| File name: | SecuriteInfo.com.IL.Trojan.MSILZilla.30886.28966.14387 |
| Full analysis: | https://app.any.run/tasks/85fd854c-1d76-4e22-9608-e8726f51b246 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | November 09, 2023, 04:32:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | ACA63B9E4AB5A783F11B125C71112242 |
| SHA1: | 82BABA92A2C1B320921AD05E56A5890F62697CF3 |
| SHA256: | BAA0CB3BC60D90CFBE000D58B1E4FF06888722BFA81C68EF1486E7E48BA8740A |
| SSDEEP: | 3072:m14iwt2CbSxPZVgwWij3tpuA6y+JrQTyy1G:m14i1CbSxRSpirt6y4C |
MALICIOUS
Adds path to the Windows Defender exclusion list
- SecuriteInfo.com.IL.Trojan.MSILZilla.30886.28966.14387.exe (PID: 2600)
- explorer.exe (PID: 1944)
Drops the executable file immediately after the start
- CasPol.exe (PID: 2216)
- ugbcmuwwFSnO95XZW7AA0tti.exe (PID: 2408)
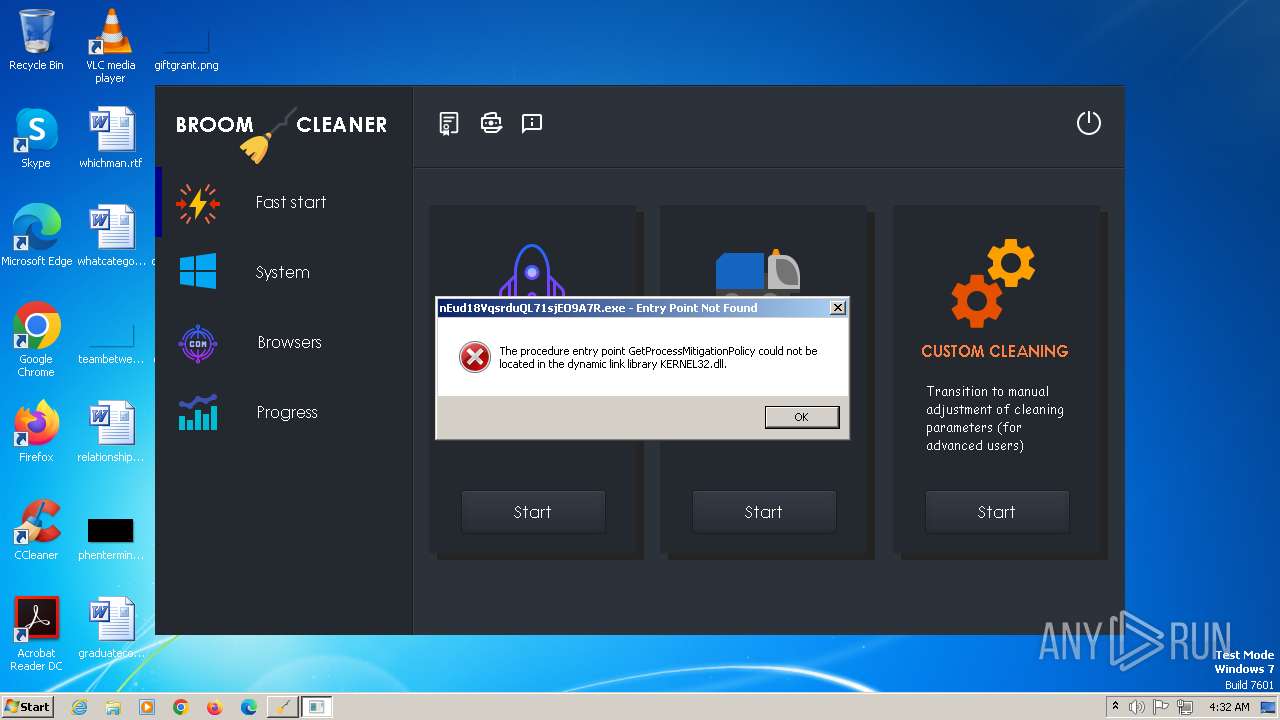
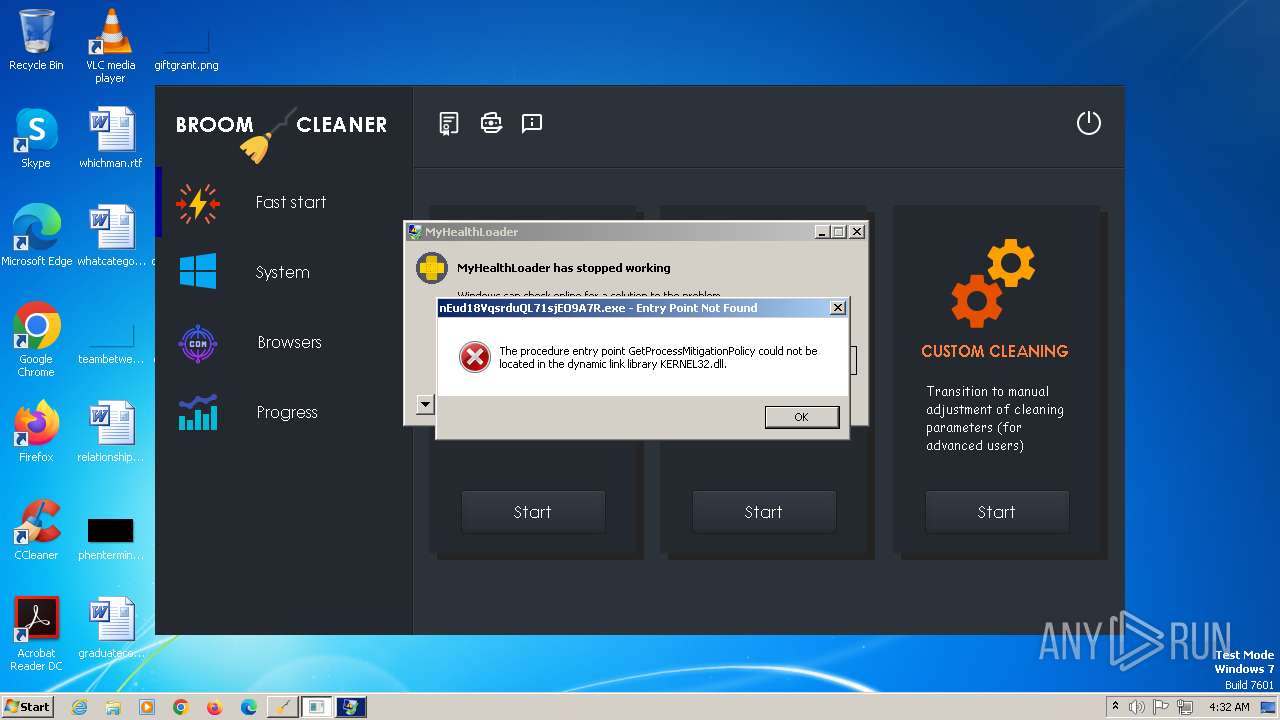
- nEud18VqsrduQL71sjEO9A7R.exe (PID: 688)
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 1940)
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- 1260521668.exe (PID: 2456)
- Utsysc.exe (PID: 2492)
- FPgG0XAkVoXc2lHGGyxtP51v.exe (PID: 308)
- updater.exe (PID: 3056)
Create files in the Startup directory
- CasPol.exe (PID: 2216)
STEALC has been detected (SURICATA)
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
GCLEANER has been detected (SURICATA)
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 1940)
Runs injected code in another process
- hunU9LeEDys0MgJ5O4NFUw2W.exe (PID: 1784)
Application was injected by another process
- explorer.exe (PID: 1944)
Steals credentials
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- rundll32.exe (PID: 2732)
- rundll32.exe (PID: 2972)
Changes the autorun value in the registry
- Utsysc.exe (PID: 2492)
Uses Task Scheduler to run other applications
- Utsysc.exe (PID: 2492)
- explorer.exe (PID: 1944)
Connects to the CnC server
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- explorer.exe (PID: 1944)
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
Steals credentials from Web Browsers
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- rundll32.exe (PID: 2732)
- rundll32.exe (PID: 2972)
AMADEY has been detected (SURICATA)
- Utsysc.exe (PID: 2492)
Starts CMD.EXE for self-deleting
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 1940)
SMOKE has been detected (SURICATA)
- explorer.exe (PID: 1944)
Unusual connection from system programs
- rundll32.exe (PID: 2732)
- rundll32.exe (PID: 2972)
- rundll32.exe (PID: 2952)
- rundll32.exe (PID: 2484)
Modifies hosts file to block updates
- FPgG0XAkVoXc2lHGGyxtP51v.exe (PID: 308)
Creates a writable file the system directory
- powershell.exe (PID: 3020)
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
PRIVATELOADER has been detected (SURICATA)
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
Actions looks like stealing of personal data
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
- rundll32.exe (PID: 2972)
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- rundll32.exe (PID: 2732)
SUSPICIOUS
Script adds exclusion path to Windows Defender
- SecuriteInfo.com.IL.Trojan.MSILZilla.30886.28966.14387.exe (PID: 2600)
- explorer.exe (PID: 1944)
