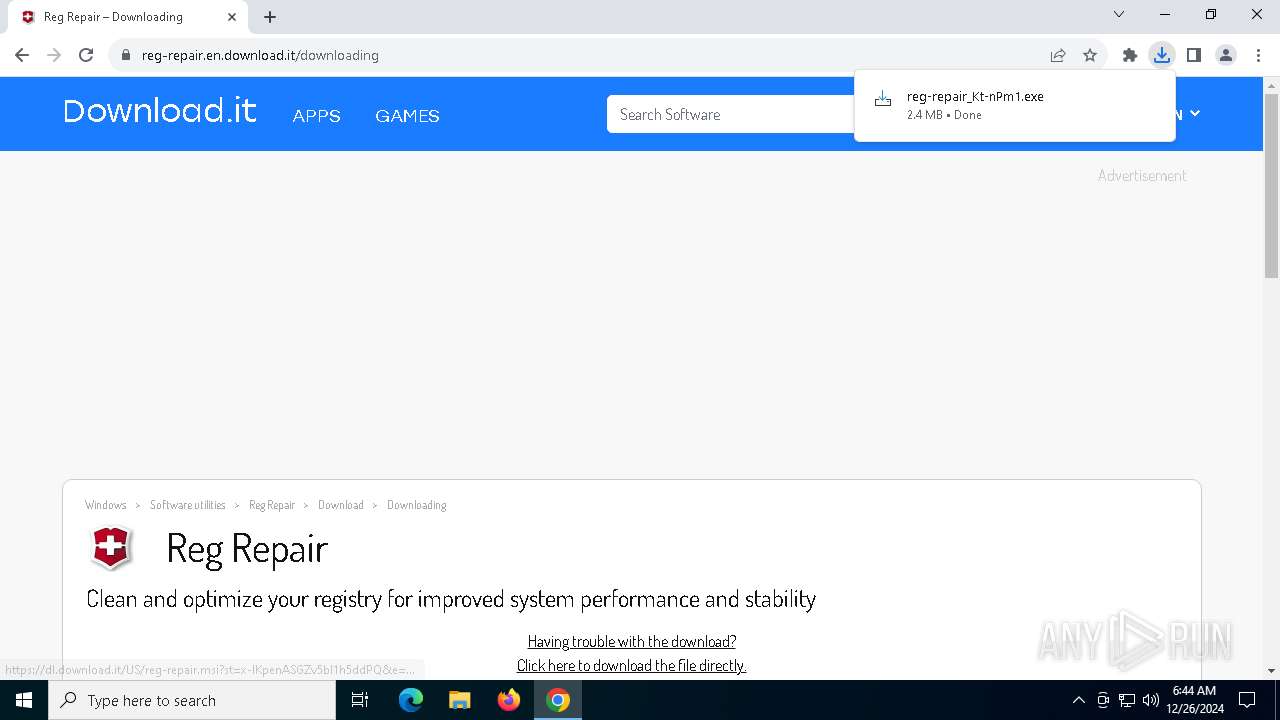
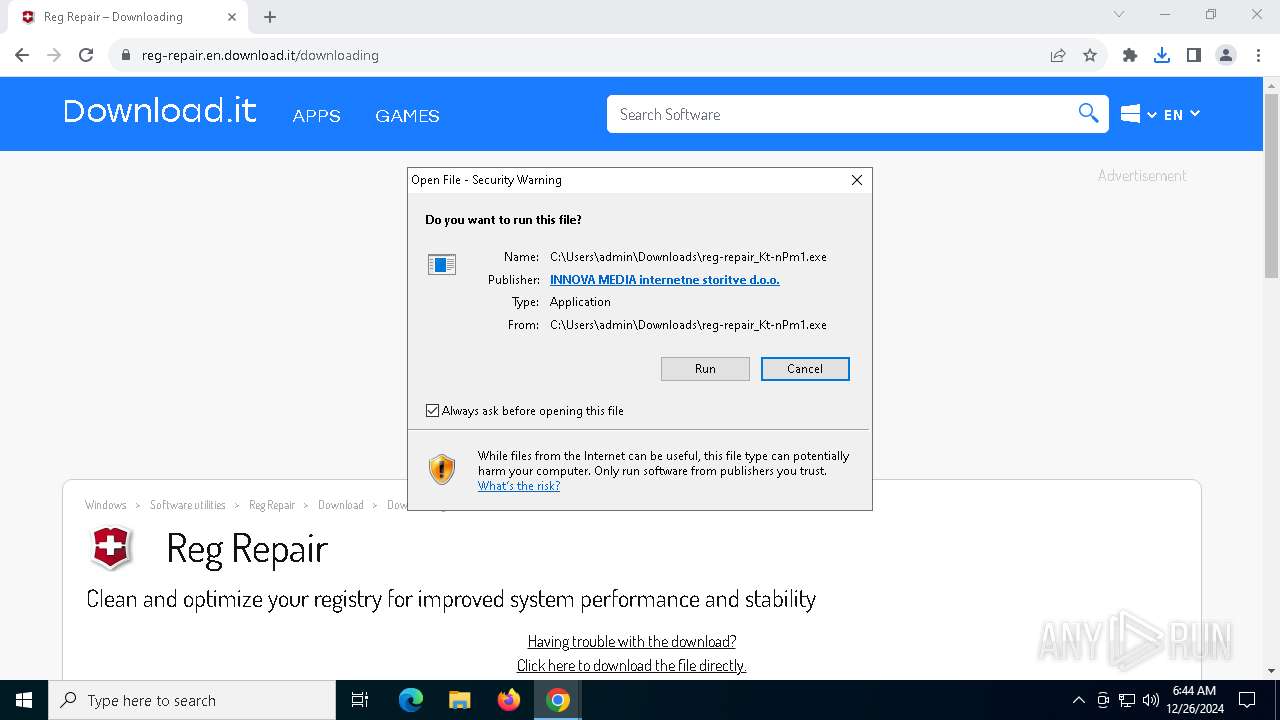
| URL: | download.it |
| Full analysis: | https://app.any.run/tasks/f58a2d1f-8d08-49c3-8192-d7cf541c3519 |
| Verdict: | Malicious activity |
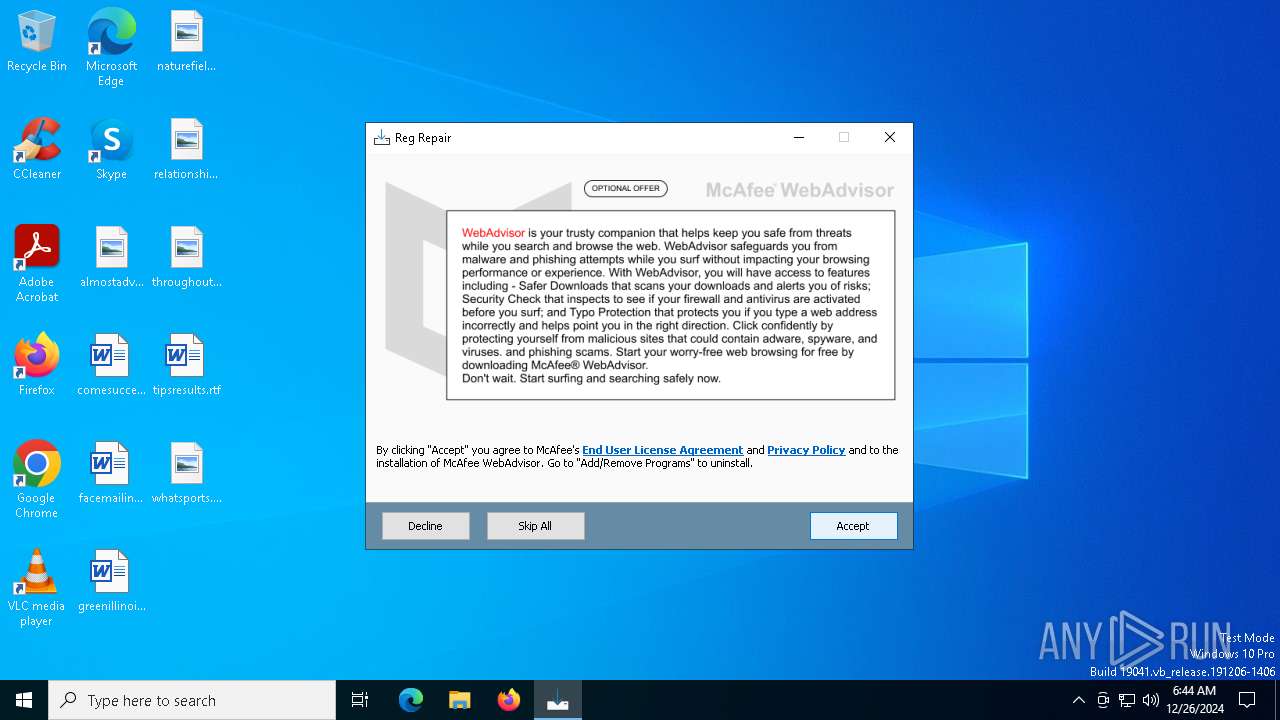
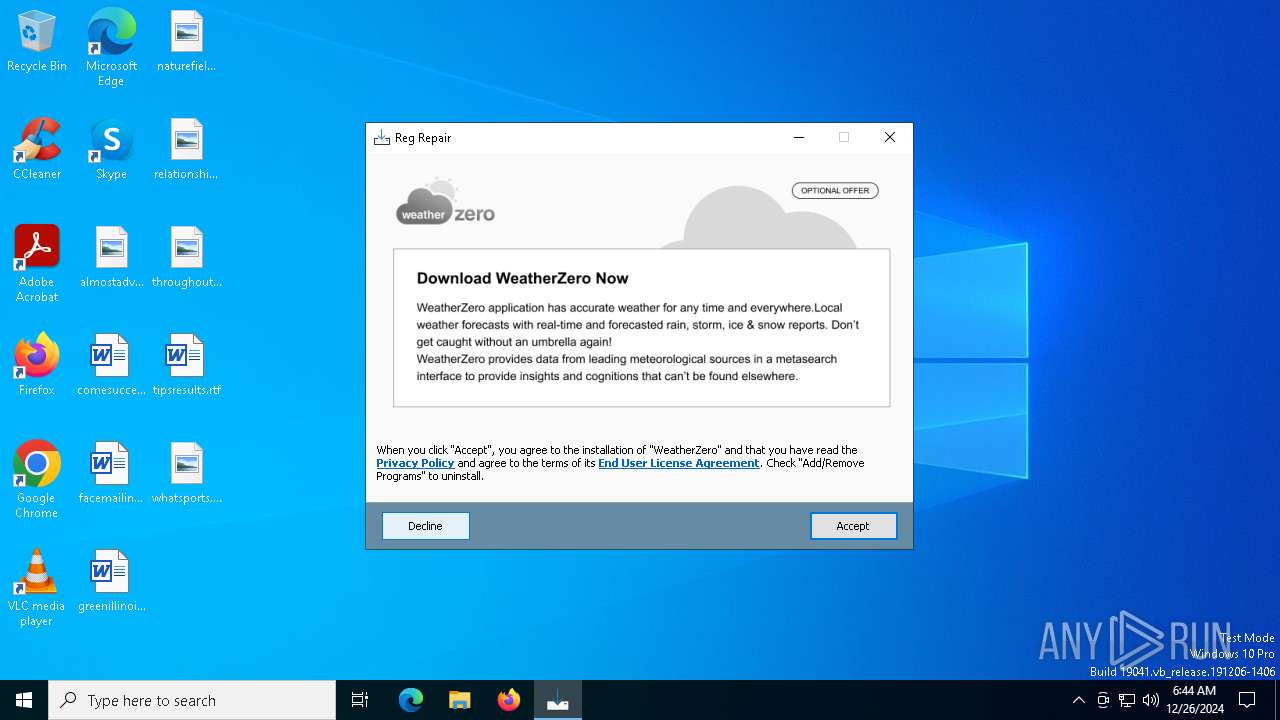
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | December 26, 2024, 06:42:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B2A852D0F40D3DAD4F780D92572B6299 |
| SHA1: | AE7A7A780539DAAC93C6FFEA97D6DEEBABE92290 |
| SHA256: | B999AC63892223C7CC7206734CE0C8CC13CA7273D2B59992D20CF098DD4B8170 |
| SSDEEP: | 3:ZKWQ:ZlQ |
MALICIOUS
INNOSETUP has been detected (SURICATA)
- reg-repair_Kt-nPm1.tmp (PID: 3900)
Starts Visual C# compiler
- WeatherZero.exe (PID: 1988)
SUSPICIOUS
Executable content was dropped or overwritten
- reg-repair_Kt-nPm1.exe (PID: 6248)
- reg-repair_Kt-nPm1.exe (PID: 2736)
- reg-repair_Kt-nPm1.tmp (PID: 3900)
- WZSetup.exe (PID: 4980)
- csc.exe (PID: 6588)
Reads security settings of Internet Explorer
- reg-repair_Kt-nPm1.tmp (PID: 6304)
- reg-repair_Kt-nPm1.tmp (PID: 3900)
- WZSetup.exe (PID: 4980)
- WeatherZero.exe (PID: 1988)
Process drops legitimate windows executable
- reg-repair_Kt-nPm1.tmp (PID: 3900)
Access to an unwanted program domain was detected
- reg-repair_Kt-nPm1.tmp (PID: 3900)
Checks Windows Trust Settings
- WZSetup.exe (PID: 4980)
- WeatherZero.exe (PID: 1988)
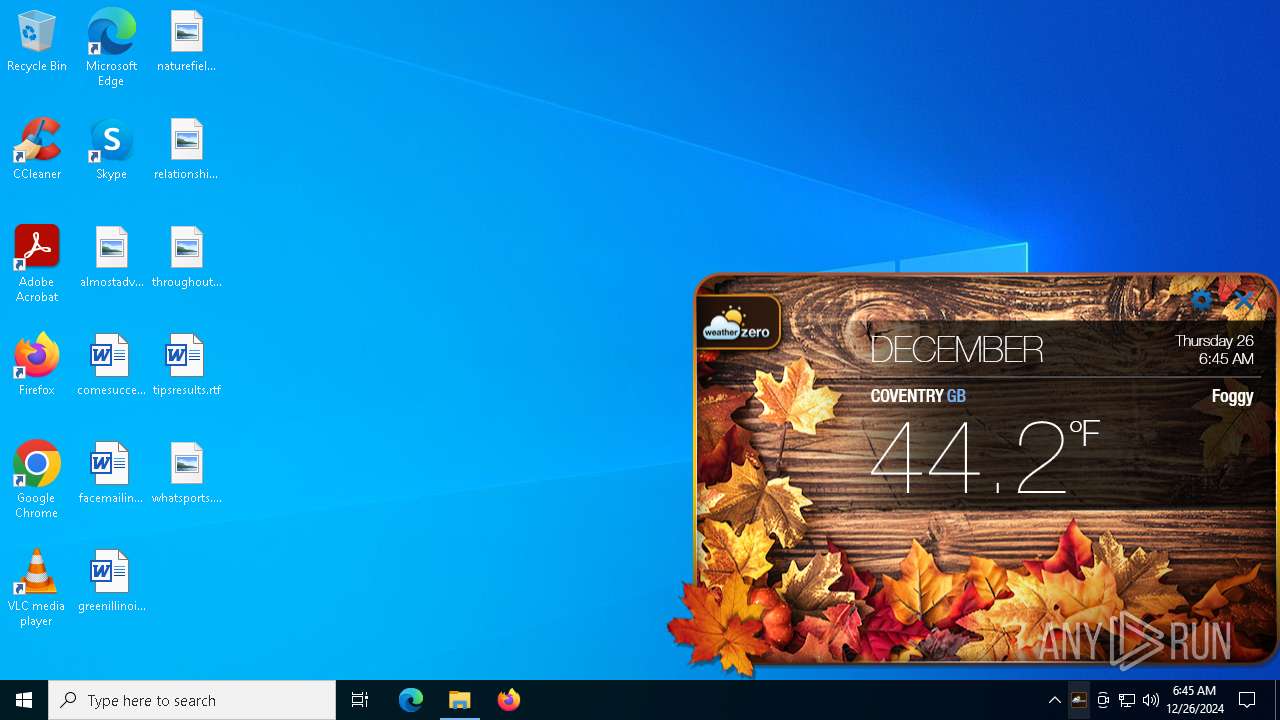
Executes as Windows Service
- WeatherZeroService.exe (PID: 4912)
- PresentationFontCache.exe (PID: 3824)
Creates a software uninstall entry
- WZSetup.exe (PID: 4980)
Searches for installed software
- WZSetup.exe (PID: 4980)
Uses .NET C# to load dll
- WeatherZero.exe (PID: 1988)
Executes application which crashes
- reg-repair_Kt-nPm1.tmp (PID: 3900)
Creates file in the systems drive root
- explorer.exe (PID: 1412)
Checks for external IP
- svchost.exe (PID: 2192)
- WeatherZero.exe (PID: 1988)
INFO
Executable content was dropped or overwritten
- chrome.exe (PID: 3928)
- chrome.exe (PID: 1572)
The sample compiled with english language support
- chrome.exe (PID: 1572)
- reg-repair_Kt-nPm1.tmp (PID: 3900)
- WZSetup.exe (PID: 4980)
Checks supported languages
- reg-repair_Kt-nPm1.exe (PID: 2736)
- reg-repair_Kt-nPm1.tmp (PID: 6304)
- reg-repair_Kt-nPm1.tmp (PID: 3900)
- WZSetup.exe (PID: 4980)
- WeatherZeroService.exe (PID: 6032)
- WeatherZeroService.exe (PID: 4912)
- WeatherZero.exe (PID: 1988)
- cvtres.exe (PID: 6160)
- csc.exe (PID: 6588)
- PresentationFontCache.exe (PID: 3824)
The process uses the downloaded file
- chrome.exe (PID: 1400)
- chrome.exe (PID: 3928)
- chrome.exe (PID: 3848)
- reg-repair_Kt-nPm1.tmp (PID: 3900)
Create files in a temporary directory
- reg-repair_Kt-nPm1.exe (PID: 2736)
- reg-repair_Kt-nPm1.exe (PID: 6248)
- reg-repair_Kt-nPm1.tmp (PID: 3900)
- WZSetup.exe (PID: 4980)
- WeatherZero.exe (PID: 1988)
- csc.exe (PID: 6588)
- cvtres.exe (PID: 6160)
Reads the computer name
- reg-repair_Kt-nPm1.tmp (PID: 6304)
- reg-repair_Kt-nPm1.tmp (PID: 3900)
- WZSetup.exe (PID: 4980)
- WeatherZeroService.exe (PID: 4912)
- WeatherZero.exe (PID: 1988)
Process checks computer location settings
- reg-repair_Kt-nPm1.tmp (PID: 6304)
- reg-repair_Kt-nPm1.tmp (PID: 3900)
Reads the machine GUID from the registry
- reg-repair_Kt-nPm1.tmp (PID: 3900)
- WeatherZeroService.exe (PID: 4912)
- WeatherZero.exe (PID: 1988)
- WZSetup.exe (PID: 4980)
- cvtres.exe (PID: 6160)
- csc.exe (PID: 6588)
- PresentationFontCache.exe (PID: 3824)
Reads the software policy settings
- reg-repair_Kt-nPm1.tmp (PID: 3900)
- WZSetup.exe (PID: 4980)
- WeatherZero.exe (PID: 1988)
- WerFault.exe (PID: 6380)
Checks proxy server information
- reg-repair_Kt-nPm1.tmp (PID: 3900)
- WZSetup.exe (PID: 4980)
- WeatherZero.exe (PID: 1988)
- WerFault.exe (PID: 6380)
Application launched itself
- chrome.exe (PID: 3928)
- msedge.exe (PID: 4968)
- msedge.exe (PID: 6800)
- msedge.exe (PID: 4684)
Creates files or folders in the user directory
- WeatherZero.exe (PID: 1988)
- WZSetup.exe (PID: 4980)
- WerFault.exe (PID: 6380)
Manual execution by a user
- msedge.exe (PID: 6800)
Creates files in the program directory
- WZSetup.exe (PID: 4980)
Sends debugging messages
- WeatherZero.exe (PID: 1988)
Reads security settings of Internet Explorer
- explorer.exe (PID: 1412)
Disables trace logs
- WeatherZero.exe (PID: 1988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
229
Monitored processes
91
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 968 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=4976 --field-trial-handle=2368,i,768370448779824164,7069745503873583734,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1304 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3864 --field-trial-handle=2368,i,768370448779824164,7069745503873583734,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=6084 --field-trial-handle=1812,i,9107750076160507969,16105481033758343262,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1400 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=6392 --field-trial-handle=1812,i,9107750076160507969,16105481033758343262,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1412 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1520 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=23 --mojo-platform-channel-handle=6596 --field-trial-handle=1812,i,9107750076160507969,16105481033758343262,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1544 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4360 --field-trial-handle=2372,i,4484225217775458750,7888598622318649798,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1544 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2540 --field-trial-handle=2368,i,768370448779824164,7069745503873583734,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1556 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5540 --field-trial-handle=2372,i,4484225217775458750,7888598622318649798,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1572 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5688 --field-trial-handle=1812,i,9107750076160507969,16105481033758343262,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
37 498
Read events
37 368
Write events
104
Delete events
26
Modification events
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Spelling\Dictionaries |
| Operation: | delete value | Name: | en-US |
Value: | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Spelling\Dictionaries |
| Operation: | delete value | Name: | en |
Value: | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Spelling\Dictionaries |
| Operation: | delete value | Name: | _Global_ |
Value: | |||
| (PID) Process: | (3848) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000D6CE99886157DB01 | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\RLZs |
| Operation: | write | Name: | C1 |
Value: 1C1GCEB_enGB1142GB1142 | |||
Executable files
30
Suspicious files
425
Text files
128
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3928 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF135f4a.TMP | — | |
MD5:— | SHA256:— | |||
| 3928 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3928 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF135f4a.TMP | — | |
MD5:— | SHA256:— | |||
| 3928 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF135f4a.TMP | — | |
MD5:— | SHA256:— | |||
| 3928 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3928 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF135f4a.TMP | — | |
MD5:— | SHA256:— | |||
| 3928 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3928 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF135f4a.TMP | — | |
MD5:— | SHA256:— | |||
| 3928 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3928 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
207
DNS requests
238
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.23:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4132 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3080 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
4132 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6268 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3080 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
3080 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
188 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.23:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.16.110.121:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
3928 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6472 | chrome.exe | 104.22.56.224:443 | download.it | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
download.it |
| unknown |
accounts.google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
static.download.it |
| unknown |
fonts.googleapis.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6472 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6472 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6472 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6472 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
3900 | reg-repair_Kt-nPm1.tmp | Possibly Unwanted Program Detected | ADWARE [ANY.RUN] InnoSetup Installer |
2192 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
1988 | WeatherZero.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
Process | Message |
|---|---|
WeatherZero.exe | Load config error: System.InvalidOperationException: There is an error in XML document (0, 0). ---> System.Xml.XmlException: Root element is missing.
at System.Xml.XmlTextReaderImpl.Throw(Exception e)
at System.Xml.XmlTextReaderImpl.ThrowWithoutLineInfo(String res)
at System.Xml.XmlTextReaderImpl.ParseDocumentContent()
at System.Xml.XmlTextReaderImpl.Read()
at System.Xml.XmlTextReader.Read()
at System.Xml.XmlReader.MoveToContent()
at Microsoft.Xml.Serialization.GeneratedAssembly.XmlSerializationReaderWFSettings.Read5_WFSettings()
--- End of inner exception stack trace ---
at System.Xml.Serialization.XmlSerializer.Deserialize(XmlReader xmlReader, String encodingStyle, XmlDeserializationEvents events)
at System.Xml.Serialization.XmlSerializer.Deserialize(TextReader textReader)
at WeatherZero.Config`1.Load()
|
WeatherZero.exe | Load config error: System.InvalidOperationException: There is an error in XML document (0, 0). ---> System.Xml.XmlException: Root element is missing.
at System.Xml.XmlTextReaderImpl.Throw(Exception e)
at System.Xml.XmlTextReaderImpl.ThrowWithoutLineInfo(String res)
at System.Xml.XmlTextReaderImpl.ParseDocumentContent()
at System.Xml.XmlTextReaderImpl.Read()
at System.Xml.XmlTextReader.Read()
at System.Xml.XmlReader.MoveToContent()
at Microsoft.Xml.Serialization.GeneratedAssembly.XmlSerializationReaderWFSettings.Read5_WFSettings()
--- End of inner exception stack trace ---
at System.Xml.Serialization.XmlSerializer.Deserialize(XmlReader xmlReader, String encodingStyle, XmlDeserializationEvents events)
at System.Xml.Serialization.XmlSerializer.Deserialize(TextReader textReader)
at WeatherZero.Config`1.Load()
|
WeatherZero.exe | Get weather thread started
|
WeatherZero.exe | ter)
at System.Windows.Threading.ExceptionWrapper.TryCatchWhen(Object source, Delegate callback, Object args, Boolean isSingleParameter, Delegate catchHandler)
WRN: Assembly binding logging is turned OFF.
To enable assembly bind failure logging, set the registry value [HKLM\Software\Microsoft\Fusion!EnableLog] (DWORD) to 1.
Note: There is some performance penalty associated with assembly bind failure logging.
To turn this feature off, remove the registry value [HKLM\Software\Microsoft\Fusion!EnableLog].
|
WeatherZero.exe | Unhandled exception
System.IO.FileLoadException: Could not load file or assembly 'WeatherZero, Culture=neutral' or one of its dependencies. The located assembly's manifest definition does not match the assembly reference. (Exception from HRESULT: 0x80131040)
File name: 'WeatherZero, Culture=neutral'
at System.Reflection.Assembly._nLoad(AssemblyName fileName, String codeBase, Evidence assemblySecurity, Assembly locationHint, StackCrawlMark& stackMark, Boolean throwOnFileNotFound, Boolean forIntrospection)
at System.Reflection.Assembly.nLoad(AssemblyName fileName, String codeBase, Evidence assemblySecurity, Assembly locationHint, StackCrawlMark& stackMark, Boolean throwOnFileNotFound, Boolean forIntrospection)
at System.Reflection.Assembly.InternalLoad(AssemblyName assemblyRef, Evidence assemblySecurity, StackCrawlMark& stackMark, Boolean forIntrospection)
at System.Reflection.Assembly.Load(AssemblyName assemblyRef)
at System.Windows.Navigation.BaseUriHelper.GetLoadedAssembly(String assemblyName, String assemblyVersion, String assemblyKey)
at MS.Internal.AppModel.ResourceContainer.GetResourceManagerWrapper(Uri uri, String& partName, Boolean& isContentFile)
at MS.Internal.AppModel.ResourceContainer.GetPartCore(Uri uri)
at System.IO.Packaging.Package.GetPartHelper(Uri partUri)
at System.IO.Packaging.Package.GetPart(Uri partUri)
at System.IO.Packaging.PackWebResponse.CachedResponse.GetResponseStream()
at System.IO.Packaging.PackWebResponse.GetResponseStream()
at System.IO.Packaging.PackWebResponse.get_ContentType()
at System.Windows.Media.Imaging.BitmapDecoder.SetupDecoderFromUriOrStream(Uri uri, Stream stream, BitmapCacheOption cacheOption, Guid& clsId, Boolean& isOriginalWritable, Stream& uriStream, UnmanagedMemoryStream& unmanagedMemoryStream, SafeFileHandle& safeFilehandle)
at System.Windows.Media.Imaging.BitmapDecoder.CreateFromUriOrStream(Uri baseUri, Uri uri, Stream stream, BitmapCreateOptions createOptions, BitmapCacheOption cacheOption, RequestCachePolicy uriCachePolicy, Boolean insertInDecoderCache)
at System.Windows.Media.Imaging.BitmapImage.FinalizeCreation()
at System.Windows.Media.Imaging.BitmapImage.EndInit()
at System.Windows.Media.Imaging.BitmapImage..ctor(Uri uriSource, RequestCachePolicy uriCachePolicy)
at System.Windows.Media.Imaging.BitmapImage..ctor(Uri uriSource)
at WeatherZero.MainWindow.OnWindowLoaded(Object sender, RoutedEventArgs e)
at System.Windows.RoutedEventHandlerInfo.InvokeHandler(Object target, RoutedEventArgs routedEventArgs)
at System.Windows.EventRoute.InvokeHandlersImpl(Object source, RoutedEventArgs args, Boolean reRaised)
at System.Windows.UIElement.RaiseEventImpl(DependencyObject sender, RoutedEventArgs args)
at System.Windows.UIElement.RaiseEvent(RoutedEventArgs e)
at System.Windows.BroadcastEventHelper.BroadcastEvent(DependencyObject root, RoutedEvent routedEvent)
at System.Windows.BroadcastEventHelper.BroadcastLoadedEvent(Object root)
at MS.Internal.LoadedOrUnloadedOperation.DoWork()
at System.Windows.Media.MediaContext.FireLoadedPendingCallbacks()
at System.Windows.Media.MediaContext.FireInvokeOnRenderCallbacks()
at System.Windows.Media.MediaContext.RenderMessageHandlerCore(Object resizedCompositionTarget)
at System.Windows.Media.MediaContext.RenderMessageHandler(Object resizedCompositionTarget)
at System.Windows.Media.MediaContext.Resize(ICompositionTarget resizedCompositionTarget)
at System.Windows.Interop.HwndTarget.OnResize()
at System.Windows.Interop.HwndTarget.HandleMessage(Int32 msg, IntPtr wparam, IntPtr lparam)
at System.Windows.Interop.HwndSource.HwndTargetFilterMessage(IntPtr hwnd, Int32 msg, IntPtr wParam, IntPtr lParam, Boolean& handled)
at MS.Win32.HwndWrapper.WndProc(IntPtr hwnd, Int32 msg, IntPtr wParam, IntPtr lParam, Boolean& handled)
at MS.Win32.HwndSubclass.DispatcherCallbackOperation(Object o)
at System.Windows.Threading.ExceptionWrapper.InternalRealCall(Delegate callback, Object args, Boolean isSingleParame |
WeatherZero.exe | http://api.openweathermap.org/data/2.5/weather?zip=CV1,gb&units=imperial&appid=70297443c6fd8391e3fc4b7b0d344ae5
|
WeatherZero.exe | {"coord":{"lon":-1.5122,"lat":52.4066},"weather":[{"id":741,"main":"Fog","description":"fog","icon":"50n"}],"base":"stations","main":{"temp":44.19,"feels_like":44.19,"temp_min":42.57,"temp_max":45.41,"pressure":1034,"humidity":98,"sea_level":1034,"grnd_level":1022},"visibility":450,"wind":{"speed":2.3,"deg":270},"clouds":{"all":100},"dt":1735195529,"sys":{"type":2,"id":2039874,"country":"GB","sunrise":1735200961,"sunset":1735228640},"timezone":0,"id":0,"name":"Coventry","cod":200}
|
WeatherZero.exe | System.IO.FileLoadException: Could not load file or assembly 'WeatherZero, Culture=neutral' or one of its dependencies. The located assembly's manifest definition does not match the assembly reference. (Exception from HRESULT: 0x80131040)
File name: 'WeatherZero, Culture=neutral'
at System.Reflection.Assembly._nLoad(AssemblyName fileName, String codeBase, Evidence assemblySecurity, Assembly locationHint, StackCrawlMark& stackMark, Boolean throwOnFileNotFound, Boolean forIntrospection)
at System.Reflection.Assembly.nLoad(AssemblyName fileName, String codeBase, Evidence assemblySecurity, Assembly locationHint, StackCrawlMark& stackMark, Boolean throwOnFileNotFound, Boolean forIntrospection)
at System.Reflection.Assembly.InternalLoad(AssemblyName assemblyRef, Evidence assemblySecurity, StackCrawlMark& stackMark, Boolean forIntrospection)
at System.Reflection.Assembly.Load(AssemblyName assemblyRef)
at System.Windows.Navigation.BaseUriHelper.GetLoadedAssembly(String assemblyName, String assemblyVersion, String assemblyKey)
at MS.Internal.AppModel.ResourceContainer.GetResourceManagerWrapper(Uri uri, String& partName, Boolean& isContentFile)
at MS.Internal.AppModel.ResourceContainer.GetPartCore(Uri uri)
at System.IO.Packaging.Package.GetPartHelper(Uri partUri)
at System.IO.Packaging.Package.GetPart(Uri partUri)
at System.IO.Packaging.PackWebResponse.CachedResponse.GetResponseStream()
at System.IO.Packaging.PackWebResponse.GetResponseStream()
at System.IO.Packaging.PackWebResponse.get_ContentType()
at System.Windows.Media.Imaging.BitmapDecoder.SetupDecoderFromUriOrStream(Uri uri, Stream stream, BitmapCacheOption cacheOption, Guid& clsId, Boolean& isOriginalWritable, Stream& uriStream, UnmanagedMemoryStream& unmanagedMemoryStream, SafeFileHandle& safeFilehandle)
at System.Windows.Media.Imaging.BitmapDecoder.CreateFromUriOrStream(Uri baseUri, Uri uri, Stream stream, BitmapCreateOptions createOptions, BitmapCacheOption cacheOption, RequestCachePolicy uriCachePolicy, Boolean insertInDecoderCache)
at System.Windows.Media.Imaging.BitmapImage.FinalizeCreation()
at System.Windows.Media.Imaging.BitmapImage.EndInit()
at System.Windows.Media.Imaging.BitmapImage..ctor(Uri uriSource, RequestCachePolicy uriCachePolicy)
at System.Windows.Media.Imaging.BitmapImage..ctor(Uri uriSource)
at WeatherZero.MainWindow.SetWeatherCondition(EnumWeatherConditions condition)
at WeatherZero.MainWindow.OnWeatherRequestCompleted(Object sender, RequestEventArgs e)
WRN: Assembly binding logging is turned OFF.
To enable assembly bind failure logging, set the registry value [HKLM\Software\Microsoft\Fusion!EnableLog] (DWORD) to 1.
Note: There is some performance penalty associated with assembly bind failure logging.
To turn this feature off, remove the registry value [HKLM\Software\Microsoft\Fusion!EnableLog].
|
WeatherZero.exe | http://api.openweathermap.org/data/2.5/weather?zip=99723,gb&units=imperial&appid=70297443c6fd8391e3fc4b7b0d344ae5
|
WeatherZero.exe | System.Net.WebException: The remote server returned an error: (404) Not Found.
at System.Net.WebClient.DownloadDataInternal(Uri address, WebRequest& request)
at System.Net.WebClient.DownloadString(Uri address)
at System.Net.WebClient.DownloadString(String address)
at WeatherZero.OpenWeatherMap.OpenWeatherMapClass.GetCurrentWeatherByZip(String zipCode, String countryCode, EnumTemperatureUnit unit)
at WeatherZero.Weather.WeatherMan.GetWeatherByCityCode(GetWeatherByZipCodeRequest request)
|