21896)
- 2klz.exe (PID: 19744)
- 2klz.exe (PID: 21596)
- seksiak.exe (PID: 18624)
- 2klz.exe (PID: 20568)
- 2klz.exe (PID: 17576)
- seksiak.exe (PID: 4304)
Searches for installed software
- whiteshadow123.exe (PID: 5864)
- 2D8630.exe (PID: 4912)
- 4e452a47dd.exe (PID: 9076)
Checks for external IP
- minimal.exe (PID: 4320)
- svchost.exe (PID: 2192)
- gem1.exe (PID: 6432)
- curl.exe (PID: 5992)
- curl.exe (PID: 6612)
- Client-built.exe (PID: 6976)
- build1.exe (PID: 7792)
- uu.exe (PID: 8280)
- mcgen.exe (PID: 16196)
- ytjgjdrthjdw.exe (PID: 16392)
- jrockekcurje.exe (PID: 16908)
- XClient.exe (PID: 19052)
- Java32.exe (PID: 18964)
- Built.exe (PID: 21368)
Connects to unusual port
- minimal.exe (PID: 4320)
- gem1.exe (PID: 6432)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- cbot.exe (PID: 236)
- tmx.exe (PID: 6456)
- 123.exe (PID: 6920)
- Client.exe (PID: 7108)
- payload.exe (PID: 5076)
- Fixer.exe (PID: 4336)
- Client-built.exe (PID: 6976)
- Steanings.exe (PID: 7748)
- build1.exe (PID: 7792)
- AsyncClientGK.exe (PID: 8048)
- uu.exe (PID: 8280)
- Server1.exe (PID: 8340)
- sysnldcvmr.exe (PID: 2792)
- sela.exe (PID: 9336)
- windows 3543.exe (PID: 9860)
- sdggwsdgdrwgrwgrwgrwgrw.exe (PID: 9812)
- prueba.exe (PID: 14396)
- evetbeta.exe (PID: 14488)
- benpolatalemdar.exe (PID: 14568)
- .exe (PID: 13588)
- server.exe (PID: 14200)
- server.exe (PID: 9196)
- ytjgjdrthjdw.exe (PID: 16392)
- Onedrive.exe (PID: 16608)
- jrockekcurje.exe (PID: 16908)
- build.exe (PID: 15188)
- toolwin.exe (PID: 14856)
- Sync.exe (PID: 17484)
- systempreter.exe (PID: 13344)
- windows 3543.exe (PID: 17012)
- mode11_UVo6.exe (PID: 15944)
- mode11_0HVJ.exe (PID: 16756)
- mode11_N1Fz.exe (PID: 16932)
- mode11_AKUh.exe (PID: 15388)
- cici.exe (PID: 18496)
- mode11_buqd.exe (PID: 18612)
- Java32.exe (PID: 18964)
- XClient.exe (PID: 19052)
- ioc.exe (PID: 20100)
- conhost.exe (PID: 19872)
There is functionality for communication over UDP network (YARA)
- Synaptics.exe (PID: 4952)
- The%20Foundry.exe (PID: 6716)
There is functionality for taking screenshot (YARA)
- Synaptics.exe (PID: 4952)
There is functionality for VM detection VirtualBox (YARA)
- whiteshadow123.exe (PID: 5864)
- WinDrive-f4855f59e0.exe (PID: 6860)
Connects to the server without a host name
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- sysnldcvmr.exe (PID: 2792)
- 1724930485.exe (PID: 6180)
- skotes.exe (PID: 6372)
- 696969.exe (PID: 9580)
- 2D8630.exe (PID: 4912)
- 3t57j.exe (PID: 10248)
- SCLKFNF21ARIHQ5RV63UYR.exe (PID: 10568)
- explorer.exe (PID: 4488)
- svchost.exe (PID: 20272)
- powershell.exe (PID: 19952)
Potential Corporate Privacy Violation
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- gem1.exe (PID: 6432)
- curl.exe (PID: 6612)
- 32.exe (PID: 4912)
- 1724930485.exe (PID: 6180)
- build1.exe (PID: 7792)
- skotes.exe (PID: 6372)
- 2D8630.exe (PID: 4912)
- svchost.exe (PID: 2192)
- explorer.exe (PID: 4488)
- powershell.exe (PID: 19952)
There is functionality for communication dyndns network (YARA)
- Synaptics.exe (PID: 4952)
There is functionality for capture public ip (YARA)
- minimal.exe (PID: 4320)
- svchost.exe (PID: 7024)
Checks Windows Trust Settings
- Synaptics.exe (PID: 4952)
- gem1.exe (PID: 6432)
- WinDrive-f4855f59e0.exe (PID: 6860)
- chrtrome22.exe (PID: 6700)
- Customer.exe (PID: 7968)
- mode11_0HVJ.exe (PID: 16756)
- mode11_UVo6.exe (PID: 15944)
- mode11_N1Fz.exe (PID: 16932)
- mode11_AKUh.exe (PID: 15388)
- mode11_buqd.exe (PID: 18612)
- ghjaedjgaw.exe (PID: 19912)
Process drops python dynamic module
- sk.exe (PID: 6684)
- mcgen.exe (PID: 14080)
- mcgen.exe (PID: 16096)
- Built.exe (PID: 20996)
- C996.tmp.zx.exe (PID: 21092)
Process drops legitimate windows executable
- sk.exe (PID: 6684)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- Synaptics.exe (PID: 4952)
- none.exe (PID: 7900)
- r3P25.exe (PID: 7944)
- TEST.exe (PID: 8624)
- Launcher_Start.exe (PID: 9404)
- mcgen.exe (PID: 14080)
- mcgen.exe (PID: 16096)
- diskutil.exe (PID: 15508)
- mcgen.exe (PID: 16196)
- dropper64.exe (PID: 20180)
- Built.exe (PID: 20996)
- microsoft-onedrive.exe (PID: 20660)
- C996.tmp.zx.exe (PID: 21092)
- Built.exe (PID: 21368)
The process drops C-runtime libraries
- sk.exe (PID: 6684)
- Launcher_Start.exe (PID: 9404)
- mcgen.exe (PID: 14080)
- mcgen.exe (PID: 16096)
- Built.exe (PID: 20996)
- C996.tmp.zx.exe (PID: 21092)
Read disk information to detect sandboxing environments
- WinDrive-f4855f59e0.exe (PID: 6860)
- gem2.exe (PID: 6704)
Script adds exclusion process to Windows Defender
- WinDrive-f4855f59e0.exe (PID: 6860)
Script adds exclusion extension to Windows Defender
- WinDrive-f4855f59e0.exe (PID: 6860)
- onedrive.exe (PID: 21100)
- vsrumanlxdbr.exe (PID: 18396)
Starts POWERSHELL.EXE for commands execution
- WinDrive-f4855f59e0.exe (PID: 6860)
- johnmartin.exe (PID: 4472)
- LummaC2.exe (PID: 4592)
- cmd.exe (PID: 16372)
- cmd.exe (PID: 16380)
- cmd.exe (PID: 16952)
- cmd.exe (PID: 14816)
- cmd.exe (PID: 15612)
- cmd.exe (PID: 19844)
- cmd.exe (PID: 18808)
- microsoft-onedrive.exe (PID: 20660)
- cmd.exe (PID: 20464)
- cmd.exe (PID: 19784)
- cmd.exe (PID: 15948)
- cmd.exe (PID: 21344)
- onedrive.exe (PID: 21100)
- cmd.exe (PID: 18544)
- cmd.exe (PID: 21604)
- cmd.exe (PID: 21892)
- cmd.exe (PID: 19672)
- vsrumanlxdbr.exe (PID: 18396)
- cmd.exe (PID: 21792)
Starts a Microsoft application from unusual location
- gem1.exe (PID: 7140)
- gem1.exe (PID: 6320)
- gem1.exe (PID: 6384)
- gem1.exe (PID: 6432)
- gem1.exe (PID: 4244)
- none.exe (PID: 7900)
- r3P25.exe (PID: 7944)
- b2l20.exe (PID: 6224)
- mcgen.exe (PID: 14080)
- mcgen.exe (PID: 14340)
- mcgen.exe (PID: 16096)
- mcgen.exe (PID: 16196)
- diskutil.exe (PID: 15508)
- dropper64.exe (PID: 20180)
- Built.exe (PID: 20996)
- Built.exe (PID: 21368)
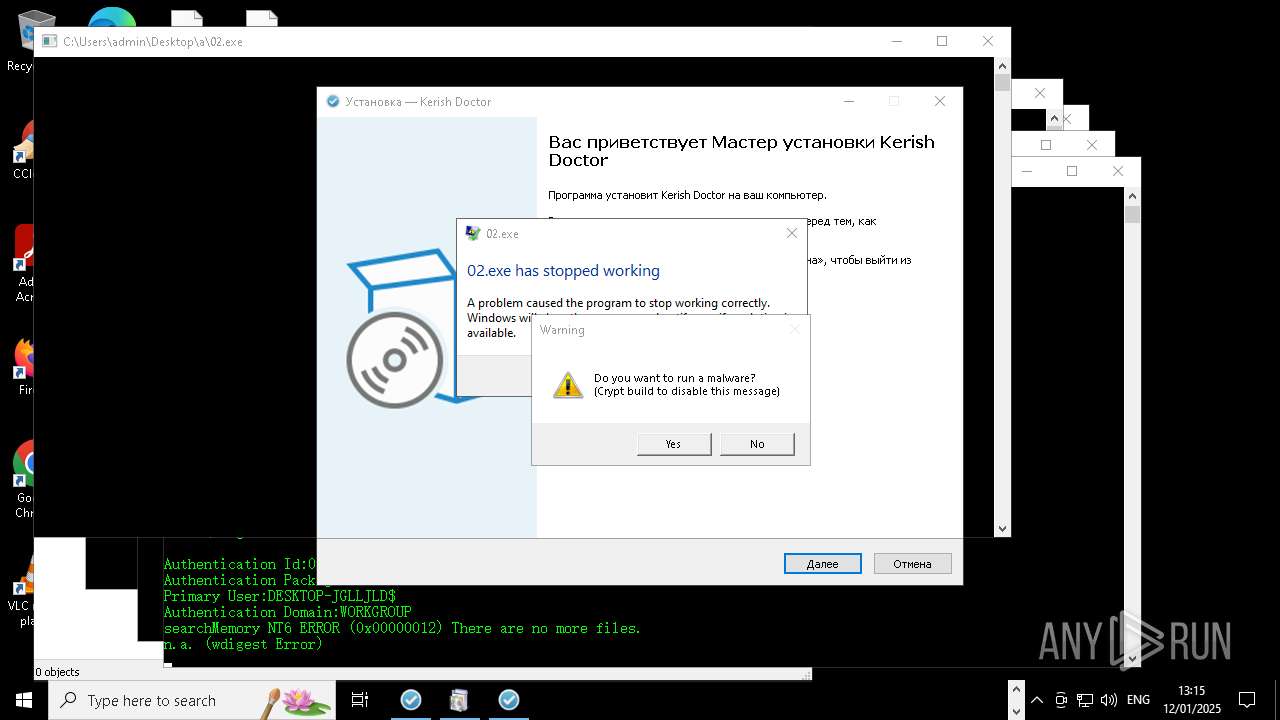
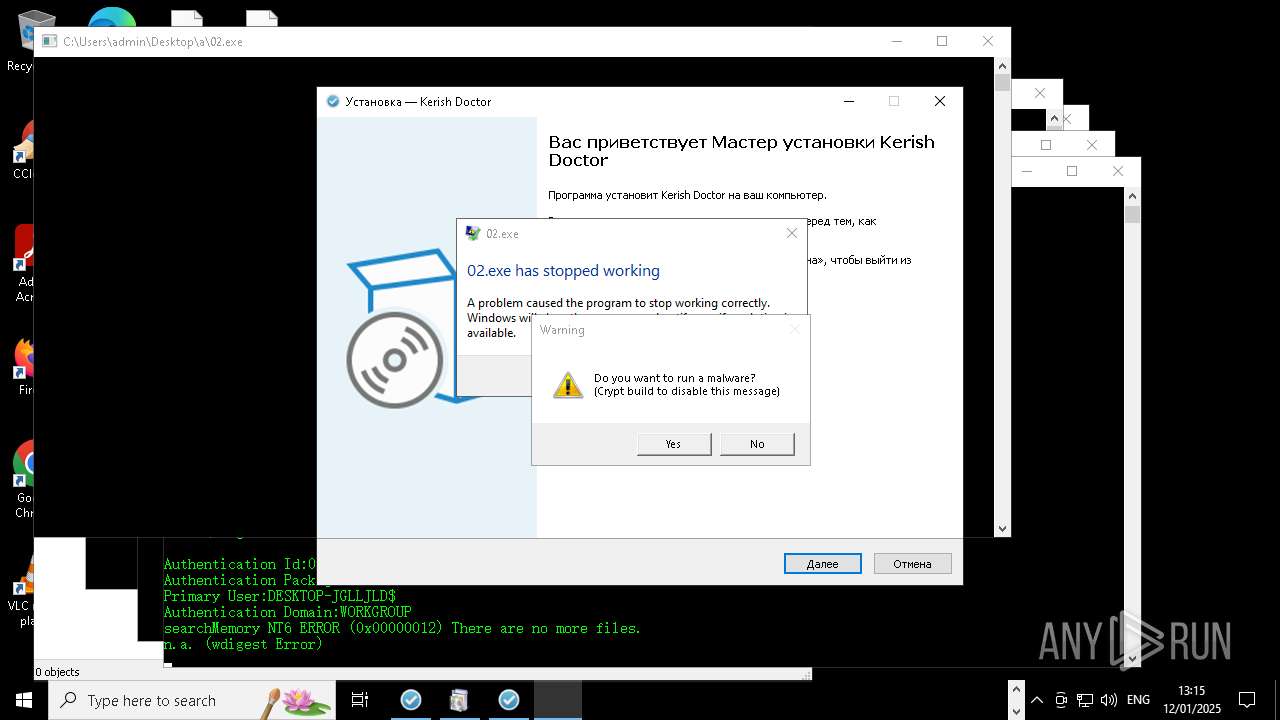
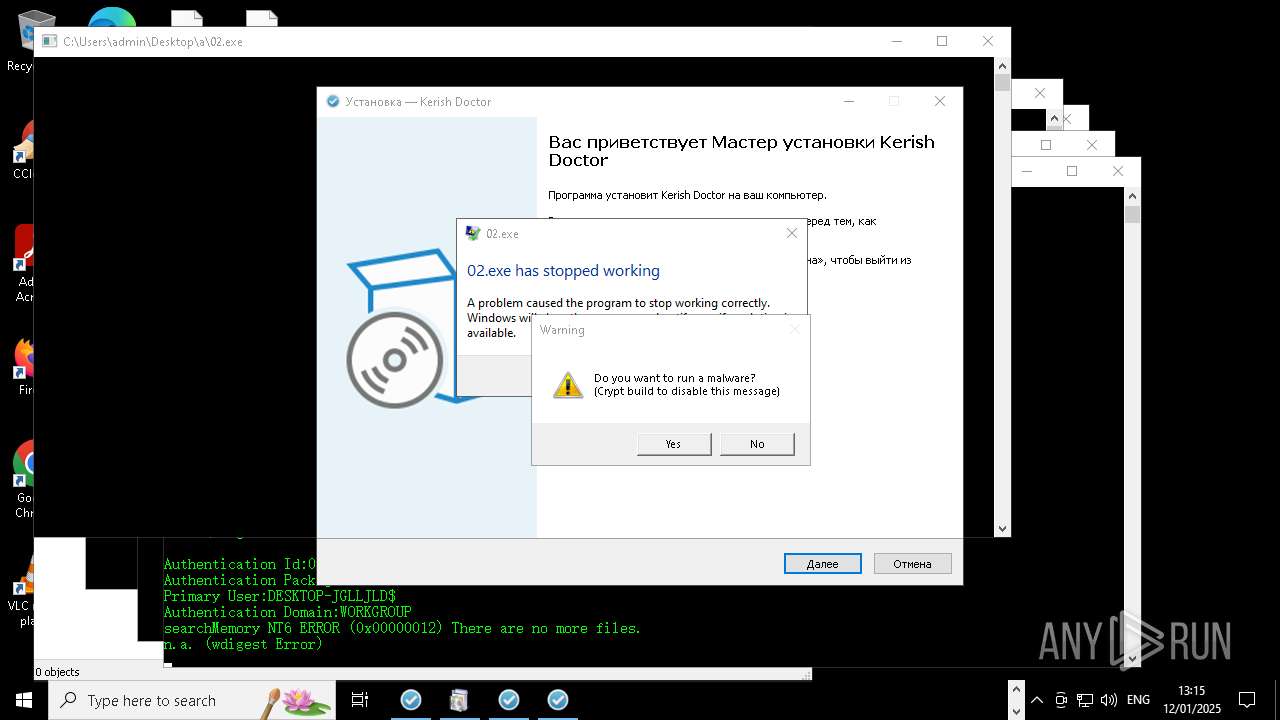
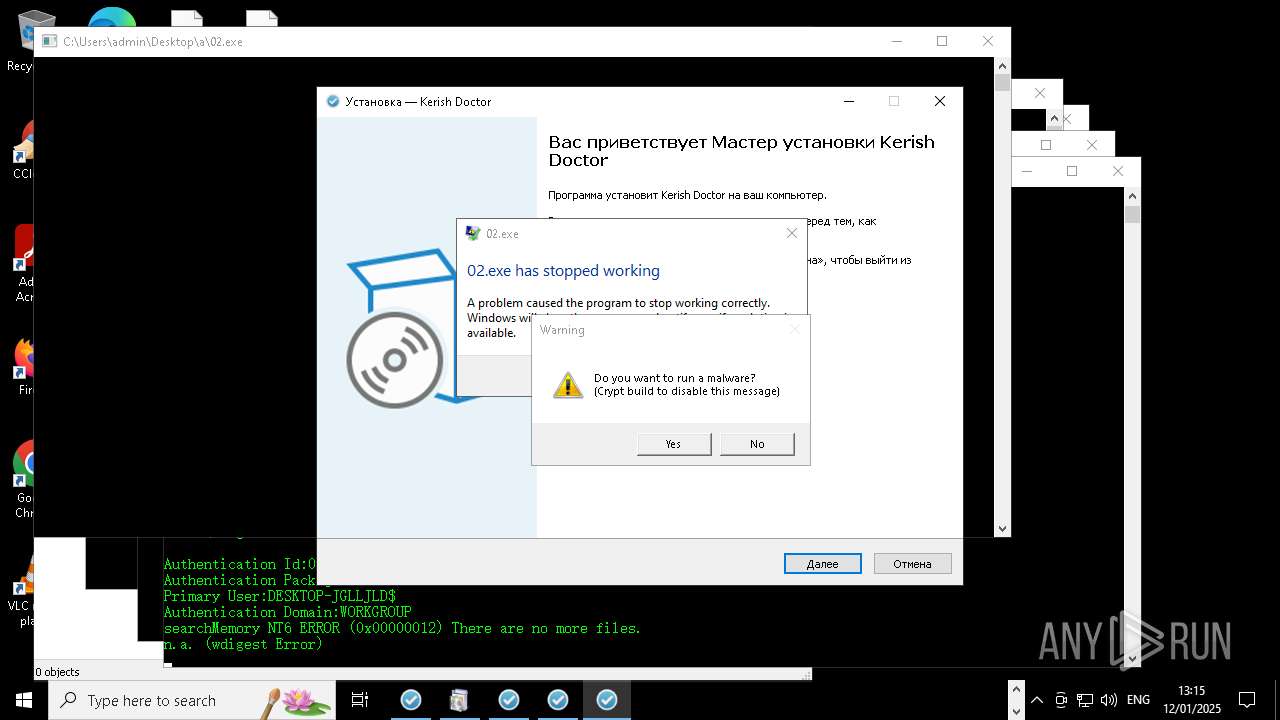
Executes application which crashes
- whiteshadow123.exe (PID: 5864)
- gem1.exe (PID: 7140)
- gem1.exe (PID: 6320)
- 00.exe (PID: 8740)
- 02.exe (PID: 4280)
- 696969.exe (PID: 9580)
- 01.exe (PID: 9528)
- 4e452a47dd.exe (PID: 9076)
- TPB-1.exe (PID: 7216)
Application launched itself
- gem1.exe (PID: 7140)
- gem1.exe (PID: 6320)
- sk.exe (PID: 6684)
- drop1.exe (PID: 10072)
- drop1.exe (PID: 5840)
- cmd.exe (PID: 13688)
- TPB-1.exe (PID: 7216)
- mcgen.exe (PID: 14080)
- mcgen.exe (PID: 16096)
- Built.exe (PID: 20996)
- C996.tmp.zx.exe (PID: 21092)
The process connected to a server suspected of theft
- gem1.exe (PID: 6432)
The process executes Powershell scripts
- johnmartin.exe (PID: 4472)
- LummaC2.exe (PID: 4592)
Found regular expressions for crypto-addresses (YARA)
- service123.exe (PID: 6900)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 7024)
- 64.exe (PID: 9820)
- IMG001.exe (PID: 10860)
- Crawl.exe (PID: 6448)
- IMG001.exe (PID: 11028)
- 3148931435.exe (PID: 12056)
- 1346722953.exe (PID: 8832)
- cmd.exe (PID: 13688)
- NOTallowedtocrypt.exe (PID: 15344)
- 76y5trfed675ytg.exe (PID: 13792)
- mcgen.exe (PID: 14340)
- seksiak.exe (PID: 8992)
- mcgen.exe (PID: 16196)
- 2klz.exe (PID: 16248)
- Client.exe (PID: 12836)
- seksiak.exe (PID: 12372)
- 2klz.exe (PID: 16300)
- Client.exe (PID: 13236)
- windows 3543.exe (PID: 9860)
- seksiak.exe (PID: 18232)
- 2klz.exe (PID: 14792)
- Client.exe (PID: 16956)
- seksiak.exe (PID: 9200)
- 2klz.exe (PID: 13192)
- seksiak.exe (PID: 16664)
- Client.exe (PID: 18068)
- 2klz.exe (PID: 18148)
- seksiak.exe (PID: 16964)
- Client.exe (PID: 16696)
- 2klz.exe (PID: 14744)
- seksiak.exe (PID: 18736)
- Client.exe (PID: 18760)
- 2klz.exe (PID: 15368)
- Client.exe (PID: 18900)
- seksiak.exe (PID: 17988)
- Coc%20Coc.exe (PID: 18552)
- 2klz.exe (PID: 18872)
- Google%20Chrome.exe (PID: 15892)
- Client.exe (PID: 17124)
- Bootxr.exe (PID: 19728)
- seksiak.exe (PID: 19252)
- 2klz.exe (PID: 17152)
- Client.exe (PID: 21012)
- seksiak.exe (PID: 20952)
- Built.exe (PID: 21368)
- 2klz.exe (PID: 9012)
- Client.exe (PID: 21464)
- seksiak.exe (PID: 18164)
- onedrive.exe (PID: 21100)
- 2klz.exe (PID: 17348)
- seksiak.exe (PID: 22292)
- Client.exe (PID: 22048)