Reads the Internet Settings
- CasPol.exe (PID: 2216)
- SecuriteInfo.com.IL.Trojan.MSILZilla.30886.28966.14387.exe (PID: 2600)
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 1940)
- 1260521668.exe (PID: 2456)
- Utsysc.exe (PID: 2492)
- cmd.exe (PID: 2856)
- rundll32.exe (PID: 2732)
- powershell.exe (PID: 2712)
- Utsysc.exe (PID: 1764)
- rundll32.exe (PID: 2972)
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
- rundll32.exe (PID: 2484)
- Utsysc.exe (PID: 2260)
- rundll32.exe (PID: 2952)
Reads settings of System Certificates
- CasPol.exe (PID: 2216)
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 1940)
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
Application launched itself
- hunU9LeEDys0MgJ5O4NFUw2W.exe (PID: 312)
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 648)
- explorer.exe (PID: 1944)
Process requests binary or script from the Internet
- CasPol.exe (PID: 2216)
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- Utsysc.exe (PID: 2492)
Connects to the server without a host name
- CasPol.exe (PID: 2216)
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 1940)
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
Checks Windows Trust Settings
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
Reads security settings of Internet Explorer
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
Connects to unusual port
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- explorer.exe (PID: 984)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
Starts POWERSHELL.EXE for commands execution
- SecuriteInfo.com.IL.Trojan.MSILZilla.30886.28966.14387.exe (PID: 2600)
- explorer.exe (PID: 1944)
Searches for installed software
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
Starts CMD.EXE for commands execution
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 1940)
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- explorer.exe (PID: 1944)
Starts itself from another location
- 1260521668.exe (PID: 2456)
The process drops C-runtime libraries
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
Process drops legitimate windows executable
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
The process drops Mozilla's DLL files
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
Reads browser cookies
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1492)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 2260)
- rundll32.exe (PID: 2396)
Accesses Microsoft Outlook profiles
- rundll32.exe (PID: 2732)
- rundll32.exe (PID: 2972)
Loads DLL from Mozilla Firefox
- rundll32.exe (PID: 2732)
- rundll32.exe (PID: 2972)
Uses NETSH.EXE to obtain data on the network
- rundll32.exe (PID: 2732)
- rundll32.exe (PID: 2972)
The process executes via Task Scheduler
- Utsysc.exe (PID: 1764)
- Utsysc.exe (PID: 2260)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1164)
Starts SC.EXE for service management
- cmd.exe (PID: 2160)
- cmd.exe (PID: 2640)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 2320)
- cmd.exe (PID: 1556)
Executes as Windows Service
- updater.exe (PID: 3056)
- raserver.exe (PID: 1696)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 3056)
Unusual connection from system programs
- powershell.exe (PID: 3020)
