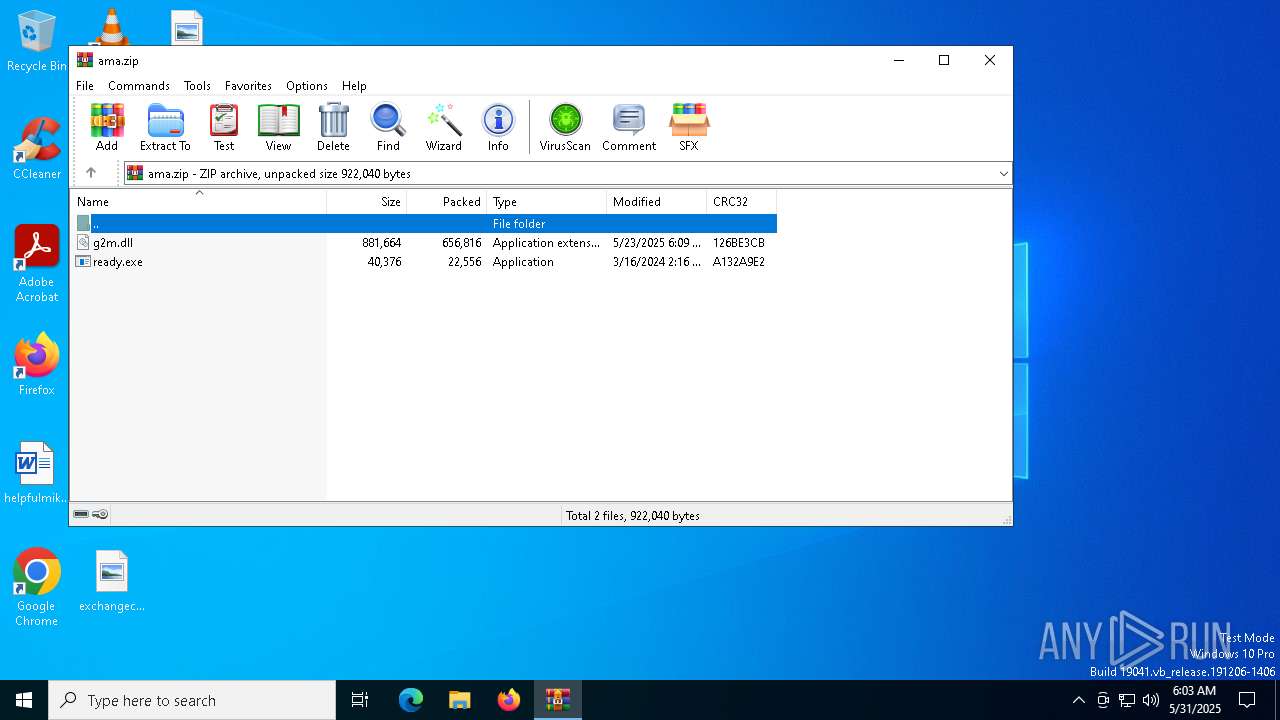
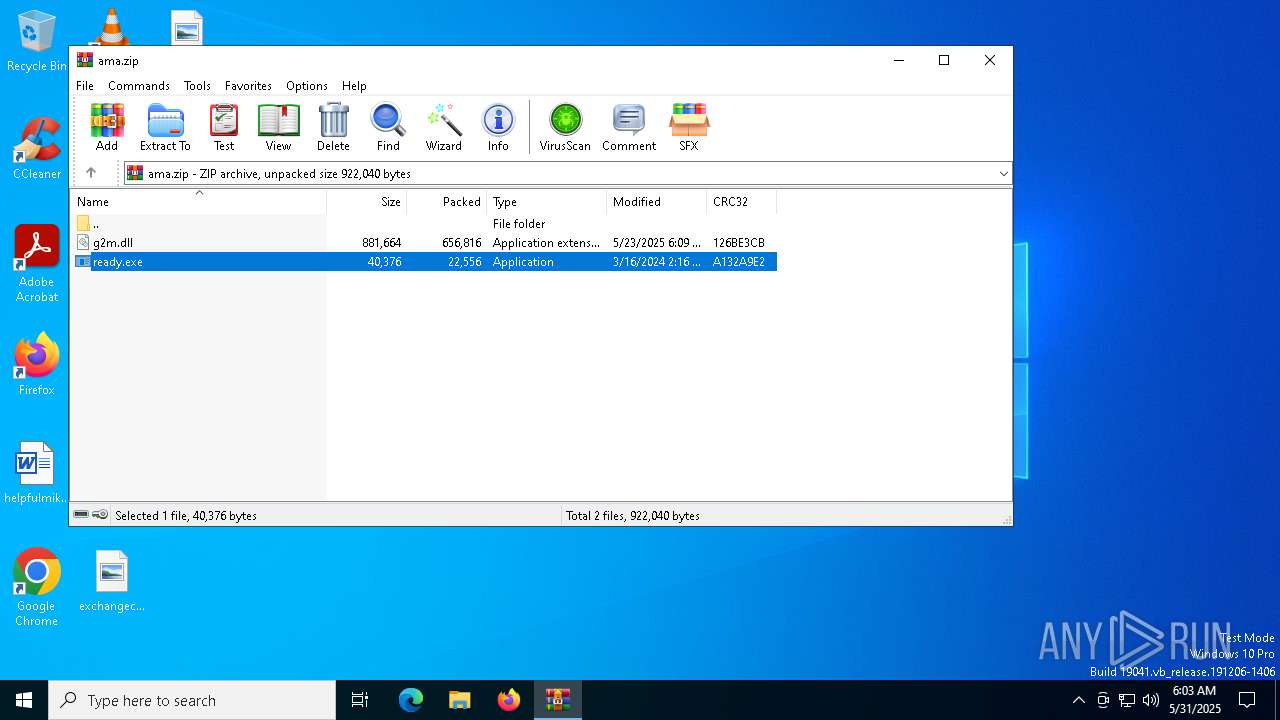
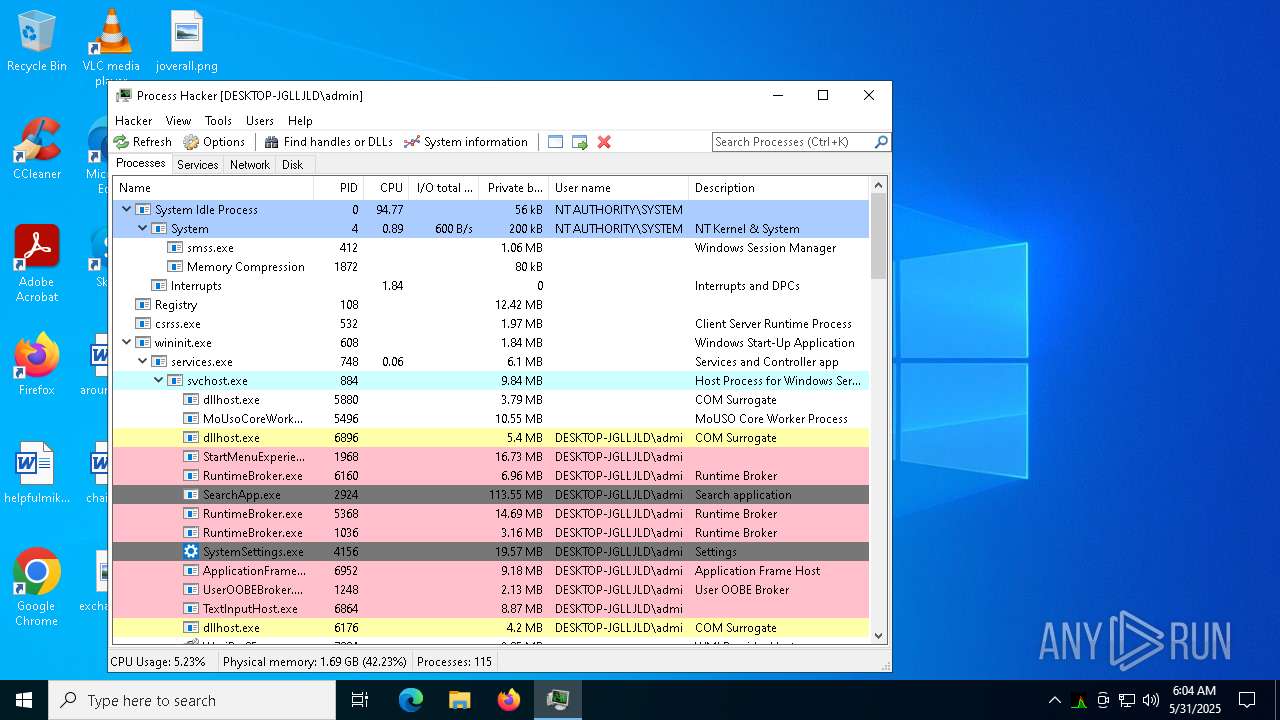
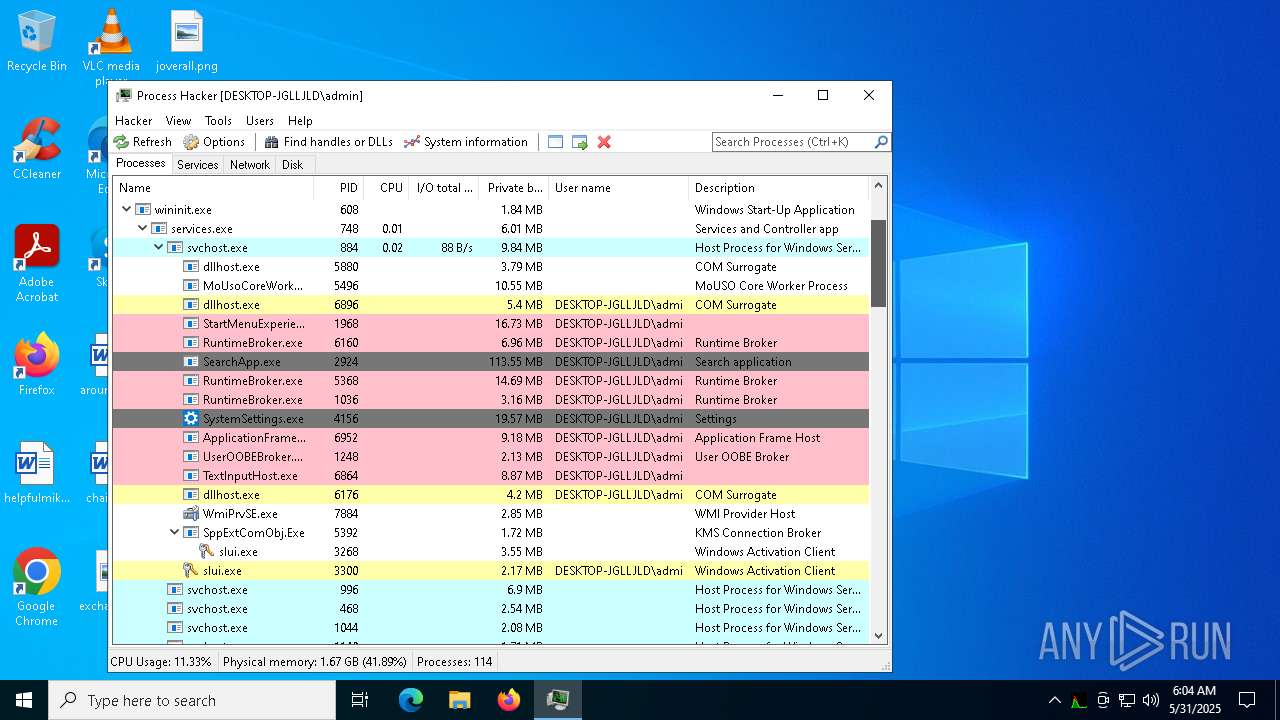
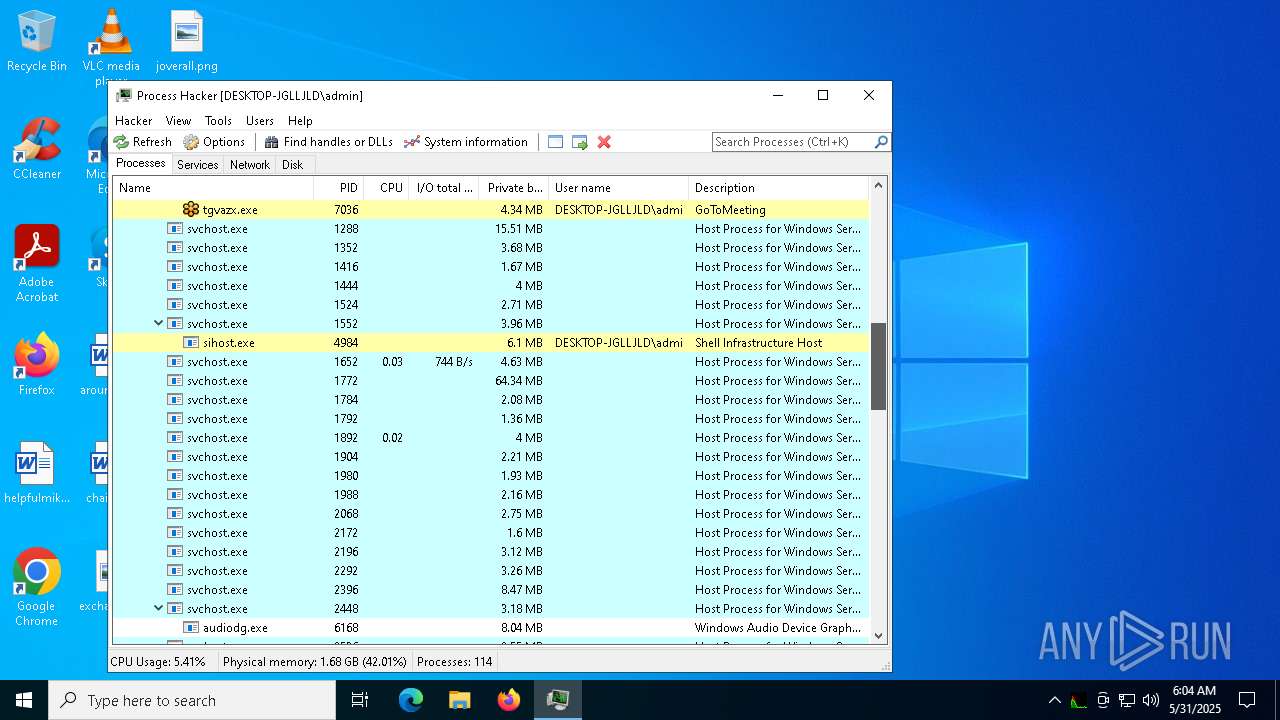
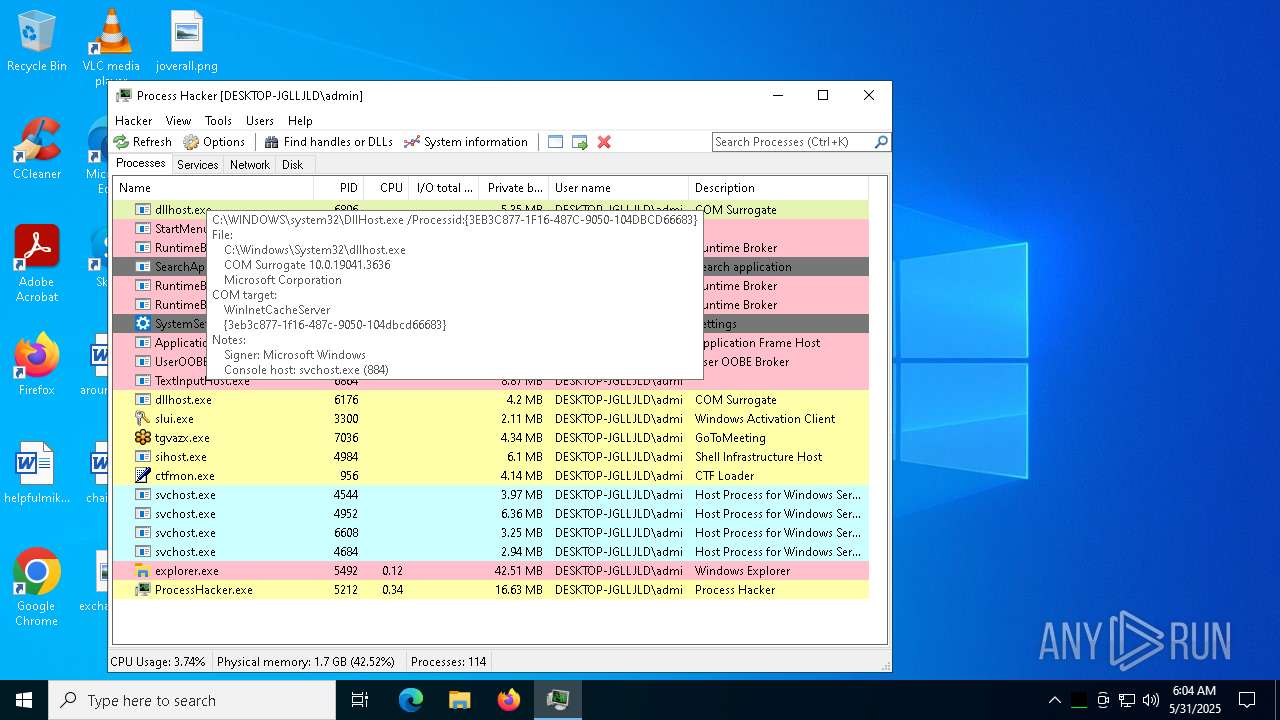
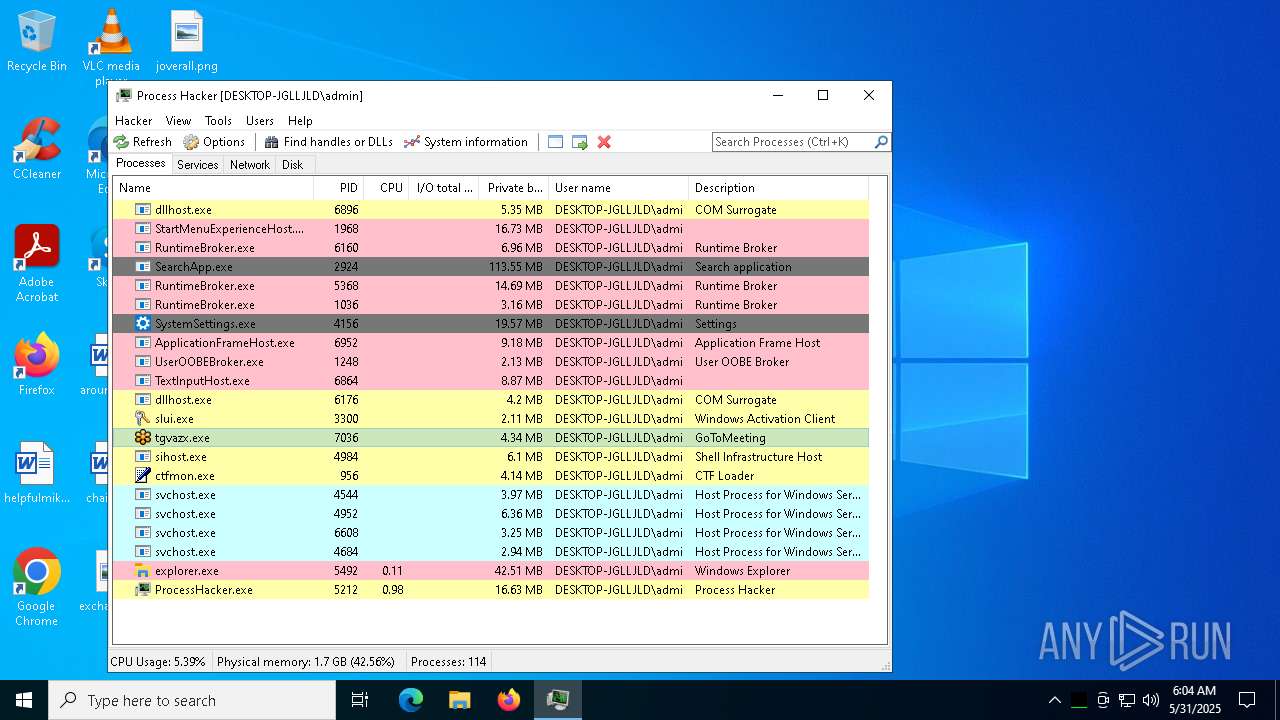
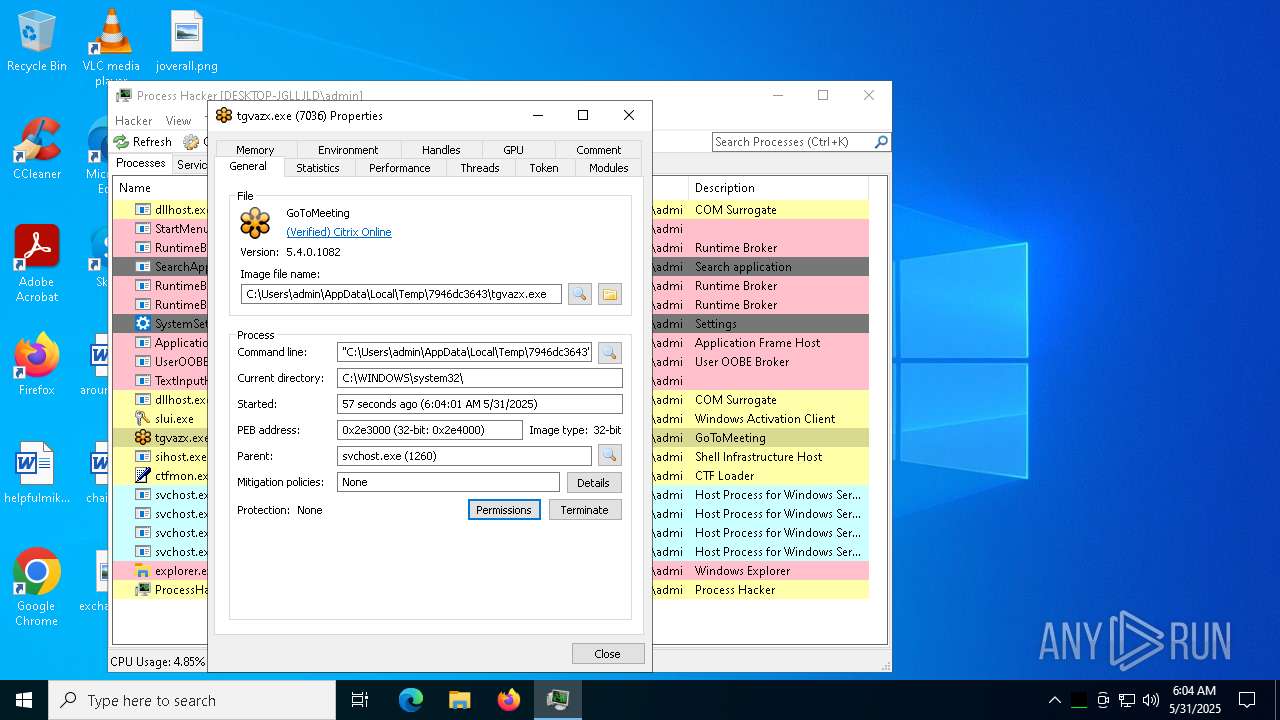
| File name: | ama.zip |
| Full analysis: | https://app.any.run/tasks/372cf1ce-d779-4c5d-b414-b3109e5f16c1 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 31, 2025, 06:03:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 10CFB27AA1F10D978F1E1F754F955A76 |
| SHA1: | 61138CA08BCDFA42026AC9643E04E013858A31DB |
| SHA256: | B77C02B3AEA649B5E3F68F34694DA0C5FD9EDB59F59A834939AD3A00CFEB8125 |
| SSDEEP: | 24576:GSBZhV2UKy9f6s1veJUlgO7dOpQyu8RjxD5mUZzShZ0QZqwCFdJLLiYA:GSBZhV2UKy9f6s1veJUlgO7dOpQyu8R+ |
MALICIOUS
SHELLRUNNER has been detected
- WinRAR.exe (PID: 6740)
- ready.exe (PID: 6992)
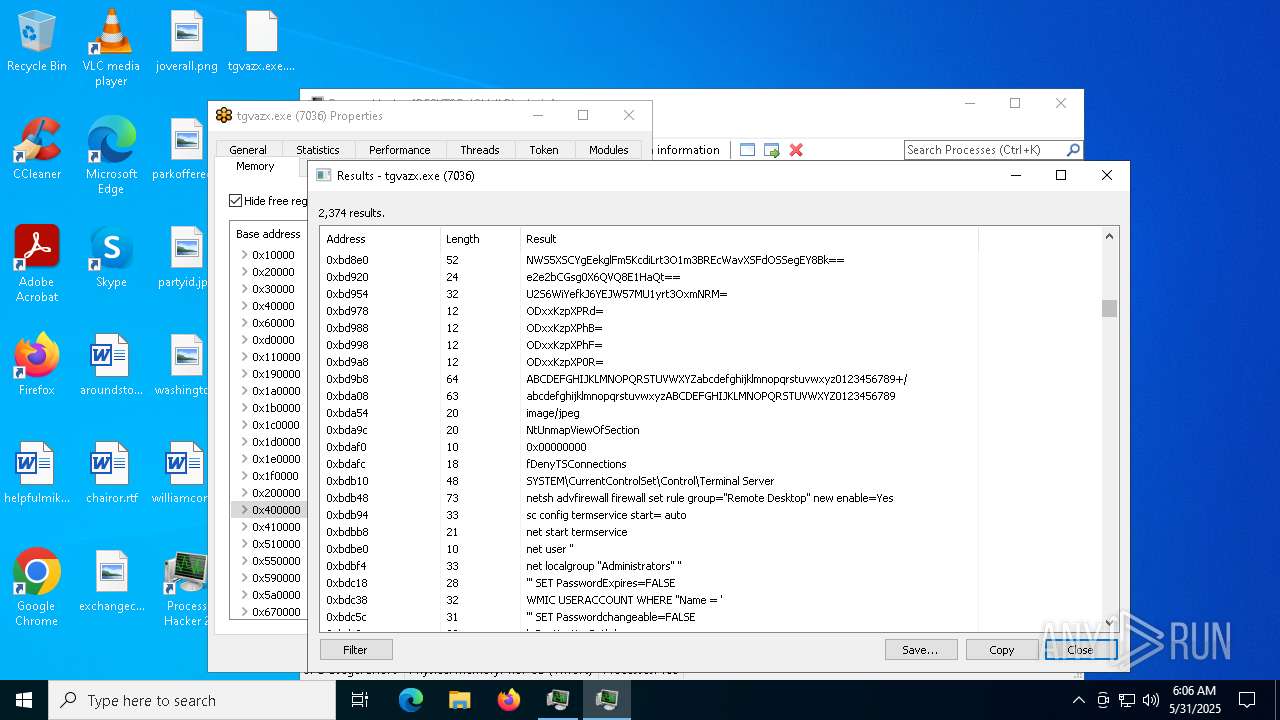
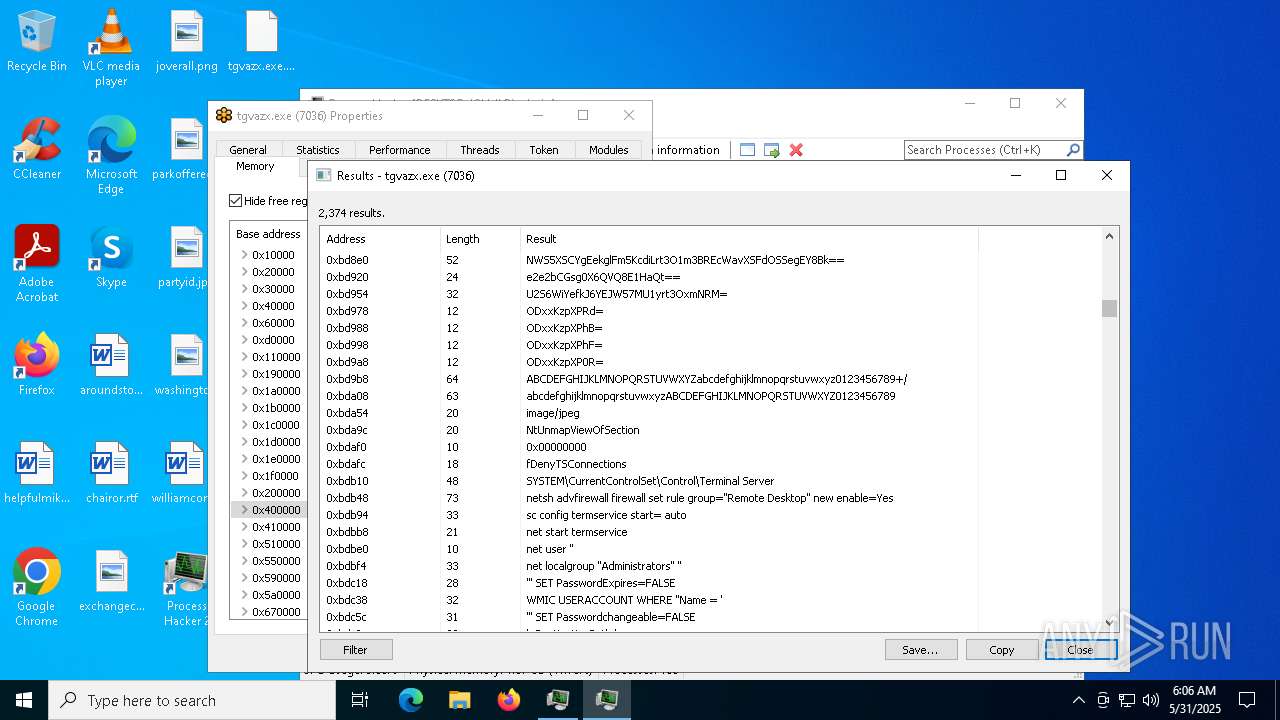
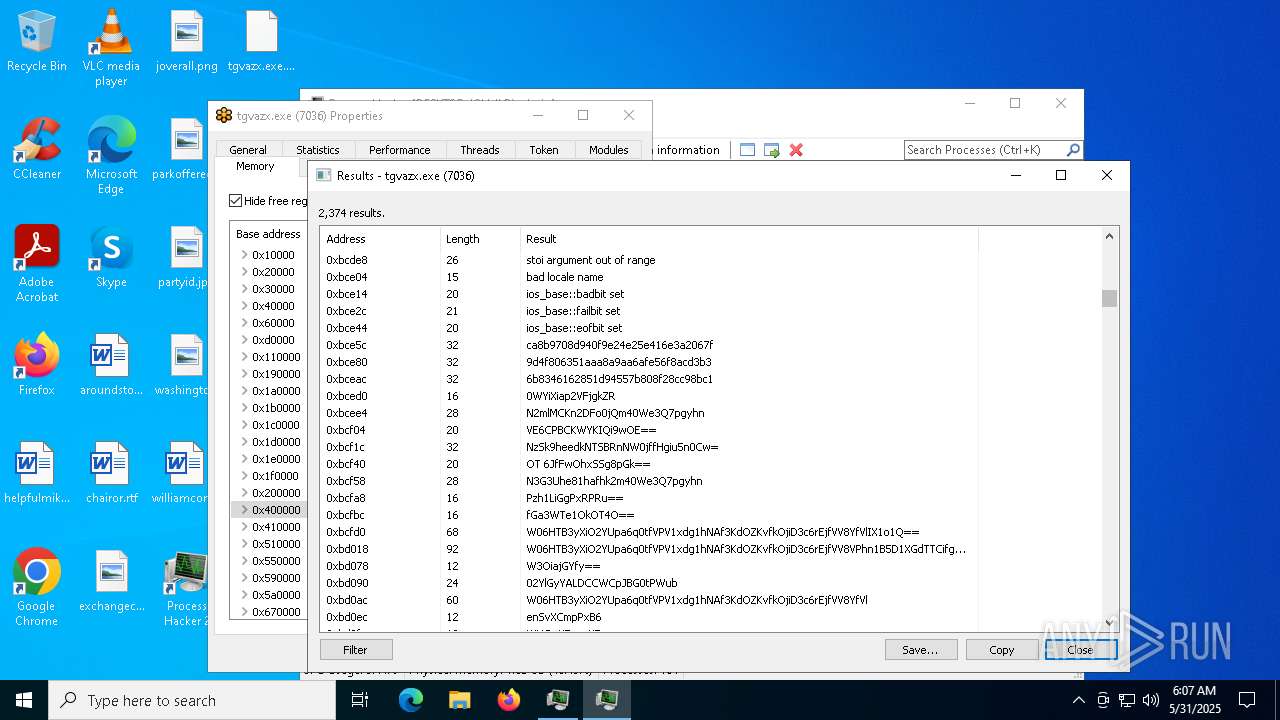
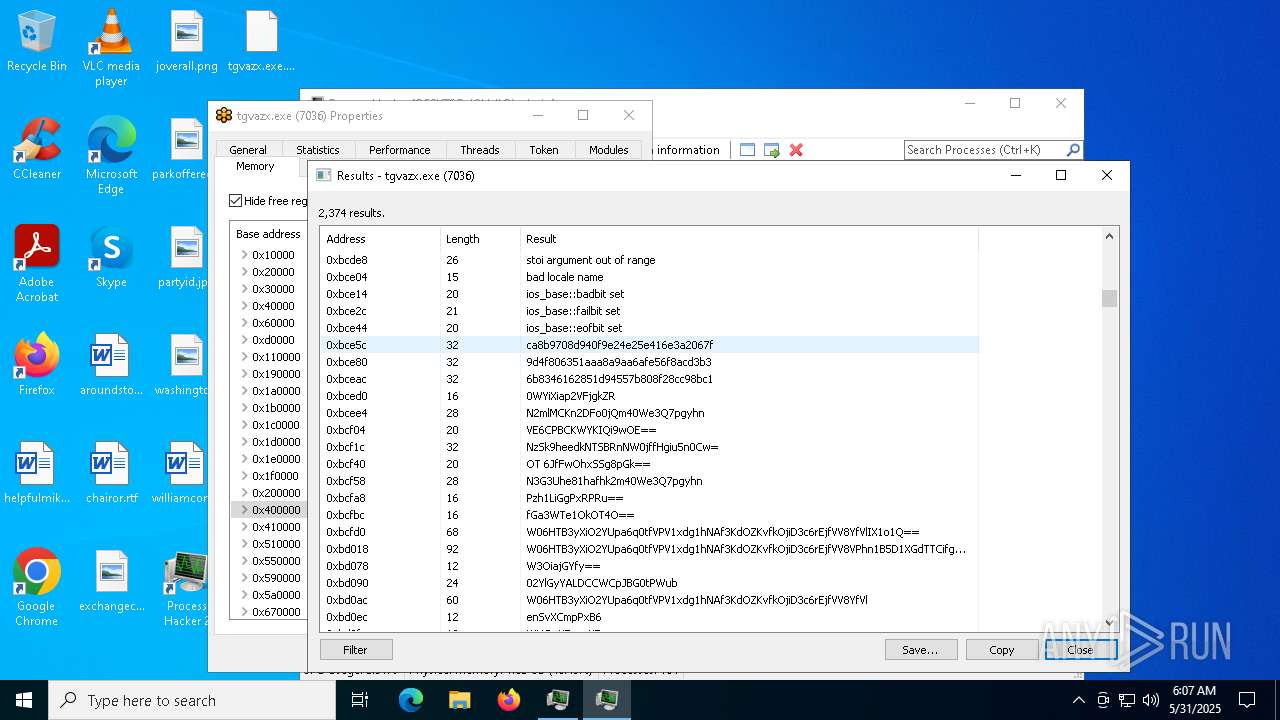
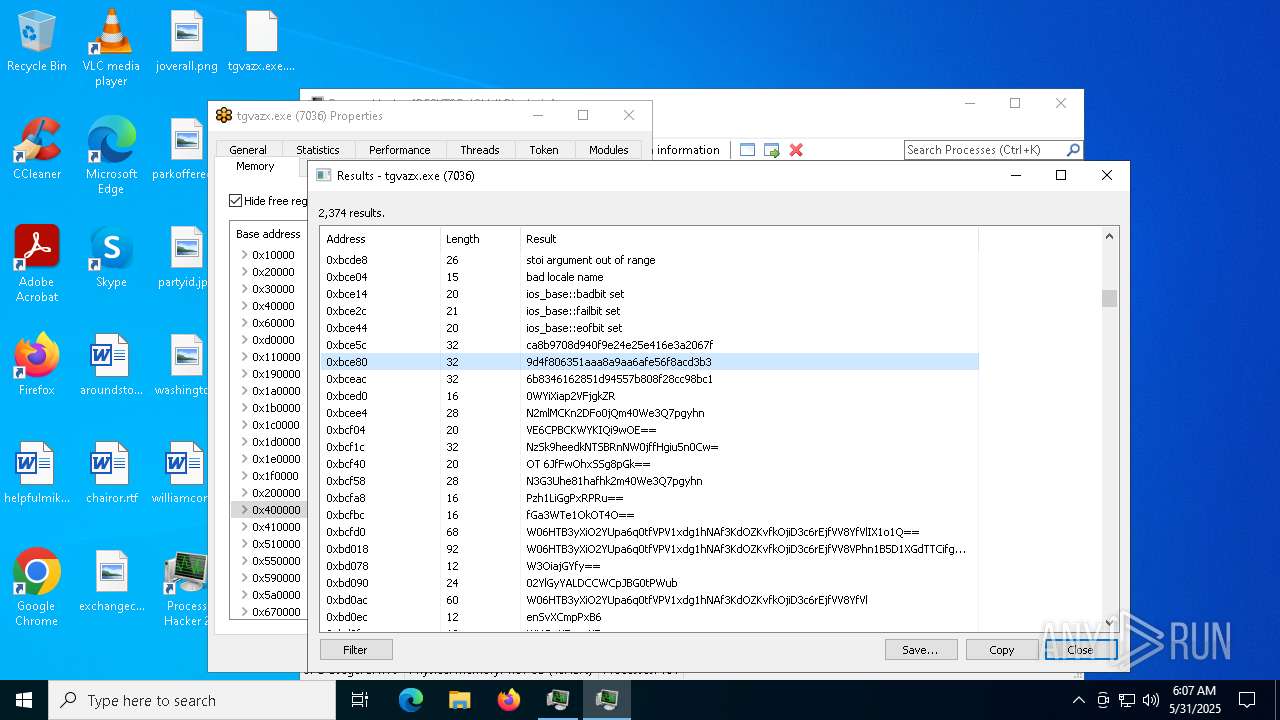
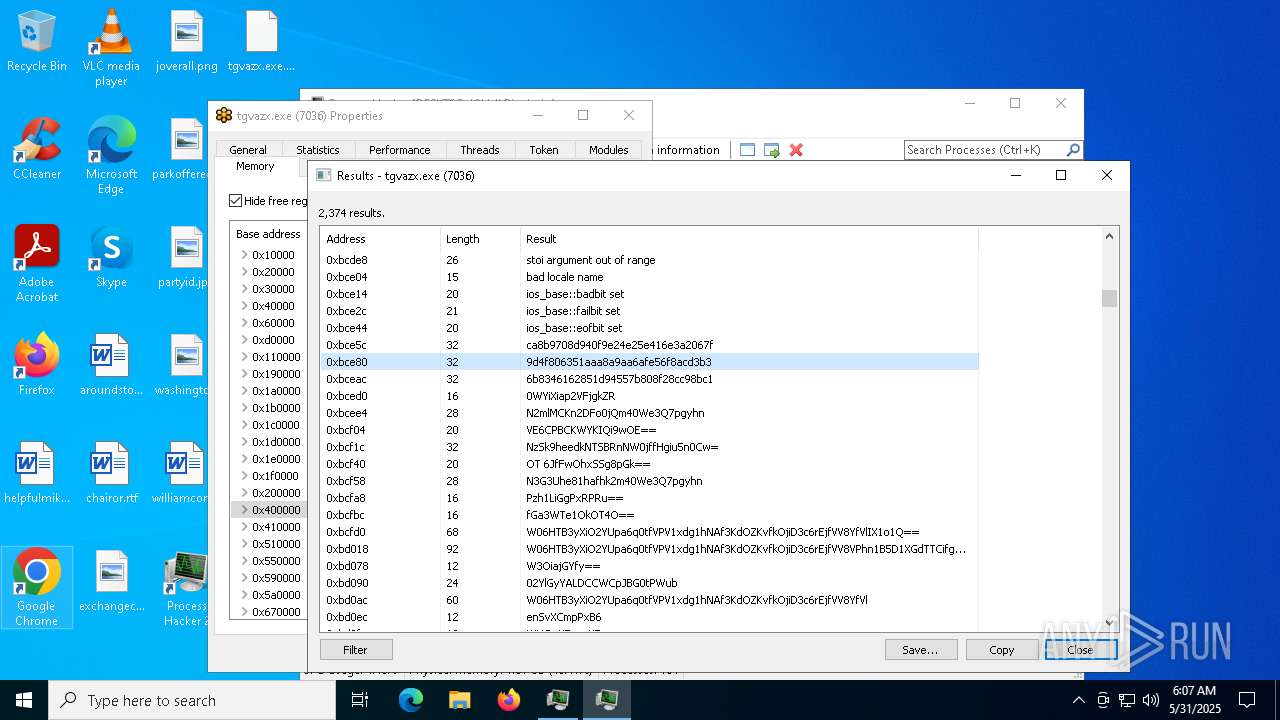
- tgvazx.exe (PID: 5400)
- WerFault.exe (PID: 1240)
- WerFault.exe (PID: 1676)