- vsrumanlxdbr.exe (PID: 18396)
- 2klz.exe (PID: 15024)
- Client.exe (PID: 21220)
- seksiak.exe (PID: 21740)
- 2klz.exe (PID: 22340)
- seksiak.exe (PID: 21896)
- Client.exe (PID: 17816)
- 2klz.exe (PID: 19744)
- seksiak.exe (PID: 19004)
- Client.exe (PID: 19488)
- 2klz.exe (PID: 21596)
- Client.exe (PID: 22364)
- seksiak.exe (PID: 18624)
- 2klz.exe (PID: 20568)
- Client.exe (PID: 17332)
- seksiak.exe (PID: 8992)
- 2klz.exe (PID: 17576)
- Client.exe (PID: 13960)
- seksiak.exe (PID: 4304)
Uses powercfg.exe to modify the power settings
- svchost.exe (PID: 7024)
- cmd.exe (PID: 8708)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2512)
- cmd.exe (PID: 6952)
- cmd.exe (PID: 10884)
- cmd.exe (PID: 12148)
- cmd.exe (PID: 9304)
- 3070213606.exe (PID: 6700)
- cmd.exe (PID: 12684)
- cmd.exe (PID: 13260)
- cmd.exe (PID: 14304)
- cmd.exe (PID: 14956)
- cmd.exe (PID: 15316)
- cmd.exe (PID: 15464)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 6540)
- cmd.exe (PID: 6492)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 2216)
Uses WMIC.EXE to obtain physical disk drive information
- svchost.exe (PID: 7024)
The process creates files with name similar to system file names
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- Launcher_Start.exe (PID: 9404)
- server.exe (PID: 14200)
The process executes via Task Scheduler
- service123.exe (PID: 6528)
- skotes.exe (PID: 3556)
- service123.exe (PID: 10320)
- skotes.exe (PID: 7656)
- service123.exe (PID: 3972)
- skotes.exe (PID: 12508)
- service123.exe (PID: 13304)
- skotes.exe (PID: 13244)
- service123.exe (PID: 12888)
- service123.exe (PID: 16884)
- skotes.exe (PID: 16724)
- service123.exe (PID: 13892)
- skotes.exe (PID: 15448)
- skotes.exe (PID: 20688)
- service123.exe (PID: 20836)
- skotes.exe (PID: 22060)
- service123.exe (PID: 19780)
- skotes.exe (PID: 21316)
Starts itself from another location
- 2018910798.exe (PID: 6416)
- 1X48r0.exe (PID: 8156)
- JJSPLOIT.V2.exe (PID: 9724)
- IMG001.exe (PID: 10860)
- 3070213606.exe (PID: 6700)
- testingg.exe (PID: 15096)
- NOTallowedtocrypt.exe (PID: 15344)
- Server.exe (PID: 15292)
- 2klz.exe (PID: 15808)
- diskutil.exe (PID: 15508)
- Test2.exe (PID: 16128)
- OneDrive.exe (PID: 15196)
- sysnldcvmr.exe (PID: 2792)
Loads Python modules
- sk.exe (PID: 6584)
- Built.exe (PID: 21368)
- C996.tmp.zx.exe (PID: 18152)
Crypto Currency Mining Activity Detected
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- svchost.exe (PID: 2192)
- 1724930485.exe (PID: 6180)
- powershell.exe (PID: 19952)
Drops a system driver (possible attempt to evade defenses)
- chrtrome22.exe (PID: 6700)
- vsrumanlxdbr.exe (PID: 18396)
Extracts files to a directory (POWERSHELL)
- chrtrome22.exe (PID: 6700)
Checks a user's role membership (POWERSHELL)
- Customer.exe (PID: 7968)
Reads the BIOS version
- skotes.exe (PID: 6372)
- 1X48r0.exe (PID: 8156)
- 2D8630.exe (PID: 4912)
- skotes.exe (PID: 3556)
- SCLKFNF21ARIHQ5RV63UYR.exe (PID: 10568)
- KQ2ZHT79N1C50FF5FGMYRJFW3BR4.exe (PID: 9412)
- 3t57j.exe (PID: 10248)
- skotes.exe (PID: 16724)
- skotes.exe (PID: 15448)
- skotes.exe (PID: 20688)
- skotes.exe (PID: 22060)
- skotes.exe (PID: 21316)
The process checks if it is being run in the virtual environment
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- Server1.exe (PID: 8340)
- server.exe (PID: 14200)
Creates file in the systems drive root
- explorer.exe (PID: 4488)
- IMG001.exe (PID: 11028)
- server.exe (PID: 14200)
Uses NETSH.EXE to add a firewall rule or allowed programs
- Server1.exe (PID: 8340)
- server.exe (PID: 14200)
- server.exe (PID: 9196)
Windows Defender mutex has been found
- 696969.exe (PID: 9580)
- 3t57j.exe (PID: 10248)
- SCLKFNF21ARIHQ5RV63UYR.exe (PID: 10568)
- daytjhasdawd.exe (PID: 18708)
Probably fake Windows Update file has been dropped
- JJSPLOIT.V2.exe (PID: 9724)
- server.exe (PID: 14200)
Probably fake Windows Update
- windows 3543.exe (PID: 9860)
- windows 3543.exe (PID: 17012)
Contacting a server suspected of hosting an Exploit Kit
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
Starts application with an unusual extension
- cmd.exe (PID: 9816)
- cmd.exe (PID: 15500)
- cmd.exe (PID: 16088)
- cmd.exe (PID: 12516)
- cmd.exe (PID: 16716)
- cmd.exe (PID: 14748)
- cmd.exe (PID: 16936)
- cmd.exe (PID: 17700)
- cmd.exe (PID: 16620)
- cmd.exe (PID: 18336)
- cmd.exe (PID: 9344)
- cmd.exe (PID: 15868)
- cmd.exe (PID: 17612)
- cmd.exe (PID: 15400)
- cmd.exe (PID: 15136)
- cmd.exe (PID: 17388)
- cmd.exe (PID: 14592)
- cmd.exe (PID: 15468)
- cmd.exe (PID: 17208)
- cmd.exe (PID: 16344)
- cmd.exe (PID: 6180)
- cmd.exe (PID: 13760)
- cmd.exe (PID: 16424)
- cmd.exe (PID: 14584)
- cmd.exe (PID: 15248)
- cmd.exe (PID: 19016)
- cmd.exe (PID: 19100)
- cmd.exe (PID: 18956)
- cmd.exe (PID: 19412)
- cmd.exe (PID: 19396)
- cmd.exe (PID: 2576)
- cmd.exe (PID: 19748)
- cmd.exe (PID: 19736)
- cmd.exe (PID: 21024)
- cmd.exe (PID: 19636)
- cmd.exe (PID: 18568)
- cmd.exe (PID: 21684)
- cmd.exe (PID: 19864)
- cmd.exe (PID: 17288)
- cmd.exe (PID: 11736)
- cmd.exe (PID: 17256)
- cmd.exe (PID: 21668)
- cmd.exe (PID: 22436)
- cmd.exe (PID: 20264)
- cmd.exe (PID: 21476)
- cmd.exe (PID: 17584)
- cmd.exe (PID: 19672)
- cmd.exe (PID: 6448)
- cmd.exe (PID: 20960)
- cmd.exe (PID: 20348)
- cmd.exe (PID: 15860)
- cmd.exe (PID: 12764)
- cmd.exe (PID: 21088)
- cmd.exe (PID: 5724)
- cmd.exe (PID: 22076)
- cmd.exe (PID: 15880)
- cmd.exe (PID: 19120)
- cmd.exe (PID: 20664)
- cmd.exe (PID: 19700)
- cmd.exe (PID: 14452)
- cmd.exe (PID: 8708)
- cmd.exe (PID: 19164)
- cmd.exe (PID: 18756)
- cmd.exe (PID: 19516)
- cmd.exe (PID: 19740)
- cmd.exe (PID: 15412)
Write to the desktop.ini file (may be used to cloak folders)
- Crawl.exe (PID: 6448)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 10904)
- cmd.exe (PID: 11148)
Hides command output
- cmd.exe (PID: 10984)
- cmd.exe (PID: 13688)
- cmd.exe (PID: 6680)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 10984)
- cmd.exe (PID: 15500)
- cmd.exe (PID: 16088)
- cmd.exe (PID: 12516)
- cmd.exe (PID: 16716)
- cmd.exe (PID: 18336)
- cmd.exe (PID: 15400)
- cmd.exe (PID: 17612)
- cmd.exe (PID: 15136)
- cmd.exe (PID: 17388)
- cmd.exe (PID: 14592)
- cmd.exe (PID: 15468)
- cmd.exe (PID: 17208)
- cmd.exe (PID: 6180)
- cmd.exe (PID: 16344)
- cmd.exe (PID: 13760)
- cmd.exe (PID: 16424)
- cmd.exe (PID: 14584)
- cmd.exe (PID: 15248)
- cmd.exe (PID: 19016)
- cmd.exe (PID: 19100)
- cmd.exe (PID: 18956)
- cmd.exe (PID: 19412)
- cmd.exe (PID: 19396)
- cmd.exe (PID: 2576)
- cmd.exe (PID: 19736)
- cmd.exe (PID: 19748)
- cmd.exe (PID: 21024)
- cmd.exe (PID: 18568)
- cmd.exe (PID: 19636)
- cmd.exe (PID: 19864)
- cmd.exe (PID: 17256)
- cmd.exe (PID: 20264)
- cmd.exe (PID: 17584)
- cmd.exe (PID: 19672)
- cmd.exe (PID: 6448)
- cmd.exe (PID: 6680)
- cmd.exe (PID: 20960)
- cmd.exe (PID: 15860)
- cmd.exe (PID: 20348)
- cmd.exe (PID: 12764)
- cmd.exe (PID: 5724)
- cmd.exe (PID: 21088)
- cmd.exe (PID: 22076)
- cmd.exe (PID: 15880)
- cmd.exe (PID: 19120)
- cmd.exe (PID: 20664)
- cmd.exe (PID: 19700)
- cmd.exe (PID: 14452)
- cmd.exe (PID: 8708)
- cmd.exe (PID: 18756)
- cmd.exe (PID: 19164)
- cmd.exe (PID: 19516)
- cmd.exe (PID: 19740)
- cmd.exe (PID: 15412)
Working with threads in the GNU C Compiler (GCC) libraries related mutex has been found
- tftp.exe (PID: 8804)
- tftp.exe (PID: 11240)
Reads the Windows owner or organization settings
- Kerish_Doctor_2023.tmp (PID: 10664)
- Kerish_Doctor_Windows_XP.tmp (PID: 6096)
- Kerish_Doctor_Windows.tmp (PID: 12092)
- Kerish_Doctor_2017.tmp (PID: 12820)
Windows service management via SC.EXE
- sc.exe (PID: 12212)
- sc.exe (PID: 10748)
- sc.exe (PID: 6448)
- sc.exe (PID: 22376)
Starts SC.EXE for service management
- cmd.exe (PID: 12148)
- cmd.exe (PID: 9304)
- onedrive.exe (PID: 21100)
Starts NET.EXE for network exploration
- cmd.exe (PID: 13732)
Process creates executable files without a name
- Synaptics.exe (PID: 4952)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- .exe (PID: 13588)
Changes default file association
- reg.exe (PID: 13216)
Found strings related to reading or modifying Windows Defender settings
- mcgen.exe (PID: 14340)
- mcgen.exe (PID: 16196)
- Built.exe (PID: 21368)
Uses WEVTUTIL.EXE to query events from a log or log file
- cmd.exe (PID: 9092)
- cmd.exe (PID: 16124)
Executing commands from a ".bat" file
- seksiak.exe (PID: 8992)
- 2klz.exe (PID: 16248)
- Client.exe (PID: 12836)
- seksiak.exe (PID: 12372)
- 2klz.exe (PID: 16300)
- Client.exe (PID: 13236)
- windows 3543.exe (PID: 9860)
- seksiak.exe (PID: 18232)
- 2klz.exe (PID: 14792)
- Client.exe (PID: 16956)
- seksiak.exe (PID: 9200)
- 2klz.exe (PID: 13192)
- seksiak.exe (PID: 16664)
- Client.exe (PID: 18068)
- 2klz.exe (PID: 18148)
- seksiak.exe (PID: 16964)
- Client.exe (PID: 16696)
- 2klz.exe (PID: 14744)
- seksiak.exe (PID: 18736)
- Client.exe (PID: 18760)
- 2klz.exe (PID: 15368)
- Client.exe (PID: 18900)
- seksiak.exe (PID: 17988)
- 2klz.exe (PID: 18872)
- Coc%20Coc.exe (PID: 18552)
- Google%20Chrome.exe (PID: 15892)
- Client.exe (PID: 17124)
- seksiak.exe (PID: 19252)
- 2klz.exe (PID: 17152)
- Client.exe (PID: 21012)
- seksiak.exe (PID: 20952)
- 2klz.exe (PID: 9012)
- Client.exe (PID: 21464)
- seksiak.exe (PID: 18164)
- 2klz.exe (PID: 17348)
- seksiak.exe (PID: 22292)
- Client.exe (PID: 22048)
- 2klz.exe (PID: 15024)
- Client.exe (PID: 21220)
- seksiak.exe (PID: 21740)
- 2klz.exe (PID: 22340)
- Client.exe (PID: 17816)
- seksiak.exe (PID: 21896)
- 2klz.exe (PID: 19744)
- Client.exe (PID: 19488)
- seksiak.exe (PID: 19004)
- 2klz.exe (PID: 21596)
- seksiak.exe (PID: 18624)
- Client.exe (PID: 22364)
- 2klz.exe (PID: 20568)
- Client.exe (PID: 17332)
- seksiak.exe (PID: 8992)
- 2klz.exe (PID: 17576)
- Client.exe (PID: 13960)
- seksiak.exe (PID: 4304)
Get information on the list of running processes
- mcgen.exe (PID: 16196)
- cmd.exe (PID: 15416)
- cmd.exe (PID: 17308)
- cmd.exe (PID: 17268)
- cmd.exe (PID: 16496)
- Built.exe (PID: 21368)
- cmd.exe (PID: 19008)
- cmd.exe (PID: 17828)
- cmd.exe (PID: 21644)
- cmd.exe (PID: 21468)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 15452)
- cmd.exe (PID: 17396)
- cmd.exe (PID: 20496)
- cmd.exe (PID: 21576)
- cmd.exe (PID: 20124)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 16380)
- cmd.exe (PID: 15948)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 16372)
- cmd.exe (PID: 16952)
- cmd.exe (PID: 19844)
- cmd.exe (PID: 19784)
- onedrive.exe (PID: 21100)
- cmd.exe (PID: 18544)
- vsrumanlxdbr.exe (PID: 18396)
Script disables Windows Defender's IPS
- cmd.exe (PID: 16380)
- cmd.exe (PID: 15948)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 16056)
- WMIC.exe (PID: 19560)
- WMIC.exe (PID: 18756)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 14016)
- cmd.exe (PID: 15712)
- cmd.exe (PID: 16400)
- cmd.exe (PID: 17812)
- cmd.exe (PID: 18024)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 3732)
- WMIC.exe (PID: 16456)
- WMIC.exe (PID: 12384)
- WMIC.exe (PID: 21464)
- WMIC.exe (PID: 19880)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 16900)
- cmd.exe (PID: 11892)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 14708)
- cmd.exe (PID: 21732)
Base64-obfuscated command line is found
- cmd.exe (PID: 14816)
- microsoft-onedrive.exe (PID: 20660)
- cmd.exe (PID: 21892)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 14816)
- cmd.exe (PID: 21892)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 14816)
- microsoft-onedrive.exe (PID: 20660)
- cmd.exe (PID: 21892)
The executable file from the user directory is run by the CMD process
- 2klz.exe (PID: 16300)
- Client.exe (PID: 13236)
- 2klz.exe (PID: 14792)
- Client.exe (PID: 16956)
- windows 3543.exe (PID: 17012)
- Client.exe (PID: 18068)
- 2klz.exe (PID: 13192)
- 2klz.exe (PID: 18148)
- Client.exe (PID: 16696)
- 2klz.exe (PID: 14744)
- Client.exe (PID: 18760)
- 2klz.exe (PID: 15368)
- Client.exe (PID: 18900)
- 2klz.exe (PID: 18872)
- portable_util.exe (PID: 14412)
- Client.exe (PID: 17124)
- 2klz.exe (PID: 17152)
- Client.exe (PID: 21012)
- 2klz.exe (PID: 9012)
- rar.exe (PID: 15624)
- Client.exe (PID: 21464)
- 2klz.exe (PID: 17348)
- Client.exe (PID: 22048)
- 2klz.exe (PID: 15024)
- Client.exe (PID: 21220)
- 2klz.exe (PID: 22340)
- Client.exe (PID: 17816)
- 2klz.exe (PID: 19744)
- Client.exe (PID: 19488)
- 2klz.exe (PID: 21596)
- Client.exe (PID: 22364)
- 2klz.exe (PID: 20568)
- Client.exe (PID: 17332)
- 2klz.exe (PID: 17576)
- Client.exe (PID: 13960)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 14788)
- cmd.exe (PID: 21780)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 15048)
- WMIC.exe (PID: 22172)
CSC.EXE is used to compile C# code
- csc.exe (PID: 17860)
- csc.exe (PID: 15868)
Captures screenshot (POWERSHELL)
- powershell.exe (PID: 17324)
- powershell.exe (PID: 22324)
The process hide an interactive prompt from the user
- cmd.exe (PID: 19844)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- ghjaedjgaw.exe (PID: 19912)
- mcgen.exe (PID: 16196)
Connects to FTP
- tftp.exe (PID: 11240)
Downloads file from URI via Powershell
- powershell.exe (PID: 19952)
Found IP address in command line
- powershell.exe (PID: 19952)
Manipulates environment variables
- powershell.exe (PID: 17656)
- powershell.exe (PID: 15868)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 22028)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 22448)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 18988)
Creates a new Windows service
- sc.exe (PID: 21604)
Stops a currently running service
- sc.exe (PID: 21744)
Executes as Windows Service
- vsrumanlxdbr.exe (PID: 18396)
Process uninstalls Windows update
- wusa.exe (PID: 19216)
- wusa.exe (PID: 15860)
INFO
The sample compiled with turkish language support
- New Text Document mod.exe.bin.exe (PID: 624)
- Synaptics.exe (PID: 4952)
- 293637911.exe (PID: 7392)
Reads the computer name
- New Text Document mod.exe.bin.exe (PID: 624)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- Synaptics.exe (PID: 4952)
- whiteshadow123.exe (PID: 5864)
- whiteshadow.exe (PID: 2992)
- minimal.exe (PID: 4320)
- johnmartin.exe (PID: 4472)
- sk.exe (PID: 6684)
- gem2.exe (PID: 6704)
- gem1.exe (PID: 7140)
- gem1.exe (PID: 4244)
- gem1.exe (PID: 6320)
- gem1.exe (PID: 6432)
- WinDrive-f4855f59e0.exe (PID: 6860)
- @bebanrti%20(1).exe (PID: 6896)
- @bebanrti%20(1).exe (PID: 6460)
- utkin.exe (PID: 68)
- elm.exe (PID: 6372)
- elm.exe (PID: 6324)
- utkin.exe (PID: 6164)
- curl.exe (PID: 6612)
- kanew.exe (PID: 7008)
- curl.exe (PID: 5992)
- kanew.exe (PID: 6184)
- hdont.exe (PID: 4708)
- hdont.exe (PID: 5572)
- markiz.exe (PID: 6656)
- markiz.exe (PID: 6564)
- LummaC2.exe (PID: 4592)
- tmx.exe (PID: 6456)
- 32.exe (PID: 4912)
- Client.exe (PID: 7108)
- svhost.exe (PID: 6892)
- sk.exe (PID: 6584)
- BitLockerToGo.exe (PID: 2940)
- win.exe (PID: 2280)
- mimikatz.exe (PID: 6348)
- sysnldcvmr.exe (PID: 2792)
- BitLockerToGo.exe (PID: 6752)
- xmrig.exe (PID: 6316)
- Fixer.exe (PID: 4336)
- chrtrome22.exe (PID: 6700)
- Client-built.exe (PID: 6976)
- 1724930485.exe (PID: 6180)
- 1.exe (PID: 7552)
- xmrig.exe (PID: 7620)
- build1.exe (PID: 7792)
- Customer.exe (PID: 7968)
- Steanings.exe (PID: 7748)
- AsyncClientGK.exe (PID: 8048)
- RuntimeBroker.exe (PID: 7216)
- 1X48r0.exe (PID: 8156)
- 2D8630.exe (PID: 4912)
- skotes.exe (PID: 6372)
- Server1.exe (PID: 8340)
- uu.exe (PID: 8280)
- TEST.exe (PID: 8624)
- windows 3543.exe (PID: 9860)
- drop1.exe (PID: 10156)
- drop1.exe (PID: 7684)
- 00.exe (PID: 8740)
- 02.exe (PID: 4280)
- sdggwsdgdrwgrwgrwgrwgrw.exe (PID: 9812)
- SCLKFNF21ARIHQ5RV63UYR.exe (PID: 10568)
- 3t57j.exe (PID: 10248)
- Kerish_Doctor_2022.tmp (PID: 3840)
- Kerish_Doctor_2022.tmp (PID: 10296)
- Kerish_Doctor_2023.tmp (PID: 10448)
- Kerish_Doctor_2023.tmp (PID: 10664)
- Kerish_Doctor.tmp (PID: 8552)
- Kerish_Doctor.exe (PID: 11356)
- Kerish_Doctor.tmp (PID: 11388)
- 3148931435.exe (PID: 12056)
- 1346722953.exe (PID: 8832)
- Kerish_Doctor_2021.tmp (PID: 12132)
- Kerish_Doctor_Windows_8.2.tmp (PID: 13072)
- Kerish_Doctor_Windows_XP.tmp (PID: 12992)
- Kerish_Doctor_Windows_8.tmp (PID: 12776)
- Kerish_Doctor_Windows_8.tmp (PID: 12572)
- Kerish_Doctor_2017.tmp (PID: 12820)
- TPB-1.exe (PID: 11640)
- NOTallowedtocrypt.exe (PID: 15344)
- Server.exe (PID: 15292)
- mcgen.exe (PID: 14080)
- mcgen.exe (PID: 16096)
- 2klz.exe (PID: 16248)
- server.exe (PID: 9196)
- mcgen.exe (PID: 16196)
- diskutil.exe (PID: 15508)
- diskutil.exe (PID: 16244)
- Gorebox%20ModMenu%201.2.0.exe (PID: 15864)
- seksiak.exe (PID: 12372)
- OneDrive.exe (PID: 15196)
- kthiokadjg.exe (PID: 16580)
- Onedrive.exe (PID: 16608)
- jrockekcurje.exe (PID: 16908)
- build.exe (PID: 15188)
- Sync.exe (PID: 17484)
- image%20logger.exe (PID: 17592)
- 2klz.exe (PID: 16300)
- toolwin.exe (PID: 14856)
- windows 3543.exe (PID: 17012)
- mode11_UVo6.exe (PID: 15944)
- Client.exe (PID: 18068)
- seksiak.exe (PID: 16664)
- seksiak.exe (PID: 16964)
- Client.exe (PID: 16696)
- seksiak.exe (PID: 18736)
- Client.exe (PID: 18760)
- Java32.exe (PID: 18964)
- cici.exe (PID: 18496)
- AdobePDFReader.exe (PID: 19308)
- seksiak.exe (PID: 17988)
- Client.exe (PID: 18900)
- Coc%20Coc.exe (PID: 18552)
- Client.exe (PID: 17124)
- seksiak.exe (PID: 19252)
- Google%20Chrome.exe (PID: 15892)
- 2klz.exe (PID: 17152)
- microsoft-onedrive.exe (PID: 20660)
- Built.exe (PID: 20996)
- Client.exe (PID: 21012)
- 33.exe (PID: 20532)
- Built.exe (PID: 21368)
- 2klz.exe (PID: 9012)
- Client.exe (PID: 21464)
- MpCmdRun.exe (PID: 15880)
- TrustedInstaller.exe (PID: 22036)
- Client.exe (PID: 22048)
- Client.exe (PID: 21220)
- seksiak.exe (PID: 21740)
- 2klz.exe (PID: 22340)
- Client.exe (PID: 17816)
- 2klz.exe (PID: 19744)
- seksiak.exe (PID: 19004)
- Client.exe (PID: 19488)
- 2klz.exe (PID: 20568)
- Client.exe (PID: 17332)
- seksiak.exe (PID: 8992)
- 2klz.exe (PID: 17576)
- Client.exe (PID: 13960)
Checks supported languages
- New Text Document mod.exe.bin.exe (PID: 624)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- Synaptics.exe (PID: 4952)
- whiteshadow.exe (PID: 2992)
- whiteshadow123.exe (PID: 5864)
- minimal.exe (PID: 4320)
- Set-up.exe (PID: 3812)
- LummaC2.exe (PID: 4592)
- johnmartin.exe (PID: 4472)
- sk.exe (PID: 6684)
- gem2.exe (PID: 6704)
- service123.exe (PID: 6900)
- gem1.exe (PID: 7140)
- gem1.exe (PID: 4244)
- gem1.exe (PID: 6320)
- gem1.exe (PID: 6432)
- WinDrive-f4855f59e0.exe (PID: 6860)
- random.exe (PID: 6768)
- The%20Foundry.exe (PID: 6716)
- @bebanrti%20(1).exe (PID: 6896)
- @bebanrti%20(1).exe (PID: 6460)
- utkin.exe (PID: 68)
- elm.exe (PID: 6372)
- utkin.exe (PID: 6164)
- elm.exe (PID: 6324)
- curl.exe (PID: 6612)
- kanew.exe (PID: 7008)
- curl.exe (PID: 5992)
- kanew.exe (PID: 6184)
- hdont.exe (PID: 5572)
- hdont.exe (PID: 4708)
- markiz.exe (PID: 6656)
- markiz.exe (PID: 6564)
- cbot.exe (PID: 236)
- tmx.exe (PID: 6456)
- Client.exe (PID: 7108)
- 32.exe (PID: 4912)
- 2018910798.exe (PID: 6416)
- svhost.exe (PID: 6892)
- service123.exe (PID: 6528)
- sysnldcvmr.exe (PID: 2792)
- sk.exe (PID: 6584)
- win.exe (PID: 2280)
- mimikatz.exe (PID: 6348)
- BitLockerToGo.exe (PID: 2940)
- BitLockerToGo.exe (PID: 6752)
- 123.exe (PID: 6920)
- xmrig.exe (PID: 6316)
- payload.exe (PID: 5076)
- Fixer.exe (PID: 4336)
- Client-built.exe (PID: 6976)
- 1724930485.exe (PID: 6180)
- 1.exe (PID: 7552)
- xmrig.exe (PID: 7620)
- 3061413023.exe (PID: 7496)
- chrtrome22.exe (PID: 6700)
- build1.exe (PID: 7792)
- Steanings.exe (PID: 7748)
- AsyncClientGK.exe (PID: 8048)
- Customer.exe (PID: 7968)
- 293637911.exe (PID: 7392)
- csc.exe (PID: 8160)
- cvtres.exe (PID: 3888)
- RuntimeBroker.exe (PID: 7216)
- 1X48r0.exe (PID: 8156)
- none.exe (PID: 7900)
- r3P25.exe (PID: 7944)
- b2l20.exe (PID: 6224)
- skotes.exe (PID: 6372)
- 2D8630.exe (PID: 4912)
- uu.exe (PID: 8280)
- Server1.exe (PID: 8340)
- TEST.exe (PID: 8624)
- 4e452a47dd.exe (PID: 9076)
- Crawl.exe (PID: 6448)
- 696969.exe (PID: 9580)
- Launcher_Start.exe (PID: 9404)
- drop1.exe (PID: 10072)
- albt.exe (PID: 9908)
- drop1.exe (PID: 10156)
- wudi.exe (PID: 4676)
- drop1.exe (PID: 7684)
- 00.exe (PID: 8740)
- 64.exe (PID: 9820)
- 02.exe (PID: 4280)
- sdggwsdgdrwgrwgrwgrwgrw.exe (PID: 9812)
- skotes.exe (PID: 3556)
- SCLKFNF21ARIHQ5RV63UYR.exe (PID: 10568)
- service123.exe (PID: 10320)
- KQ2ZHT79N1C50FF5FGMYRJFW3BR4.exe (PID: 9412)
- 3t57j.exe (PID: 10248)
- IMG001.exe (PID: 10860)
- Kerish_Doctor_2022.exe (PID: 6636)
- Kerish_Doctor_2022.tmp (PID: 3840)
- Kerish_Doctor_2022.exe (PID: 10268)
- Kerish_Doctor_2022.tmp (PID: 10296)
- IMG001.exe (PID: 11028)
- tftp.exe (PID: 11240)
- service123.exe (PID: 7980)
- Kerish_Doctor_2023.exe (PID: 7920)
- Kerish_Doctor_2023.tmp (PID: 10448)
- skotes.exe (PID: 7656)
- Kerish_Doctor.exe (PID: 7656)
- Kerish_Doctor.exe (PID: 11356)
- Kerish_Doctor.tmp (PID: 11388)
- service123.exe (PID: 3972)
- 3148931435.exe (PID: 12056)
- 1346722953.exe (PID: 8832)
- Kerish_Doctor_2021.tmp (PID: 12132)
- Kerish_Doctor_2021.exe (PID: 12068)
- 3070213606.exe (PID: 6700)
- winmngrsa.exe (PID: 11164)
- Kerish_Doctor_Windows_8.2.tmp (PID: 13228)
- service123.exe (PID: 13304)
- Kerish_Doctor_Windows_XP.exe (PID: 11716)
- Kerish_Doctor_Windows_8.2.tmp (PID: 13072)
- Kerish_Doctor_Windows_8.tmp (PID: 12776)
- Kerish_Doctor_Windows_8.exe (PID: 12644)
- Kerish_Doctor_Windows_XP.tmp (PID: 12992)
- Kerish_Doctor_Windows.exe (PID: 11544)
- Kerish_Doctor_Windows.exe (PID: 9232)
- Kerish_Doctor_Windows.tmp (PID: 11568)
- Kerish_Doctor_Windows.tmp (PID: 12092)
- Kerish_Doctor_Windows_8.exe (PID: 12952)
- Kerish_Doctor_2017.exe (PID: 13880)
- Kerish_Doctor_2017.tmp (PID: 13900)
- skotes.exe (PID: 13244)
- Kerish_Doctor_2017.tmp (PID: 12820)
- service123.exe (PID: 12888)
- Kerish_Doctor_Windows_Vista.exe (PID: 13372)
- Kerish_Doctor_Windows_Vista.tmp (PID: 13452)
- Kerish_Doctor_Windows_Vista.tmp (PID: 13616)
- .exe (PID: 13588)
- BootstrapperNew.exe (PID: 8104)
- TPB-1.exe (PID: 11640)
- TPB-1.exe (PID: 7216)
- benpolatalemdar.exe (PID: 14568)
- NOTallowedtocrypt.exe (PID: 15344)
- Server.exe (PID: 15292)
- ShellExperienceHost.exe (PID: 13568)
- 76y5trfed675ytg.exe (PID: 13792)
- server.exe (PID: 14200)
- seksiak.exe (PID: 8992)
- mcgen.exe (PID: 14340)
- 2klz.exe (PID: 15808)
- chcp.com (PID: 15912)
- 2klz.exe (PID: 16248)
- mcgen.exe (PID: 16196)
- diskutil.exe (PID: 15508)
- diskutil.exe (PID: 16244)
- Test2.exe (PID: 16128)
- chcp.com (PID: 16220)
- Client.exe (PID: 12836)
- OneDrive.exe (PID: 15196)
- Gorebox%20ModMenu%201.2.0.exe (PID: 15864)
- Onedrive.exe (PID: 16608)
- jrockekcurje.exe (PID: 16908)
- skotes.exe (PID: 16724)
- toolwin.exe (PID: 14856)
- tree.com (PID: 16856)
- build.exe (PID: 15188)
- ytjgjdrthjdw.exe (PID: 16392)
- systempreter.exe (PID: 13344)
- 2klz.exe (PID: 16300)
- Sync.exe (PID: 17484)
- tree.com (PID: 17576)
- image%20logger.exe (PID: 17592)
- tree.com (PID: 18120)
- tree.com (PID: 14188)
- csc.exe (PID: 17860)
- chcp.com (PID: 17820)
- seksiak.exe (PID: 18232)
- Client.exe (PID: 13236)
- chcp.com (PID: 15492)
- chcp.com (PID: 16344)
- Client.exe (PID: 16956)
- windows 3543.exe (PID: 17012)
- Loader.exe (PID: 15480)
- seksiak.exe (PID: 9200)
- chcp.com (PID: 16920)
- 2621933628.exe (PID: 8764)
- chcp.com (PID: 16532)
- chcp.com (PID: 12036)
- mode11_UVo6.exe (PID: 15944)
- Client.exe (PID: 18068)
- chcp.com (PID: 10032)
- 2klz.exe (PID: 18148)
- mode11_AKUh.exe (PID: 15388)
- skotes.exe (PID: 15448)
- chcp.com (PID: 17692)
- seksiak.exe (PID: 16964)
- mode11_N1Fz.exe (PID: 16932)
- chcp.com (PID: 9344)
- 2klz.exe (PID: 14744)
- mode11_buqd.exe (PID: 18612)
- seksiak.exe (PID: 18736)
- Client.exe (PID: 18760)
- image.exe (PID: 18824)
- Java32.exe (PID: 18964)
- XClient.exe (PID: 19052)
- AdobePDFReader.exe (PID: 19308)
- 2klz.exe (PID: 15368)
- dw20.exe (PID: 18872)
- chcp.com (PID: 19184)
- chcp.com (PID: 19168)
- vnc.exe (PID: 19348)
- Client.exe (PID: 18900)
- seksiak.exe (PID: 17988)
- chcp.com (PID: 15728)
- Coc%20Coc.exe (PID: 18552)
- chcp.com (PID: 15676)
- portable_util.exe (PID: 14412)
- Client.exe (PID: 17124)
- winvnc.exe (PID: 19128)
- seksiak.exe (PID: 19252)
- Bootxr.exe (PID: 19728)
- chcp.com (PID: 19896)
- ghjaedjgaw.exe (PID: 19912)
- ioc.exe (PID: 20100)
- dropper64.exe (PID: 20180)
- skotes.exe (PID: 20688)
- microsoft-onedrive.exe (PID: 20660)
- Client.exe (PID: 21012)
- onedrive.exe (PID: 21100)
- 33.exe (PID: 20532)
- C996.tmp.zx.exe (PID: 18152)
- tcoin.exe (PID: 20876)
- Built.exe (PID: 21368)
- 2klz.exe (PID: 9012)
- seksiak.exe (PID: 18164)
- Client.exe (PID: 21464)
- tree.com (PID: 22396)
- chcp.com (PID: 22436)
- tree.com (PID: 20804)
- chcp.com (PID: 21296)
- tree.com (PID: 17680)
- TrustedInstaller.exe (PID: 22036)
- tree.com (PID: 20960)
- service123.exe (PID: 20836)
- csc.exe (PID: 15868)
- vsrumanlxdbr.exe (PID: 18396)
- 2klz.exe (PID: 17348)
- chcp.com (PID: 17108)
- seksiak.exe (PID: 22292)
- Client.exe (PID: 22048)
- chcp.com (PID: 19744)
- chcp.com (PID: 21168)
- 2klz.exe (PID: 15024)
- Client.exe (PID: 21220)
- seksiak.exe (PID: 21740)
- skotes.exe (PID: 22060)
- chcp.com (PID: 22196)
- 2klz.exe (PID: 22340)
- chcp.com (PID: 14160)
- seksiak.exe (PID: 21896)
- Client.exe (PID: 17816)
- chcp.com (PID: 21028)
- chcp.com (PID: 16724)
- 2klz.exe (PID: 19744)
- Client.exe (PID: 19488)
- 2klz.exe (PID: 21596)
- chcp.com (PID: 22132)
- Client.exe (PID: 22364)
- seksiak.exe (PID: 18624)
- chcp.com (PID: 22252)
- chcp.com (PID: 16968)
- 2klz.exe (PID: 20568)
- Client.exe (PID: 17332)
- seksiak.exe (PID: 8992)
- chcp.com (PID: 17380)
- 2klz.exe (PID: 17576)
- chcp.com (PID: 16464)
- Client.exe (PID: 13960)
- seksiak.exe (PID: 4304)
- chcp.com (PID: 21748)
- chcp.com (PID: 22432)
Creates files in the program directory
- New Text Document mod.exe.bin.exe (PID: 624)
- Synaptics.exe (PID: 4952)
- svchost.exe (PID: 7000)
- WinDrive-f4855f59e0.exe (PID: 6860)
- svchost.exe (PID: 11680)
- BootstrapperNew.exe (PID: 8104)
- dw20.exe (PID: 18872)
- svchost.exe (PID: 16544)
- XClient.exe (PID: 19052)
- ghjaedjgaw.exe (PID: 19912)
- Built.exe (PID: 21368)
- onedrive.exe (PID: 21100)
Reads Environment values
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- minimal.exe (PID: 4320)
- chrtrome22.exe (PID: 6700)
- Customer.exe (PID: 7968)
- RuntimeBroker.exe (PID: 7216)
- TEST.exe (PID: 8624)
- Launcher_Start.exe (PID: 9404)
- Test2.exe (PID: 16128)
- seksiak.exe (PID: 12372)
- Onedrive.exe (PID: 16608)
- Client.exe (PID: 13236)
- seksiak.exe (PID: 18232)
- 2klz.exe (PID: 14792)
- seksiak.exe (PID: 9200)
- 2klz.exe (PID: 13192)
- Client.exe (PID: 18068)
- 2klz.exe (PID: 14744)
- seksiak.exe (PID: 18736)
- Client.exe (PID: 18760)
- XClient.exe (PID: 19052)
- AdobePDFReader.exe (PID: 19308)
- Java32.exe (PID: 18964)
- dw20.exe (PID: 18872)
- 2klz.exe (PID: 18872)
- seksiak.exe (PID: 19252)
- 2klz.exe (PID: 17152)
- Client.exe (PID: 21012)
- 2klz.exe (PID: 17348)
- Client.exe (PID: 22048)
- Client.exe (PID: 21220)
- seksiak.exe (PID: 19004)
- 2klz.exe (PID: 21596)
- seksiak.exe (PID: 18624)
- 2klz.exe (PID: 20568)
- Client.exe (PID: 17332)
- 2klz.exe (PID: 17576)
- Client.exe (PID: 13960)
Reads the machine GUID from the registry
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- whiteshadow123.exe (PID: 5864)
- Set-up.exe (PID: 3812)
- minimal.exe (PID: 4320)
- johnmartin.exe (PID: 4472)
- Synaptics.exe (PID: 4952)
- gem2.exe (PID: 6704)
- service123.exe (PID: 6900)
- gem1.exe (PID: 4244)
- gem1.exe (PID: 6432)
- WinDrive-f4855f59e0.exe (PID: 6860)
- @bebanrti%20(1).exe (PID: 6896)
- utkin.exe (PID: 68)
- elm.exe (PID: 6372)
- kanew.exe (PID: 7008)
- hdont.exe (PID: 5572)
- markiz.exe (PID: 6656)
- LummaC2.exe (PID: 4592)
- tmx.exe (PID: 6456)
- service123.exe (PID: 6528)
- Client.exe (PID: 7108)
- BitLockerToGo.exe (PID: 2940)
- BitLockerToGo.exe (PID: 6752)
- chrtrome22.exe (PID: 6700)
- Fixer.exe (PID: 4336)
- Client-built.exe (PID: 6976)
- build1.exe (PID: 7792)
- Steanings.exe (PID: 7748)
- Customer.exe (PID: 7968)
- csc.exe (PID: 8160)
- RuntimeBroker.exe (PID: 7216)
- AsyncClientGK.exe (PID: 8048)
- 2D8630.exe (PID: 4912)
- TEST.exe (PID: 8624)
- uu.exe (PID: 8280)
- Launcher_Start.exe (PID: 9404)
- 4e452a47dd.exe (PID: 9076)
- Server1.exe (PID: 8340)
- JJSPLOIT.V2.exe (PID: 9724)
- windows 3543.exe (PID: 9860)
- sysnldcvmr.exe (PID: 2792)
- drop1.exe (PID: 10156)
- sdggwsdgdrwgrwgrwgrwgrw.exe (PID: 9812)
- service123.exe (PID: 10320)
- service123.exe (PID: 7980)
- service123.exe (PID: 3972)
- service123.exe (PID: 12888)
- .exe (PID: 13588)
- BootstrapperNew.exe (PID: 8104)
- TPB-1.exe (PID: 11640)
- 2klz.exe (PID: 15808)
- 2klz.exe (PID: 16248)
- diskutil.exe (PID: 15508)
- diskutil.exe (PID: 16244)
- Test2.exe (PID: 16128)
- Client.exe (PID: 12836)
- Gorebox%20ModMenu%201.2.0.exe (PID: 15864)
- seksiak.exe (PID: 12372)
- OneDrive.exe (PID: 15196)
- Onedrive.exe (PID: 16608)
- jrockekcurje.exe (PID: 16908)
- ytjgjdrthjdw.exe (PID: 16392)
- toolwin.exe (PID: 14856)
- build.exe (PID: 15188)
- image%20logger.exe (PID: 17592)
- Sync.exe (PID: 17484)
- systempreter.exe (PID: 13344)
- csc.exe (PID: 17860)
- Client.exe (PID: 13236)
- seksiak.exe (PID: 18232)
- service123.exe (PID: 16884)
- 2klz.exe (PID: 14792)
- prueba.exe (PID: 14396)
- seksiak.exe (PID: 9200)
- windows 3543.exe (PID: 17012)
- 2klz.exe (PID: 13192)
- mode11_UVo6.exe (PID: 15944)
- Client.exe (PID: 18068)
- seksiak.exe (PID: 16664)
- 2klz.exe (PID: 18148)
- mode11_0HVJ.exe (PID: 16756)
- mode11_AKUh.exe (PID: 15388)
- Client.exe (PID: 16696)
- seksiak.exe (PID: 16964)
- mode11_N1Fz.exe (PID: 16932)
- 2klz.exe (PID: 14744)
- seksiak.exe (PID: 18736)
- Client.exe (PID: 18760)
- XClient.exe (PID: 19052)
- Java32.exe (PID: 18964)
- cici.exe (PID: 18496)
- dw20.exe (PID: 18872)
- mode11_buqd.exe (PID: 18612)
- Client.exe (PID: 18900)
- seksiak.exe (PID: 17988)
- 2klz.exe (PID: 18872)
- service123.exe (PID: 13892)
- seksiak.exe (PID: 19252)
- Client.exe (PID: 17124)
- ghjaedjgaw.exe (PID: 19912)
- ioc.exe (PID: 20100)
- 2klz.exe (PID: 17152)
- Client.exe (PID: 21012)
- C996.tmp.zx.exe (PID: 18152)
- 33.exe (PID: 20532)
- 2klz.exe (PID: 9012)
- rar.exe (PID: 15624)
- Client.exe (PID: 21464)
- seksiak.exe (PID: 18164)
- csc.exe (PID: 15868)
- 2klz.exe (PID: 17348)
- seksiak.exe (PID: 22292)
- Client.exe (PID: 22048)
- 2klz.exe (PID: 15024)
- Client.exe (PID: 21220)
- seksiak.exe (PID: 21740)
- 2klz.exe (PID: 22340)
- Client.exe (PID: 17816)
- seksiak.exe (PID: 21896)
- 2klz.exe (PID: 19744)
- seksiak.exe (PID: 19004)
- Client.exe (PID: 19488)
- 2klz.exe (PID: 21596)
- seksiak.exe (PID: 18624)
- Client.exe (PID: 22364)
- Client.exe (PID: 17332)
- 2klz.exe (PID: 17576)
- seksiak.exe (PID: 4304)
- Client.exe (PID: 13960)
Disables trace logs
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- chrtrome22.exe (PID: 6700)
- Client-built.exe (PID: 6976)
- build1.exe (PID: 7792)
- uu.exe (PID: 8280)
- TEST.exe (PID: 8624)
- ytjgjdrthjdw.exe (PID: 16392)
- Java32.exe (PID: 18964)
- powershell.exe (PID: 19952)
Checks proxy server information
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- Synaptics.exe (PID: 4952)
- WerFault.exe (PID: 7164)
- gem1.exe (PID: 6432)
- WerFault.exe (PID: 2828)
- WerFault.exe (PID: 3700)
- WinDrive-f4855f59e0.exe (PID: 6860)
- 32.exe (PID: 4912)
- sysnldcvmr.exe (PID: 2792)
- chrtrome22.exe (PID: 6700)
- Client-built.exe (PID: 6976)
- 1724930485.exe (PID: 6180)
- build1.exe (PID: 7792)
- skotes.exe (PID: 6372)
- uu.exe (PID: 8280)
- TEST.exe (PID: 8624)
- Launcher_Start.exe (PID: 9404)
- 696969.exe (PID: 9580)
- WerFault.exe (PID: 5704)
- WerFault.exe (PID: 7672)
- 3t57j.exe (PID: 10248)
- SCLKFNF21ARIHQ5RV63UYR.exe (PID: 10568)
- IMG001.exe (PID: 11028)
- WerFault.exe (PID: 14348)
- ytjgjdrthjdw.exe (PID: 16392)
- jrockekcurje.exe (PID: 16908)
- mode11_UVo6.exe (PID: 15944)
- mode11_AKUh.exe (PID: 15388)
- Java32.exe (PID: 18964)
- XClient.exe (PID: 19052)
- image.exe (PID: 18824)
- mode11_buqd.exe (PID: 18612)
- ghjaedjgaw.exe (PID: 19912)
- explorer.exe (PID: 4488)
- powershell.exe (PID: 19952)
Reads the software policy settings
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- consent.exe (PID: 1544)
- minimal.exe (PID: 4320)
- johnmartin.exe (PID: 4472)
- Synaptics.exe (PID: 4952)
- consent.exe (PID: 6744)
- consent.exe (PID: 5980)
- consent.exe (PID: 2928)
- WerFault.exe (PID: 7164)
- gem1.exe (PID: 6432)
- WerFault.exe (PID: 2828)
- WerFault.exe (PID: 3700)
- WinDrive-f4855f59e0.exe (PID: 6860)
- consent.exe (PID: 4932)
- consent.exe (PID: 7020)
- consent.exe (PID: 6752)
- consent.exe (PID: 2280)
- consent.exe (PID: 6388)
- consent.exe (PID: 6296)
- consent.exe (PID: 4968)
- consent.exe (PID: 2084)
- consent.exe (PID: 6444)
- consent.exe (PID: 6492)
- consent.exe (PID: 4336)
- consent.exe (PID: 4548)
- LummaC2.exe (PID: 4592)
- BitLockerToGo.exe (PID: 2940)
- BitLockerToGo.exe (PID: 6752)
- chrtrome22.exe (PID: 6700)
- consent.exe (PID: 7916)
- Customer.exe (PID: 7968)
- 2D8630.exe (PID: 4912)
- consent.exe (PID: 8508)
- build1.exe (PID: 7792)
- Launcher_Start.exe (PID: 9404)
- consent.exe (PID: 10216)
- consent.exe (PID: 9752)
- consent.exe (PID: 10092)
- consent.exe (PID: 4688)
- WerFault.exe (PID: 7672)
- albt.exe (PID: 9908)
- consent.exe (PID: 8232)
- WerFault.exe (PID: 8336)
- WerFault.exe (PID: 5704)
- consent.exe (PID: 10588)
- consent.exe (PID: 11280)
- SIHClient.exe (PID: 12784)
- consent.exe (PID: 13200)
- consent.exe (PID: 12896)
- consent.exe (PID: 13920)
- consent.exe (PID: 9244)
- consent.exe (PID: 13120)
- consent.exe (PID: 13396)
- TPB-1.exe (PID: 11640)
- consent.exe (PID: 14972)
- WerFault.exe (PID: 14348)
- consent.exe (PID: 18360)
- mode11_UVo6.exe (PID: 15944)
- mode11_0HVJ.exe (PID: 16756)
- mode11_AKUh.exe (PID: 15388)
- mode11_N1Fz.exe (PID: 16932)
- dw20.exe (PID: 18872)
- ghjaedjgaw.exe (PID: 19912)
The process uses the downloaded file
- consent.exe (PID: 1544)
- whiteshadow.exe (PID: 2992)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- dllhost.exe (PID: 6784)
- whiteshadow123.exe (PID: 5864)
- dllhost.exe (PID: 6172)
- dllhost.exe (PID: 6176)
- dllhost.exe (PID: 4036)
- 32.exe (PID: 4912)
- 2018910798.exe (PID: 6416)
- sysnldcvmr.exe (PID: 2792)
- Client-built.exe (PID: 6976)
- chrtrome22.exe (PID: 6700)
- consent.exe (PID: 7916)
- 1724930485.exe (PID: 6180)
- Customer.exe (PID: 7968)
- RuntimeBroker.exe (PID: 7216)
- 1X48r0.exe (PID: 8156)
- uu.exe (PID: 8280)
- consent.exe (PID: 8508)
- skotes.exe (PID: 6372)
- JJSPLOIT.V2.exe (PID: 9724)
- windows 3543.exe (PID: 9860)
- consent.exe (PID: 4688)
- consent.exe (PID: 10108)
- IMG001.exe (PID: 10860)
- consent.exe (PID: 8232)
- IMG001.exe (PID: 11028)
- 4e452a47dd.exe (PID: 9076)
- consent.exe (PID: 11280)
- 1346722953.exe (PID: 8832)
- consent.exe (PID: 12084)
- consent.exe (PID: 13920)
- seksiak.exe (PID: 8992)
- cmd.exe (PID: 15128)
- consent.exe (PID: 15484)
- 2klz.exe (PID: 15808)
- 2klz.exe (PID: 16248)
- diskutil.exe (PID: 15508)
- Test2.exe (PID: 16128)
- Client.exe (PID: 12836)
- Gorebox%20ModMenu%201.2.0.exe (PID: 15864)
- seksiak.exe (PID: 12372)
- OneDrive.exe (PID: 15196)
- Onedrive.exe (PID: 16608)
- 2klz.exe (PID: 16300)
- Client.exe (PID: 13236)
- seksiak.exe (PID: 18232)
- 2klz.exe (PID: 14792)
- Client.exe (PID: 16956)
- windows 3543.exe (PID: 17012)
- seksiak.exe (PID: 9200)
- 2klz.exe (PID: 13192)
- Client.exe (PID: 18068)
- seksiak.exe (PID: 16664)
- 2klz.exe (PID: 18148)
- seksiak.exe (PID: 16964)
- Client.exe (PID: 16696)
- seksiak.exe (PID: 18736)
- Client.exe (PID: 18760)
- AdobePDFReader.exe (PID: 19308)
- 2klz.exe (PID: 15368)
- Client.exe (PID: 18900)
- seksiak.exe (PID: 17988)
- Coc%20Coc.exe (PID: 18552)
- 2klz.exe (PID: 18872)
- seksiak.exe (PID: 19252)
- 2klz.exe (PID: 17152)
- seksiak.exe (PID: 20952)
- powershell.exe (PID: 20884)
- Client.exe (PID: 21464)
- seksiak.exe (PID: 18164)
- powershell.exe (PID: 21816)
- 2klz.exe (PID: 17348)
- powershell.exe (PID: 15868)
- Client.exe (PID: 22048)
- 2klz.exe (PID: 15024)
- seksiak.exe (PID: 21740)
- Client.exe (PID: 21220)
- 2klz.exe (PID: 22340)
- seksiak.exe (PID: 21896)
- 2klz.exe (PID: 19744)
- seksiak.exe (PID: 19004)
- Client.exe (PID: 19488)
- 2klz.exe (PID: 21596)
- Client.exe (PID: 22364)
- seksiak.exe (PID: 18624)
- 2klz.exe (PID: 20568)
- seksiak.exe (PID: 8992)
- Client.exe (PID: 17332)
- 2klz.exe (PID: 17576)
- Client.exe (PID: 13960)
- seksiak.exe (PID: 4304)
Create files in a temporary directory
- whiteshadow.exe (PID: 2992)
- whiteshadow123.exe (PID: 5864)
- Synaptics.exe (PID: 4952)
- sk.exe (PID: 6684)
- gem2.exe (PID: 6704)
- johnmartin.exe (PID: 4472)
- 32.exe (PID: 4912)
- chrtrome22.exe (PID: 6700)
- sysnldcvmr.exe (PID: 2792)
- LummaC2.exe (PID: 4592)
- 1724930485.exe (PID: 6180)
- 3061413023.exe (PID: 7496)
- Customer.exe (PID: 7968)
- csc.exe (PID: 8160)
- cvtres.exe (PID: 3888)
- build1.exe (PID: 7792)
- r3P25.exe (PID: 7944)
- none.exe (PID: 7900)
- 1X48r0.exe (PID: 8156)
- b2l20.exe (PID: 6224)
- skotes.exe (PID: 6372)
- Server1.exe (PID: 8340)
- Launcher_Start.exe (PID: 9404)
- Crawl.exe (PID: 6448)
- 4e452a47dd.exe (PID: 9076)
- IMG001.exe (PID: 11028)
- Kerish_Doctor_2022.exe (PID: 10268)
- Kerish_Doctor_2022.tmp (PID: 10296)
- Kerish_Doctor_2023.exe (PID: 7920)
- Kerish_Doctor.exe (PID: 11356)
- Kerish_Doctor.tmp (PID: 11388)
- Kerish_Doctor_2021.tmp (PID: 10748)
- Kerish_Doctor_Windows_8.2.exe (PID: 13052)
- Kerish_Doctor_Windows_8.2.exe (PID: 13204)
- Kerish_Doctor_Windows_8.2.tmp (PID: 13228)
- Kerish_Doctor_Windows_XP.exe (PID: 11716)
- Kerish_Doctor_Windows_XP.exe (PID: 12244)
- Kerish_Doctor_Windows_XP.tmp (PID: 6096)
- Kerish_Doctor_Windows_8.exe (PID: 12644)
- Kerish_Doctor_Windows_8.tmp (PID: 12572)
- Kerish_Doctor_Windows.tmp (PID: 12092)
- Kerish_Doctor_2017.exe (PID: 13880)
- Kerish_Doctor_2017.exe (PID: 9008)
- Kerish_Doctor_2017.tmp (PID: 12820)
- Kerish_Doctor_Windows_Vista.exe (PID: 13372)
- Kerish_Doctor_Windows_8.exe (PID: 12952)
- server.exe (PID: 14200)
- Server.exe (PID: 15292)
- mcgen.exe (PID: 14080)
- mcgen.exe (PID: 16096)
- mcgen.exe (PID: 16196)
- 2klz.exe (PID: 16248)
- MpCmdRun.exe (PID: 18040)
- csc.exe (PID: 17860)
- Client.exe (PID: 13236)
- windows 3543.exe (PID: 9860)
- 2klz.exe (PID: 14792)
- Client.exe (PID: 16956)
- seksiak.exe (PID: 9200)
- seksiak.exe (PID: 16664)
- 2klz.exe (PID: 18148)
- seksiak.exe (PID: 16964)
- Client.exe (PID: 18760)
- 2klz.exe (PID: 15368)
- seksiak.exe (PID: 17988)
- Coc%20Coc.exe (PID: 18552)
- Google%20Chrome.exe (PID: 15892)
- seksiak.exe (PID: 19252)
- 2klz.exe (PID: 17152)
- Built.exe (PID: 20996)
- C996.tmp.zx.exe (PID: 21092)
- Client.exe (PID: 21012)
- Built.exe (PID: 21368)
- rar.exe (PID: 15624)
- seksiak.exe (PID: 18164)
- Client.exe (PID: 21464)
- csc.exe (PID: 15868)
- cvtres.exe (PID: 11256)
- 2klz.exe (PID: 17348)
- Client.exe (PID: 22048)
- seksiak.exe (PID: 21740)
- Client.exe (PID: 21220)
- 2klz.exe (PID: 22340)
- Client.exe (PID: 17816)
- seksiak.exe (PID: 19004)
- Client.exe (PID: 19488)
- 2klz.exe (PID: 21596)
- Client.exe (PID: 22364)
- 2klz.exe (PID: 20568)
- Client.exe (PID: 17332)
- seksiak.exe (PID: 4304)
- Client.exe (PID: 13960)
Creates files or folders in the user directory
- minimal.exe (PID: 4320)
- explorer.exe (PID: 4488)
- WerFault.exe (PID: 7164)
- WerFault.exe (PID: 2828)
- WerFault.exe (PID: 3700)
- WinDrive-f4855f59e0.exe (PID: 6860)
- cbot.exe (PID: 236)
- 32.exe (PID: 4912)
- sysnldcvmr.exe (PID: 2792)
- 1724930485.exe (PID: 6180)
- 293637911.exe (PID: 7392)
- Server1.exe (PID: 8340)
- skotes.exe (PID: 6372)
- Crawl.exe (PID: 6448)
- JJSPLOIT.V2.exe (PID: 9724)
- WerFault.exe (PID: 5704)
- IMG001.exe (PID: 11028)
- 3t57j.exe (PID: 10248)
- WerFault.exe (PID: 8336)
- WerFault.exe (PID: 14348)
- testingg.exe (PID: 15096)
- NOTallowedtocrypt.exe (PID: 15344)
- server.exe (PID: 14200)
- 2klz.exe (PID: 15808)
- diskutil.exe (PID: 15508)
- Test2.exe (PID: 16128)
- OneDrive.exe (PID: 15196)
- Coc%20Coc.exe (PID: 18552)
- ghjaedjgaw.exe (PID: 19912)
Drops encrypted VBS script (Microsoft Script Encoder)
- whiteshadow123.exe (PID: 5864)
- tmx.exe (PID: 6456)
- 3061413023.exe (PID: 7496)
- Steanings.exe (PID: 7748)
- build1.exe (PID: 7792)
- 293637911.exe (PID: 7392)
- cici.exe (PID: 18496)
Application based on Golang
- minimal.exe (PID: 4320)
- random.exe (PID: 6768)
- The%20Foundry.exe (PID: 6716)
Reads CPU info
- whiteshadow123.exe (PID: 5864)
- dw20.exe (PID: 18872)
Application launched itself
- chrome.exe (PID: 4204)
- chrome.exe (PID: 11200)
- chrome.exe (PID: 19868)
Process checks computer location settings
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- whiteshadow123.exe (PID: 5864)
- gem1.exe (PID: 6432)
- chrtrome22.exe (PID: 6700)
- 1X48r0.exe (PID: 8156)
- skotes.exe (PID: 6372)
- IMG001.exe (PID: 10860)
- IMG001.exe (PID: 11028)
- Kerish_Doctor_2022.tmp (PID: 3840)
- 4e452a47dd.exe (PID: 9076)
- Kerish_Doctor_2023.tmp (PID: 10448)
- 3148931435.exe (PID: 12056)
- Kerish_Doctor_2021.tmp (PID: 12132)
- Kerish_Doctor_Windows_8.2.tmp (PID: 13072)
- Kerish_Doctor_Windows_XP.tmp (PID: 12992)
- Kerish_Doctor_Windows_8.tmp (PID: 12776)
- Kerish_Doctor_2017.tmp (PID: 13900)
- NOTallowedtocrypt.exe (PID: 15344)
- seksiak.exe (PID: 8992)
- 2klz.exe (PID: 16248)
- Client.exe (PID: 12836)
- 2klz.exe (PID: 16300)
- Client.exe (PID: 13236)
- seksiak.exe (PID: 9200)
- seksiak.exe (PID: 16964)
- 2klz.exe (PID: 14744)
- Client.exe (PID: 18760)
- dw20.exe (PID: 18872)
- 2klz.exe (PID: 15368)
- seksiak.exe (PID: 17988)
- Client.exe (PID: 18900)
- Client.exe (PID: 17124)
- seksiak.exe (PID: 19252)
- microsoft-onedrive.exe (PID: 20660)
- Client.exe (PID: 21012)
- 2klz.exe (PID: 9012)
- Client.exe (PID: 21464)
- 2klz.exe (PID: 17348)
- Client.exe (PID: 22048)
- seksiak.exe (PID: 21740)
- 2klz.exe (PID: 22340)
- seksiak.exe (PID: 21896)
- Client.exe (PID: 17816)
- 2klz.exe (PID: 19744)
- seksiak.exe (PID: 18624)
- 2klz.exe (PID: 20568)
- 2klz.exe (PID: 17576)
- seksiak.exe (PID: 4304)
Reads Windows Product ID
- WmiPrvSE.exe (PID: 6568)
- WmiPrvSE.exe (PID: 14596)
The sample compiled with english language support
- sk.exe (PID: 6684)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- Synaptics.exe (PID: 4952)
- none.exe (PID: 7900)
- r3P25.exe (PID: 7944)
- 293637911.exe (PID: 7392)
- TEST.exe (PID: 8624)
- Launcher_Start.exe (PID: 9404)
- IMG001.exe (PID: 11028)
- mcgen.exe (PID: 14080)
- mcgen.exe (PID: 16096)
- mcgen.exe (PID: 16196)
- Coc%20Coc.exe (PID: 18552)
- dropper64.exe (PID: 20180)
- Built.exe (PID: 20996)
- microsoft-onedrive.exe (PID: 20660)
- C996.tmp.zx.exe (PID: 21092)
- Built.exe (PID: 21368)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 6172)
- dllhost.exe (PID: 6176)
- WMIC.exe (PID: 6032)
- dllhost.exe (PID: 4036)
- WMIC.exe (PID: 6692)
- WMIC.exe (PID: 7032)
- WMIC.exe (PID: 9760)
- WMIC.exe (PID: 10976)
- dllhost.exe (PID: 1288)
- dllhost.exe (PID: 15124)
- ComputerDefaults.exe (PID: 15712)
- WMIC.exe (PID: 16456)
- WMIC.exe (PID: 15048)
- svchost.exe (PID: 20272)
- explorer.exe (PID: 4488)
- WMIC.exe (PID: 12384)
- WMIC.exe (PID: 22172)
- WMIC.exe (PID: 22448)
- WMIC.exe (PID: 18756)
- WMIC.exe (PID: 19880)
Checks transactions between databases Windows and Oracle
- gem2.exe (PID: 6704)
- utkin.exe (PID: 68)
- elm.exe (PID: 6372)
- kanew.exe (PID: 7008)
- hdont.exe (PID: 5572)
- markiz.exe (PID: 6656)
- @bebanrti%20(1).exe (PID: 6896)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6884)
- Customer.exe (PID: 7968)
- powershell.exe (PID: 15916)
- powershell.exe (PID: 16144)
- powershell.exe (PID: 17200)
- powershell.exe (PID: 20020)
- powershell.exe (PID: 20884)
- powershell.exe (PID: 21424)
- powershell.exe (PID: 20628)
- powershell.exe (PID: 17656)
- powershell.exe (PID: 21816)
- powershell.exe (PID: 15868)
Reads the time zone
- gem1.exe (PID: 6432)
- WmiPrvSE.exe (PID: 6568)
- WmiPrvSE.exe (PID: 14596)
PyInstaller has been detected (YARA)
- sk.exe (PID: 6684)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1944)
- powershell.exe (PID: 6884)
- powershell.exe (PID: 7240)
- powershell.exe (PID: 16144)
- powershell.exe (PID: 17200)
- powershell.exe (PID: 15916)
- powershell.exe (PID: 4460)
- powershell.exe (PID: 15712)
- powershell.exe (PID: 20628)
- powershell.exe (PID: 17656)
- powershell.exe (PID: 21816)
- powershell.exe (PID: 20884)
- powershell.exe (PID: 21424)
- powershell.exe (PID: 15868)
.NET Reactor protector has been detected
- gem1.exe (PID: 6432)
Execution of CURL command
- svchost.exe (PID: 7024)
Failed to create an executable file in Windows directory
- 2018910798.exe (PID: 6416)
- Server1.exe (PID: 8340)
- server.exe (PID: 14200)
Attempting to use instant messaging service
- sk.exe (PID: 6584)
- svchost.exe (PID: 2192)
- ghjaedjgaw.exe (PID: 19912)
The sample compiled with japanese language support
- chrtrome22.exe (PID: 6700)
- vsrumanlxdbr.exe (PID: 18396)
Sends debugging messages
- skotes.exe (PID: 6372)
- 1X48r0.exe (PID: 8156)
- 2D8630.exe (PID: 4912)
- 4e452a47dd.exe (PID: 9076)
- wudi.exe (PID: 4676)
- skotes.exe (PID: 3556)
- SCLKFNF21ARIHQ5RV63UYR.exe (PID: 10568)
- KQ2ZHT79N1C50FF5FGMYRJFW3BR4.exe (PID: 9412)
- 3t57j.exe (PID: 10248)
- skotes.exe (PID: 7656)
- skotes.exe (PID: 12508)
- skotes.exe (PID: 13244)
- skotes.exe (PID: 16724)
- skotes.exe (PID: 15448)
- skotes.exe (PID: 20688)
- skotes.exe (PID: 22060)
- skotes.exe (PID: 21316)
- Launcher_Start.exe (PID: 9404)
The sample compiled with korean language support
- Launcher_Start.exe (PID: 9404)
The sample compiled with chinese language support
- wudi.exe (PID: 4676)
- ._cache_New Text Document mod.exe.bin.exe (PID: 3420)
- 33.exe (PID: 20532)
Changes the display of characters in the console
- cmd.exe (PID: 9816)
- cmd.exe (PID: 15500)
- cmd.exe (PID: 16088)
- cmd.exe (PID: 12516)
- cmd.exe (PID: 16716)
- cmd.exe (PID: 18336)
- cmd.exe (PID: 15400)
- cmd.exe (PID: 15136)
- cmd.exe (PID: 17612)
- cmd.exe (PID: 17388)
- cmd.exe (PID: 14592)
- cmd.exe (PID: 15468)
- cmd.exe (PID: 17208)
- cmd.exe (PID: 16344)
- cmd.exe (PID: 6180)
- cmd.exe (PID: 13760)
- cmd.exe (PID: 14584)
- cmd.exe (PID: 16424)
- cmd.exe (PID: 15248)
- cmd.exe (PID: 19016)
- cmd.exe (PID: 19100)
- cmd.exe (PID: 18956)
- cmd.exe (PID: 19412)
- cmd.exe (PID: 19396)
- cmd.exe (PID: 2576)
- cmd.exe (PID: 19748)
- cmd.exe (PID: 19736)
- cmd.exe (PID: 21024)
- cmd.exe (PID: 19636)
- cmd.exe (PID: 18568)
- cmd.exe (PID: 19864)
- cmd.exe (PID: 20264)
- cmd.exe (PID: 17256)
- cmd.exe (PID: 17584)
- cmd.exe (PID: 19672)
- cmd.exe (PID: 6448)
- cmd.exe (PID: 20960)
- cmd.exe (PID: 20348)
- cmd.exe (PID: 15860)
- cmd.exe (PID: 12764)
- cmd.exe (PID: 5724)
- cmd.exe (PID: 21088)
- cmd.exe (PID: 22076)
- cmd.exe (PID: 15880)
- cmd.exe (PID: 20664)
- cmd.exe (PID: 19120)
- cmd.exe (PID: 19700)
- cmd.exe (PID: 14452)
- cmd.exe (PID: 8708)
- cmd.exe (PID: 19164)
- cmd.exe (PID: 18756)
- cmd.exe (PID: 19516)
- cmd.exe (PID: 19740)
- cmd.exe (PID: 15412)
The sample compiled with russian language support
- Kerish_Doctor_2022.tmp (PID: 10296)
- Kerish_Doctor_2023.tmp (PID: 10664)
- Kerish_Doctor.tmp (PID: 11388)
- Kerish_Doctor_2021.tmp (PID: 10748)
- Kerish_Doctor_Windows_8.2.tmp (PID: 13228)
- Kerish_Doctor_Windows_XP.tmp (PID: 6096)
- Kerish_Doctor_Windows_8.tmp (PID: 12572)
- Kerish_Doctor_Windows.tmp (PID: 12092)
- Kerish_Doctor_2017.tmp (PID: 12820)
- Kerish_Doctor_Windows_Vista.tmp (PID: 13616)
Connects to unusual port
- iexplore.exe (PID: 13116)
Checks the directory tree
- tree.com (PID: 16856)
- tree.com (PID: 17576)
- tree.com (PID: 18120)
- tree.com (PID: 17580)
- tree.com (PID: 14188)
- tree.com (PID: 17256)
- tree.com (PID: 22396)
- tree.com (PID: 21904)
- tree.com (PID: 20804)
- tree.com (PID: 17680)
- tree.com (PID: 17808)
- tree.com (PID: 20960)
The Powershell gets current clipboard
- powershell.exe (PID: 15004)
- powershell.exe (PID: 22312)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 14852)
- getmac.exe (PID: 21936)
Reads product name
- dw20.exe (PID: 18872)
Loads dropped or rewritten executable
- chrome.exe (PID: 6160)
- chrome.exe (PID: 9288)
- chrome.exe (PID: 19892)
- chrome.exe (PID: 20040)
- chrome.exe (PID: 11212)
- chrome.exe (PID: 3564)
- chrome.exe (PID: 9280)
- chrome.exe (PID: 10776)
- chrome.exe (PID: 20048)
- chrome.exe (PID: 17312)
- chrome.exe (PID: 2324)
- chrome.exe (PID: 6220)
- chrome.exe (PID: 10716)
- chrome.exe (PID: 17880)
- chrome.exe (PID: 1864)
- chrome.exe (PID: 6148)
- chrome.exe (PID: 20576)
- chrome.exe (PID: 11200)
- chrome.exe (PID: 20052)
- chrome.exe (PID: 4160)
- chrome.exe (PID: 7640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 7 (96.4) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (2) |
| .exe | | | Win32 Executable (generic) (0.6) |
| .exe | | | Win16/32 Executable Delphi generic (0.3) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 629760 |
| InitializedDataSize: | 148992 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9ab80 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.4 |
| ProductVersionNumber: | 1.0.0.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Turkish |
| CharacterSet: | Windows, Turkish |
| CompanyName: | Synaptics |
| FileDescription: | Synaptics Pointing Device Driver |
| FileVersion: | 1.0.0.4 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | Synaptics Pointing Device Driver |
| ProductVersion: | 1.0.0.0 |
| Comments: | - |
Total processes
1 909
Monitored processes
1 790
Malicious processes
255
Suspicious processes
119
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | "C:\Users\admin\Desktop\a\utkin.exe" | C:\Users\admin\Desktop\a\utkin.exe | — | ._cache_New Text Document mod.exe.bin.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1630 Modules
| |||||||||||||||
| 236 | "C:\Users\admin\Desktop\a\cbot.exe" | C:\Users\admin\Desktop\a\cbot.exe | ._cache_New Text Document mod.exe.bin.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 308 | "C:\Windows\SysWOW64\explorer.exe" | C:\Windows\SysWOW64\explorer.exe | — | WinDrive-f4855f59e0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) | |||||||||||||||
| 420 | "C:\Windows\SysWOW64\explorer.exe" | C:\Windows\SysWOW64\explorer.exe | — | WinDrive-f4855f59e0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) | |||||||||||||||
| 624 | "C:\Users\admin\Desktop\New Text Document mod.exe.bin.exe" | C:\Users\admin\Desktop\New Text Document mod.exe.bin.exe | explorer.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: MEDIUM Description: Synaptics Pointing Device Driver Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
| 640 | "C:\Windows\SysWOW64\explorer.exe" | C:\Windows\SysWOW64\explorer.exe | — | WinDrive-f4855f59e0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) | |||||||||||||||
| 768 | "C:\Windows\SysWOW64\explorer.exe" | C:\Windows\SysWOW64\explorer.exe | — | WinDrive-f4855f59e0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) | |||||||||||||||
| 828 | "C:\Windows\SysWOW64\explorer.exe" | C:\Windows\SysWOW64\explorer.exe | — | WinDrive-f4855f59e0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) | |||||||||||||||
| 1172 | "C:\Windows\SysWOW64\explorer.exe" | C:\Windows\SysWOW64\explorer.exe | — | WinDrive-f4855f59e0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) | |||||||||||||||
| 1288 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{D2E7041B-2927-42FB-8E9F-7CE93B6DC937} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
616 532
Read events
614 976
Write events
1 365
Delete events
191
Modification events
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000080284 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456A48A294F7A40804AB924005FF030B61F | |||
| (PID) Process: | (624) New Text Document mod.exe.bin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (624) New Text Document mod.exe.bin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Synaptics Pointing Device Driver |
Value: C:\ProgramData\Synaptics\Synaptics.exe | |||
| (PID) Process: | (624) New Text Document mod.exe.bin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A7803901000060B81DB4E48ED2119906E49FADC173CA8D000000 | |||
| (PID) Process: | (3420) ._cache_New Text Document mod.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3420) ._cache_New Text Document mod.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (3420) ._cache_New Text Document mod.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3420) ._cache_New Text Document mod.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3420) ._cache_New Text Document mod.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3420) ._cache_New Text Document mod.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
Executable files
683
Suspicious files
1 190
Text files
1 660
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF141a2d.TMP | — | |
MD5:— | SHA256:— | |||
| 4204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF141a3d.TMP | — | |
MD5:— | SHA256:— | |||
| 4204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF141a3d.TMP | — | |
MD5:— | SHA256:— | |||
| 4204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF141a3d.TMP | — | |
MD5:— | SHA256:— | |||
| 4204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 624 | New Text Document mod.exe.bin.exe | C:\Users\admin\Desktop\._cache_New Text Document mod.exe.bin.exe | executable | |
MD5:69994FF2F00EECA9335CCD502198E05B | SHA256:2E2E035ECE4ACCDEE838ECAACDC263FA526939597954D18D1320D73C8BF810C2 | |||
| 4204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:358BEEE7F7282D5889B103BD631DCCA2 | SHA256:DF277E0A3314509AF3C1A82B1B71F2FBD83087A32F2A288257C083663477E437 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5 987
TCP/UDP connections
14 908
DNS requests
285
Threats
1 057
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
204 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3420 | ._cache_New Text Document mod.exe.bin.exe | GET | 200 | 185.215.113.16:80 | http://185.215.113.16/inc/whiteshadow123.exe | unknown | — | — | malicious |
4952 | Synaptics.exe | GET | 200 | 69.42.215.252:80 | http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978 | unknown | — | — | whitelisted |
3420 | ._cache_New Text Document mod.exe.bin.exe | GET | 200 | 185.215.113.16:80 | http://185.215.113.16/inc/whiteshadow.exe | unknown | — | — | malicious |
5864 | whiteshadow123.exe | GET | 200 | 176.53.147.104:80 | http://home.twelve12vs.top/AvWHJxAVCxPehbRictmJ1736163220?argument=ZiFktoWr0tLdKFfu1736687468 | unknown | — | — | malicious |
204 | svchost.exe | GET | 200 | 23.48.23.141:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.141:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5864 | whiteshadow123.exe | POST | 200 | 176.53.147.104:80 | http://home.twelve12vs.top/AvWHJxAVCxPehbRictmJ1736163220 | unknown | — | — | malicious |
3420 | ._cache_New Text Document mod.exe.bin.exe | GET | 200 | 185.215.113.16:80 | http://185.215.113.16/inc/minimal.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.31:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
204 | svchost.exe | 23.48.23.141:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.141:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
204 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3420 | ._cache_New Text Document mod.exe.bin.exe | 151.101.130.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
3420 | ._cache_New Text Document mod.exe.bin.exe | 185.215.113.16:80 | — | 1337team Limited | SC | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
xred.mooo.com |
| whitelisted |
freedns.afraid.org |
| whitelisted |
httpbin.org |
| unknown |
home.twelve12vs.top |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3420 | ._cache_New Text Document mod.exe.bin.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3420 | ._cache_New Text Document mod.exe.bin.exe | Misc activity | ET INFO Packed Executable Download |
3420 | ._cache_New Text Document mod.exe.bin.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3420 | ._cache_New Text Document mod.exe.bin.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3420 | ._cache_New Text Document mod.exe.bin.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
3420 | ._cache_New Text Document mod.exe.bin.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to Abused Domain *.mooo.com |
3420 | ._cache_New Text Document mod.exe.bin.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5864 | whiteshadow123.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
5864 | whiteshadow123.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
229 ETPRO signatures available at the full report
Process | Message |
|---|---|
1X48r0.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
skotes.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
2D8630.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
4e452a47dd.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
wudi.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2010 Oreans Technologies ---
------------------------------------------------
|
skotes.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
SCLKFNF21ARIHQ5RV63UYR.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
KQ2ZHT79N1C50FF5FGMYRJFW3BR4.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
3t57j.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
skotes.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|