| download: | MBSetup.exe |
| Full analysis: | https://app.any.run/tasks/25400285-3e05-4a25-bb31-07dc7579f1b7 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | November 21, 2019, 20:32:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 83CAF0B992DD5D57DA15FEDB067F53AB |
| SHA1: | 21F8EFE01FC98B1CC0EDC2D46C0C1DCE97853875 |
| SHA256: | B9DC6DAFB81BCC3EDF2C89F9B8D72D3060964EE32E173D59D60EBF559FEC7A82 |
| SSDEEP: | 24576:XCDc7EcvoQryaudJChHAkvEvZEG3VwQx/m5+WC:yAh7T1AkiZE0VwQxK+1 |
MALICIOUS
Loads dropped or rewritten executable
- MBAMInstallerService.exe (PID: 1536)
- MBAMService.exe (PID: 1024)
- mbamtray.exe (PID: 2728)
- mbam.exe (PID: 1732)
- assistant.exe (PID: 1488)
Application was dropped or rewritten from another process
- MBAMInstallerService.exe (PID: 1536)
- MBAMService.exe (PID: 1024)
- MBAMService.exe (PID: 3084)
- mbamtray.exe (PID: 2728)
- mbam.exe (PID: 1732)
- assistant.exe (PID: 1488)
- ig.exe (PID: 2472)
- ig.exe (PID: 2276)
Changes settings of System certificates
- certutil.exe (PID: 2992)
- certutil.exe (PID: 3088)
- MBAMService.exe (PID: 1024)
AGENTTESLA was detected
- MBAMService.exe (PID: 1024)
Stealing of credential data
- MBAMService.exe (PID: 1024)
Loads the Task Scheduler COM API
- MBAMService.exe (PID: 1024)
Actions looks like stealing of personal data
- MBAMService.exe (PID: 1024)
SUSPICIOUS
Creates files in the program directory
- MBSetup.exe (PID: 616)
- MBAMInstallerService.exe (PID: 1536)
- MBAMService.exe (PID: 1024)
Creates files in the Windows directory
- certutil.exe (PID: 2992)
- certutil.exe (PID: 3088)
- MBAMService.exe (PID: 3084)
- MBAMService.exe (PID: 1024)
- MBAMInstallerService.exe (PID: 1536)
Executable content was dropped or overwritten
- MBSetup.exe (PID: 616)
- MBAMInstallerService.exe (PID: 1536)
- MBAMService.exe (PID: 1024)
Executed as Windows Service
- MBAMInstallerService.exe (PID: 1536)
- MBAMService.exe (PID: 1024)
Modifies the open verb of a shell class
- MBAMInstallerService.exe (PID: 1536)
Starts CMD.EXE for commands execution
- MBAMInstallerService.exe (PID: 1536)
Removes files from Windows directory
- certutil.exe (PID: 3088)
- certutil.exe (PID: 2992)
- MBAMService.exe (PID: 1024)
- MBAMInstallerService.exe (PID: 1536)
Creates files in the driver directory
- MBAMInstallerService.exe (PID: 1536)
- MBAMService.exe (PID: 1024)
Changes IE settings (feature browser emulation)
- MBAMInstallerService.exe (PID: 1536)
Creates COM task schedule object
- MBAMService.exe (PID: 1024)
Creates a software uninstall entry
- MBAMInstallerService.exe (PID: 1536)
Creates or modifies windows services
- MBAMService.exe (PID: 1024)
Reads Internet Cache Settings
- mbamtray.exe (PID: 2728)
- rundll32.exe (PID: 2344)
- rundll32.exe (PID: 2864)
Uses RUNDLL32.EXE to load library
- mbamtray.exe (PID: 2728)
- mbam.exe (PID: 1732)
Creates files in the user directory
- mbam.exe (PID: 1732)
Searches for installed software
- MBAMService.exe (PID: 1024)
Low-level read access rights to disk partition
- MBAMService.exe (PID: 1024)
INFO
Dropped object may contain Bitcoin addresses
- MBAMInstallerService.exe (PID: 1536)
- MBAMService.exe (PID: 1024)
Reads settings of System Certificates
- MBAMService.exe (PID: 1024)
Reads the hosts file
- MBAMService.exe (PID: 1024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:10:21 16:30:43+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14.15 |
| CodeSize: | 418816 |
| InitializedDataSize: | 1443328 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x296e4 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.0.0.108 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Malwarebytes |
| FileDescription: | Malwarebytes |
| FileVersion: | 4.0.0.108 |
| LegalCopyright: | Copyright (C) 2017 - 2019 Malwarebytes, Inc. All rights reserved. |
| InternalName: | MBSetup.exe |
| OriginalFileName: | MBSetup.exe |
| ProductVersion: | 4.0.0.108 |
| ProductName: | Malwarebytes |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 21-Oct-2019 14:30:43 |
| Detected languages: |
|
| Debug artifacts: |
|
| CompanyName: | Malwarebytes |
| FileDescription: | Malwarebytes |
| FileVersion: | 4.0.0.108 |
| LegalCopyright: | Copyright (C) 2017 - 2019 Malwarebytes, Inc. All rights reserved. |
| InternalName: | MBSetup.exe |
| OriginalFilename: | MBSetup.exe |
| ProductVersion: | 4.0.0.108 |
| ProductName: | Malwarebytes |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 21-Oct-2019 14:30:43 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0006628D | 0x00066400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.63275 |
.rdata | 0x00068000 | 0x0001A0B8 | 0x0001A200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.17702 |
.data | 0x00083000 | 0x00004ED8 | 0x00002A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.38103 |
.rsrc | 0x00088000 | 0x0013B420 | 0x0013B600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.69578 |
.reloc | 0x001C4000 | 0x00005C18 | 0x00005E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.62209 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.16648 | 1842 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.77507 | 67624 | UNKNOWN | English - United States | RT_ICON |
3 | 4.01467 | 16936 | UNKNOWN | English - United States | RT_ICON |
4 | 4.15499 | 9640 | UNKNOWN | English - United States | RT_ICON |
5 | 4.31512 | 4264 | UNKNOWN | English - United States | RT_ICON |
6 | 4.69584 | 1128 | UNKNOWN | English - United States | RT_ICON |
7 | 4.9625 | 266 | UNKNOWN | UNKNOWN | RT_STRING |
8 | 3.52137 | 110 | UNKNOWN | UNKNOWN | RT_STRING |
9 | 2.1346 | 2216 | UNKNOWN | English - United States | RT_ICON |
10 | 5.354 | 618 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
ADVAPI32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
WINHTTP.dll |
ole32.dll |
Total processes
66
Monitored processes
20
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
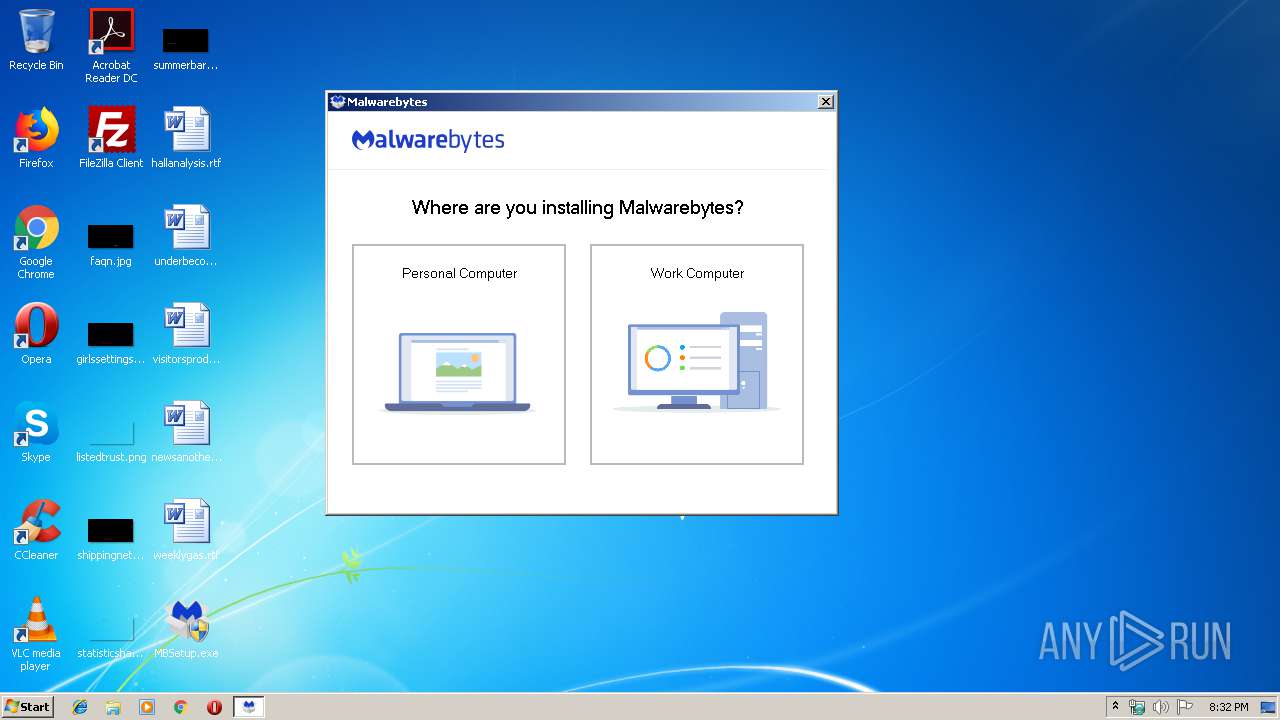
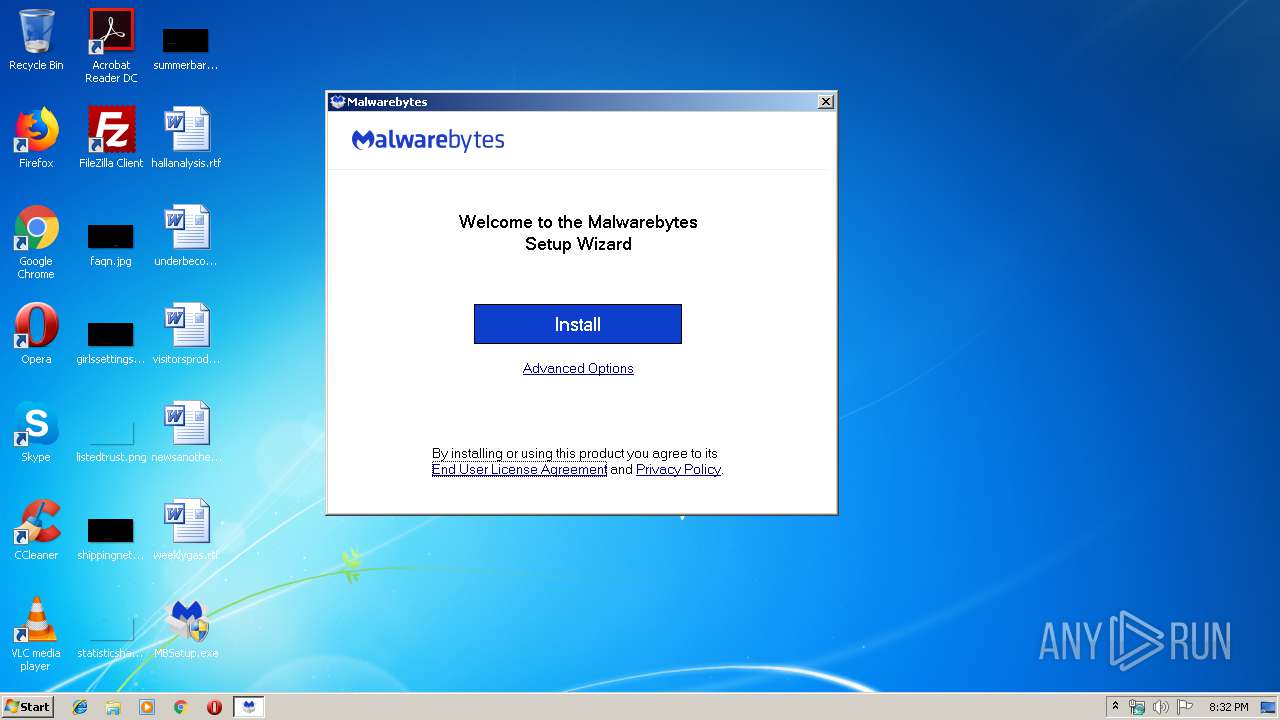
| 616 | "C:\Users\admin\Desktop\MBSetup.exe" | C:\Users\admin\Desktop\MBSetup.exe | explorer.exe | ||||||||||||
User: admin Company: Malwarebytes Integrity Level: HIGH Description: Malwarebytes Exit code: 0 Version: 4.0.0.108 Modules
| |||||||||||||||
| 892 | "C:\Users\admin\Desktop\MBSetup.exe" | C:\Users\admin\Desktop\MBSetup.exe | — | explorer.exe | |||||||||||
User: admin Company: Malwarebytes Integrity Level: MEDIUM Description: Malwarebytes Exit code: 3221226540 Version: 4.0.0.108 | |||||||||||||||
| 1024 | "C:\Program Files\Malwarebytes\Anti-Malware\MBAMService.exe" | C:\Program Files\Malwarebytes\Anti-Malware\MBAMService.exe | services.exe | ||||||||||||
User: SYSTEM Company: Malwarebytes Integrity Level: SYSTEM Description: Malwarebytes Service Exit code: 0 Version: 3.2.0.874 Modules
| |||||||||||||||
| 1488 | "C:\Program Files\Malwarebytes\Anti-Malware\assistant.exe" --showdashboard | C:\Program Files\Malwarebytes\Anti-Malware\assistant.exe | — | mbamtray.exe | |||||||||||
User: admin Company: Malwarebytes Integrity Level: MEDIUM Description: Malwarebytes Assistant Exit code: 0 Version: 4.0.0.443 Modules
| |||||||||||||||
| 1536 | "C:\Program Files\Malwarebytes\Anti-Malware\MBAMInstallerService.exe" | C:\Program Files\Malwarebytes\Anti-Malware\MBAMInstallerService.exe | services.exe | ||||||||||||
User: SYSTEM Company: Malwarebytes Integrity Level: SYSTEM Description: Malwarebytes Installer Service Exit code: 0 Version: 4.0.0.130 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\Malwarebytes\Anti-Malware\mbam.exe" | C:\Program Files\Malwarebytes\Anti-Malware\mbam.exe | MBSetup.exe | ||||||||||||
User: admin Company: Malwarebytes Integrity Level: MEDIUM Description: Malwarebytes Exit code: 0 Version: 4.0.0.443 Modules
| |||||||||||||||
| 2152 | C:\Windows\system32\cmd.exe /c "C:\Program Files\Malwarebytes\Anti-Malware\MBAMService.exe" /Service | C:\Windows\system32\cmd.exe | — | MBAMInstallerService.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2168 | C:\Windows\system32\cmd.exe /c certutil.exe -f -addstore root "C:\Windows\TEMP\InstallTemp\servicepkg\DigiCertEVRoot.crt" | C:\Windows\system32\cmd.exe | — | MBAMInstallerService.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2276 | ig.exe secure | C:\Users\admin\AppData\LocalLow\ig.exe | — | MBAMService.exe | |||||||||||
User: admin Company: MalwareBytes Integrity Level: LOW Description: Malware Scanner Exit code: 3235811341 Version: 1.0.0.27 Modules
| |||||||||||||||
| 2344 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | mbamtray.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 329
Read events
919
Write events
1 403
Delete events
7
Modification events
| (PID) Process: | (616) MBSetup.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (616) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | ProductCode |
Value: MBAM-C | |||
| (PID) Process: | (616) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | ProgramDirectory |
Value: C:\Program Files\Malwarebytes\Anti-Malware | |||
| (PID) Process: | (616) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | Channel |
Value: /release | |||
| (PID) Process: | (616) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | Installer |
Value: C:\Users\admin\Desktop\MBSetup.exe | |||
| (PID) Process: | (616) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | Silent |
Value: false | |||
| (PID) Process: | (616) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | Reboot |
Value: true | |||
| (PID) Process: | (616) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | Staging |
Value: false | |||
| (PID) Process: | (616) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | CreateIcon |
Value: true | |||
| (PID) Process: | (616) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | BifucationShown |
Value: true | |||
Executable files
288
Suspicious files
110
Text files
1 104
Unknown types
72
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1536 | MBAMInstallerService.exe | C:\Windows\TEMP\InstallTemp\servicepkg.7z | — | |
MD5:— | SHA256:— | |||
| 1536 | MBAMInstallerService.exe | C:\Windows\TEMP\InstallTemp\ctlrpkg.7z | — | |
MD5:— | SHA256:— | |||
| 1536 | MBAMInstallerService.exe | C:\Windows\TEMP\InstallTemp\dbclspkg.7z | — | |
MD5:— | SHA256:— | |||
| 616 | MBSetup.exe | C:\Program Files\Malwarebytes\Anti-Malware\MBAMInstallerService.exe | executable | |
MD5:— | SHA256:— | |||
| 1536 | MBAMInstallerService.exe | C:\Windows\TEMP\InstallTemp\servicepkg\AEControllerCOM.dll | executable | |
MD5:— | SHA256:— | |||
| 1536 | MBAMInstallerService.exe | C:\Windows\TEMP\InstallTemp\servicepkg\srvversion.dat | text | |
MD5:— | SHA256:— | |||
| 1536 | MBAMInstallerService.exe | C:\Windows\TEMP\InstallTemp\servicepkg\CloudControllerCOM.dll | executable | |
MD5:— | SHA256:— | |||
| 1536 | MBAMInstallerService.exe | C:\Windows\TEMP\InstallTemp\servicepkg\LogControllerCOM.dll | executable | |
MD5:— | SHA256:— | |||
| 1536 | MBAMInstallerService.exe | C:\Windows\TEMP\InstallTemp\servicepkg\CleanControllerCOM.dll | executable | |
MD5:— | SHA256:— | |||
| 1536 | MBAMInstallerService.exe | C:\Windows\TEMP\InstallTemp\servicepkg\PoliciesControllerCOM.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
30
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1024 | MBAMService.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA%2BoSQYV1wCgviF2%2FcXsbb0%3D | US | der | 471 b | whitelisted |
1024 | MBAMService.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSYagvY3tfizDNoybzVSPFZmSEm0wQUe2jOKarAF75JeuHlP9an90WPNTICEAii7E54oJ4XSxkuVTWYS1k%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
616 | MBSetup.exe | 3.82.89.44:443 | ark.mwbsys.com | — | US | unknown |
616 | MBSetup.exe | 23.210.248.238:443 | cdn.mwbsys.com | Akamai International B.V. | NL | whitelisted |
1536 | MBAMInstallerService.exe | 3.82.89.44:443 | ark.mwbsys.com | — | US | unknown |
1536 | MBAMInstallerService.exe | 23.210.248.238:443 | cdn.mwbsys.com | Akamai International B.V. | NL | whitelisted |
1024 | MBAMService.exe | 54.186.245.210:443 | telemetry.malwarebytes.com | Amazon.com, Inc. | US | unknown |
1024 | MBAMService.exe | 54.172.81.225:443 | keystone.mwbsys.com | Amazon.com, Inc. | US | unknown |
2728 | mbamtray.exe | 143.204.214.126:443 | www.malwarebytes.com | — | US | suspicious |
1732 | mbam.exe | 107.23.57.228:443 | cleo.mb-internal.com | Amazon.com, Inc. | US | unknown |
1732 | mbam.exe | 23.210.248.238:443 | cdn.mwbsys.com | Akamai International B.V. | NL | whitelisted |
1732 | mbam.exe | 143.204.214.126:443 | www.malwarebytes.com | — | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ark.mwbsys.com |
| suspicious |
cdn.mwbsys.com |
| whitelisted |
telemetry.malwarebytes.com |
| whitelisted |
keystone.mwbsys.com |
| unknown |
links.malwarebytes.com |
| whitelisted |
cleo.mb-internal.com |
| unknown |
www.malwarebytes.com |
| shared |
prod-www.malwarebytes.com |
| suspicious |
sirius.mwbsys.com |
| suspicious |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
mbamtray.exe | QAxBase::setControl: requested control {F36AD0D0-B5F0-4C69-AF08-603D177FEF0E} could not be instantiated
|
mbamtray.exe | Code : -2147467259
|
mbamtray.exe | Code : -2147467259
|
mbamtray.exe | Source :
|
mbamtray.exe | Description:
|
mbamtray.exe | Help :
|
mbamtray.exe | Connect to the exception(int,QString,QString,QString) signal to catch this exception
|
mbamtray.exe | qt.scenegraph.general: Loading backend software
|
mbamtray.exe | void __thiscall PageStatusMonitor::OnRequestFinished(class QNetworkReply *) "Page: https://links.malwarebytes.com/link/3x_cart?affiliate=&uuid=81e0cbe954fffb2dd4e10325decf35d73a7107c5&x-source=trial-avail&x-action=comparison_chart&x-token_secret=jgQTeomKKCX-ohzCvjCx3kBoFTSELqVEnjpdujhGKxAWwRzt4h-KGvWhgzcBqySel1QrviDIFDE68IPKpbLb7kOrXDEkHfyDfAM1EL66wmLbLVL57yF4CdAhhtpKrLzy&ADDITIONAL_x-token_secret=jgQTeomKKCX-ohzCvjCx3kBoFTSELqVEnjpdujhGKxAWwRzt4h-KGvWhgzcBqySel1QrviDIFDE68IPKpbLb7kOrXDEkHfyDfAM1EL66wmLbLVL57yF4CdAhhtpKrLzy&x-prodcode=MBAM-C&lang=en&version=4.0.4.49 received code: 307"
|
mbamtray.exe | class QUrl __thiscall PageStatusMonitor::processRedirectUrl(const class QUrl &,const class QUrl &) const Potential Redirect is: "https://cleo.mb-internal.com/?x-source=trial-avail&ADDITIONAL_x-source=inproduct&ADDITIONAL_machineid=81e0cbe954fffb2dd4e10325decf35d73a7107c5&x-action=comparison_chart&ADDITIONAL_x-token_secret=jgQTeomKKCX-ohzCvjCx3kBoFTSELqVEnjpdujhGKxAWwRzt4h-KGvWhgzcBqySel1QrviDIFDE68IPKpbLb7kOrXDEkHfyDfAM1EL66wmLbLVL57yF4CdAhhtpKrLzy&x-token_secret=jgQTeomKKCX-ohzCvjCx3kBoFTSELqVEnjpdujhGKxAWwRzt4h-KGvWhgzcBqySel1QrviDIFDE68IPKpbLb7kOrXDEkHfyDfAM1EL66wmLbLVL57yF4CdAhhtpKrLzy&x-prodcode=MBAM-C&LANG=en" Last Redirect is: ""
|