The Powershell connects to the Internet
- powershell.exe (PID: 3020)
Reads the BIOS version
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
Checks for external IP
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
INFO
Reads the computer name
- SecuriteInfo.com.IL.Trojan.MSILZilla.30886.28966.14387.exe (PID: 2600)
- CasPol.exe (PID: 2216)
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- ugbcmuwwFSnO95XZW7AA0tti.exe (PID: 2408)
- Broom.exe (PID: 2412)
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 1940)
- ZRrXarxyDbf2YAXhpkJ5EIUD.exe (PID: 2496)
- 1260521668.exe (PID: 2456)
- Utsysc.exe (PID: 2492)
- 6kJ4P6T6tCYCLqC7ZZCu4H8j.exe (PID: 1268)
- 2KpHlJSCa39xRpGmijiDY5an.exe (PID: 2440)
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
Checks supported languages
- CasPol.exe (PID: 2216)
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 648)
- hunU9LeEDys0MgJ5O4NFUw2W.exe (PID: 312)
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- hunU9LeEDys0MgJ5O4NFUw2W.exe (PID: 1784)
- ugbcmuwwFSnO95XZW7AA0tti.exe (PID: 2408)
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 1940)
- Broom.exe (PID: 2412)
- SecuriteInfo.com.IL.Trojan.MSILZilla.30886.28966.14387.exe (PID: 2600)
- ZRrXarxyDbf2YAXhpkJ5EIUD.exe (PID: 2496)
- nEud18VqsrduQL71sjEO9A7R.exe (PID: 688)
- 6kJ4P6T6tCYCLqC7ZZCu4H8j.exe (PID: 1268)
- 2KpHlJSCa39xRpGmijiDY5an.exe (PID: 2440)
- 1260521668.exe (PID: 2456)
- Utsysc.exe (PID: 2492)
- FPgG0XAkVoXc2lHGGyxtP51v.exe (PID: 308)
- Utsysc.exe (PID: 1764)
- updater.exe (PID: 3056)
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
- Utsysc.exe (PID: 2260)
Reads Environment values
- CasPol.exe (PID: 2216)
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
Creates files or folders in the user directory
- CasPol.exe (PID: 2216)
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 1940)
- Utsysc.exe (PID: 2492)
- explorer.exe (PID: 1944)
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
Reads the machine GUID from the registry
- CasPol.exe (PID: 2216)
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- SecuriteInfo.com.IL.Trojan.MSILZilla.30886.28966.14387.exe (PID: 2600)
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 1940)
- Utsysc.exe (PID: 2492)
- 2KpHlJSCa39xRpGmijiDY5an.exe (PID: 2440)
- 6kJ4P6T6tCYCLqC7ZZCu4H8j.exe (PID: 1268)
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
Create files in a temporary directory
- CasPol.exe (PID: 2216)
- ugbcmuwwFSnO95XZW7AA0tti.exe (PID: 2408)
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 1940)
- 1260521668.exe (PID: 2456)
- nEud18VqsrduQL71sjEO9A7R.exe (PID: 688)
- Utsysc.exe (PID: 2492)
- FPgG0XAkVoXc2lHGGyxtP51v.exe (PID: 308)
Checks proxy server information
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- B5jzgU6zAoh3YKAvZrsoxE5C.exe (PID: 1940)
- Utsysc.exe (PID: 2492)
- rundll32.exe (PID: 2732)
- rundll32.exe (PID: 2972)
- rundll32.exe (PID: 2952)
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
- rundll32.exe (PID: 2484)
Reads product name
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
Reads CPU info
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
Creates files in the program directory
- dLU2QMHGwPdQRsBLpbT0UhfT.exe (PID: 2220)
- FPgG0XAkVoXc2lHGGyxtP51v.exe (PID: 308)
The executable file from the user directory is run by the CMD process
- 1260521668.exe (PID: 2456)
Drops the executable file immediately after the start
- explorer.exe (PID: 1944)
Reads the Internet Settings
- explorer.exe (PID: 1944)
Process checks are UAC notifies on
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
Process checks computer location settings
- 0iKe2ksxj7r6XHCrqCoEylUI.exe (PID: 2464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:11:07 19:07:31+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 124551 |
| InitializedDataSize: | 3072 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20681 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.93.266.9 |
| ProductVersionNumber: | 6.93.266.9 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | ofexIbu |
| FileDescription: | OYiYA abOLa OhuXAY uCikoqEi UxOb euUNaI. |
| FileVersion: | 6.93.266.9 |
| InternalName: | IVuviBO |
| LegalCopyright: | © 2023 ofexIbu. |
| OriginalFileName: | omuQId |
| ProductName: | OlUmeNOi |
| ProductVersion: | 6.93.266.9 |
| Comments: | AVevuziIOgi EiIye aJAdavUia UzOl AfOp OtAve iZIQiCImOZO. |
Total processes
133
Monitored processes
71
Malicious processes
21
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\Users\admin\Pictures\FPgG0XAkVoXc2lHGGyxtP51v.exe" | C:\Users\admin\Pictures\FPgG0XAkVoXc2lHGGyxtP51v.exe | CasPol.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 312 | "C:\Users\admin\Pictures\hunU9LeEDys0MgJ5O4NFUw2W.exe" | C:\Users\admin\Pictures\hunU9LeEDys0MgJ5O4NFUw2W.exe | — | CasPol.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 364 | "C:\Windows\System32\schtasks.exe" /Create /SC MINUTE /MO 1 /TN Utsysc.exe /TR "C:\Users\admin\AppData\Local\Temp\5125296e5f\Utsysc.exe" /F | C:\Windows\SysWOW64\schtasks.exe | — | Utsysc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | "C:\Windows\System32\cmd.exe" /c start /I "" "C:\Users\admin\AppData\Local\Temp\1260521668.exe" | C:\Windows\SysWOW64\cmd.exe | — | B5jzgU6zAoh3YKAvZrsoxE5C.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 648 | "C:\Users\admin\Pictures\B5jzgU6zAoh3YKAvZrsoxE5C.exe" | C:\Users\admin\Pictures\B5jzgU6zAoh3YKAvZrsoxE5C.exe | — | CasPol.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 688 | "C:\Users\admin\Pictures\nEud18VqsrduQL71sjEO9A7R.exe" --silent --allusers=0 | C:\Users\admin\Pictures\nEud18VqsrduQL71sjEO9A7R.exe | — | CasPol.exe | |||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Installer Exit code: 0 Version: 104.0.4944.36 Modules
| |||||||||||||||
| 712 | sc stop WaaSMedicSvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 812 | C:\Windows\System32\schtasks.exe /create /f /ru "System" /tn "GoogleUpdateTaskMachineQC" /xml "C:\Users\admin\AppData\Local\Temp\tlxvacrdjkek.xml" | C:\Windows\System32\schtasks.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 812 | C:\Windows\System32\schtasks.exe /create /f /ru "System" /tn "GoogleUpdateTaskMachineQC" /xml "C:\Windows\TEMP\tlxvacrdjkek.xml" | C:\Windows\System32\schtasks.exe | explorer.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | netsh wlan show profiles | C:\Windows\System32\netsh.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
25 129
Read events
24 807
Write events
304
Delete events
18
Modification events
| (PID) Process: | (1944) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000088AF72B0747534094337F63DE35C94A000000000200000000001066000000010000200000003A7AE26404D75DF41C31FF40C5EA8CE90BAF74FA9E9BD7A9ACA34C7048350C1E000000000E8000000002000020000000BD2D56D46506C12C41A6A70B10E79EE53CB79EF36FD2BA8CDD2460CB8F4BE86A300000009B5D1418CBF2EB49F3C4BD4C21D58CA55B82FA3D3ED08AF0EF59D6C7ECAFC1055FA323A80FF7C154B1C9B60253392B6640000000DED9FDCC168073324C3013F1BB125E066EB1A2F09FD2C8E7CC7A793AA992E21EF1C942BF7294D04E036428704009B863B1CB981B97312E2530E3E816780CF7C9 | |||
| (PID) Process: | (2600) SecuriteInfo.com.IL.Trojan.MSILZilla.30886.28966.14387.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2600) SecuriteInfo.com.IL.Trojan.MSILZilla.30886.28966.14387.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2600) SecuriteInfo.com.IL.Trojan.MSILZilla.30886.28966.14387.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2600) SecuriteInfo.com.IL.Trojan.MSILZilla.30886.28966.14387.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2216) CasPol.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2216) CasPol.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2216) CasPol.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2216) CasPol.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2216) CasPol.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\156\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
47
Suspicious files
30
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2216 | CasPol.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 2688 | powershell.exe | C:\Users\admin\AppData\Local\Temp\4rrzzgez.kkl.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2216 | CasPol.exe | C:\Users\admin\AppData\Local\Temp\CabAE66.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 2216 | CasPol.exe | C:\Users\admin\Pictures\YJJidFhMmKH6lGKIWnAIffoI.exe | html | |
MD5:FCAD815E470706329E4E327194ACC07C | SHA256:280D939A66A0107297091B3B6F86D6529EF6FAC222A85DBC82822C3D5DC372B8 | |||
| 2216 | CasPol.exe | C:\Users\admin\AppData\Local\Temp\TarAE67.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 2216 | CasPol.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\yJhL1PbjVCXIov1qA13ZnUpZ.bat | text | |
MD5:1678F55E2FD81934827D9A256DD4D33D | SHA256:175D90C35D32104217A9E66A064C98EC21EDE781C504E96D8BB6EF1BD0AAA76D | |||
| 2688 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 2220 | dLU2QMHGwPdQRsBLpbT0UhfT.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\9MT7S6RO.txt | text | |
MD5:E06F5DD17E939BDCAB7AD4684802332D | SHA256:9B4EEF0BBE33593BD67EFB5BB8AE9AD5C6645268B74FECD90B372A3789175D13 | |||
| 2216 | CasPol.exe | C:\Users\admin\AppData\Local\0zT6mfF3hhYTXTOgT5xs5uCD.exe | executable | |
MD5:5AB2B28BC1E00519DCD55B67E9198C2C | SHA256:D8CA36406BFACDD794CC8BBC54F38B1C88116F1A180D4D069C3AD4A2210EF2F4 | |||
| 2216 | CasPol.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\rvD9Uh32eAiUWIlWpndcTcCd.bat | text | |
MD5:551C094FD9FA59F53712942B17C3C861 | SHA256:84E4F8AC550F97F873F4BB72C54F9636B8B9CA75F13C30A9D755296DF3EC385E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
62
DNS requests
39
Threats
118
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2220 | dLU2QMHGwPdQRsBLpbT0UhfT.exe | GET | 200 | 116.203.165.60:2087 | http://116.203.165.60:2087/ | unknown | — | — | unknown |
2216 | CasPol.exe | GET | 200 | 95.214.26.28:80 | http://galandskiyher5.com/downloads/toolspub1.exe | unknown | executable | 318 Kb | unknown |
2216 | CasPol.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?f0f0f46a9543f796 | unknown | compressed | 61.6 Kb | unknown |
2216 | CasPol.exe | GET | 200 | 194.49.94.48:80 | http://194.49.94.48/InstallSetup3.exe | unknown | executable | 2.55 Mb | unknown |
1940 | B5jzgU6zAoh3YKAvZrsoxE5C.exe | GET | 200 | 85.209.11.204:80 | http://85.209.11.204/api/files/client/s51 | unknown | executable | 887 Kb | unknown |
2220 | dLU2QMHGwPdQRsBLpbT0UhfT.exe | POST | 200 | 116.203.165.60:2087 | http://116.203.165.60:2087/ | unknown | text | 48 b | unknown |
2216 | CasPol.exe | GET | 200 | 89.191.234.21:80 | http://gobo11fc.top/build.exe | unknown | executable | 324 Kb | unknown |
1940 | B5jzgU6zAoh3YKAvZrsoxE5C.exe | GET | 200 | 85.209.11.204:80 | http://85.209.11.204/ip.php | unknown | text | 13 b | unknown |
1940 | B5jzgU6zAoh3YKAvZrsoxE5C.exe | GET | 200 | 85.209.11.204:80 | http://85.209.11.204/api/files/client/s51 | unknown | executable | 887 Kb | unknown |
2220 | dLU2QMHGwPdQRsBLpbT0UhfT.exe | POST | 200 | 116.203.165.60:2087 | http://116.203.165.60:2087/ | unknown | text | 8 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2216 | CasPol.exe | 188.114.96.3:443 | yip.su | CLOUDFLARENET | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2216 | CasPol.exe | 104.20.68.143:443 | pastebin.com | CLOUDFLARENET | — | unknown |
2216 | CasPol.exe | 177.229.198.250:443 | etiquetaspiura.com | Mega Cable, S.A. de C.V. | MX | unknown |
2216 | CasPol.exe | 103.55.39.107:443 | wahyurahmat.id | PT Cloud Hosting Indonesia | ID | unknown |
2216 | CasPol.exe | 85.209.11.204:80 | — | LLC Baxet | RU | malicious |
2216 | CasPol.exe | 95.214.26.28:80 | galandskiyher5.com | Enes Koken | US | unknown |
2216 | CasPol.exe | 194.49.94.48:80 | — | Enes Koken | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| shared |
yip.su |
| whitelisted |
etiquetaspiura.com |
| unknown |
wahyurahmat.id |
| unknown |
galandskiyher5.com |
| malicious |
flyawayaero.net |
| unknown |
gons07fc.top |
| unknown |
gobo11fc.top |
| unknown |
lycheepanel.info |
| unknown |
laubenstein.space |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
324 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
324 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2216 | CasPol.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2216 | CasPol.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2216 | CasPol.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2216 | CasPol.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2216 | CasPol.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2216 | CasPol.exe | Misc activity | ET INFO Packed Executable Download |
2216 | CasPol.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2216 | CasPol.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
11 ETPRO signatures available at the full report