- tgvazx.exe (PID: 7036)
Executing a file with an untrusted certificate
- ready.exe (PID: 6992)
- tgvazx.exe (PID: 5400)
- tgvazx.exe (PID: 7036)
Connects to the CnC server
- tgvazx.exe (PID: 7036)
AMADEY has been detected (YARA)
- tgvazx.exe (PID: 7036)
OUSABAN has been detected (YARA)
- tgvazx.exe (PID: 7036)
AMADEY has been detected (SURICATA)
- tgvazx.exe (PID: 7036)
Vulnerable driver has been detected
- processhacker-2.39-setup.tmp (PID: 3272)
SUSPICIOUS
Executable content was dropped or overwritten
- ready.exe (PID: 6992)
- processhacker-2.39-setup.exe (PID: 8188)
- processhacker-2.39-setup.exe (PID: 2596)
- processhacker-2.39-setup.tmp (PID: 3272)
- ProcessHacker.exe (PID: 5212)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6740)
- ready.exe (PID: 6992)
- tgvazx.exe (PID: 7036)
- processhacker-2.39-setup.tmp (PID: 5324)
- ProcessHacker.exe (PID: 5212)
Starts itself from another location
- ready.exe (PID: 6992)
Executes application which crashes
- ready.exe (PID: 6992)
- tgvazx.exe (PID: 5400)
The process executes via Task Scheduler
- tgvazx.exe (PID: 7036)
Contacting a server suspected of hosting an CnC
- tgvazx.exe (PID: 7036)
Connects to the server without a host name
- tgvazx.exe (PID: 7036)
Reads the Windows owner or organization settings
- processhacker-2.39-setup.tmp (PID: 3272)
Process drops legitimate windows executable
- processhacker-2.39-setup.tmp (PID: 3272)
Drops a system driver (possible attempt to evade defenses)
- processhacker-2.39-setup.tmp (PID: 3272)
There is functionality for taking screenshot (YARA)
- ProcessHacker.exe (PID: 5212)
INFO
Create files in a temporary directory
- ready.exe (PID: 6992)
- processhacker-2.39-setup.exe (PID: 8188)
- processhacker-2.39-setup.exe (PID: 2596)
- processhacker-2.39-setup.tmp (PID: 3272)
Checks supported languages
- ready.exe (PID: 6992)
- tgvazx.exe (PID: 5400)
- tgvazx.exe (PID: 7036)
- processhacker-2.39-setup.exe (PID: 8188)
- processhacker-2.39-setup.tmp (PID: 5324)
- processhacker-2.39-setup.exe (PID: 2596)
- processhacker-2.39-setup.tmp (PID: 3272)
- ProcessHacker.exe (PID: 5212)
Process checks computer location settings
- ready.exe (PID: 6992)
- processhacker-2.39-setup.tmp (PID: 5324)
Reads the computer name
- ready.exe (PID: 6992)
- tgvazx.exe (PID: 7036)
- processhacker-2.39-setup.tmp (PID: 5324)
- processhacker-2.39-setup.tmp (PID: 3272)
- ProcessHacker.exe (PID: 5212)
The sample compiled with english language support
- ready.exe (PID: 6992)
- processhacker-2.39-setup.tmp (PID: 3272)
- WinRAR.exe (PID: 6740)
Manual execution by a user
- chrome.exe (PID: 6660)
- notepad.exe (PID: 5588)
Application launched itself
- chrome.exe (PID: 6660)
Creates files or folders in the user directory
- WerFault.exe (PID: 1676)
- WerFault.exe (PID: 1240)
Checks proxy server information
- tgvazx.exe (PID: 7036)
- ProcessHacker.exe (PID: 5212)
Reads the software policy settings
- slui.exe (PID: 3268)
- ProcessHacker.exe (PID: 5212)
Launch of the file from Downloads directory
- chrome.exe (PID: 6660)
Executable content was dropped or overwritten
- chrome.exe (PID: 6660)
- chrome.exe (PID: 8036)
- WinRAR.exe (PID: 6740)
PROCESSHACKER mutex has been found
- processhacker-2.39-setup.tmp (PID: 3272)
Creates files in the program directory
- processhacker-2.39-setup.tmp (PID: 3272)
Compiled with Borland Delphi (YARA)
- processhacker-2.39-setup.tmp (PID: 5324)
Detects InnoSetup installer (YARA)
- processhacker-2.39-setup.tmp (PID: 5324)
- processhacker-2.39-setup.exe (PID: 8188)
Creates a software uninstall entry
- processhacker-2.39-setup.tmp (PID: 3272)
Reads Environment values
- ProcessHacker.exe (PID: 5212)
Reads the machine GUID from the registry
- ProcessHacker.exe (PID: 5212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:23 23:39:54 |
| ZipCRC: | 0x126be3cb |
| ZipCompressedSize: | 656816 |
| ZipUncompressedSize: | 881664 |
| ZipFileName: | g2m.dll |
Total processes
179
Monitored processes
40
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 656 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=3284 --field-trial-handle=2332,i,9452516210366950076,12123256825669683410,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 896 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3732 --field-trial-handle=2332,i,9452516210366950076,12123256825669683410,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffc89a2dc40,0x7ffc89a2dc4c,0x7ffc89a2dc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1240 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6992 -s 1716 | C:\Windows\SysWOW64\WerFault.exe | ready.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3340 --field-trial-handle=2332,i,9452516210366950076,12123256825669683410,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1676 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5400 -s 300 | C:\Windows\SysWOW64\WerFault.exe | tgvazx.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2084 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5356 --field-trial-handle=2332,i,9452516210366950076,12123256825669683410,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=5500 --field-trial-handle=2332,i,9452516210366950076,12123256825669683410,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2596 | "C:\Users\admin\Downloads\processhacker-2.39-setup.exe" /SPAWNWND=$303D6 /NOTIFYWND=$80336 | C:\Users\admin\Downloads\processhacker-2.39-setup.exe | processhacker-2.39-setup.tmp | ||||||||||||
User: admin Company: wj32 Integrity Level: HIGH Description: Process Hacker Setup Exit code: 0 Version: 2.39 (r124) Modules
| |||||||||||||||
| 3268 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
25 606
Read events
25 424
Write events
175
Delete events
7
Modification events
| (PID) Process: | (6740) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6740) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6740) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6740) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ama.zip | |||
| (PID) Process: | (6740) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6740) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6740) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6740) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6660) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6660) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
Executable files
52
Suspicious files
228
Text files
36
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF12139f.TMP | — | |
MD5:— | SHA256:— | |||
| 6660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF1213af.TMP | — | |
MD5:— | SHA256:— | |||
| 6660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF1213af.TMP | — | |
MD5:— | SHA256:— | |||
| 6660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1213ce.TMP | — | |
MD5:— | SHA256:— | |||
| 6660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1213ce.TMP | — | |
MD5:— | SHA256:— | |||
| 6660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF1213ce.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
145
DNS requests
130
Threats
45
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
864 | svchost.exe | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
864 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1388 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1388 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7036 | tgvazx.exe | POST | 200 | 179.43.176.26:80 | http://179.43.176.26/rvZZZb8jrf/index.php | unknown | — | — | unknown |
7036 | tgvazx.exe | POST | 200 | 179.43.176.26:80 | http://LOADSMODS.NET/5cjZaje843pQ/index.php | unknown | — | — | unknown |
7036 | tgvazx.exe | POST | 200 | 179.43.176.26:80 | http://amafiles.net/jd8ejdS3VS/index.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7548 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
864 | svchost.exe | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
864 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
864 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6660 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
ogads-pa.clients6.google.com |
| whitelisted |
apis.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7036 | tgvazx.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
7036 | tgvazx.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
7036 | tgvazx.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
7036 | tgvazx.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
7036 | tgvazx.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
7036 | tgvazx.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
7036 | tgvazx.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
7036 | tgvazx.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
7036 | tgvazx.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
7036 | tgvazx.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |