| File name: | x269280.bat |
| Full analysis: | https://app.any.run/tasks/ea8f7a0d-506e-4db5-b5c3-47e2b0bd52ef |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | December 23, 2024, 18:12:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | C36788578D91842B6781CC4A787FFCE7 |
| SHA1: | ED4B8C7F263EFF747416F1F971EBFED6056FF20A |
| SHA256: | B89BC4C948D65DB77EA54A7C34ABB0DE5080CBD71B7E8AB38EF78A069B8F825B |
| SSDEEP: | 12:EfQBu0YBKYoV5BQx1ijBG2BGfxBlc09B13Bu09QB1sYocYoU:xBeBQQxaBG2BGfxBe09B1BHQBy |
MALICIOUS
ZEPHYR has been detected
- xcopy.exe (PID: 6680)
- xcopy.exe (PID: 5400)
- printui.exe (PID: 6356)
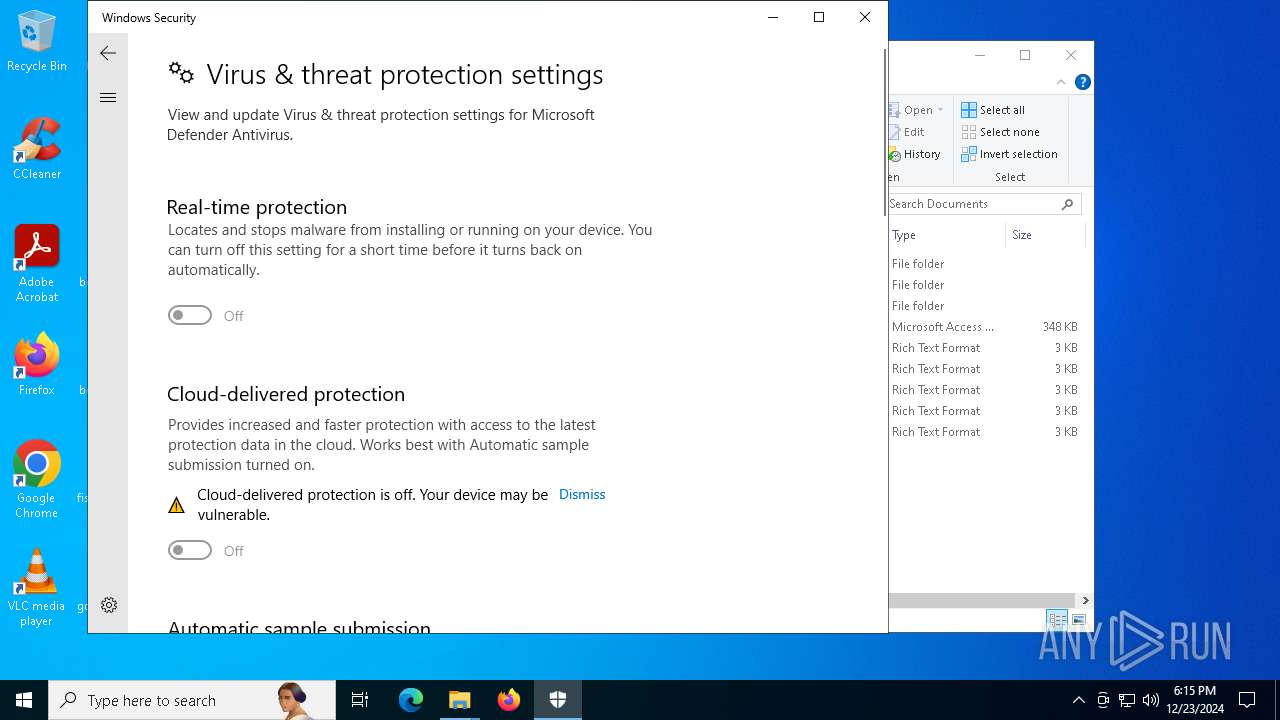
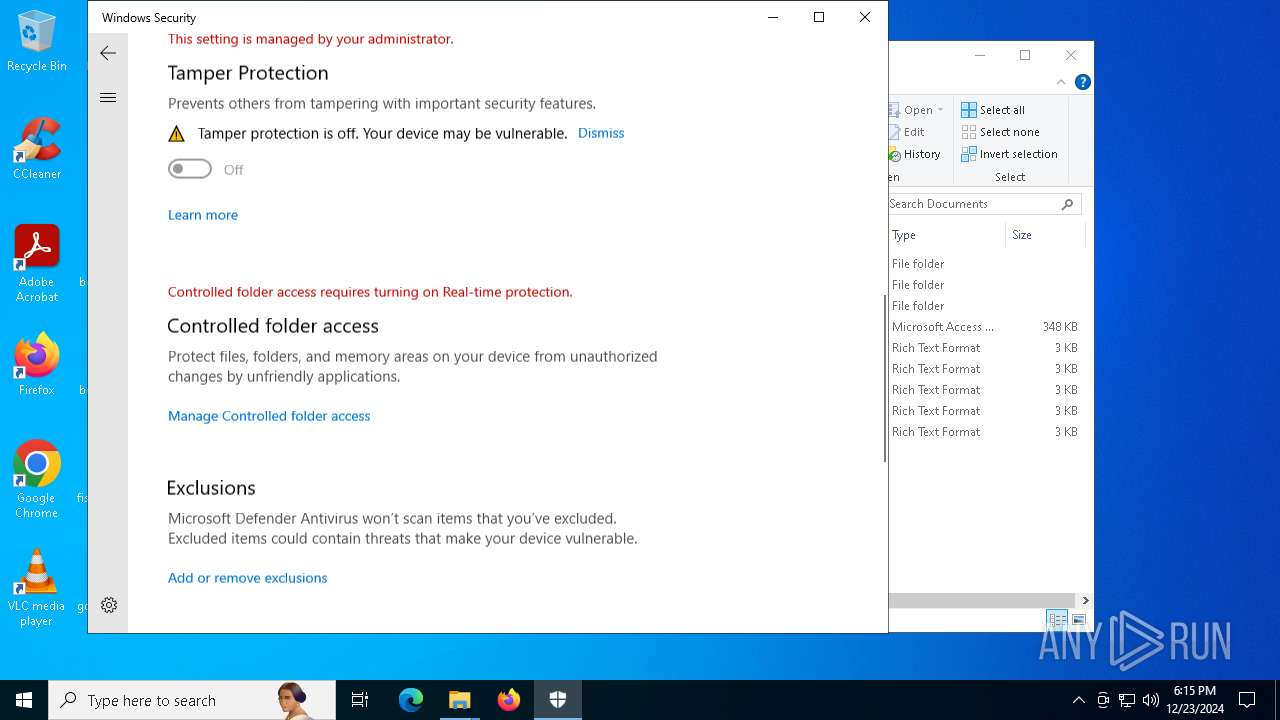
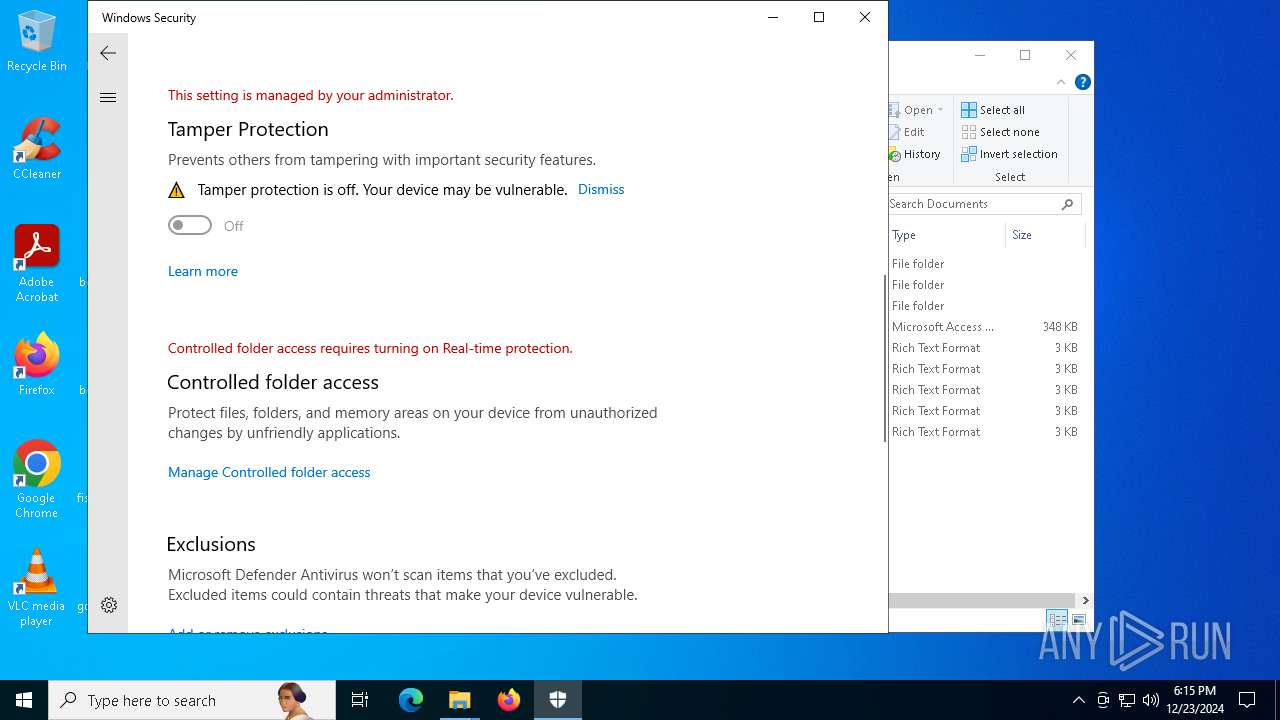
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 6476)
- printui.exe (PID: 6356)
- cmd.exe (PID: 6204)
- cmd.exe (PID: 2452)
- cmd.exe (PID: 6216)
Starts CMD.EXE for self-deleting
- printui.exe (PID: 6356)
Creates or modifies Windows services
- reg.exe (PID: 3560)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 3224)
SUSPICIOUS
Starts application with an unusual extension
- cmd.exe (PID: 6396)
- cmd.exe (PID: 5464)
Process copies executable file
- cmd.exe (PID: 6396)
- cmd.exe (PID: 5464)
Executable content was dropped or overwritten
- xcopy.exe (PID: 6680)
- printui.exe (PID: 6356)
- xcopy.exe (PID: 5400)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6164)
- printui.exe (PID: 6356)
- console_zero.exe (PID: 6092)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6164)
Executing commands from a ".bat" file
- wscript.exe (PID: 6164)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7044)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7092)
- cmd.exe (PID: 6476)
- cmd.exe (PID: 2452)
- cmd.exe (PID: 6204)
- cmd.exe (PID: 6216)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 7092)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 6476)
- cmd.exe (PID: 2452)
- cmd.exe (PID: 6204)
- cmd.exe (PID: 6216)
Process drops legitimate windows executable
- printui.exe (PID: 6356)
The process drops C-runtime libraries
- printui.exe (PID: 6356)
Starts SC.EXE for service management
- cmd.exe (PID: 5488)
Creates a new Windows service
- sc.exe (PID: 6816)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5488)
Windows service management via SC.EXE
- sc.exe (PID: 5028)
The process deletes folder without confirmation
- printui.exe (PID: 6356)
Reads security settings of Internet Explorer
- SecHealthUI.exe (PID: 6980)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6156)
- cmd.exe (PID: 2144)
INFO
Checks supported languages
- chcp.com (PID: 6460)
- chcp.com (PID: 6252)
- printui.exe (PID: 6356)
- console_zero.exe (PID: 6092)
- SecHealthUI.exe (PID: 6980)
Changes the display of characters in the console
- cmd.exe (PID: 6396)
- cmd.exe (PID: 5464)
The sample compiled with english language support
- xcopy.exe (PID: 6680)
- xcopy.exe (PID: 5400)
- printui.exe (PID: 6356)
Reads security settings of Internet Explorer
- explorer.exe (PID: 6640)
- explorer.exe (PID: 6864)
Manual execution by a user
- WinRAR.exe (PID: 4308)
- wscript.exe (PID: 6164)
The process uses the downloaded file
- wscript.exe (PID: 6164)
- WinRAR.exe (PID: 4308)
- cmd.exe (PID: 5464)
- powershell.exe (PID: 6488)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 6904)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- printui.exe (PID: 6356)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7044)
- powershell.exe (PID: 6340)
- powershell.exe (PID: 6488)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 6904)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7044)
- powershell.exe (PID: 6340)
- powershell.exe (PID: 6488)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 6904)
Sends debugging messages
- SecHealthUI.exe (PID: 6980)
Reads the computer name
- SecHealthUI.exe (PID: 6980)
Checks transactions between databases Windows and Oracle
- SecurityHealthHost.exe (PID: 4596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
193
Monitored processes
58
Malicious processes
7
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 648 | xcopy "x325336.dat" "C:\Windows \System32" /Y | C:\Windows\System32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2144 | cmd.exe /c timeout /t 16 /nobreak && del /q "C:\Windows\System32\svculdr64.dat" | C:\Windows\System32\cmd.exe | — | printui.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2260 | timeout /t 16 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2452 | cmd.exe /c powershell -Command Add-MpPreference -ExclusionPath 'c:\windows\system32' | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2484 | C:\Windows\System32\SecurityHealthHost.exe {E041C90B-68BA-42C9-991E-477B73A75C90} -Embedding | C:\Windows\System32\SecurityHealthHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Security Health Host Exit code: 0 Version: 4.18.1907.16384 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2512 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3172 | powershell -Command Add-MpPreference -ExclusionPath 'C:\Windows \System32' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3224 | cmd.exe /c schtasks /create /tn "console_zero" /sc ONLOGON /tr "C:\Windows\System32\console_zero.exe" /rl HIGHEST /f | C:\Windows\System32\cmd.exe | console_zero.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3560 | explorer "..\NEW VOLUME" | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
45 917
Read events
45 861
Write events
55
Delete events
1
Modification events
| (PID) Process: | (6640) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | MinimizedStateTabletModeOff |
Value: 0 | |||
| (PID) Process: | (6640) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | QatItems |
Value: 3C7369713A637573746F6D554920786D6C6E733A7369713D22687474703A2F2F736368656D61732E6D6963726F736F66742E636F6D2F77696E646F77732F323030392F726962626F6E2F716174223E3C7369713A726962626F6E206D696E696D697A65643D2266616C7365223E3C7369713A71617420706F736974696F6E3D2230223E3C7369713A736861726564436F6E74726F6C733E3C7369713A636F6E74726F6C206964513D227369713A3136313238222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3136313239222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333532222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333834222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333336222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333537222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C2F7369713A736861726564436F6E74726F6C733E3C2F7369713A7161743E3C2F7369713A726962626F6E3E3C2F7369713A637573746F6D55493E | |||
| (PID) Process: | (6640) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar\ShellBrowser |
| Operation: | write | Name: | ITBar7Layout |
Value: 13000000000000000000000020000000100000000000000001000000010700005E01000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6640) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6640) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 040000000E0000000300000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (6640) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (6640) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 105 | |||
| (PID) Process: | (6640) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 0AA8696700000000 | |||
| (PID) Process: | (6640) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (6640) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
Executable files
15
Suspicious files
4
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
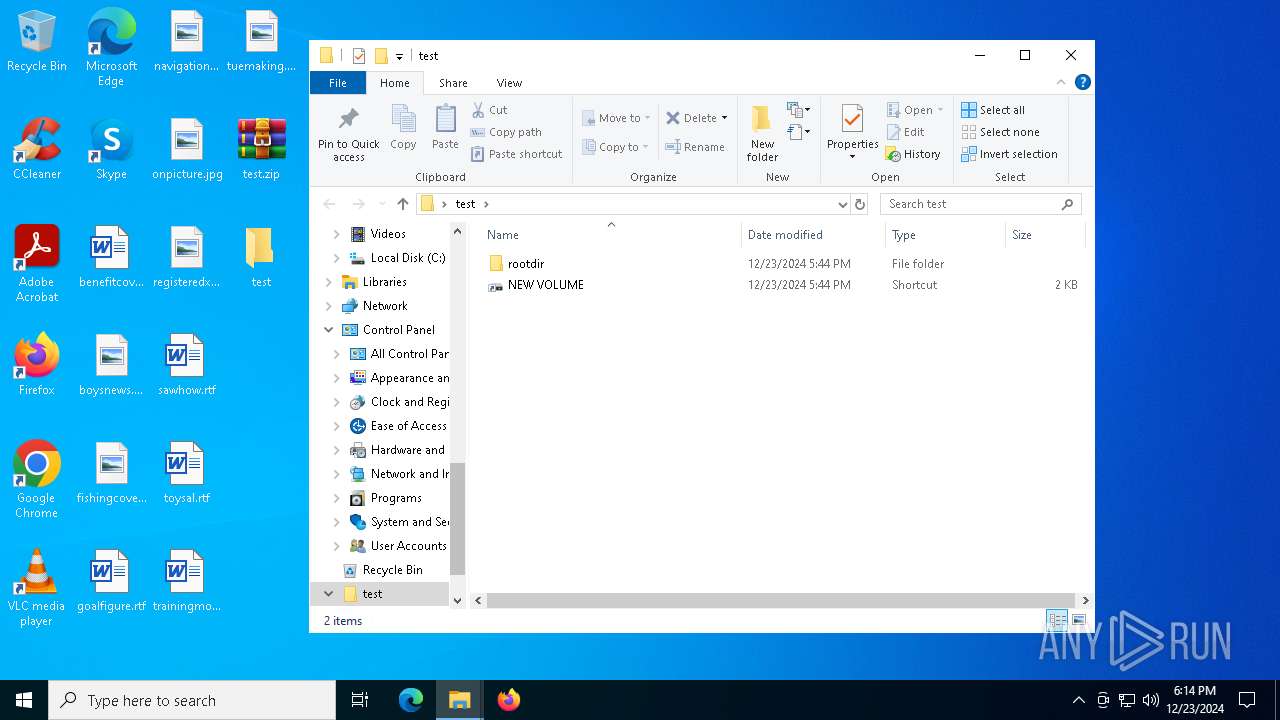
| 4308 | WinRAR.exe | C:\Users\admin\Desktop\test\rootdir\x325336.dat | — | |
MD5:— | SHA256:— | |||
| 648 | xcopy.exe | C:\Windows \System32\x325336.dat | — | |
MD5:— | SHA256:— | |||
| 5464 | cmd.exe | C:\Windows \System32\printui.dll | — | |
MD5:— | SHA256:— | |||
| 4308 | WinRAR.exe | C:\Users\admin\Desktop\test\rootdir\x269280.bat | text | |
MD5:C36788578D91842B6781CC4A787FFCE7 | SHA256:B89BC4C948D65DB77EA54A7C34ABB0DE5080CBD71B7E8AB38EF78A069B8F825B | |||
| 6680 | xcopy.exe | C:\Windows \System32\printui.exe | executable | |
MD5:E43252474ADF63E69B1FC65D202D88C3 | SHA256:53DB039D9D46F2F3F80DF42C8BA48BB96CE4FB96C1BFCE5CD61514A7FF369411 | |||
| 4308 | WinRAR.exe | C:\Users\admin\Desktop\test\rootdir\x506012.vbs | text | |
MD5:69F66D671DD0802C35D9C8D33A13F567 | SHA256:1C34AA75C894BC75E83298DDE7519D8347EBBCF2F2B7A03051407F4B31CC930B | |||
| 5400 | xcopy.exe | C:\Windows \System32\printui.exe | executable | |
MD5:E43252474ADF63E69B1FC65D202D88C3 | SHA256:53DB039D9D46F2F3F80DF42C8BA48BB96CE4FB96C1BFCE5CD61514A7FF369411 | |||
| 6340 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_h5fupgxo.gng.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7044 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_voz03abi.gz0.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6356 | printui.exe | C:\Windows\System32\svculdr64.dat | executable | |
MD5:274B1840839ADB90CE331A7C702BD83A | SHA256:469CCF15CFAAD396E385C553E4EAB9239A10BAB1C7D6505D31D38FB1C15AE4BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
44
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3296 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3296 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6240 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6240 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
372 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.209.189:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3296 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3296 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4160 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |